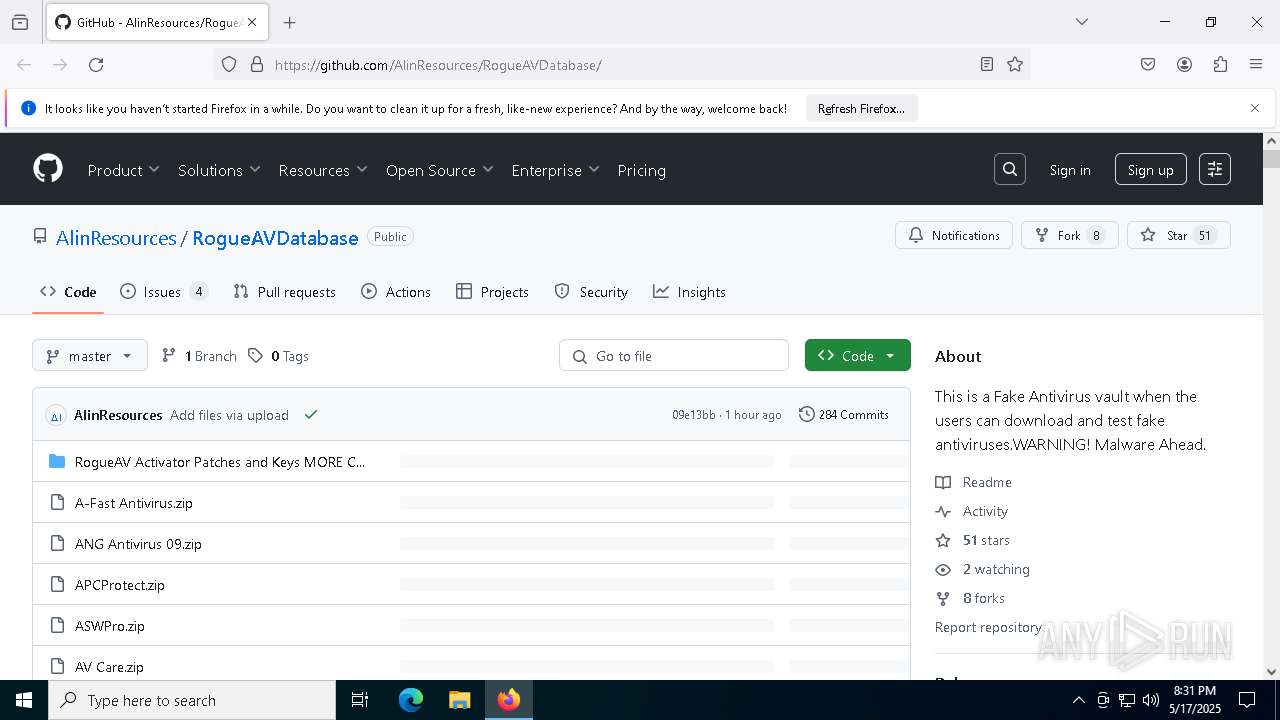
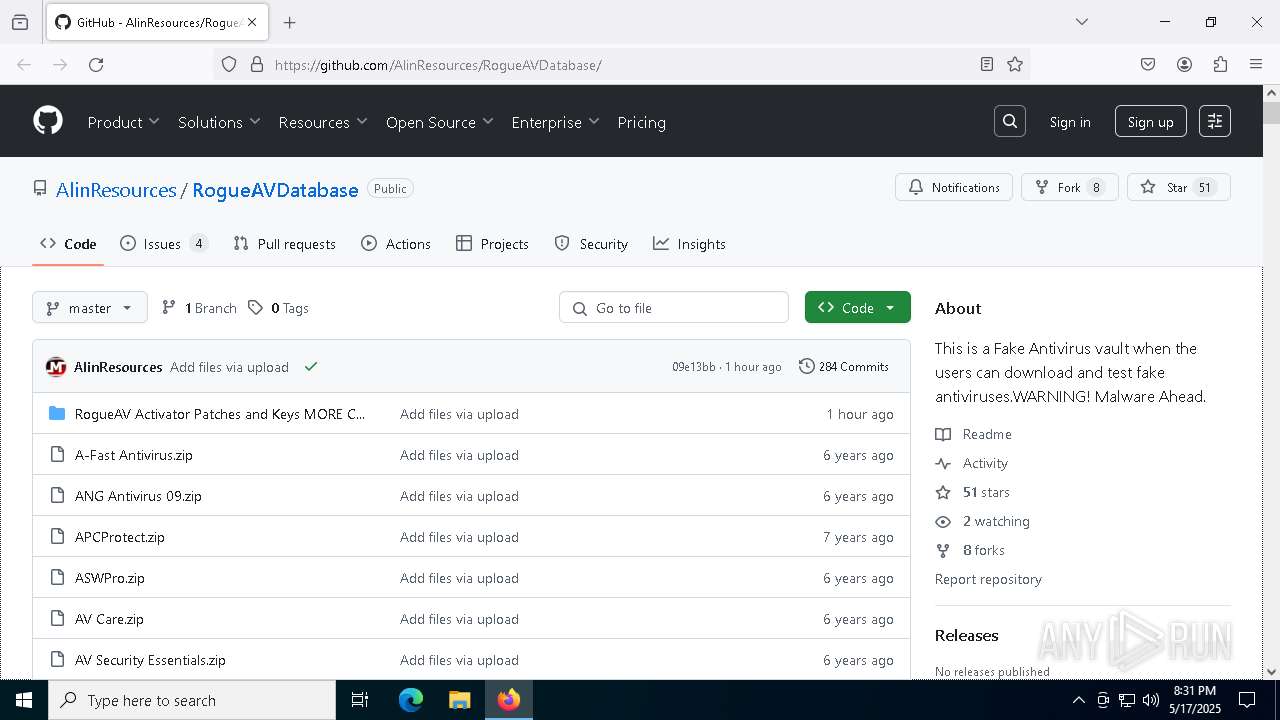
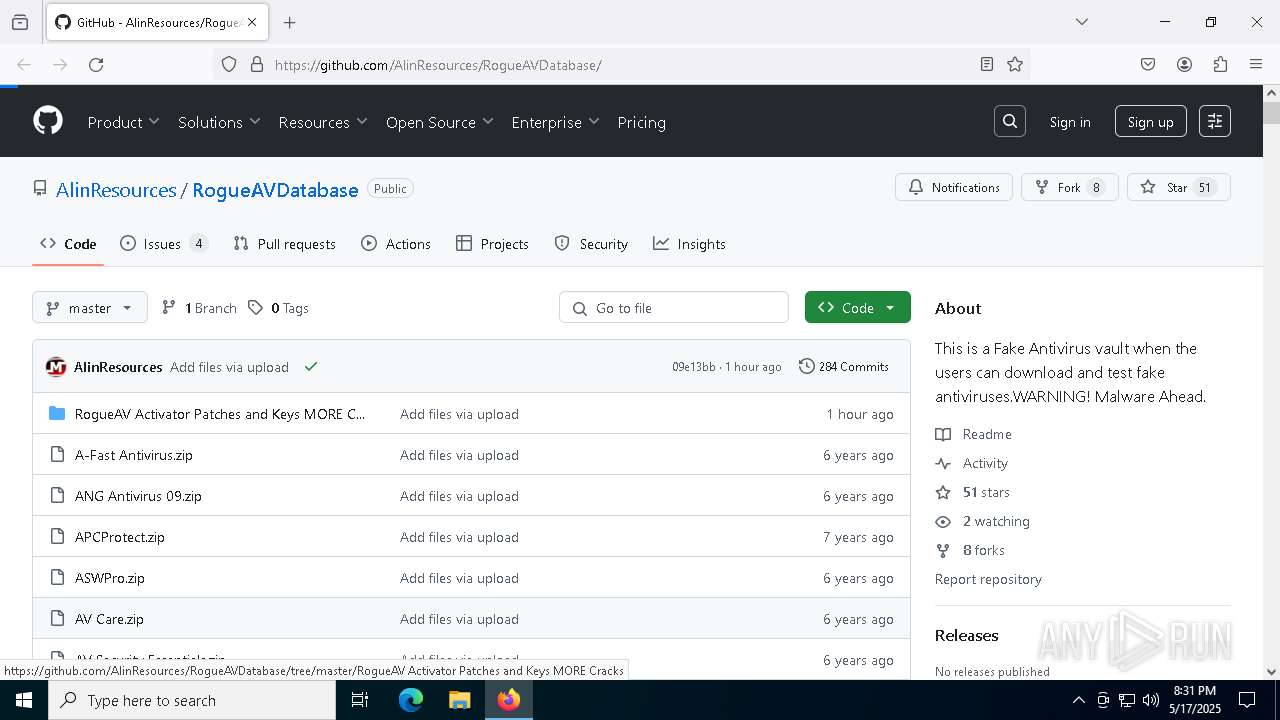
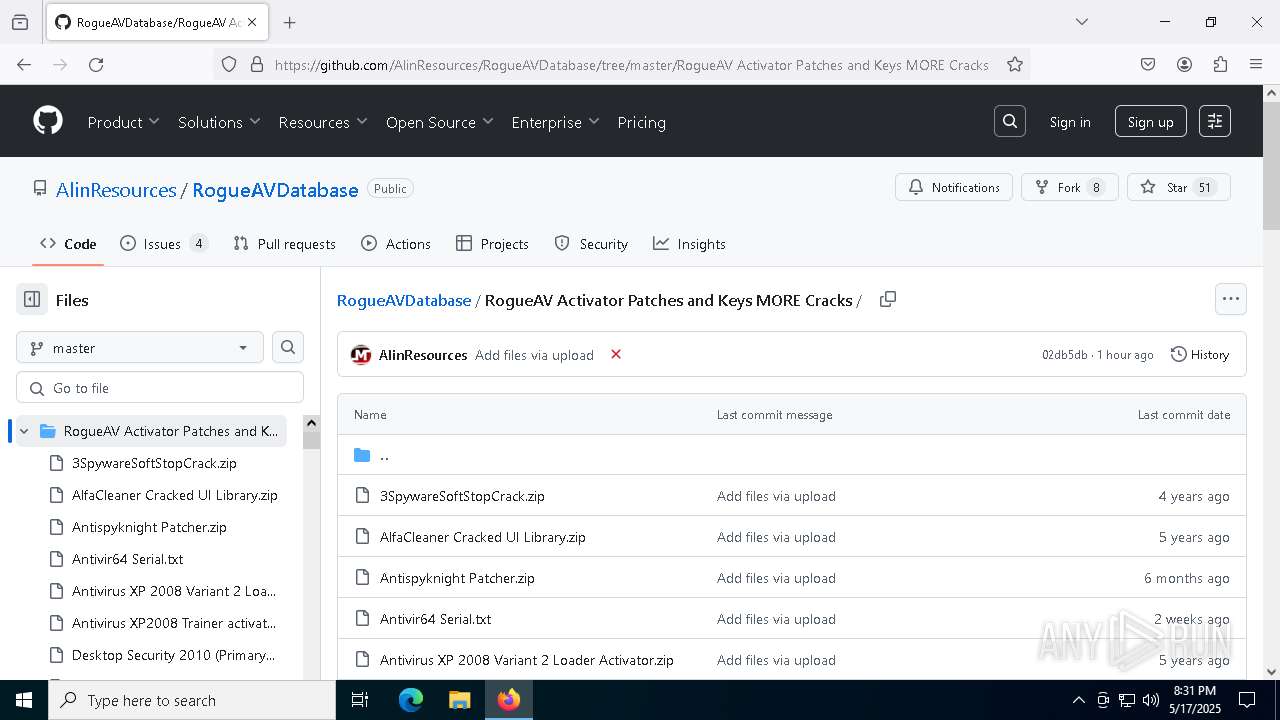
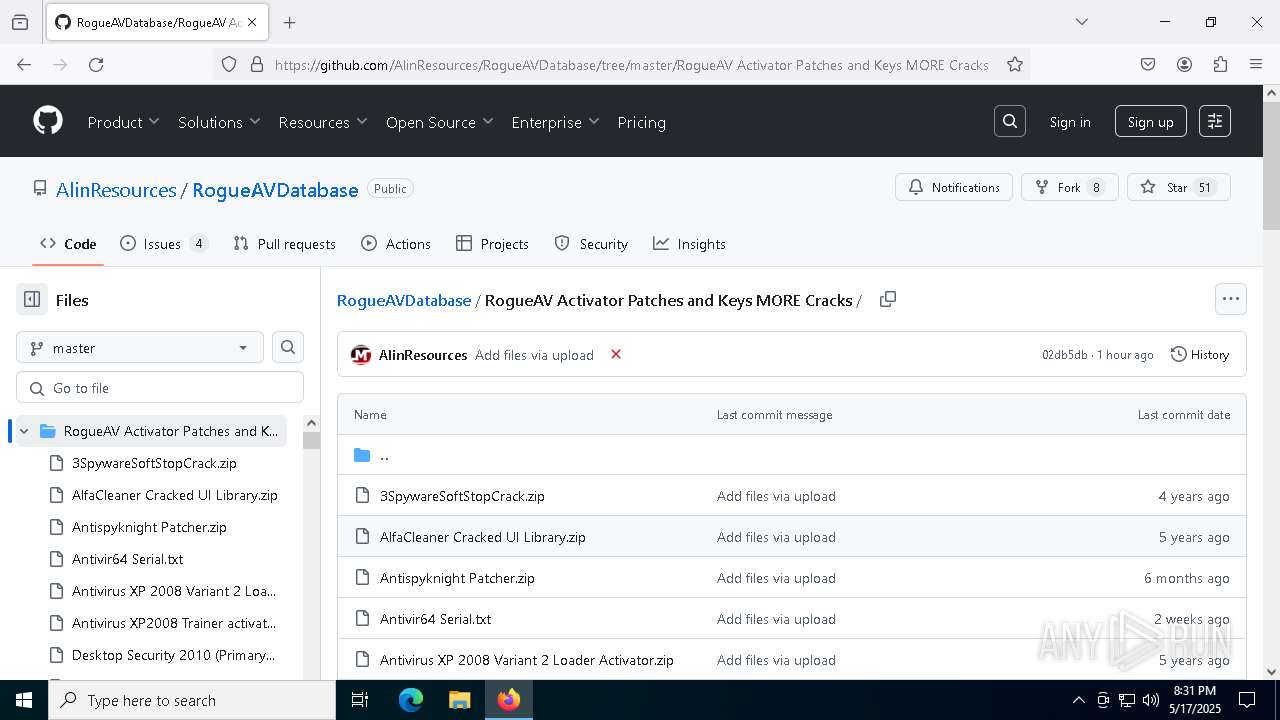
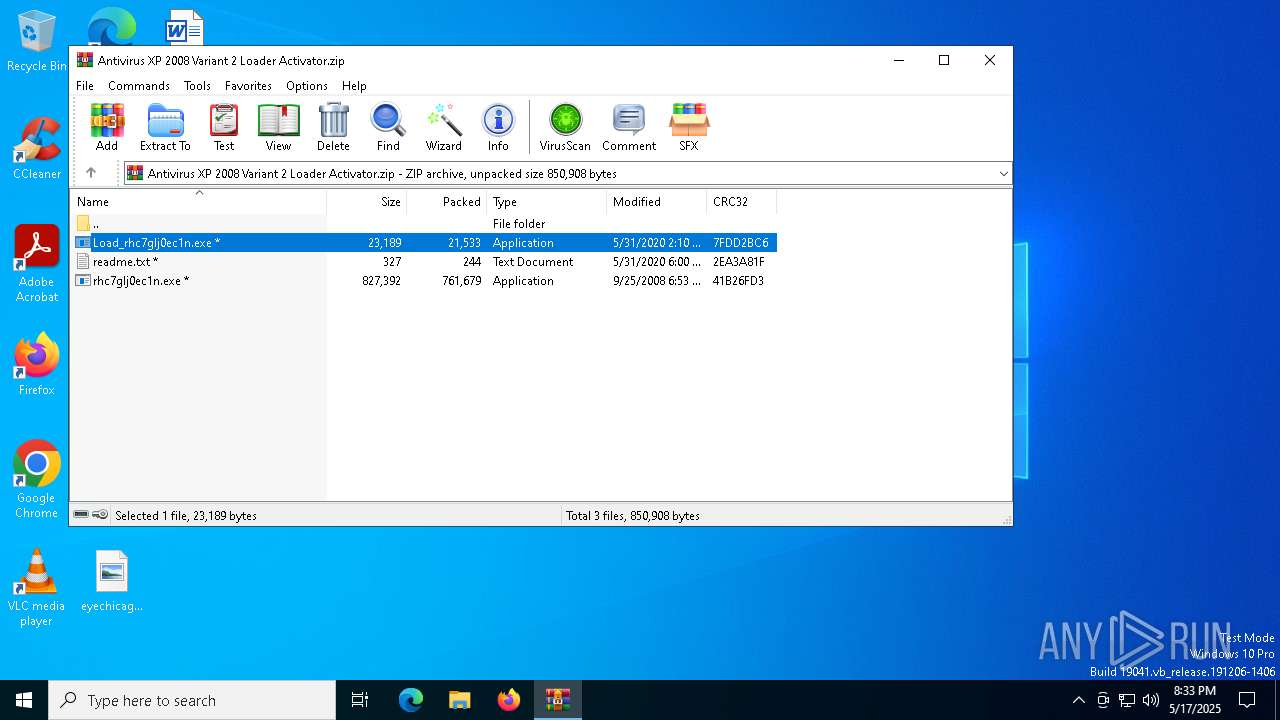
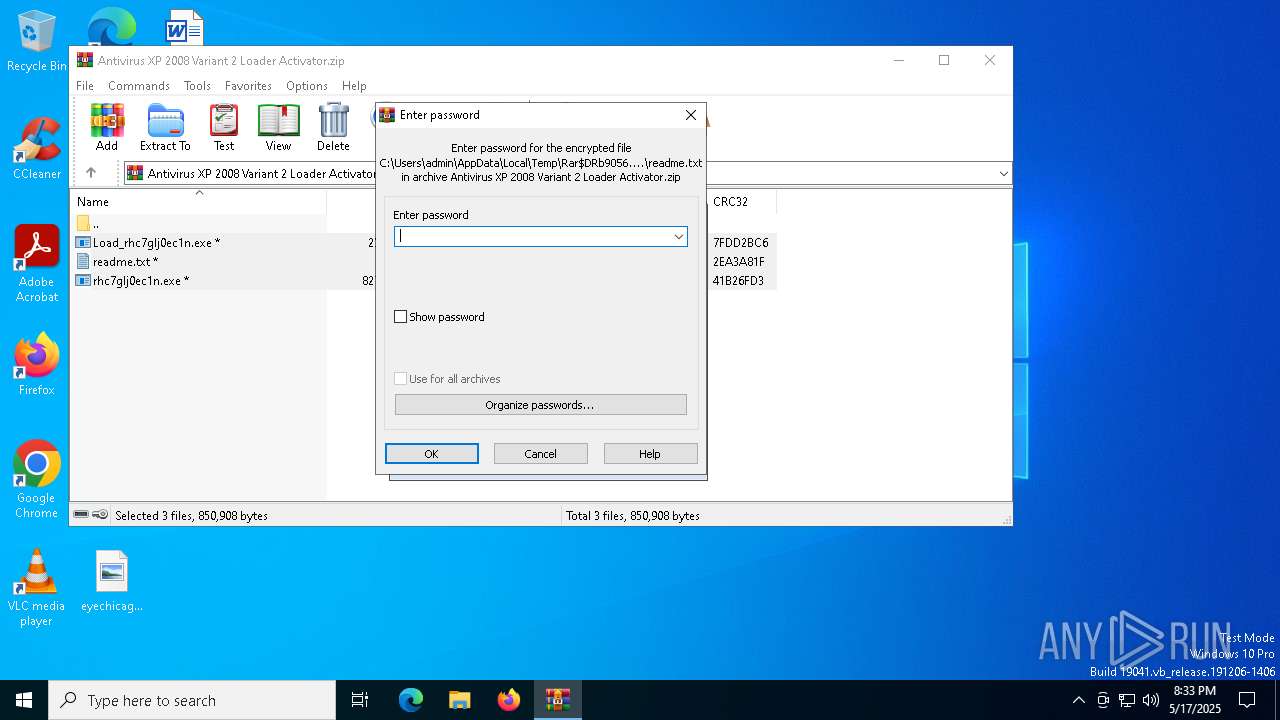
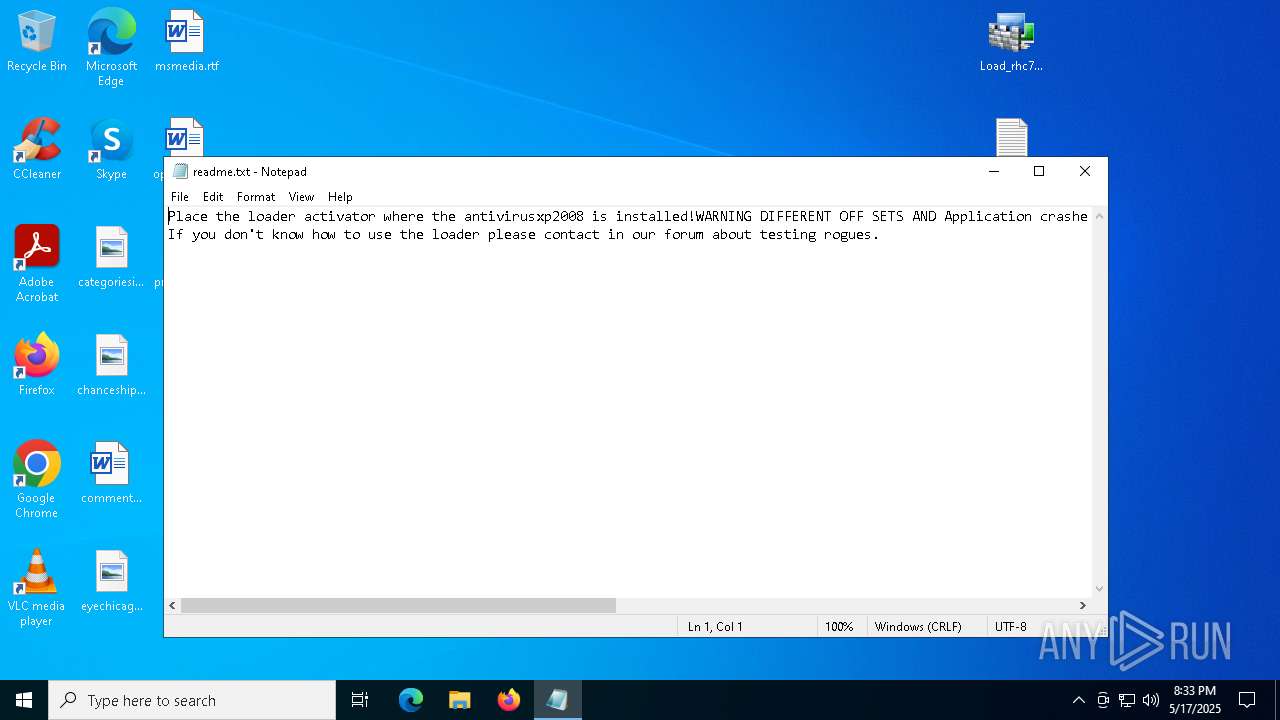
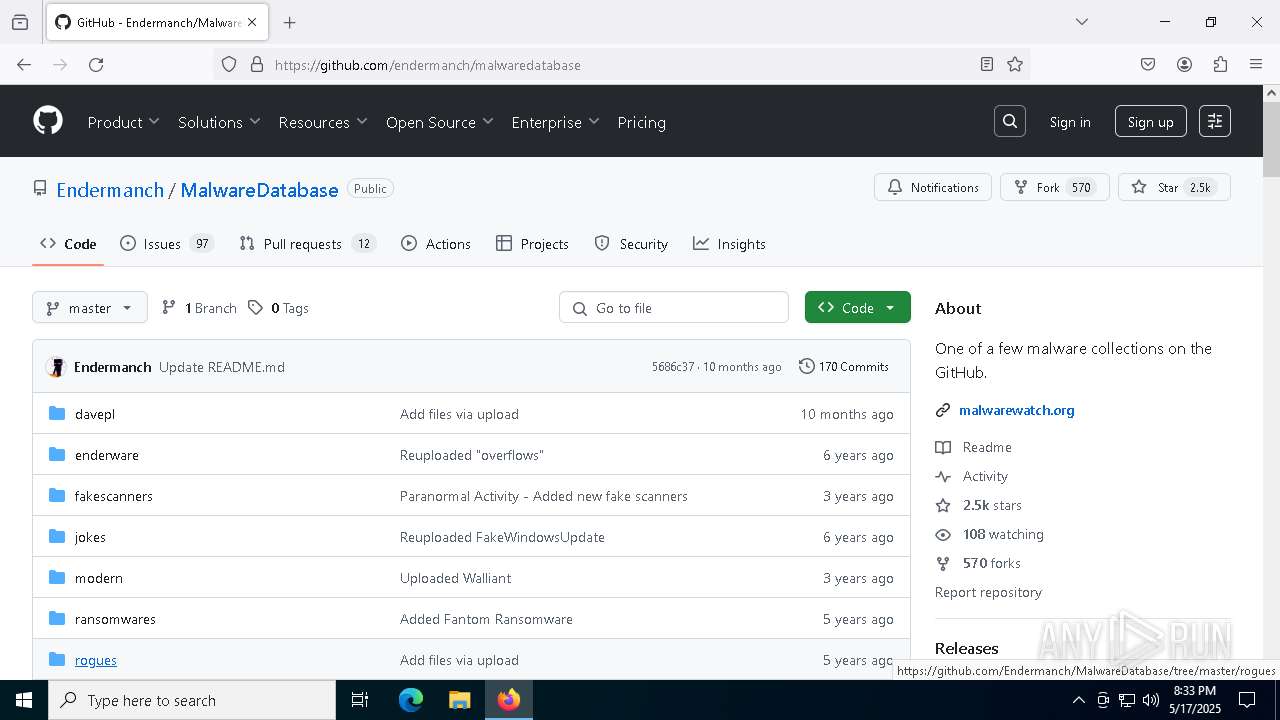
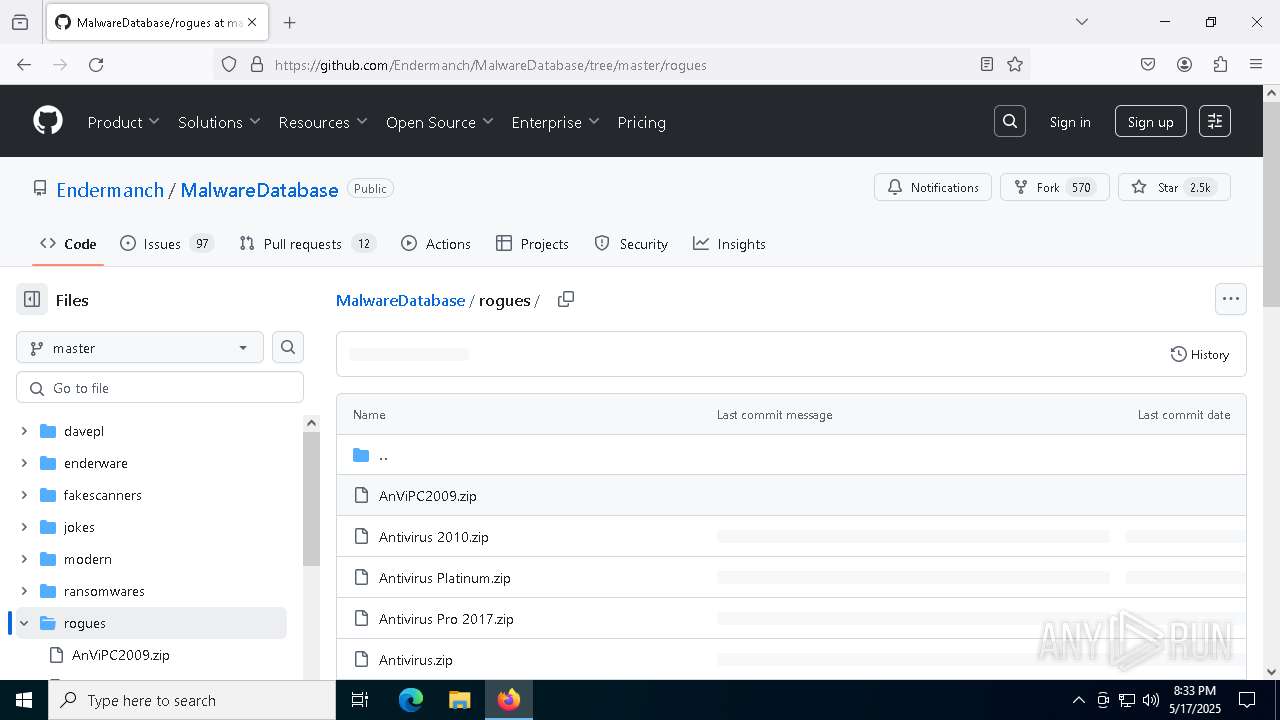
| URL: | https://github.com/AlinResources/RogueAVDatabase/ |
| Full analysis: | https://app.any.run/tasks/2fc6020f-cc27-4e81-a4da-b8a5d4cb17a6 |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 20:31:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 604E978145C9C7361477AF4943BB9993 |
| SHA1: | B1C20088943DBFE53A77B6F7E30CB4275B282895 |
| SHA256: | 56927486E6143E6107D273E1834AB3E13184F9661DA91BC9512551CC5BE4A988 |
| SSDEEP: | 3:N8tEdalNERLqn:2uklWNq |
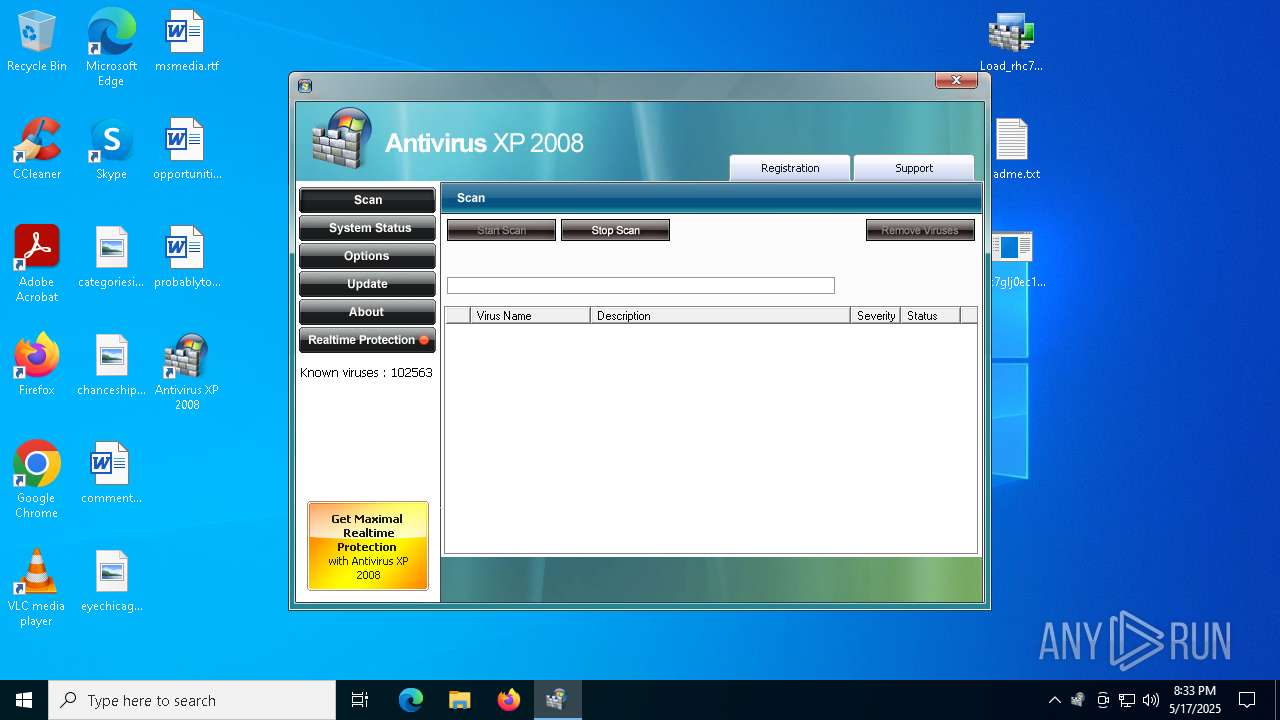
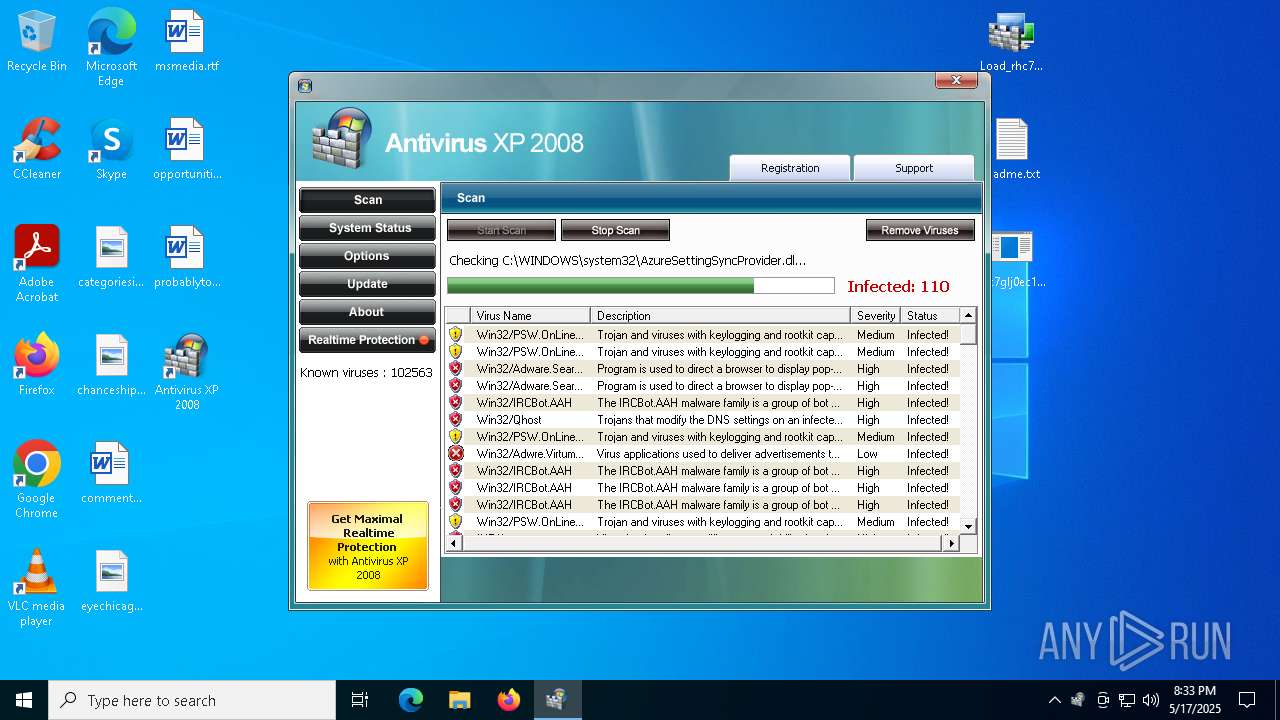
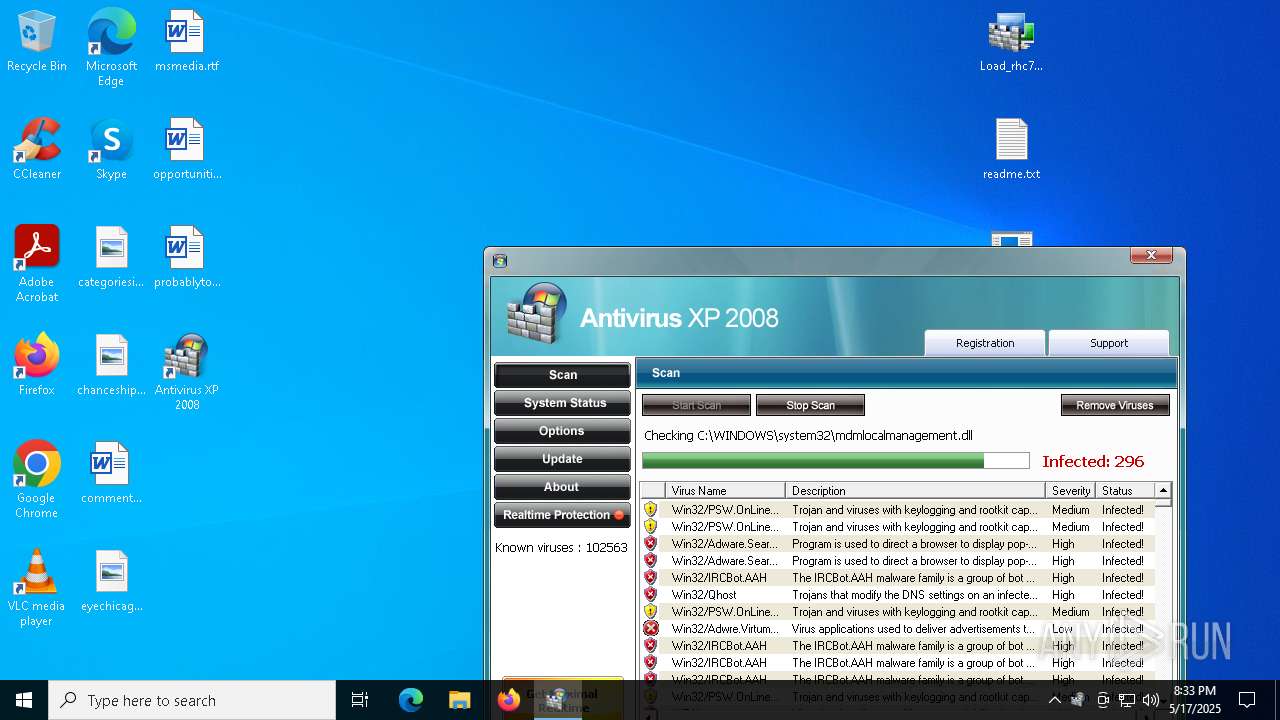
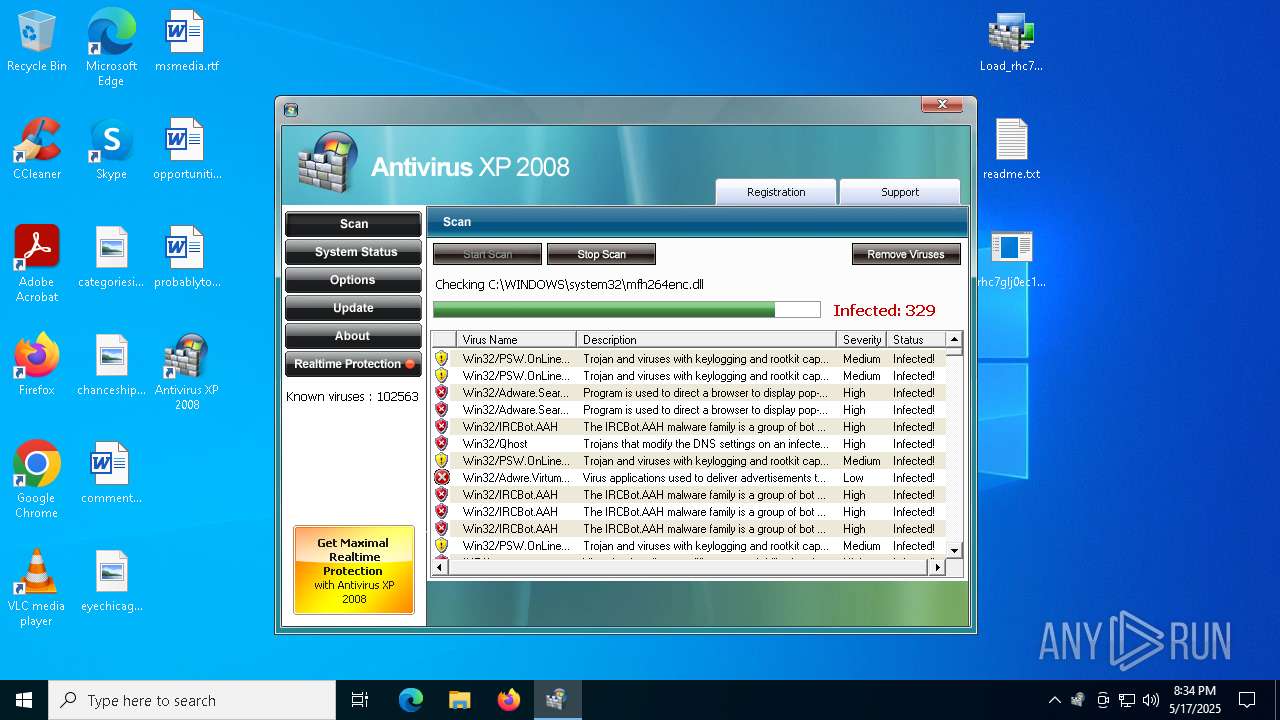
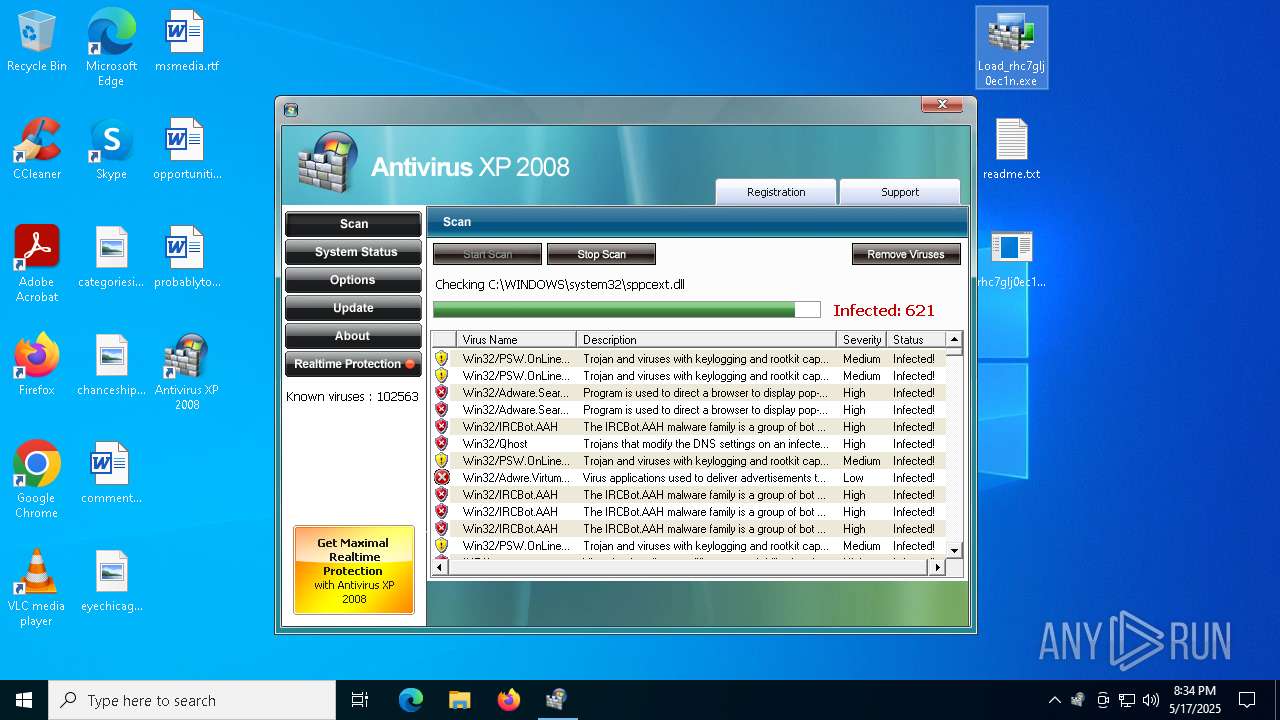
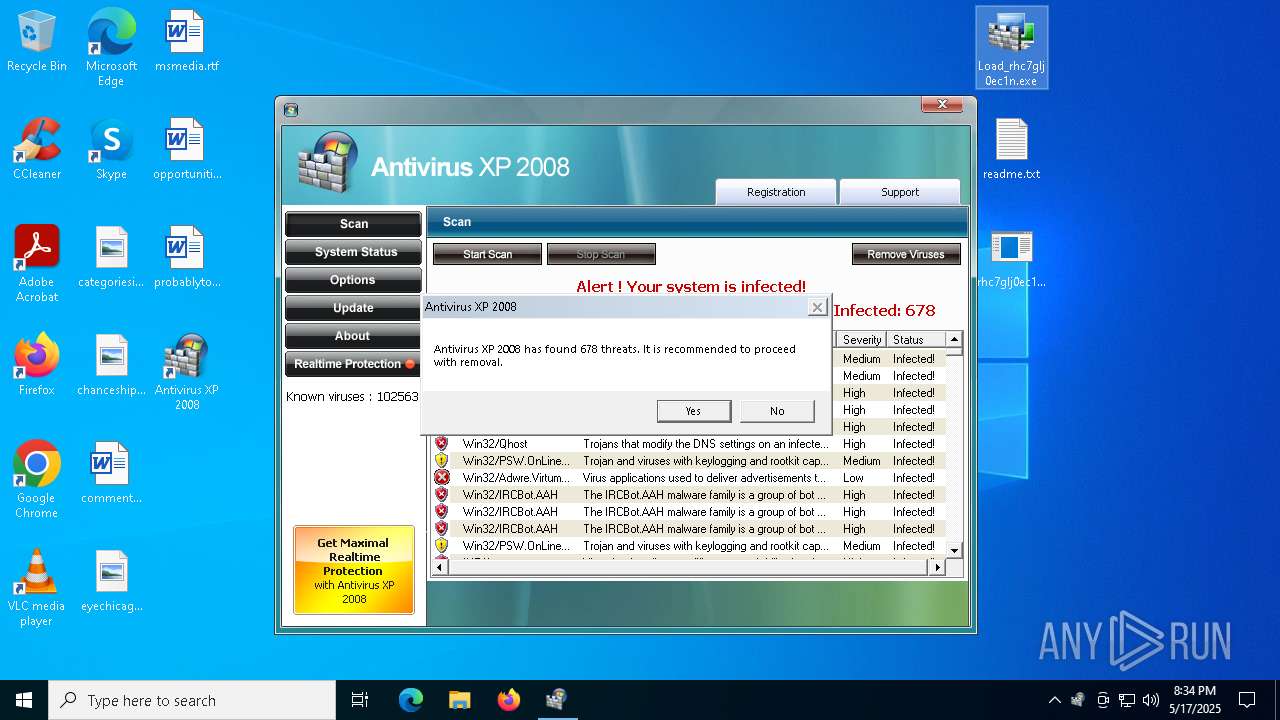
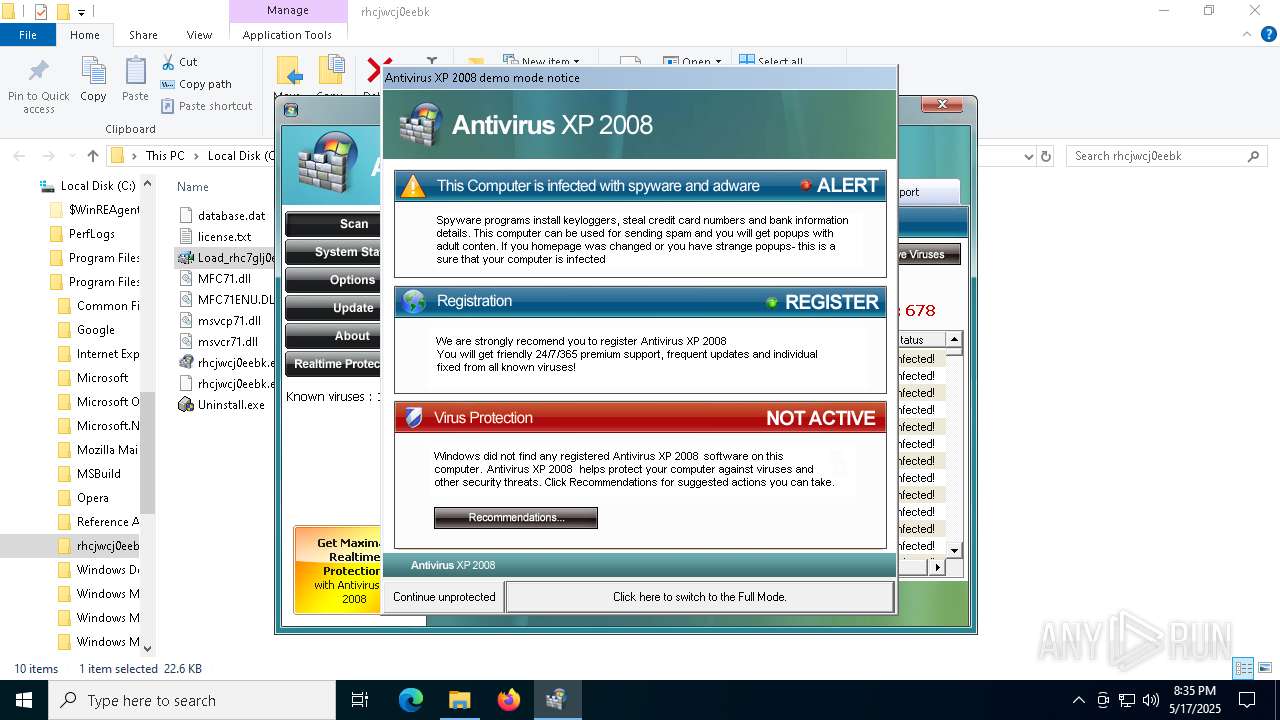
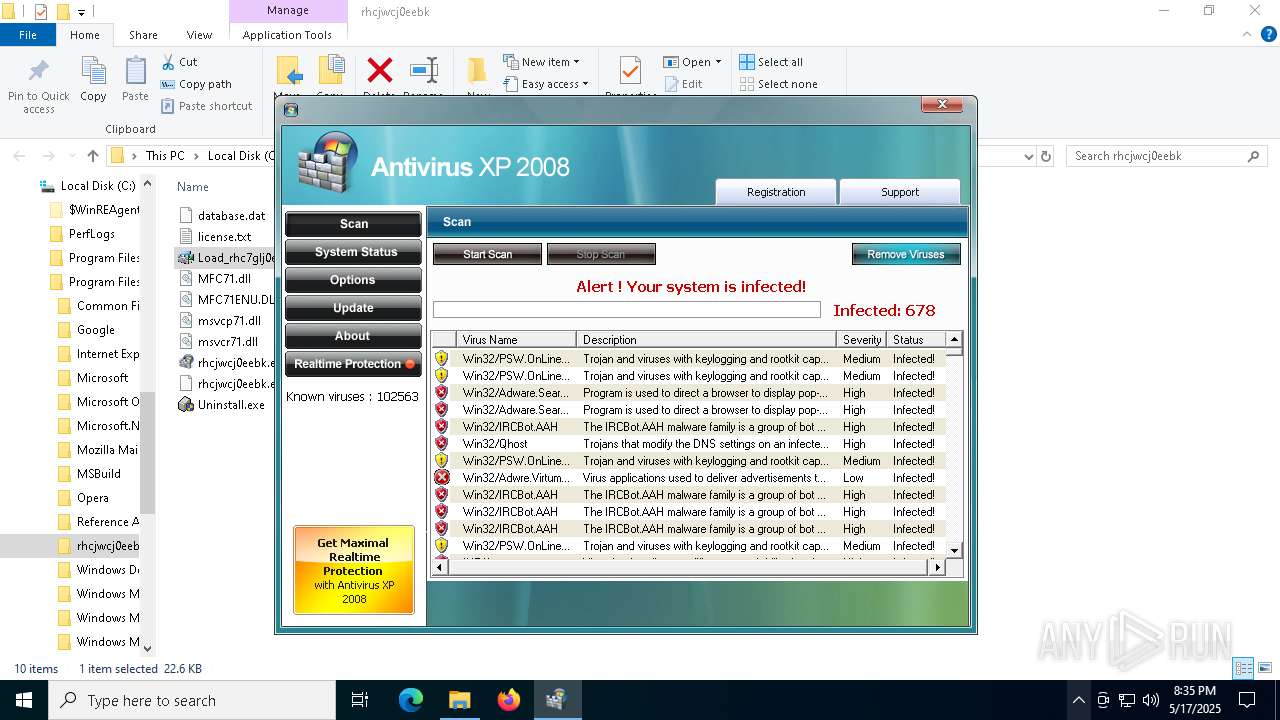
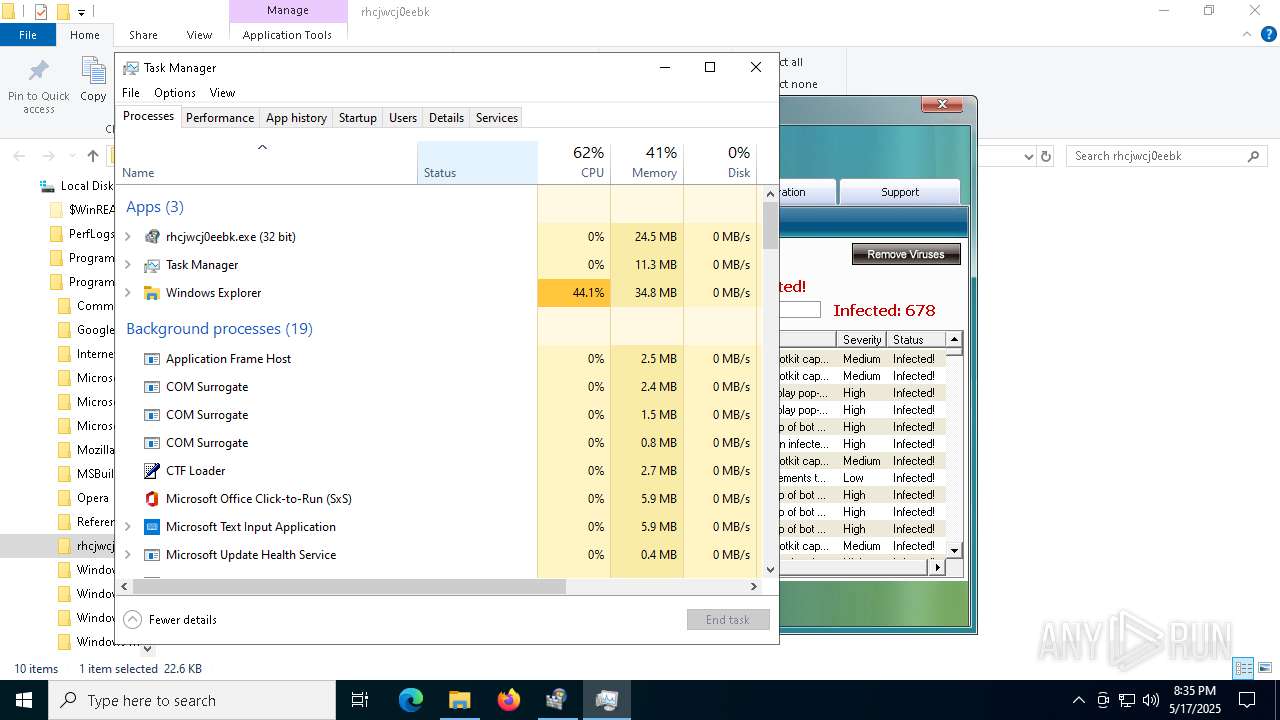
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5548)
- WinRAR.exe (PID: 9056)
Process drops legitimate windows executable
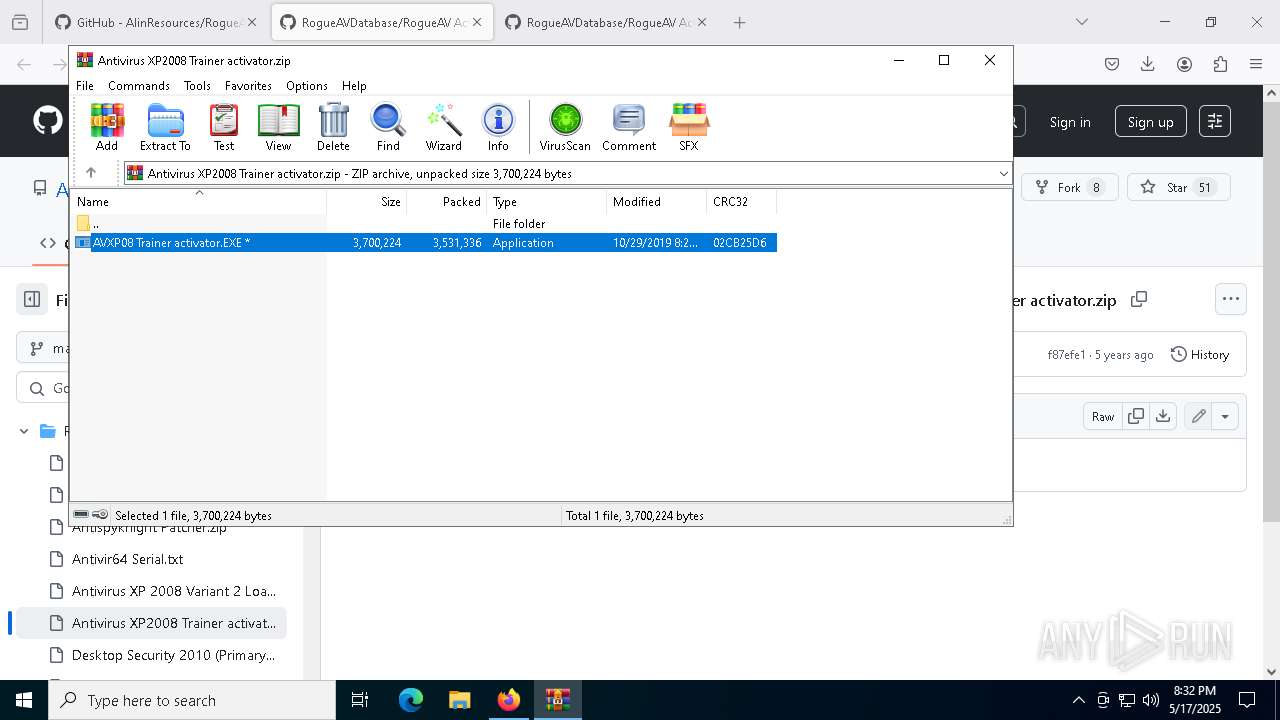
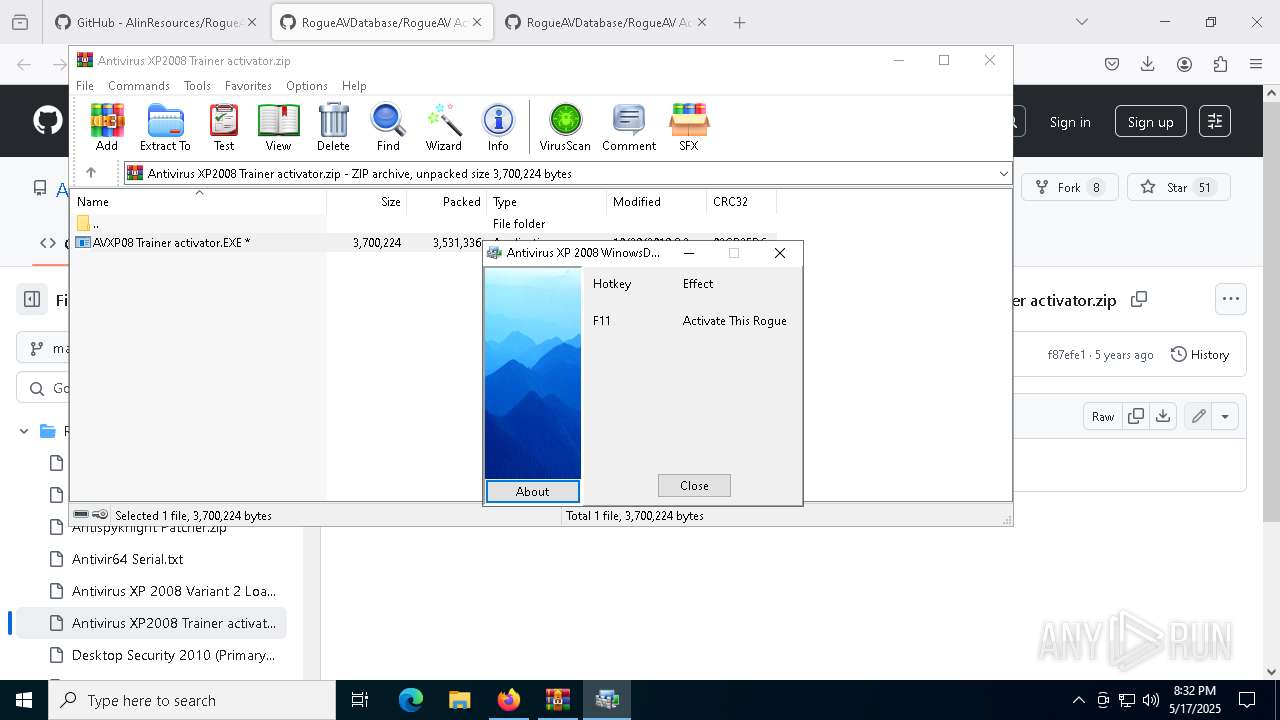
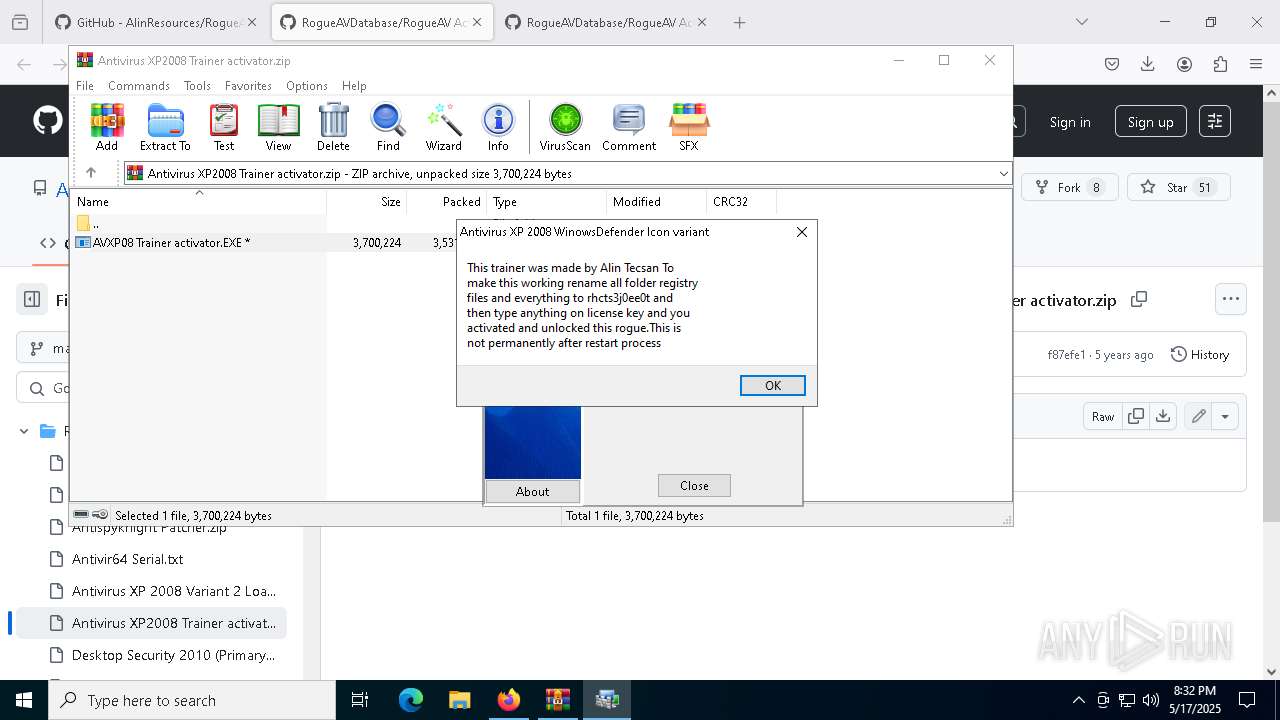
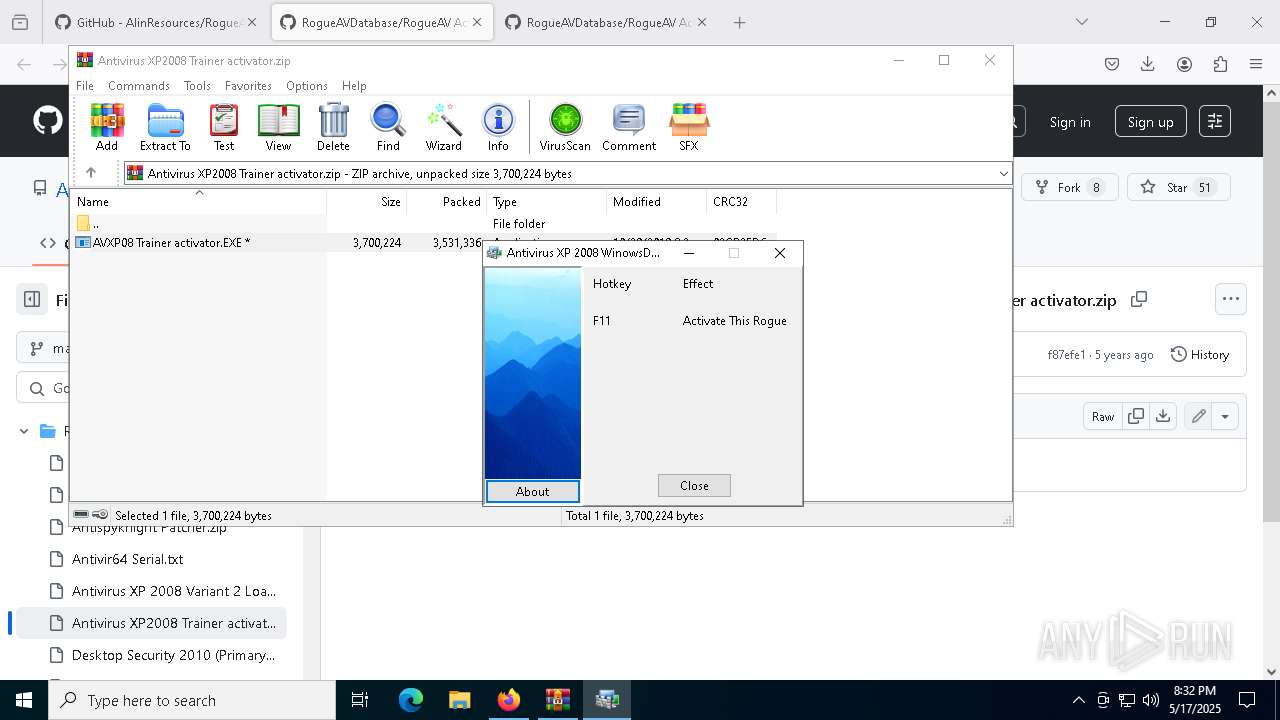
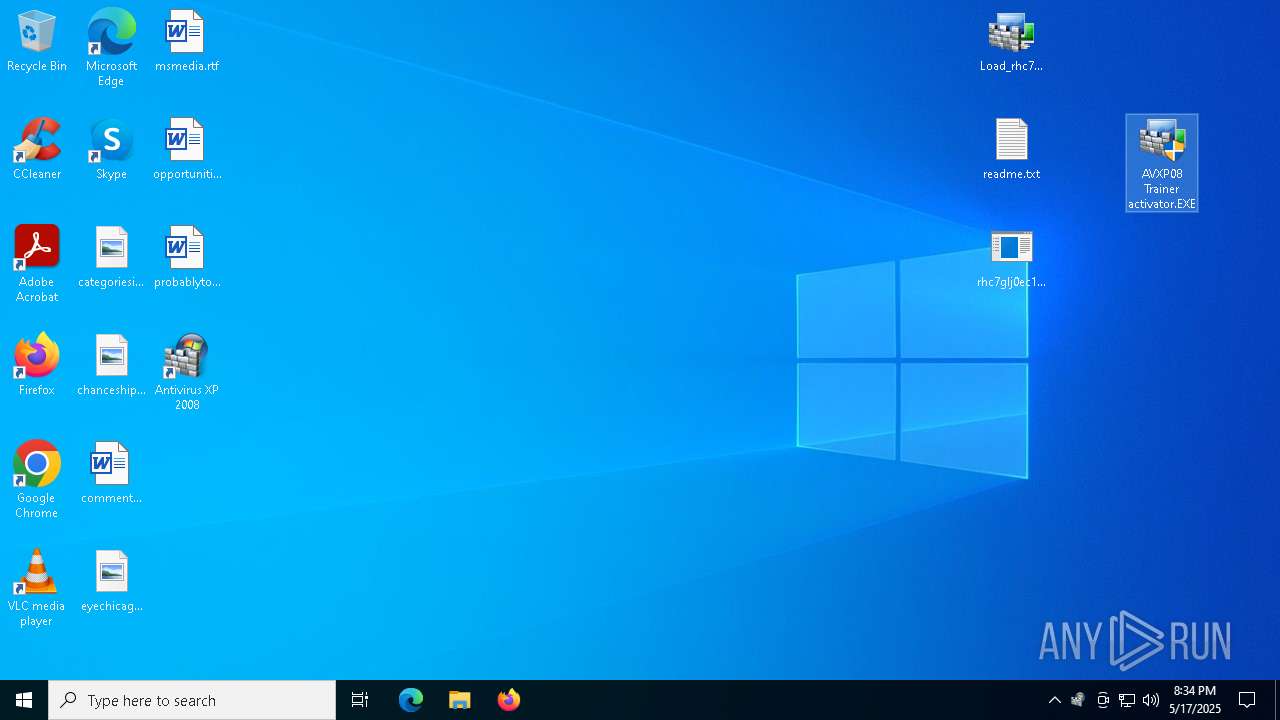
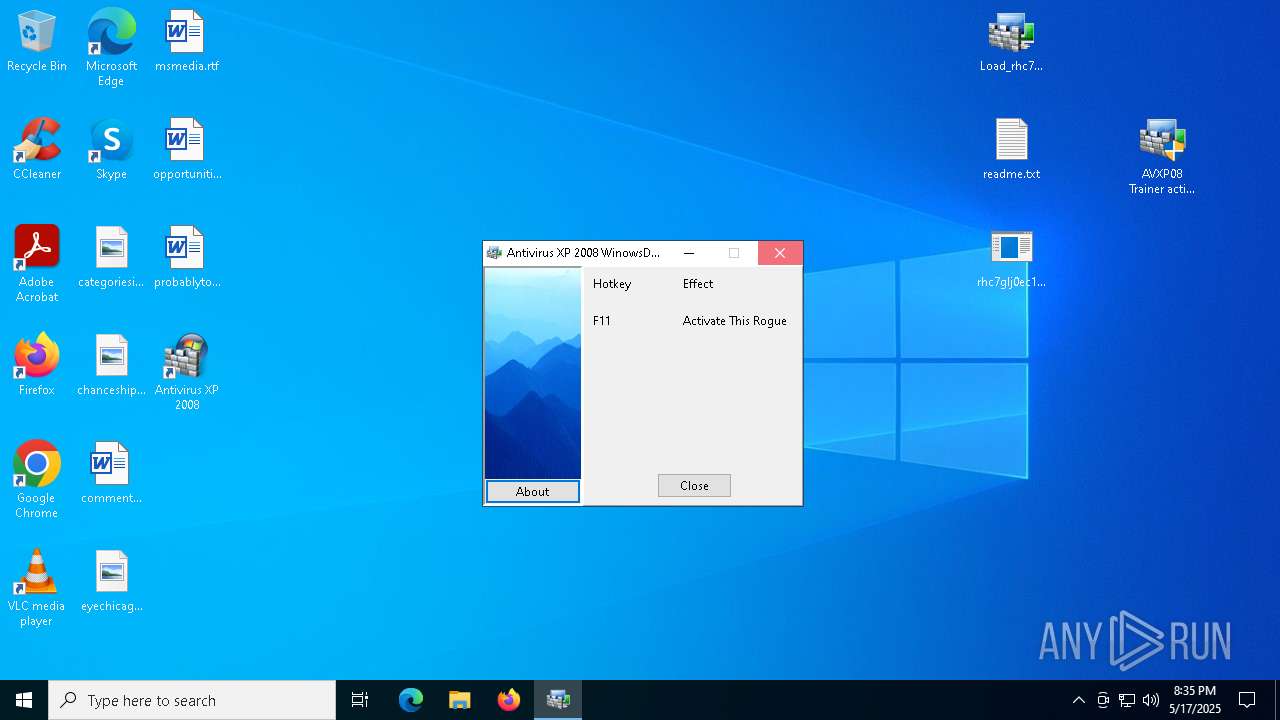
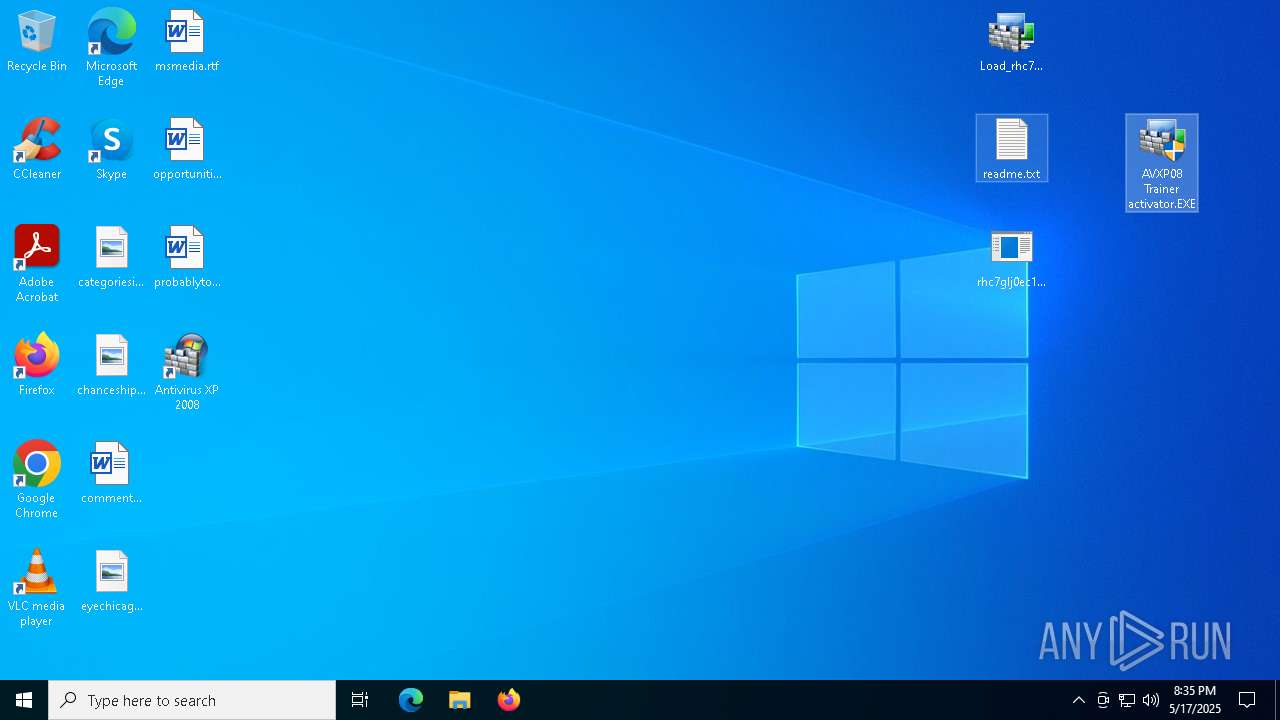
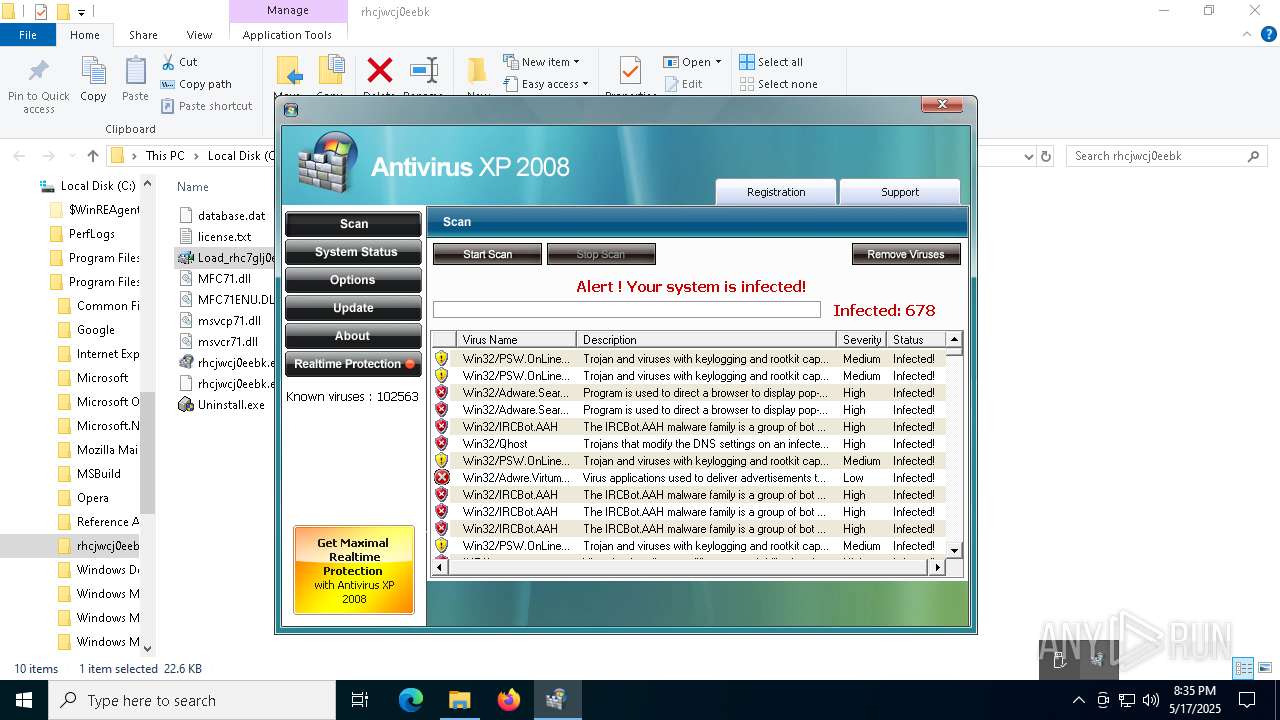
- AVXP08 Trainer activator.EXE (PID: 8936)
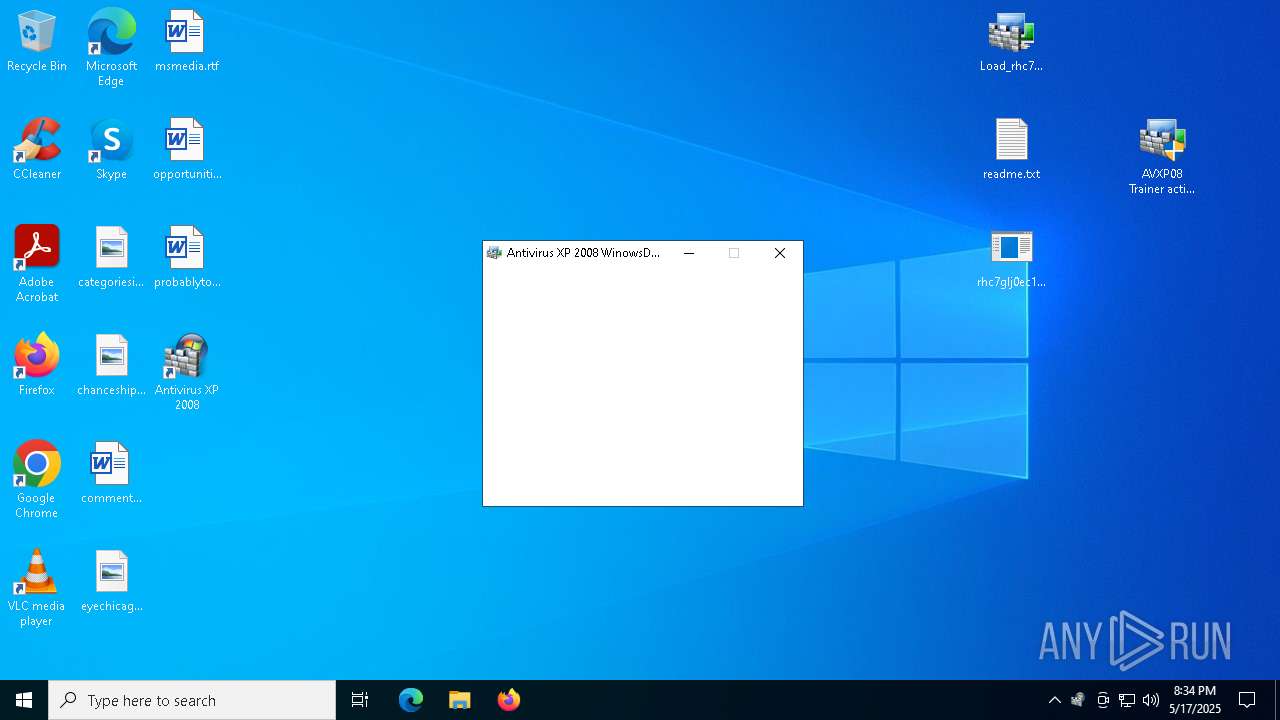
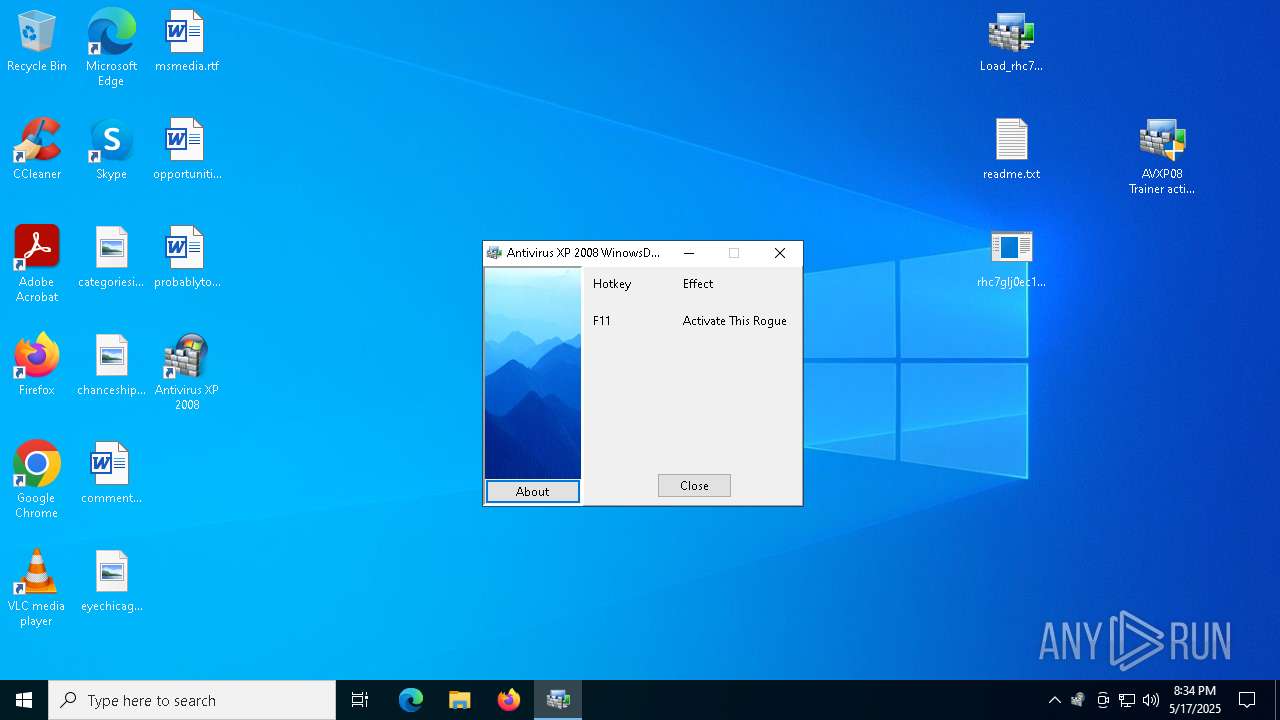
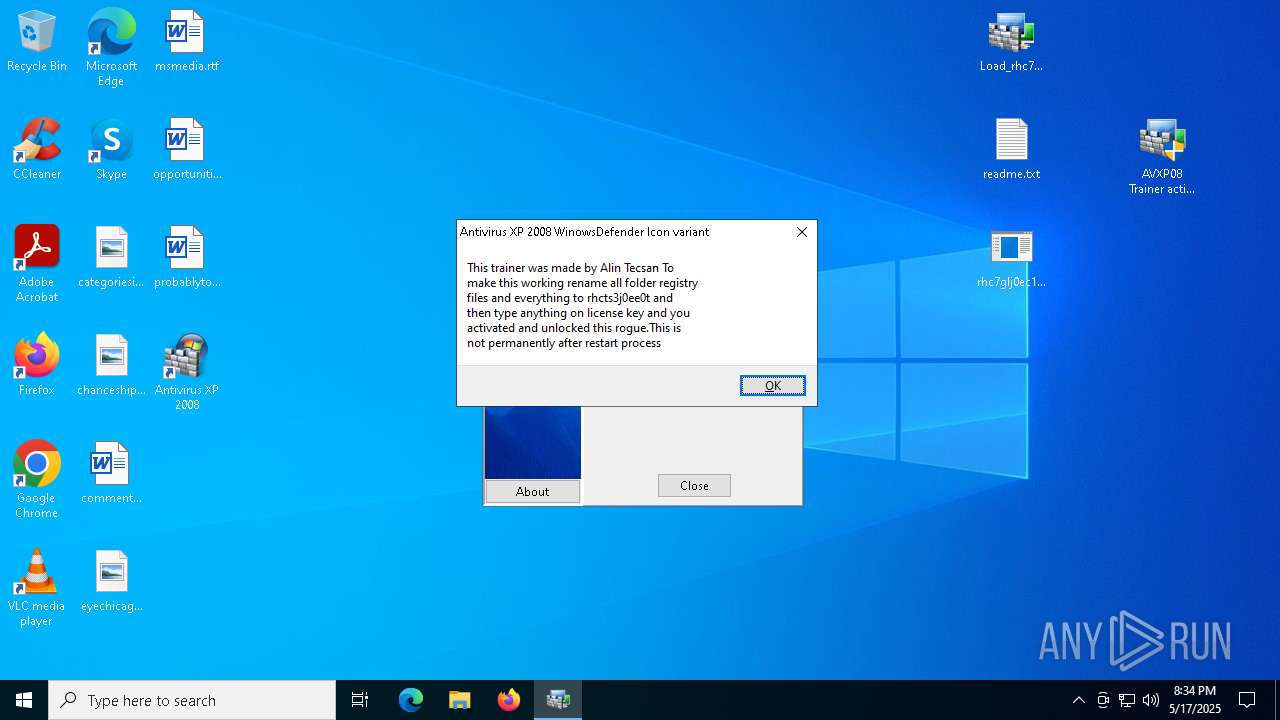
- Endermanch@XPAntivirus2008.exe (PID: 8160)
- AVXP08 Trainer activator.EXE (PID: 7552)
There is functionality for taking screenshot (YARA)
- AVXP08 Trainer activator.EXE (PID: 7544)
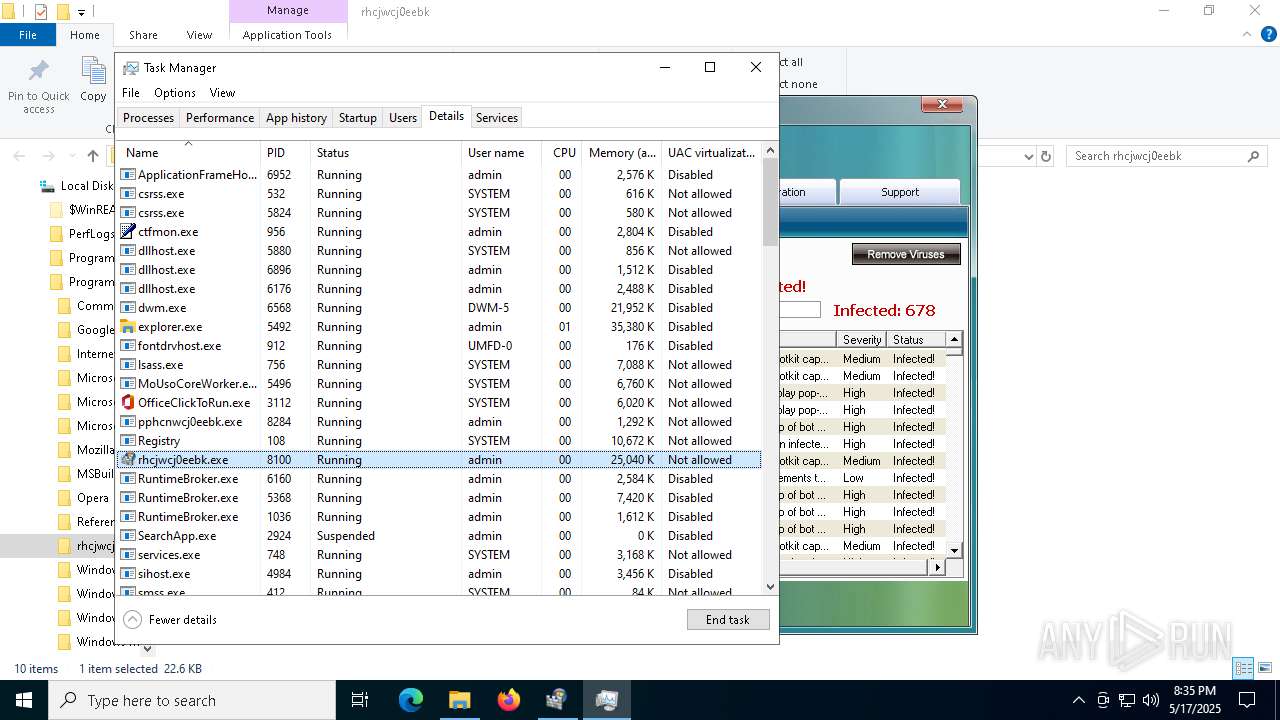
- rhcjwcj0eebk.exe (PID: 8100)
- AVXP08 Trainer activator.EXE (PID: 7608)
Executes application which crashes
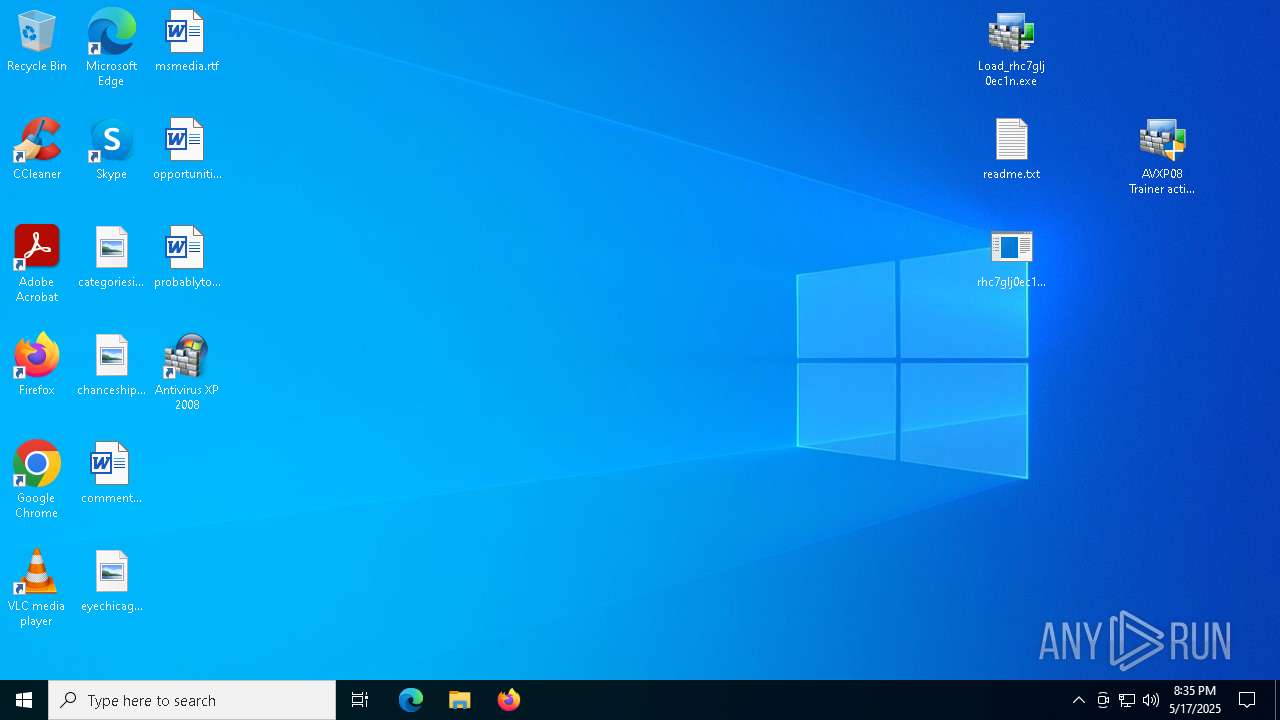
- rhc7glj0ec1n.exe (PID: 812)
- rhc7glj0ec1n.exe (PID: 5384)
- rhc7glj0ec1n.exe (PID: 968)
- rhc7glj0ec1n.exe (PID: 8700)
- rhc7glj0ec1n.exe (PID: 7560)
- rhc7glj0ec1n.exe (PID: 6944)
Starts CMD.EXE for commands execution
- Endermanch@XPAntivirus2008.exe (PID: 8160)
The process drops C-runtime libraries
- Endermanch@XPAntivirus2008.exe (PID: 8160)
Executing commands from a ".bat" file
- Endermanch@XPAntivirus2008.exe (PID: 8160)
Executable content was dropped or overwritten
- Endermanch@XPAntivirus2008.exe (PID: 8160)
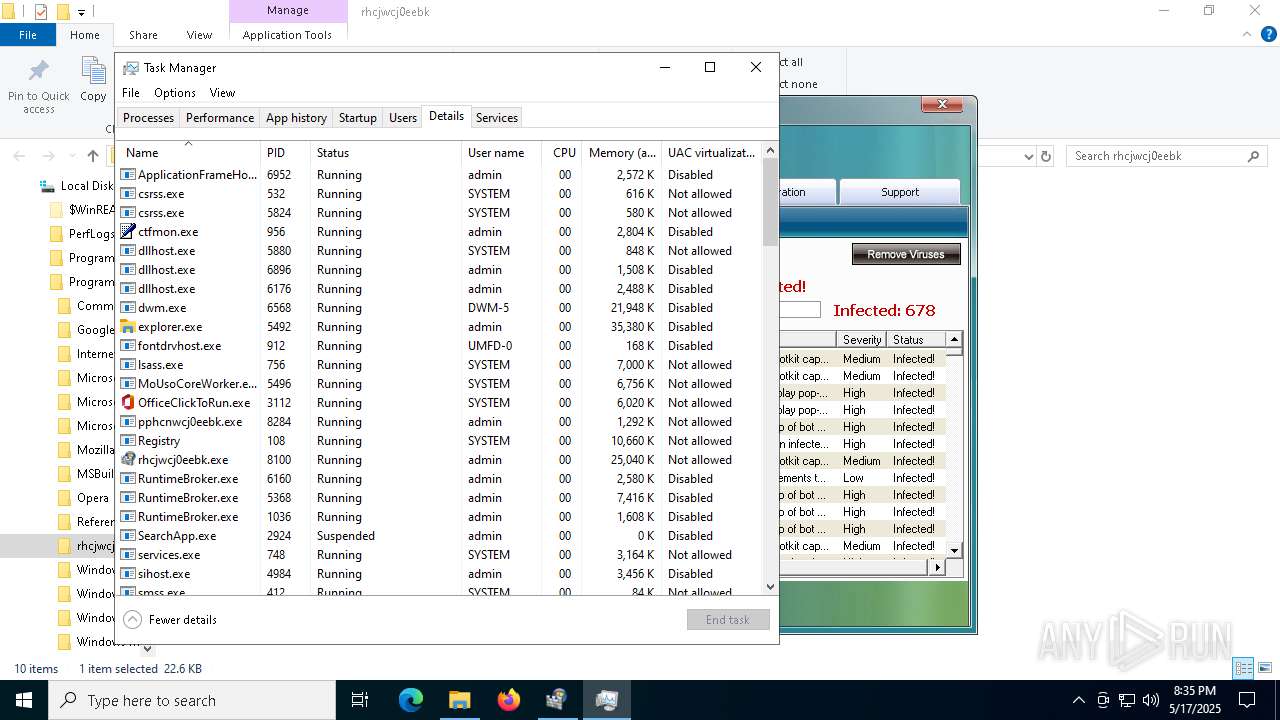
- rhcjwcj0eebk.exe (PID: 8100)
- AVXP08 Trainer activator.EXE (PID: 7828)
- AVXP08 Trainer activator.EXE (PID: 7552)
- dllhost.exe (PID: 5512)
- dllhost.exe (PID: 7808)
- AVXP08 Trainer activator.EXE (PID: 8200)
- AVXP08 Trainer activator.EXE (PID: 8936)
The process executes VB scripts
- Endermanch@XPAntivirus2008.exe (PID: 8160)
There is functionality for communication over UDP network (YARA)
- AVXP08 Trainer activator.EXE (PID: 7608)
INFO
Application launched itself
- firefox.exe (PID: 7492)
- firefox.exe (PID: 7512)
- firefox.exe (PID: 7148)
- firefox.exe (PID: 4408)
Reads the software policy settings
- slui.exe (PID: 8420)
Manual execution by a user
- WinRAR.exe (PID: 5548)
- WinRAR.exe (PID: 9056)
- rhc7glj0ec1n.exe (PID: 968)
- notepad.exe (PID: 8480)
- Load_rhc7glj0ec1n.exe (PID: 3332)
- firefox.exe (PID: 4408)
- WinRAR.exe (PID: 8636)
- Endermanch@XPAntivirus2008.exe (PID: 9172)
- Endermanch@XPAntivirus2008.exe (PID: 8160)
- Load_rhc7glj0ec1n.exe (PID: 6668)
- WinRAR.exe (PID: 7916)
- AVXP08 Trainer activator.EXE (PID: 7860)
- AVXP08 Trainer activator.EXE (PID: 7828)
- notepad.exe (PID: 1300)
- Load_rhc7glj0ec1n.exe (PID: 8552)
- Taskmgr.exe (PID: 9104)
- Load_rhc7glj0ec1n.exe (PID: 8956)
- Load_rhc7glj0ec1n.exe (PID: 9000)
- notepad.exe (PID: 8576)
- rhc7glj0ec1n.exe (PID: 6944)
- Taskmgr.exe (PID: 2772)
- Load_rhc7glj0ec1n.exe (PID: 900)
Checks supported languages
- AVXP08 Trainer activator.EXE (PID: 8200)
- AVXP08 Trainer activator.EXE (PID: 7544)
- Load_rhc7glj0ec1n.exe (PID: 9036)
- AVXP08 Trainer activator.EXE (PID: 8936)
Reads the computer name
- AVXP08 Trainer activator.EXE (PID: 8200)
- Load_rhc7glj0ec1n.exe (PID: 9036)
- AVXP08 Trainer activator.EXE (PID: 7544)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5548)
- WinRAR.exe (PID: 9056)
- WinRAR.exe (PID: 8636)
- WinRAR.exe (PID: 7916)
Create files in a temporary directory
- AVXP08 Trainer activator.EXE (PID: 8200)
- AVXP08 Trainer activator.EXE (PID: 8936)
The sample compiled with english language support
- Endermanch@XPAntivirus2008.exe (PID: 8160)
- AVXP08 Trainer activator.EXE (PID: 7552)
- AVXP08 Trainer activator.EXE (PID: 8936)
The process uses Lua
- AVXP08 Trainer activator.EXE (PID: 7608)
Compiled with Borland Delphi (YARA)
- AVXP08 Trainer activator.EXE (PID: 7608)
- AVXP08 Trainer activator.EXE (PID: 7544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
227
Monitored processes
74
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5212 -childID 3 -isForBrowser -prefsHandle 5200 -prefMapHandle 2176 -prefsLen 31321 -prefMapSize 244591 -jsInitHandle 1444 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {fca087c8-30d3-40f6-b196-8077c85e2845} 7148 "\\.\pipe\gecko-crash-server-pipe.7148" 20f89b84850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 616 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | "C:\Users\admin\Desktop\rhc7glj0ec1n.exe" /avxp08crack | C:\Users\admin\Desktop\rhc7glj0ec1n.exe | Load_rhc7glj0ec1n.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 900 | "C:\Program Files (x86)\rhcjwcj0eebk\Load_rhc7glj0ec1n.exe" "C:\Program Files (x86)\rhcjwcj0eebk\rhcjwcj0eebk.exe" | C:\Program Files (x86)\rhcjwcj0eebk\Load_rhc7glj0ec1n.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 968 | "C:\Users\admin\Desktop\rhc7glj0ec1n.exe" | C:\Users\admin\Desktop\rhc7glj0ec1n.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
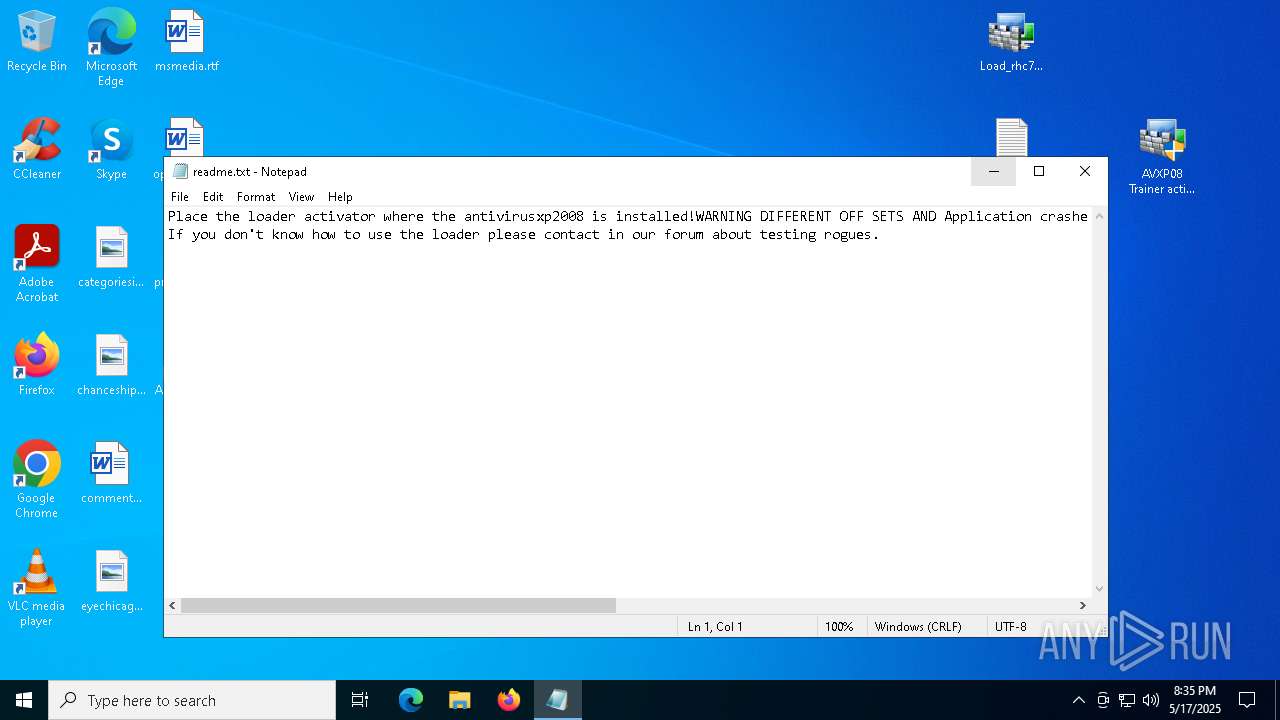
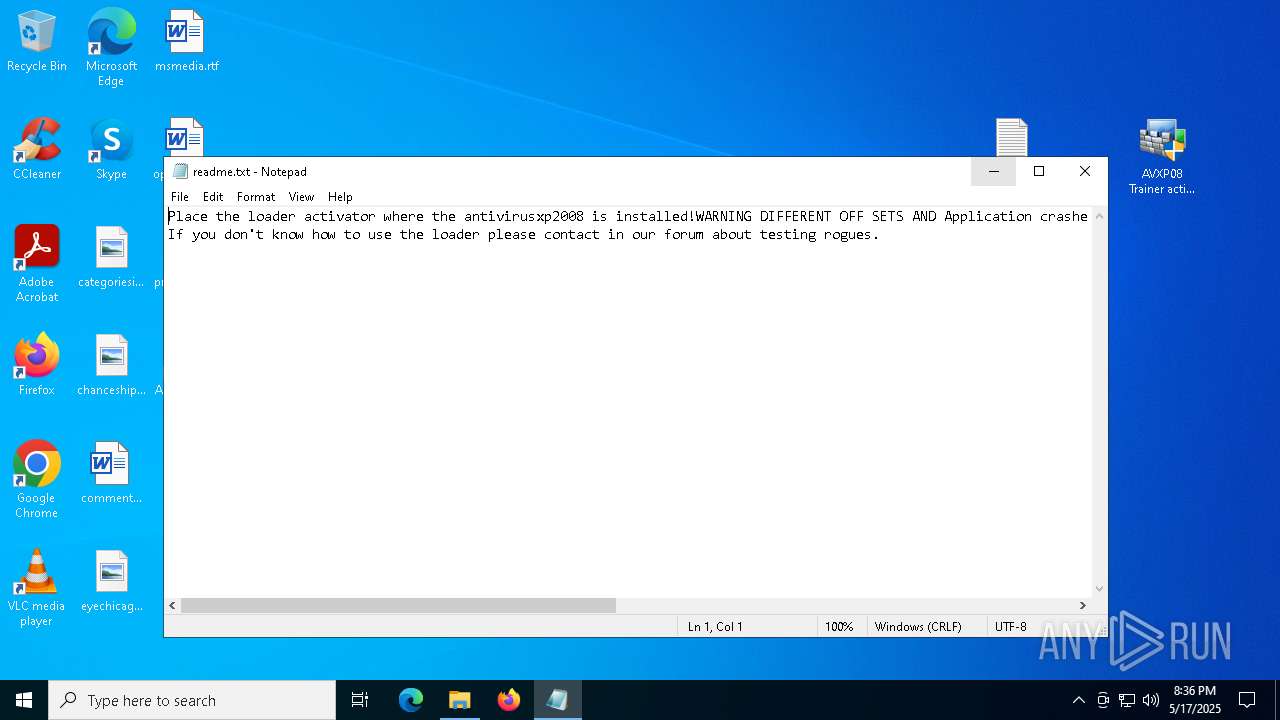
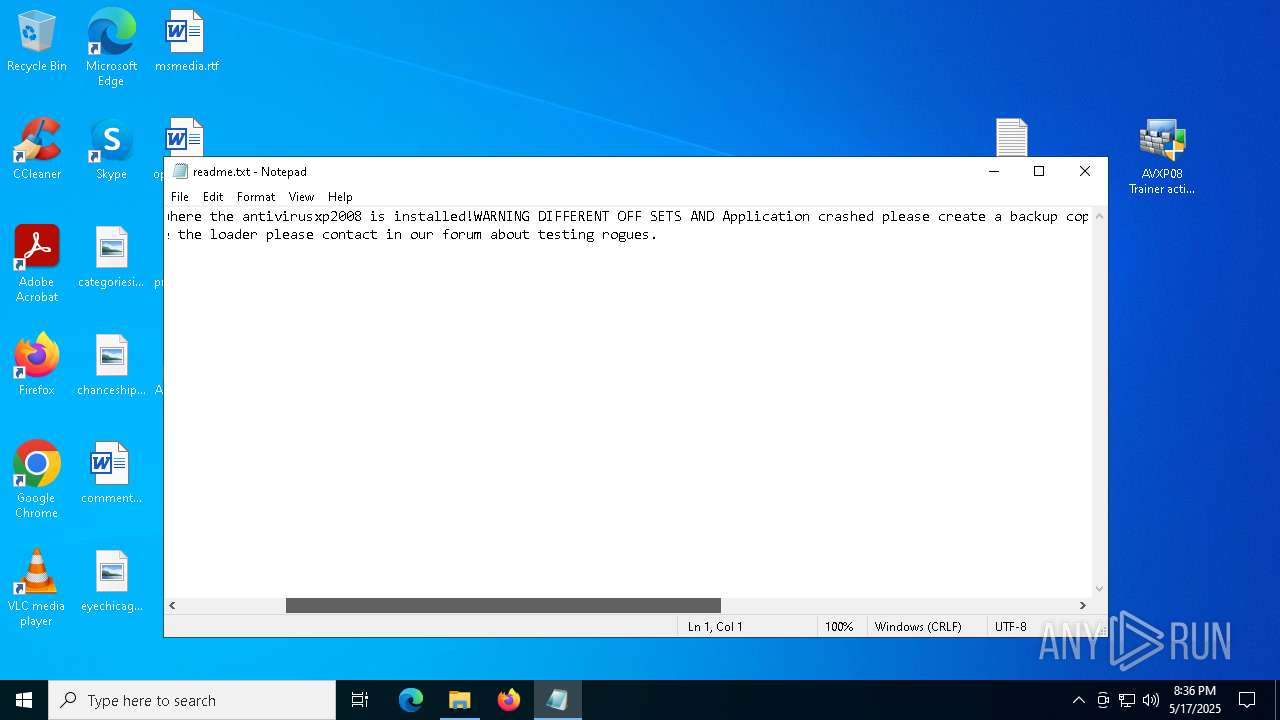
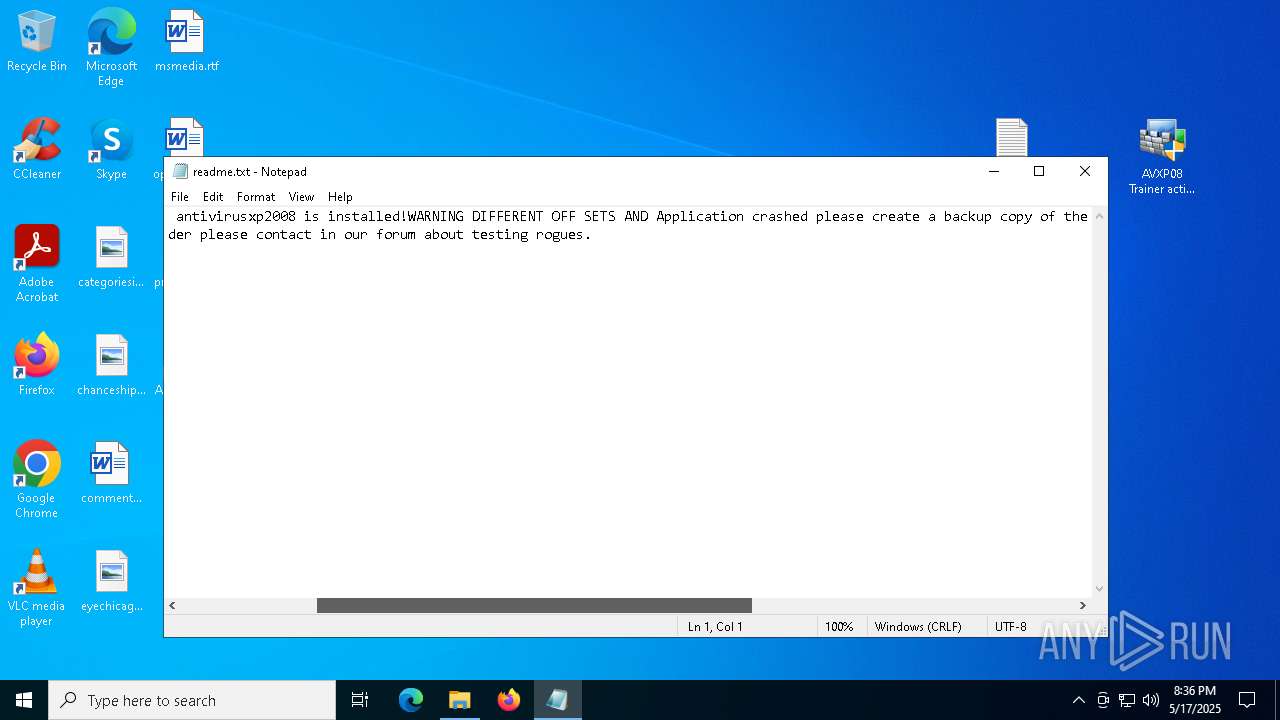
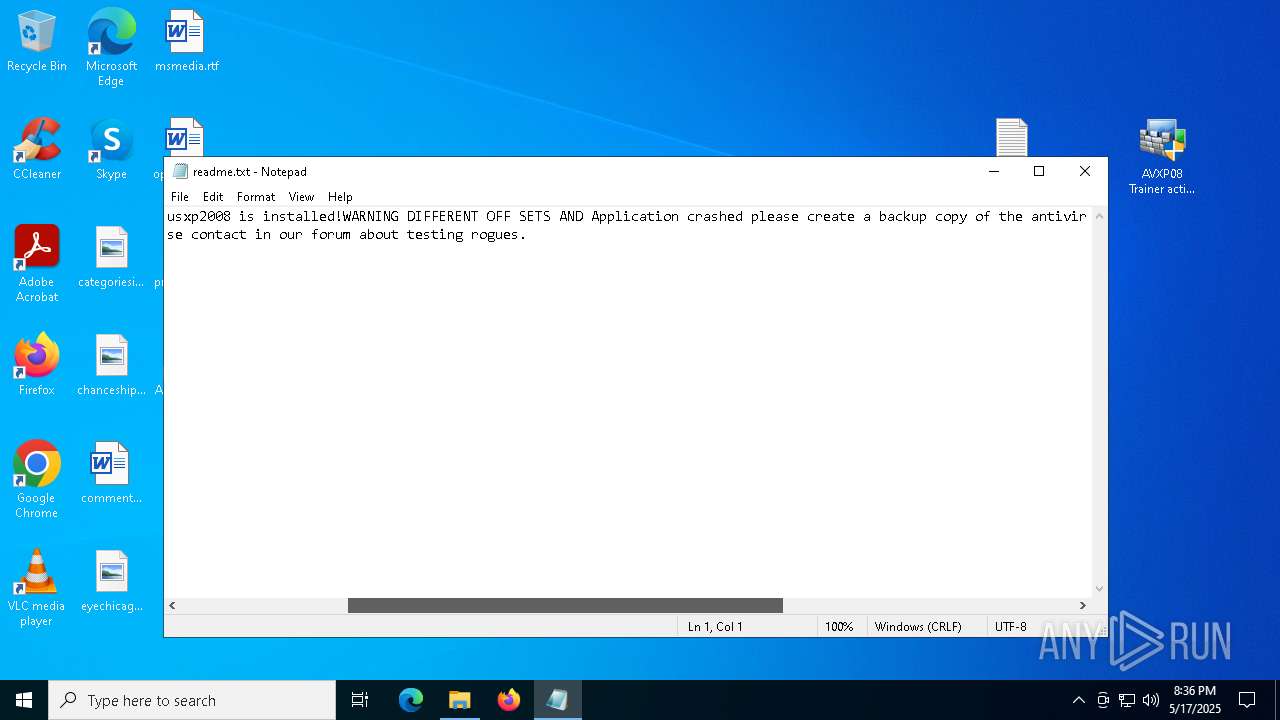
| 1300 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\readme.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3032 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=3184 -childID 1 -isForBrowser -prefsHandle 3076 -prefMapHandle 3160 -prefsLen 32716 -prefMapSize 244591 -jsInitHandle 1444 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {24ce2ffd-4fcc-4621-9c34-818ed752d911} 7148 "\\.\pipe\gecko-crash-server-pipe.7148" 20f83ddcf50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 3332 | "C:\Users\admin\Desktop\Load_rhc7glj0ec1n.exe" | C:\Users\admin\Desktop\Load_rhc7glj0ec1n.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4040 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1884 -parentBuildID 20240213221259 -prefsHandle 1824 -prefMapHandle 1816 -prefsLen 32300 -prefMapSize 244591 -appDir "C:\Program Files\Mozilla Firefox\browser" - {b8f7db22-2a0e-4cd7-8d16-f8ae4edba128} 7148 "\\.\pipe\gecko-crash-server-pipe.7148" 20ffefea710 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
Total events
51 805
Read events
51 661
Write events
142
Delete events
2
Modification events
| (PID) Process: | (7512) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
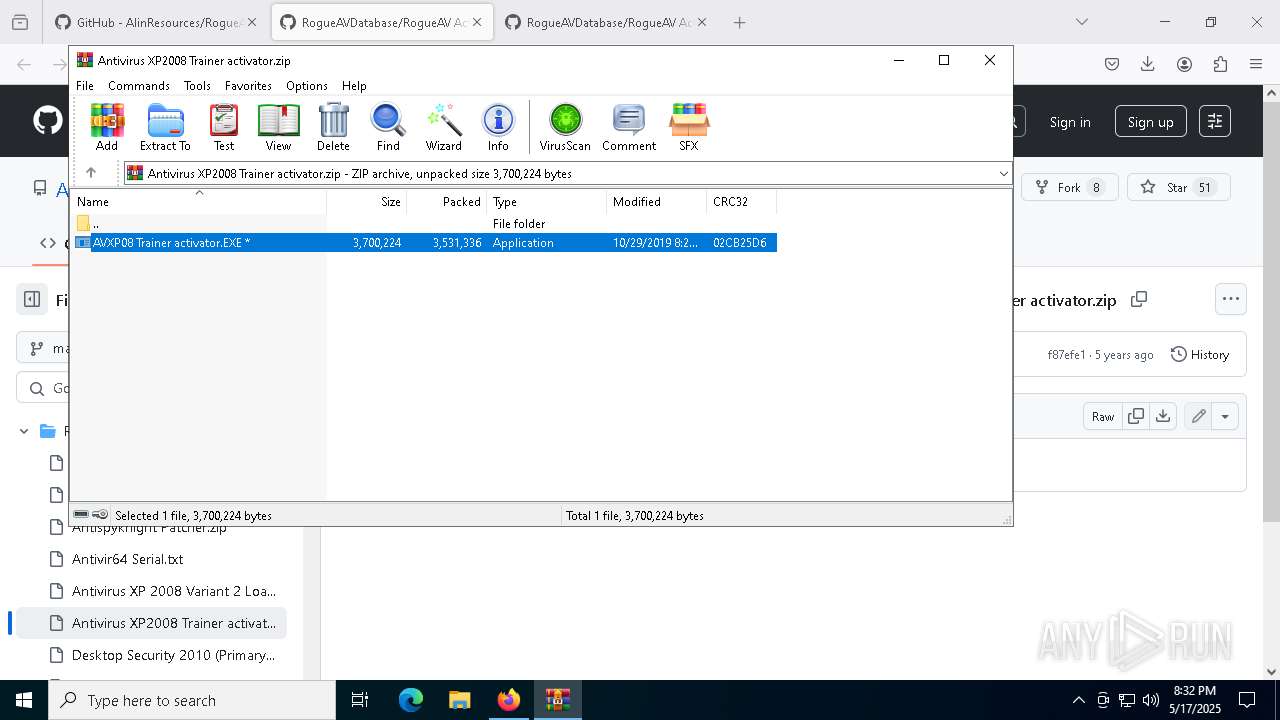
Value: C:\Users\admin\Downloads\Antivirus XP2008 Trainer activator.zip | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
29
Suspicious files
280
Text files
47
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7512 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7512 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 7512 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7512 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7512 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 7512 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 7512 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 7512 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7512 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 7512 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:CF89BF2D8A5104F008782353E042AA8D | SHA256:7203A54525BCD07566B1144DEA5C1ABFC9307871CCCD6961B9BB6A293783C9DB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
49
TCP/UDP connections
125
DNS requests
193
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7512 | firefox.exe | POST | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/ | unknown | — | — | whitelisted |
7512 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7512 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7512 | firefox.exe | POST | 200 | 184.24.77.45:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7512 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
7512 | firefox.exe | POST | 200 | 184.24.77.45:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7512 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.37:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7512 | firefox.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
7512 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
7512 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
github.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
example.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |