| File name: | 1302fdf298c1cd6551a3560d782079b6 |
| Full analysis: | https://app.any.run/tasks/6303e6b2-3d2f-4bce-9f7d-0df0eaf913f8 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 11:56:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Title: 331 372 393 331, Author: Windows User, Template: Normal.dotm, Last Saved By: Windows User, Revision Number: 7, Name of Creating Application: Microsoft Office Word, Total Editing Time: 05:00, Create Time/Date: Mon Dec 2 20:45:00 2019, Last Saved Time/Date: Mon Dec 2 21:02:00 2019, Number of Pages: 10, Number of Words: 43971, Number of Characters: 250640, Security: 0 |
| MD5: | 1302FDF298C1CD6551A3560D782079B6 |
| SHA1: | 3404BAC497F27832F2A5EB72DC2AC0015BCB3212 |
| SHA256: | 5728A1B772E60B54AB67BB3B7B3579673BB4906D32BE767C0D68D4E228A5210A |
| SSDEEP: | 6144:Tx7ZRcU8ajOuxc9bLwdft9EJSp9/qNLs+kwEF+5:Tx7ZRVjEudft9E8pEywEF |
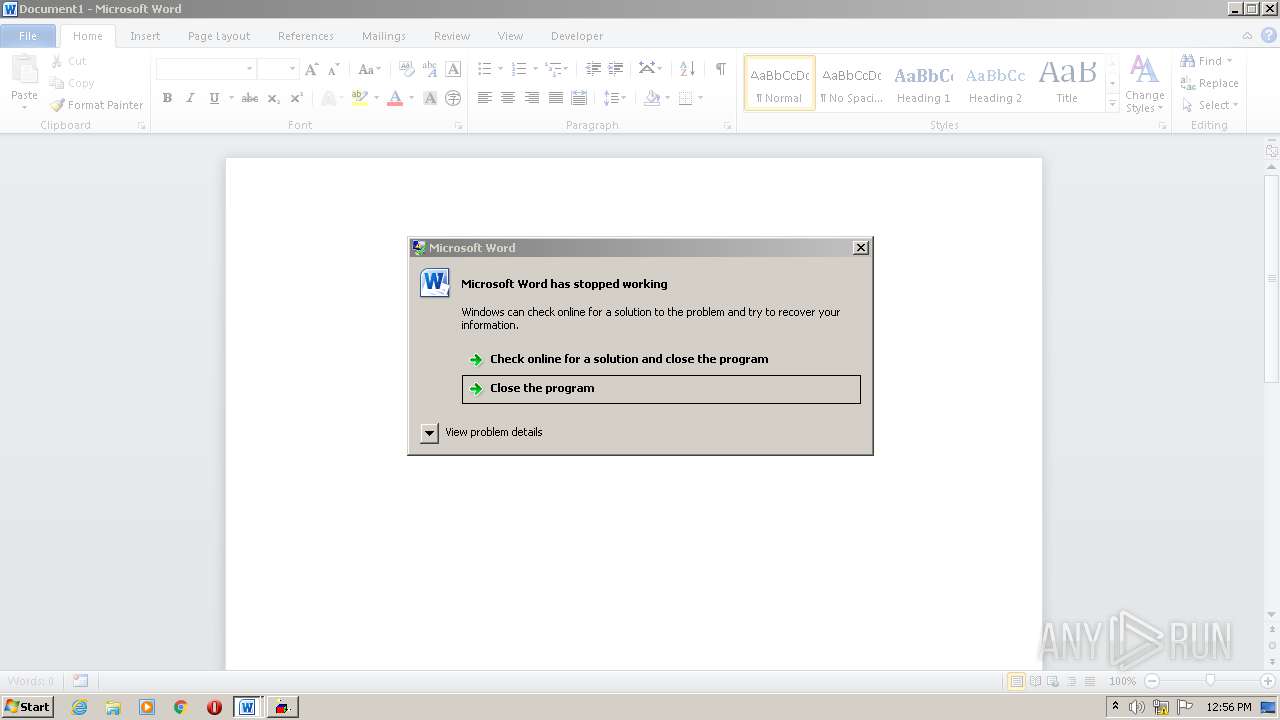
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 1880)
Executes scripts
- WINWORD.EXE (PID: 1880)
SUSPICIOUS
No suspicious indicators.INFO
Creates files in the user directory
- WINWORD.EXE (PID: 1880)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | 331 372 393 331 |
|---|---|
| Subject: | - |
| Author: | Windows User |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | Windows User |
| RevisionNumber: | 7 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 5.0 minutes |
| CreateDate: | 2019:12:02 20:45:00 |
| ModifyDate: | 2019:12:02 21:02:00 |
| Pages: | 10 |
| Words: | 43971 |
| Characters: | 250640 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| Lines: | 2088 |
| Paragraphs: | 588 |
| CharCountWithSpaces: | 294023 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
39
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1880 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\1302fdf298c1cd6551a3560d782079b6.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1948 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Word\MassFol\Users.jse" C:\Users\admin\AppData\Roaming\Microsoft\Templates\Normal.dotm | C:\Windows\System32\WScript.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2304 | C:\Windows\system32\dwwin.exe -x -s 1468 | C:\Windows\system32\dwwin.exe | — | DW20.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Watson Client Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2396 | "C:\PROGRA~1\COMMON~1\MICROS~1\DW\DW20.EXE" -x -s 1468 | C:\PROGRA~1\COMMON~1\MICROS~1\DW\DW20.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Application Error Reporting Exit code: 0 Version: 14.0.6015.1000 Modules
| |||||||||||||||
Total events
1 279
Read events
854
Write events
239
Delete events
186
Modification events
| (PID) Process: | (1880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 1)/ |
Value: 31292F0058070000010000000000000000000000 | |||
| (PID) Process: | (1880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
3
Text files
0
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR41B1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\D1085DF0.wmf | — | |
MD5:— | SHA256:— | |||
| 1880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\1CE1A97E.wmf | — | |
MD5:— | SHA256:— | |||
| 1880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{E9C0B391-F407-4C36-947E-B5E1D88532BC}.tmp | — | |
MD5:— | SHA256:— | |||
| 1880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF6A839020CD801946.TMP | — | |
MD5:— | SHA256:— | |||
| 1880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF5BD546497DE36352.TMP | — | |
MD5:— | SHA256:— | |||
| 1880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\1F4A6531.wmf | wmf | |
MD5:— | SHA256:— | |||
| 1880 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\EDA70EB.wmf | wmf | |
MD5:— | SHA256:— | |||
| 1880 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$02fdf298c1cd6551a3560d782079b6.doc | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report