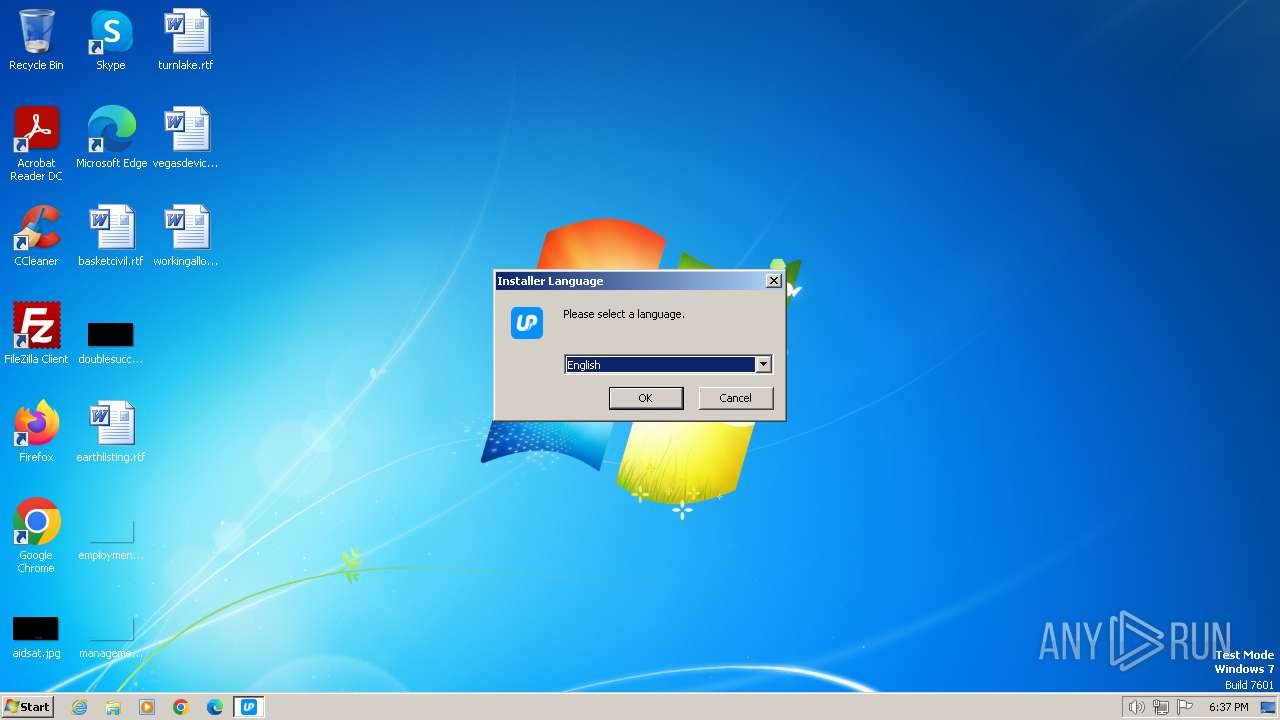
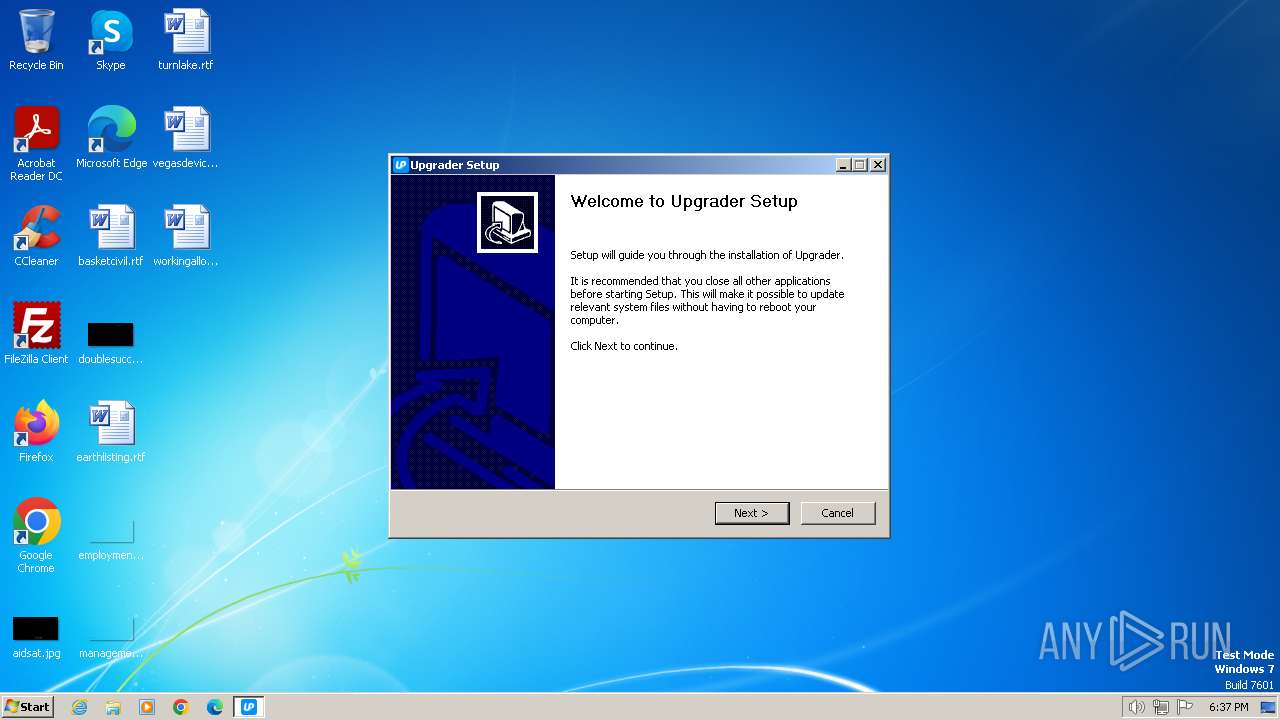
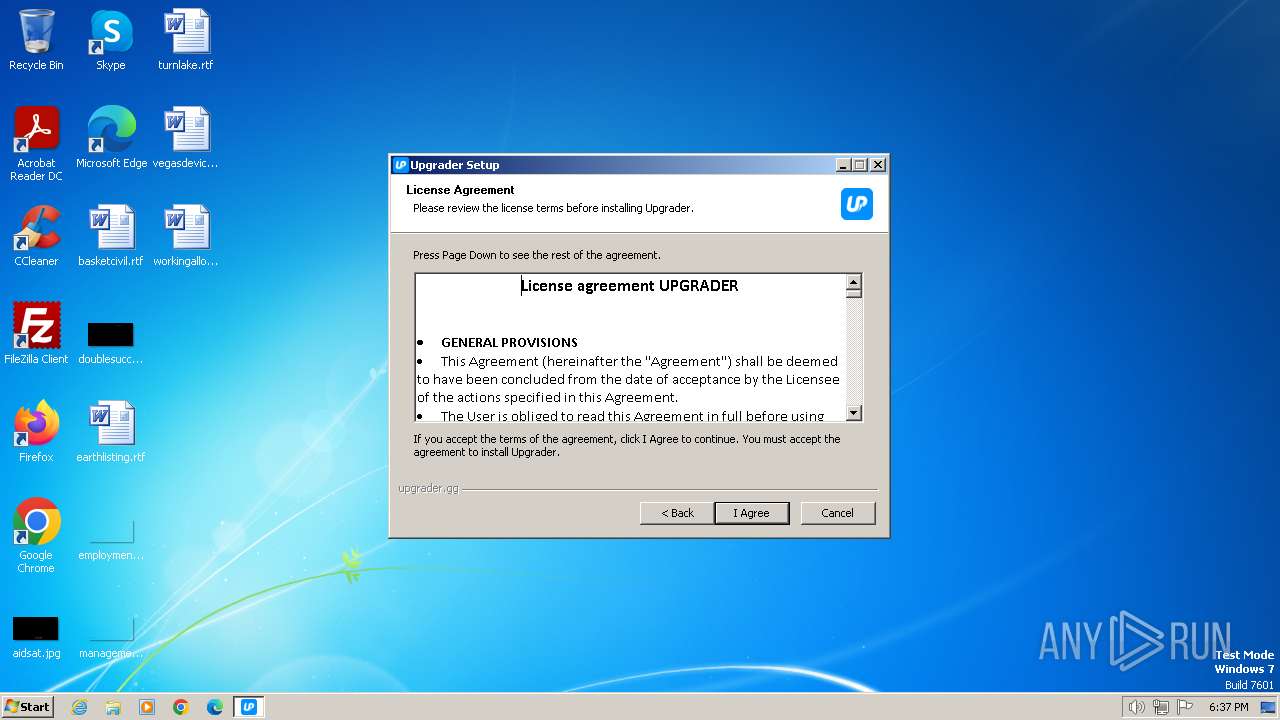
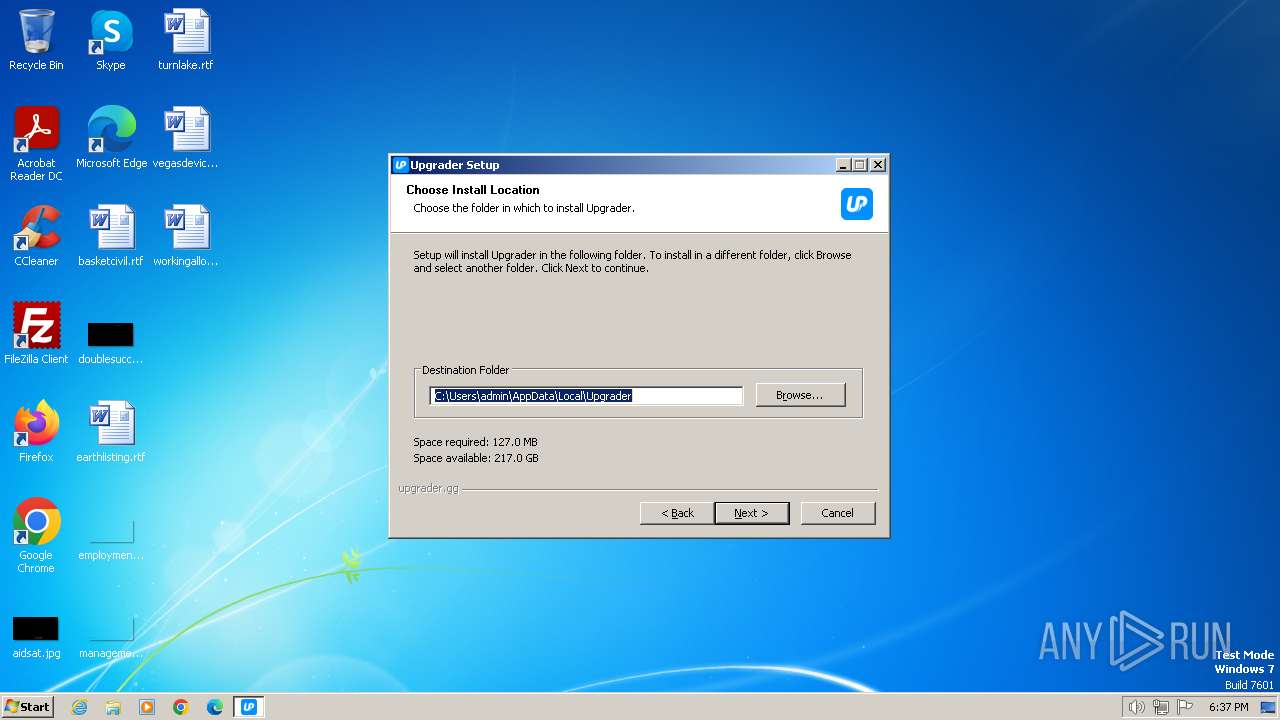
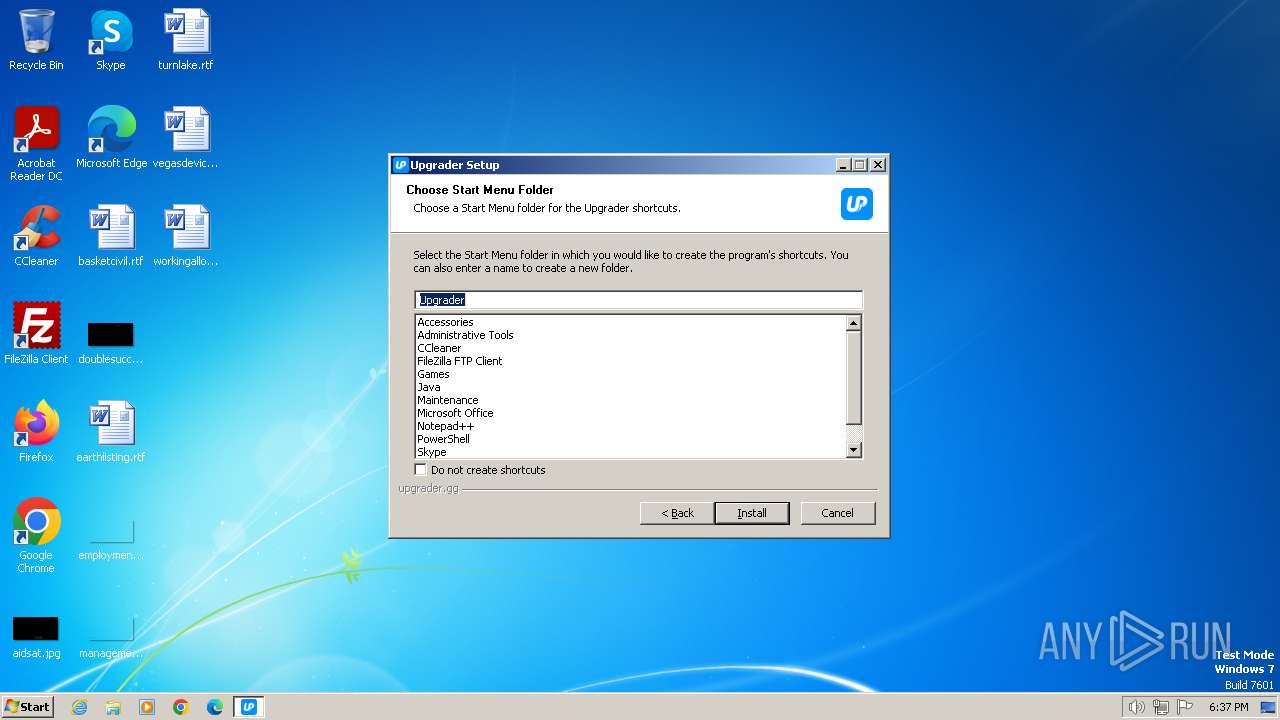
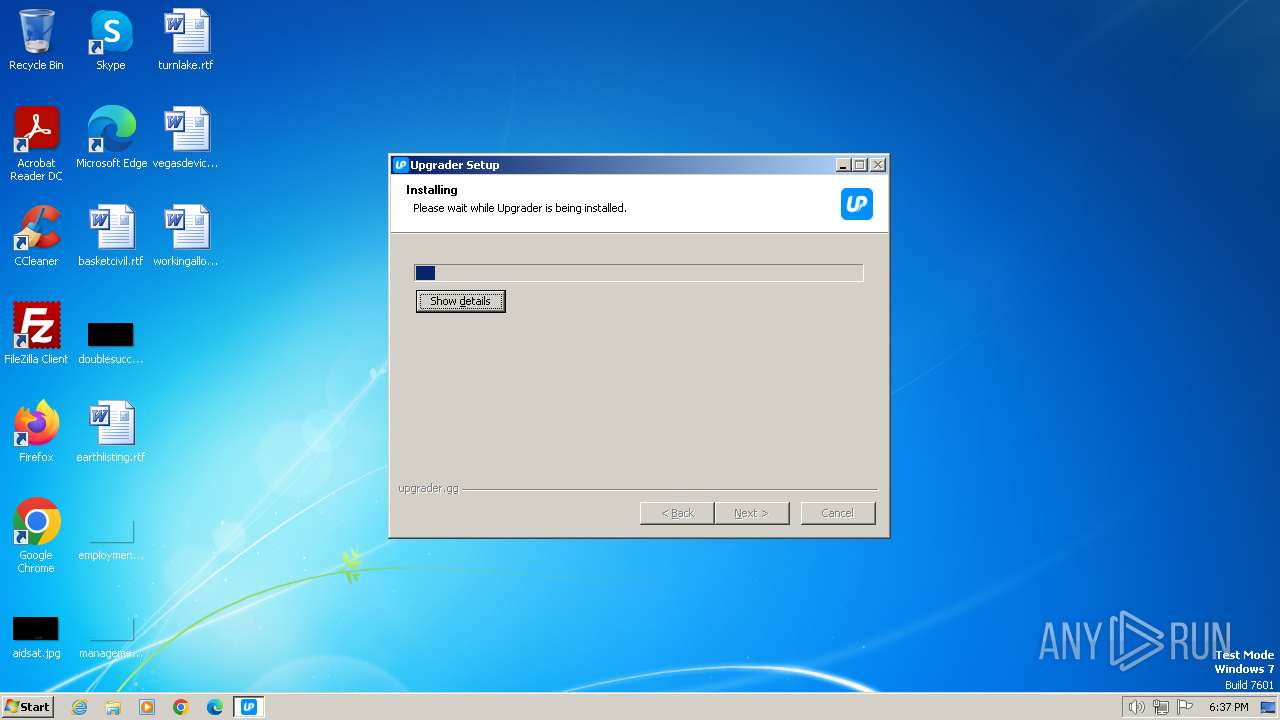
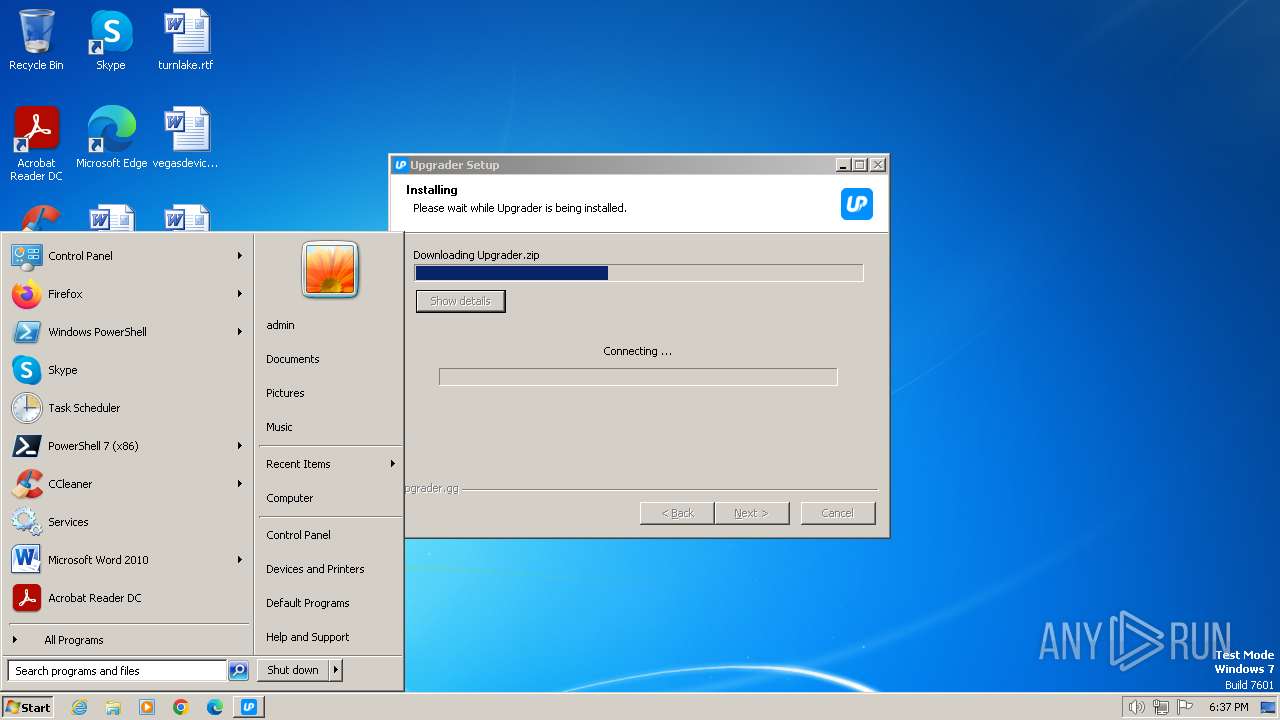
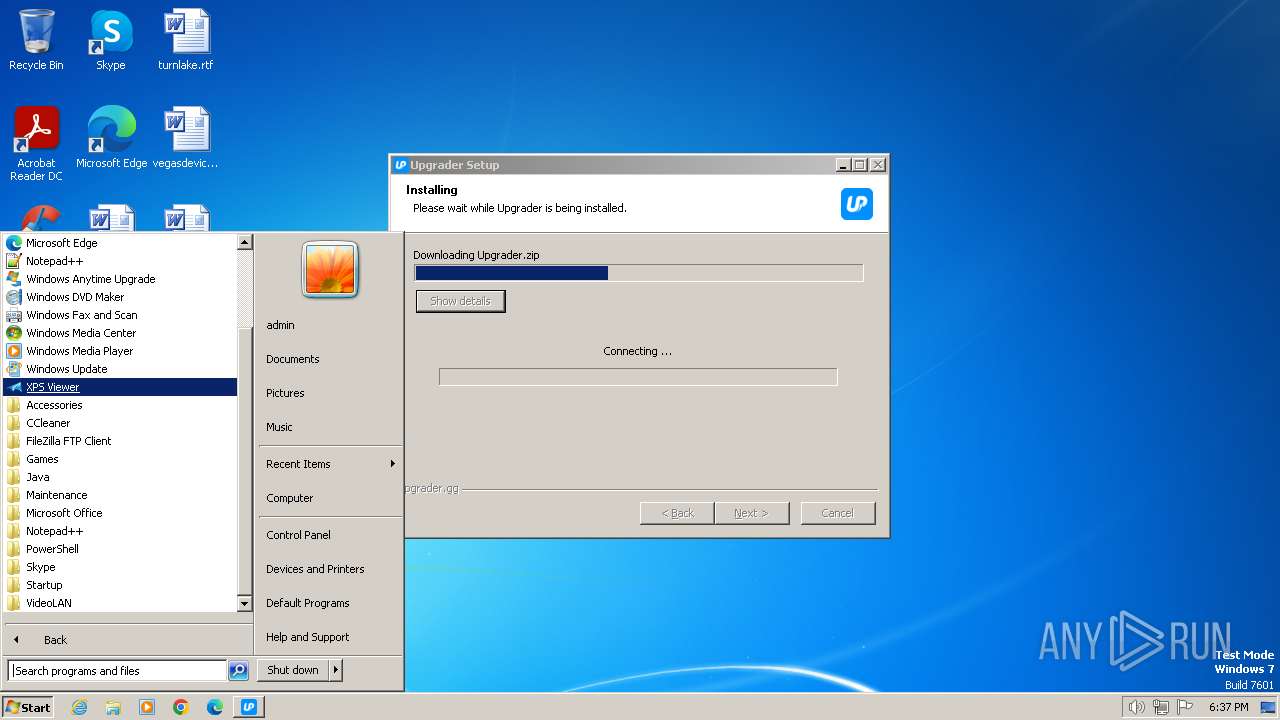
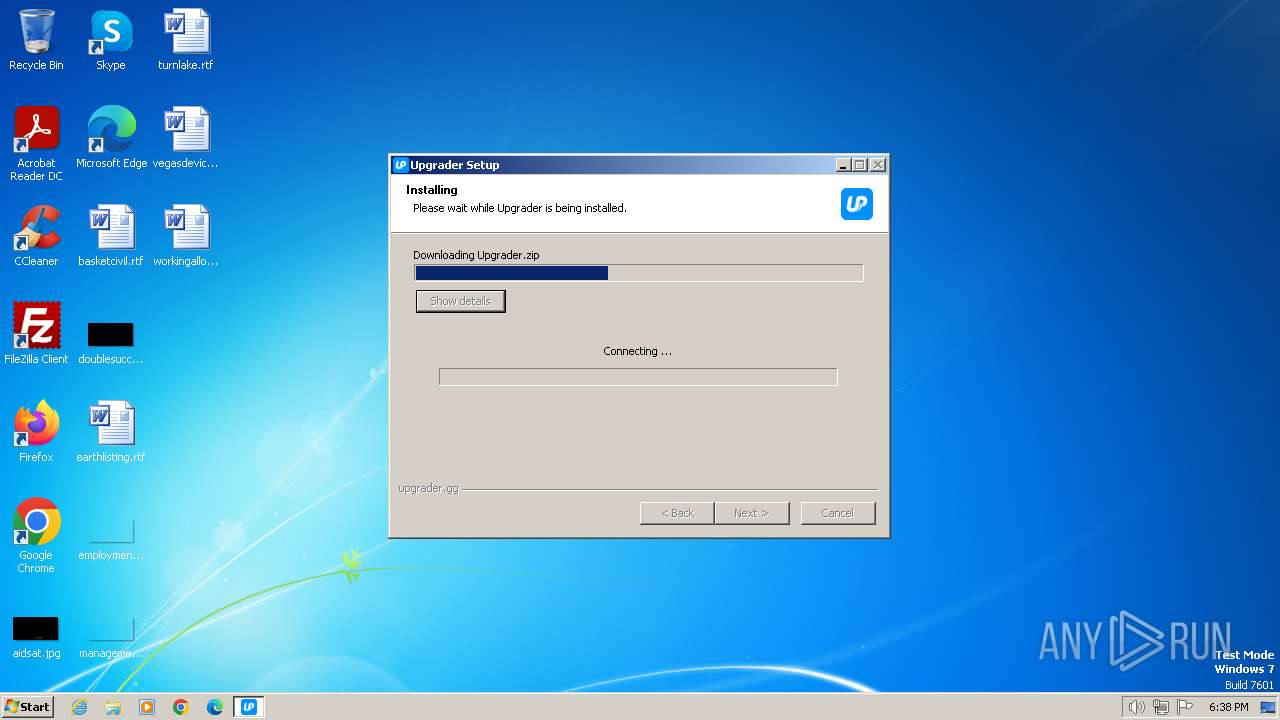
| File name: | Upgrader.exe |
| Full analysis: | https://app.any.run/tasks/adf5ef2e-4ecd-48ef-9fdb-aab2054531c1 |
| Verdict: | Malicious activity |
| Analysis date: | March 05, 2024, 18:36:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 4D3896E7169301C87D7A0097763ACF62 |
| SHA1: | 9668EE942B6F55D1165C8D39443F64A279203B87 |
| SHA256: | 56D1A4FFE025C62C0426C2053117F0ED36E5EE8D49E5BCEE71B04DC2F8365321 |
| SSDEEP: | 24576:SYXTXw5h6V1m6RxrNzPqi7whfzAglqLhSp5l+HaWVB2z8Ajds:SYXTXwn6V1m6RxrNzPqi7whfzAglqLhx |
MALICIOUS
Drops the executable file immediately after the start
- Upgrader.exe (PID: 2848)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- Upgrader.exe (PID: 2848)
The process creates files with name similar to system file names
- Upgrader.exe (PID: 2848)
Executable content was dropped or overwritten
- Upgrader.exe (PID: 2848)
Reads security settings of Internet Explorer
- Upgrader.exe (PID: 2848)
Reads the Internet Settings
- Upgrader.exe (PID: 2848)
INFO
Checks supported languages
- Upgrader.exe (PID: 2848)
Reads the computer name
- Upgrader.exe (PID: 2848)
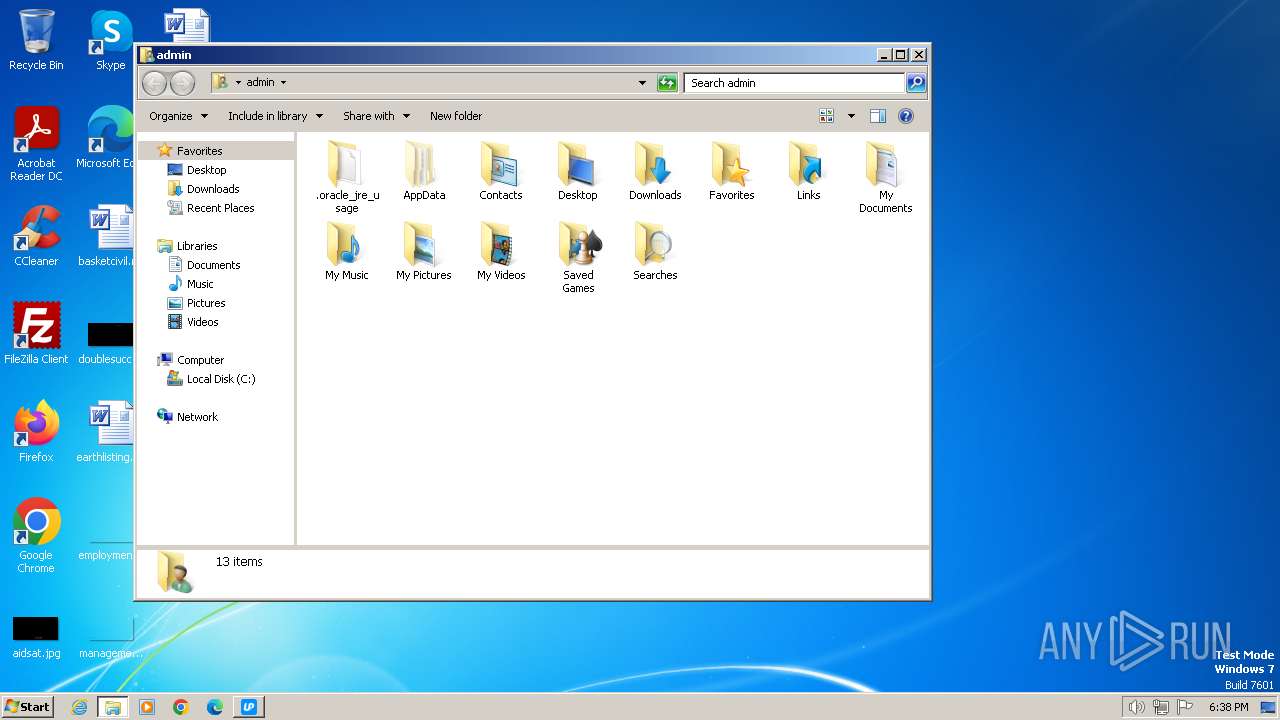
Creates files or folders in the user directory
- Upgrader.exe (PID: 2848)
Checks proxy server information
- Upgrader.exe (PID: 2848)
Create files in a temporary directory
- Upgrader.exe (PID: 2848)
Reads the machine GUID from the registry
- Upgrader.exe (PID: 2848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:57:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 186880 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x352d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 1.0.0.0 |
| LegalCopyright: | - |
Total processes
42
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2848 | "C:\Users\admin\AppData\Local\Temp\Upgrader.exe" | C:\Users\admin\AppData\Local\Temp\Upgrader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4052 | "C:\Users\admin\AppData\Local\Temp\Upgrader.exe" | C:\Users\admin\AppData\Local\Temp\Upgrader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
2 921
Read events
2 895
Write events
20
Delete events
6
Modification events
| (PID) Process: | (2848) Upgrader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2848) Upgrader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (2848) Upgrader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (2848) Upgrader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (2848) Upgrader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (2848) Upgrader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005C010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2848) Upgrader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2848) Upgrader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2848) Upgrader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2848) Upgrader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
8
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2848 | Upgrader.exe | C:\Users\admin\AppData\Local\Upgrader\uninstall.exe | executable | |
MD5:FAB7BE1A4B04F914D3A2C9D0F88E39EA | SHA256:CB25622E62CD86EAA8605718601AC98398EE0909D563A8DCE407F8632483FF1D | |||
| 2848 | Upgrader.exe | C:\Users\admin\AppData\Local\Temp\nsaF473.tmp\System.dll | executable | |
MD5:CFF85C549D536F651D4FB8387F1976F2 | SHA256:8DC562CDA7217A3A52DB898243DE3E2ED68B80E62DDCB8619545ED0B4E7F65A8 | |||
| 2848 | Upgrader.exe | C:\Users\admin\AppData\Local\Temp\nsaF473.tmp\StartMenu.dll | executable | |
MD5:D070F3275DF715BF3708BEFF2C6C307D | SHA256:42DD4DDA3249A94E32E20F76EAFFAE784A5475ED00C60EF0197C8A2C1CCD2FB7 | |||
| 2848 | Upgrader.exe | C:\Users\admin\AppData\Local\Upgrader\placeholder.txt | text | |
MD5:6A99C575AB87F8C7D1ED1E52E7E349CE | SHA256:4097889236A2AF26C293033FEB964C4CF118C0224E0D063FEC0A89E9D0569EF2 | |||
| 2848 | Upgrader.exe | C:\Users\admin\AppData\Local\Temp\nsaF473.tmp\INetC.dll | executable | |
MD5:29B52AA747452B26F36F68B969DFB357 | SHA256:3D6B7BCDA91463304B1B634A0B3598E2C77E36D75027A4F415AA0A87F8480A40 | |||
| 2848 | Upgrader.exe | C:\Users\admin\AppData\Local\Temp\nsaF473.tmp\nsDialogs.dll | executable | |
MD5:6C3F8C94D0727894D706940A8A980543 | SHA256:56B96ADD1978B1ABBA286F7F8982B0EFBE007D4A48B3DED6A4D408E01D753FE2 | |||
| 2848 | Upgrader.exe | C:\Users\admin\AppData\Local\Temp\nsaF473.tmp\LangDLL.dll | executable | |
MD5:68B287F4067BA013E34A1339AFDB1EA8 | SHA256:18E8B40BA22C7A1687BD16E8D585380BC2773FFF5002D7D67E9485FCC0C51026 | |||
| 2848 | Upgrader.exe | C:\Users\admin\AppData\Local\Temp\nsaF473.tmp\ZipDLL.dll | executable | |
MD5:348EF6C04882C7EB661AC8BE5A231716 | SHA256:A806A329E2E96CFDB92674F7881F3DCA06A0544E84915969B23E5AB2E2C7829B | |||
| 2848 | Upgrader.exe | C:\Users\admin\AppData\Local\Temp\nsaF473.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 2848 | Upgrader.exe | C:\Users\admin\AppData\Local\Temp\nsaF473.tmp\KillProcDLL.dll | executable | |
MD5:52D1725BB60D633F3317843556B6C4ED | SHA256:CE1A1FA055BA074885EC836D19F61FFDFECC294BF30D4DDD95E73C356948AF86 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
7
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2848 | Upgrader.exe | 34.118.126.199:443 | upgrader.gg | GOOGLE-CLOUD-PLATFORM | PL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
upgrader.gg |
| unknown |