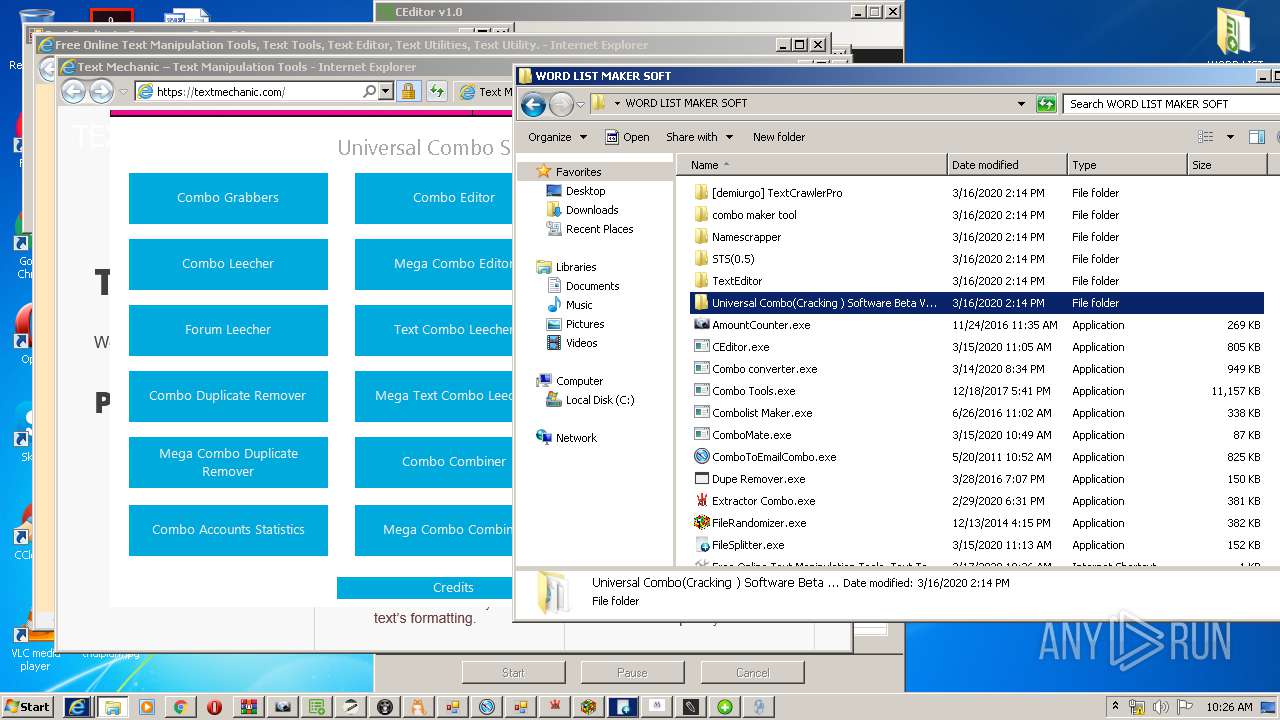
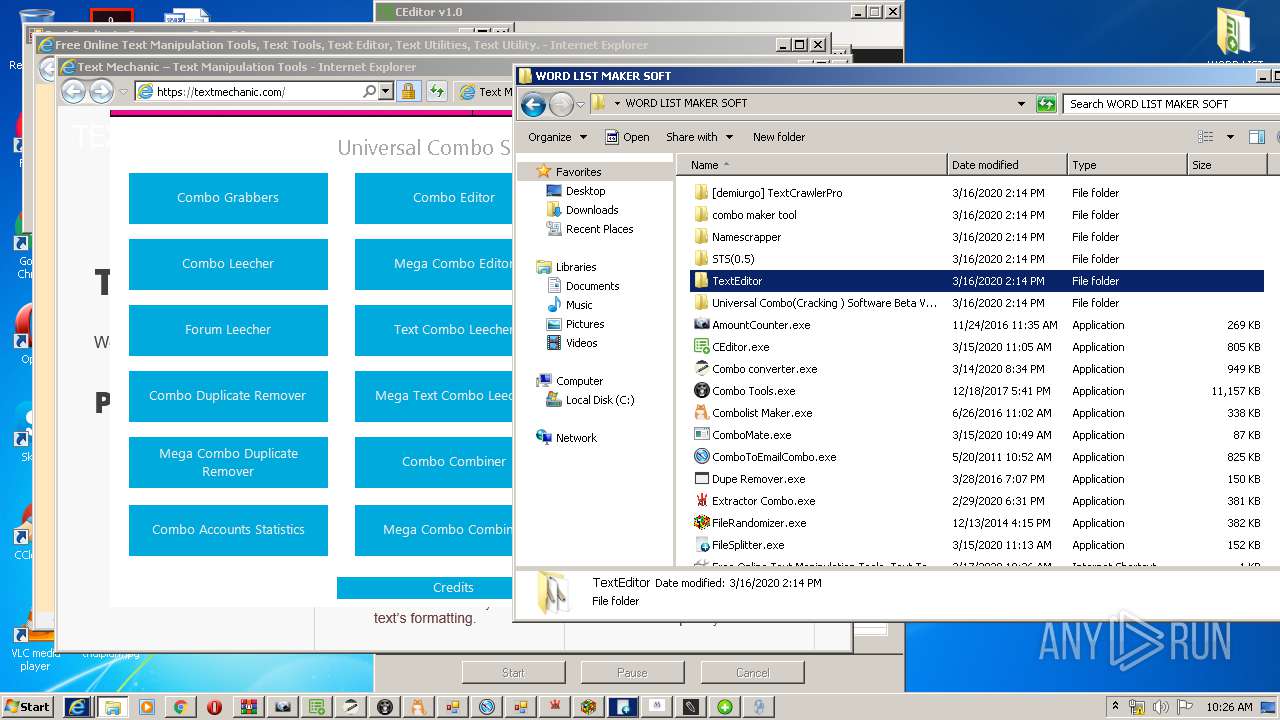
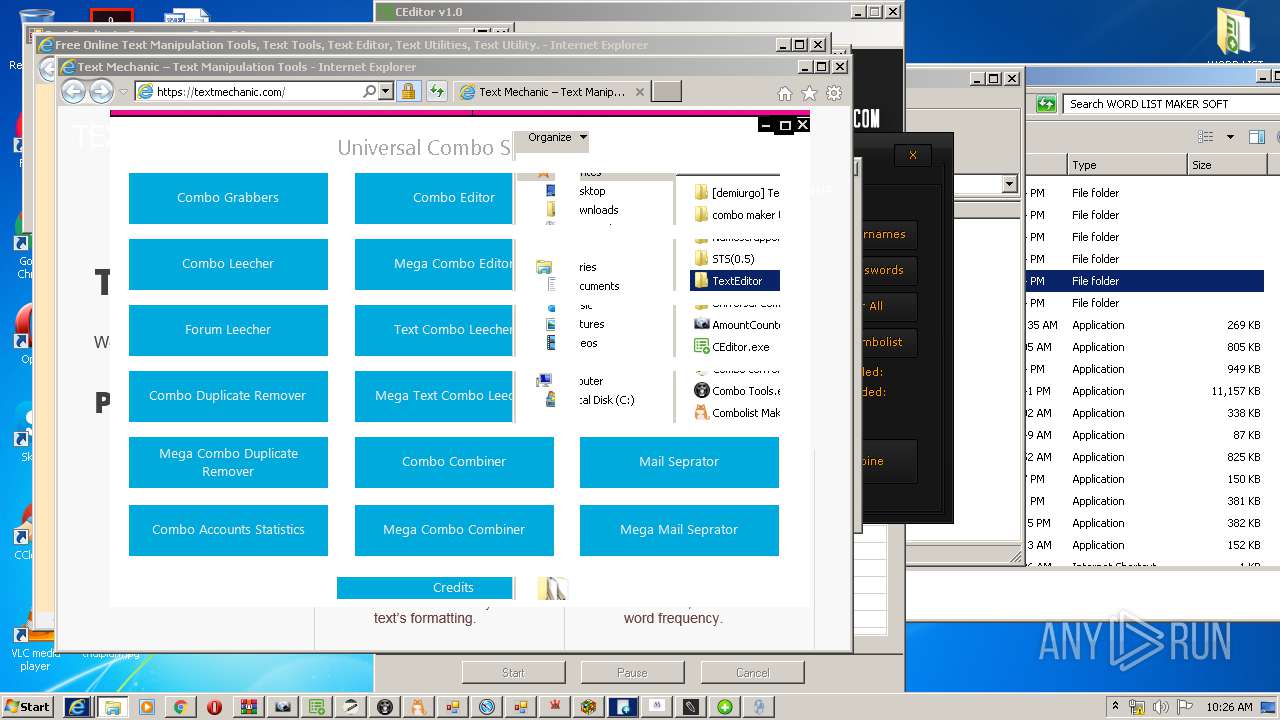
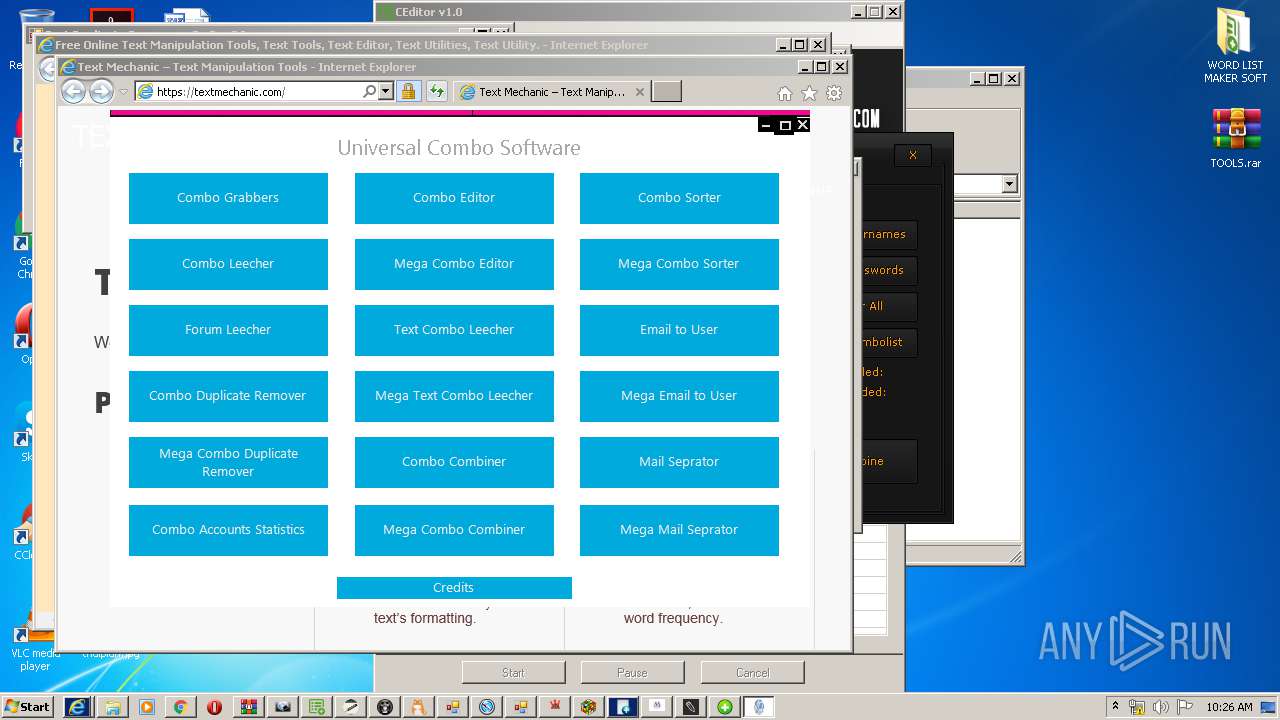
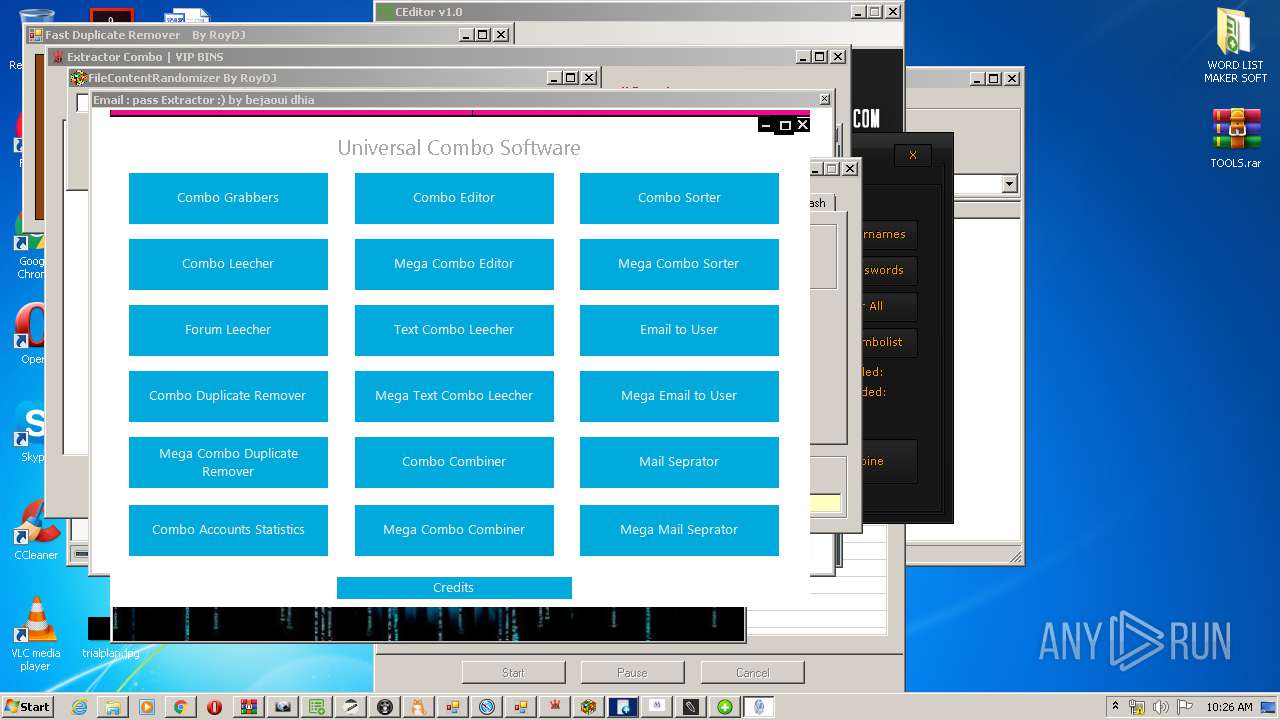
| URL: | https://anonfiles.com/Z3R4M1heoe/TOOLS_rar |
| Full analysis: | https://app.any.run/tasks/80fc6054-854c-4017-a4b5-dff1872d70d1 |
| Verdict: | Malicious activity |
| Analysis date: | March 17, 2020, 10:25:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8837838E89BF1C2B3BEAE4C3D580B59C |
| SHA1: | 51D6C9C6D15A847E2E1D9D5B2512E58870F5CAD8 |
| SHA256: | 5766488410B2AAE5192A09E109DBB9EF6D16F4B14DE7CCB63646EB475D4C6CEE |
| SSDEEP: | 3:N8M22UnxVO:2M22QO |
MALICIOUS
Application was dropped or rewritten from another process
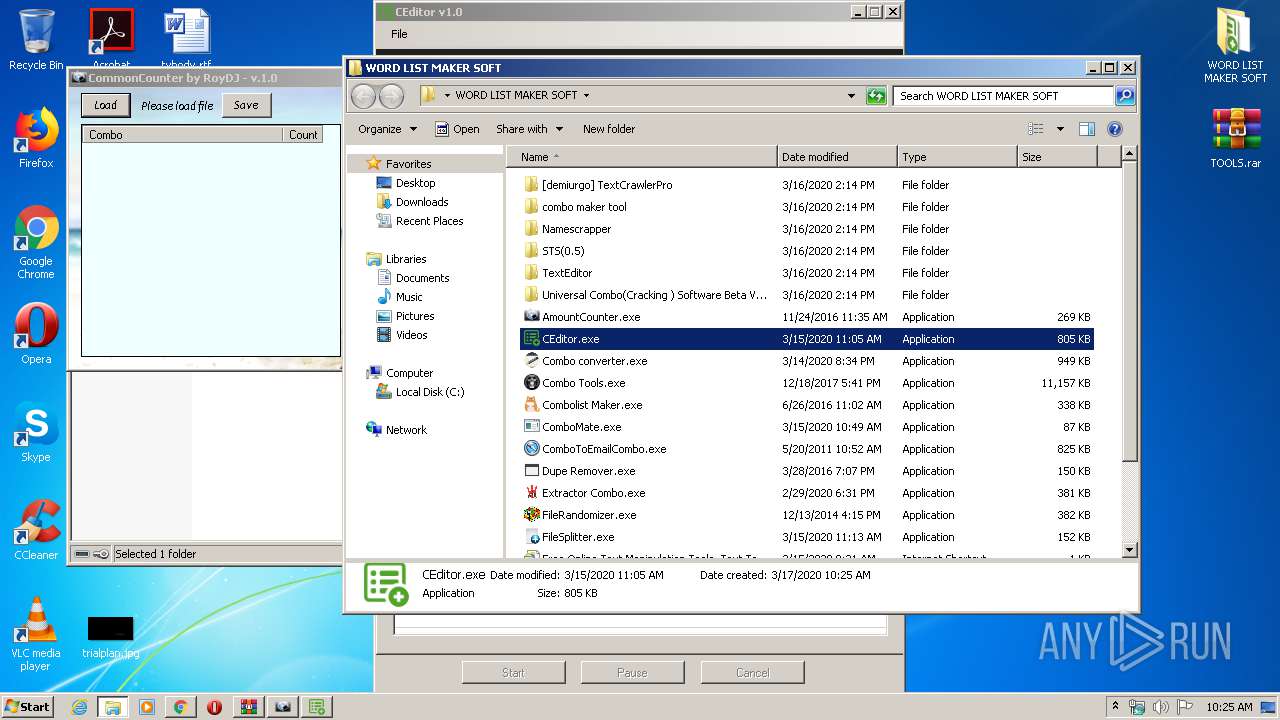
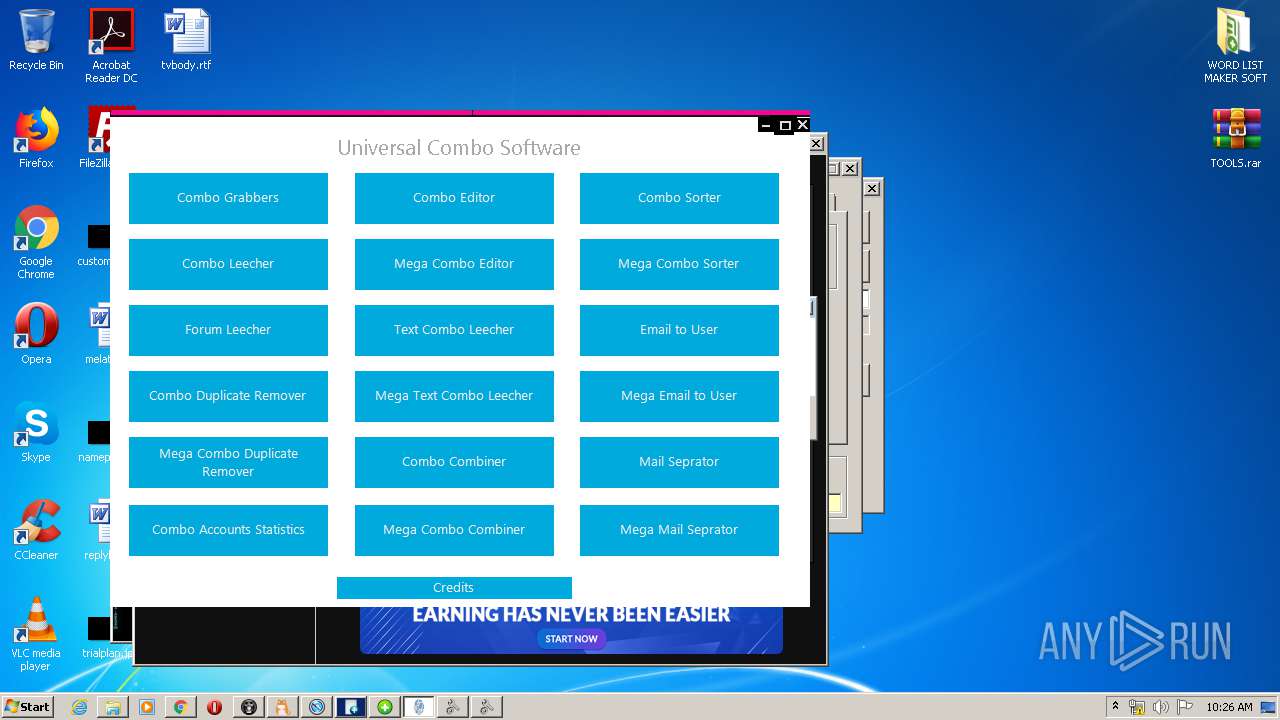
- AmountCounter.exe (PID: 3364)
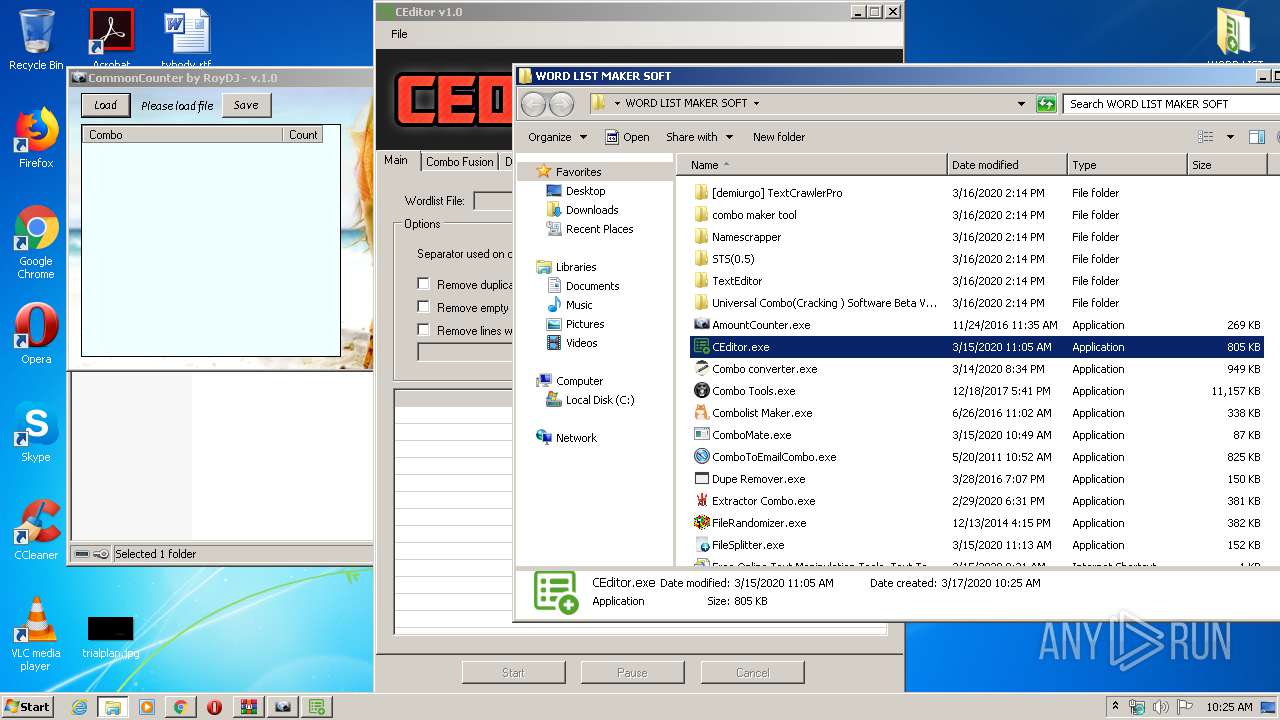
- CEditor.exe (PID: 3212)
- ComboToEmailCombo.exe (PID: 2408)
- ComboMate.exe (PID: 2340)
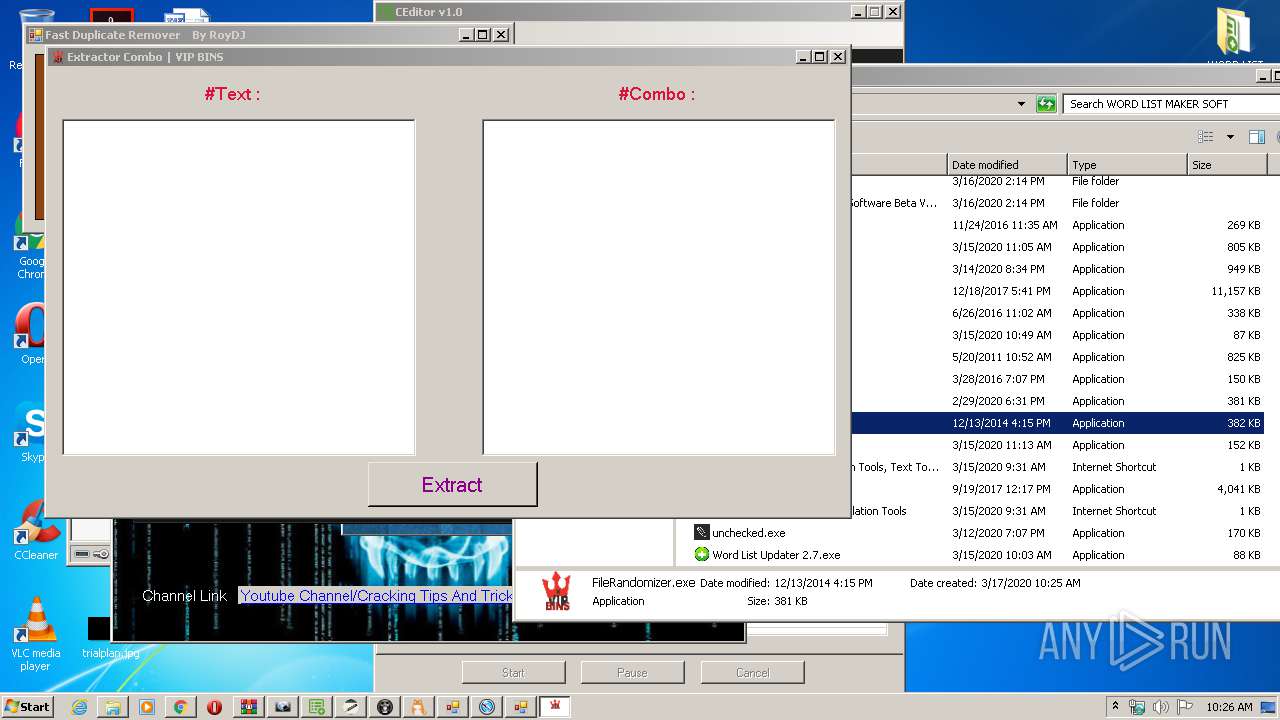
- Extractor Combo.exe (PID: 2872)
- Dupe Remover.exe (PID: 2356)
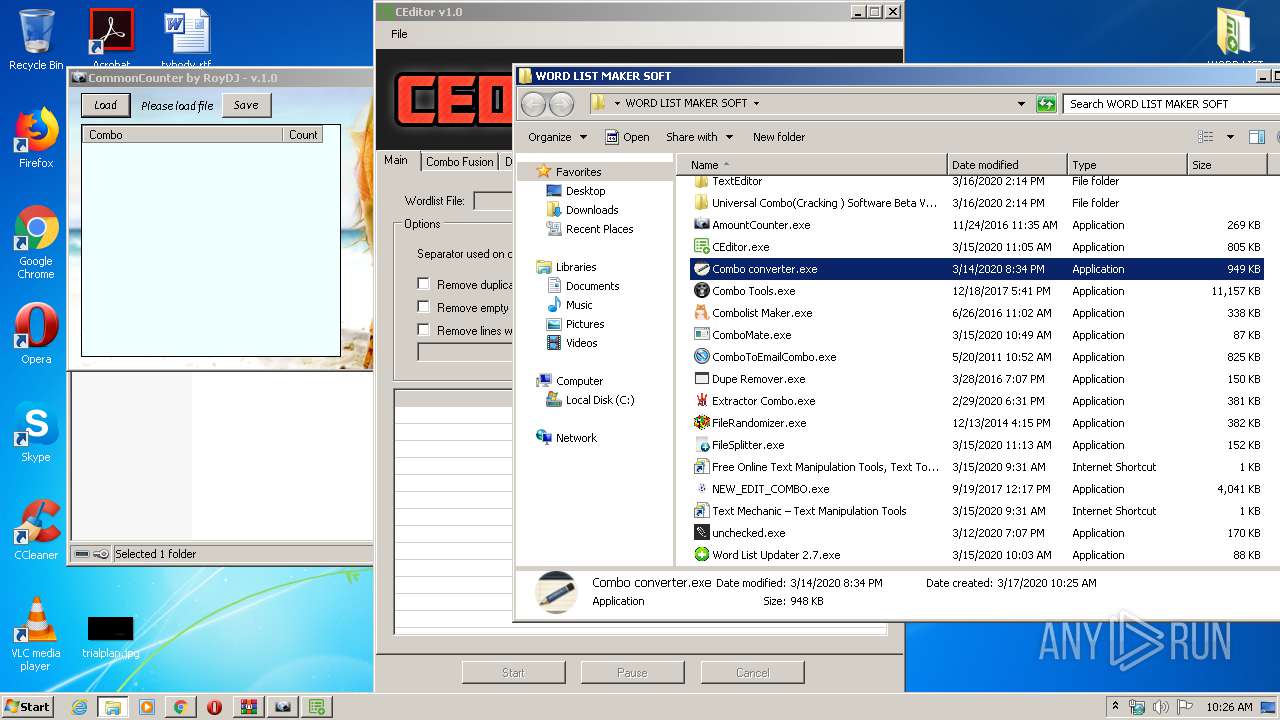
- Combo converter.exe (PID: 2620)
- Combo Tools.exe (PID: 2664)
- Combolist Maker.exe (PID: 2056)
- FileRandomizer.exe (PID: 2816)
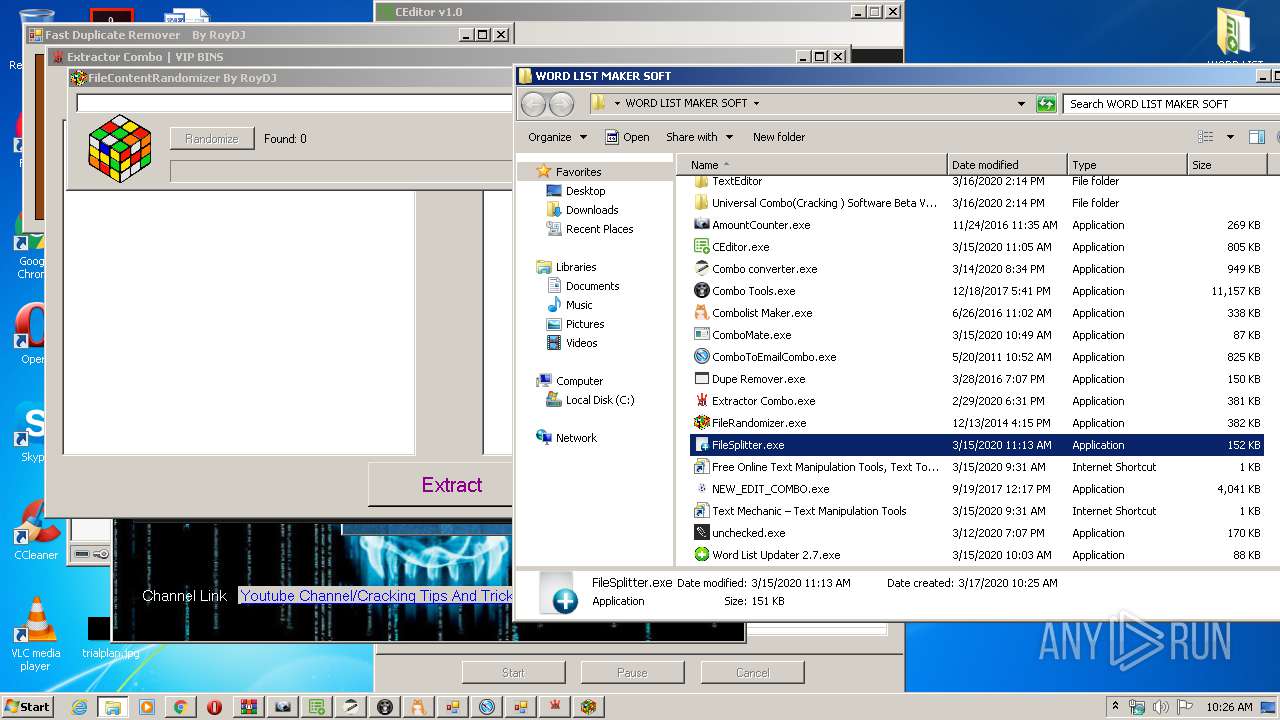
- FileSplitter.exe (PID: 3472)
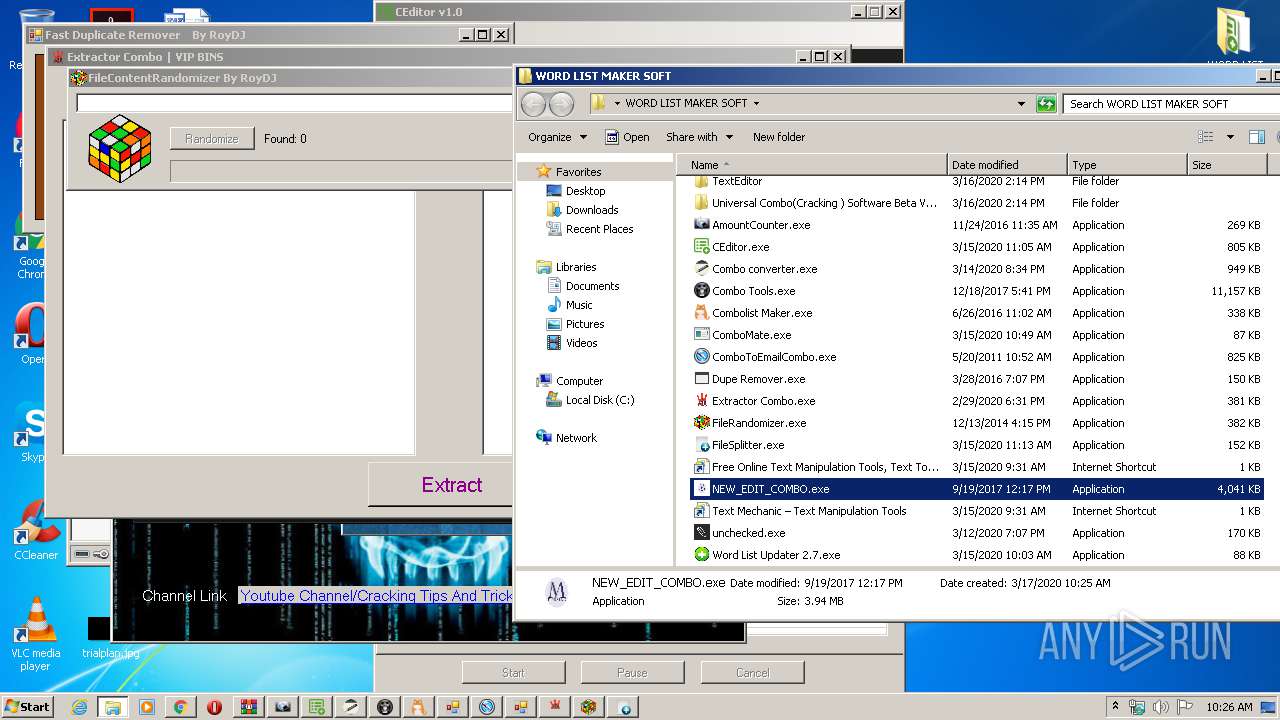
- NEW_EDIT_COMBO.exe (PID: 916)
- unchecked.exe (PID: 3732)
- Word List Updater 2.7.exe (PID: 3740)
- TextEditor 1.0.exe (PID: 2524)
- TextEditor 1.2.exe (PID: 1860)
- Universal Combo Software Beta V3.exe (PID: 3724)
- TextSplitter.exe (PID: 2888)
- NameScraper.exe (PID: 3636)
- Combo Maker Tool.exe (PID: 4064)
- TextCrawlerPro_setup.exe (PID: 3376)
- TextCrawlerPro_setup.exe (PID: 2704)
- TextCrawler.exe (PID: 3920)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3548)
- TextEditor 1.2.exe (PID: 1860)
- TextEditor 1.0.exe (PID: 2524)
- TextCrawlerPro_setup.exe (PID: 2704)
- TextCrawler.exe (PID: 3920)
Starts Visual C# compiler
- TextCrawler.exe (PID: 3920)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 3244)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2560)
- TextCrawlerPro_setup.exe (PID: 2704)
Executed via COM
- iexplore.exe (PID: 3772)
- explorer.exe (PID: 2796)
Reads internet explorer settings
- TextEditor 1.0.exe (PID: 2524)
- TextEditor 1.2.exe (PID: 1860)
Creates files in the user directory
- TextEditor 1.0.exe (PID: 2524)
- TextCrawlerPro_setup.exe (PID: 2704)
- TextCrawler.exe (PID: 3920)
Reads Internet Cache Settings
- TextEditor 1.2.exe (PID: 1860)
- TextEditor 1.0.exe (PID: 2524)
Creates files in the program directory
- TextCrawlerPro_setup.exe (PID: 2704)
- TextCrawler.exe (PID: 3920)
Modifies the open verb of a shell class
- TextCrawlerPro_setup.exe (PID: 2704)
Creates a software uninstall entry
- TextCrawlerPro_setup.exe (PID: 2704)
Creates COM task schedule object
- TextCrawler.exe (PID: 3920)
INFO
Reads the hosts file
- chrome.exe (PID: 3244)
- chrome.exe (PID: 2868)
Reads Internet Cache Settings
- chrome.exe (PID: 3244)
- iexplore.exe (PID: 3772)
- iexplore.exe (PID: 3624)
- iexplore.exe (PID: 3112)
Manual execution by user
- WinRAR.exe (PID: 2560)
- CEditor.exe (PID: 3212)
- AmountCounter.exe (PID: 3364)
- ComboMate.exe (PID: 2340)
- ComboToEmailCombo.exe (PID: 2408)
- Dupe Remover.exe (PID: 2356)
- Extractor Combo.exe (PID: 2872)
- FileRandomizer.exe (PID: 2816)
- Combo converter.exe (PID: 2620)
- Combo Tools.exe (PID: 2664)
- Combolist Maker.exe (PID: 2056)
- FileSplitter.exe (PID: 3472)
- NEW_EDIT_COMBO.exe (PID: 916)
- Word List Updater 2.7.exe (PID: 3740)
- unchecked.exe (PID: 3732)
- TextEditor 1.0.exe (PID: 2524)
- TextEditor 1.2.exe (PID: 1860)
- Universal Combo Software Beta V3.exe (PID: 3724)
- TextSplitter.exe (PID: 2888)
- NameScraper.exe (PID: 3636)
- Combo Maker Tool.exe (PID: 4064)
- TextCrawlerPro_setup.exe (PID: 3376)
- TextCrawlerPro_setup.exe (PID: 2704)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2560)
Application launched itself
- chrome.exe (PID: 3244)
- iexplore.exe (PID: 3772)
Changes internet zones settings
- iexplore.exe (PID: 3772)
Reads internet explorer settings
- iexplore.exe (PID: 3624)
- iexplore.exe (PID: 3112)
Creates files in the user directory
- iexplore.exe (PID: 3624)
- iexplore.exe (PID: 3112)
Reads settings of System Certificates
- iexplore.exe (PID: 3624)
- iexplore.exe (PID: 3112)
- chrome.exe (PID: 2868)
- TextEditor 1.2.exe (PID: 1860)
- iexplore.exe (PID: 3772)
Dropped object may contain TOR URL's
- iexplore.exe (PID: 3624)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3772)
Changes settings of System certificates
- iexplore.exe (PID: 3772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
109
Monitored processes
61
Malicious processes
21
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 628 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,3348642055562109217,10350340324290237480,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6639913840446444002 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3320 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 916 | "C:\Users\admin\Desktop\WORD LIST MAKER SOFT\NEW_EDIT_COMBO.exe" | C:\Users\admin\Desktop\WORD LIST MAKER SOFT\NEW_EDIT_COMBO.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: NEW_EDIT_COMBO Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 968 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,3348642055562109217,10350340324290237480,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14199232192049816442 --renderer-client-id=21 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4612 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1024 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,3348642055562109217,10350340324290237480,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1651950615441643398 --mojo-platform-channel-handle=3452 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1064 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,3348642055562109217,10350340324290237480,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13790154419478391092 --mojo-platform-channel-handle=3584 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,3348642055562109217,10350340324290237480,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14917160922964716532 --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3796 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,3348642055562109217,10350340324290237480,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=3042746348115718120 --mojo-platform-channel-handle=4708 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1632 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,3348642055562109217,10350340324290237480,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=14528250547670568850 --mojo-platform-channel-handle=4252 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1676 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,3348642055562109217,10350340324290237480,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=7631543977484513590 --mojo-platform-channel-handle=4628 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6fa8a9d0,0x6fa8a9e0,0x6fa8a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
9 040
Read events
3 565
Write events
3 748
Delete events
1 727
Modification events
| (PID) Process: | (3244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3120-13213713943555664 |
Value: 0 | |||
| (PID) Process: | (3244) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3244-13228914318429125 |
Value: 259 | |||
| (PID) Process: | (3244) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
33
Suspicious files
144
Text files
458
Unknown types
90
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5E70A58F-CAC.pma | — | |
MD5:— | SHA256:— | |||
| 3244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\6917f362-cef7-4b7f-9469-a723c95b3d51.tmp | — | |
MD5:— | SHA256:— | |||
| 3244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RFa66bb2.TMP | text | |
MD5:— | SHA256:— | |||
| 3244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFa66bb2.TMP | text | |
MD5:— | SHA256:— | |||
| 3244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RFa66bd2.TMP | text | |
MD5:— | SHA256:— | |||
| 3244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3244 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFa66e04.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
112
TCP/UDP connections
178
DNS requests
74
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3624 | iexplore.exe | GET | 200 | 144.217.81.121:80 | http://www.text-filter.com/tool/style.css | CA | text | 338 b | unknown |
3624 | iexplore.exe | GET | 200 | 144.217.81.121:80 | http://www.text-filter.com/ico_new1.gif | CA | image | 53 b | unknown |
3624 | iexplore.exe | GET | 200 | 144.217.81.121:80 | http://www.text-filter.com/inboxmassmailer.gif | CA | image | 4.77 Kb | unknown |
3624 | iexplore.exe | GET | 200 | 144.217.81.121:80 | http://www.text-filter.com/ico_new.gif | CA | image | 235 b | unknown |
3624 | iexplore.exe | GET | 200 | 144.217.81.121:80 | http://www.text-filter.com/ | CA | html | 8.62 Kb | unknown |
3624 | iexplore.exe | GET | 200 | 144.217.81.121:80 | http://www.text-filter.com/ico_new2.gif | CA | image | 126 b | unknown |
3624 | iexplore.exe | GET | 200 | 144.217.81.121:80 | http://www.text-filter.com/languagfes-icon-78x78.gif | CA | image | 55 b | unknown |
3624 | iexplore.exe | GET | 200 | 144.217.81.121:80 | http://www.text-filter.com/sm_fb.png | CA | image | 30.1 Kb | unknown |
3624 | iexplore.exe | GET | 200 | 144.217.81.121:80 | http://www.text-filter.com/downloadhthm.png | CA | image | 31.3 Kb | unknown |
3624 | iexplore.exe | GET | 200 | 157.240.20.19:80 | http://connect.facebook.net/en_US/sdk.js | US | text | 1.74 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2868 | chrome.exe | 104.18.11.25:443 | urchrevening.info | Cloudflare Inc | US | suspicious |
2868 | chrome.exe | 52.234.130.150:443 | install.videoconverterz.com | Microsoft Corporation | US | whitelisted |
2868 | chrome.exe | 172.217.18.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2868 | chrome.exe | 104.17.65.4:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | unknown |
2868 | chrome.exe | 104.18.38.170:443 | anonfiles.com | Cloudflare Inc | US | unknown |
2868 | chrome.exe | 172.217.23.141:443 | accounts.google.com | Google Inc. | US | whitelisted |
2868 | chrome.exe | 151.101.2.217:443 | vjs.zencdn.net | Fastly | US | suspicious |
2868 | chrome.exe | 13.35.254.116:443 | djv99sxoqpv11.cloudfront.net | — | US | malicious |
2868 | chrome.exe | 104.18.44.125:443 | baconaces.pro | Cloudflare Inc | US | shared |
2868 | chrome.exe | 172.217.22.110:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
anonfiles.com |
| shared |
accounts.google.com |
| shared |
vjs.zencdn.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
djv99sxoqpv11.cloudfront.net |
| shared |
www.google-analytics.com |
| whitelisted |
baconaces.pro |
| shared |
www.google.com |
| malicious |
villandoping.site |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |
1860 | TextEditor 1.2.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
2524 | TextEditor 1.0.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |