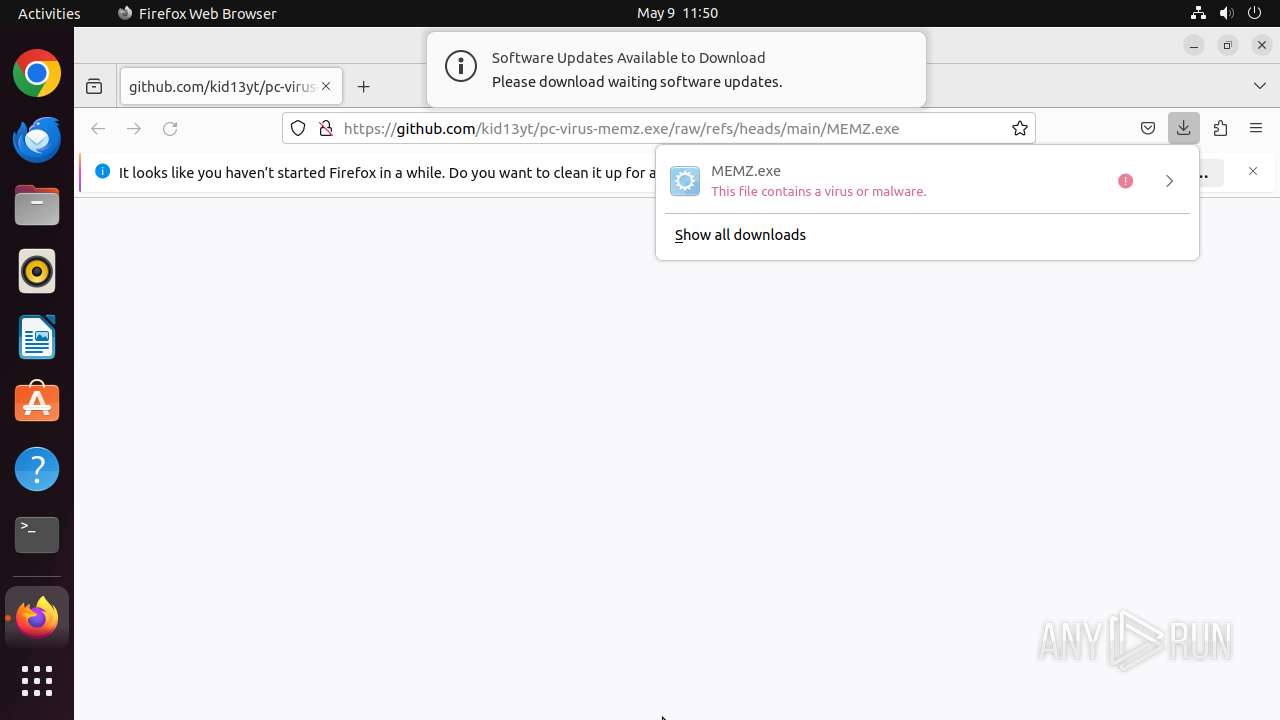
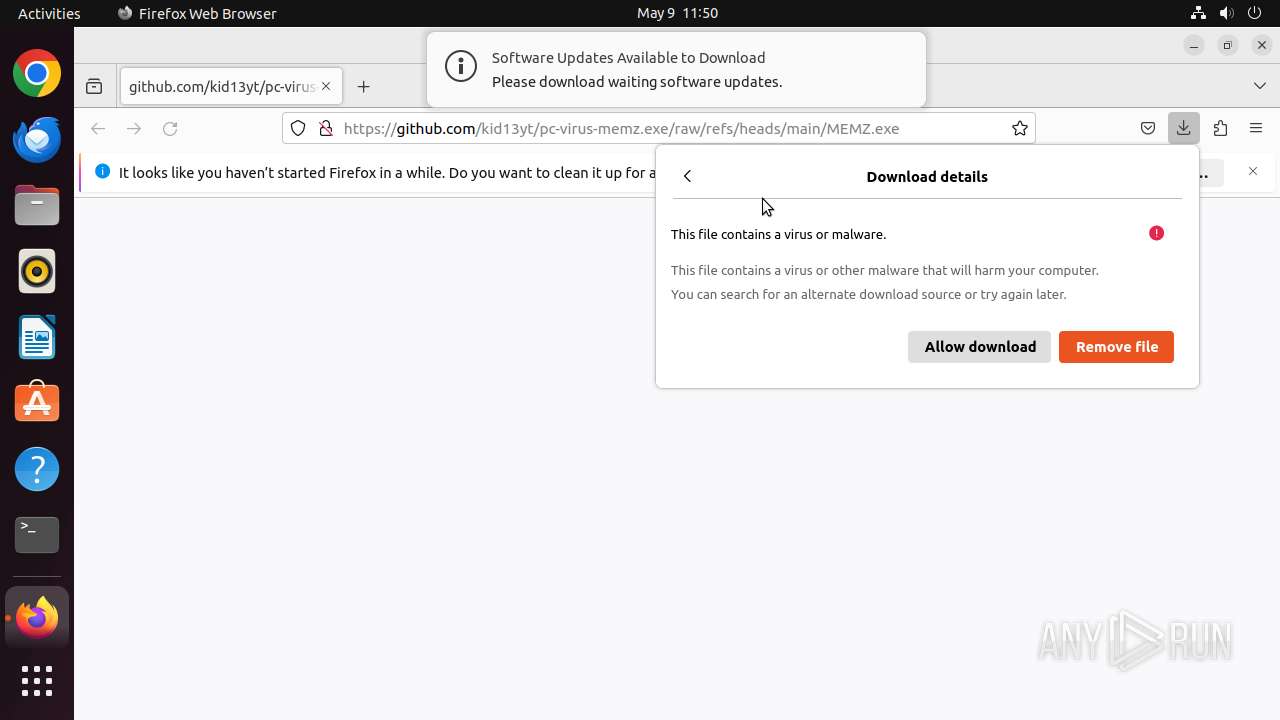
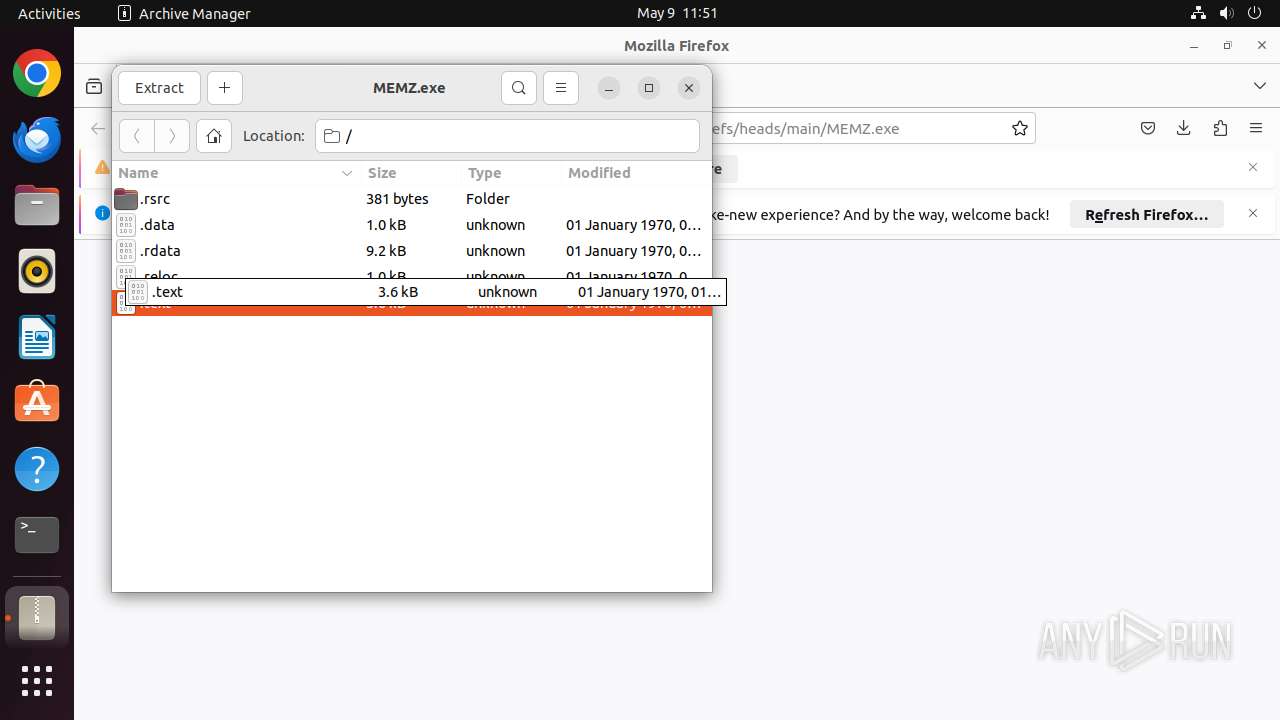
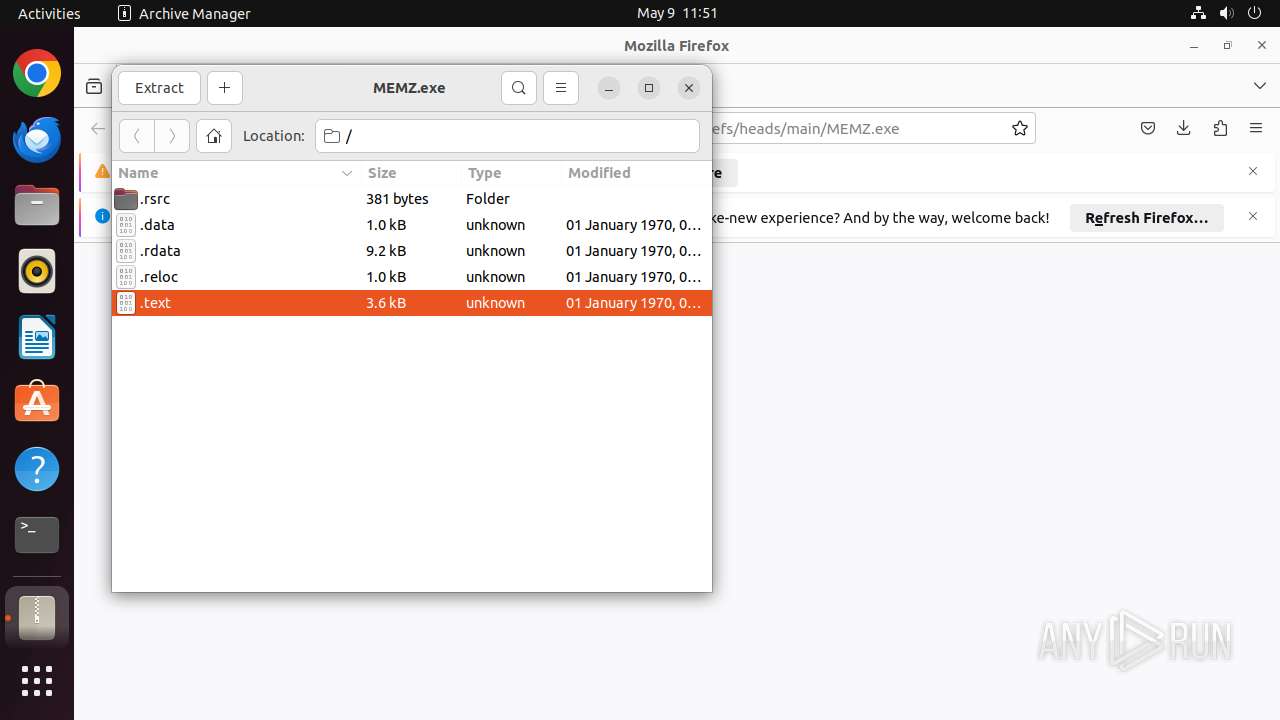
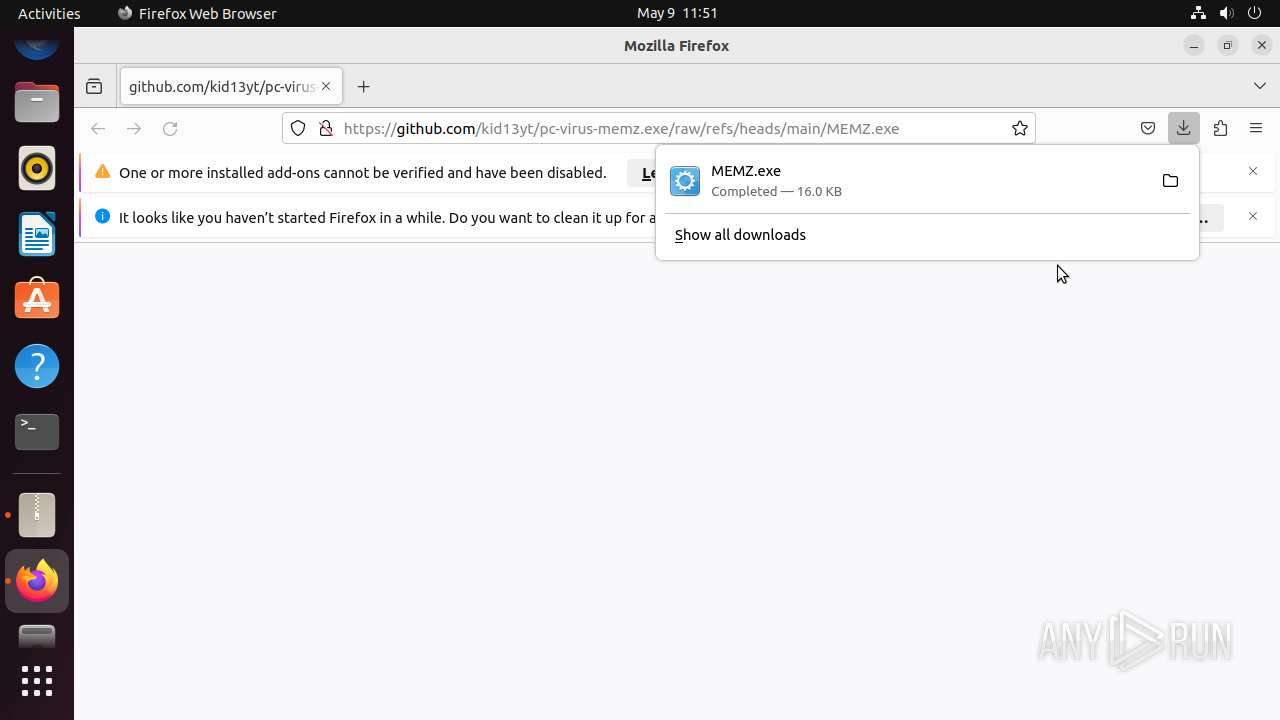
| URL: | https://github.com/kid13yt/pc-virus-memz.exe/raw/refs/heads/main/MEMZ.exe |
| Full analysis: | https://app.any.run/tasks/b4871514-5a0d-4a5d-b761-68c89e08cb0d |
| Verdict: | Malicious activity |
| Analysis date: | May 09, 2025, 10:50:33 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| MD5: | CBDF8AE6ECF1A57C8AE763048C921C96 |
| SHA1: | 952235DB423355738D023FE899A88F5C882CF7EE |
| SHA256: | 570E27C6BCA3F45A3B9B9CA6CD0E4AABFC55E070AAF564E9A6FF5F388C82009C |
| SSDEEP: | 3:N8tEd+MiWtGDXbAdP7OLNKkL4A:2uoxwIUZ7OLNK2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes commands using command-line interpreter
- sudo (PID: 40667)
- firefox (PID: 40668)
Check the Environment Variables Related to System Identification (os-release)
- firefox (PID: 40668)
- snapctl (PID: 40723)
- snapctl (PID: 40717)
- snapctl (PID: 40770)
- snapctl (PID: 41181)
- snapctl (PID: 41218)
- snapctl (PID: 40765)
Reads passwd file
- dumpe2fs (PID: 40688)
- dumpe2fs (PID: 40697)
Executes the "rm" command to delete files or directories
- firefox (PID: 40668)
INFO
Checks timezone
- dumpe2fs (PID: 40697)
- dumpe2fs (PID: 40688)
- file-roller (PID: 41188)
- 7z (PID: 41232)
- 7z (PID: 41201)
Creates file in the temporary folder
- firefox (PID: 40668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
402
Monitored processes
182
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 40666 | /bin/sh -c "DISPLAY=:0 sudo -iu user firefox https://github\.com/kid13yt/pc-virus-memz\.exe/raw/refs/heads/main/MEMZ\.exe " | /usr/bin/dash | — | any-guest-agent |
User: root Integrity Level: UNKNOWN | ||||
| 40667 | sudo -iu user firefox https://github.com/kid13yt/pc-virus-memz.exe/raw/refs/heads/main/MEMZ.exe | /usr/bin/sudo | — | dash |
User: root Integrity Level: UNKNOWN | ||||
| 40668 | /snap/firefox/3358/usr/lib/firefox/firefox https://github.com/kid13yt/pc-virus-memz.exe/raw/refs/heads/main/MEMZ.exe | /snap/firefox/3358/usr/lib/firefox/firefox | sudo | |
User: user Integrity Level: UNKNOWN | ||||
| 40669 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | firefox |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40680 | /snap/snapd/20290/usr/lib/snapd/snap-seccomp version-info | /snap/snapd/20290/usr/lib/snapd/snap-seccomp | — | firefox |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40686 | /snap/snapd/20290/usr/lib/snapd/snap-confine --base core22 snap.firefox.firefox /usr/lib/snapd/snap-exec firefox https://github.com/kid13yt/pc-virus-memz.exe/raw/refs/heads/main/MEMZ.exe | /snap/snapd/20290/usr/lib/snapd/snap-confine | — | firefox |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40688 | dumpe2fs -h /dev/sda3 | /usr/sbin/dumpe2fs | — | udisksd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40689 | snap-update-ns --from-snap-confine firefox | /snap/snapd/20290/usr/lib/snapd/snap-update-ns | — | firefox |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40696 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40697 | dumpe2fs -h /dev/sda3 | /usr/sbin/dumpe2fs | — | udisksd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 41188 | file-roller | /home/user/.local/share/recently-used.xbel | xml | |
MD5:— | SHA256:— | |||
| 41188 | file-roller | /home/user/.local/share/recently-used.xbel.CI4252 | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
55
DNS requests
95
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 91.189.91.96:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
— | — | GET | 204 | 91.189.91.96:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
40668 | firefox | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
40668 | firefox | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
40668 | firefox | POST | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/ | unknown | — | — | whitelisted |
40668 | firefox | POST | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/ | unknown | — | — | whitelisted |
40668 | firefox | POST | 200 | 184.24.77.57:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
40668 | firefox | POST | 200 | 142.250.185.99:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
40668 | firefox | POST | 200 | 184.24.77.57:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
40668 | firefox | POST | 200 | 142.250.185.99:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
484 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 91.189.91.96:80 | — | Canonical Group Limited | US | unknown |
— | — | 169.150.255.184:443 | odrs.gnome.org | — | GB | whitelisted |
512 | snapd | 185.125.188.58:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
40668 | firefox | 34.36.137.203:443 | contile.services.mozilla.com | — | — | whitelisted |
40668 | firefox | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
40668 | firefox | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
40668 | firefox | 172.64.149.23:80 | ocsp.sectigo.com | CLOUDFLARENET | US | whitelisted |
40668 | firefox | 184.24.77.57:80 | r11.o.lencr.org | Akamai International B.V. | DE | whitelisted |
40668 | firefox | 142.250.185.99:80 | o.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
odrs.gnome.org |
| whitelisted |
api.snapcraft.io |
| whitelisted |
github.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
445 | systemd-resolved | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
445 | systemd-resolved | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |