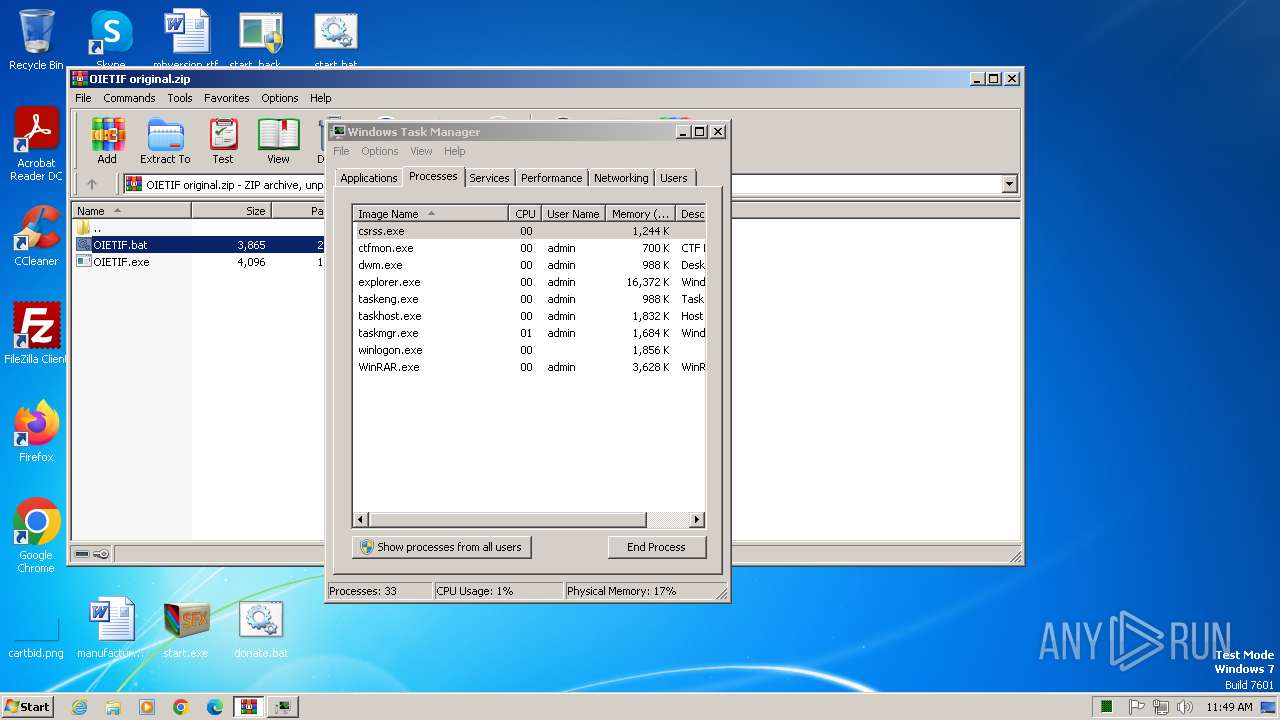
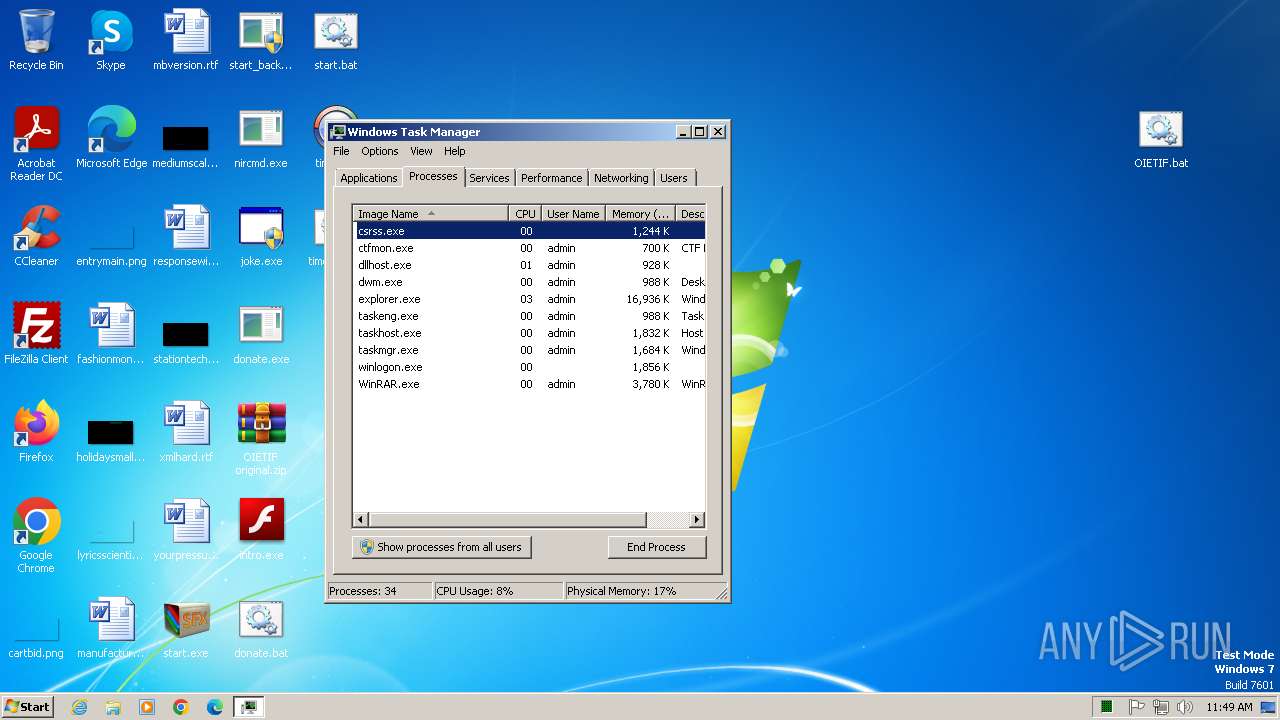
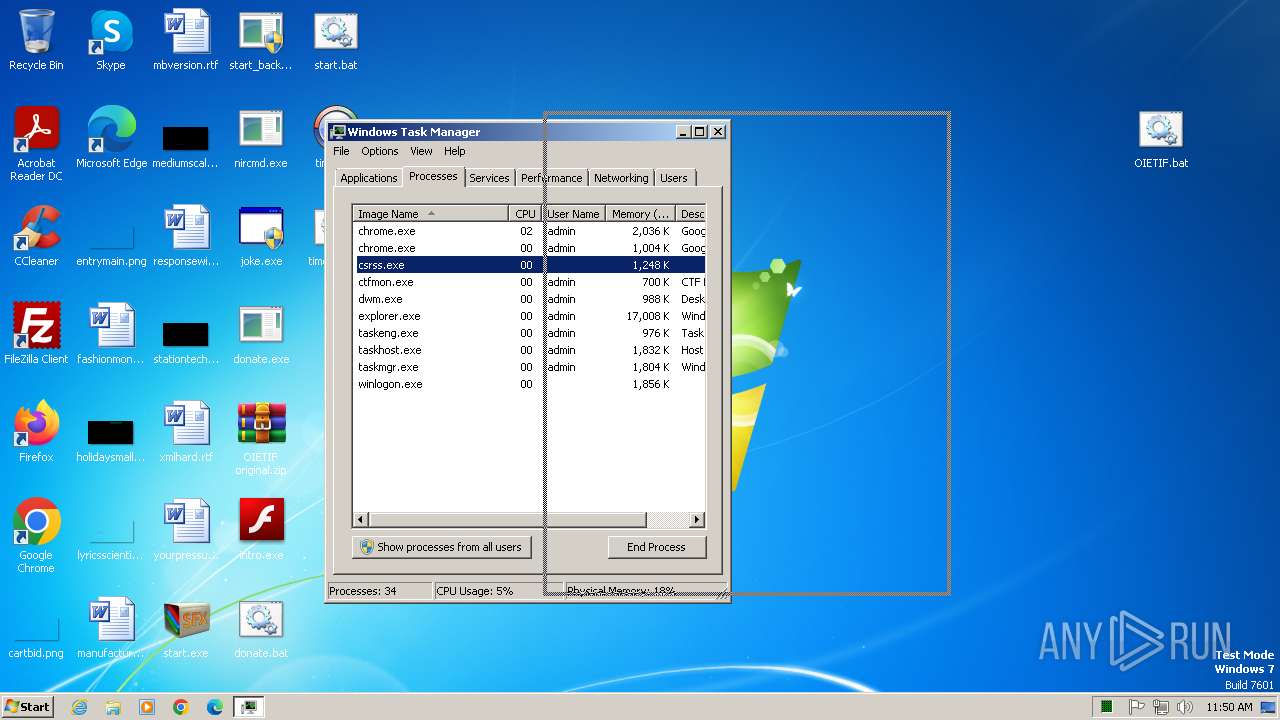
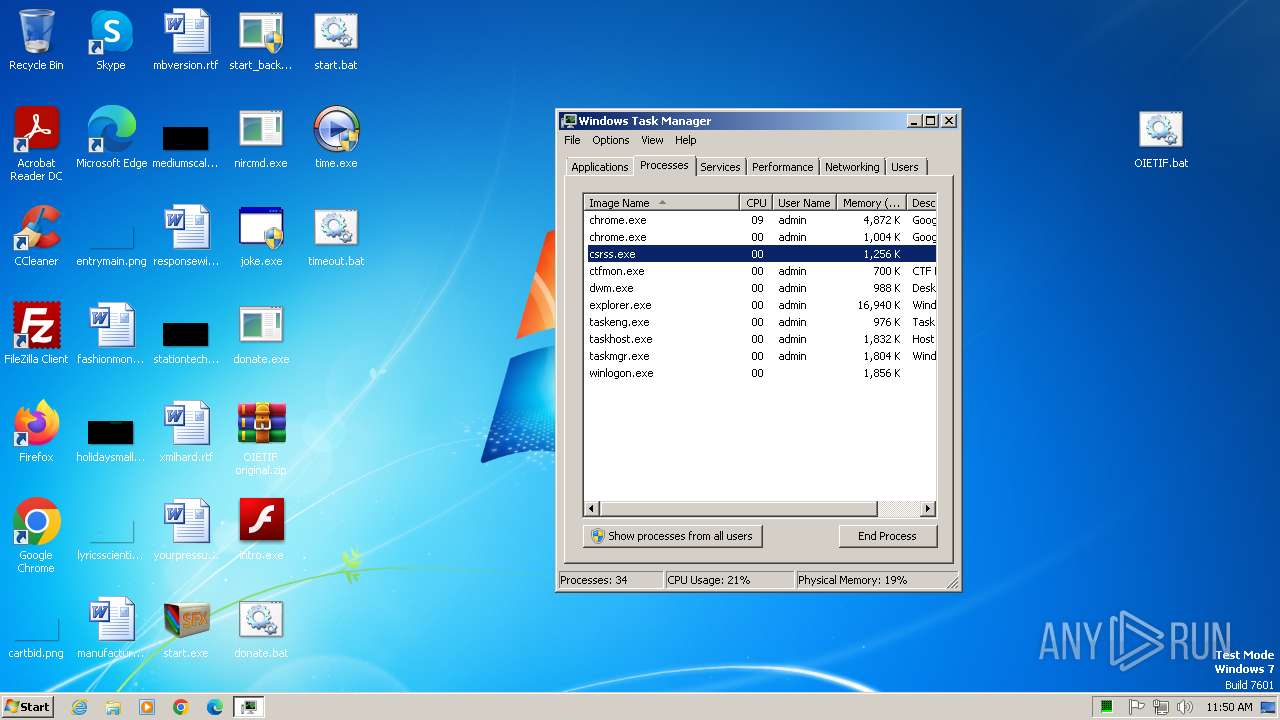
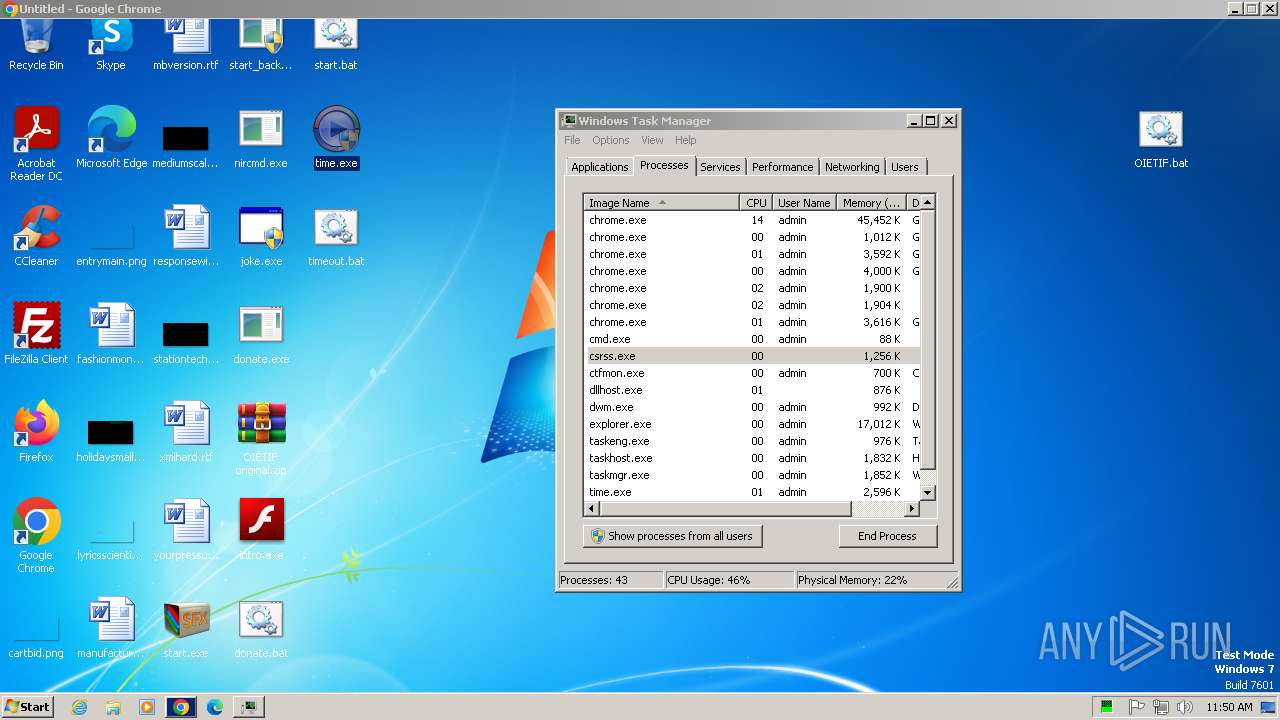
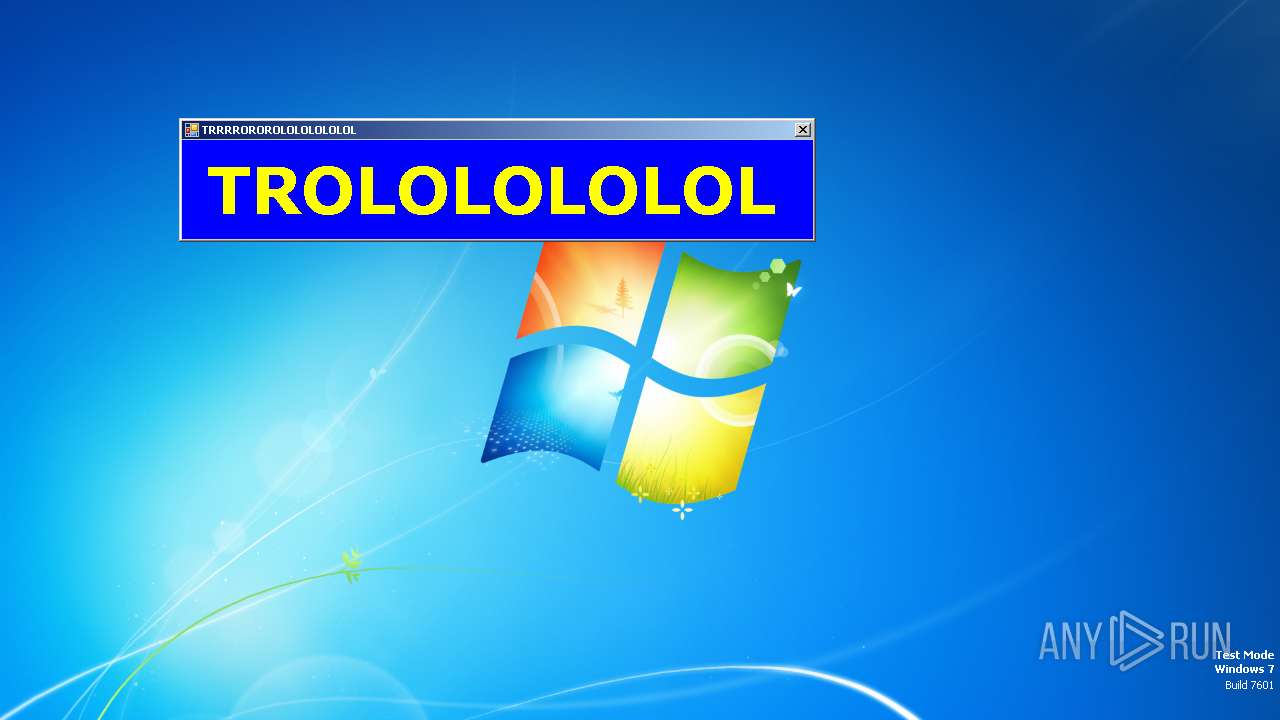
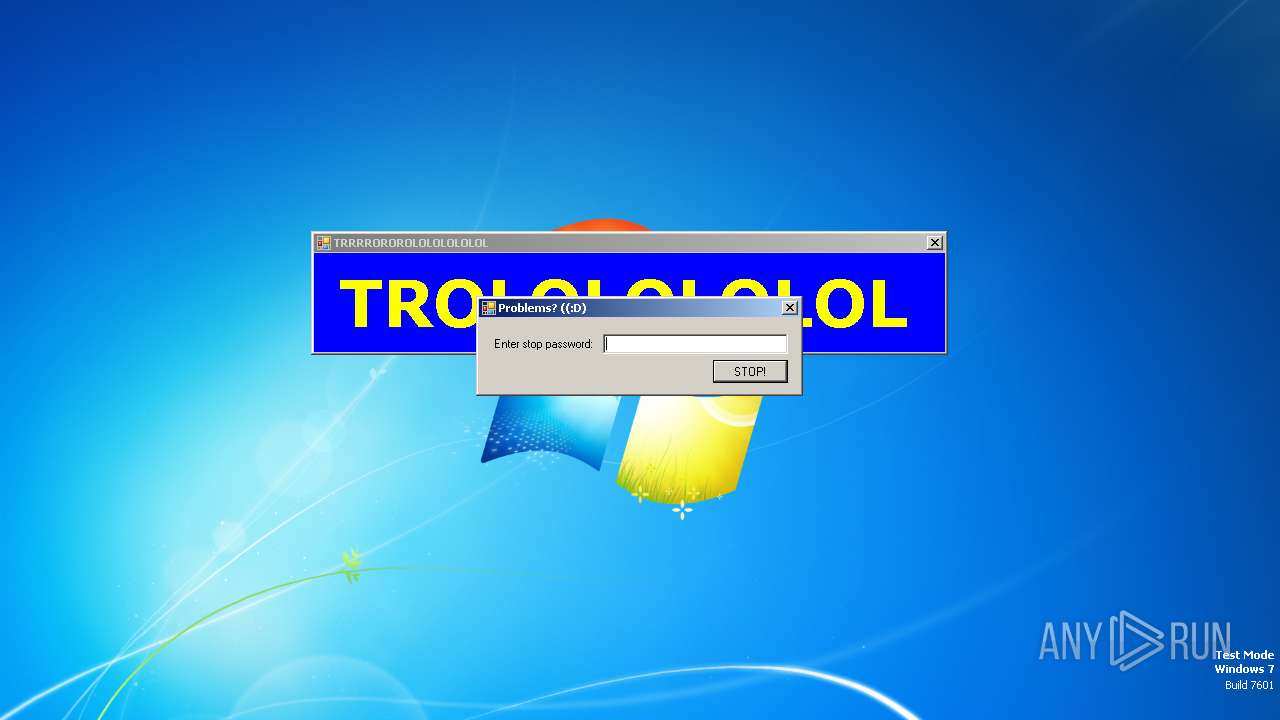
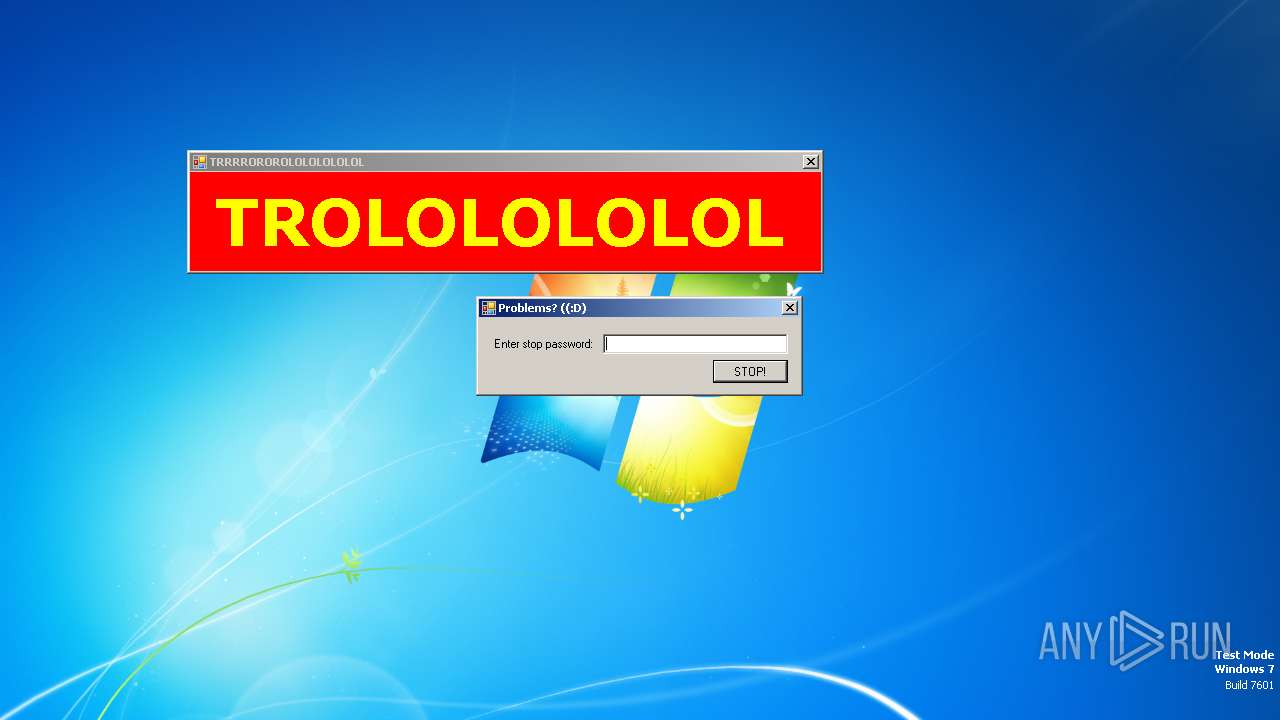
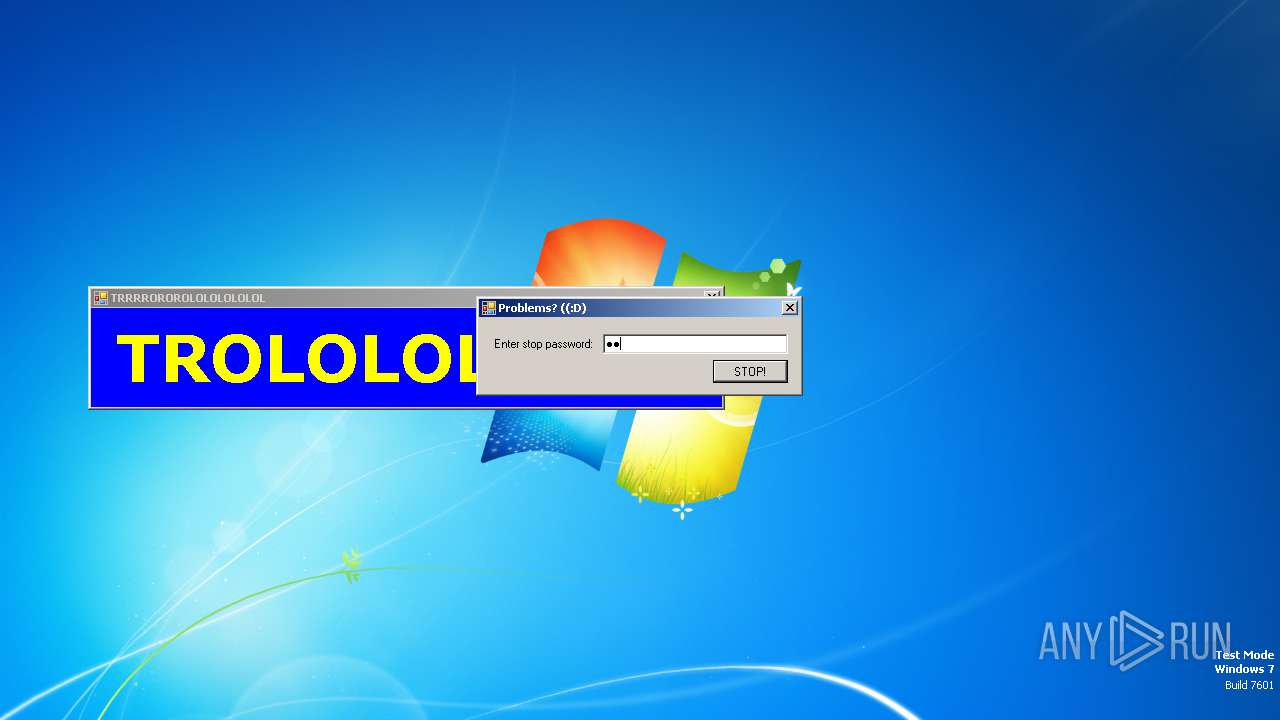
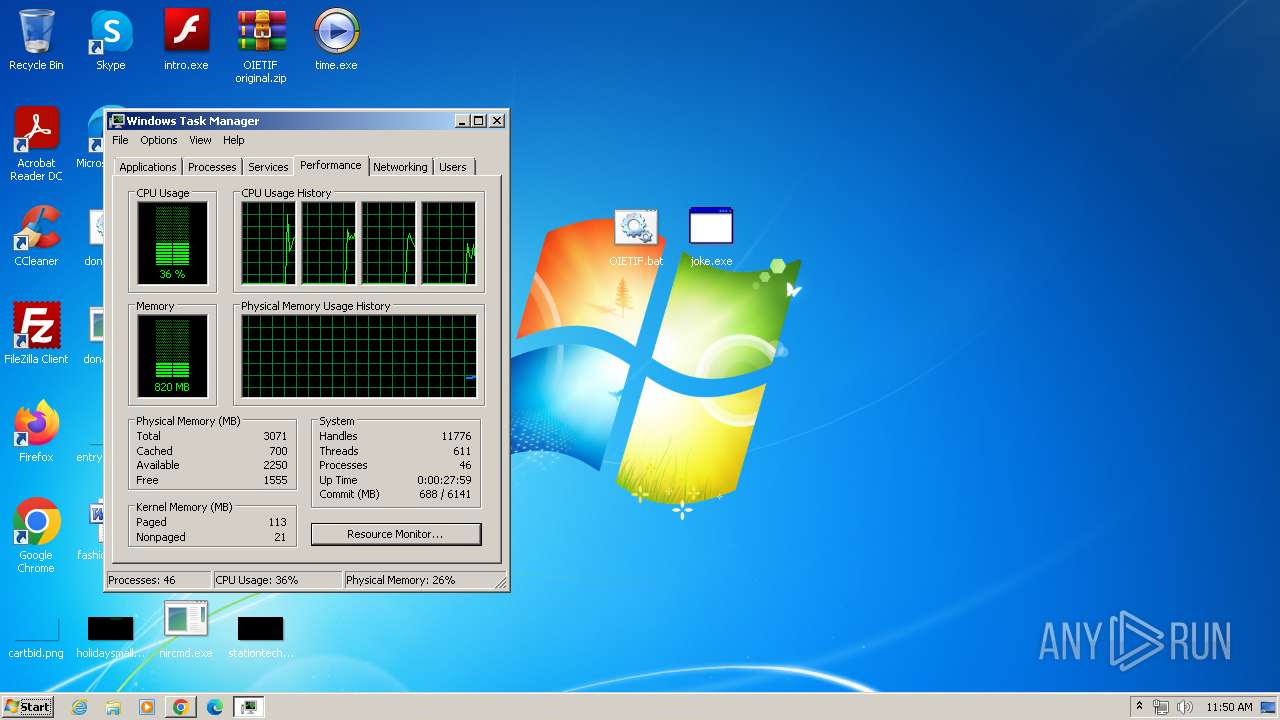
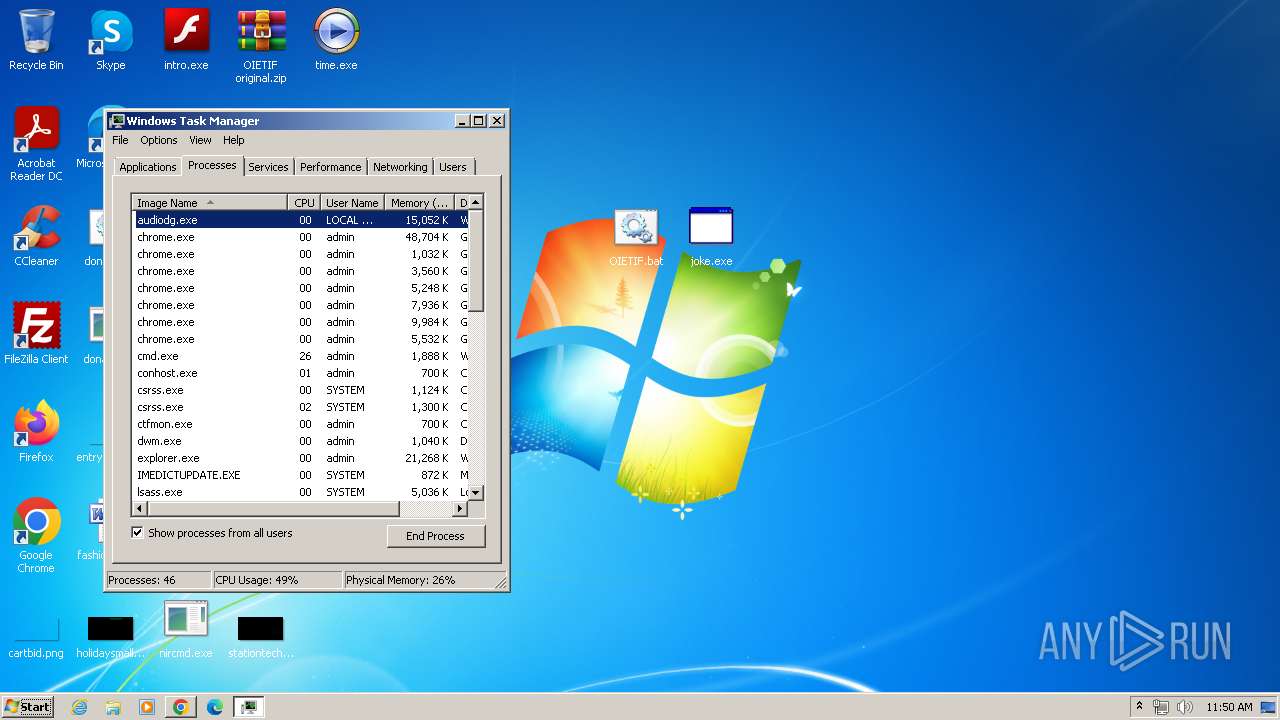
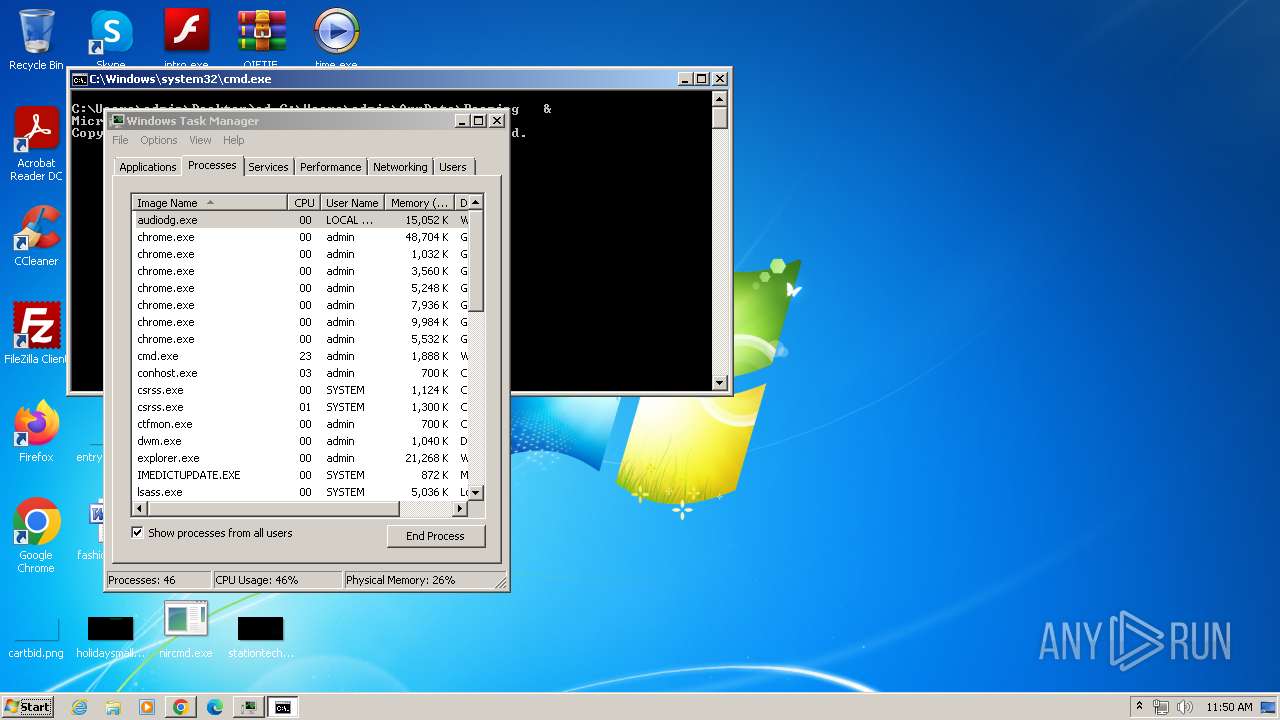
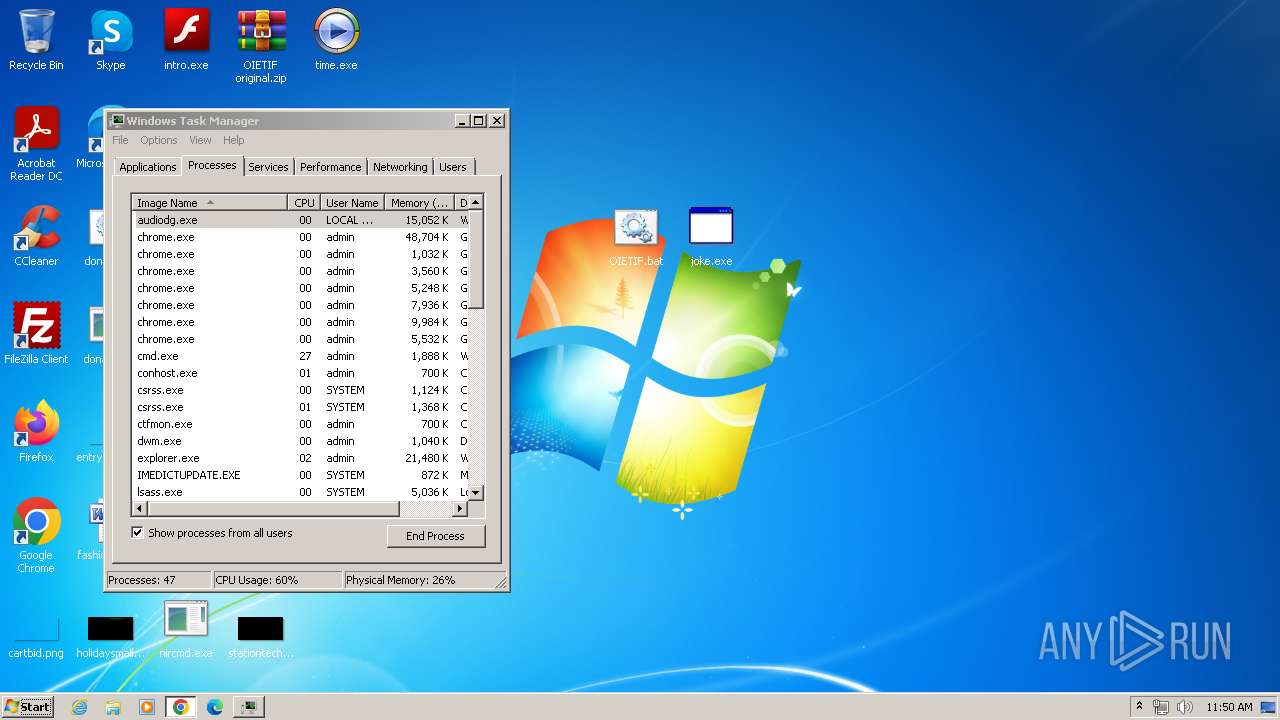
| File name: | start.exe |
| Full analysis: | https://app.any.run/tasks/fee298db-2505-44e6-968b-8b4094495c14 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2025, 10:48:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | AB3847BFF89EB639A99AFECFC2FA05C5 |
| SHA1: | 1E018D2911C0FF22908752FB1134945BC6944FA5 |
| SHA256: | 5751CEB02DA4FBABA02AC497385AF9A898D964204A11F00F1410A3A0DBB3B06D |
| SSDEEP: | 12288:tcgCzNHJj96xfKJStJkRm3bYXob0AnmFMcaGQx8n54cAAfkIJpDfK:EQKgLIQmFuGQxuAAfkIbjK |
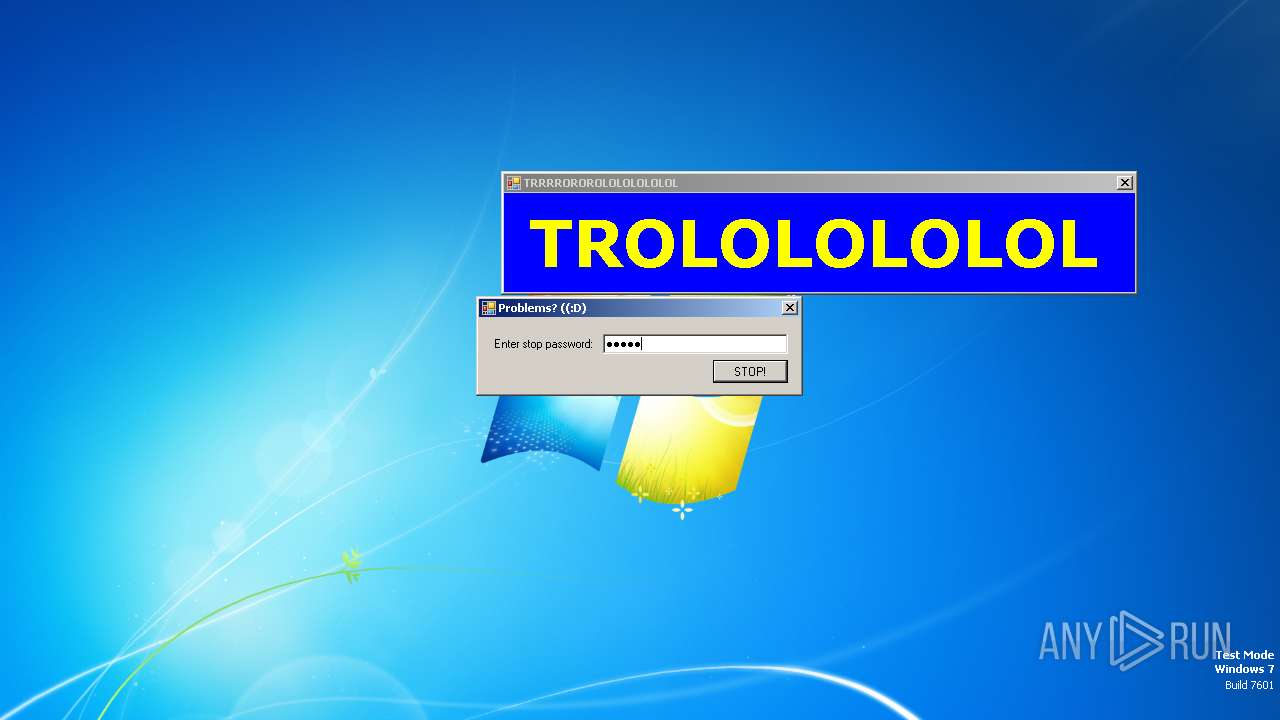
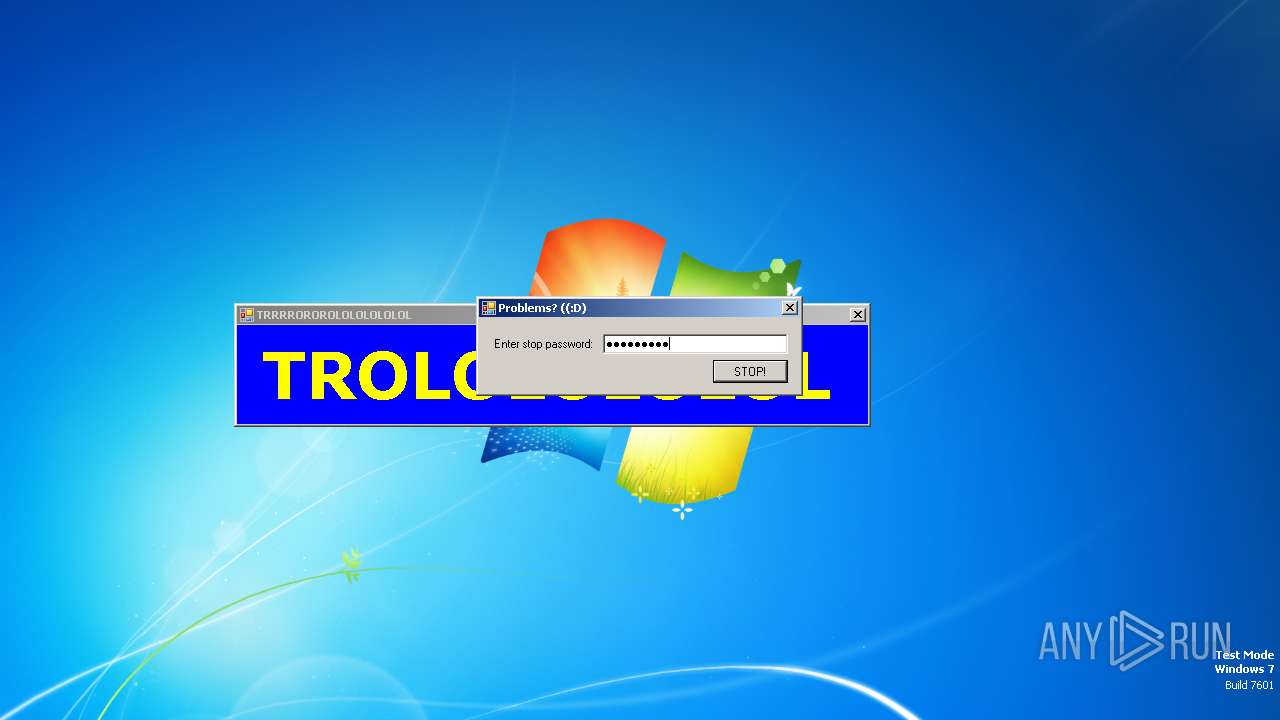
MALICIOUS
SFX dropper has been detected
- start.exe (PID: 1572)
SUSPICIOUS
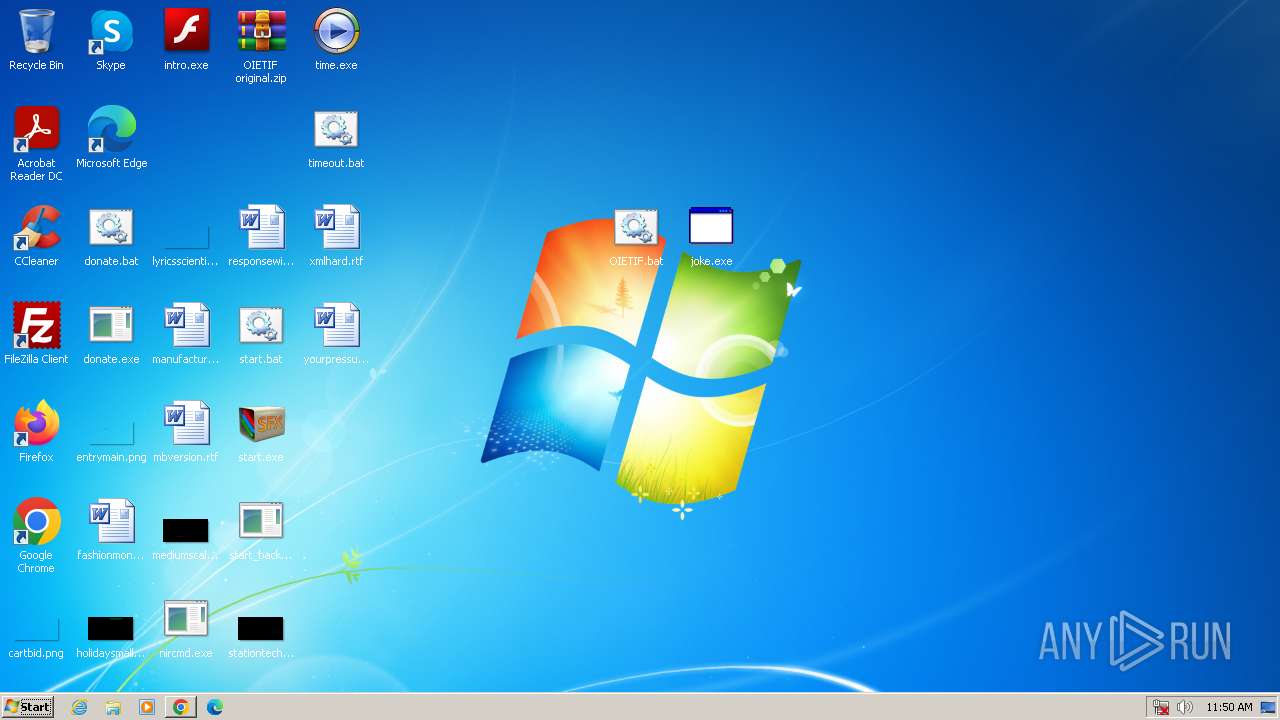
Application launched itself
- start.exe (PID: 1572)
Reads the Internet Settings
- start.exe (PID: 1572)
- start.exe (PID: 2656)
- cmd.exe (PID: 676)
- time.exe (PID: 2888)
- donate.exe (PID: 1892)
Reads security settings of Internet Explorer
- start.exe (PID: 1572)
- time.exe (PID: 2888)
- donate.exe (PID: 1892)
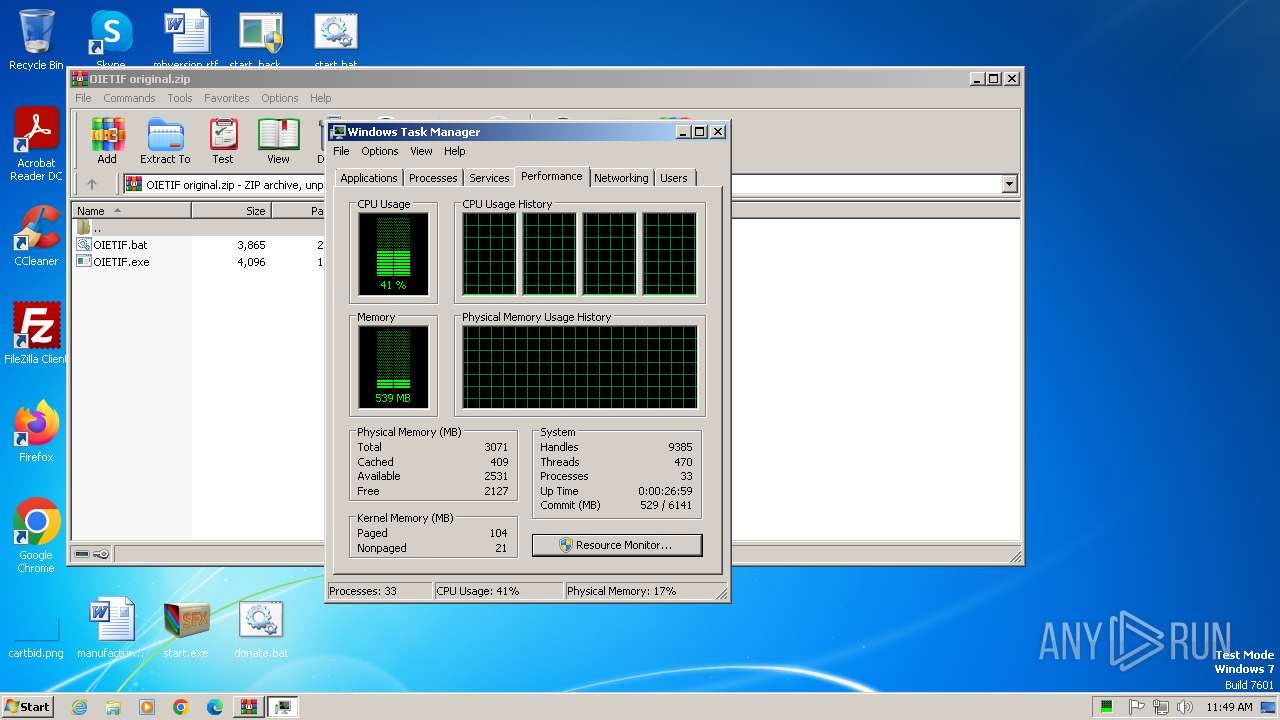
There is functionality for taking screenshot (YARA)
- start.exe (PID: 1572)
- start.exe (PID: 2656)
Executing commands from a ".bat" file
- donate.exe (PID: 1892)
- time.exe (PID: 2888)
- explorer.exe (PID: 2196)
Starts CMD.EXE for commands execution
- donate.exe (PID: 1892)
- time.exe (PID: 2888)
- explorer.exe (PID: 2196)
Uses REG/REGEDIT.EXE to modify registry
- joke.exe (PID: 1632)
Uses TASKKILL.EXE to kill process
- joke.exe (PID: 1632)
The process executes JS scripts
- cmd.exe (PID: 3304)
The executable file from the user directory is run by the CMD process
- s.exe (PID: 3976)
Executable content was dropped or overwritten
- cscript.exe (PID: 2772)
INFO
Reads the computer name
- start.exe (PID: 1572)
- donate.exe (PID: 1892)
- start.exe (PID: 2656)
- time.exe (PID: 2888)
Checks supported languages
- start.exe (PID: 1572)
- start.exe (PID: 2656)
- time.exe (PID: 2888)
- donate.exe (PID: 1892)
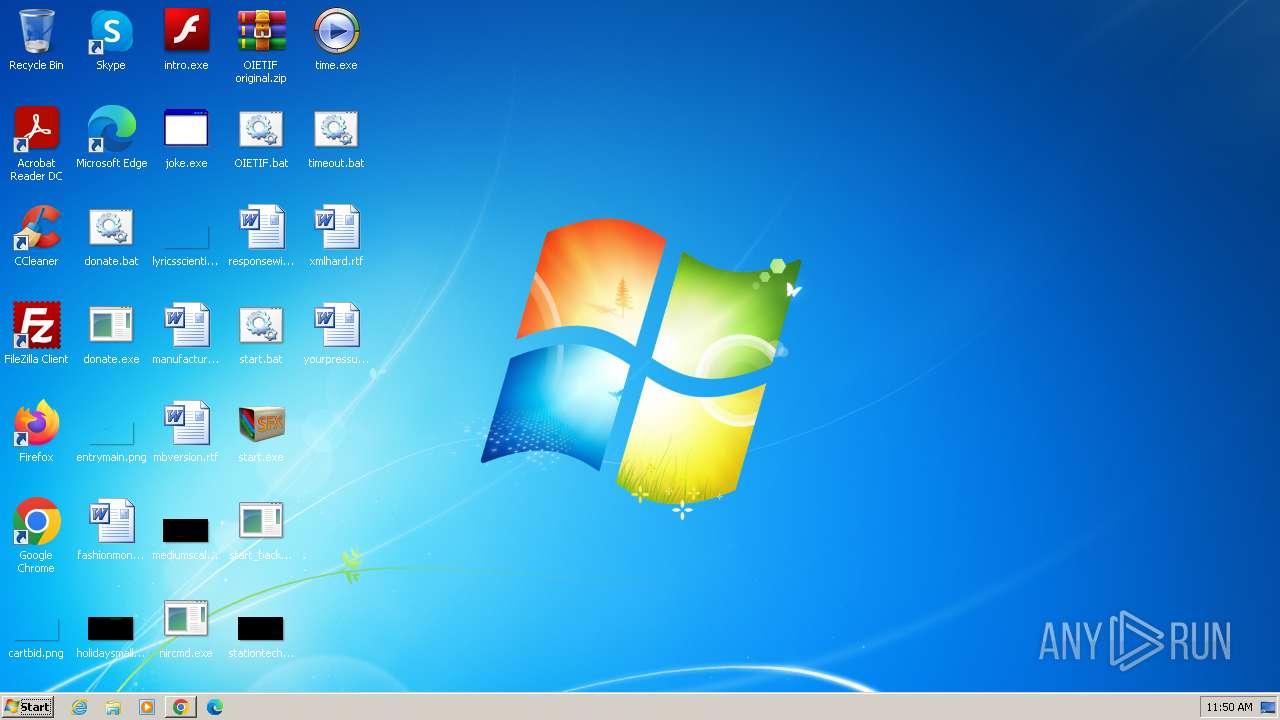
Creates files in the program directory
- start.exe (PID: 2656)
Manual execution by a user
- WinRAR.exe (PID: 2960)
- time.exe (PID: 2888)
- time.exe (PID: 2780)
- joke.exe (PID: 1632)
- joke.exe (PID: 4048)
- taskmgr.exe (PID: 2416)
- donate.exe (PID: 1892)
Application launched itself
- chrome.exe (PID: 1848)
Create files in a temporary directory
- time.exe (PID: 2888)
- donate.exe (PID: 1892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:10:03 07:51:19+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 214528 |
| InitializedDataSize: | 188928 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x21d50 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
82
Monitored processes
29
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 676 | "C:\Windows\system32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\E74E.tmp\E74F.tmp\E750.bat C:\Users\admin\Desktop\donate.exe" | C:\Windows\System32\cmd.exe | — | donate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1548 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Task Manager Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1572 | "C:\Users\admin\Desktop\start.exe" | C:\Users\admin\Desktop\start.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1632 | "C:\Users\admin\Desktop\joke.exe" | C:\Users\admin\Desktop\joke.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: Virus Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
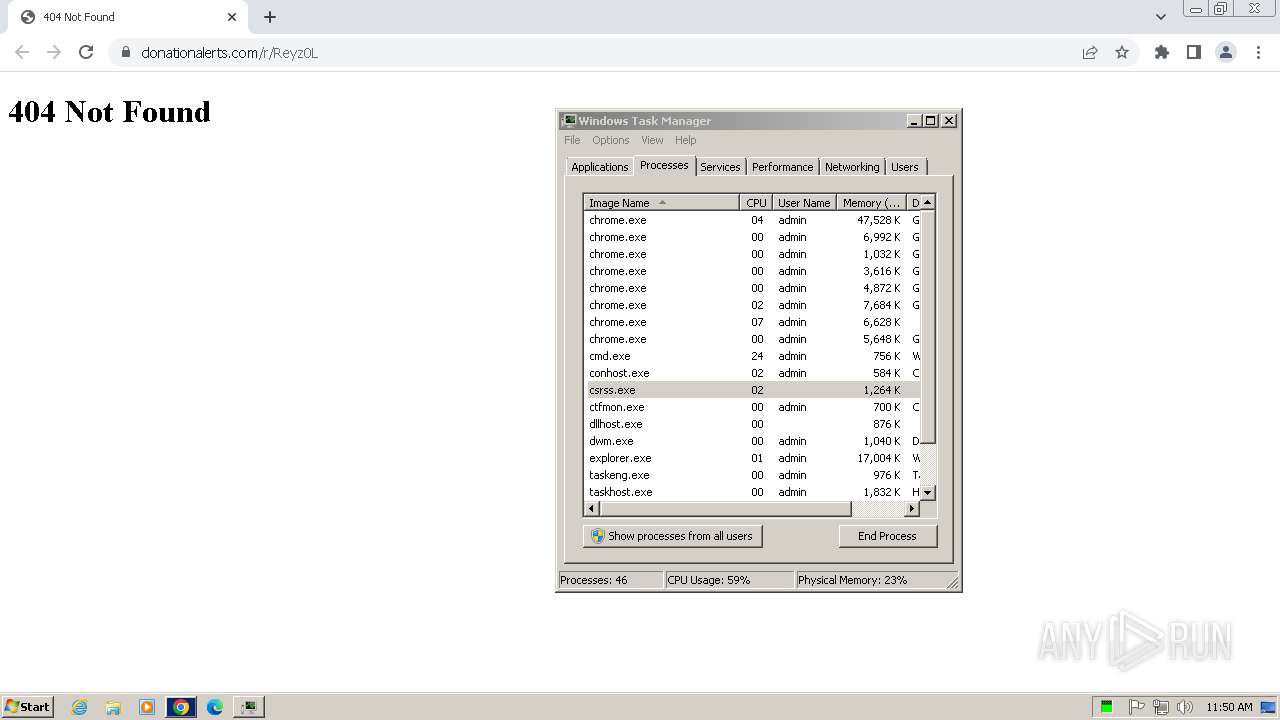
| 1848 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "https://www.donationalerts.com/r/Reyz0L" | C:\Program Files\Google\Chrome\Application\chrome.exe | cmd.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1892 | "C:\Users\admin\Desktop\donate.exe" | C:\Users\admin\Desktop\donate.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2196 | explorer.exe | C:\Windows\explorer.exe | — | joke.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2416 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2580 | REG add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | joke.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2608 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=2804 --field-trial-handle=1164,i,2602935251816353573,14682431328285503331,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
19 744
Read events
19 538
Write events
204
Delete events
2
Modification events
| (PID) Process: | (1572) start.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1572) start.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1572) start.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1572) start.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2960) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
1
Suspicious files
20
Text files
25
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1848 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF19016d.TMP | — | |
MD5:— | SHA256:— | |||
| 1848 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1848 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF1900f0.TMP | text | |
MD5:456D3EF989973A7C218E338A6CFFAD25 | SHA256:75631D994431F254B94255C50038A3657BFC45D76FCE9D794D514E57CA678872 | |||
| 1892 | donate.exe | C:\Users\admin\AppData\Local\Temp\E74E.tmp\E74F.tmp\E750.bat | text | |
MD5:45D022431CB16738A2CC3E942AFD5588 | SHA256:AEEF76E749F86EDF2BFCB60A263AD3613339FC06750BC0060ABB69568B923725 | |||
| 1848 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:5CB0B2845A3BDF2304E7CEA61A3FC51E | SHA256:0A73277FE3C683BCACFCF2658568C9D750AB78F56A4DEA9FBD563AA5D67EC666 | |||
| 1848 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old~RF190620.TMP | text | |
MD5:FF6BABA737D50E515029C3F3A1305BBC | SHA256:670EED15EAA8E3F1A4F8612B229654EB0C64107AEAF0B1017E4BD45E3F7EED83 | |||
| 1848 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\489cccaf-e057-43a5-9065-c7a77e673cf5.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 1848 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF19011f.TMP | text | |
MD5:825B582C78EC88D54C215EFDF1EAD639 | SHA256:367995D01A8F13E5C30C79499F86B034775BFD009D83DC97635DE438D47DFA37 | |||
| 1848 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:A24B909E4573DE480D459FBFBD20D770 | SHA256:E7D33D7AD48DE7D8C150ED0DA355C8ACE856C8C5F7DEE13CD74EE41B13748284 | |||
| 1848 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:1C6BD9993E8ECB91342E78927D81DCA3 | SHA256:76BE6BB39D2B3287BCBBCF6465599F0CF66FE5B9F4F55D10ED38B0BCF1A4BEC3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
20
DNS requests
15
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3012 | chrome.exe | 142.250.185.131:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
1848 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3012 | chrome.exe | 92.38.244.24:443 | www.donationalerts.com | LLC Digital Network | RU | unknown |
3012 | chrome.exe | 74.125.71.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
3012 | chrome.exe | 142.250.186.132:443 | www.google.com | GOOGLE | US | whitelisted |
1848 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.donationalerts.com |
| unknown |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
optimizationguide-pa.googleapis.com |
| whitelisted |
www.googleapis.com |
| whitelisted |