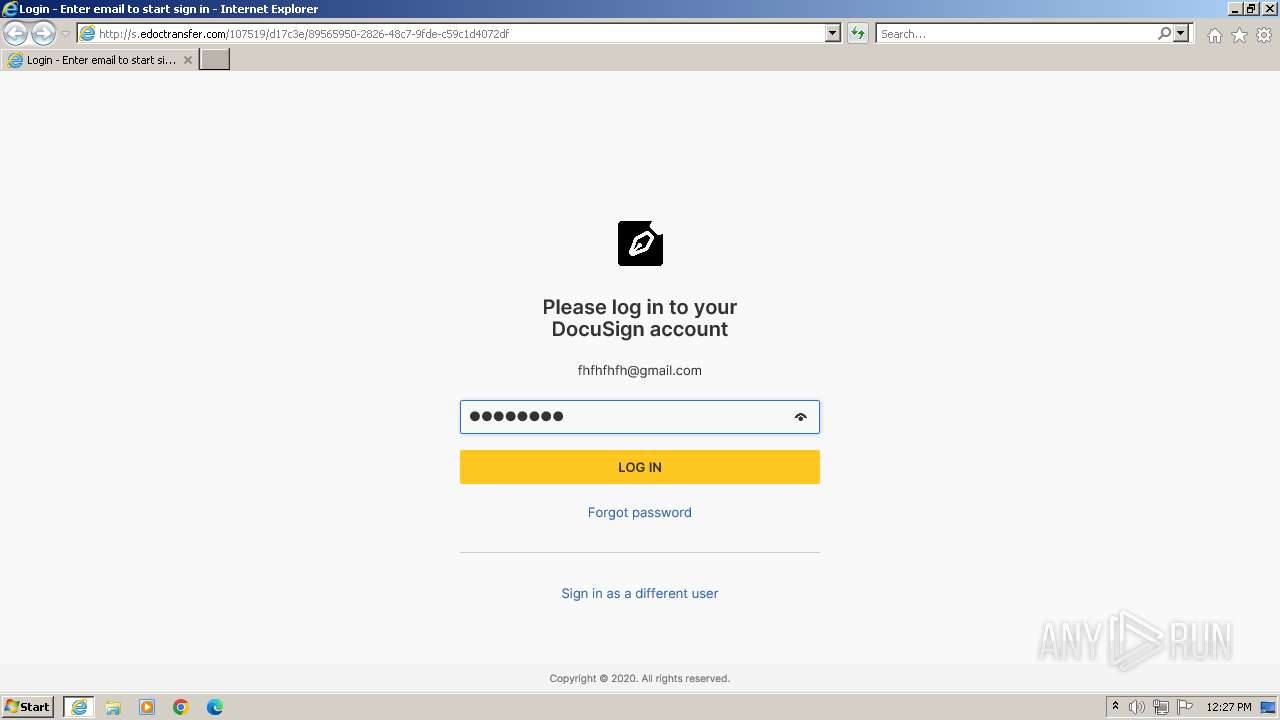
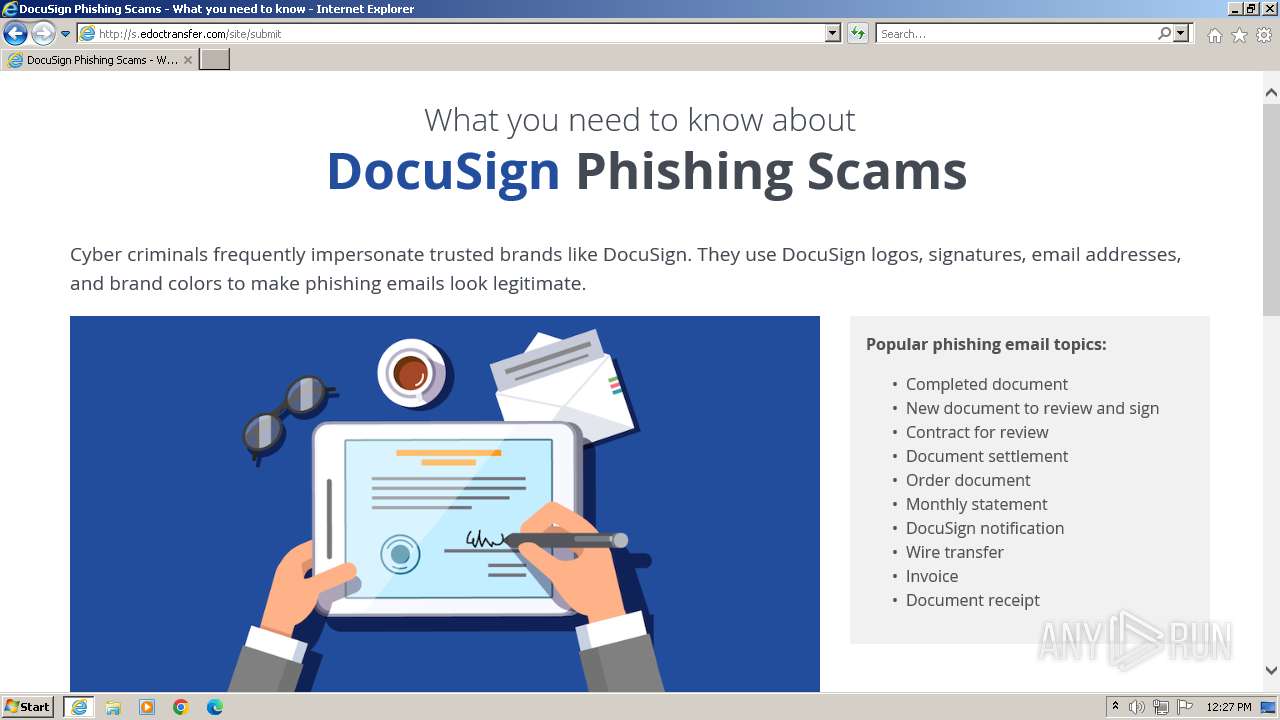
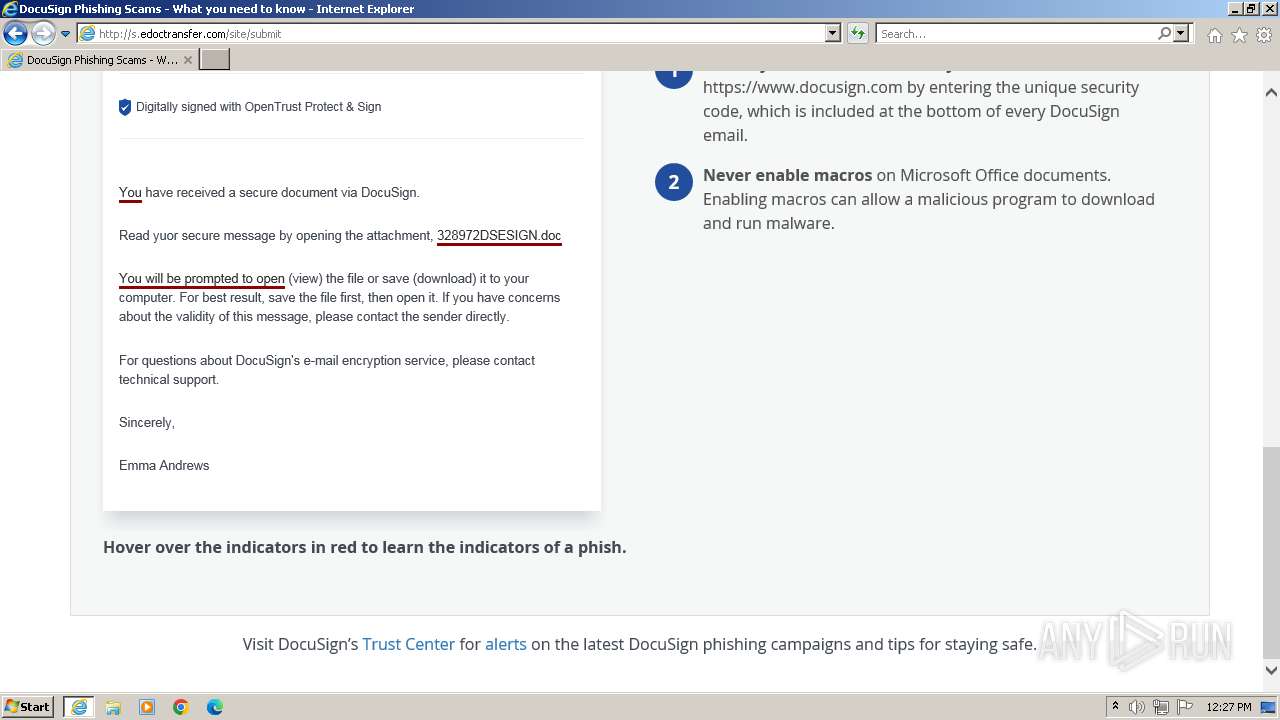
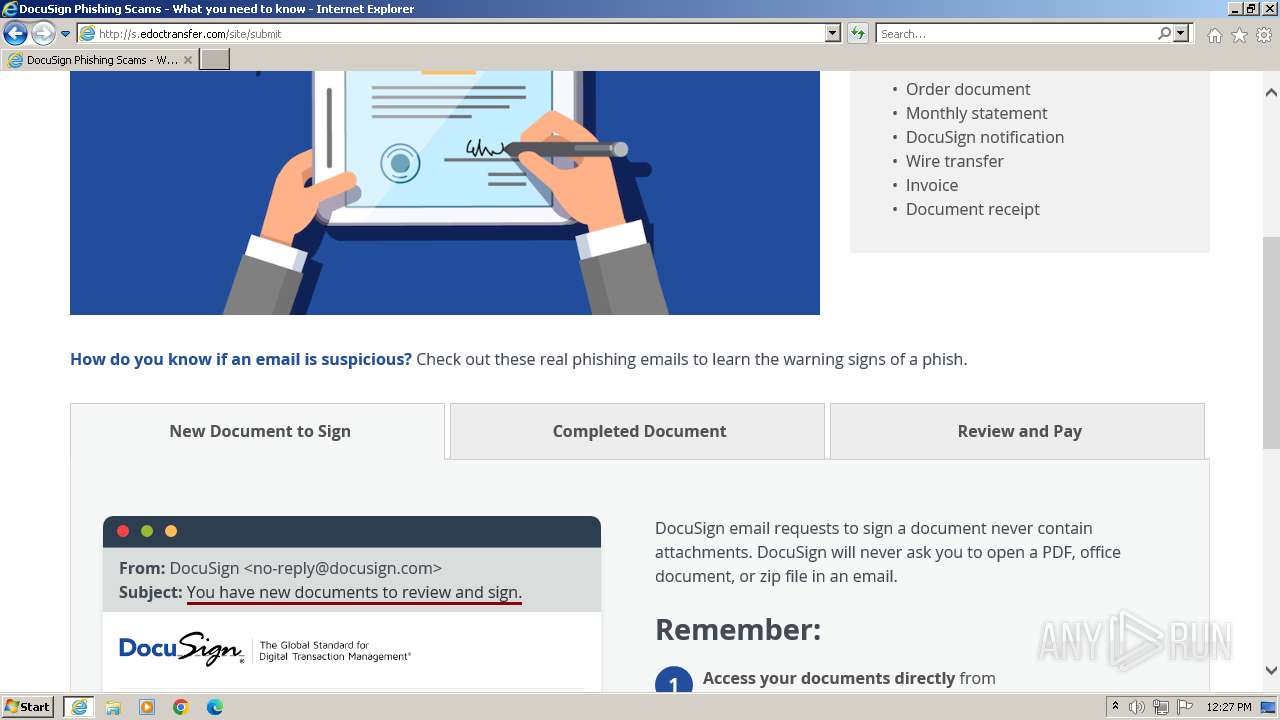
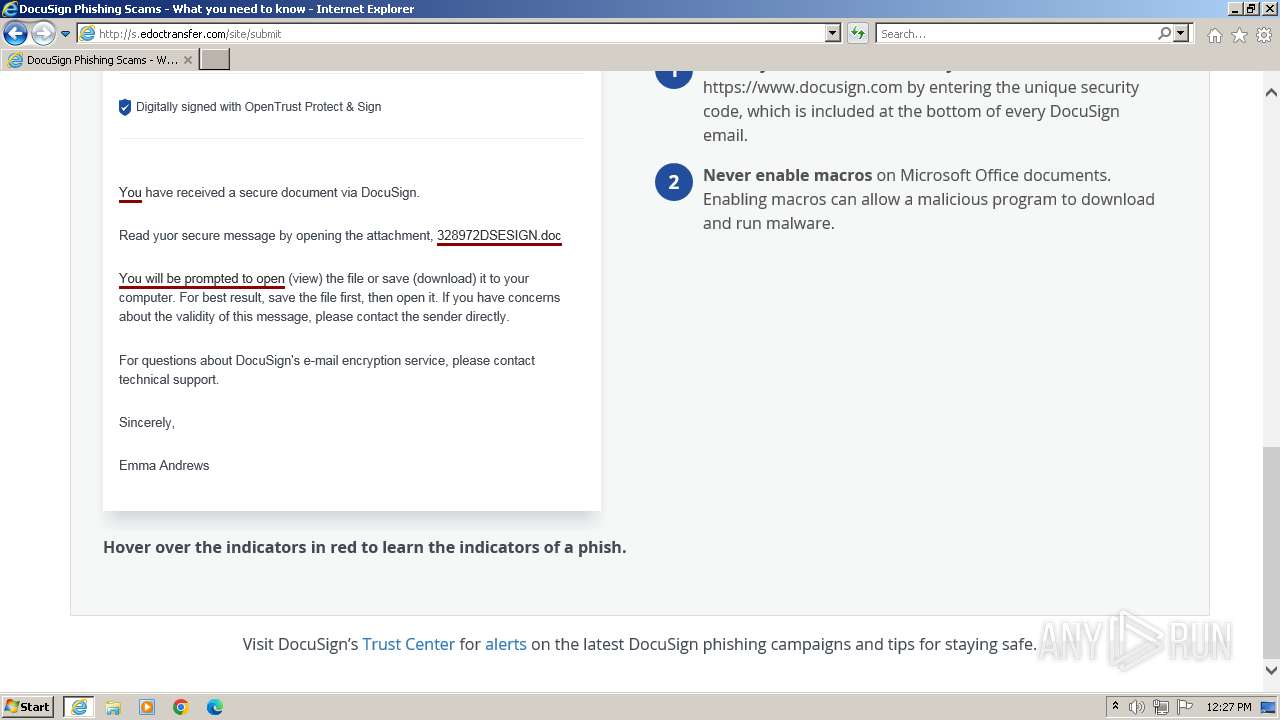
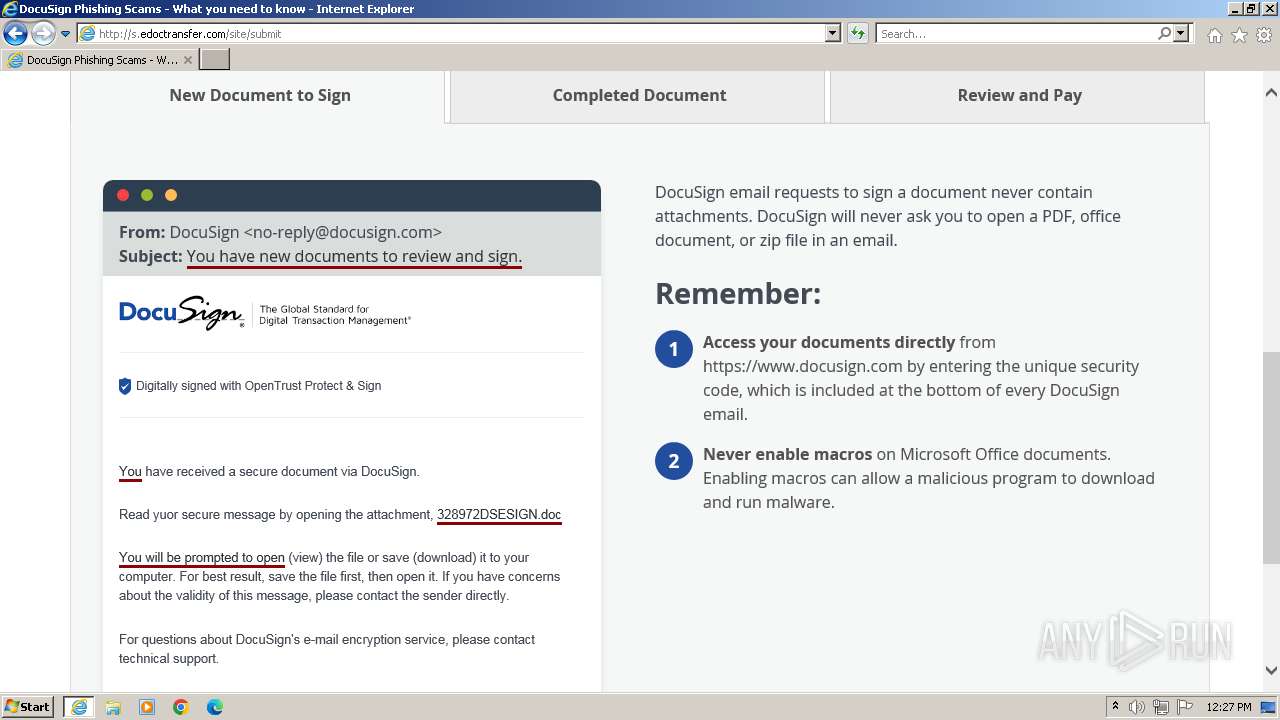
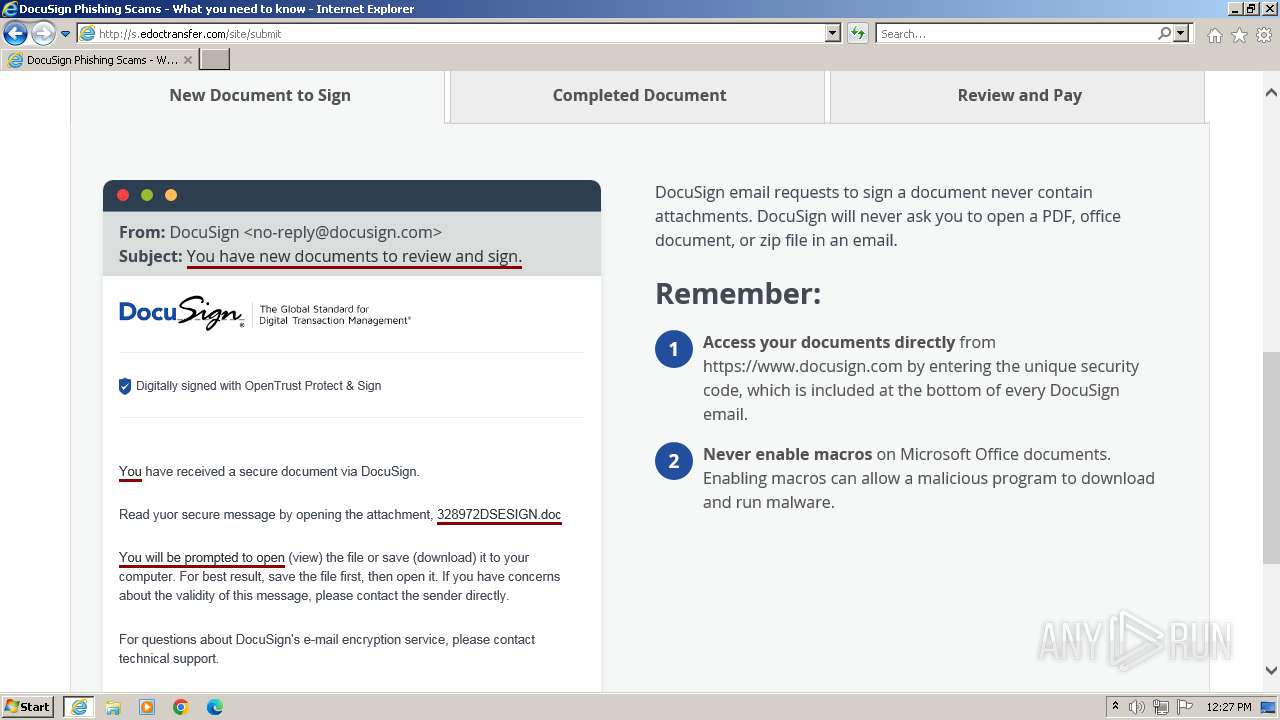
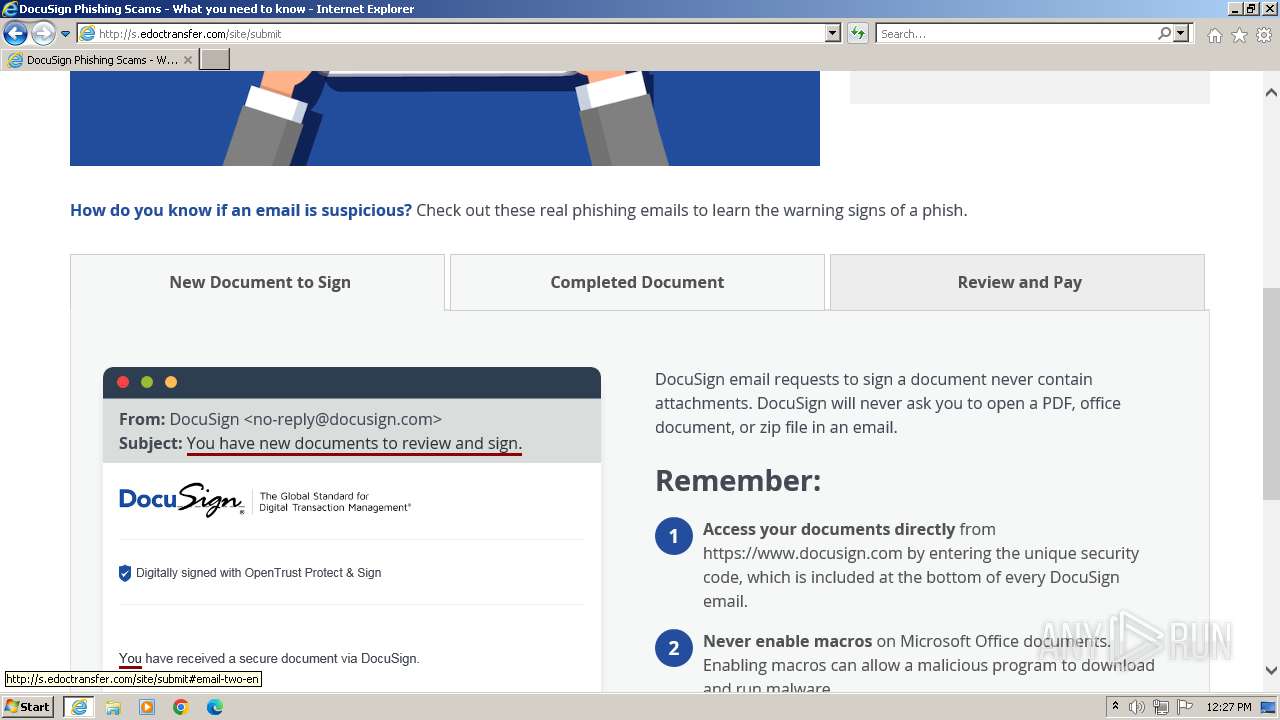
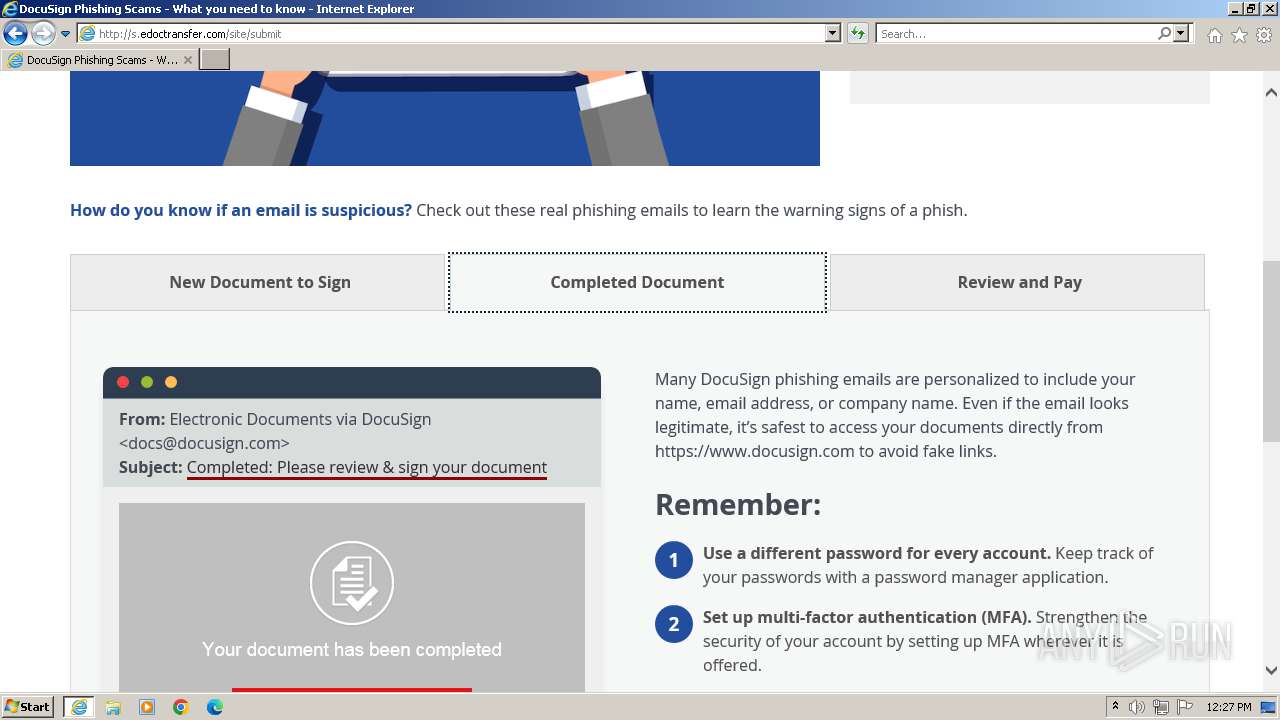
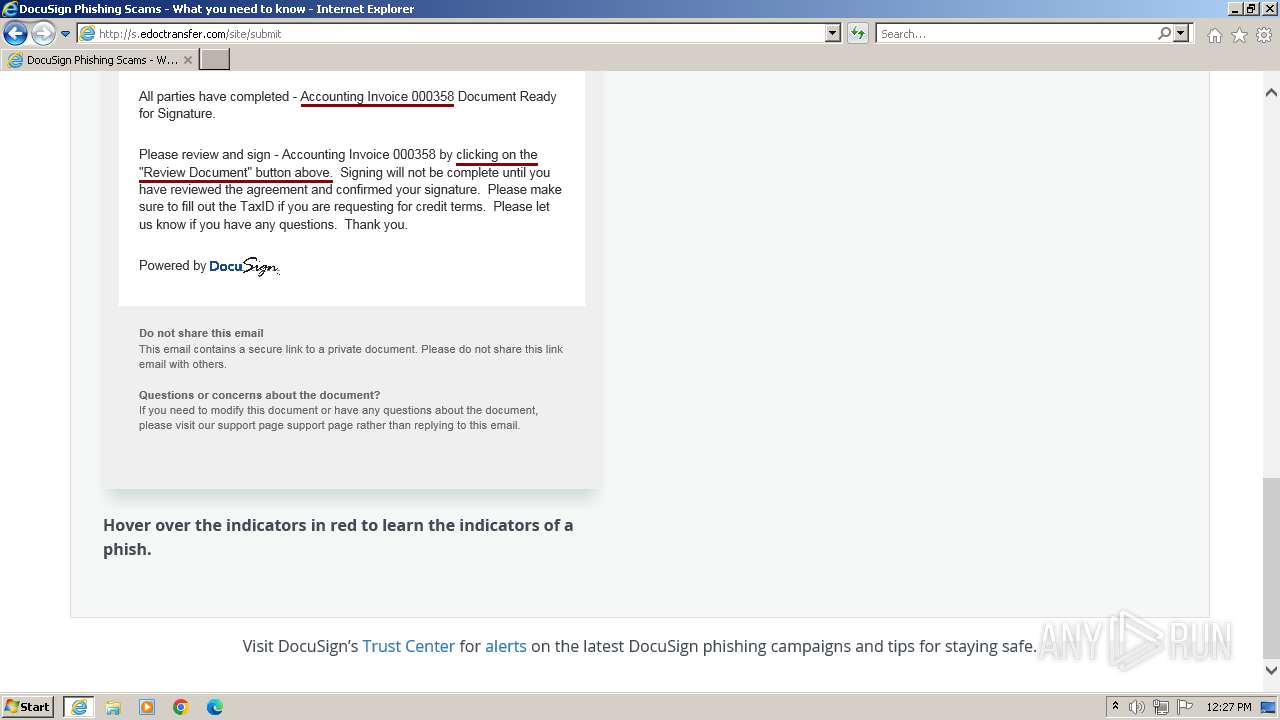
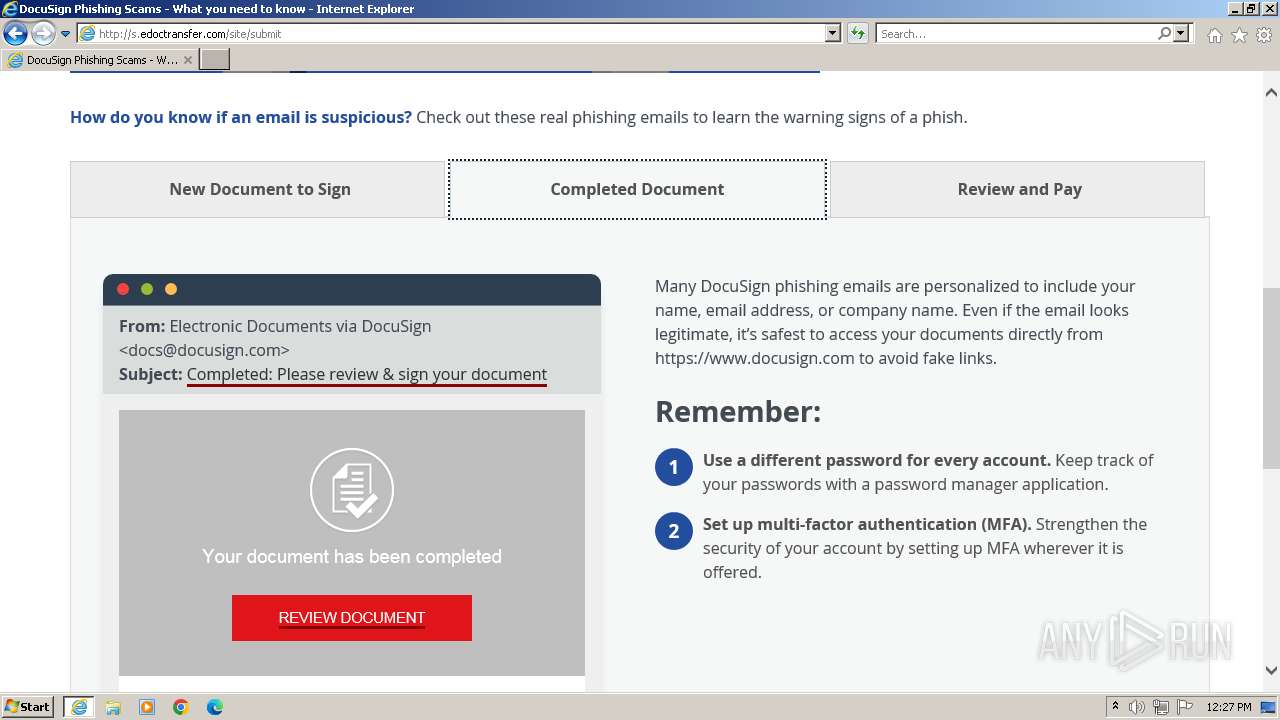
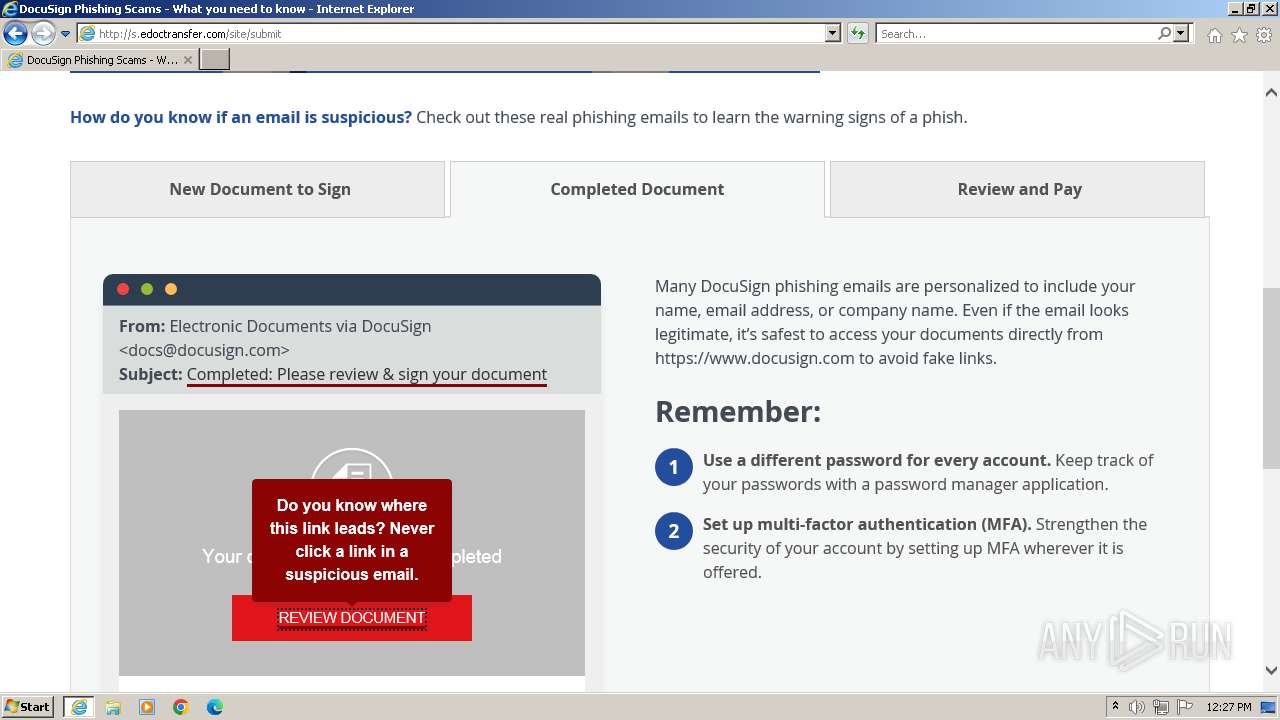
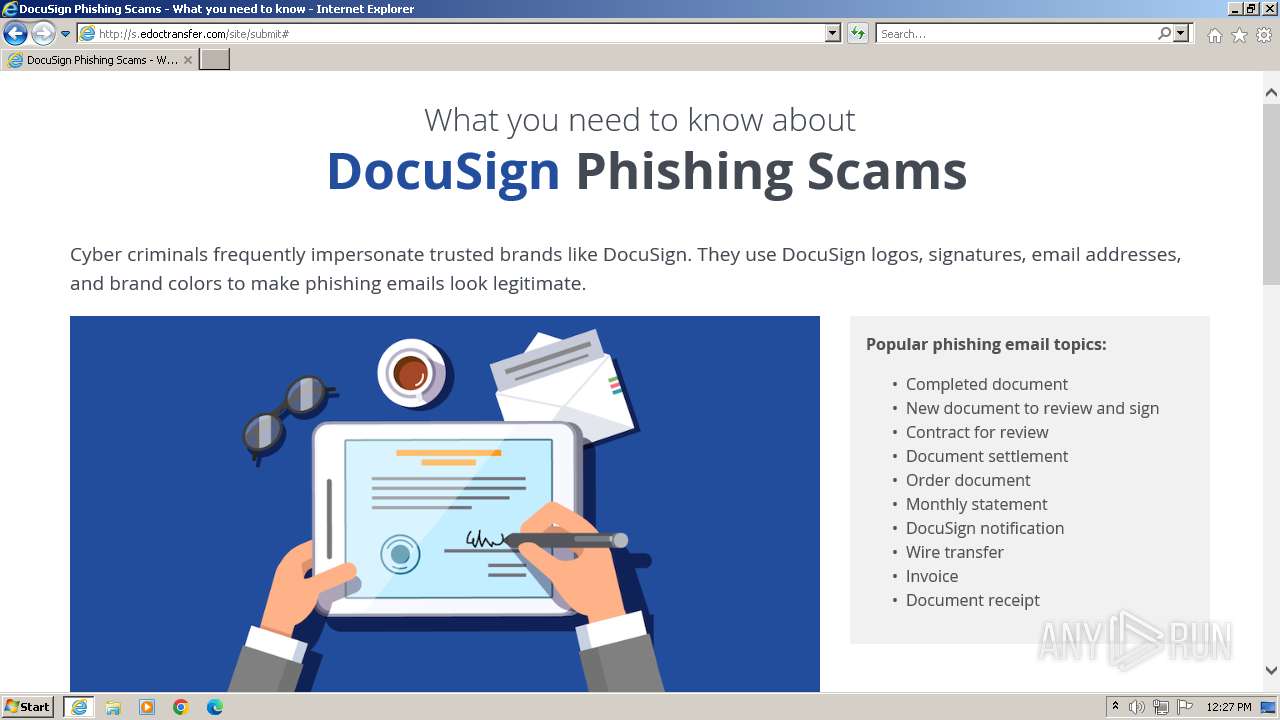
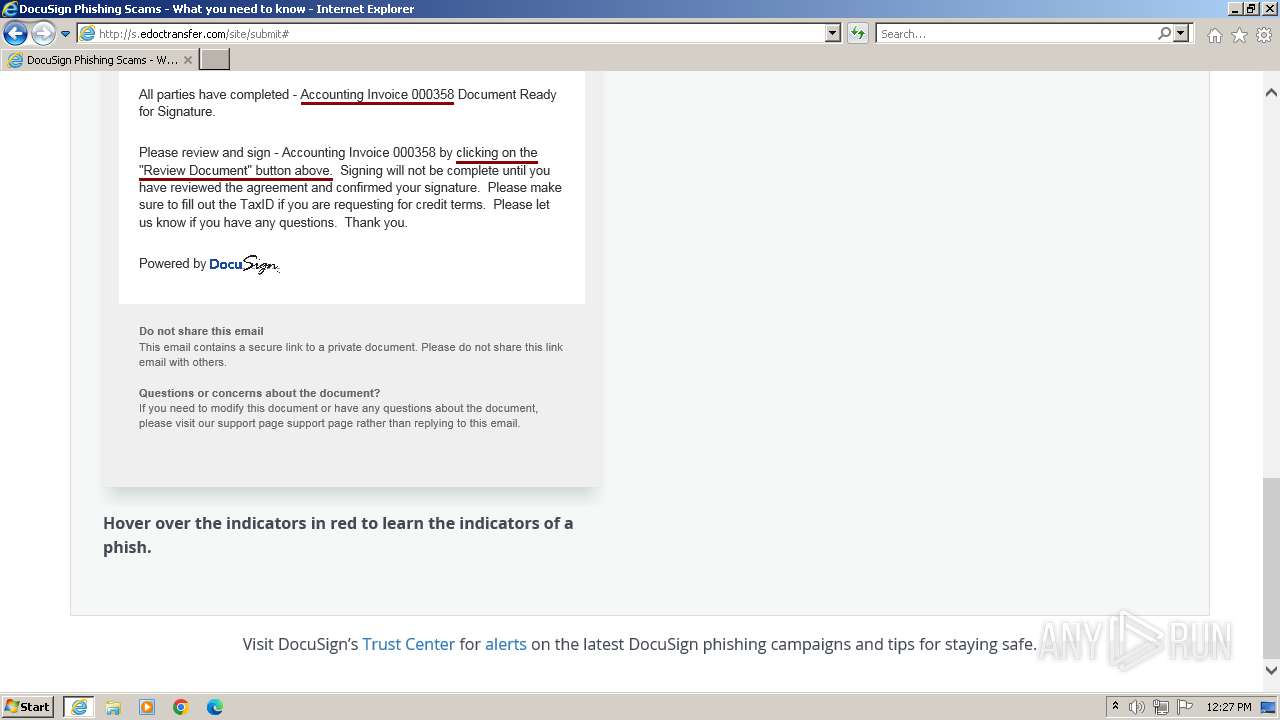
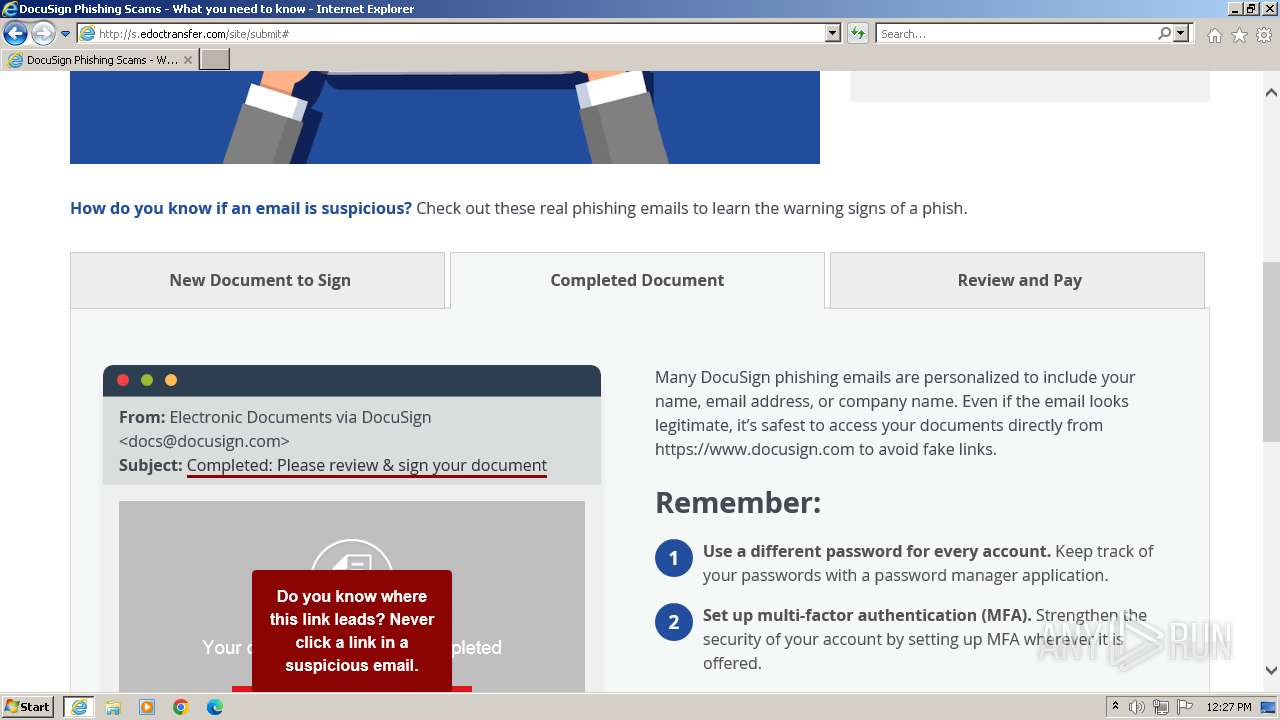
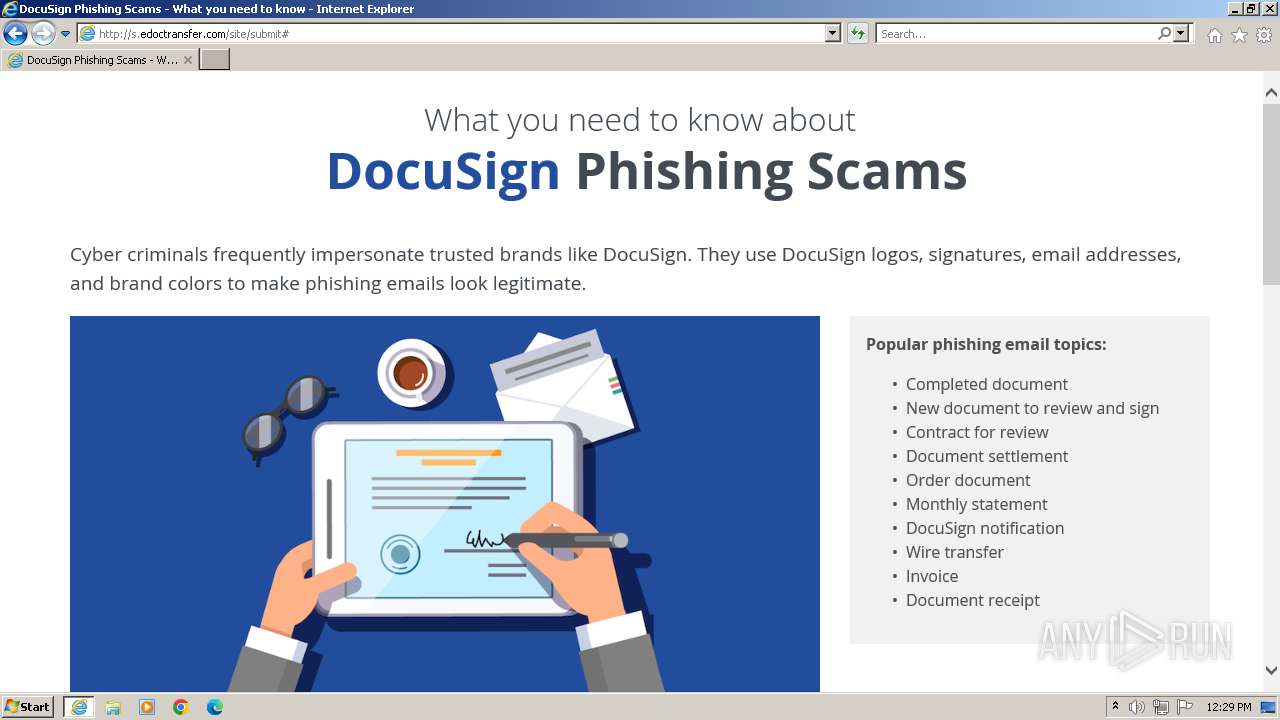
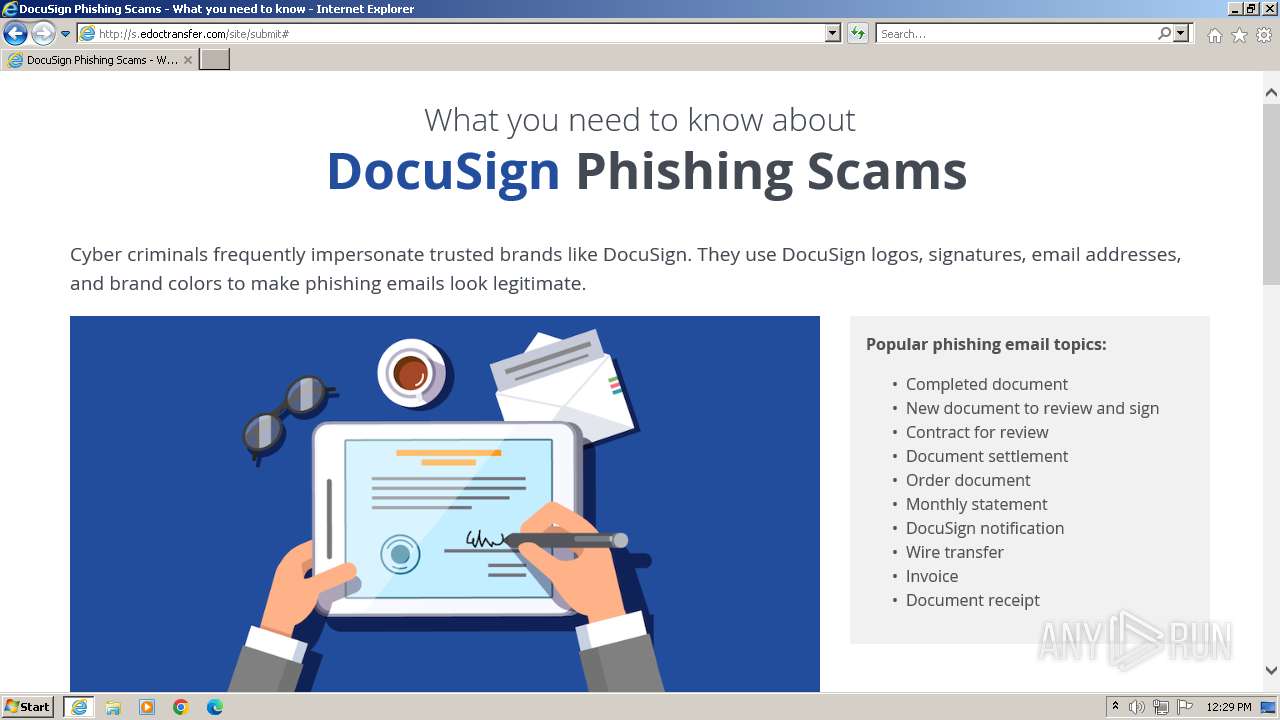
| URL: | http://s.edoctransfer.com/107519/d17c3e/89565950-2826-48c7-9fde-c59c1d4072df |
| Full analysis: | https://app.any.run/tasks/756c31e7-8e5d-441b-b23e-3169f6c2f32b |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2023, 11:26:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| SHA1: | 7BB35EE3532CD5A2B10EF75034111B51895F5DE8 |
| SHA256: | 56C9FC74A4E7FDD95489AB7A972E01A8922BBB1082DD6F131528F2D4DDEDC059 |
| SSDEEP: | 3:N1KN08GxELWXKcjUckALQlDsE7cccDn:C4JoILSIMccyn |
MALICIOUS
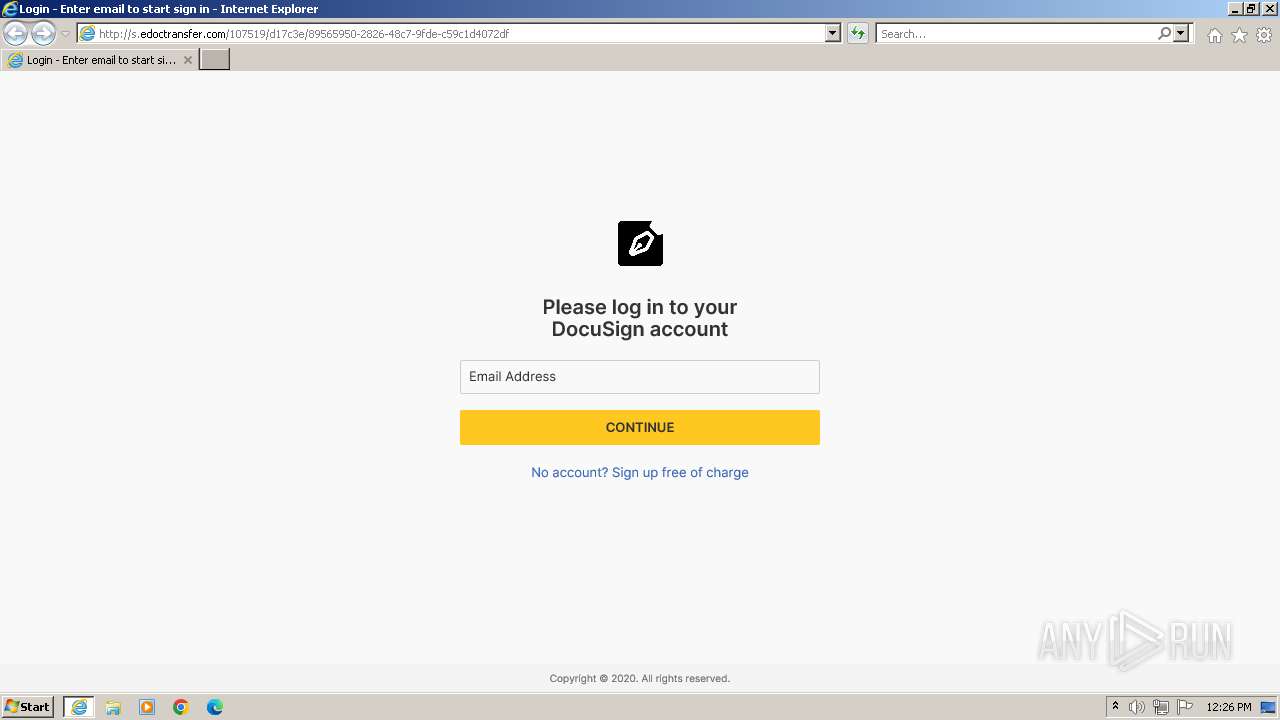
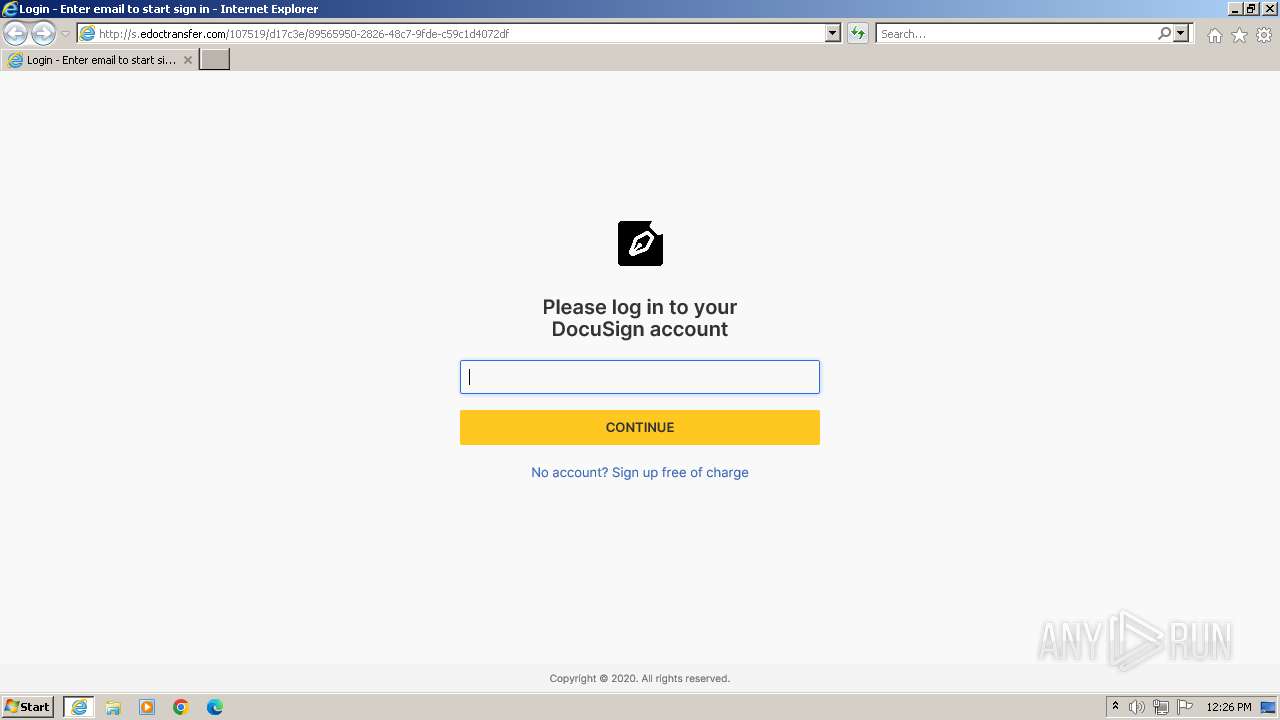
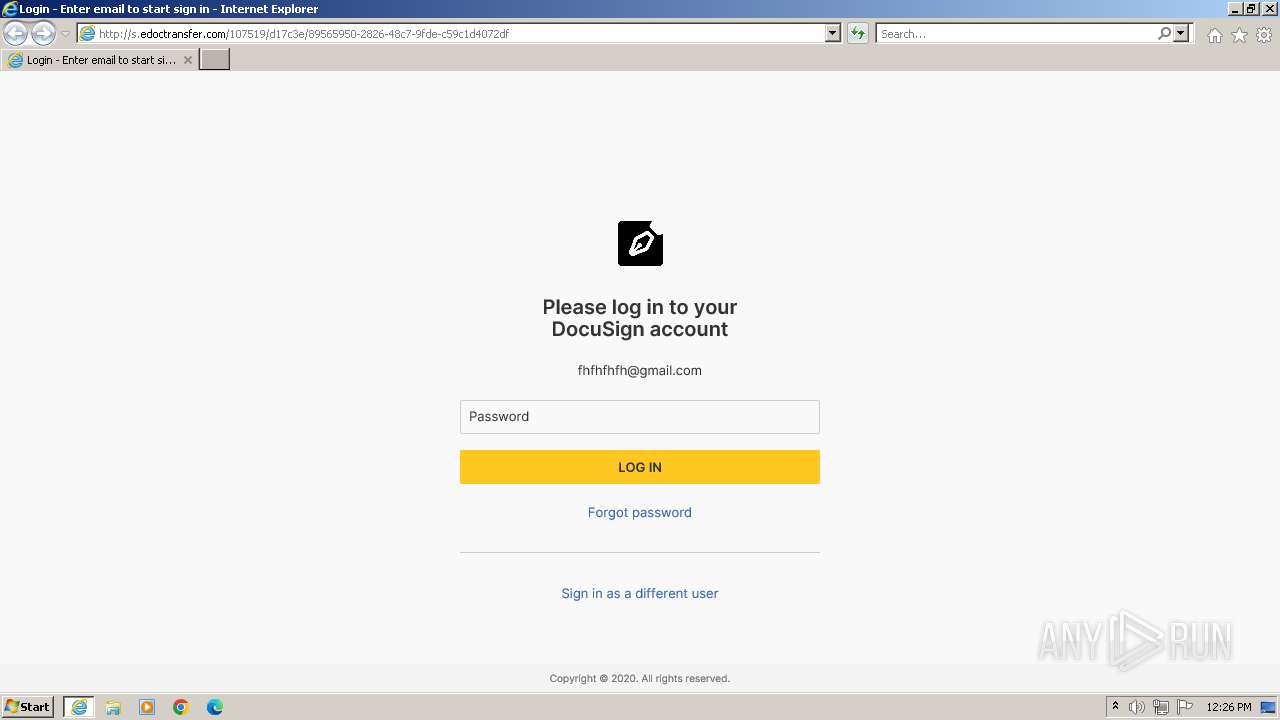
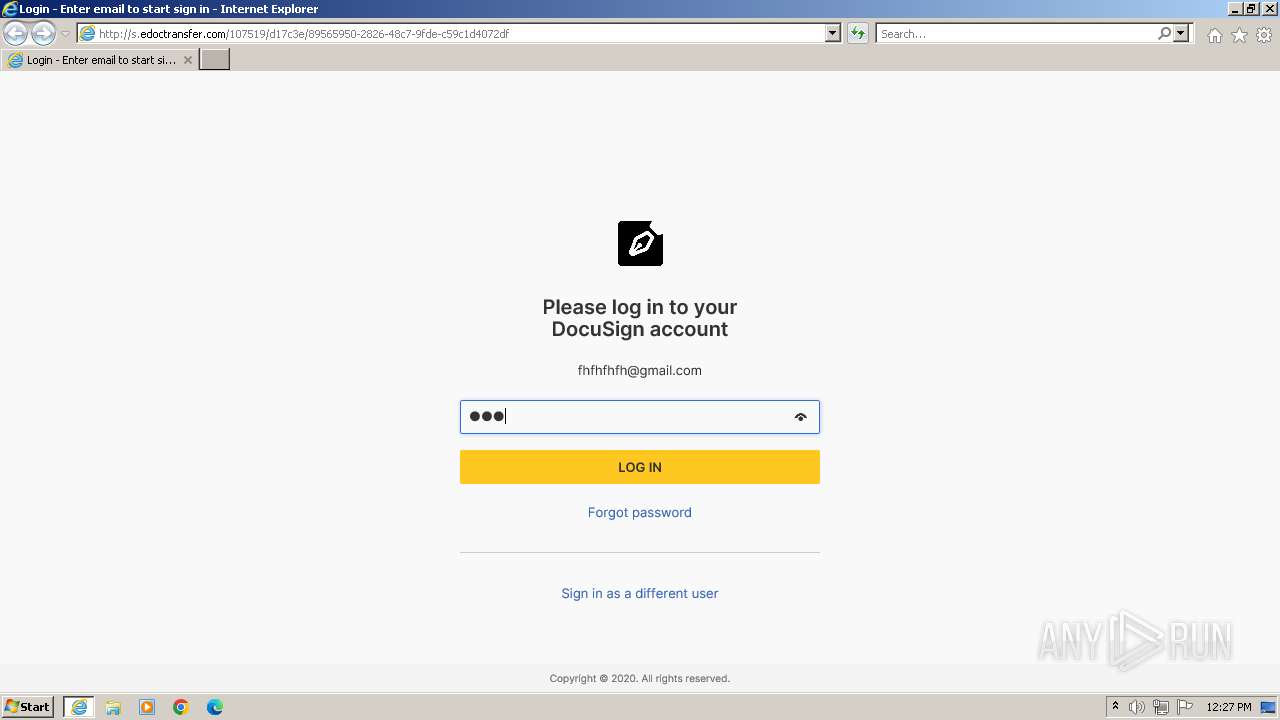
PHISHING was detected
- iexplore.exe (PID: 3452)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
2
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3452 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3636 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3636 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://s.edoctransfer.com/107519/d17c3e/89565950-2826-48c7-9fde-c59c1d4072df" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
21 724
Read events
21 656
Write events
68
Delete events
0
Modification events
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3636) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
33
Text files
63
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3452 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\docusign-landing[1].css | text | |
MD5:450A6D81FE654256B0E5BC99E050017D | SHA256:EE458231D91947AD91B90F917BADA69A609135349D672E179735F61DAF74F0E2 | |||
| 3452 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\warning-icon[1].png | image | |
MD5:06D410631F5ADC2439153921B0E9C0B3 | SHA256:9E1A544AEA8AFC80CC38BF0EC5232E0E7E278B53C187D6BE18312AA760266B26 | |||
| 3452 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\bootstrap-landings[1].css | text | |
MD5:526B740DCA32600A2E6E8F1B25DB6FF8 | SHA256:24CA84ED70DD60B91A40988E518DABC7BC6A9958AF3070F8ED366FC87661CC49 | |||
| 3452 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\89565950-2826-48c7-9fde-c59c1d4072df[1].htm | html | |
MD5:247485AF900DB914CDF2414832A3E8AC | SHA256:FFE1C3B8F7918CFB00126DDE95CEB7A8CC8045A150E62F6A4A098219E79B9FEC | |||
| 3452 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:81847486BCEEE62BAD6F8F74F80F3FEF | SHA256:AE84E8D58436FCB8E42FA7EE2D2510CA491E370DEAED7C19CE777DAA0764B294 | |||
| 3452 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\pen-icon-v2[1].png | image | |
MD5:1580339B73152A853DE8ED65181F1A3A | SHA256:7487746288F449F2A2BDB84FDEE991B1D0CF3A7B7F6D9D86040866380E4731EA | |||
| 3452 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\jquery-latest.min[1].js | text | |
MD5:220AFD743D9E9643852E31A135A9F3AE | SHA256:0925E8AD7BD971391A8B1E98BE8E87A6971919EB5B60C196485941C3C1DF089A | |||
| 3452 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:1E14EED7510CEAB13EB3B5C1782133E1 | SHA256:8D3047758F242B87E988986985B08604DA448F5625E9868B8100216A0E556095 | |||
| 3452 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3452 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:2E02B9E1CF9A378214F0901D91D813BE | SHA256:C938875CA8D3ECADB558BDD0612FCBEBA5B2AD0A211498DCBE8E421ABDEC22CB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
68
DNS requests
19
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3636 | iexplore.exe | GET | 404 | 54.83.101.48:80 | http://s.edoctransfer.com/favicon.ico | unknown | — | — | unknown |
3452 | iexplore.exe | GET | 200 | 54.83.101.48:80 | http://s.edoctransfer.com/system/content_images/uploads/093/e54/62-/original/pen-icon-v2.png | unknown | image | 5.88 Kb | unknown |
3452 | iexplore.exe | GET | 200 | 54.83.101.48:80 | http://s.edoctransfer.com/system/content_files/uploads/5b8/ee7/1e-/original/jquery-latest.min.js | unknown | text | 29.9 Kb | unknown |
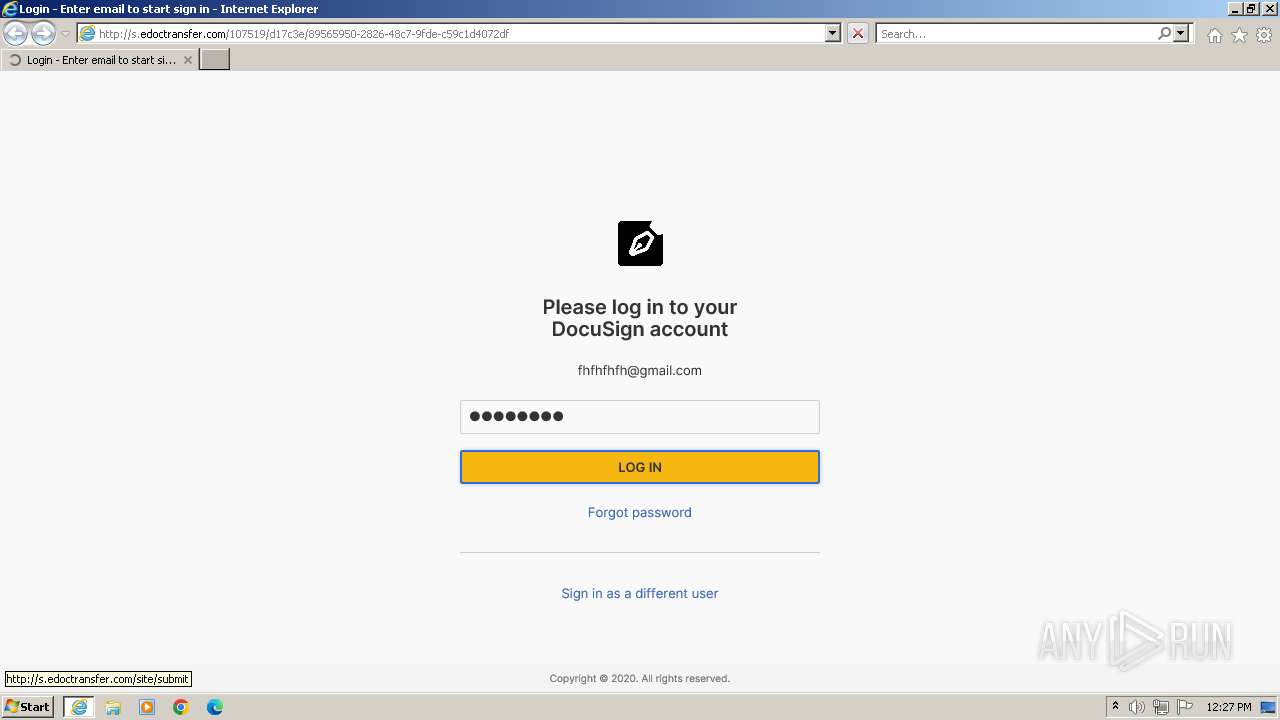
3452 | iexplore.exe | POST | — | 54.83.101.48:80 | http://s.edoctransfer.com/site/submit | unknown | — | — | unknown |
3452 | iexplore.exe | GET | 200 | 172.217.169.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDLYsQ7yv2LMwmxOu34tlfG | unknown | binary | 472 b | unknown |
3452 | iexplore.exe | GET | 200 | 54.83.101.48:80 | http://s.edoctransfer.com/system/content_images/uploads/b1b/8b7/a8-/original/warning-icon.png | unknown | image | 250 b | unknown |
3452 | iexplore.exe | GET | 200 | 67.27.157.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?760b6ca7d02878db | unknown | compressed | 4.66 Kb | unknown |
3452 | iexplore.exe | GET | 200 | 54.83.101.48:80 | http://s.edoctransfer.com/107519/d17c3e/89565950-2826-48c7-9fde-c59c1d4072df | unknown | html | 3.21 Kb | unknown |
3452 | iexplore.exe | GET | 200 | 172.217.169.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQC%2BZny5ZpKT1Qo7Jl2xxLWu | unknown | binary | 472 b | unknown |
3452 | iexplore.exe | GET | 200 | 172.217.169.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEBwpDYp%2BzHCUEI%2F24pyO%2BvY%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3452 | iexplore.exe | 54.83.101.48:80 | — | AMAZON-AES | US | unknown |
3452 | iexplore.exe | 172.217.20.72:443 | www.googletagmanager.com | GOOGLE | US | whitelisted |
3452 | iexplore.exe | 142.251.140.42:443 | fonts.googleapis.com | GOOGLE | US | unknown |
3452 | iexplore.exe | 67.27.157.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3452 | iexplore.exe | 172.217.169.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3452 | iexplore.exe | 142.251.140.3:443 | fonts.gstatic.com | GOOGLE | US | unknown |
3452 | iexplore.exe | 142.251.140.78:443 | www.google-analytics.com | GOOGLE | US | unknown |
3452 | iexplore.exe | 142.250.145.154:443 | stats.g.doubleclick.net | GOOGLE | US | unknown |
3452 | iexplore.exe | 216.239.34.36:443 | region1.google-analytics.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.googletagmanager.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
region1.google-analytics.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3452 | iexplore.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspicious sending of an email address as an unencrypted POST request |