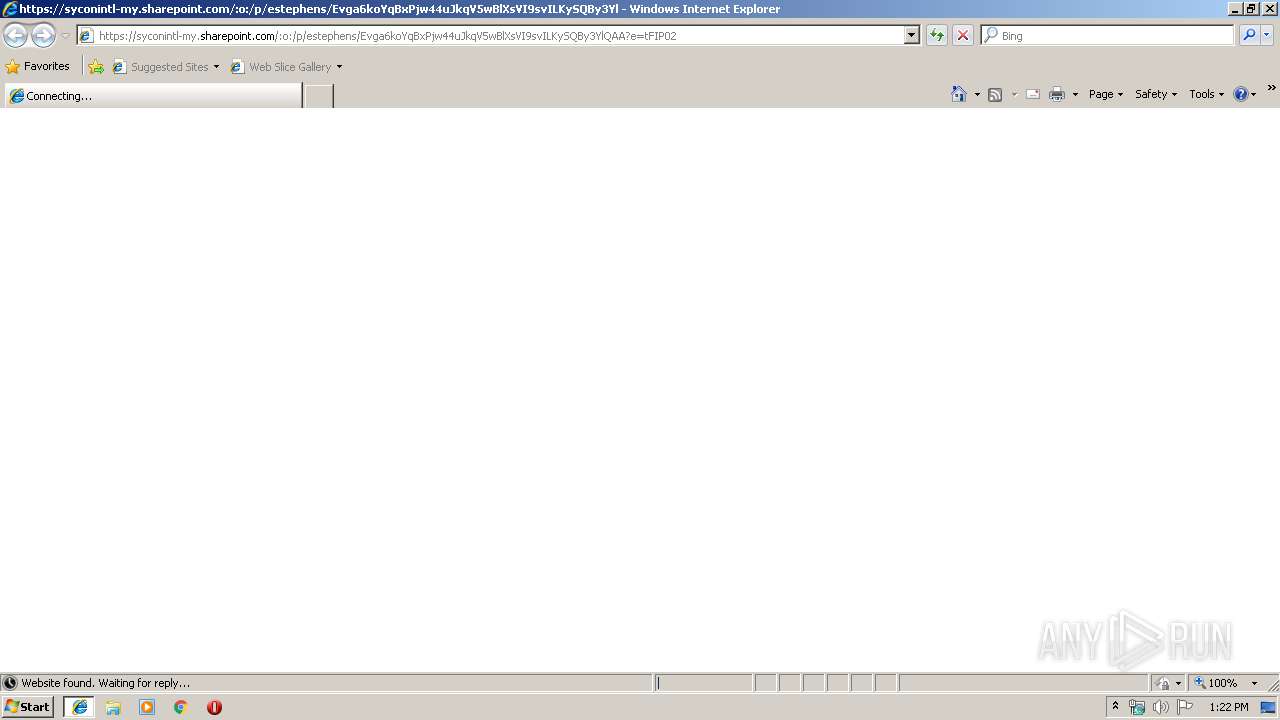
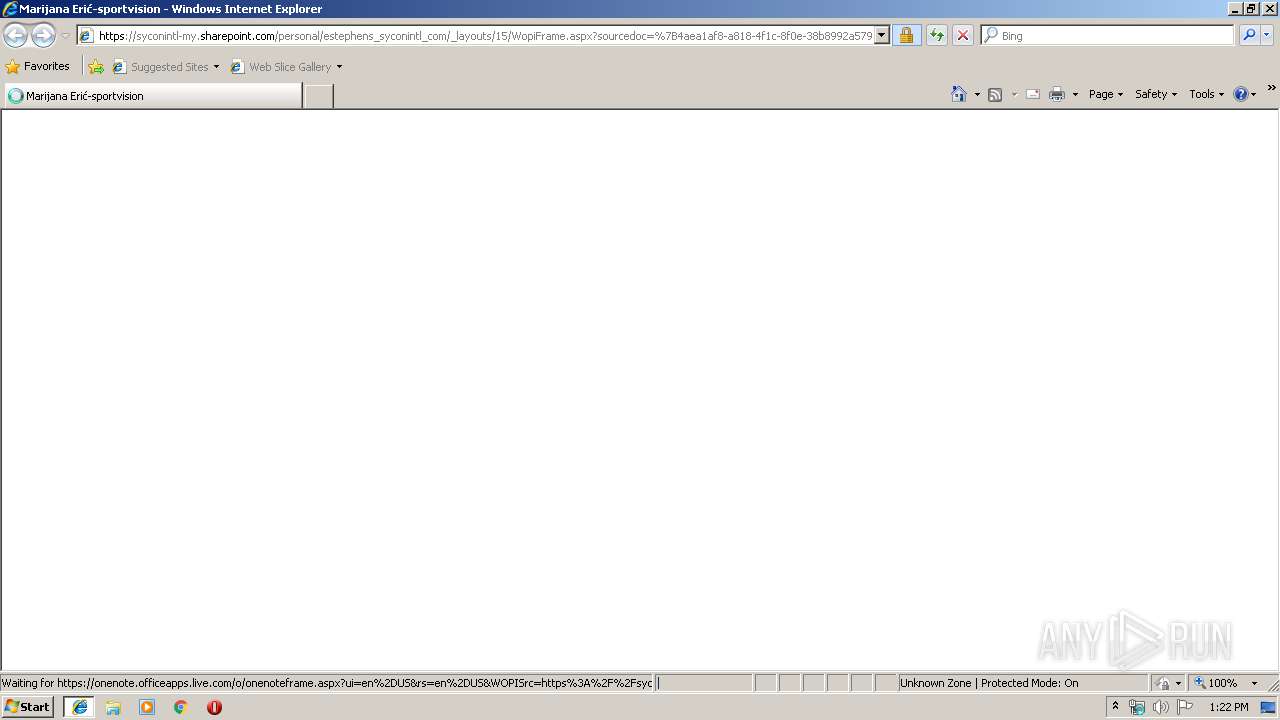
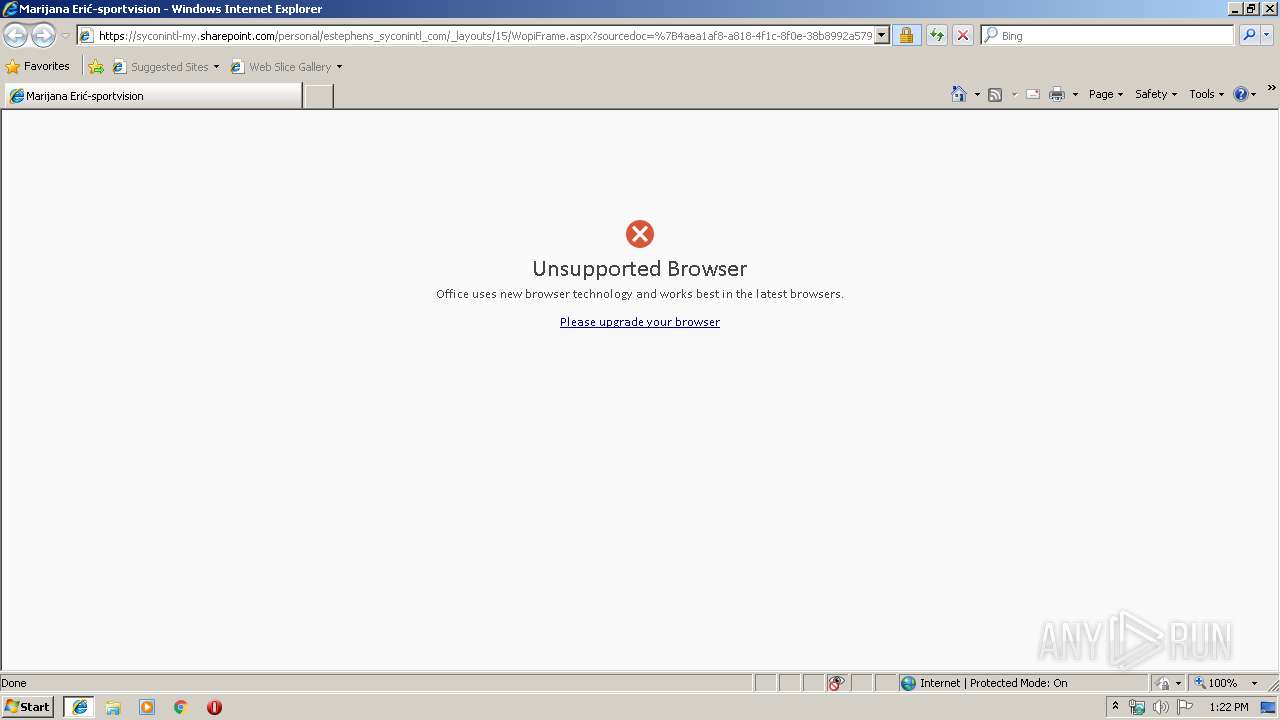
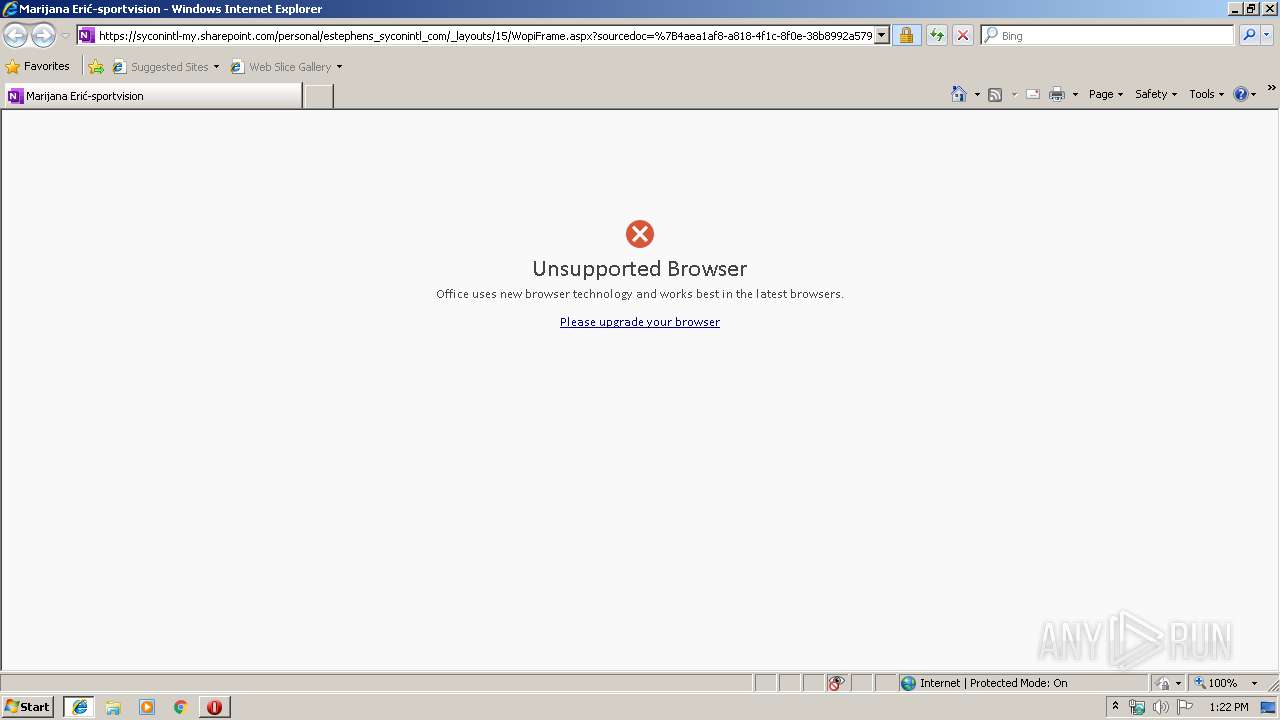
| URL: | https://syconintl-my.sharepoint.com/:o:/p/estephens/Evga6koYqBxPjw44uJkqV5wBlXsVI9svILKySQBy3YlQAA?e=tFIP02 |
| Full analysis: | https://app.any.run/tasks/4444dc65-be43-4380-85a8-b1d0f04b635f |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2019, 13:21:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 65AB2F3E4F1A5DB36AAF6E62FCC3E102 |
| SHA1: | 033CFDDC89682E2FB9268EA0DD50995A50939619 |
| SHA256: | 56953F67F89A4FD802637C6BFFCDB5F2F166166D737EC3DC4CB6091F5A72B5DE |
| SSDEEP: | 3:N8RdL7IciN+ArL5pDAOrTjd176juHDTMys1VX:2z7Iv+AfXDAI6jkg/fX |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Changes internet zones settings
- iexplore.exe (PID: 2428)
Application launched itself
- iexplore.exe (PID: 2428)
Reads internet explorer settings
- iexplore.exe (PID: 3468)
Reads Internet Cache Settings
- iexplore.exe (PID: 3468)
Reads settings of System Certificates
- iexplore.exe (PID: 2428)
Changes settings of System certificates
- iexplore.exe (PID: 2428)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2428)
Manual execution by user
- opera.exe (PID: 1244)
Creates files in the user directory
- opera.exe (PID: 1244)
- iexplore.exe (PID: 2428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1244 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 2428 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://syconintl-my.sharepoint.com/:o:/p/estephens/Evga6koYqBxPjw44uJkqV5wBlXsVI9svILKySQBy3YlQAA?e=tFIP02" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3468 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2428 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
665
Read events
526
Write events
136
Delete events
3
Modification events
| (PID) Process: | (2428) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2428) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2428) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2428) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2428) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2428) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2428) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {C6028AA1-022A-11EA-AB41-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2428) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2428) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (2428) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070B00050008000D0016000D001002 | |||
Executable files
0
Suspicious files
12
Text files
38
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2428 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2428 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\3BX5YRHO\WopiFrame[1].aspx | — | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\3BX5YRHO\WopiFrame[1].htm | html | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\GLKVS81S\blank[1].js | text | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\3BX5YRHO\init[1].js | text | |
MD5:— | SHA256:— | |||
| 3468 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\47QMO1N0\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 2428 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\favicon[1].png | image | |
MD5:9FB559A691078558E77D6848202F6541 | SHA256:6D8A01DC7647BC218D003B58FE04049E24A9359900B7E0CEBAE76EDF85B8B914 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
29
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1244 | opera.exe | GET | 200 | 72.21.91.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 564 b | whitelisted |
2428 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3468 | iexplore.exe | 13.107.6.171:443 | onenote.officeapps.live.com | Microsoft Corporation | US | whitelisted |
1244 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
1244 | opera.exe | 13.107.136.9:443 | syconintl-my.sharepoint.com | Microsoft Corporation | US | whitelisted |
3468 | iexplore.exe | 13.107.136.9:443 | syconintl-my.sharepoint.com | Microsoft Corporation | US | whitelisted |
2428 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1244 | opera.exe | 107.167.110.216:443 | sitecheck2.opera.com | Opera Software Americas LLC | US | malicious |
1244 | opera.exe | 185.26.182.94:443 | certs.opera.com | Opera Software AS | — | whitelisted |
3468 | iexplore.exe | 184.50.167.104:443 | static.sharepointonline.com | Akamai Technologies, Inc. | NL | whitelisted |
1244 | opera.exe | 72.21.91.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2428 | iexplore.exe | 72.247.225.58:443 | c1-onenote-15.cdn.office.net | Akamai Technologies, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
syconintl-my.sharepoint.com |
| suspicious |
www.bing.com |
| whitelisted |
static.sharepointonline.com |
| whitelisted |
onenote.officeapps.live.com |
| whitelisted |
c1-onenote-15.cdn.office.net |
| whitelisted |
certs.opera.com |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |