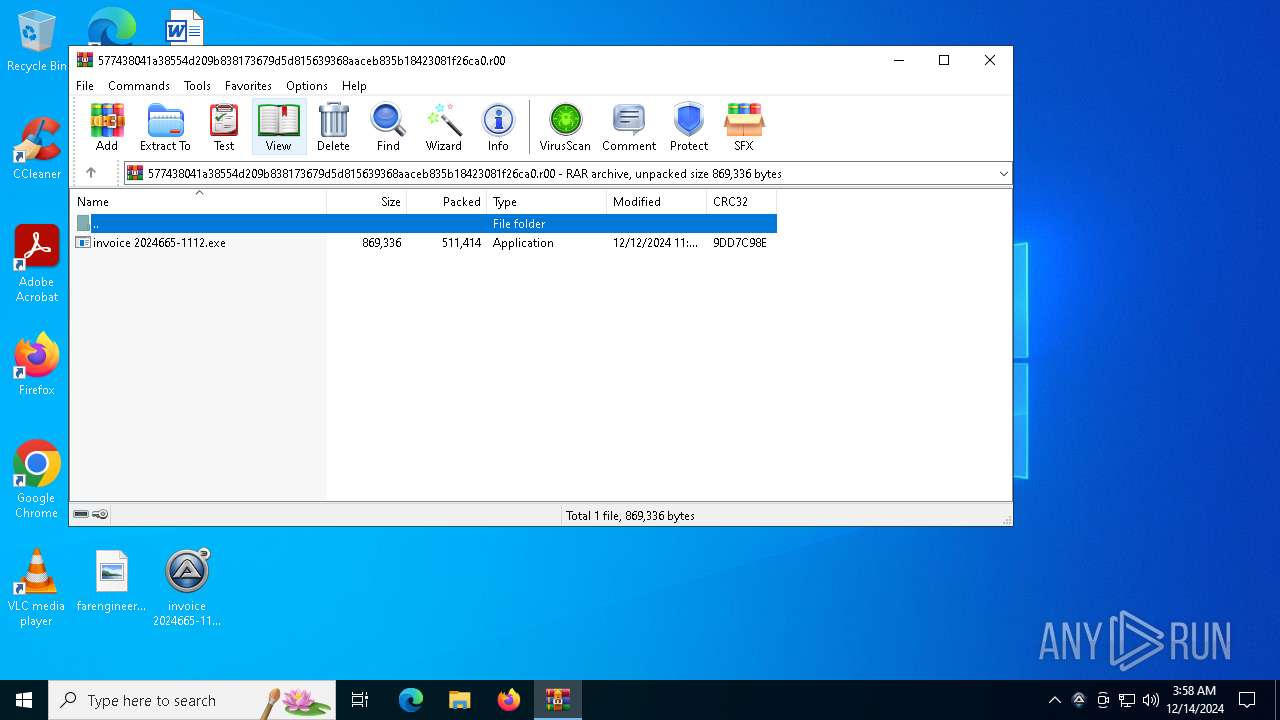
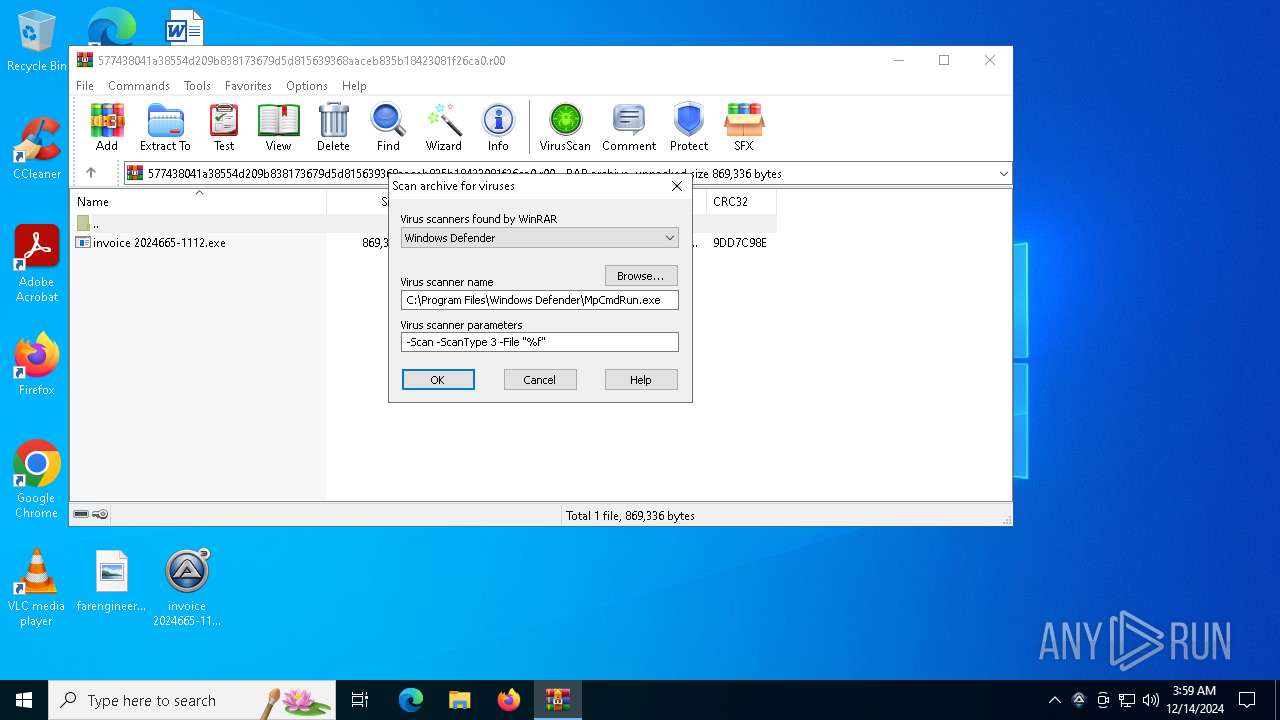
| File name: | 577438041a38554d209b838173679d5d815639368aaceb835b18423081f26ca0.r00 |
| Full analysis: | https://app.any.run/tasks/311c1c9b-26e5-4372-9de0-ab82b0853299 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2024, 03:58:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 0A768B9B6B38CD8FFBF58ACF3E8F54B4 |
| SHA1: | 7DF73CFC685A57076F90944B8A2BBA54B7FDF6B3 |
| SHA256: | 577438041A38554D209B838173679D5D815639368AACEB835B18423081F26CA0 |
| SSDEEP: | 24576:G1WRyYNc72n4VEFa7Rdn7/1ORXaKPpgxYMKT9E8xhH+dmg3OX:G1WRyYNc724SFa9dn7/1O5aKPpaYMKTh |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5720)
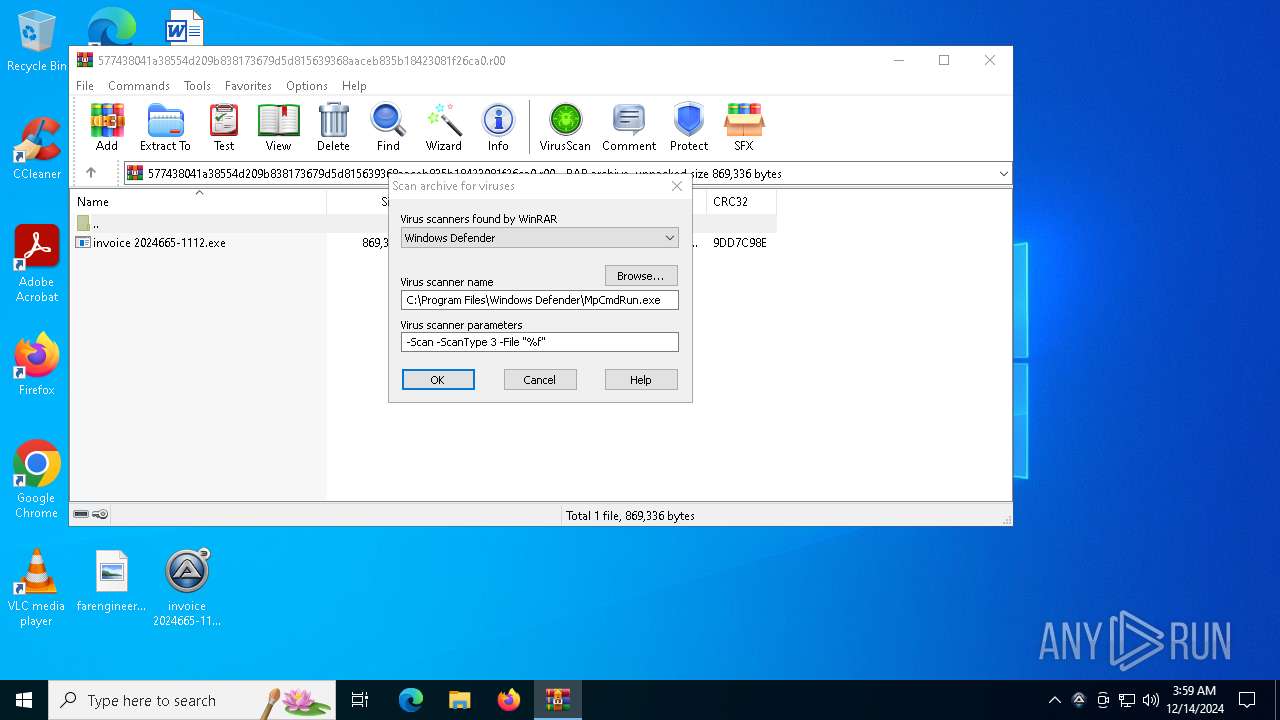
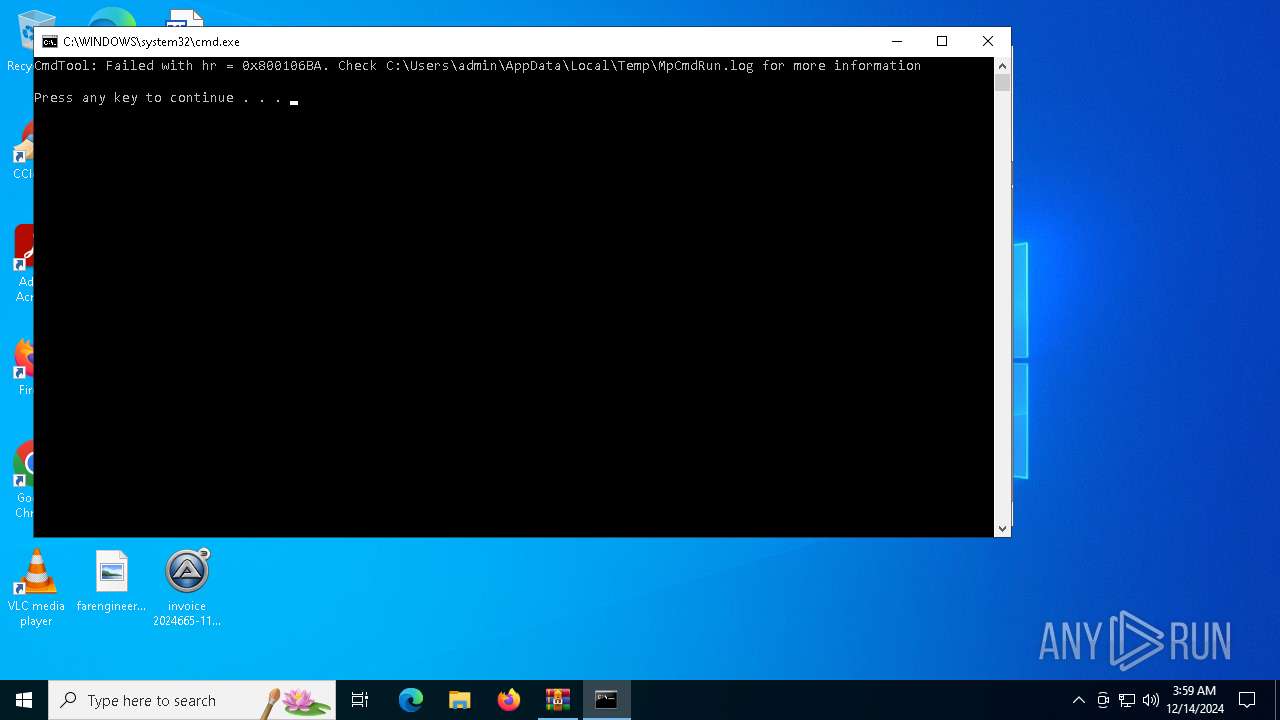
Antivirus name has been found in the command line (generic signature)
- MpCmdRun.exe (PID: 2260)
SUSPICIOUS
Executes application which crashes
- invoice 2024665-1112.exe (PID: 3724)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5720)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 5720)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 5720)
INFO
Manual execution by a user
- invoice 2024665-1112.exe (PID: 3724)
Reads mouse settings
- invoice 2024665-1112.exe (PID: 3724)
Checks supported languages
- invoice 2024665-1112.exe (PID: 3724)
- MpCmdRun.exe (PID: 2260)
Create files in a temporary directory
- invoice 2024665-1112.exe (PID: 3724)
- MpCmdRun.exe (PID: 2260)
Checks proxy server information
- WerFault.exe (PID: 4764)
Reads the software policy settings
- WerFault.exe (PID: 4764)
Creates files or folders in the user directory
- WerFault.exe (PID: 4764)
The sample compiled with english language support
- WinRAR.exe (PID: 5720)
The process uses the downloaded file
- WinRAR.exe (PID: 5720)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5720)
Reads the computer name
- MpCmdRun.exe (PID: 2260)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 511414 |
| UncompressedSize: | 869336 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | invoice 2024665-1112.exe |
Total processes
126
Monitored processes
7
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2008 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2260 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR5720.6633" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3724 | "C:\Users\admin\Desktop\invoice 2024665-1112.exe" | C:\Users\admin\Desktop\invoice 2024665-1112.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Version: 3, 3, 6, 0 Modules
| |||||||||||||||
| 4052 | "C:\Users\admin\Desktop\invoice 2024665-1112.exe" | C:\Windows\SysWOW64\svchost.exe | — | invoice 2024665-1112.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 4520 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR5720.6633\Rar$Scan53470.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4764 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 3724 -s 776 | C:\Windows\SysWOW64\WerFault.exe | invoice 2024665-1112.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5720 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\577438041a38554d209b838173679d5d815639368aaceb835b18423081f26ca0.r00.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
7 898
Read events
7 874
Write events
24
Delete events
0
Modification events
| (PID) Process: | (5720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\577438041a38554d209b838173679d5d815639368aaceb835b18423081f26ca0.r00.rar | |||
| (PID) Process: | (5720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (5720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
1
Suspicious files
4
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4764 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_invoice 2024665-_106ab43f8bfe6f854535ac97a1bc5ee373ca49e3_c46520bf_9fed1424-a1de-4940-a63f-c208f3b59747\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4764 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6EAB.tmp.dmp | binary | |
MD5:3517B7FF83295452F811A8CF1A74FA1B | SHA256:22469D25A95558C253A4135E30C923F89530B6B325E359CB1125F38A9980333D | |||
| 4764 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6FB7.tmp.xml | xml | |
MD5:C709BCDD935319A83DBF28308EA53EE0 | SHA256:4000050C959CBCCF09408F4A223BCE125D358AD65DFAE865CA0935D9D51405DC | |||
| 5720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5720.6633\577438041a38554d209b838173679d5d815639368aaceb835b18423081f26ca0.r00\invoice 2024665-1112.exe | executable | |
MD5:01558475F7D940F2FD80C0F2E4819169 | SHA256:A4FA23E8786DE563FD0EEF88E32EA883672DC02C823F119EE8FFC82C0C0B6F9E | |||
| 3724 | invoice 2024665-1112.exe | C:\Users\admin\AppData\Local\Temp\aut699A.tmp | binary | |
MD5:B9CF23BA012C5D6D53A0DF733571C8A1 | SHA256:6331389AC502FAFB2D28CA331EDF3E1807CD148333F88864BA9BC40891C0F781 | |||
| 4764 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\invoice 2024665-1112.exe.3724.dmp | binary | |
MD5:A936F9D7B5C2C25EACB44F03A49BC8E3 | SHA256:BB8C9D9402BC224692EDF9B8544AEFA9AF2A698679998D4F8CF56633DC27F96D | |||
| 4764 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6F77.tmp.WERInternalMetadata.xml | xml | |
MD5:9C7D4266DC38F91CC3D07828191BA481 | SHA256:06A3FC443B07C7E0F5EE8765802696B1BF5D5875DF54217AA0ECF3F6812538C4 | |||
| 3724 | invoice 2024665-1112.exe | C:\Users\admin\AppData\Local\Temp\juvenilely | binary | |
MD5:6FD67241227ADA43F42E1B27FEA54C0A | SHA256:94AF449A72538676C6058F6017ABFFDE3A950CDF8689186EFD8E82B5954C0E80 | |||
| 2260 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:A4350BEA1A58DC5FA4F27C374666182D | SHA256:CFAB1C8A385DF95D3C46FEBC081DB9A49979E800F38BE2EE6823EF0BDAC0CE4E | |||
| 5720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5720.6633\Rar$Scan53470.bat | text | |
MD5:CEB61561B2233BBDB2E2FC52018C7338 | SHA256:A34326AB3CE8DFB24FF221609829FBB0FCEDC89B10396AF8AEB13B41FE25D2E3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
18
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2356 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2356 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2356 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2356 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2356 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4764 | WerFault.exe | 104.208.16.94:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |