| File name: | DrvUpdater.exe |
| Full analysis: | https://app.any.run/tasks/9fb0a68b-1822-4340-ae5c-3ccd671bb135 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2023, 05:25:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 1DB3300FE6EF0D52ECABBB903FCA6A41 |
| SHA1: | D5BC16779827E1CD0BB6D7DC652CDEE40C0B9BAC |
| SHA256: | 574D0CA9CDA56CD8DD6398BAF3E1CDCF56E9CA4F71D85D9155FAC4325444EA25 |
| SSDEEP: | 3072:Qj52RXf17lQSfIR08uBlCfsUaJAgtpl+xu+QXGOw07mEiEo+C9eIT6RfbtDw9ouk:QdGvgKIR08uBlCfVOAIpl+4vcHz9ek6R |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- DrvUpdater.exe (PID: 3804)
Reads the Internet Settings
- DrvUpdater.exe (PID: 3804)
- DrvUpdater.exe (PID: 4000)
- rundll32.exe (PID: 2580)
Drops a self-deleting batch file
- DrvUpdater.exe (PID: 3804)
Executing commands from a ".bat" file
- DrvUpdater.exe (PID: 3804)
Starts CMD.EXE for commands execution
- DrvUpdater.exe (PID: 3804)
Uses RUNDLL32.EXE to load library
- DrvUpdater.exe (PID: 4000)
INFO
Checks supported languages
- DrvUpdater.exe (PID: 3804)
- DrvUpdater.exe (PID: 4000)
The process checks LSA protection
- DrvUpdater.exe (PID: 3804)
- DrvUpdater.exe (PID: 4000)
Reads the computer name
- DrvUpdater.exe (PID: 3804)
- DrvUpdater.exe (PID: 4000)
Creates files or folders in the user directory
- DrvUpdater.exe (PID: 3804)
Create files in a temporary directory
- DrvUpdater.exe (PID: 3804)
- DrvUpdater.exe (PID: 4000)
- iexplore.exe (PID: 3788)
The executable file from the user directory is run by the CMD process
- DrvUpdater.exe (PID: 4000)
Application launched itself
- iexplore.exe (PID: 3788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| ProductVersion: | 0, 0, 25, 0 |
|---|---|
| ProductName: | DRP Su Updater |
| OriginalFileName: | DrvUpdater.exe |
| LegalCopyright: | DriverPack Solution |
| InternalName: | DRP Su Updater |
| FileVersion: | 0, 0, 25, 0 |
| FileDescription: | DRP Su Updater |
| CharacterSet: | Unicode |
| LanguageCode: | Russian |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x0017 |
| ProductVersionNumber: | 0.0.25.0 |
| FileVersionNumber: | 0.0.25.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5 |
| ImageVersion: | - |
| OSVersion: | 5 |
| EntryPoint: | 0x65ba0 |
| UninitializedDataSize: | 253952 |
| InitializedDataSize: | 28672 |
| CodeSize: | 163840 |
| LinkerVersion: | 9 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, 32-bit |
| TimeStamp: | 2011:04:28 08:25:13+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 28-Apr-2011 08:25:13 |
| Detected languages: |
|
| FileDescription: | DRP Su Updater |
| FileVersion: | 0, 0, 25, 0 |
| InternalName: | DRP Su Updater |
| LegalCopyright: | DriverPack Solution |
| OriginalFilename: | DrvUpdater.exe |
| ProductName: | DRP Su Updater |
| ProductVersion: | 0, 0, 25, 0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 28-Apr-2011 08:25:13 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x0003E000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x0003F000 | 0x00028000 | 0x00027800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.9964 |
.rsrc | 0x00067000 | 0x00007000 | 0x00006600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 6.37124 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.02301 | 622 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 5.32861 | 2216 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 5.37959 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 6.76869 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 7.14025 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 6.84141 | 1128 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 6.03749 | 80 | Latin 1 / Western European | English - United States | RT_STRING |
8 | 7.91353 | 2216 | Latin 1 / Western European | English - United States | RT_ICON |
9 | 7.86022 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
10 | 7.98229 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
Imports
ADVAPI32.dll |
GDI32.dll |
KERNEL32.DLL |
MSIMG32.dll |
SETUPAPI.dll |
SHELL32.dll |
USER32.dll |
WS2_32.dll |
Total processes
43
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1596 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\DrvUpdater.Run.bat" " | C:\Windows\System32\cmd.exe | — | DrvUpdater.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
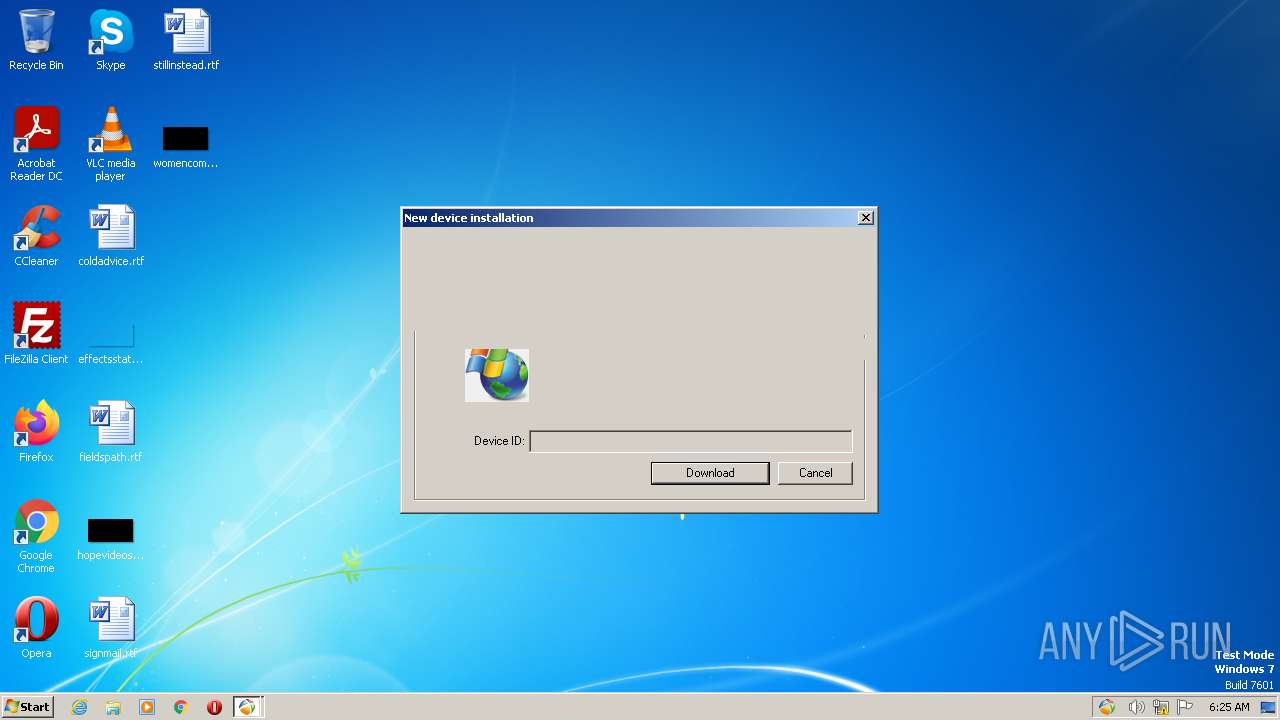
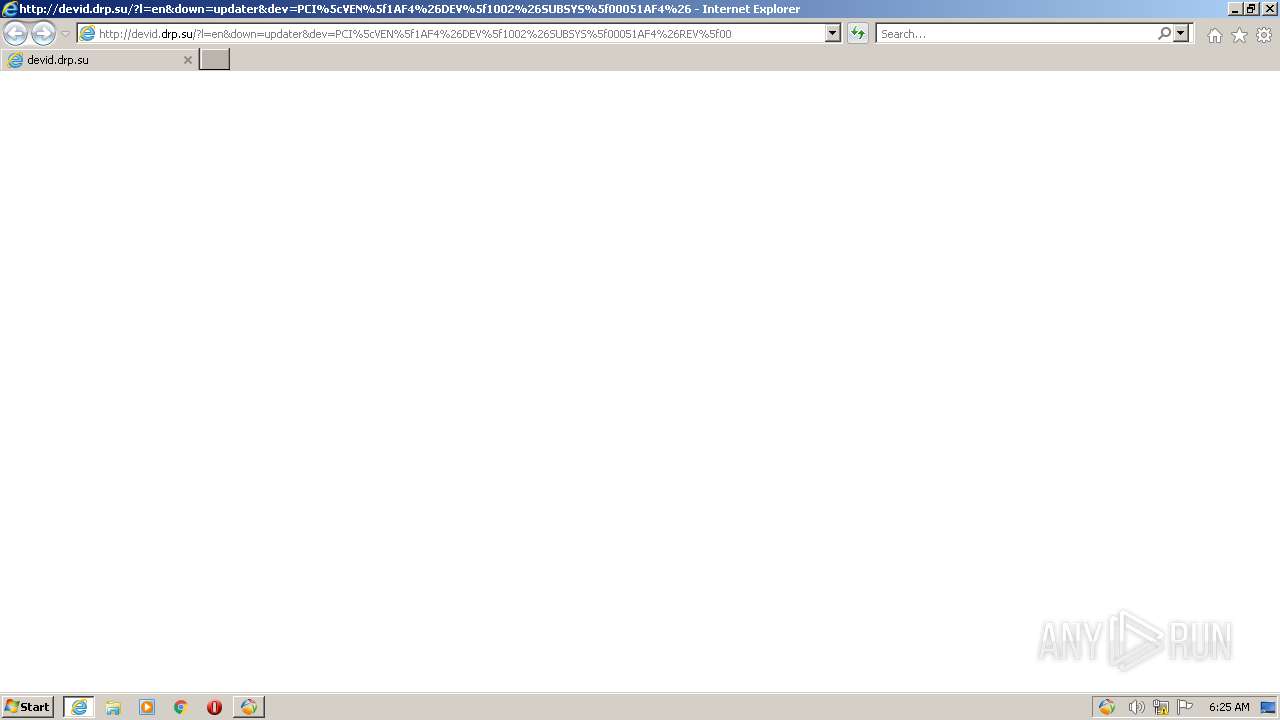
| 2580 | "C:\Windows\System32\rundll32.exe" url.dll,FileProtocolHandler http://devid.drp.su/?l=en&down=updater&dev=PCI%5cVEN%5f1AF4%26DEV%5f1002%26SUBSYS%5f00051AF4%26REV%5f00 | C:\Windows\System32\rundll32.exe | — | DrvUpdater.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3788 | "C:\Program Files\Internet Explorer\iexplore.exe" http://devid.drp.su/?l=en&down=updater&dev=PCI%5cVEN%5f1AF4%26DEV%5f1002%26SUBSYS%5f00051AF4%26REV%5f00 | C:\Program Files\Internet Explorer\iexplore.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3804 | "C:\Users\admin\AppData\Local\Temp\DrvUpdater.exe" | C:\Users\admin\AppData\Local\Temp\DrvUpdater.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: DRP Su Updater Exit code: 0 Version: 0, 0, 25, 0 Modules
| |||||||||||||||
| 4000 | DrvUpdater.exe | C:\Users\admin\AppData\Roaming\DRPSu\DrvUpdater.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: DRP Su Updater Exit code: 0 Version: 0, 0, 25, 0 Modules
| |||||||||||||||
| 4080 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3788 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
12 837
Read events
12 728
Write events
109
Delete events
0
Modification events
| (PID) Process: | (3804) DrvUpdater.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3804) DrvUpdater.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3804) DrvUpdater.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3804) DrvUpdater.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4000) DrvUpdater.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4000) DrvUpdater.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4000) DrvUpdater.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4000) DrvUpdater.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3788) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3788) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
Executable files
1
Suspicious files
8
Text files
7
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3804 | DrvUpdater.exe | C:\Users\admin\AppData\Roaming\DRPSu\DrvUpdater.exe | executable | |
MD5:1DB3300FE6EF0D52ECABBB903FCA6A41 | SHA256:574D0CA9CDA56CD8DD6398BAF3E1CDCF56E9CA4F71D85D9155FAC4325444EA25 | |||
| 3804 | DrvUpdater.exe | C:\Users\admin\AppData\Local\Temp\DrvUpdater.Run.bat | text | |
MD5:098E4875545948C68E6019FC86B0415F | SHA256:22DFA6F8670D27AA0E3B0D87C7D18867B6B8D6C5C631B9C6E7188758F4447E76 | |||
| 4080 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:F621FC93ED56BF8D0A67F9D0F967C3B7 | SHA256:473FAAF3D1987BF614FFDEF3F27393F457C83D04FC79DB851D31A64464B6AAEE | |||
| 3788 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3788 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\versionlist.xml | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 4080 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:064C170A703F2C840E02918CD5B51C83 | SHA256:D15C16C629D2D1467052D36959C8BF7AFE618EFFB0928AFEAD0C4849706EF112 | |||
| 3788 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3788 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:EFEDEA436AA3B5824FA409913020A281 | SHA256:57901431ED277F9C15600D0147E9F67735BB9841C7E848C0C1D8270058D956FD | |||
| 3788 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\verA90E.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 4080 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\main[1].css | text | |
MD5:FF26F59E28A5FE6EA4AB23586415696B | SHA256:D30B4EA6F68456672F5ABB35E9DCF7D54226372B66E9D60A7EE26B7A52568E74 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
16
DNS requests
9
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
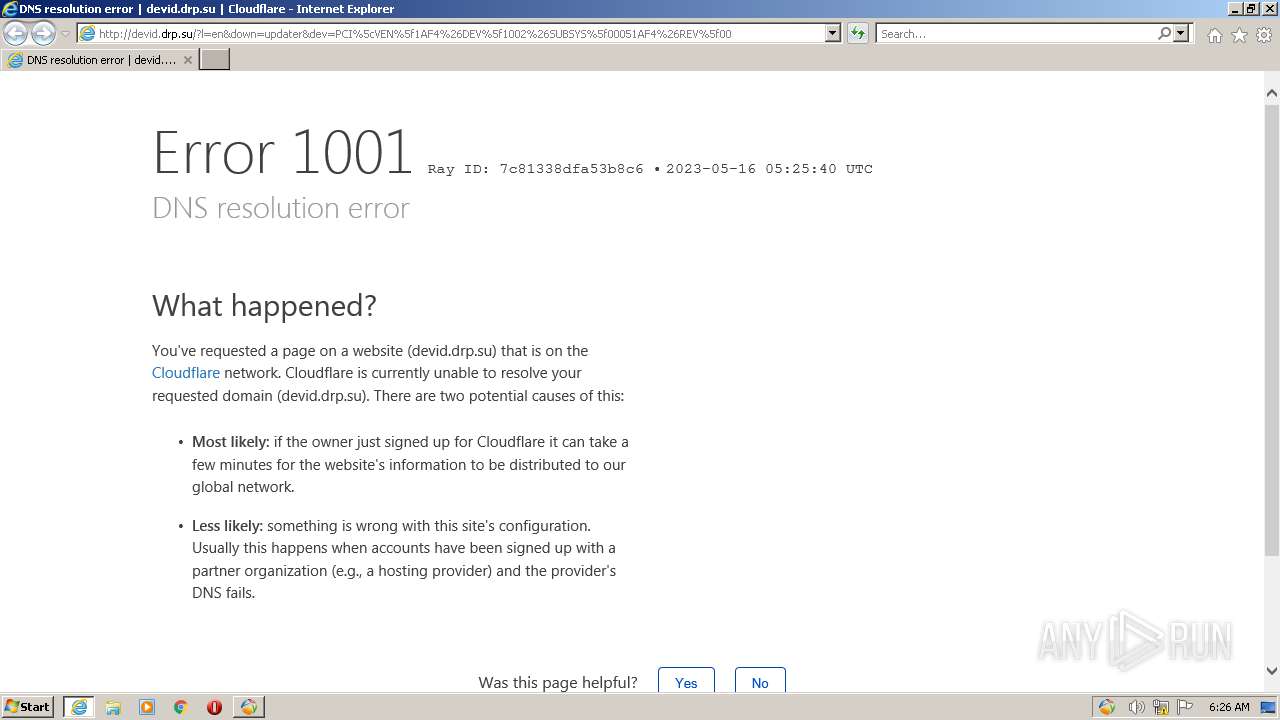
4080 | iexplore.exe | GET | 409 | 104.20.168.62:80 | http://devid.drp.su/?l=en&down=updater&dev=PCI%5cVEN%5f1AF4%26DEV%5f1002%26SUBSYS%5f00051AF4%26REV%5f00 | US | html | 5.96 Kb | suspicious |
4080 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3788 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
4080 | iexplore.exe | GET | 200 | 104.20.169.62:80 | http://devid.drp.su/cdn-cgi/styles/main.css | US | text | 2.13 Kb | suspicious |
4080 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ac6de0a0a027b64c | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4080 | iexplore.exe | 104.18.31.78:443 | performance.radar.cloudflare.com | CLOUDFLARENET | — | suspicious |
4080 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4080 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3788 | iexplore.exe | 92.123.104.38:443 | www.bing.com | Akamai International B.V. | DE | suspicious |
4080 | iexplore.exe | 104.20.169.62:80 | devid.drp.su | CLOUDFLARENET | — | suspicious |
3788 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3396 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
devid.drp.su |
| suspicious |
performance.radar.cloudflare.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1076 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
1076 | svchost.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP DriverPack Domain in DNS Query |
1076 | svchost.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to DriverPack Domain ( .drp .su) |
1076 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
1076 | svchost.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP DriverPack Domain in DNS Query |
1076 | svchost.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Observed DNS Query to DriverPack Domain ( .drp .su) |
4080 | iexplore.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
4080 | iexplore.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |