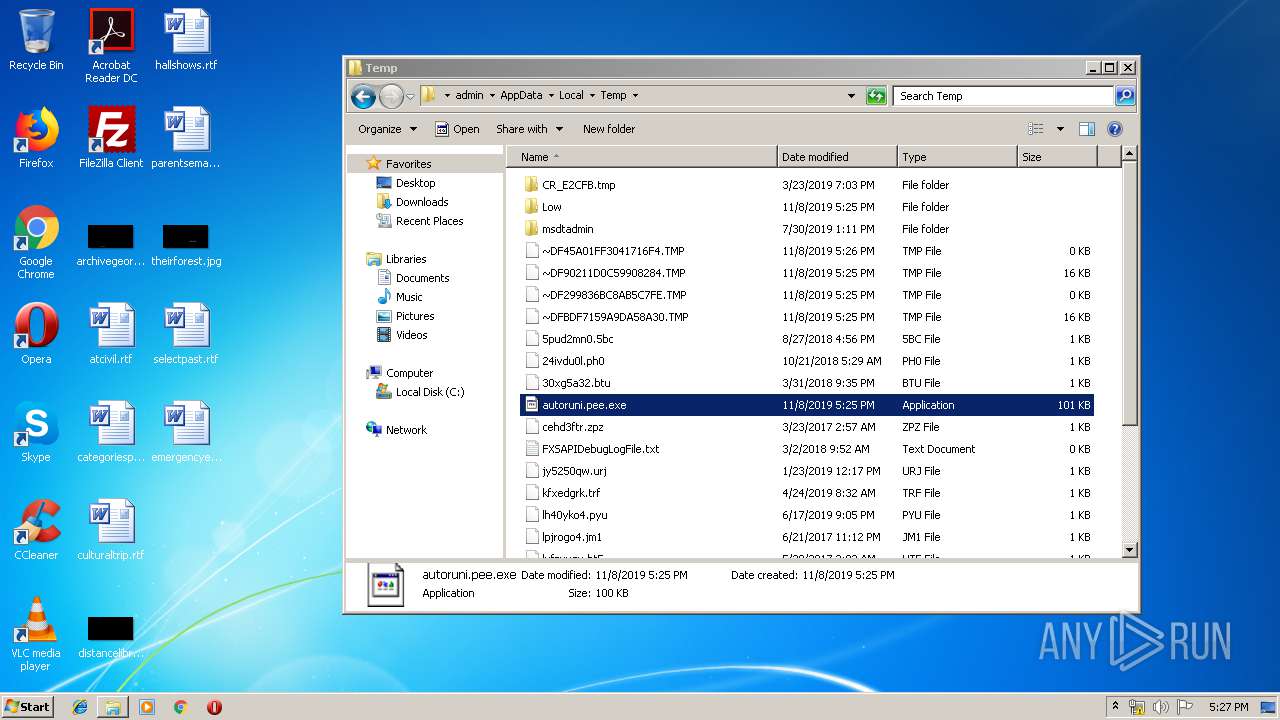
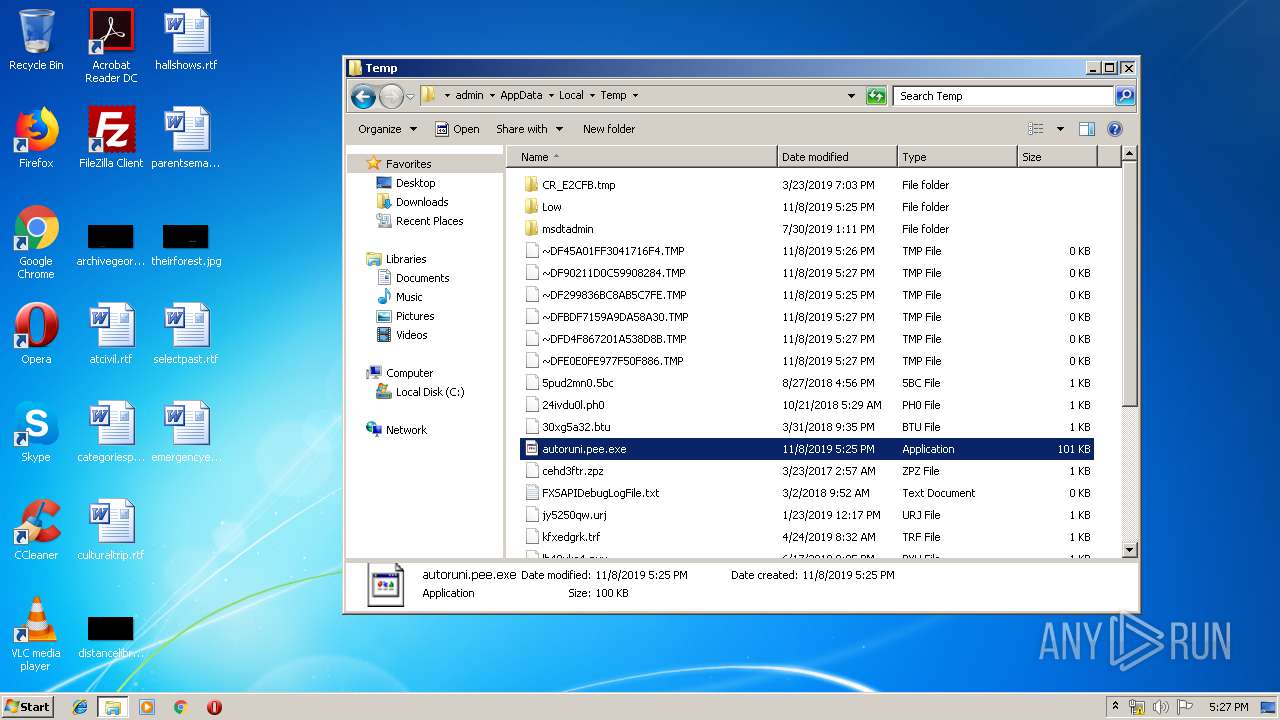
| File name: | autoruni.pee |
| Full analysis: | https://app.any.run/tasks/31cc5645-9894-4373-b94e-d78e78e0c894 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2019, 17:24:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Petite compressed |
| MD5: | AAE219D4E703051D60351F73CA288D1D |
| SHA1: | 1B28CBC3D27A92281EBF4754C27B9AC4A3A8C214 |
| SHA256: | 56947C93FB17D3339FF2A778556F4A4F95516FB5112DB61AE0804ECDCF4D1307 |
| SSDEEP: | 3072:J2MWsQvnyo/CtkgEcnz7fsmqLGnQ7eMDLyPexpZ:J2jsgpYtEcnzwlLFeMD2Pex |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- autoruni.pee.exe (PID: 2104)
- autoruni.pee.exe (PID: 2328)
Uses ATTRIB.EXE to modify file attributes
- Cmd.exe (PID: 4008)
- Cmd.exe (PID: 4052)
- Cmd.exe (PID: 284)
- Cmd.exe (PID: 2752)
- Cmd.exe (PID: 1952)
- Cmd.exe (PID: 1796)
- Cmd.exe (PID: 1600)
- Cmd.exe (PID: 2644)
- Cmd.exe (PID: 996)
- Cmd.exe (PID: 2408)
Modifies the open verb of a shell class
- autoruni.pee.exe (PID: 2104)
- autoruni.pee.exe (PID: 2328)
INFO
Manual execution by user
- iexplore.exe (PID: 3960)
- autoruni.pee.exe (PID: 2328)
- taskmgr.exe (PID: 3652)
Application launched itself
- iexplore.exe (PID: 3960)
Changes internet zones settings
- iexplore.exe (PID: 3960)
Reads Internet Cache Settings
- iexplore.exe (PID: 2352)
- iexplore.exe (PID: 3960)
Reads internet explorer settings
- iexplore.exe (PID: 2352)
Creates files in the user directory
- iexplore.exe (PID: 2352)
- iexplore.exe (PID: 3960)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2352)
Reads settings of System Certificates
- iexplore.exe (PID: 2352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Petite compressed Win32 executable (53.5) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (20.2) |
| .exe | | | Win32 EXE Yoda's Crypter (19.8) |
| .exe | | | Win32 Executable (generic) (3.3) |
| .exe | | | Generic Win/DOS Executable (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:08:08 22:19:47+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 144145 |
| InitializedDataSize: | 148241 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x25046 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Explorer |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | vx |
| OriginalFileName: | vx.exe |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 08-Aug-2007 20:19:47 |
| Detected languages: |
|
| ProductName: | Explorer |
| FileVersion: | 1.00 |
| ProductVersion: | 1.00 |
| InternalName: | vx |
| OriginalFilename: | vx.exe |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000C0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 08-Aug-2007 20:19:47 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.petite | 0x00001000 | 0x00023000 | 0x00009600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.91302 |
.rsrc | 0x00024000 | 0x00001000 | 0x000005B8 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.60554 |
0x00025000 | 0x00000311 | 0x00000400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.712 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.08373 | 460 | Unicode (UTF 16LE) | English - United States | RT_VERSION |
30001 | 3.13767 | 744 | Unicode (UTF 16LE) | UNKNOWN | RT_ICON |
Imports
MSVBVM60.DLL |
kernel32.dll |
user32.dll |
Total processes
72
Monitored processes
25
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | Cmd.exe /c Attrib +a +s +r +h C:\Windows\System32\cmd.com | C:\Windows\system32\Cmd.exe | — | autoruni.pee.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 992 | Attrib +a +s +r +h C:\Windows\System32\LeChucK.exe | C:\Windows\system32\attrib.exe | — | Cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 996 | Cmd.exe /c Attrib +a +s +r +h C:\Windows\System32\cmd.com | C:\Windows\system32\Cmd.exe | — | autoruni.pee.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 996 | Attrib +a +s +r +h C:\Windows\regedit.com | C:\Windows\system32\attrib.exe | — | Cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1400 | Attrib +a +s +r +h C:\Windows\spolis.exe | C:\Windows\system32\attrib.exe | — | Cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1600 | Cmd.exe /c Attrib +a +s +r +h C:\Windows\System32\wins.exe | C:\Windows\system32\Cmd.exe | — | autoruni.pee.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1740 | Attrib +a +s +r +h C:\Windows\System32\LeChucK.exe | C:\Windows\system32\attrib.exe | — | Cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1796 | Cmd.exe /c Attrib +a +s +r +h C:\Windows\System32\LeChucK.exe | C:\Windows\system32\Cmd.exe | — | autoruni.pee.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1952 | Cmd.exe /c Attrib +a +s +r +h C:\Windows\spolis.exe | C:\Windows\system32\Cmd.exe | — | autoruni.pee.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2104 | "C:\Users\admin\AppData\Local\Temp\autoruni.pee.exe" | C:\Users\admin\AppData\Local\Temp\autoruni.pee.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
600
Read events
494
Write events
103
Delete events
3
Modification events
| (PID) Process: | (2104) autoruni.pee.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\exefile\shell\open\command |
| Operation: | write | Name: | |
Value: C:\Windows\System32\wins.exe "%1" %* | |||
| (PID) Process: | (2104) autoruni.pee.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\cmdfile\shell\open\command |
| Operation: | write | Name: | |
Value: C:\Windows\System32\wins.exe "%1" %* | |||
| (PID) Process: | (2104) autoruni.pee.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\piffile\shell\open\command |
| Operation: | write | Name: | |
Value: C:\Windows\System32\wins.exe "%1" %* | |||
| (PID) Process: | (2104) autoruni.pee.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\comfile\shell\open\command |
| Operation: | write | Name: | |
Value: C:\Windows\System32\wins.exe "%1" %* | |||
| (PID) Process: | (2104) autoruni.pee.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\batfile\shell\open\command |
| Operation: | write | Name: | |
Value: C:\Windows\System32\wins.exe "%1" %* | |||
| (PID) Process: | (2104) autoruni.pee.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\exefile\shell |
| Operation: | write | Name: | |
Value: Open | |||
| (PID) Process: | (2104) autoruni.pee.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\cmdfile\shell |
| Operation: | write | Name: | |
Value: Open | |||
| (PID) Process: | (2104) autoruni.pee.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\piffile\shell |
| Operation: | write | Name: | |
Value: Open | |||
| (PID) Process: | (2104) autoruni.pee.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\comfile\shell |
| Operation: | write | Name: | |
Value: Open | |||
| (PID) Process: | (2104) autoruni.pee.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\batfile\shell |
| Operation: | write | Name: | |
Value: Open | |||
Executable files
0
Suspicious files
4
Text files
55
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2104 | autoruni.pee.exe | C:\Users\admin\AppData\Local\Temp\~DF299836BC8AB5C7FE.TMP | — | |
MD5:— | SHA256:— | |||
| 3960 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2352 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@bing[2].txt | — | |
MD5:— | SHA256:— | |||
| 2352 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\F05JY564\qsml[1].aspx | — | |
MD5:— | SHA256:— | |||
| 2352 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\Z54ZG8HZ\qsml[1].aspx | — | |
MD5:— | SHA256:— | |||
| 2352 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\F05JY564\search[1].txt | — | |
MD5:— | SHA256:— | |||
| 2352 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3960 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
| 2352 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\F05JY564\qsml[1].xml | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
51
TCP/UDP connections
25
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2352 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=v&maxwidth=253&rowheight=20§ionHeight=400&FORM=IE8SSC&market=en-us | US | xml | 238 b | whitelisted |
2352 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=virus&maxwidth=253&rowheight=20§ionHeight=400&FORM=IE8SSC&market=en-us | US | xml | 227 b | whitelisted |
2352 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rb/5i/cj,nj/a96870c9/9fb0244f.js?bu=Et0f_h-fH6ofgwW7H68fiyCxH8Ufyx_5H_cf6R_ZHucd6h3cHg | US | text | 5.05 Kb | whitelisted |
2352 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/30/2e/cj,nj/4c7364c5/40e1b425.js | US | text | 816 b | whitelisted |
2352 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/8/2Y/cj,nj/4c10930c/19b40d8c.js | US | text | 272 b | whitelisted |
2352 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/59/2N/cj,nj/4df0cf24/0120f753.js | US | text | 2.92 Kb | whitelisted |
2352 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/search?q=virus&src=IE-SearchBox&FORM=IE8SRC | US | html | 78.1 Kb | whitelisted |
2352 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/sa/simg/SharedSpriteDesktopRewards_022118.png | US | image | 5.71 Kb | whitelisted |
2352 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/fd/ls/l?IG=10B6CA08E8354BCBA0CD30EB86F47A1B&CID=3684C52AC8836D472B68CB24C9DA6C6F&Type=Event.CPT&DATA={"pp":{"S":"A","FC":62,"BC":-1,"SE":-1,"TC":-1,"H":-1,"BP":-1,"CT":312,"IL":2},"ad":[-1,-1,772,444,1089,121,0]}&P=SERP&DA=DUB02 | US | image | 5.71 Kb | whitelisted |
2352 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/30/27/cj,nj/3f1e2270/f8c6dd44.js | US | text | 773 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3960 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2352 | iexplore.exe | 13.107.5.80:80 | api.bing.com | Microsoft Corporation | US | whitelisted |
2352 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2352 | iexplore.exe | 40.90.137.126:443 | login.live.com | Microsoft Corporation | US | unknown |
2352 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2352 | iexplore.exe | 104.211.96.15:80 | 0aded00a6d775f04dab8037898d97c75.clo.footprintdns.com | Microsoft Corporation | IN | whitelisted |
2352 | iexplore.exe | 52.231.32.10:80 | 6bb1c7dbd1a65614eeaed84b5f3c6605.clo.footprintdns.com | Microsoft Corporation | KR | whitelisted |
2352 | iexplore.exe | 65.52.143.224:80 | 31119e79512735c863ec70af046eb0a2.clo.footprintdns.com | Microsoft Corporation | NL | whitelisted |
2352 | iexplore.exe | 204.79.197.222:80 | fp.msedge.net | Microsoft Corporation | US | whitelisted |
2352 | iexplore.exe | 13.107.4.254:80 | b30b530a7eb3c42ea753ae4ed2cac8cc.clo.footprintdns.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
0aded00a6d775f04dab8037898d97c75.clo.footprintdns.com |
| unknown |
6bb1c7dbd1a65614eeaed84b5f3c6605.clo.footprintdns.com |
| unknown |
31119e79512735c863ec70af046eb0a2.clo.footprintdns.com |
| unknown |
fp.msedge.net |
| whitelisted |
b30b530a7eb3c42ea753ae4ed2cac8cc.clo.footprintdns.com |
| suspicious |
71808839d8e3a25db93011a00897dc6c.clo.footprintdns.com |
| suspicious |
2f8f0165b666d7ca8dc758d18b5df6e1.clo.footprintdns.com |
| unknown |