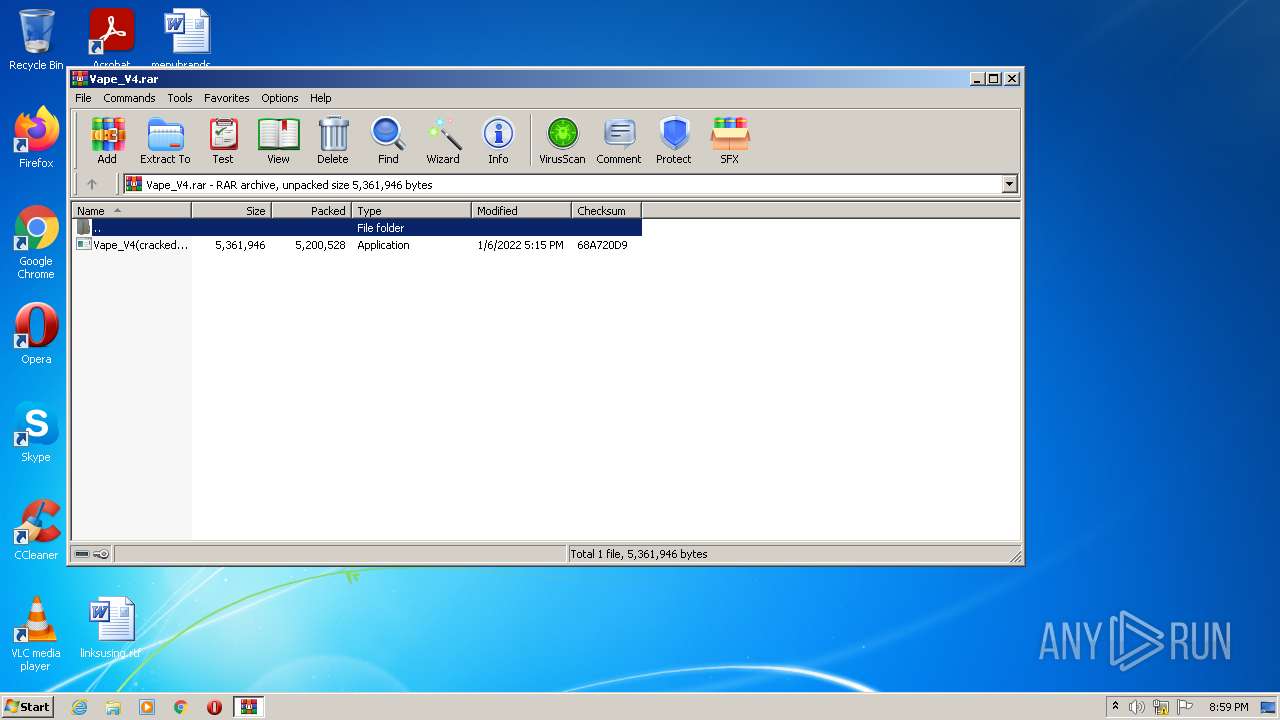
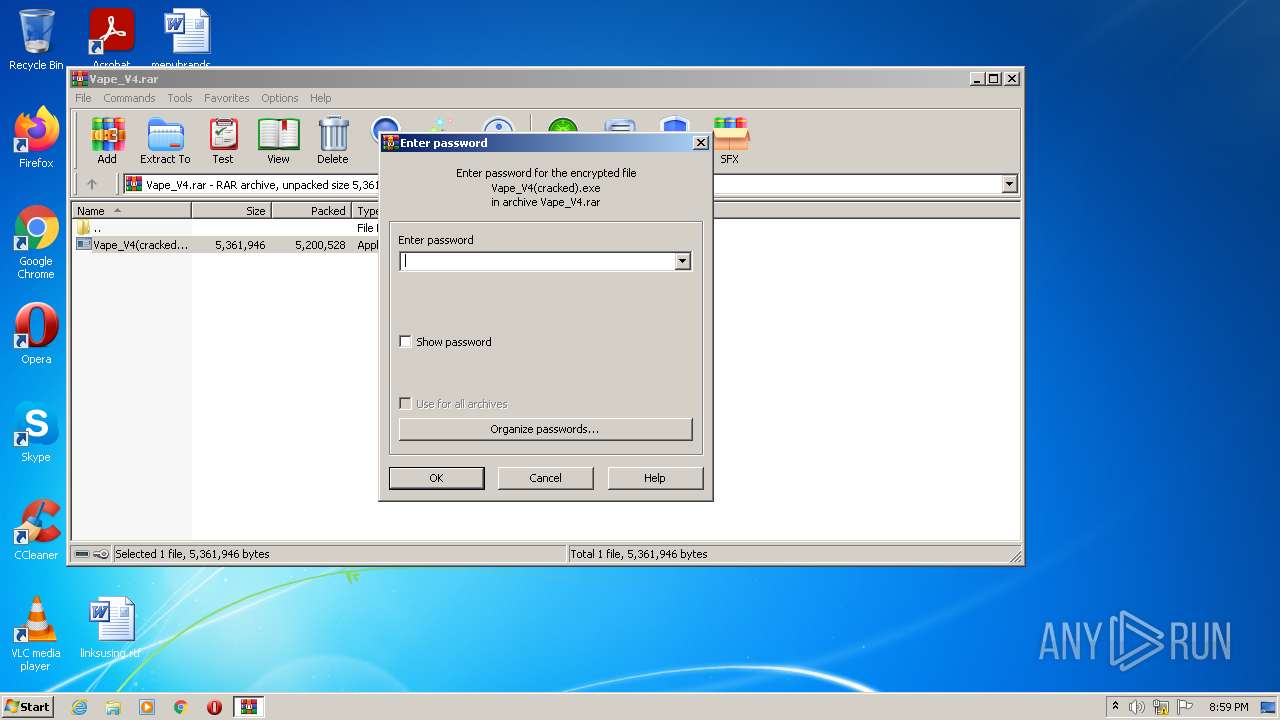
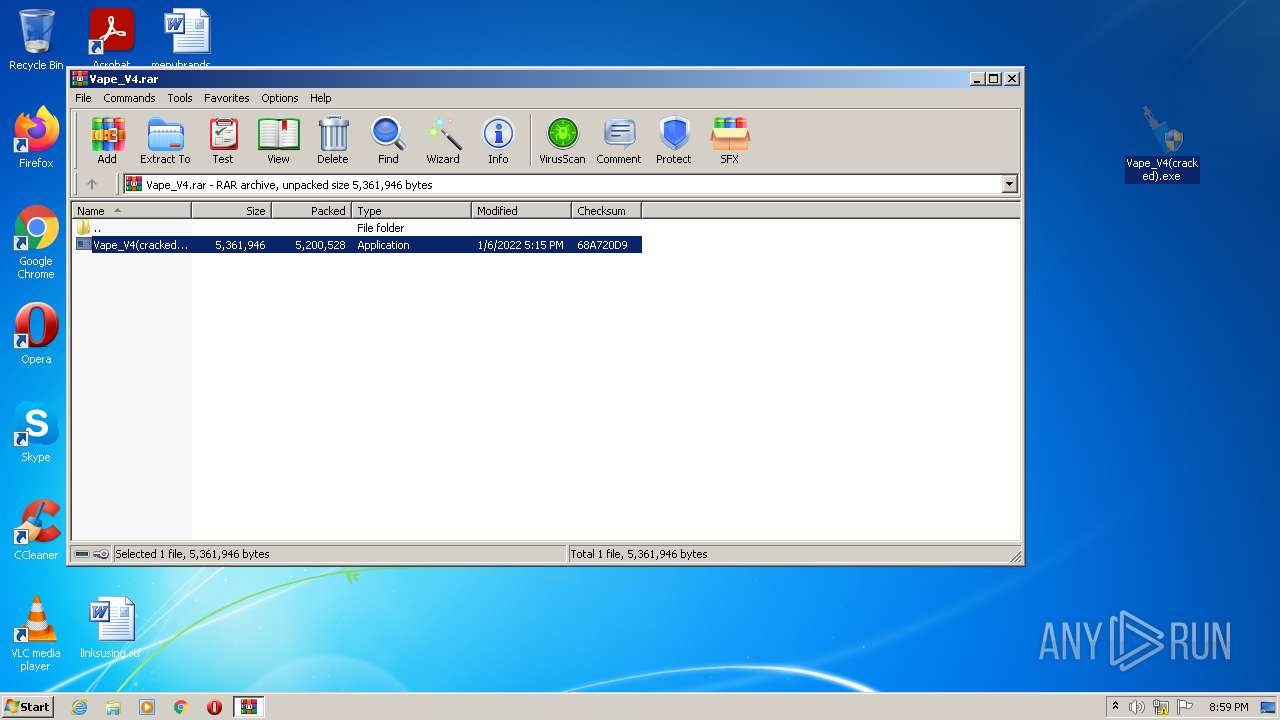
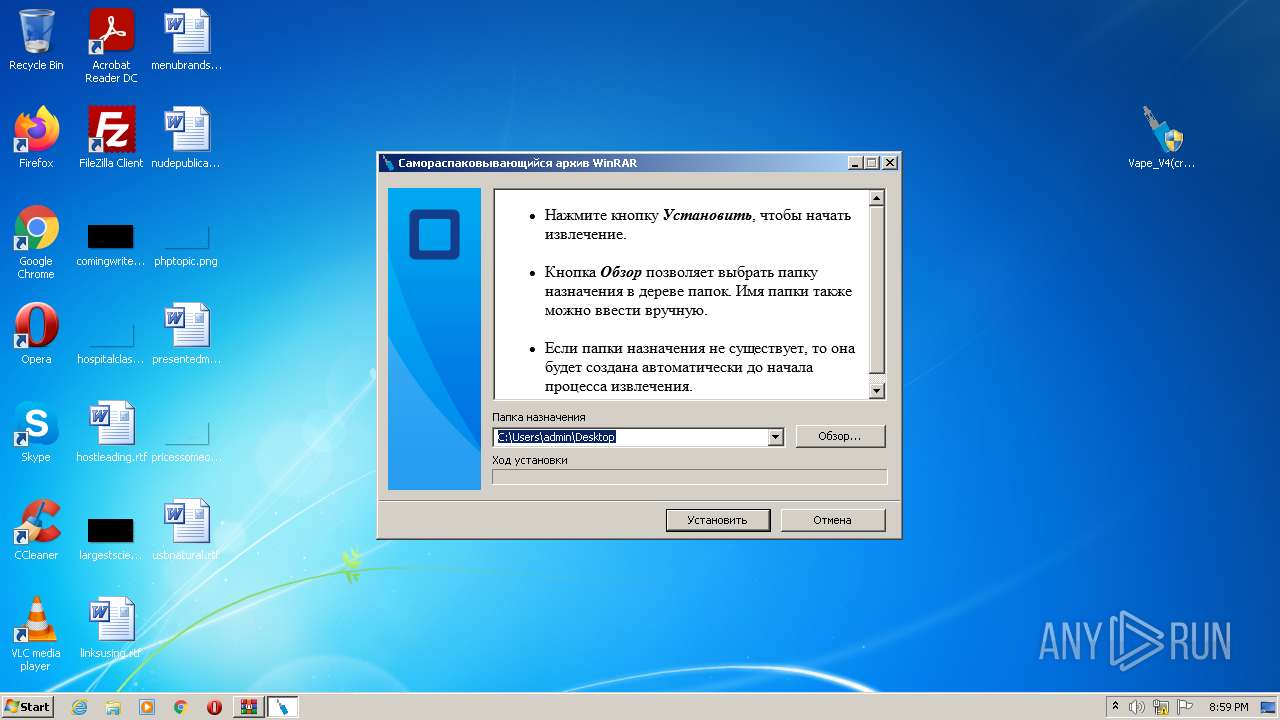
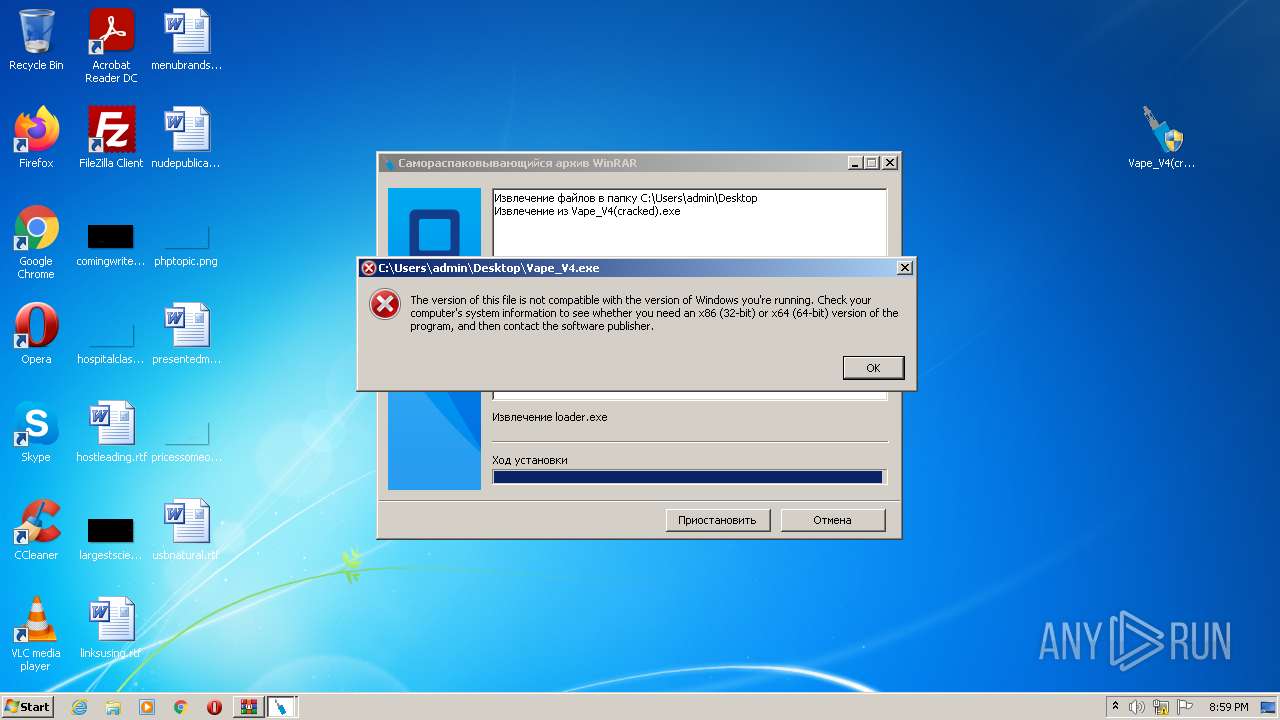
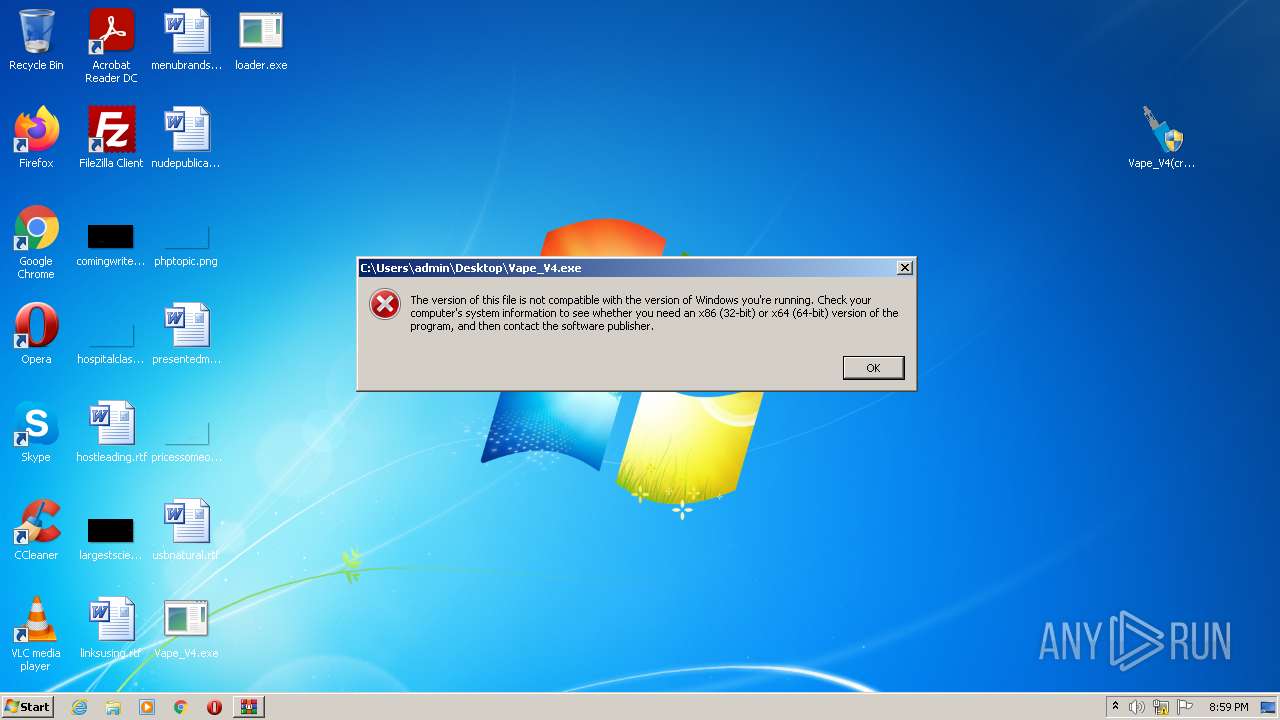
| File name: | Vape_V4.rar |
| Full analysis: | https://app.any.run/tasks/50b715ff-a646-4805-8a4d-19cd583d071d |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2022, 20:58:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C6ACE39B722D1D8FA5801CECA23CA2FF |
| SHA1: | E6603C1B451F7AEC0B329EEE501E8ADD56F26315 |
| SHA256: | 568C27822F2CA179D30BEFEFD84735277BBA8283F1F3D35C127B82DE7AD2658D |
| SSDEEP: | 98304:mMQ6ohtFTElSCfueK/0oL93WHB9XbcjINOtd1MZgSN6iNVWpP:mMQjttELI8GlKBO0NOtdBBP |
MALICIOUS
Application was dropped or rewritten from another process
- Vape_V4(cracked).exe (PID: 2940)
- Vape_V4(cracked).exe (PID: 1324)
- loader.exe (PID: 1088)
- loader.exe (PID: 2100)
- loader.exe (PID: 4004)
- loader.exe (PID: 3088)
- loader.exe (PID: 3280)
- loader.exe (PID: 2288)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 612)
- Vape_V4(cracked).exe (PID: 1324)
- loader.exe (PID: 1088)
- loader.exe (PID: 2100)
- loader.exe (PID: 4004)
- loader.exe (PID: 3088)
- loader.exe (PID: 3280)
- loader.exe (PID: 2288)
Checks supported languages
- WinRAR.exe (PID: 612)
- Vape_V4(cracked).exe (PID: 1324)
- loader.exe (PID: 1088)
- loader.exe (PID: 3088)
- loader.exe (PID: 4004)
- loader.exe (PID: 2100)
- loader.exe (PID: 2288)
- loader.exe (PID: 3280)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 612)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 612)
- Vape_V4(cracked).exe (PID: 1324)
Reads Microsoft Outlook installation path
- Vape_V4(cracked).exe (PID: 1324)
Reads internet explorer settings
- Vape_V4(cracked).exe (PID: 1324)
Drops a file with a compile date too recent
- Vape_V4(cracked).exe (PID: 1324)
Reads Environment values
- loader.exe (PID: 1088)
- loader.exe (PID: 3088)
- loader.exe (PID: 2100)
- loader.exe (PID: 4004)
- loader.exe (PID: 3280)
INFO
Manual execution by user
- Vape_V4(cracked).exe (PID: 2940)
- Vape_V4(cracked).exe (PID: 1324)
- loader.exe (PID: 3088)
- loader.exe (PID: 2100)
- loader.exe (PID: 4004)
- loader.exe (PID: 2288)
- loader.exe (PID: 3280)
Reads settings of System Certificates
- loader.exe (PID: 1088)
- loader.exe (PID: 3088)
- loader.exe (PID: 2100)
- loader.exe (PID: 3280)
- loader.exe (PID: 4004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
47
Monitored processes
9
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 612 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Vape_V4.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1088 | "C:\Users\admin\Desktop\loader.exe" | C:\Users\admin\Desktop\loader.exe | Vape_V4(cracked).exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1324 | "C:\Users\admin\Desktop\Vape_V4(cracked).exe" | C:\Users\admin\Desktop\Vape_V4(cracked).exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2100 | "C:\Users\admin\Desktop\loader.exe" | C:\Users\admin\Desktop\loader.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2288 | "C:\Users\admin\Desktop\loader.exe" | C:\Users\admin\Desktop\loader.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2940 | "C:\Users\admin\Desktop\Vape_V4(cracked).exe" | C:\Users\admin\Desktop\Vape_V4(cracked).exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3088 | "C:\Users\admin\Desktop\loader.exe" | C:\Users\admin\Desktop\loader.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3280 | "C:\Users\admin\Desktop\loader.exe" | C:\Users\admin\Desktop\loader.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 4004 | "C:\Users\admin\Desktop\loader.exe" | C:\Users\admin\Desktop\loader.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
17 555
Read events
17 443
Write events
112
Delete events
0
Modification events
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Vape_V4.rar | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1324 | Vape_V4(cracked).exe | C:\Users\admin\Desktop\loader.exe | executable | |
MD5:— | SHA256:— | |||
| 612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb612.10253\Vape_V4(cracked).exe | executable | |
MD5:— | SHA256:— | |||
| 1324 | Vape_V4(cracked).exe | C:\Users\admin\Desktop\Vape_V4.exe | executable | |
MD5:7407FD99EE1940051B4F543656EA9B0A | SHA256:BEF628B23396D36849BEAC1BF633859D02F82AE9DC877281862B7E9E85148ECD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1088 | loader.exe | 162.159.133.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
3088 | loader.exe | 162.159.133.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
2100 | loader.exe | 162.159.133.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
4004 | loader.exe | 162.159.133.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
3280 | loader.exe | 162.159.133.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.discordapp.com |
| shared |