| File name: | Setup.zip |
| Full analysis: | https://app.any.run/tasks/6fc18a9b-e8ae-4674-823a-94c77f2eb8a6 |
| Verdict: | Malicious activity |
| Threats: | INC Ransomware is a ransomware-as-a-service (RaaS) spotted in mid-2023. It targets industries like retail, real estate, finance, healthcare, and education, primarily in the U.S. and UK. It encrypts and exfiltrates data demanding a ransom. It employs advanced evasion techniques, destroys backup, and abuses legitimate system tools at all the stages of the kill chain. |
| Analysis date: | May 15, 2025, 10:55:41 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | AEF3F786A2C692663CA0C8A109287AA5 |
| SHA1: | 28C2DC6E060E2D5F249372142F80B7849AF6DB5B |
| SHA256: | 577145456BF9EB4000B0CD161B0E57FEB166EB7643108638FE59C56A3EDF1A15 |
| SSDEEP: | 3072:B+Pl/knG9W28rInpqaOTWUGxHOlSKQyLjx/8/u8llm/:B+PlMGt8rcfkJuRcd/8G8Hm/ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6572)
INC has been found (auto)
- WinRAR.exe (PID: 6572)
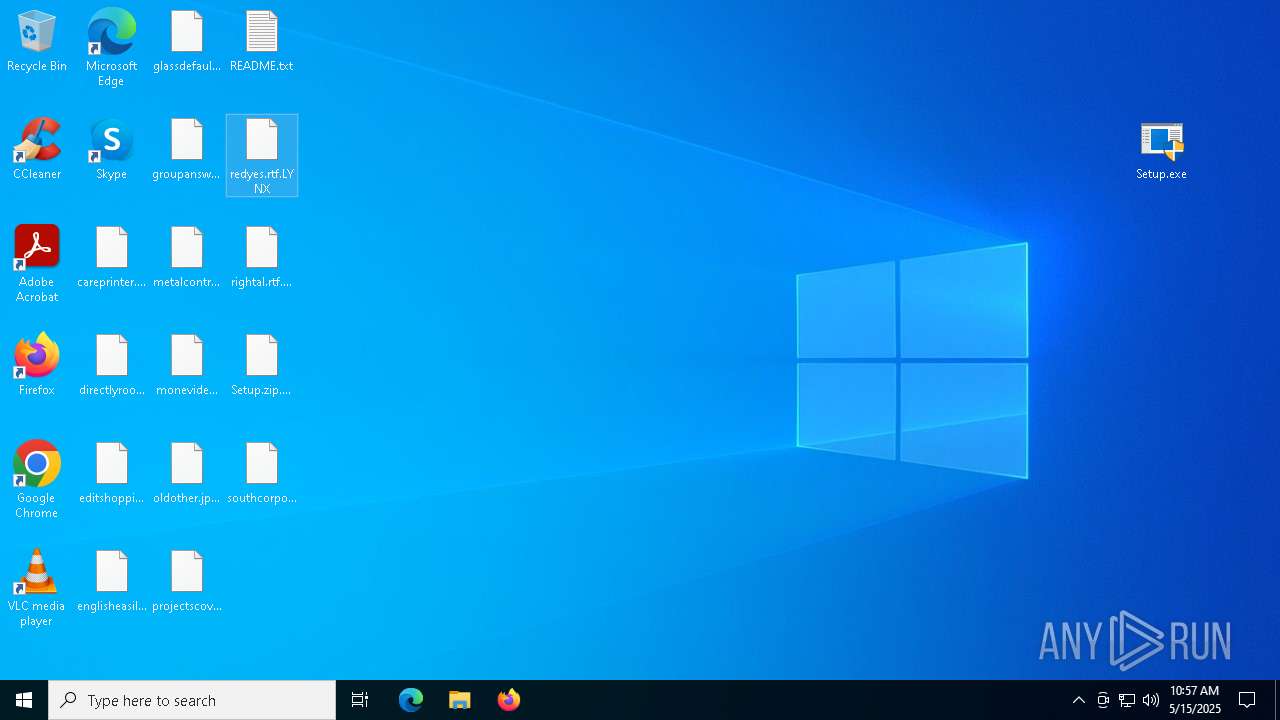
Renames files like ransomware
- Setup.exe (PID: 7956)
RANSOMWARE has been detected
- Setup.exe (PID: 7956)
LYNX has been detected (YARA)
- Setup.exe (PID: 7956)
LYNX has been detected
- Setup.exe (PID: 7956)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- Setup.exe (PID: 7956)
Creates file in the systems drive root
- Setup.exe (PID: 7956)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6572)
Manual execution by a user
- Setup.exe (PID: 7908)
- Setup.exe (PID: 7956)
Checks supported languages
- Setup.exe (PID: 7956)
Reads the computer name
- Setup.exe (PID: 7956)
Reads the machine GUID from the registry
- Setup.exe (PID: 7956)
Creates files in the program directory
- Setup.exe (PID: 7956)
Reads the software policy settings
- slui.exe (PID: 7240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:01 18:45:50 |
| ZipCRC: | 0x2e4740c8 |
| ZipCompressedSize: | 91599 |
| ZipUncompressedSize: | 168960 |
| ZipFileName: | Setup.exe |
Total processes
135
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6572 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Setup.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7208 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7240 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7908 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7956 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225786 Modules
| |||||||||||||||
| 7968 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 9340 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 573
Read events
9 555
Write events
18
Delete events
0
Modification events
| (PID) Process: | (6572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Setup.zip | |||
| (PID) Process: | (6572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
3
Suspicious files
1 074
Text files
313
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7956 | Setup.exe | C:\$WinREAgent\Scratch\README.txt | text | |
MD5:65EC4FF07245CB1EAD57B4C2B4ECCE24 | SHA256:A8FF6F2A9FC190659ABBAF4F359C85F9EF3E93AAB9EA5CF10273A365734EB95B | |||
| 7956 | Setup.exe | C:\$WinREAgent\README.txt | text | |
MD5:65EC4FF07245CB1EAD57B4C2B4ECCE24 | SHA256:A8FF6F2A9FC190659ABBAF4F359C85F9EF3E93AAB9EA5CF10273A365734EB95B | |||
| 7956 | Setup.exe | C:\found.000\dir0000.chk\README.txt | text | |
MD5:65EC4FF07245CB1EAD57B4C2B4ECCE24 | SHA256:A8FF6F2A9FC190659ABBAF4F359C85F9EF3E93AAB9EA5CF10273A365734EB95B | |||
| 7956 | Setup.exe | C:\$WinREAgent\Rollback.xml | binary | |
MD5:018978CB9C354DF4FAE418173C72C47A | SHA256:A55F108527409A073BCB60FE3EF527131A28734E1154D62BA873A7DD121F5744 | |||
| 7956 | Setup.exe | C:\README.txt | text | |
MD5:65EC4FF07245CB1EAD57B4C2B4ECCE24 | SHA256:A8FF6F2A9FC190659ABBAF4F359C85F9EF3E93AAB9EA5CF10273A365734EB95B | |||
| 7956 | Setup.exe | C:\$WinREAgent\Rollback\README.txt | text | |
MD5:65EC4FF07245CB1EAD57B4C2B4ECCE24 | SHA256:A8FF6F2A9FC190659ABBAF4F359C85F9EF3E93AAB9EA5CF10273A365734EB95B | |||
| 6572 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6572.37949\Setup.exe | executable | |
MD5:B1D81E8BBECCCC547645D17395538A2D | SHA256:0315DBB793F855F154AA8D227151F1098BD9B580A4F85064648B85BAC1321663 | |||
| 7956 | Setup.exe | C:\$WinREAgent\Backup\README.txt | text | |
MD5:65EC4FF07245CB1EAD57B4C2B4ECCE24 | SHA256:A8FF6F2A9FC190659ABBAF4F359C85F9EF3E93AAB9EA5CF10273A365734EB95B | |||
| 7956 | Setup.exe | C:\$WinREAgent\Backup\location.txt.LYNX | binary | |
MD5:242EFCF481CA8628C6938854E41022FF | SHA256:0A076BB3BAEE050400AA2E0E1221E9677B3D90BCCE8DCDF965C778DBC20BE644 | |||
| 7956 | Setup.exe | C:\$WinREAgent\Backup\location.txt | binary | |
MD5:242EFCF481CA8628C6938854E41022FF | SHA256:0A076BB3BAEE050400AA2E0E1221E9677B3D90BCCE8DCDF965C778DBC20BE644 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7776 | SIHClient.exe | GET | 200 | 23.12.150.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7776 | SIHClient.exe | GET | 200 | 23.12.150.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |