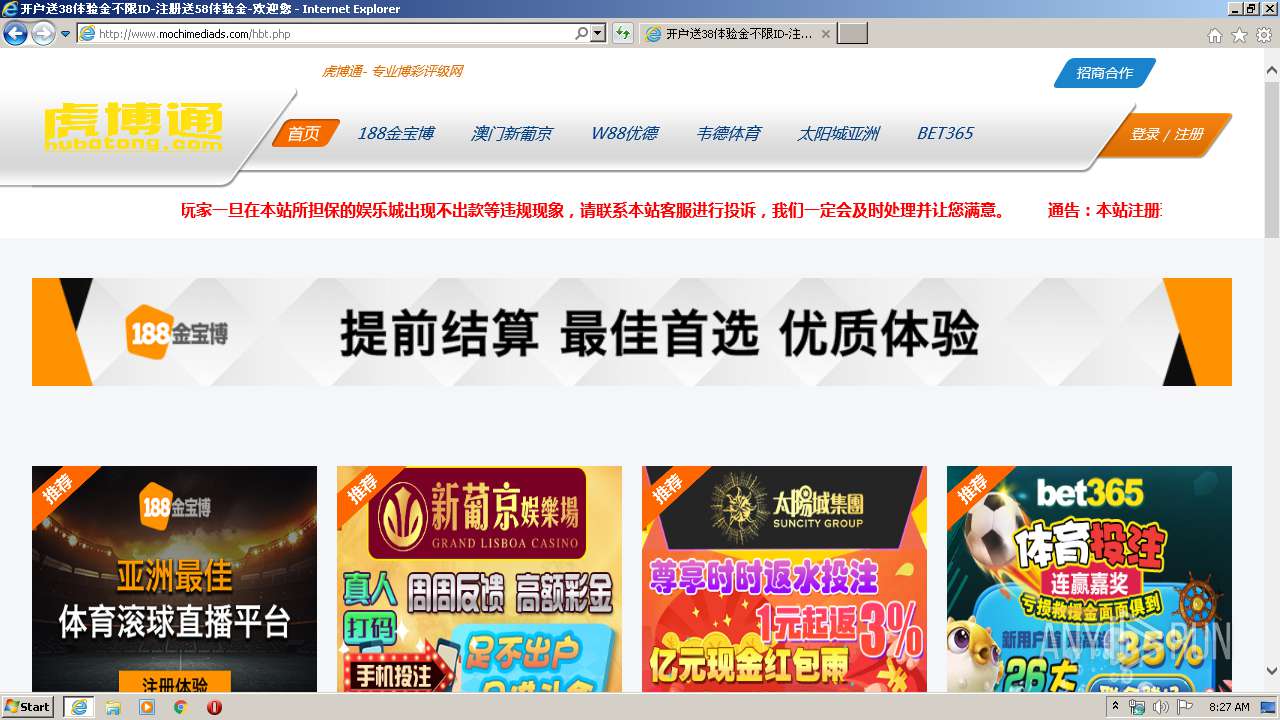
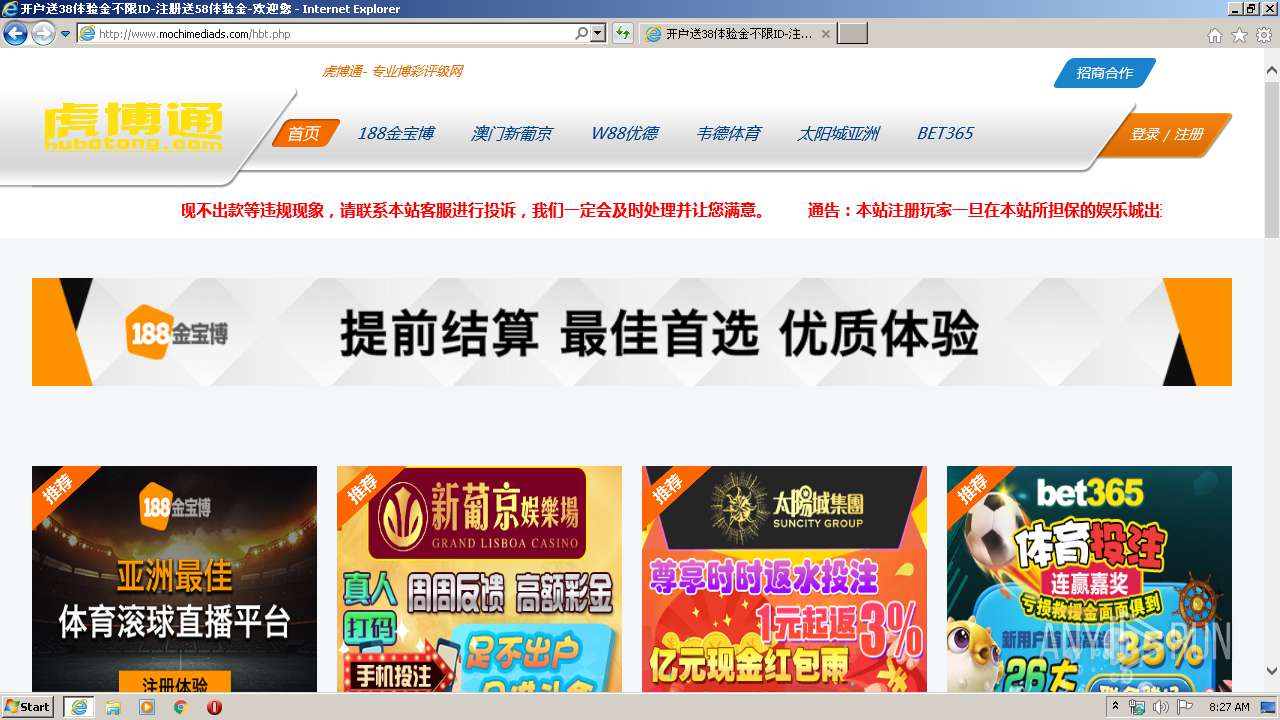
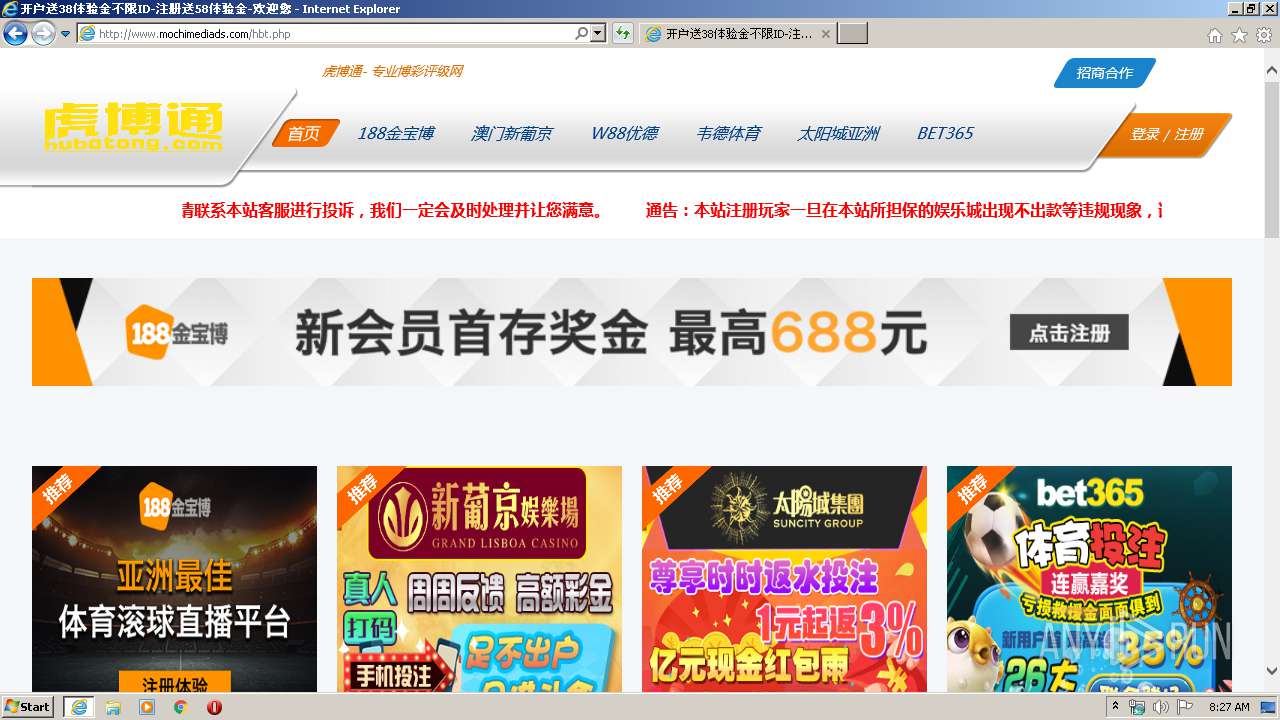
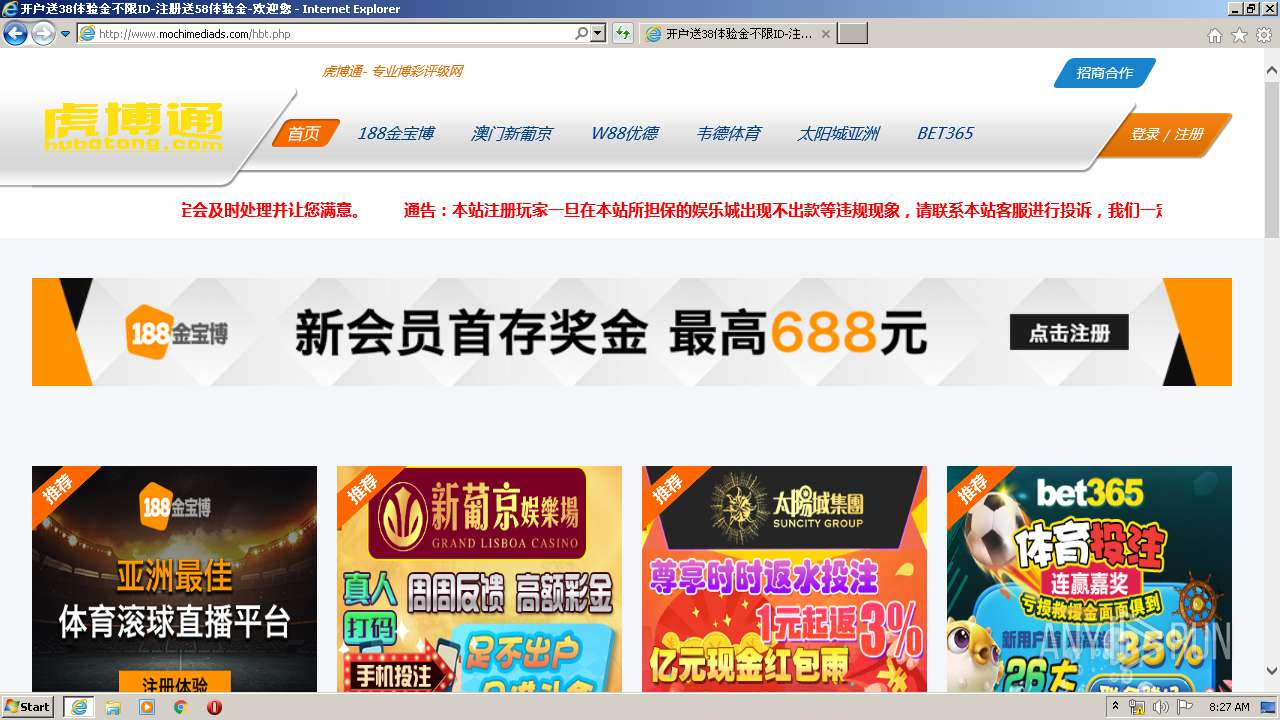
| URL: | http://www.mochimediads.com |
| Full analysis: | https://app.any.run/tasks/71ffddc8-b5b3-4d80-923d-b588012f8df7 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2020, 07:26:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C56C27461561161E3FD34BB4BD43C57C |
| SHA1: | 7CA50E17DD3DA6A39644A2C5392A30C85BF029EF |
| SHA256: | 574FF75E071A65A4B03D05E4D52260DA6BDA87BF9D1C6058BC343E62DFDE832F |
| SSDEEP: | 3:N1KJS42NMIFOKIn:Cc42NG |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2864)
- iexplore.exe (PID: 3608)
Changes internet zones settings
- iexplore.exe (PID: 2864)
Reads settings of System Certificates
- iexplore.exe (PID: 3608)
- iexplore.exe (PID: 2864)
Reads internet explorer settings
- iexplore.exe (PID: 3608)
Creates files in the user directory
- iexplore.exe (PID: 3608)
Changes settings of System certificates
- iexplore.exe (PID: 2864)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2864 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://www.mochimediads.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3608 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2864 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
4 110
Read events
290
Write events
2 562
Delete events
1 258
Modification events
| (PID) Process: | (2864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3399433928 | |||
| (PID) Process: | (2864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30803757 | |||
| (PID) Process: | (2864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
23
Text files
44
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3608 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab7C3D.tmp | — | |
MD5:— | SHA256:— | |||
| 3608 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar7C3E.tmp | — | |
MD5:— | SHA256:— | |||
| 2864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].htm | — | |
MD5:— | SHA256:— | |||
| 3608 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\tj[1].js | html | |
MD5:— | SHA256:— | |||
| 3608 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\jquery.min[1].js | text | |
MD5:— | SHA256:— | |||
| 3608 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\ACF244F1A10D4DBED0D88EBA0C43A9B5_3FB9EBFC1D18D5E09631A5E5A62F6EF3 | der | |
MD5:— | SHA256:— | |||
| 3608 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BD5208ADDEC1165FD57AF2BF2F455EAA_122109DC1B817B623370C1AE58AD2245 | binary | |
MD5:— | SHA256:— | |||
| 3608 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\hbt[1].htm | html | |
MD5:— | SHA256:— | |||
| 2864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\favicon[1].htm | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
35
DNS requests
18
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3608 | iexplore.exe | GET | 200 | 183.131.207.66:80 | http://ia.51.la/go1?id=20619795&rt=1585639605914&rl=1280*720&lang=en-US&ct=unknow&pf=1&ins=1&vd=1&ce=1&cd=24&ds=%25E5%25BC%2580%25E6%2588%25B7%25E9%2580%258138%25E4%25BD%2593%25E9%25AA%258C%25E9%2587%2591%25E4%25B8%258D%25E9%2599%2590ID%25E5%25BD%2593%25E5%2589%258D%25E4%25B8%259A%25E7%2595%258C%25E7%259F%25A5%25E5%2590%258D%25E5%259C%25A8%25E7%25BA%25BF%25E5%25A8%25B1%25E4%25B9%2590%25E5%2593%2581%25E7%2589%258C%252C%25E7%25BD%2591%25E7%25BD%2597%25E7%258E%25B0%25E4%25BB%258A%25E6%259C%2580&ing=1&ekc=&sid=1585639605914&tt=%25E5%25BC%2580%25E6%2588%25B7%25E9%2580%258138%25E4%25BD%2593%25E9%25AA%258C%25E9%2587%2591%25E4%25B8%258D%25E9%2599%2590ID-%25E6%25B3%25A8%25E5%2586%258C%25E9%2580%258158%25E4%25BD%2593%25E9%25AA%258C%25E9%2587%2591-%25E6%25AC%25A2%25E8%25BF%258E%25E6%2582%25A8&kw=%25E5%25BC%2580%25E6%2588%25B7%25E9%2580%258138%25E4%25BD%2593%25E9%25AA%258C%25E9%2587%2591%25E4%25B8%258D%25E9%2599%2590ID%252C%25E6%25B3%25A8%25E5%2586%258C%25E9%2580%258158%25E4%25BD%2593%25E9%25AA%258C%25E9%2587%2591%252C%25E6%25AC%25A2%25E8%25BF%258E%25E6%2582%25A8&cu=http%253A%252F%252Fwww.mochimediads.com%252Fhbt.php&pu= | CN | — | — | whitelisted |
3608 | iexplore.exe | GET | 200 | 183.131.207.66:80 | http://ia.51.la/go1?id=20646327&rt=1585639605968&rl=1280*720&lang=en-US&ct=unknow&pf=1&ins=1&vd=1&ce=1&cd=24&ds=%25E5%25BC%2580%25E6%2588%25B7%25E9%2580%258138%25E4%25BD%2593%25E9%25AA%258C%25E9%2587%2591%25E4%25B8%258D%25E9%2599%2590ID%25E5%25BD%2593%25E5%2589%258D%25E4%25B8%259A%25E7%2595%258C%25E7%259F%25A5%25E5%2590%258D%25E5%259C%25A8%25E7%25BA%25BF%25E5%25A8%25B1%25E4%25B9%2590%25E5%2593%2581%25E7%2589%258C%252C%25E7%25BD%2591%25E7%25BD%2597%25E7%258E%25B0%25E4%25BB%258A%25E6%259C%2580&ing=2&ekc=&sid=1585639605968&tt=%25E5%25BC%2580%25E6%2588%25B7%25E9%2580%258138%25E4%25BD%2593%25E9%25AA%258C%25E9%2587%2591%25E4%25B8%258D%25E9%2599%2590ID-%25E6%25B3%25A8%25E5%2586%258C%25E9%2580%258158%25E4%25BD%2593%25E9%25AA%258C%25E9%2587%2591-%25E6%25AC%25A2%25E8%25BF%258E%25E6%2582%25A8&kw=%25E5%25BC%2580%25E6%2588%25B7%25E9%2580%258138%25E4%25BD%2593%25E9%25AA%258C%25E9%2587%2591%25E4%25B8%258D%25E9%2599%2590ID%252C%25E6%25B3%25A8%25E5%2586%258C%25E9%2580%258158%25E4%25BD%2593%25E9%25AA%258C%25E9%2587%2591%252C%25E6%25AC%25A2%25E8%25BF%258E%25E6%2582%25A8&cu=http%253A%252F%252Fwww.mochimediads.com%252Fhbt.php&pu= | CN | — | — | whitelisted |
3608 | iexplore.exe | GET | 200 | 104.167.24.46:80 | http://www.mochimediads.com/tj.js | US | html | 167 b | whitelisted |
3608 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/MEwwSjBIMEYwRDAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCCwQAAAAAAURO8D4g | US | der | 1.49 Kb | whitelisted |
3608 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/gsdomainvalsha2g2/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTR8bV2%2Be7AwQ96%2FHwxJKnDYl18YQQU6k581IAt5RWBhiaMgm3AmKTPlw8CDDiWzNnGaYzcF90Uxg%3D%3D | US | der | 1.53 Kb | whitelisted |
3608 | iexplore.exe | GET | 200 | 104.167.24.46:80 | http://www.mochimediads.com/hbt.php | US | html | 439 b | whitelisted |
2864 | iexplore.exe | GET | 200 | 104.167.24.46:80 | http://www.mochimediads.com/hbt.php | US | html | 439 b | whitelisted |
3608 | iexplore.exe | GET | 200 | 104.167.24.46:80 | http://www.mochimediads.com/jquery.min.js | US | text | 432 b | whitelisted |
3608 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgO%2FmClH1hx76wq%2FmoZTNLO7wg%3D%3D | unknown | der | 527 b | whitelisted |
3608 | iexplore.exe | GET | 200 | 172.247.228.163:80 | http://www.kaibet.cc/images/meun-bj1.png | US | image | 9.00 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2864 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3608 | iexplore.exe | 198.16.61.139:443 | 2019chonga.com | CloudRadium L.L.C | US | unknown |
3608 | iexplore.exe | 192.124.249.41:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
3608 | iexplore.exe | 104.167.24.46:80 | www.mochimediads.com | YHSRV | US | unknown |
3608 | iexplore.exe | 163.171.131.194:443 | js.users.51.la | — | US | unknown |
3608 | iexplore.exe | 198.16.61.141:443 | www.hubotong88.cc | CloudRadium L.L.C | US | malicious |
3608 | iexplore.exe | 2.16.186.35:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
3608 | iexplore.exe | 2.16.186.11:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
3608 | iexplore.exe | 103.235.46.191:443 | hm.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | suspicious |
3608 | iexplore.exe | 172.247.228.163:80 | www.kaibet.cc | CloudRadium L.L.C | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.mochimediads.com |
| whitelisted |
js.users.51.la |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
ia.51.la |
| whitelisted |
2019chonga.com |
| unknown |
ocsp.godaddy.com |
| whitelisted |
www.hubotong88.cc |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |