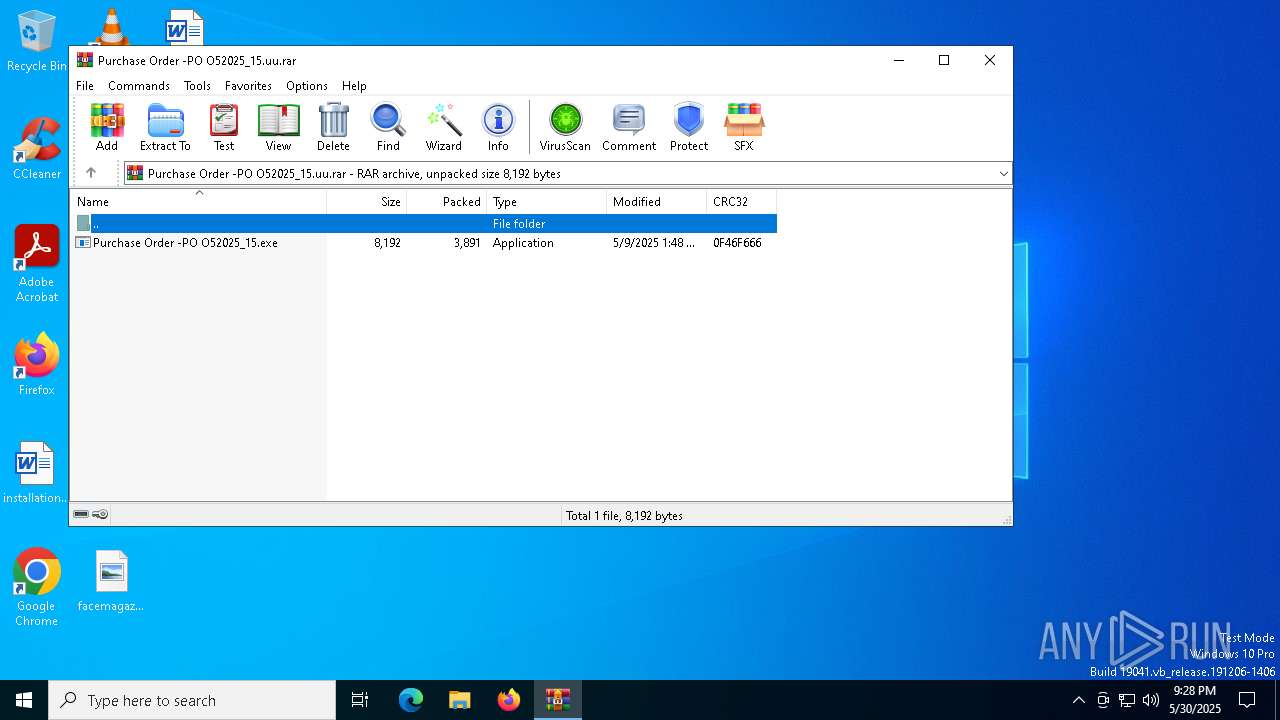
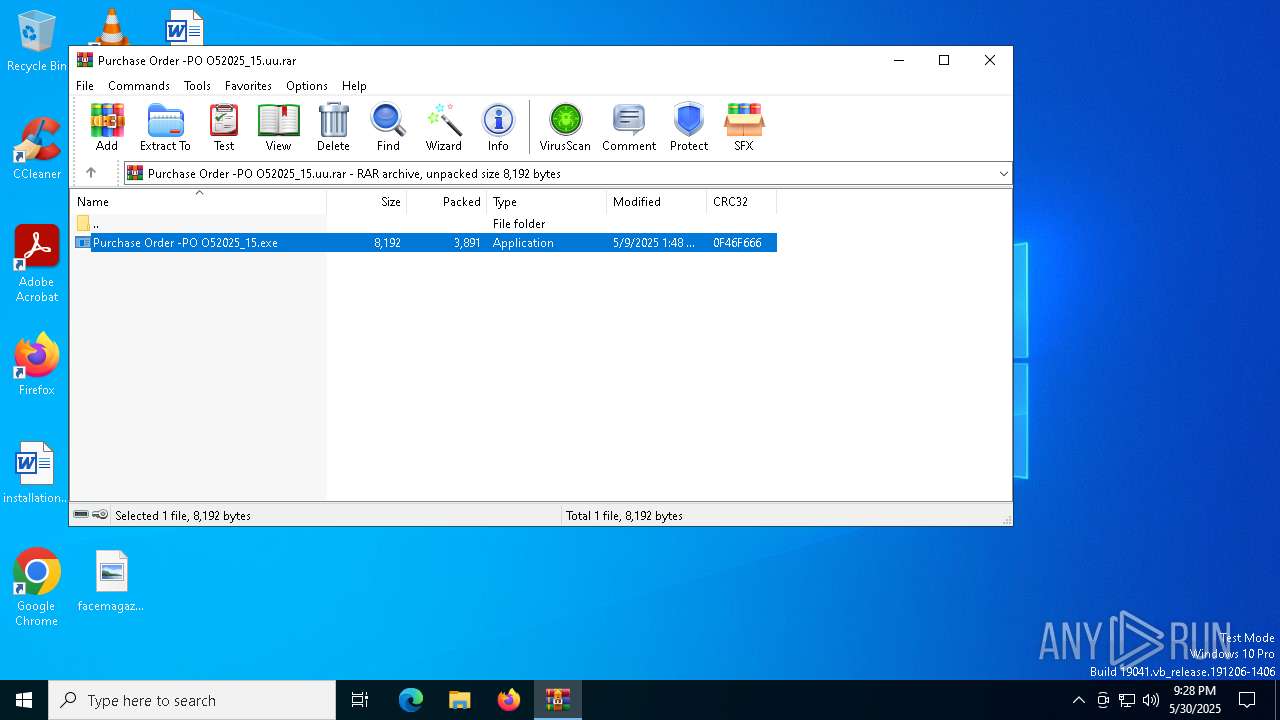
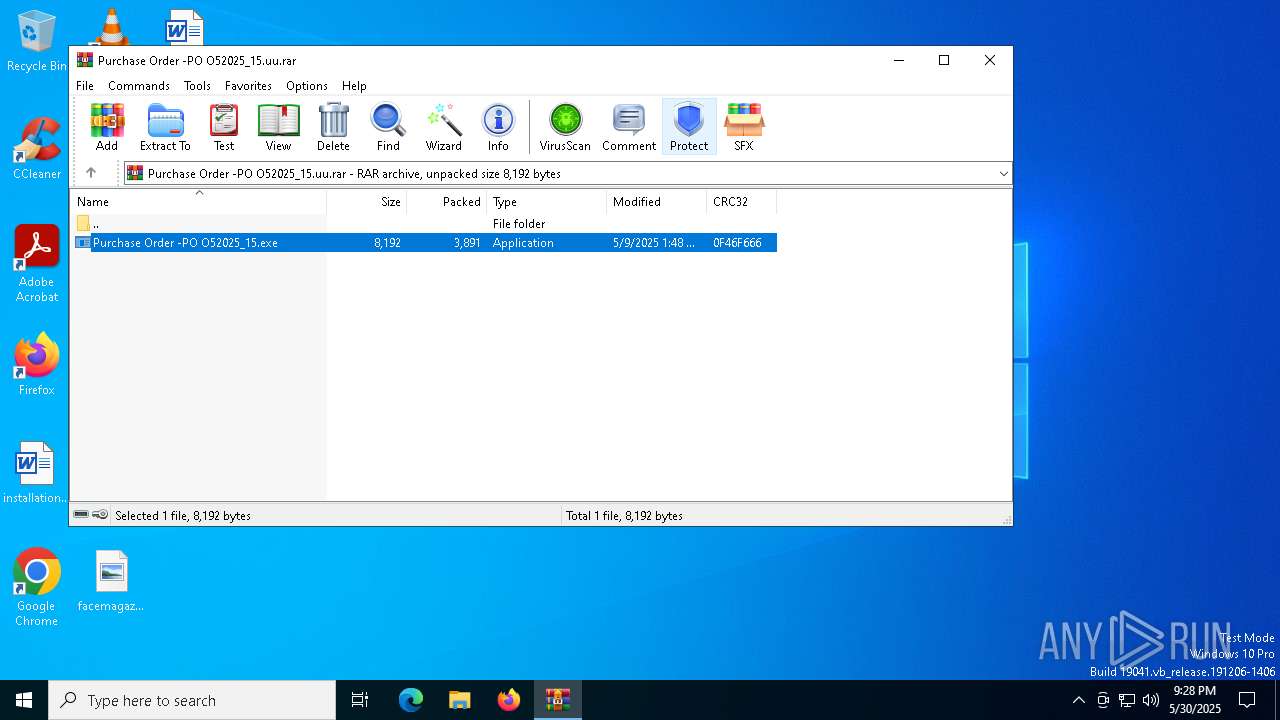
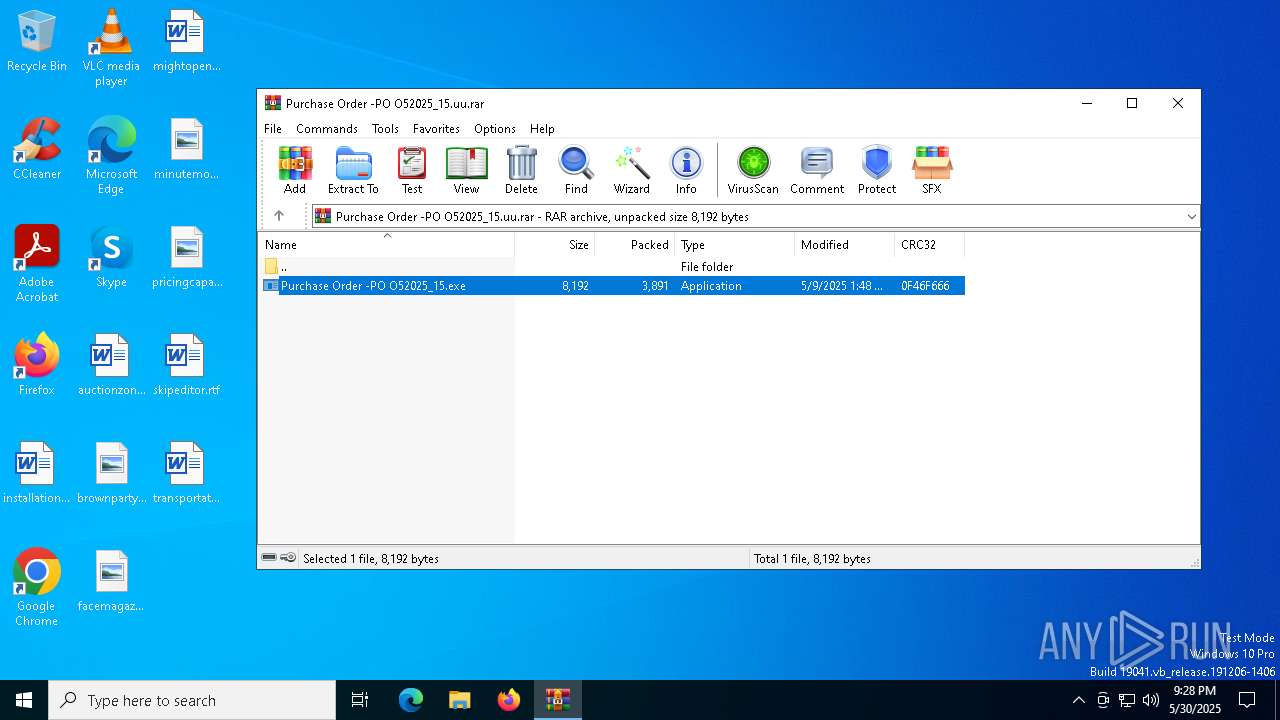
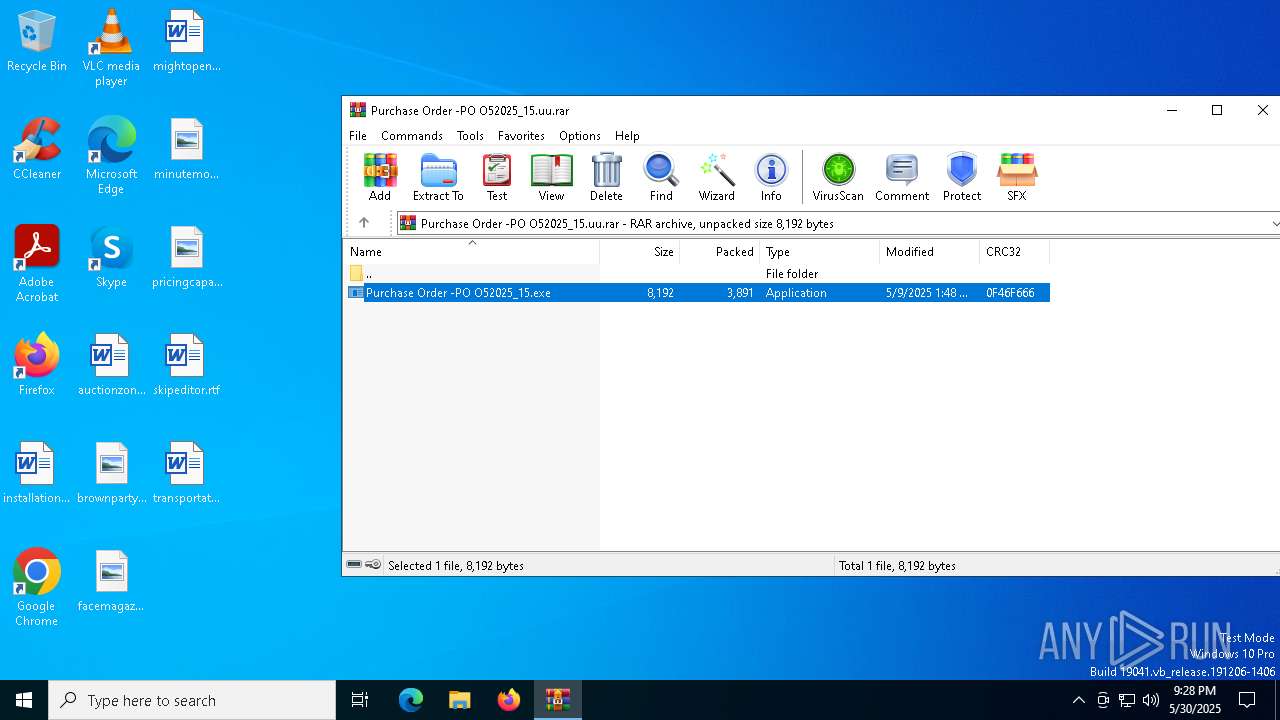
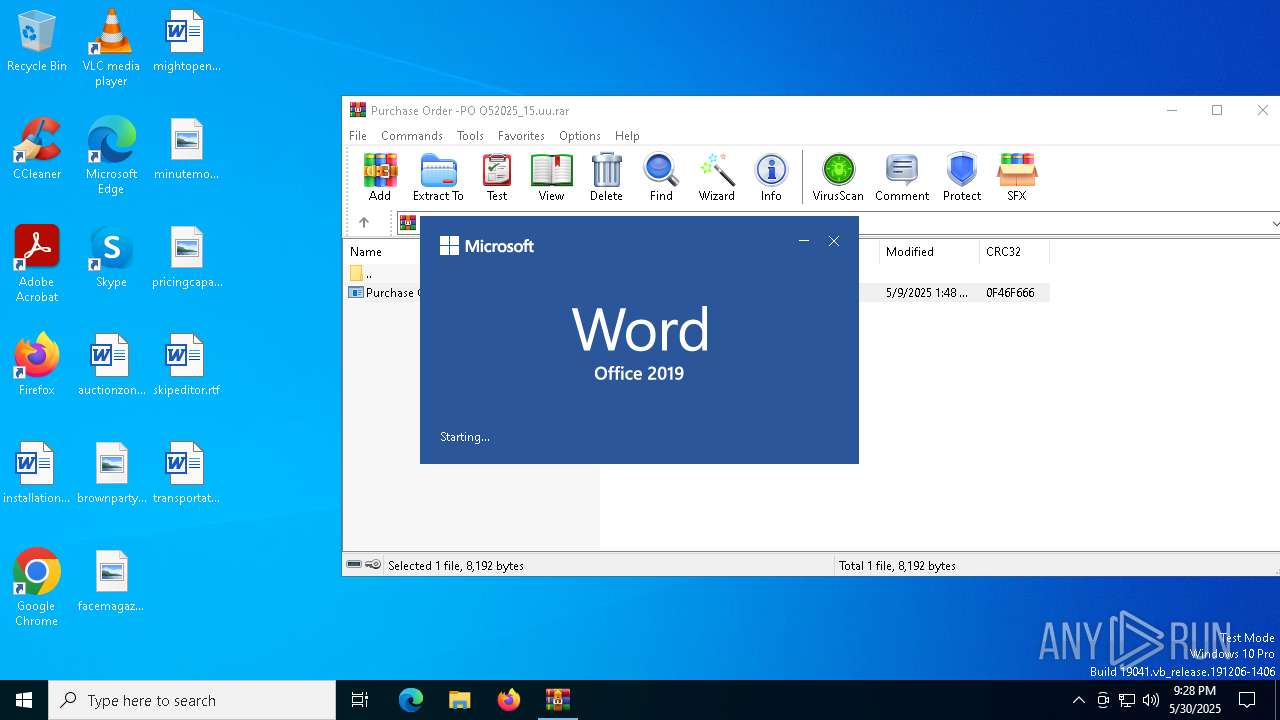
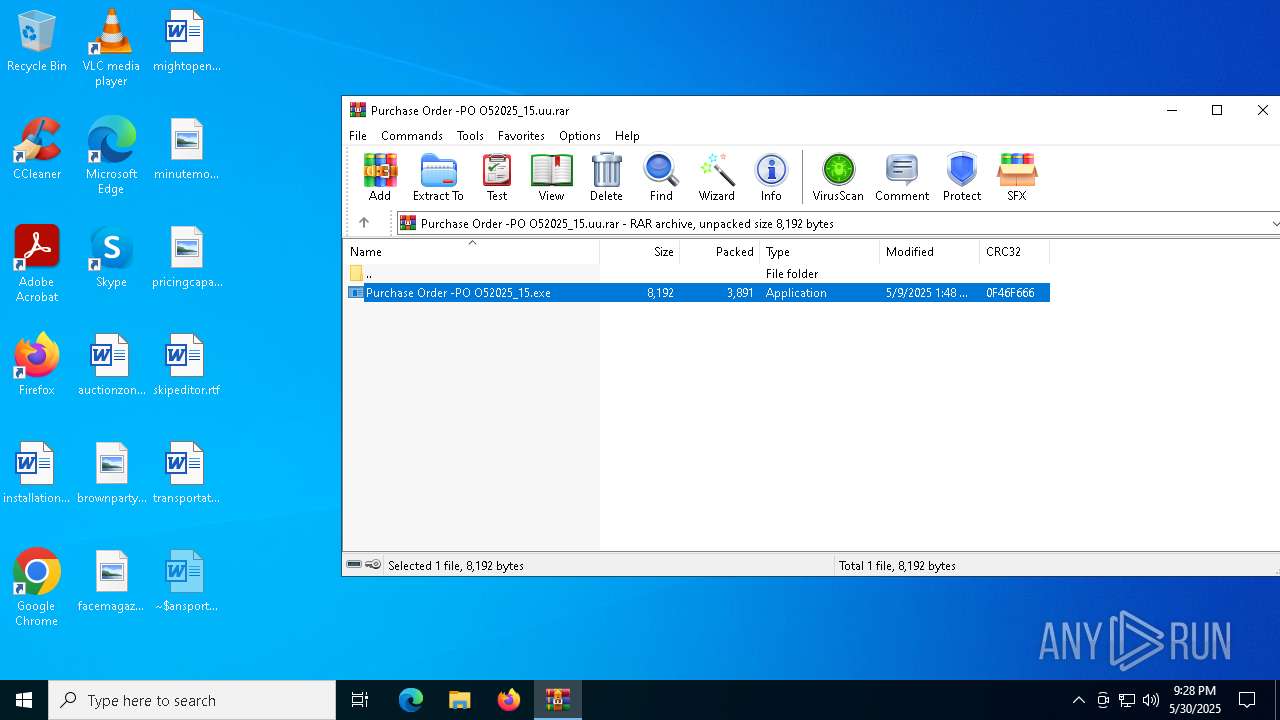
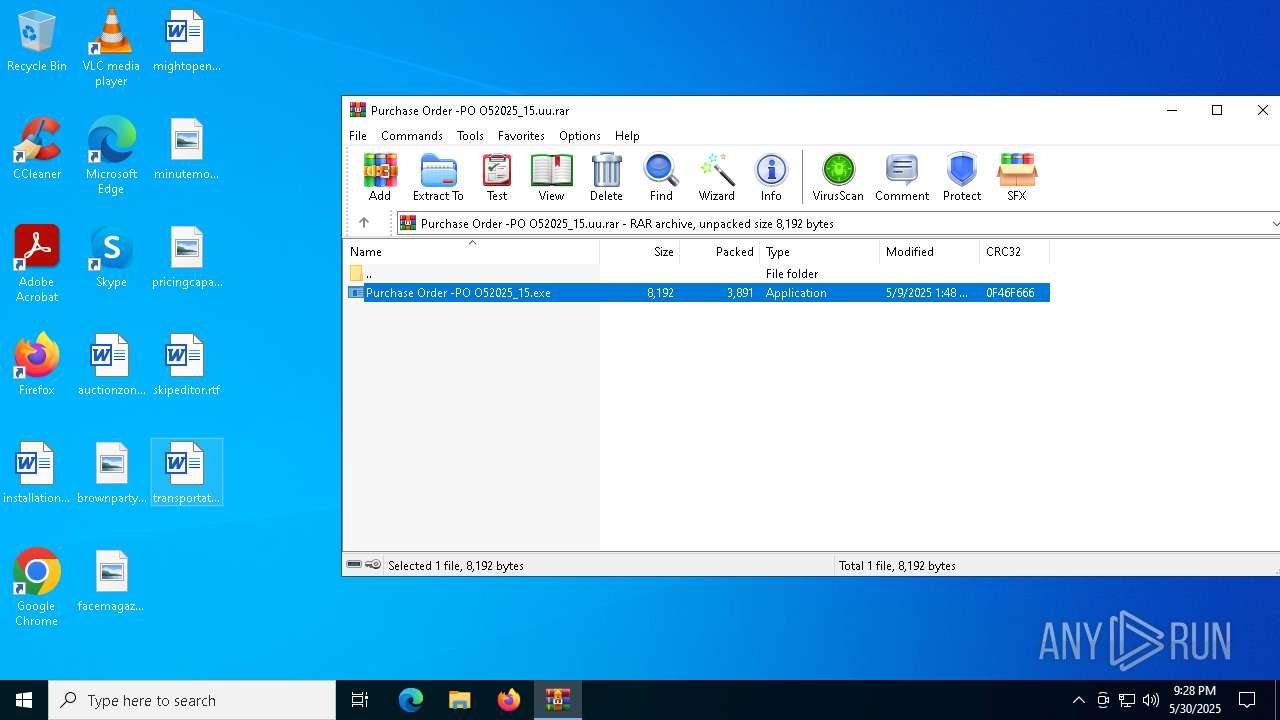
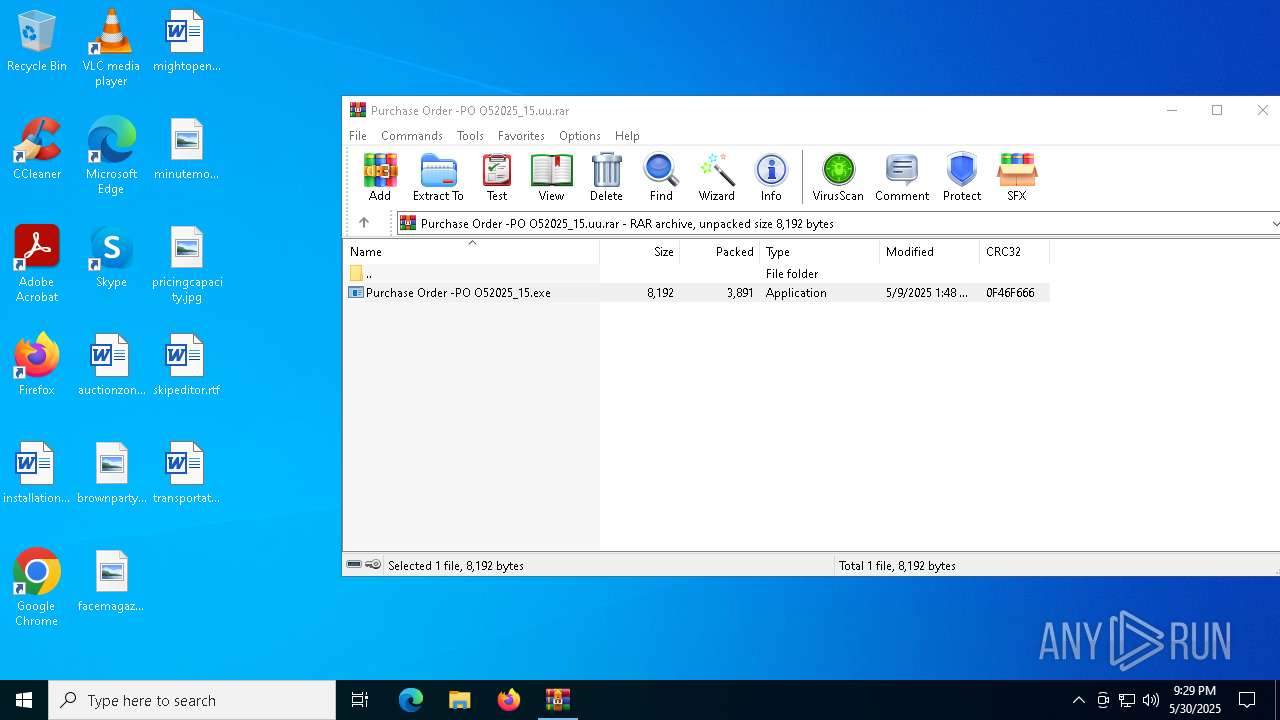
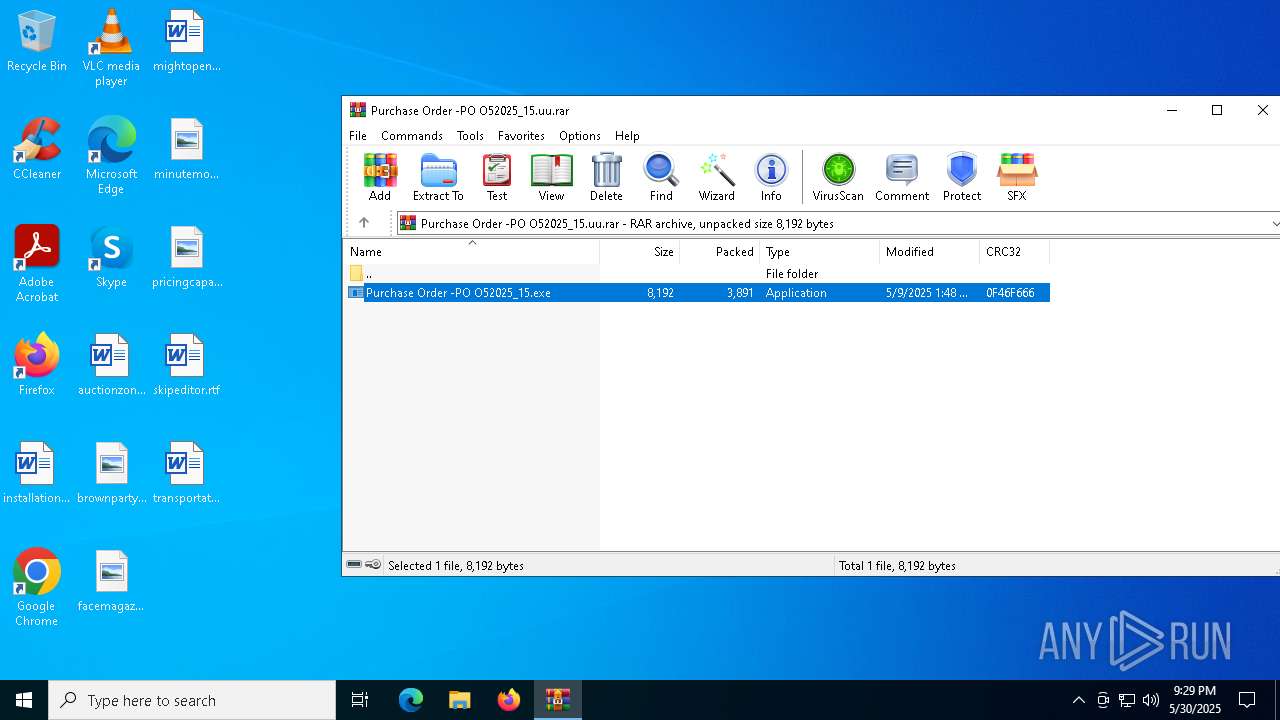
| File name: | Purchase Order -PO O52025_15.uu |
| Full analysis: | https://app.any.run/tasks/8dedb406-fdec-447a-a0c1-343c698f5d29 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2025, 21:28:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | EAA7D0B638B67C44B79895C57D981B37 |
| SHA1: | B3825DF14CDA542A8C205D451605AB64281D364E |
| SHA256: | 5716C983F316DC79A898F3131745F78EDC7A5E7813C4D6DE8DB94AEE2F194EBA |
| SSDEEP: | 192:0PJT01+Z7X9eFGlCx+2jRlKafNj+/TLmKFKCn:yT0Yp9evx++i3mKln |
MALICIOUS
GENERIC has been found (auto)
- WinRAR.exe (PID: 8060)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 8060)
INFO
Checks supported languages
- Purchase Order -PO O52025_15.exe (PID: 7496)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8060)
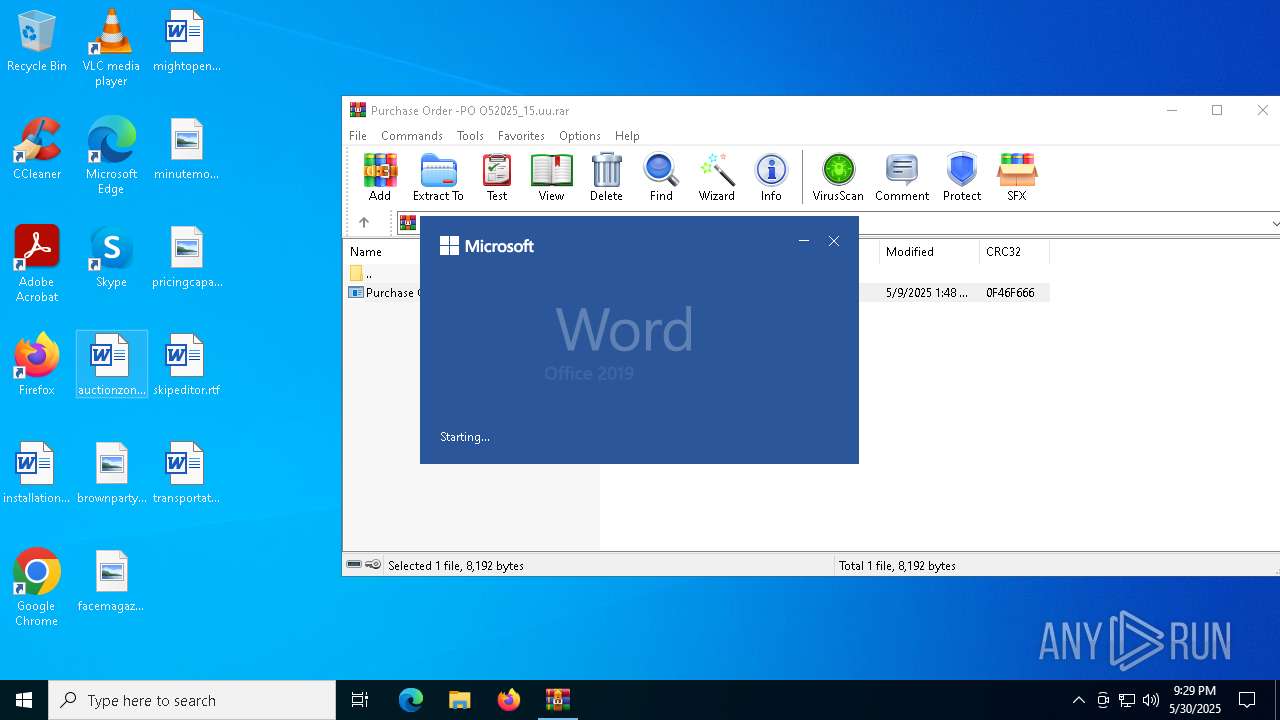
Manual execution by a user
- WINWORD.EXE (PID: 4120)
- WINWORD.EXE (PID: 3176)
- mspaint.exe (PID: 6652)
- WINWORD.EXE (PID: 716)
- WINWORD.EXE (PID: 2320)
- WINWORD.EXE (PID: 7992)
- mspaint.exe (PID: 6808)
Reads the machine GUID from the registry
- Purchase Order -PO O52025_15.exe (PID: 7496)
Reads the computer name
- Purchase Order -PO O52025_15.exe (PID: 7496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 3891 |
| UncompressedSize: | 8192 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Purchase Order -PO O52025_15.exe |
Total processes
149
Monitored processes
16
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "421B7020-C0F3-4EF1-9CAE-D5A7881A8E55" "C8435E91-45A2-4047-B6A3-3FBC18A6BDFA" "716" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 716 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\auctionzone.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2088 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "9336B96C-35E5-43E5-9A49-646DB80EC0EB" "4B838376-75F4-4F13-B0AF-F7E42EAD13EA" "7992" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 3221225547 Version: 0.12.2.0 Modules
| |||||||||||||||
| 2152 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "485D8B34-E8B2-4A1F-A63E-0A8A3BDC3434" "F204DF21-7DCA-465E-B509-02A9ECC99191" "4120" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 2320 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\mightopen.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 3176 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\skipeditor.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
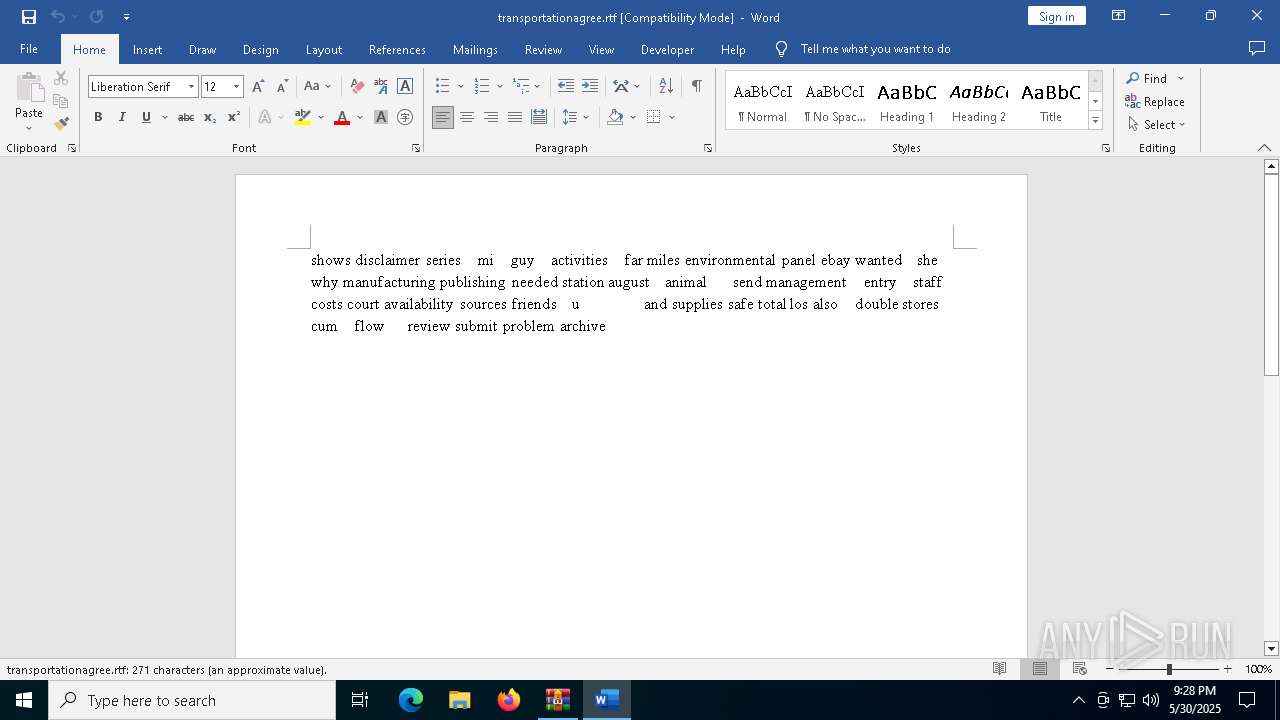
| 4120 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\transportationagree.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 4400 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6048 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "54736846-8AA1-43E8-8ECE-42672C59ECC3" "9BA49217-1DDD-4A0D-B223-D17183F21D37" "2320" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 6208 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "D18F9B63-C1EC-4A25-A1FB-31E12A485113" "8687528F-03EF-4AC8-97C7-61DFE4E58B79" "3176" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 3221225547 Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
36 846
Read events
35 251
Write events
1 413
Delete events
182
Modification events
| (PID) Process: | (8060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (8060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (8060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (8060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (8060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (8060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Purchase Order -PO O52025_15.uu.rar | |||
| (PID) Process: | (8060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (8060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (8060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (8060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
78
Text files
10
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4120 | WINWORD.EXE | C:\Users\admin\Desktop\~$ansportationagree.rtf | binary | |
MD5:16D4CE1ACBF8B8BEC1D86F69BFB2FBB8 | SHA256:1E773EF3C9D38187E614EEE0AD74D1B5905E22F345C8D69C171820F9EBCCA010 | |||
| 4120 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:B4262EC541CBFE3C61E1E25381C79C2E | SHA256:826B410B6BE1815D54BBC93906FD432EA27B59F0C7927EF6D713EA764A76E570 | |||
| 4120 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\transportationagree.rtf.LNK | binary | |
MD5:14D431DB9C71678B1D491C695D4BAC5A | SHA256:9B9F8EBBB6DCDA02DD42994D54046EFC818C908EF57BD4504681F6490D321967 | |||
| 4120 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:476DAF7C44508478F7BD6B692415AD6E | SHA256:C69ED67C32942E51AA155EA232284B501962336557BDC74EDFE3FEDA78C2DBAE | |||
| 4120 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Word.Settings.json | binary | |
MD5:E4E83F8123E9740B8AA3C3DFA77C1C04 | SHA256:6034F27B0823B2A6A76FE296E851939FD05324D0AF9D55F249C79AF118B0EB31 | |||
| 4120 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Diagnostics\WINWORD\App1748640519329262000_8E24B472-3E44-4B80-B8F0-3333787A35B5.log | — | |
MD5:— | SHA256:— | |||
| 4120 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRS{33DFE809-D7BE-4A75-86B9-4CA10BA23A4B}.tmp | binary | |
MD5:830FBF83999E052538EAF156AB6ECB17 | SHA256:D5098A2CEAE815DB29CD53C76F85240C95DC4D2E3FEDDD71D628617064C29869 | |||
| 4120 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Word.SurveyEventActivityStats.json | binary | |
MD5:6CA4960355E4951C72AA5F6364E459D5 | SHA256:88301F0B7E96132A2699A8BCE47D120855C7F0A37054540019E3204D6BCBABA3 | |||
| 4120 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CF539082.tmp | binary | |
MD5:79A22F4E754991FB51F73F0B26C85324 | SHA256:E6FB6546D3BC59FCC139767277C294A5E83068D710C9920174C3009AA4F33785 | |||
| 4120 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Word.SurveyHistoryStats.json | binary | |
MD5:6CA4960355E4951C72AA5F6364E459D5 | SHA256:88301F0B7E96132A2699A8BCE47D120855C7F0A37054540019E3204D6BCBABA3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
47
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 104.75.232.13:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.20.174.91:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 92.122.166.122:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4120 | WINWORD.EXE | GET | 200 | 104.75.232.13:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
8080 | SIHClient.exe | GET | 200 | 2.20.174.91:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8080 | SIHClient.exe | GET | 200 | 2.20.174.91:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.190.160.5:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 104.75.232.13:80 | ocsp.digicert.com | Akamai International B.V. | FR | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 92.122.166.122:80 | crl.microsoft.com | AKAMAI-AS | NL | whitelisted |
6544 | svchost.exe | 20.190.160.5:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.20.174.91:80 | www.microsoft.com | AKAMAI-AS | NL | whitelisted |
7556 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.172.255.218:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7292 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |