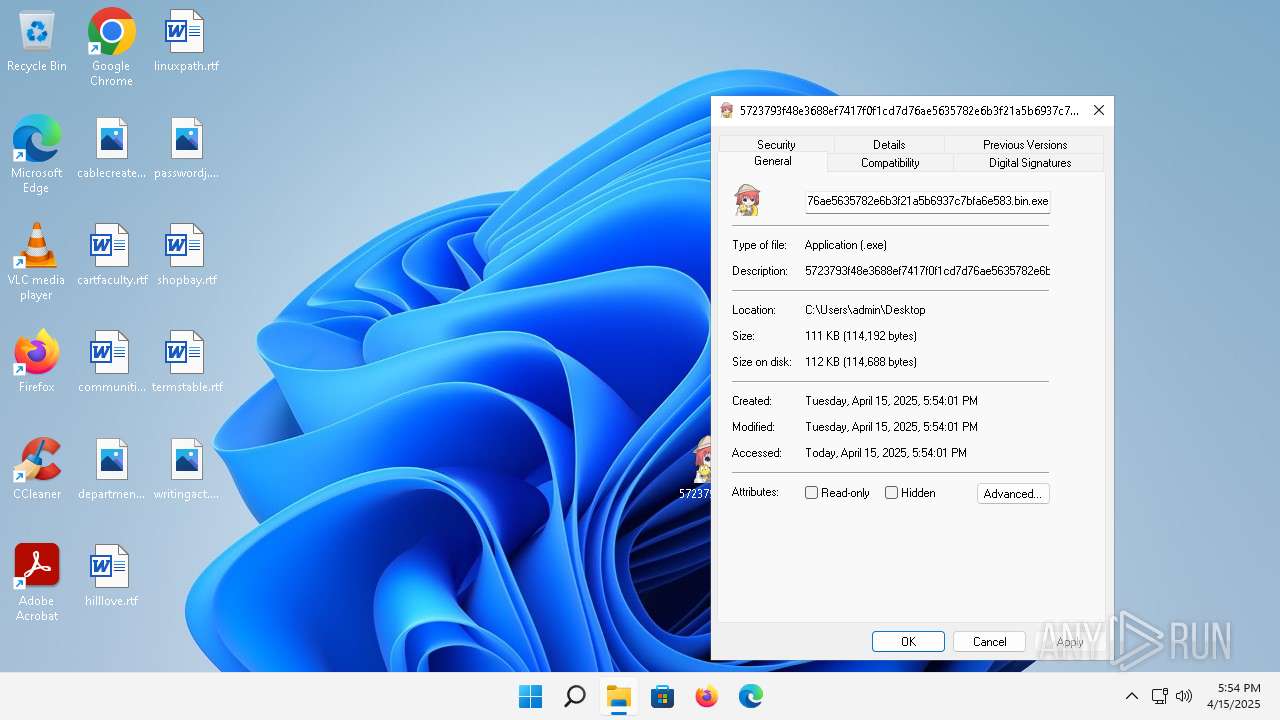
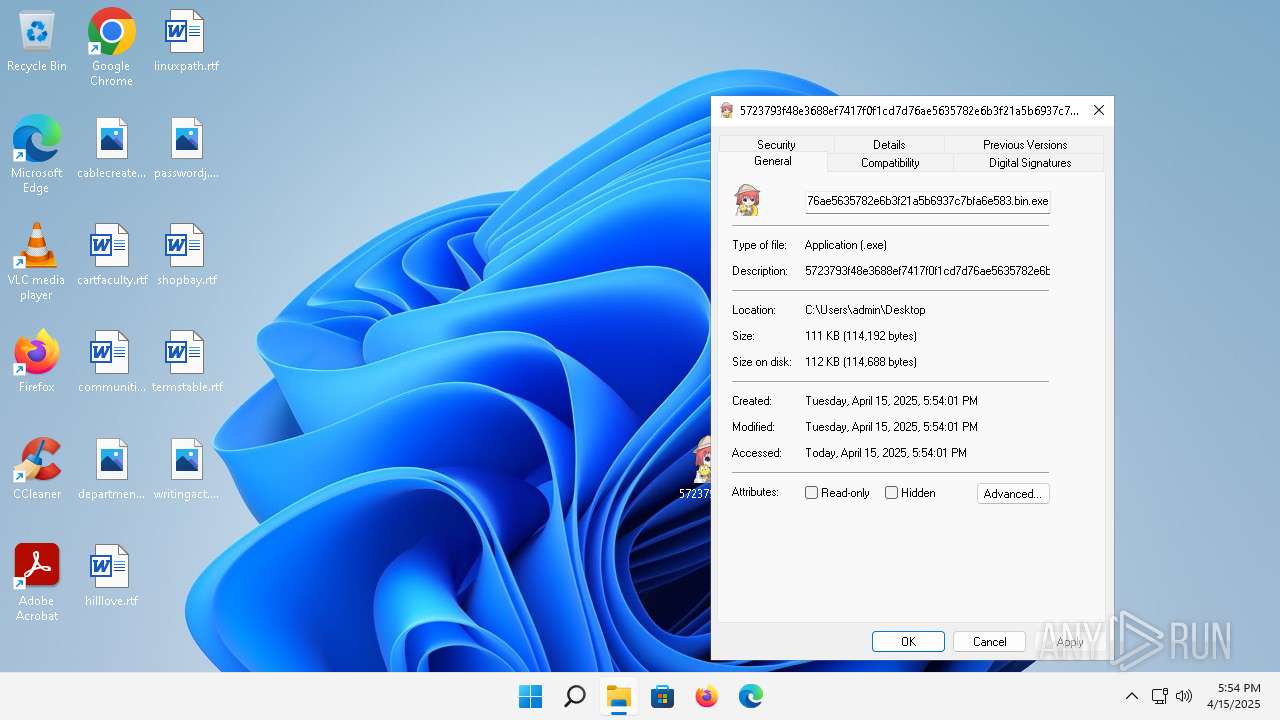
| File name: | 5723793f48e3688ef7417f0f1cd7d76ae5635782e6b3f21a5b6937c7bfa6e583.bin |
| Full analysis: | https://app.any.run/tasks/c606f7da-40b0-4741-bd20-73145a9f6b5d |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2025, 17:53:56 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | CD60623FF3AAA18F0F133AC52CD2994B |
| SHA1: | 2238A3306BADB1B80C6F04B272C4CE1F6E4356B5 |
| SHA256: | 5723793F48E3688EF7417F0F1CD7D76AE5635782E6B3F21A5B6937C7BFA6E583 |
| SSDEEP: | 3072:fAUXrUFJugKZudJ86w5IxyUIefCnon6FGM+F74S7:IUbUeqdJ8zGxyuCnp1S7 |
MALICIOUS
Executing a file with an untrusted certificate
- 5723793f48e3688ef7417f0f1cd7d76ae5635782e6b3f21a5b6937c7bfa6e583.bin.exe (PID: 1708)
SUSPICIOUS
Reads the Internet Settings
- WerFault.exe (PID: 4596)
Executes application which crashes
- 5723793f48e3688ef7417f0f1cd7d76ae5635782e6b3f21a5b6937c7bfa6e583.bin.exe (PID: 1708)
INFO
Checks supported languages
- 5723793f48e3688ef7417f0f1cd7d76ae5635782e6b3f21a5b6937c7bfa6e583.bin.exe (PID: 1708)
Creates files or folders in the user directory
- WerFault.exe (PID: 4596)
Checks proxy server information
- WerFault.exe (PID: 4596)
Reads the software policy settings
- WerFault.exe (PID: 4596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:17 14:10:40+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14 |
| CodeSize: | 7680 |
| InitializedDataSize: | 95744 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1140 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
115
Monitored processes
3
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1708 | "C:\Users\admin\Desktop\5723793f48e3688ef7417f0f1cd7d76ae5635782e6b3f21a5b6937c7bfa6e583.bin.exe" | C:\Users\admin\Desktop\5723793f48e3688ef7417f0f1cd7d76ae5635782e6b3f21a5b6937c7bfa6e583.bin.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 2840 | "C:\Windows\system32\DllHost.exe" /Processid:{B41DB860-64E4-11D2-9906-E49FADC173CA} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4596 | C:\Windows\system32\WerFault.exe -u -p 1708 -s 216 | C:\Windows\System32\WerFault.exe | 5723793f48e3688ef7417f0f1cd7d76ae5635782e6b3f21a5b6937c7bfa6e583.bin.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.22000.348 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 098
Read events
3 098
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
3
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4596 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_5723793f48e3688e_9fd2bbce996079c4a9f1fdcda61671e62ae1e53_a0007d22_f6e59ed0-8d8e-46c7-ab74-02fa83c788c8\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4596 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER.59f66c28-3c98-40fd-8bbb-14c934d79d21.tmp.xml | xml | |
MD5:32611E4B2CC45EA5D36B2EE02A60A67A | SHA256:9A9C6C1B9333189FBD5547D6439F3A7718323D22BD68457011F01B06D5A7025E | |||
| 4596 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER.4c3c8b8c-0679-47e3-b8e9-a3f908886921.tmp.dmp | binary | |
MD5:D8C8EAC26853C881EE978F1D9A2D8D1B | SHA256:36D3B683471D4EC0268BC709827AAE107ADD7B61D9EC04F713B893CD005A6250 | |||
| 4596 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\5723793f48e3688ef7417f0f1cd7d76ae5635782e6b3f21a5b6937c7bfa6e583.bin.exe.1708.dmp | binary | |
MD5:AE81EC66940A2DD63E9B6C24E42C6D18 | SHA256:5D6B9671AB03E47489A0FF42EF06B5F7B856DFFE89EAFE0D19A60DC297F952F8 | |||
| 4596 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER.6421d532-6014-42d5-9020-9eb7fb9da4d3.tmp.WERInternalMetadata.xml | binary | |
MD5:C92C10CAE57C963D09AC193312E1E327 | SHA256:881C8E92511EE958B07A415DFA4DA2C38CA2407694F45543014B5EFCDD716447 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
33
DNS requests
29
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3040 | smartscreen.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d0a596e17d8c3902 | unknown | — | — | whitelisted |
3040 | smartscreen.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1784 | firefox.exe | POST | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
1784 | firefox.exe | POST | 200 | 184.24.77.65:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
1352 | svchost.exe | GET | 200 | 2.23.155.168:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
1784 | firefox.exe | POST | 200 | 184.24.77.62:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
3640 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4012 | svchost.exe | POST | 403 | 23.218.210.69:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | whitelisted |
4012 | svchost.exe | POST | 403 | 23.218.210.69:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | whitelisted |
4012 | svchost.exe | POST | 403 | 23.218.210.69:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
5960 | OfficeC2RClient.exe | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
5936 | rundll32.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3040 | smartscreen.exe | 48.209.144.71:443 | checkappexec.microsoft.com | — | US | whitelisted |
3040 | smartscreen.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
3040 | smartscreen.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | unknown |
4596 | WerFault.exe | 104.208.16.94:443 | umwatson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1352 | svchost.exe | 2.23.155.147:80 | — | Akamai International B.V. | IT | unknown |
5184 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1784 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
umwatson.events.data.microsoft.com |
| whitelisted |
incoming.telemetry.mozilla.org |
| whitelisted |
firefox.settings.services.mozilla.com |
| whitelisted |
prod.remote-settings.prod.webservices.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1352 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |