| File name: | cache.exe |
| Full analysis: | https://app.any.run/tasks/fb143b36-d011-456a-981c-09aad66401ad |
| Verdict: | Malicious activity |
| Analysis date: | May 02, 2024, 19:53:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | BF78AC2C1076B63B14BF63F93266DAAF |
| SHA1: | C5BA1F3953D3D6361F8B2A4FCEB2BE3BDC617359 |
| SHA256: | 56A4EBDE6F5146038418753B4374F02D5B0B1DC590103B96012A98A446F2AC74 |
| SSDEEP: | 24576:0QbPRgBoCss4ROxLeW8pe2fQg41fSvIc+rW0abJ077n:0QTRgBoCss4ROxKW8pe2og41fSgc+rWe |
MALICIOUS
Drops the executable file immediately after the start
- cache.exe (PID: 3968)
- gegcazmfdfb.exe (PID: 4028)
- gegcazmfdfb.exe (PID: 2224)
UAC/LUA settings modification
- gegcazmfdfb.exe (PID: 4028)
- ccors.exe (PID: 4064)
- ccors.exe (PID: 4072)
- regedit.exe (PID: 312)
- gegcazmfdfb.exe (PID: 2224)
- ccors.exe (PID: 2364)
- ccors.exe (PID: 2356)
- gegcazmfdfb.exe (PID: 3252)
Changes the login/logoff helper path in the registry
- gegcazmfdfb.exe (PID: 4028)
- ccors.exe (PID: 4064)
- ccors.exe (PID: 4072)
- ccors.exe (PID: 2356)
- gegcazmfdfb.exe (PID: 2224)
- ccors.exe (PID: 2364)
- gegcazmfdfb.exe (PID: 3252)
Changes appearance of the Explorer extensions
- gegcazmfdfb.exe (PID: 4028)
- ccors.exe (PID: 4064)
- ccors.exe (PID: 4072)
- gegcazmfdfb.exe (PID: 2224)
- ccors.exe (PID: 2356)
- ccors.exe (PID: 2364)
Changes the autorun value in the registry
- gegcazmfdfb.exe (PID: 4028)
- ccors.exe (PID: 4064)
- ccors.exe (PID: 4072)
- gegcazmfdfb.exe (PID: 2224)
- ccors.exe (PID: 2364)
- ccors.exe (PID: 2356)
- gegcazmfdfb.exe (PID: 3252)
Creates a writable file in the system directory
- ccors.exe (PID: 4064)
- gegcazmfdfb.exe (PID: 2224)
- ccors.exe (PID: 2356)
Modify registry editing tools (regedit)
- ccors.exe (PID: 2356)
- ccors.exe (PID: 2364)
Deletes the SafeBoot registry key
- ccors.exe (PID: 2356)
SUSPICIOUS
Executable content was dropped or overwritten
- cache.exe (PID: 3968)
- gegcazmfdfb.exe (PID: 4028)
- gegcazmfdfb.exe (PID: 2224)
Reads security settings of Internet Explorer
- cache.exe (PID: 3968)
- gegcazmfdfb.exe (PID: 4028)
- ccors.exe (PID: 4064)
- csunebrmkfqykqyhevlng.exe (PID: 2128)
- zkhvhzkatjpszadh.exe (PID: 2144)
- gegcazmfdfb.exe (PID: 2224)
Reads the Internet Settings
- cache.exe (PID: 3968)
- gegcazmfdfb.exe (PID: 4028)
- sipnotify.exe (PID: 1632)
- ccors.exe (PID: 4064)
- csunebrmkfqykqyhevlng.exe (PID: 2128)
- zkhvhzkatjpszadh.exe (PID: 2144)
- gegcazmfdfb.exe (PID: 2224)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1632)
- ctfmon.exe (PID: 1548)
Reads settings of System Certificates
- sipnotify.exe (PID: 1632)
Reads the date of Windows installation
- pwsh.exe (PID: 2712)
Checks for external IP
- ccors.exe (PID: 2356)
Potential Corporate Privacy Violation
- ccors.exe (PID: 2356)
Suspected information leak
- ccors.exe (PID: 2356)
INFO
Create files in a temporary directory
- cache.exe (PID: 3968)
- gegcazmfdfb.exe (PID: 4028)
- ccors.exe (PID: 4064)
- gegcazmfdfb.exe (PID: 2224)
- ccors.exe (PID: 2356)
Reads the computer name
- cache.exe (PID: 3968)
- gegcazmfdfb.exe (PID: 4028)
- ccors.exe (PID: 4064)
- ccors.exe (PID: 4072)
- IMEKLMG.EXE (PID: 2100)
- csunebrmkfqykqyhevlng.exe (PID: 2128)
- IMEKLMG.EXE (PID: 2108)
- zkhvhzkatjpszadh.exe (PID: 2144)
- gegcazmfdfb.exe (PID: 2224)
- gegcazmfdfb.exe (PID: 2216)
- ccors.exe (PID: 2364)
- ccors.exe (PID: 2356)
- wmpnscfg.exe (PID: 2504)
- pwsh.exe (PID: 2712)
- wmpnscfg.exe (PID: 2532)
- gegcazmfdfb.exe (PID: 3252)
Checks supported languages
- cache.exe (PID: 3968)
- gegcazmfdfb.exe (PID: 4028)
- ccors.exe (PID: 4064)
- ccors.exe (PID: 4072)
- IMEKLMG.EXE (PID: 2100)
- IMEKLMG.EXE (PID: 2108)
- csunebrmkfqykqyhevlng.exe (PID: 2128)
- zkhvhzkatjpszadh.exe (PID: 2144)
- gegcazmfdfb.exe (PID: 2216)
- gegcazmfdfb.exe (PID: 2224)
- ccors.exe (PID: 2356)
- ccors.exe (PID: 2364)
- wmpnscfg.exe (PID: 2504)
- pwsh.exe (PID: 2712)
- wmpnscfg.exe (PID: 2532)
- gegcazmfdfb.exe (PID: 3252)
Process checks whether UAC notifications are on
- gegcazmfdfb.exe (PID: 4028)
- ccors.exe (PID: 4072)
- ccors.exe (PID: 4064)
- IMEKLMG.EXE (PID: 2100)
- IMEKLMG.EXE (PID: 2108)
- gegcazmfdfb.exe (PID: 2224)
- ccors.exe (PID: 2364)
- ccors.exe (PID: 2356)
- gegcazmfdfb.exe (PID: 3252)
Creates files or folders in the user directory
- ccors.exe (PID: 4064)
- ccors.exe (PID: 2356)
Manual execution by a user
- IMEKLMG.EXE (PID: 2100)
- IMEKLMG.EXE (PID: 2108)
- zkhvhzkatjpszadh.exe (PID: 2144)
- csunebrmkfqykqyhevlng.exe (PID: 2128)
- wmpnscfg.exe (PID: 2504)
- wmpnscfg.exe (PID: 2532)
- pwsh.exe (PID: 2712)
Reads the software policy settings
- sipnotify.exe (PID: 1632)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1632)
Creates files in the program directory
- ccors.exe (PID: 2356)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:03:19 17:31:48+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 20480 |
| InitializedDataSize: | 573440 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1ff5 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
103
Monitored processes
21
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
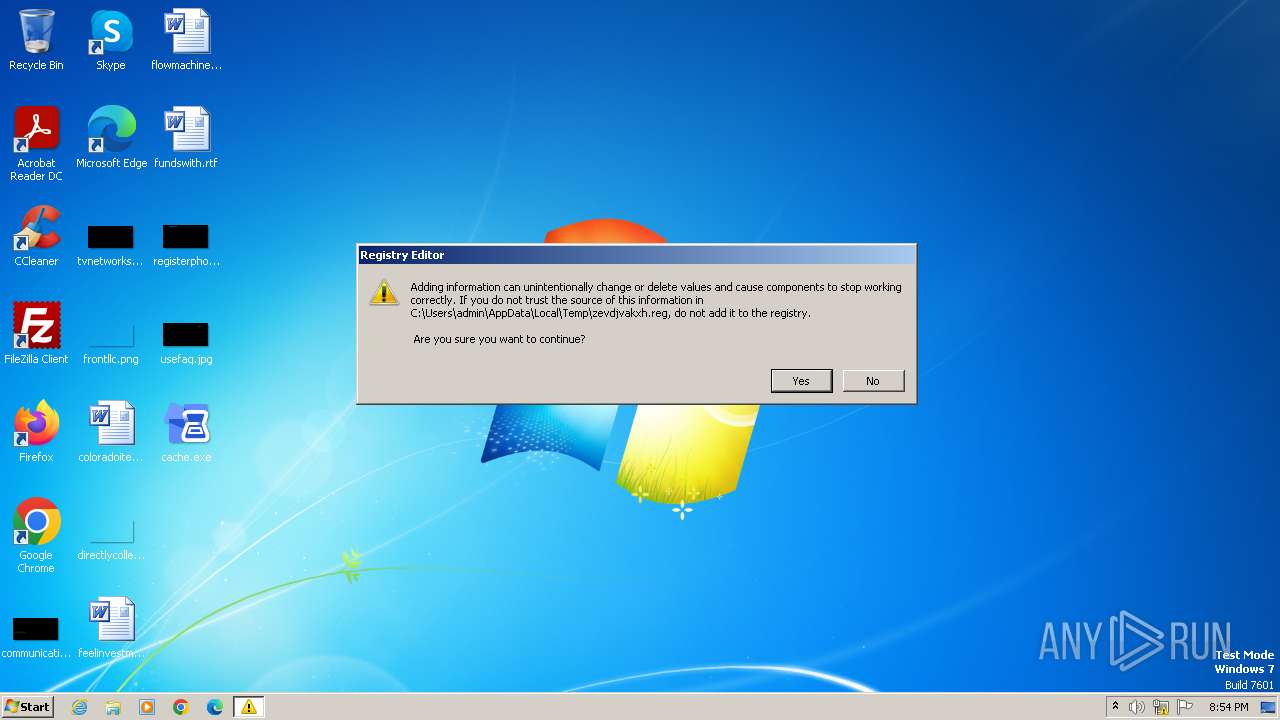
| 112 | "regedit.exe" "C:\Users\admin\AppData\Local\Temp\zevdjvakxh.reg" | C:\Windows\regedit.exe | — | ccors.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 312 | "regedit.exe" "C:\Users\admin\AppData\Local\Temp\zevdjvakxh.reg" | C:\Windows\regedit.exe | ccors.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1548 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1632 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 2100 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2108 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2128 | "C:\Users\admin\AppData\Local\Temp\csunebrmkfqykqyhevlng.exe" | C:\Users\admin\AppData\Local\Temp\csunebrmkfqykqyhevlng.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2144 | "C:\Users\admin\AppData\Local\Temp\zkhvhzkatjpszadh.exe" . | C:\Users\admin\AppData\Local\Temp\zkhvhzkatjpszadh.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2216 | "C:\Users\admin\AppData\Local\Temp\gegcazmfdfb.exe" "c:\users\admin\appdata\local\temp\zkhvhzkatjpszadh.exe*." | C:\Users\admin\AppData\Local\Temp\gegcazmfdfb.exe | — | zkhvhzkatjpszadh.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2224 | "C:\Users\admin\AppData\Local\Temp\gegcazmfdfb.exe" "c:\users\admin\appdata\local\temp\csunebrmkfqykqyhevlng.exe*" | C:\Users\admin\AppData\Local\Temp\gegcazmfdfb.exe | csunebrmkfqykqyhevlng.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
29 753
Read events
28 309
Write events
1 378
Delete events
66
Modification events
| (PID) Process: | (3968) cache.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3968) cache.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3968) cache.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3968) cache.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4028) gegcazmfdfb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (4028) gegcazmfdfb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: Explorer.exe | |||
| (PID) Process: | (4028) gegcazmfdfb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | acqvyhj |
Value: gsqfslxoizgksuydw.exe | |||
| (PID) Process: | (4028) gegcazmfdfb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | pshnrbem |
Value: gsqfslxoizgksuydw.exe . | |||
| (PID) Process: | (4028) gegcazmfdfb.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | zevdjvakxh |
Value: aoofupdwsluakoubwlz.exe | |||
| (PID) Process: | (4028) gegcazmfdfb.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | uasbivbmalm |
Value: aoofupdwsluakoubwlz.exe . | |||
Executable files
29
Suspicious files
3
Text files
8
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4064 | ccors.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\mkuvuzxagjcsmaqhmljtutywz.ibr | — | |
MD5:— | SHA256:— | |||
| 4064 | ccors.exe | C:\Users\admin\AppData\Local\mkuvuzxagjcsmaqhmljtutywz.ibr | — | |
MD5:— | SHA256:— | |||
| 4064 | ccors.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\mkuvuzxagjcsmaqhmljtutywz.ibr | — | |
MD5:— | SHA256:— | |||
| 4064 | ccors.exe | C:\Users\admin\AppData\Local\Temp\mkuvuzxagjcsmaqhmljtutywz.ibr | — | |
MD5:— | SHA256:— | |||
| 4028 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\gsqfslxoizgksuydw.exe | executable | |
MD5:BF78AC2C1076B63B14BF63F93266DAAF | SHA256:56A4EBDE6F5146038418753B4374F02D5B0B1DC590103B96012A98A446F2AC74 | |||
| 4028 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\aoofupdwsluakoubwlz.exe | executable | |
MD5:BF78AC2C1076B63B14BF63F93266DAAF | SHA256:56A4EBDE6F5146038418753B4374F02D5B0B1DC590103B96012A98A446F2AC74 | |||
| 3968 | cache.exe | C:\Users\admin\AppData\Local\Temp\gegcazmfdfb.exe | executable | |
MD5:85CB856B920E7B0B7B75115336FC2AF2 | SHA256:6FFF20AABE8265B6E811C9DBCB987F9C15CF07D1D8B80CED7B287D96900F5C62 | |||
| 4028 | gegcazmfdfb.exe | C:\Users\admin\AppData\Local\Temp\tknhzxokjfranudnlduxrj.exe | executable | |
MD5:BF78AC2C1076B63B14BF63F93266DAAF | SHA256:56A4EBDE6F5146038418753B4374F02D5B0B1DC590103B96012A98A446F2AC74 | |||
| 2224 | gegcazmfdfb.exe | C:\Windows\system32\gsqfslxoizgksuydw.exe | executable | |
MD5:BF78AC2C1076B63B14BF63F93266DAAF | SHA256:56A4EBDE6F5146038418753B4374F02D5B0B1DC590103B96012A98A446F2AC74 | |||
| 2224 | gegcazmfdfb.exe | C:\Windows\system32\ncdvlhwqnhryjovdzpef.exe | executable | |
MD5:BF78AC2C1076B63B14BF63F93266DAAF | SHA256:56A4EBDE6F5146038418753B4374F02D5B0B1DC590103B96012A98A446F2AC74 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
25
DNS requests
9
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1632 | sipnotify.exe | HEAD | 200 | 104.64.171.144:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133591569151400000 | unknown | — | — | unknown |
2356 | ccors.exe | GET | 403 | 104.19.223.79:80 | http://whatismyipaddress.com/ | unknown | — | — | unknown |
2356 | ccors.exe | GET | 301 | 104.27.206.92:80 | http://www.whatismyip.com/ | unknown | — | — | unknown |
2356 | ccors.exe | GET | 301 | 188.114.96.3:80 | http://www.showmyipaddress.com/ | unknown | — | — | unknown |
2356 | ccors.exe | GET | 301 | 188.114.96.3:80 | http://www.showmyipaddress.com/ | unknown | — | — | unknown |
2356 | ccors.exe | GET | 403 | 104.19.223.79:80 | http://whatismyipaddress.com/ | unknown | — | — | unknown |
2356 | ccors.exe | GET | — | 104.27.206.92:80 | http://www.whatismyip.com/ | unknown | — | — | unknown |
2356 | ccors.exe | GET | 301 | 104.27.206.92:80 | http://www.whatismyip.com/ | unknown | — | — | unknown |
2356 | ccors.exe | GET | 301 | 104.27.206.92:80 | http://www.whatismyip.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1468 | svchost.exe | 239.255.255.250:3702 | — | — | — | unknown |
1112 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1632 | sipnotify.exe | 104.64.171.144:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | CZ | unknown |
2356 | ccors.exe | 49.13.77.253:80 | www.whatismyip.ca | Hetzner Online GmbH | DE | unknown |
2356 | ccors.exe | 104.19.223.79:80 | whatismyipaddress.com | CLOUDFLARENET | — | unknown |
2356 | ccors.exe | 104.27.206.92:80 | www.whatismyip.com | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |
www.whatismyip.ca |
| malicious |
dns.msftncsi.com |
| shared |
whatismyipaddress.com |
| shared |
www.whatismyip.com |
| shared |
www.showmyipaddress.com |
| malicious |
aka.ms |
| whitelisted |
pscoretestdata.blob.core.windows.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2356 | ccors.exe | A Network Trojan was detected | ET MALWARE Win32/Pykspa.C Public IP Check |
— | — | A Network Trojan was detected | ET MALWARE Win32/Pykspa.C Public IP Check |
— | — | Attempted Information Leak | ET POLICY IP Check Domain (whatismyip in HTTP Host) |
2356 | ccors.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (showmyipaddress .com in HTTP Host) |
— | — | A Network Trojan was detected | ET MALWARE Win32/Pykspa.C Public IP Check |
2356 | ccors.exe | A Network Trojan was detected | ET MALWARE Win32/Pykspa.C Public IP Check |
2356 | ccors.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (showmyipaddress .com in HTTP Host) |
2356 | ccors.exe | A Network Trojan was detected | ET MALWARE Win32/Pykspa.C Public IP Check |
2356 | ccors.exe | A Network Trojan was detected | ET MALWARE Win32/Pykspa.C Public IP Check |
2356 | ccors.exe | Attempted Information Leak | ET POLICY IP Check Domain (whatismyip in HTTP Host) |
2 ETPRO signatures available at the full report