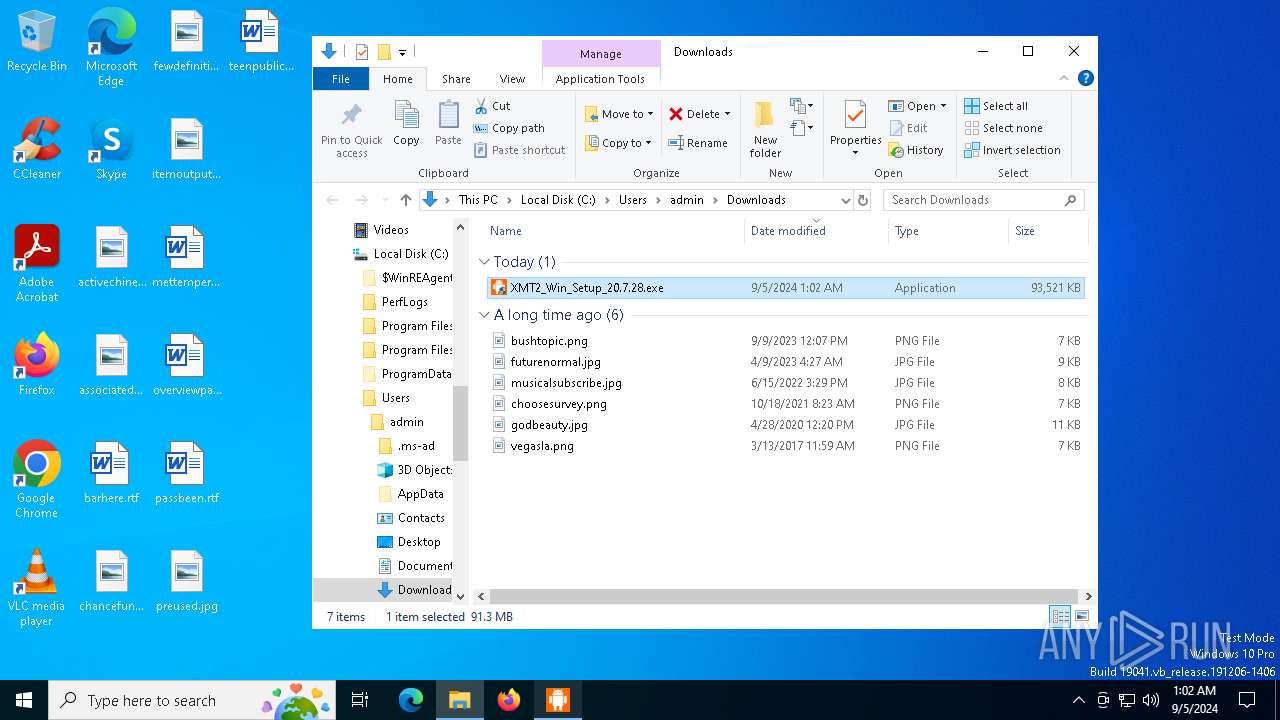
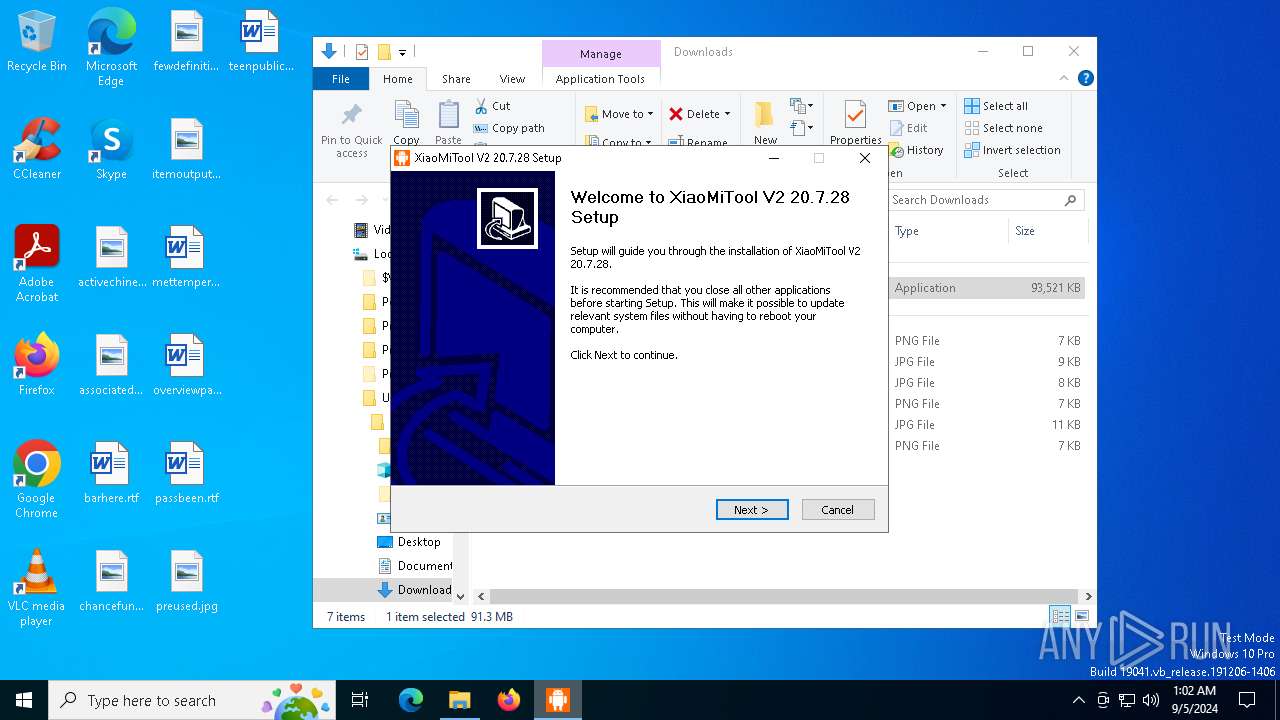
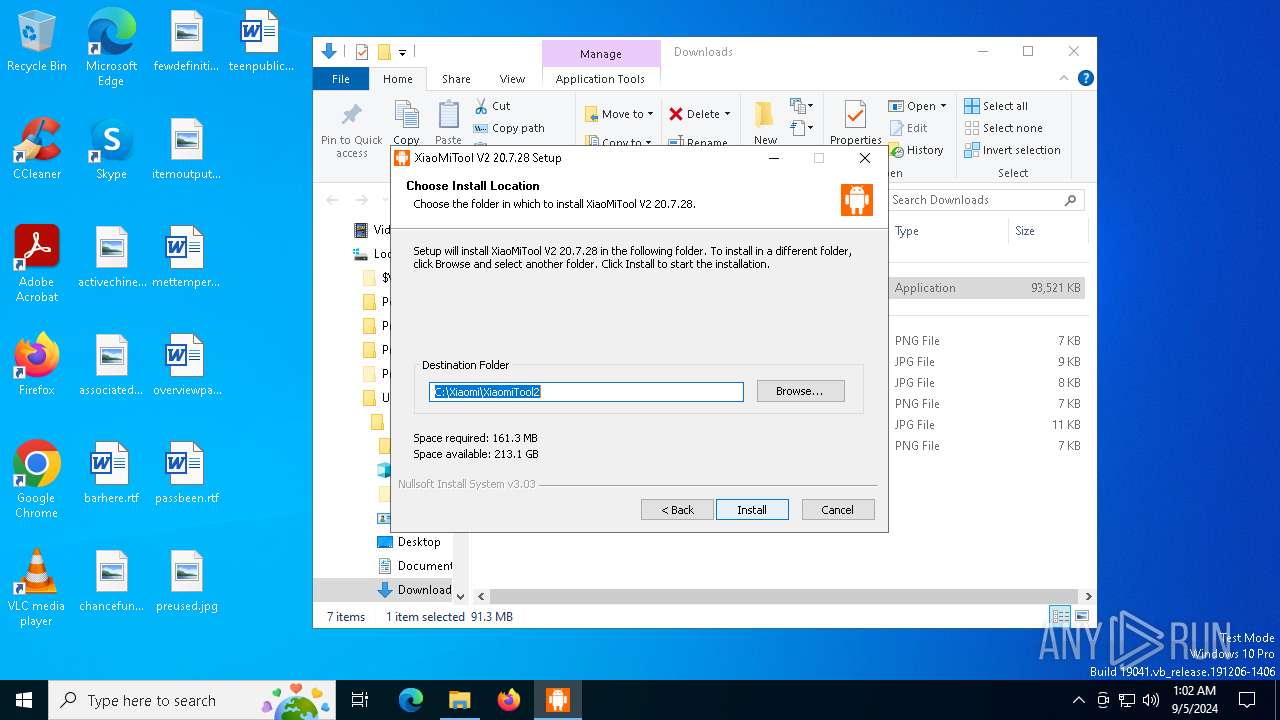
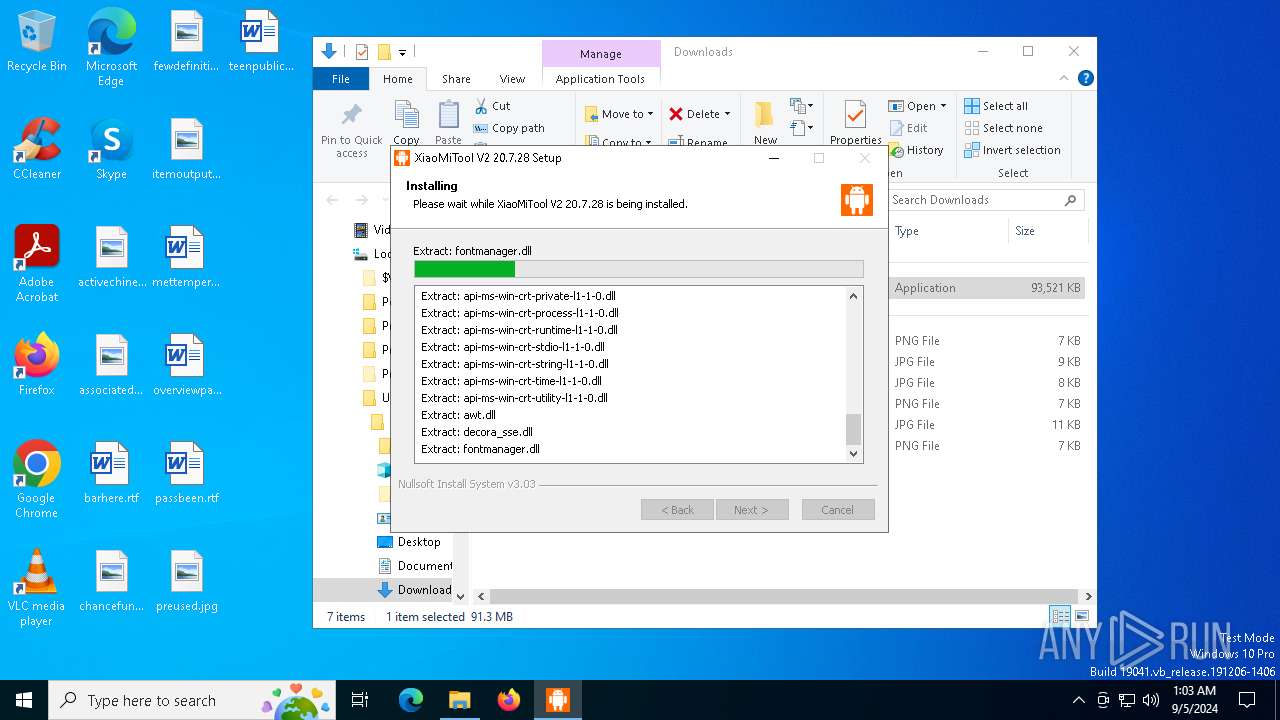
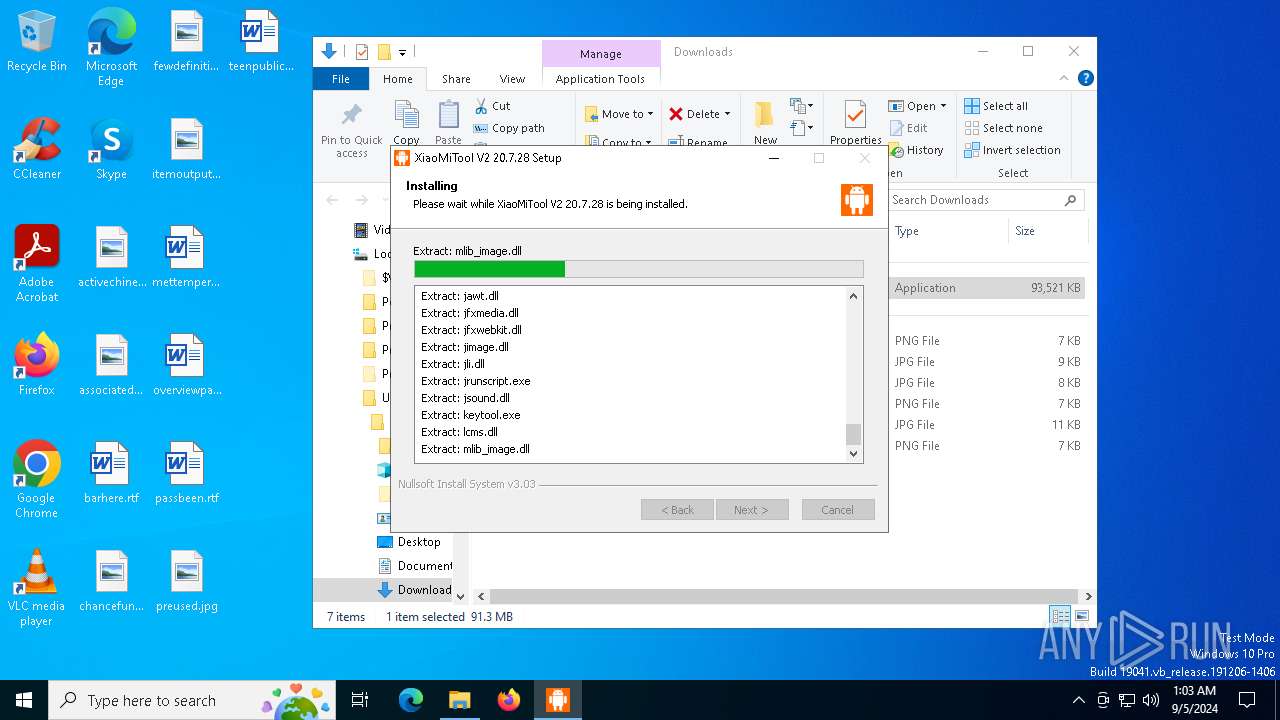
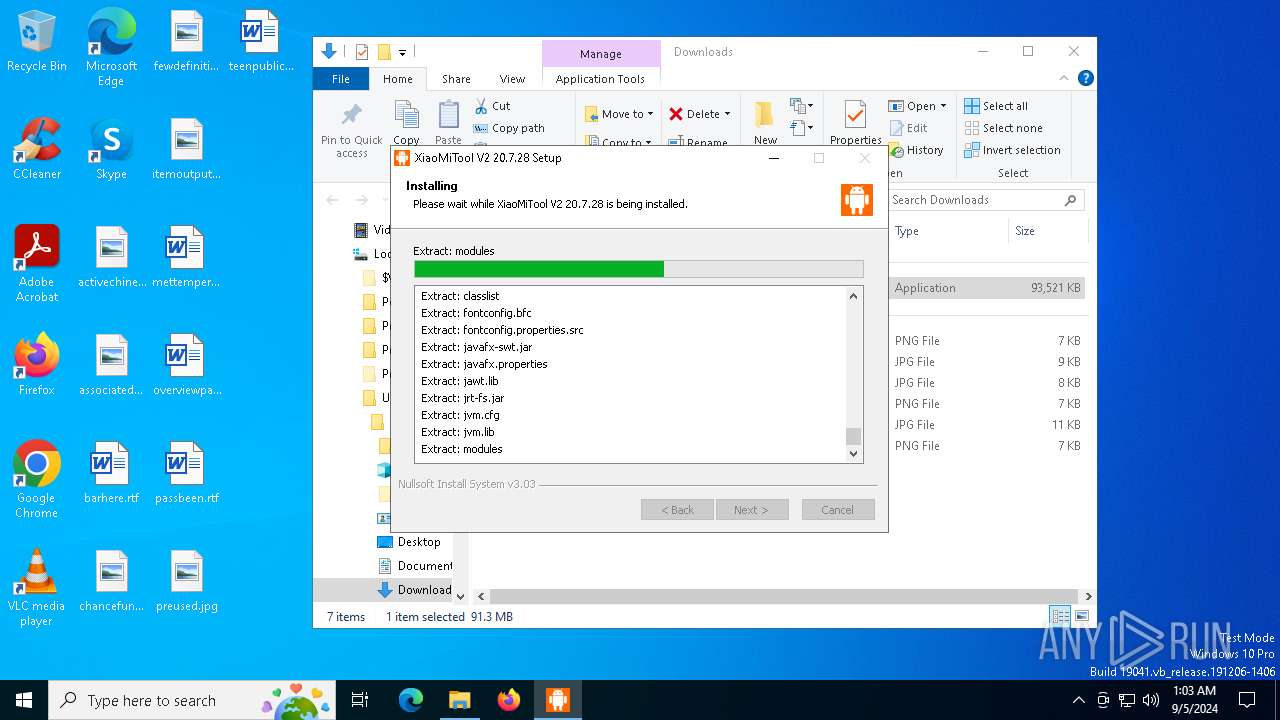
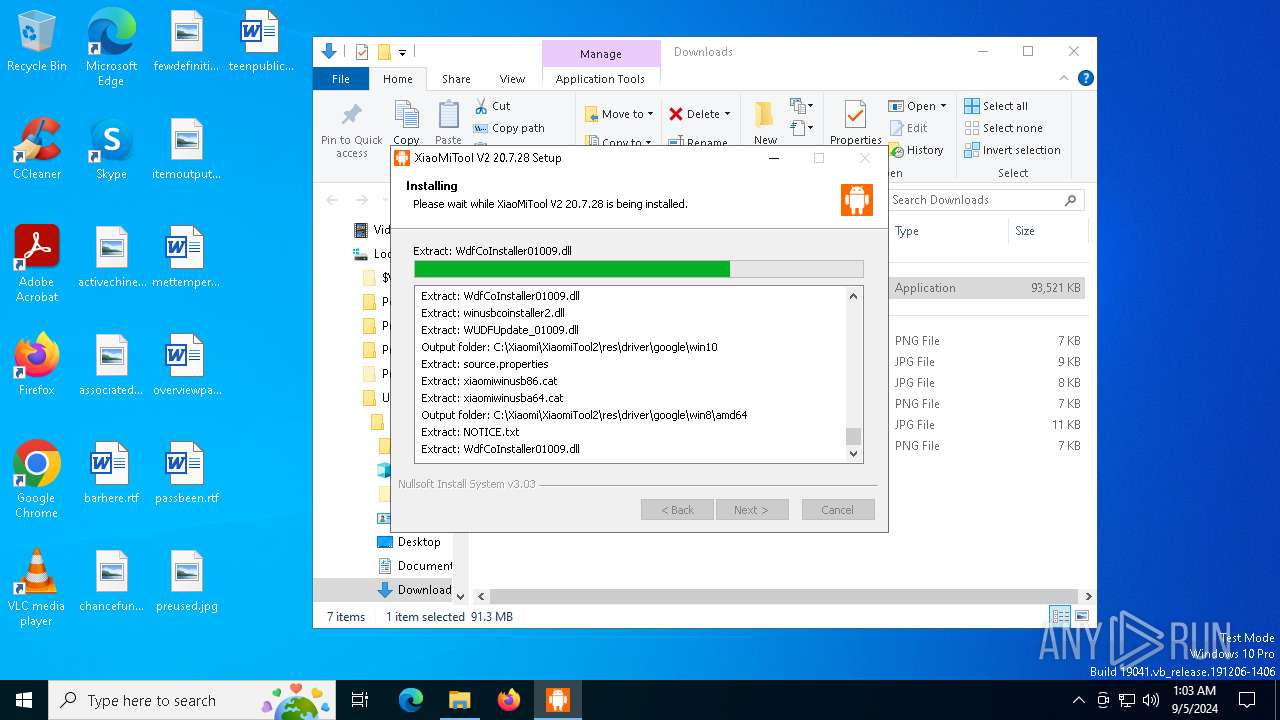
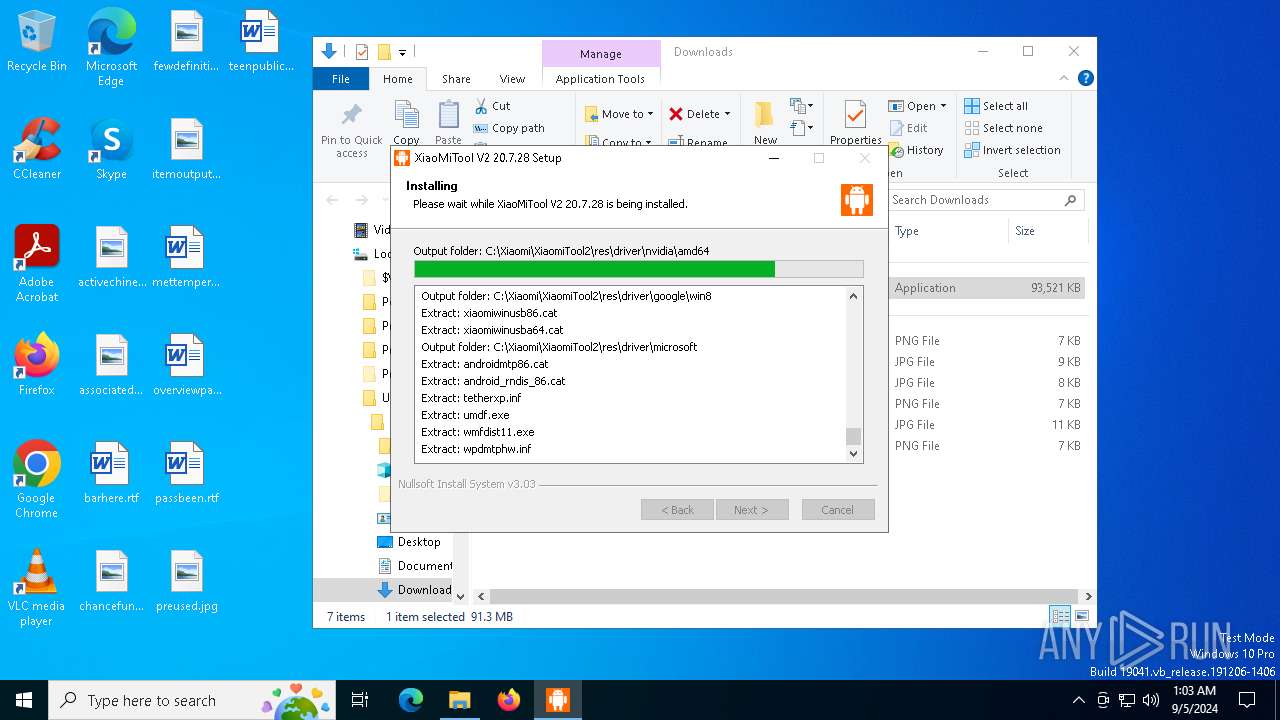
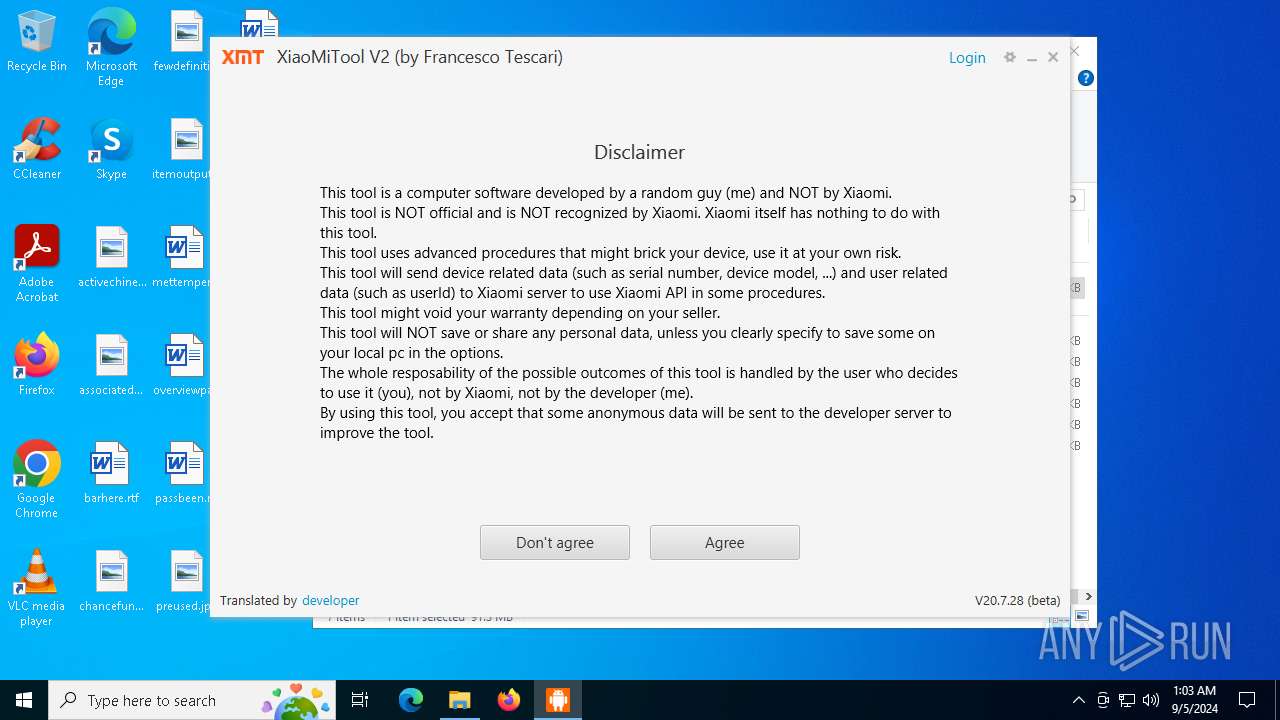
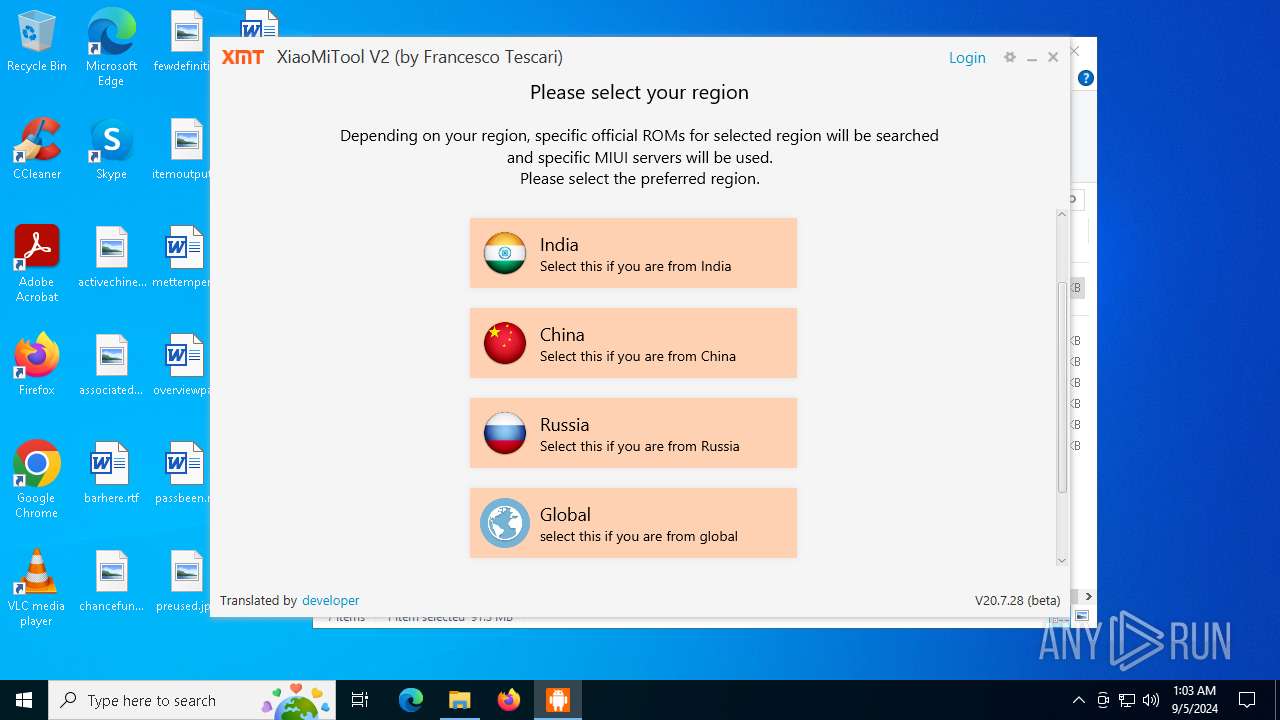
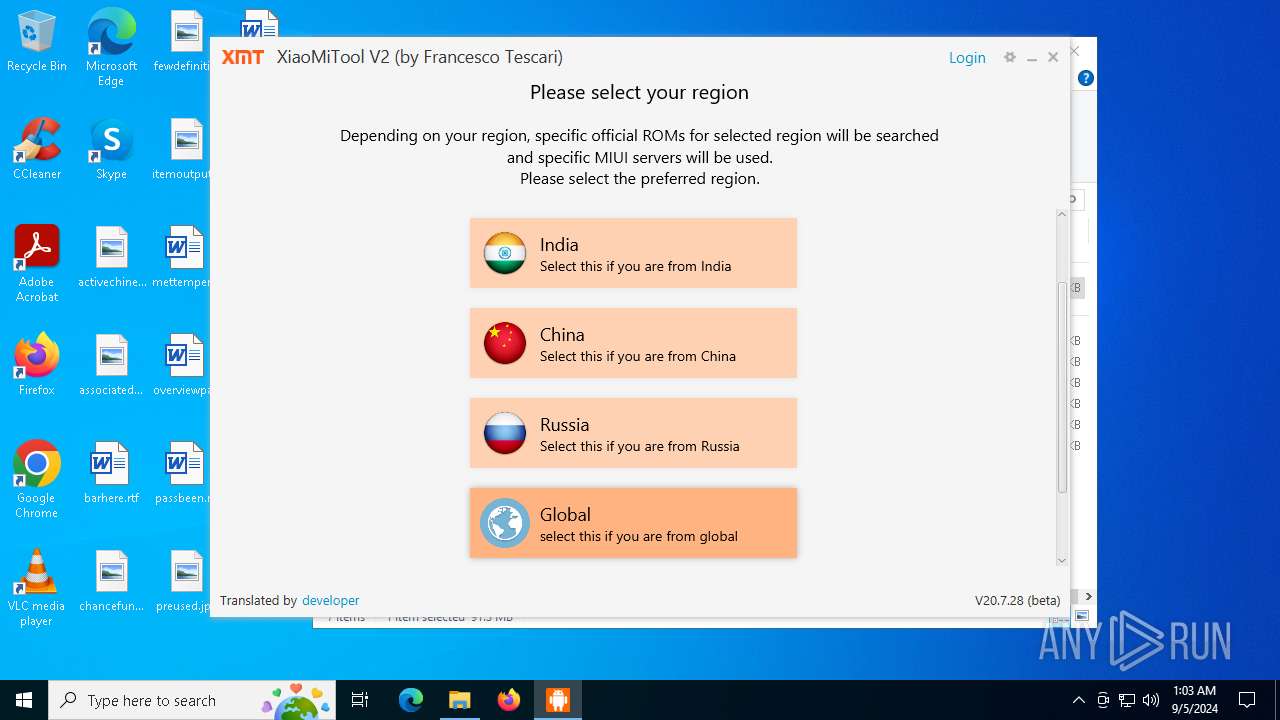
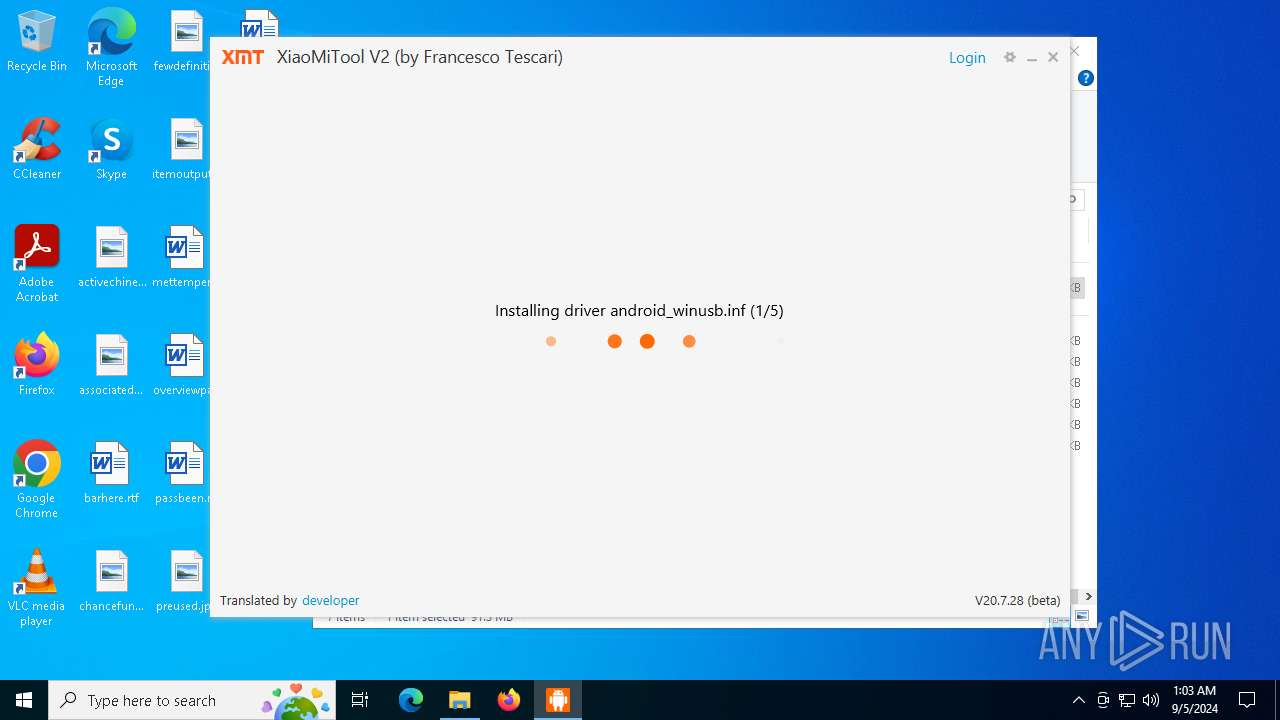
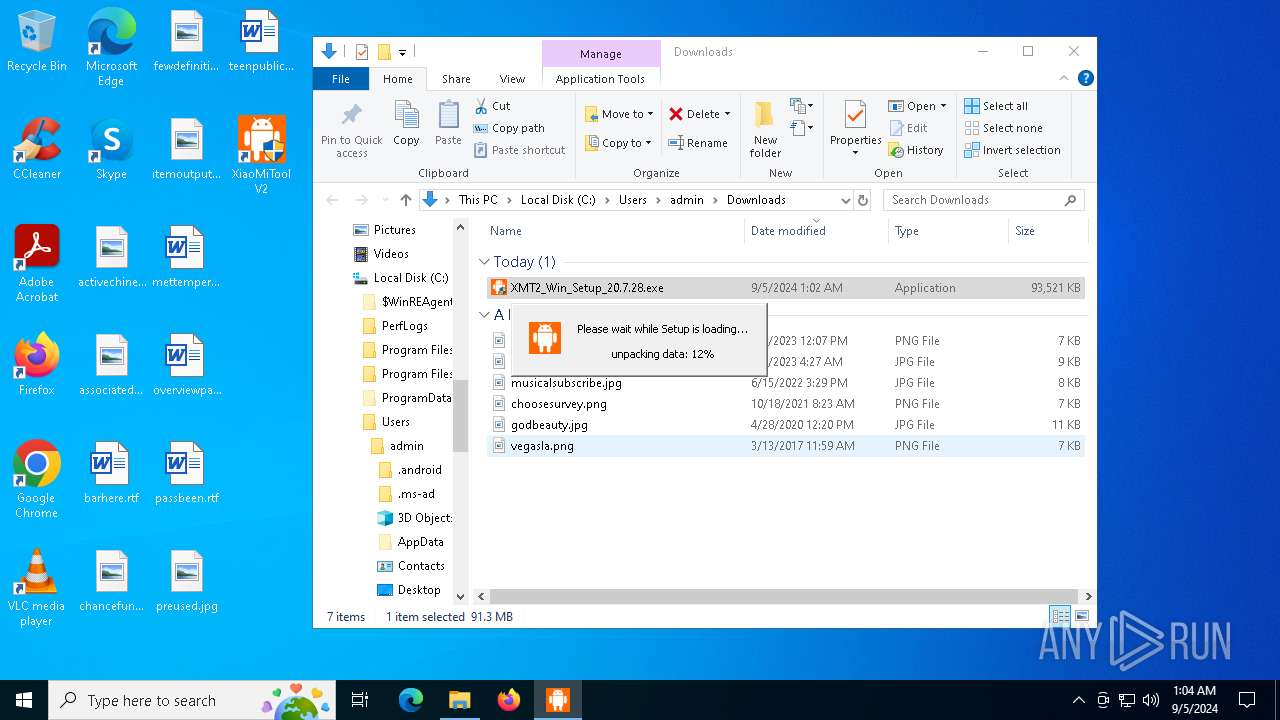
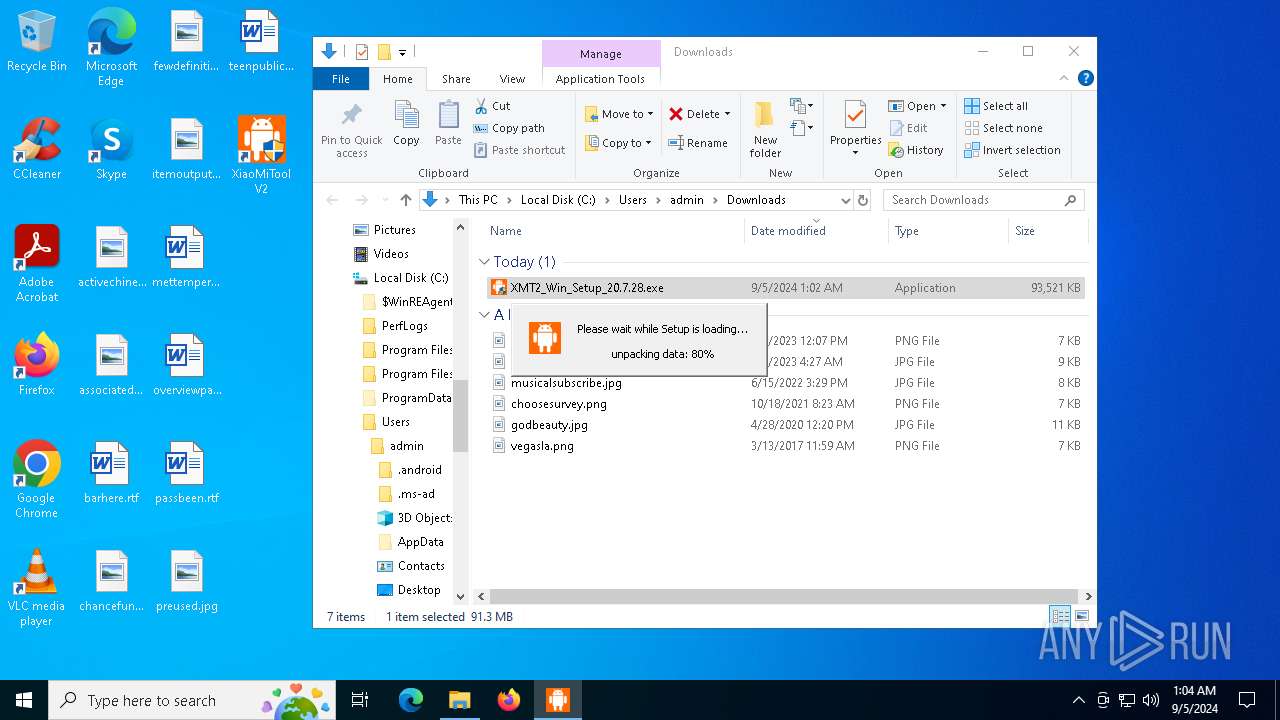
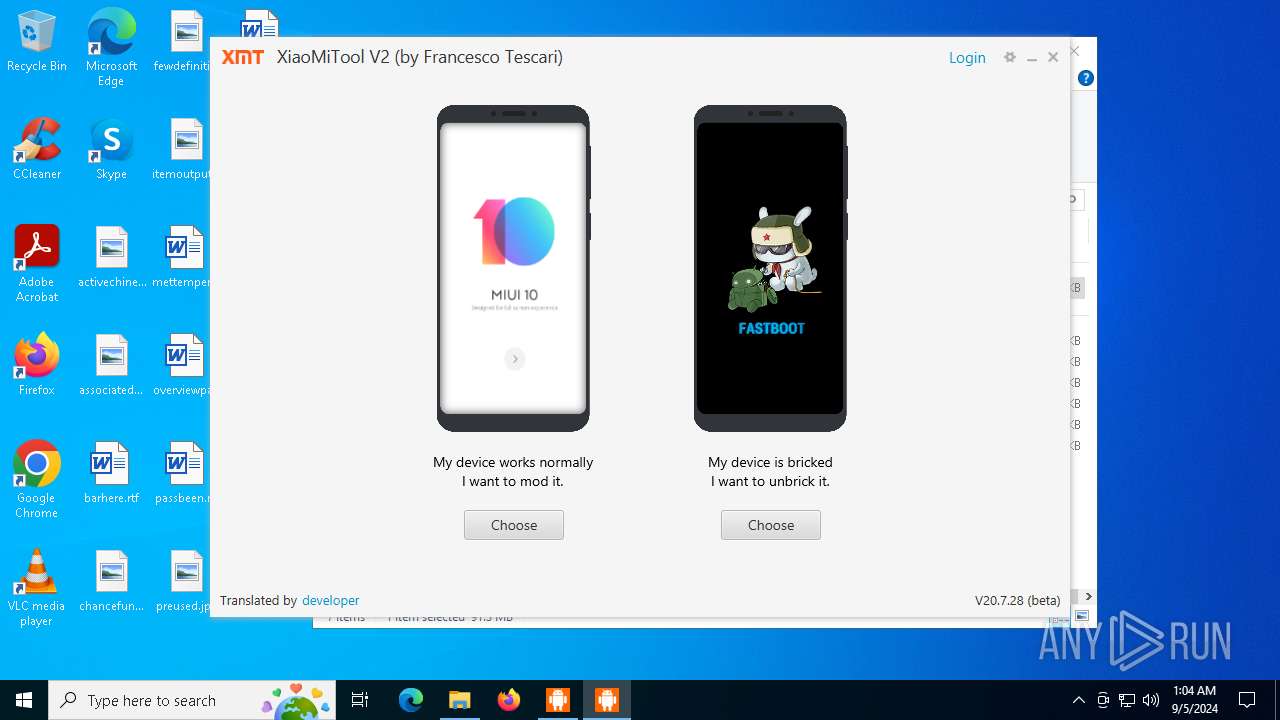
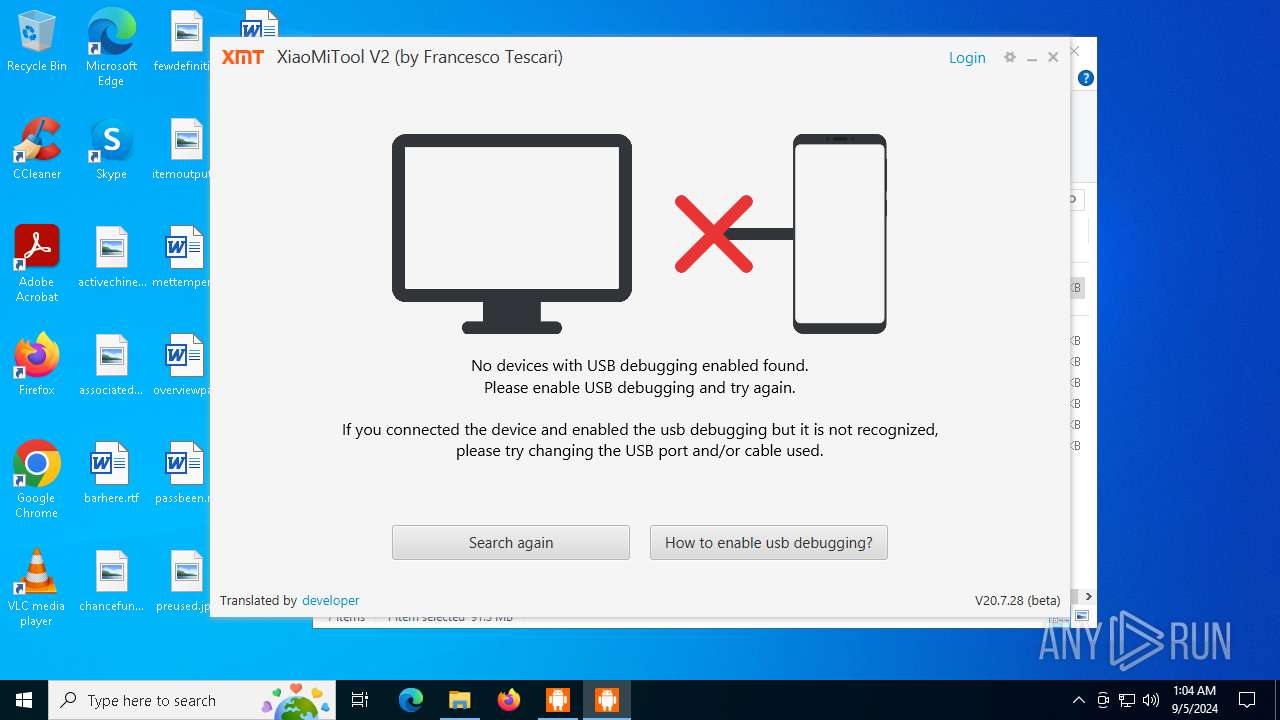
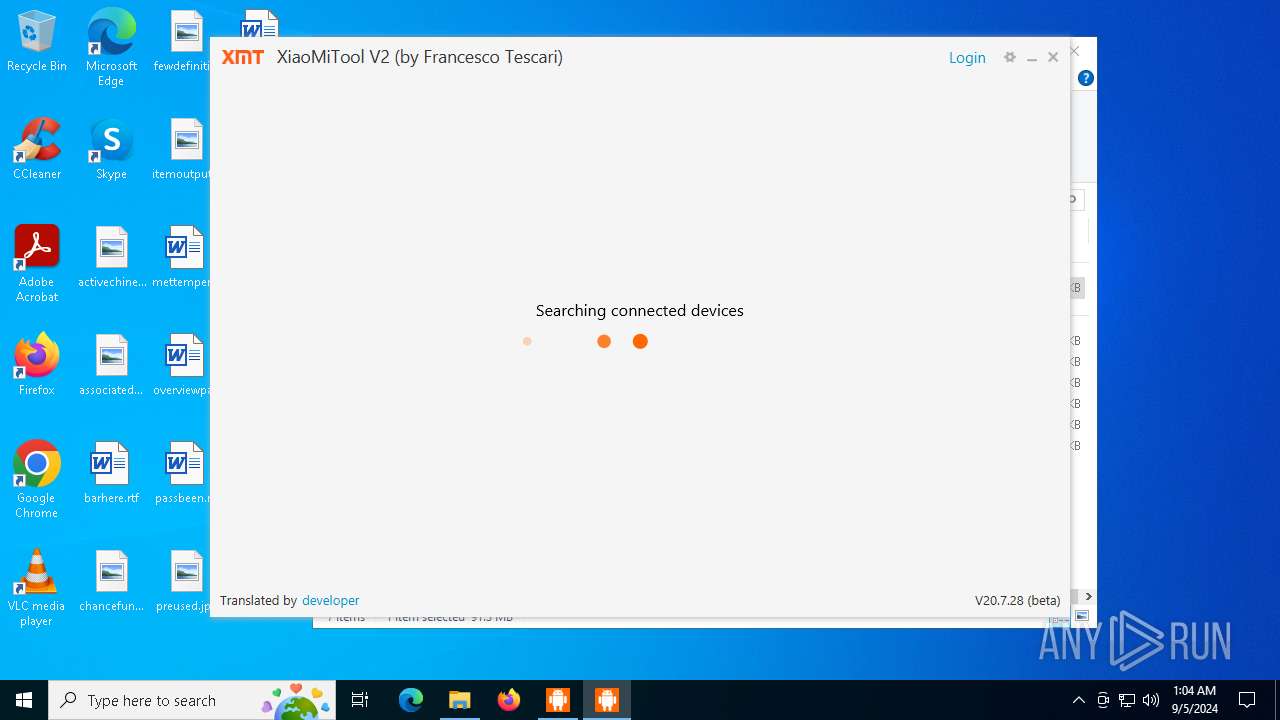
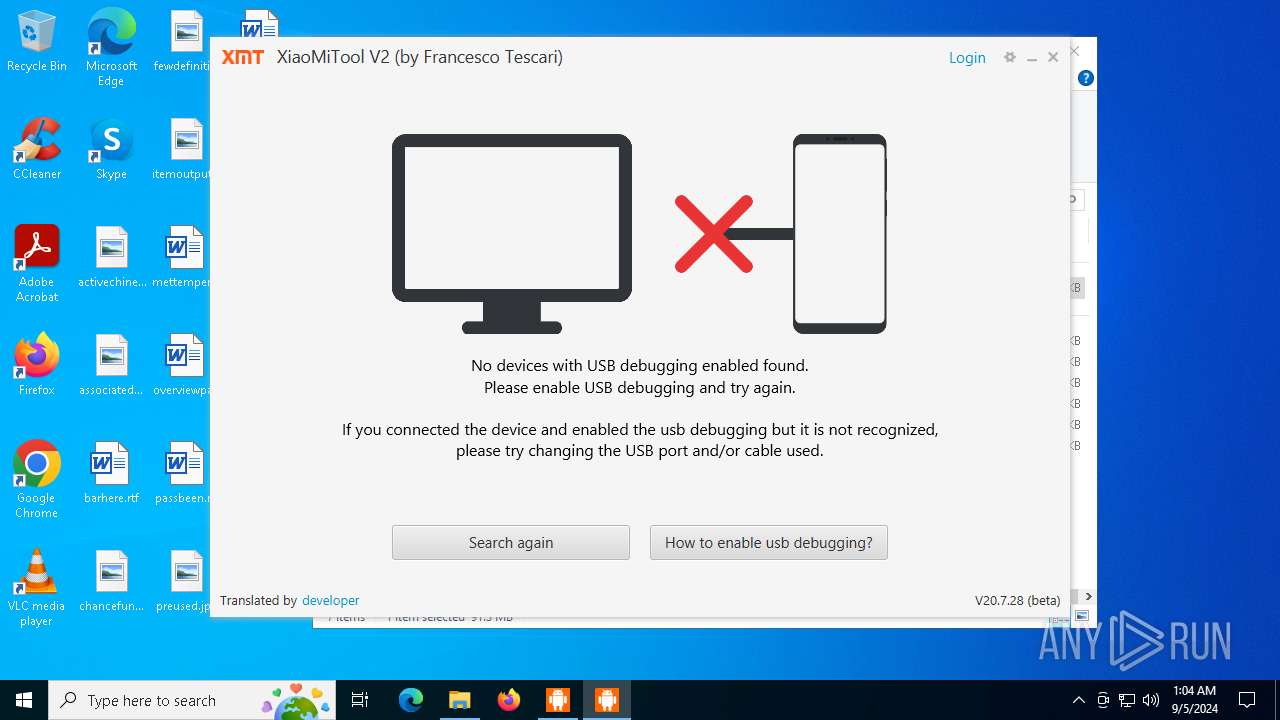
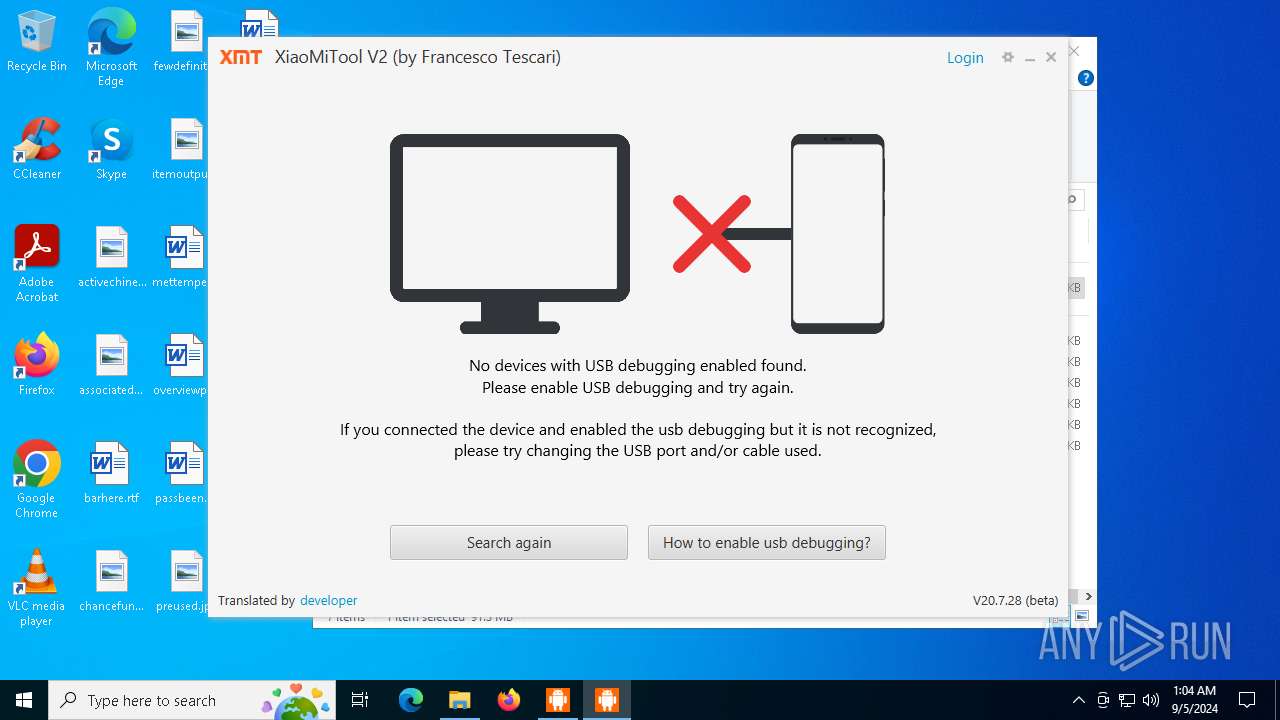
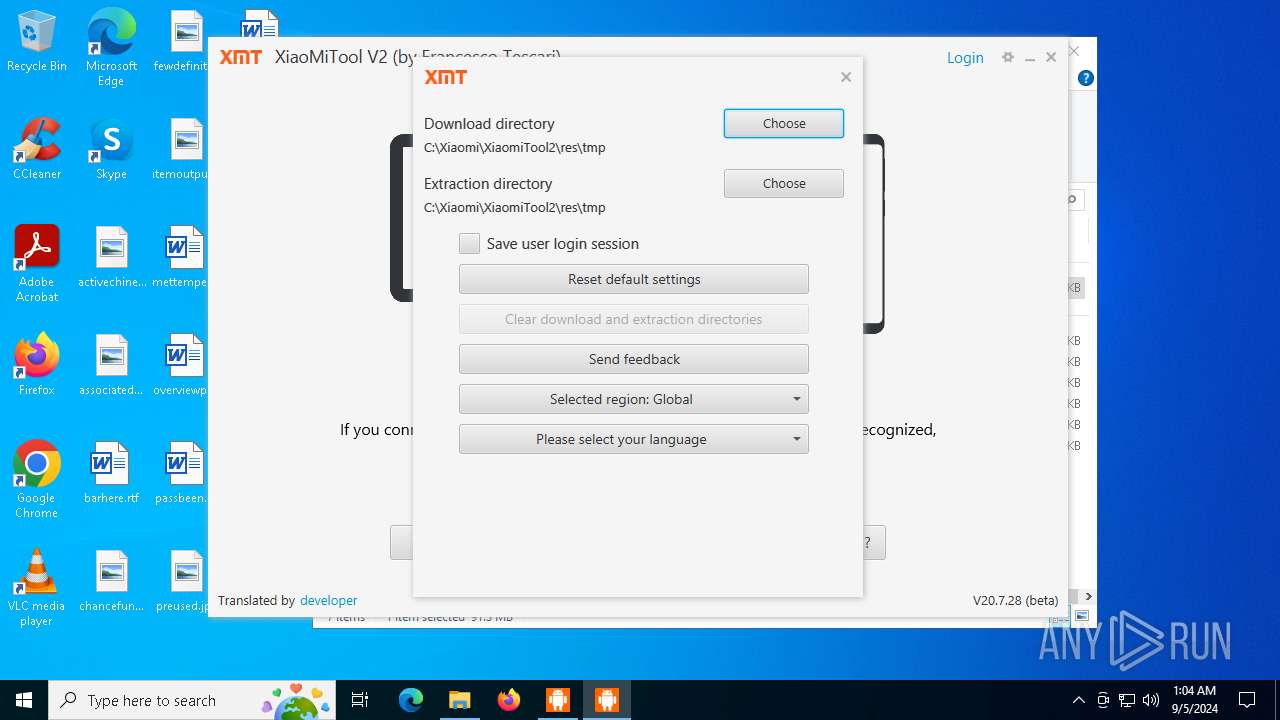
| URL: | https://www.xiaomitool.com/V2/latest |
| Full analysis: | https://app.any.run/tasks/d3670df6-047f-4b42-8b50-35f00109da48 |
| Verdict: | Malicious activity |
| Analysis date: | September 05, 2024, 01:01:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 5B7C7F49F71F567FD37621BB486546D3 |
| SHA1: | B41E57CD042C65A44FD409D8BEC498434A1A5DA8 |
| SHA256: | 56279943BB66F612B4F6A261E44588882EDF595B5462F9783F59891C2A876F58 |
| SSDEEP: | 3:N8DSLrKBsRJEhR:2OLrK+RC |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
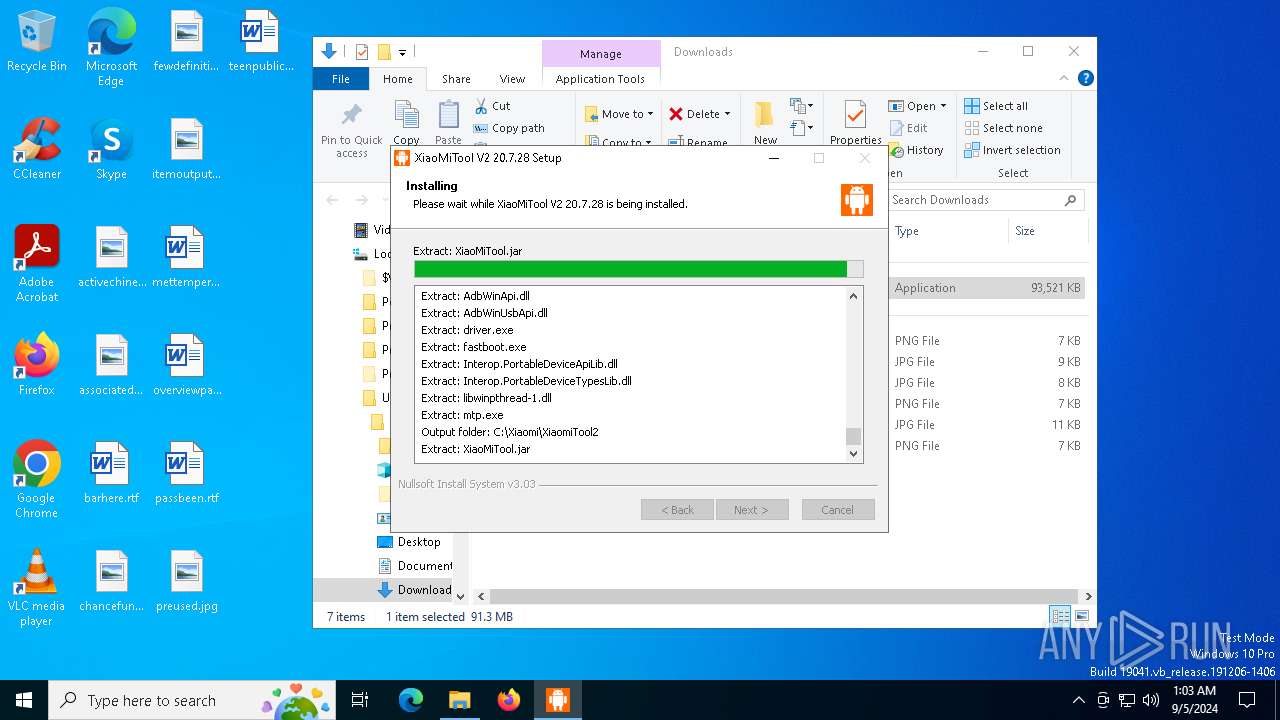
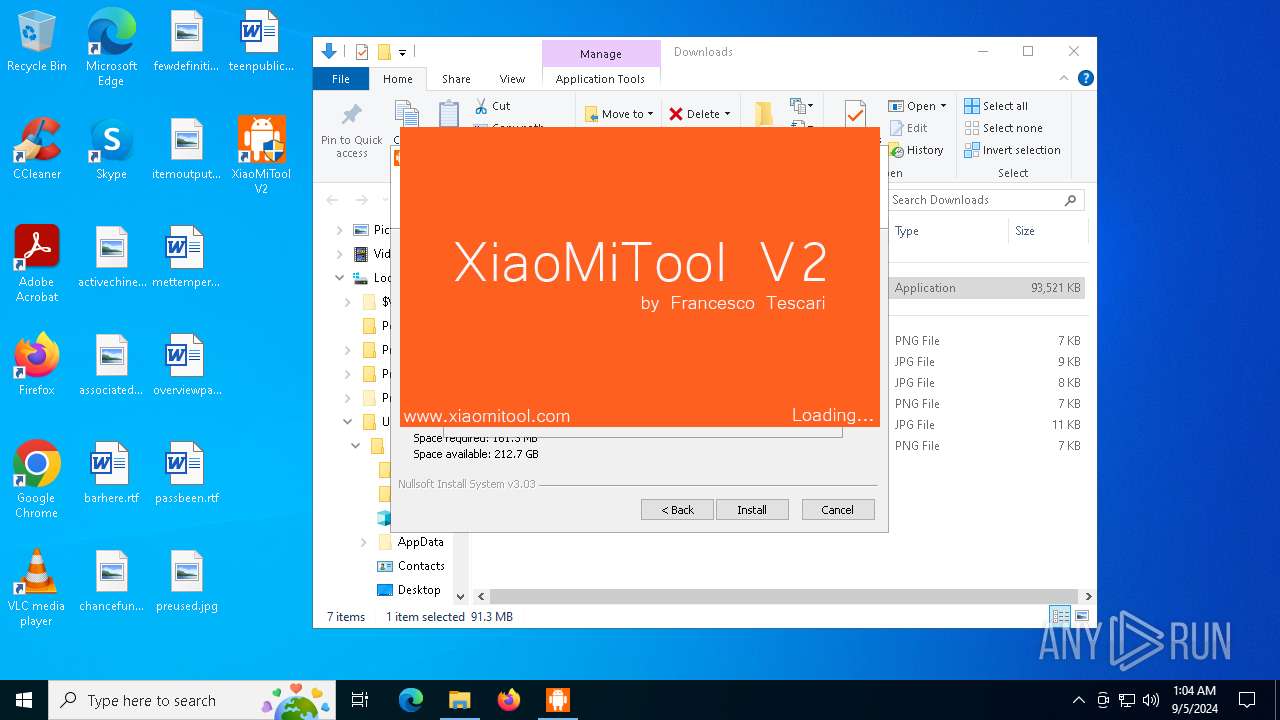
- XMT2_Win_Setup_20.7.28.exe (PID: 6920)
The process creates files with name similar to system file names
- XMT2_Win_Setup_20.7.28.exe (PID: 6920)
- XMT2_Win_Setup_20.7.28.exe (PID: 4084)
Malware-specific behavior (creating "System.dll" in Temp)
- XMT2_Win_Setup_20.7.28.exe (PID: 6920)
- XMT2_Win_Setup_20.7.28.exe (PID: 4084)
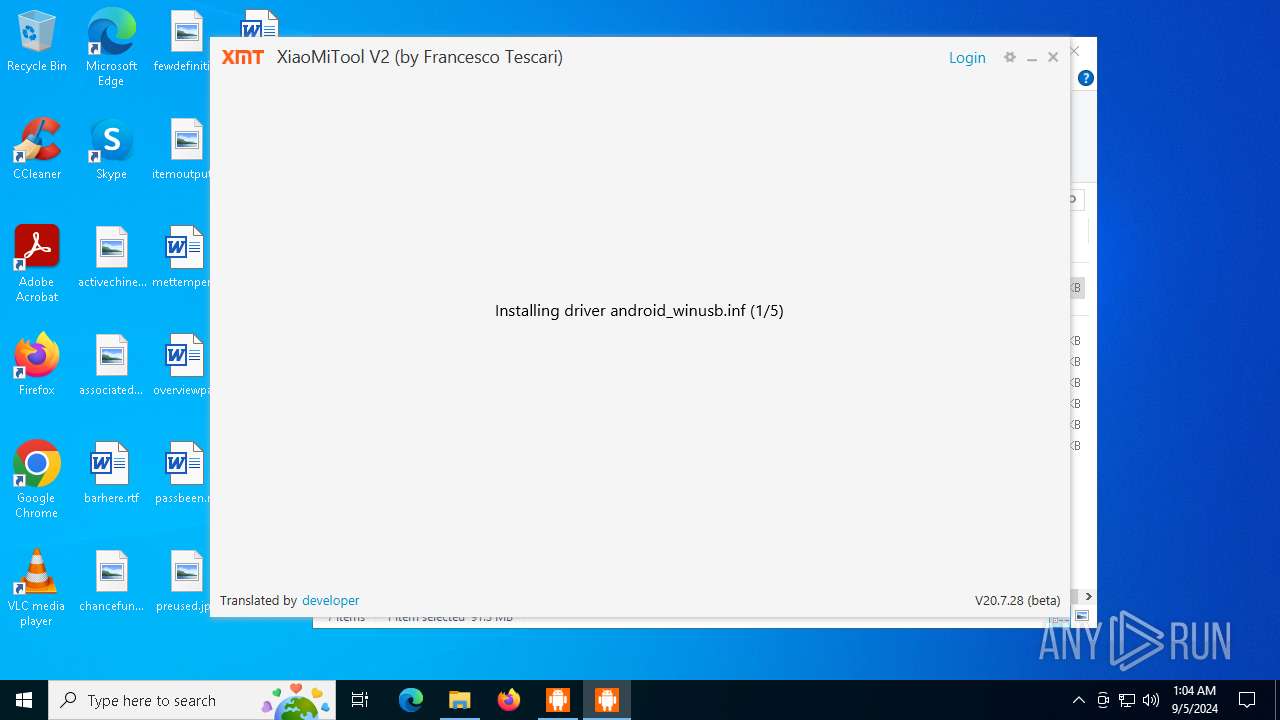
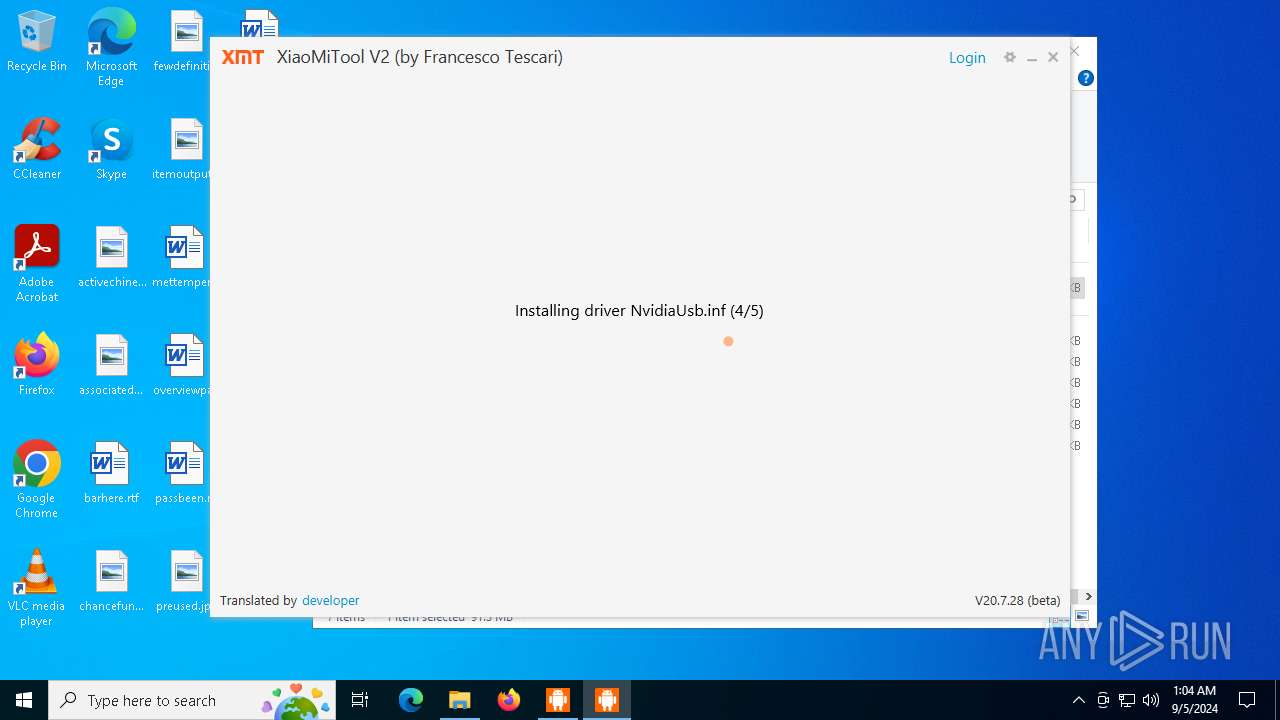
Process drops legitimate windows executable
- XMT2_Win_Setup_20.7.28.exe (PID: 6920)
- driver.exe (PID: 3352)
- drvinst.exe (PID: 4084)
- driver.exe (PID: 1480)
- drvinst.exe (PID: 4644)
- drvinst.exe (PID: 5852)
- driver.exe (PID: 6648)
Drops a system driver (possible attempt to evade defenses)
- XMT2_Win_Setup_20.7.28.exe (PID: 6920)
- driver.exe (PID: 6748)
- drvinst.exe (PID: 3812)
Executable content was dropped or overwritten
- XMT2_Win_Setup_20.7.28.exe (PID: 6920)
- driver.exe (PID: 3352)
- drvinst.exe (PID: 4084)
- driver.exe (PID: 1480)
- drvinst.exe (PID: 4644)
- driver.exe (PID: 6748)
- drvinst.exe (PID: 3812)
- XMT2_Win_Setup_20.7.28.exe (PID: 4084)
- driver.exe (PID: 6648)
- drvinst.exe (PID: 5852)
Creates files in the driver directory
- drvinst.exe (PID: 4084)
- drvinst.exe (PID: 3784)
- drvinst.exe (PID: 4644)
- drvinst.exe (PID: 3812)
- drvinst.exe (PID: 4936)
- drvinst.exe (PID: 1692)
- drvinst.exe (PID: 7036)
- drvinst.exe (PID: 5852)
Checks Windows Trust Settings
- drvinst.exe (PID: 4084)
- driver.exe (PID: 5220)
- driver.exe (PID: 2508)
- drvinst.exe (PID: 3812)
- driver.exe (PID: 3036)
- driver.exe (PID: 3548)
Reads security settings of Internet Explorer
- driver.exe (PID: 2508)
- driver.exe (PID: 5220)
- driver.exe (PID: 3036)
- driver.exe (PID: 3548)
There is functionality for VM detection (antiVM strings)
- javaw.exe (PID: 3840)
- javaw.exe (PID: 5116)
There is functionality for VM detection (VMWare)
- javaw.exe (PID: 3840)
- javaw.exe (PID: 5116)
Application launched itself
- adb.exe (PID: 4524)
- adb.exe (PID: 6428)
- adb.exe (PID: 2700)
Executes application which crashes
- adb.exe (PID: 7040)
INFO
Application launched itself
- firefox.exe (PID: 6168)
- firefox.exe (PID: 5624)
Executable content was dropped or overwritten
- firefox.exe (PID: 5624)
Checks supported languages
- XMT2_Win_Setup_20.7.28.exe (PID: 6920)
- javaw.exe (PID: 3840)
- XiaoMiTool.exe (PID: 5552)
- adb.exe (PID: 6128)
- driver.exe (PID: 3352)
- drvinst.exe (PID: 4084)
- driver.exe (PID: 5220)
- drvinst.exe (PID: 3784)
- driver.exe (PID: 1480)
- drvinst.exe (PID: 4644)
- drvinst.exe (PID: 3812)
- driver.exe (PID: 6748)
- driver.exe (PID: 5184)
- adb.exe (PID: 6428)
- adb.exe (PID: 940)
- adb.exe (PID: 4524)
- adb.exe (PID: 7040)
- fastboot.exe (PID: 2768)
- fastboot.exe (PID: 4436)
- adb.exe (PID: 1640)
- adb.exe (PID: 3160)
- driver.exe (PID: 5096)
- fastboot.exe (PID: 3908)
- fastboot.exe (PID: 1448)
- adb.exe (PID: 2132)
- adb.exe (PID: 6480)
- fastboot.exe (PID: 6208)
- fastboot.exe (PID: 6564)
- adb.exe (PID: 2056)
- adb.exe (PID: 2700)
- fastboot.exe (PID: 7080)
- fastboot.exe (PID: 5984)
- adb.exe (PID: 1280)
- fastboot.exe (PID: 6204)
- adb.exe (PID: 6408)
- fastboot.exe (PID: 5164)
- adb.exe (PID: 4092)
- adb.exe (PID: 3984)
- fastboot.exe (PID: 2724)
- adb.exe (PID: 2612)
- fastboot.exe (PID: 5852)
- fastboot.exe (PID: 5944)
- XMT2_Win_Setup_20.7.28.exe (PID: 4084)
- adb.exe (PID: 6352)
- drvinst.exe (PID: 7036)
- driver.exe (PID: 2508)
- XiaoMiTool.exe (PID: 6640)
- javaw.exe (PID: 5116)
- adb.exe (PID: 3728)
- driver.exe (PID: 3036)
- driver.exe (PID: 7164)
- drvinst.exe (PID: 4936)
- driver.exe (PID: 3548)
- drvinst.exe (PID: 1692)
- driver.exe (PID: 6648)
- drvinst.exe (PID: 5852)
- driver.exe (PID: 2720)
- driver.exe (PID: 1680)
- adb.exe (PID: 1176)
- adb.exe (PID: 6996)
- adb.exe (PID: 2700)
- adb.exe (PID: 6252)
- adb.exe (PID: 5072)
- fastboot.exe (PID: 7136)
- fastboot.exe (PID: 5152)
- adb.exe (PID: 7068)
- fastboot.exe (PID: 5140)
- driver.exe (PID: 4732)
- adb.exe (PID: 5492)
- driver.exe (PID: 6216)
- fastboot.exe (PID: 6724)
- adb.exe (PID: 6304)
- adb.exe (PID: 4936)
- fastboot.exe (PID: 5544)
- fastboot.exe (PID: 1452)
- adb.exe (PID: 6816)
- fastboot.exe (PID: 5880)
- adb.exe (PID: 5796)
- fastboot.exe (PID: 6292)
- adb.exe (PID: 5744)
- fastboot.exe (PID: 6952)
- adb.exe (PID: 1640)
- fastboot.exe (PID: 6844)
- fastboot.exe (PID: 1920)
- adb.exe (PID: 5140)
- adb.exe (PID: 6224)
- fastboot.exe (PID: 6200)
- adb.exe (PID: 4644)
- fastboot.exe (PID: 6404)
- adb.exe (PID: 7136)
- adb.exe (PID: 508)
- adb.exe (PID: 5180)
- fastboot.exe (PID: 5376)
- fastboot.exe (PID: 7144)
- adb.exe (PID: 460)
- fastboot.exe (PID: 4524)
- fastboot.exe (PID: 6936)
- adb.exe (PID: 4248)
- adb.exe (PID: 2252)
- fastboot.exe (PID: 4820)
- adb.exe (PID: 7024)
- fastboot.exe (PID: 4168)
- fastboot.exe (PID: 2724)
- adb.exe (PID: 3728)
Manual execution by a user
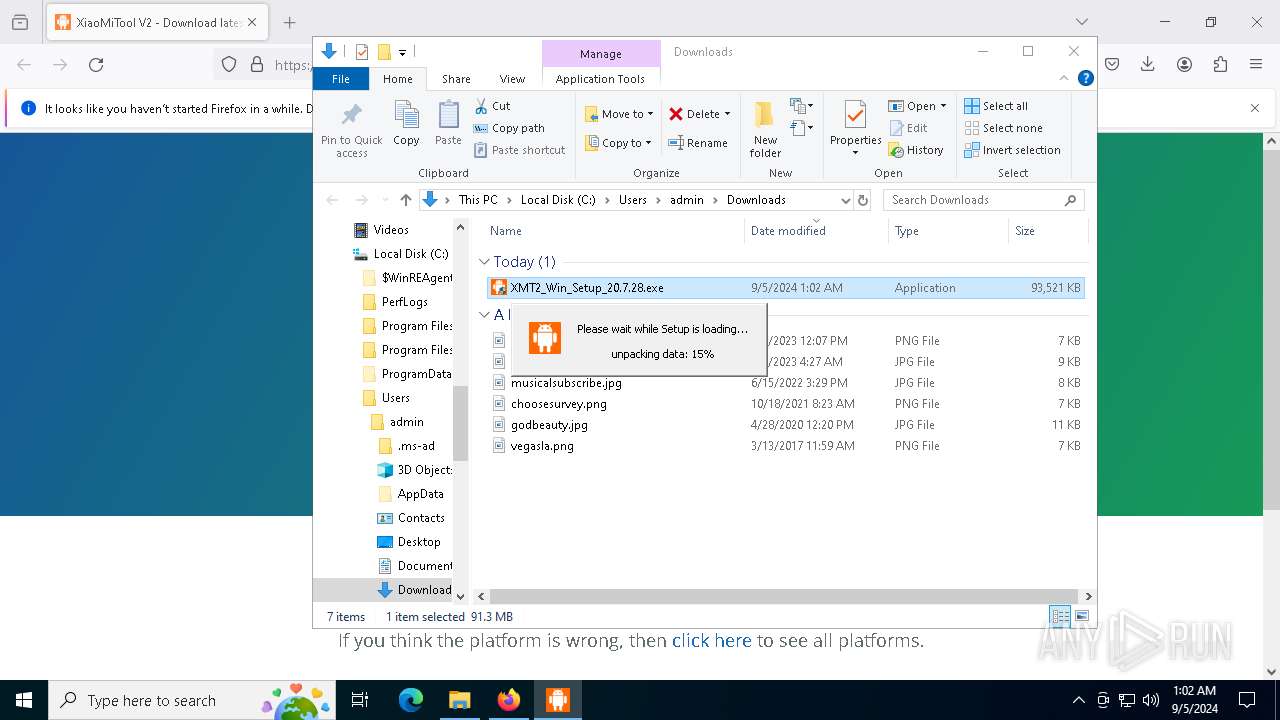
- XMT2_Win_Setup_20.7.28.exe (PID: 6172)
- XMT2_Win_Setup_20.7.28.exe (PID: 6920)
- XMT2_Win_Setup_20.7.28.exe (PID: 5468)
- XMT2_Win_Setup_20.7.28.exe (PID: 4084)
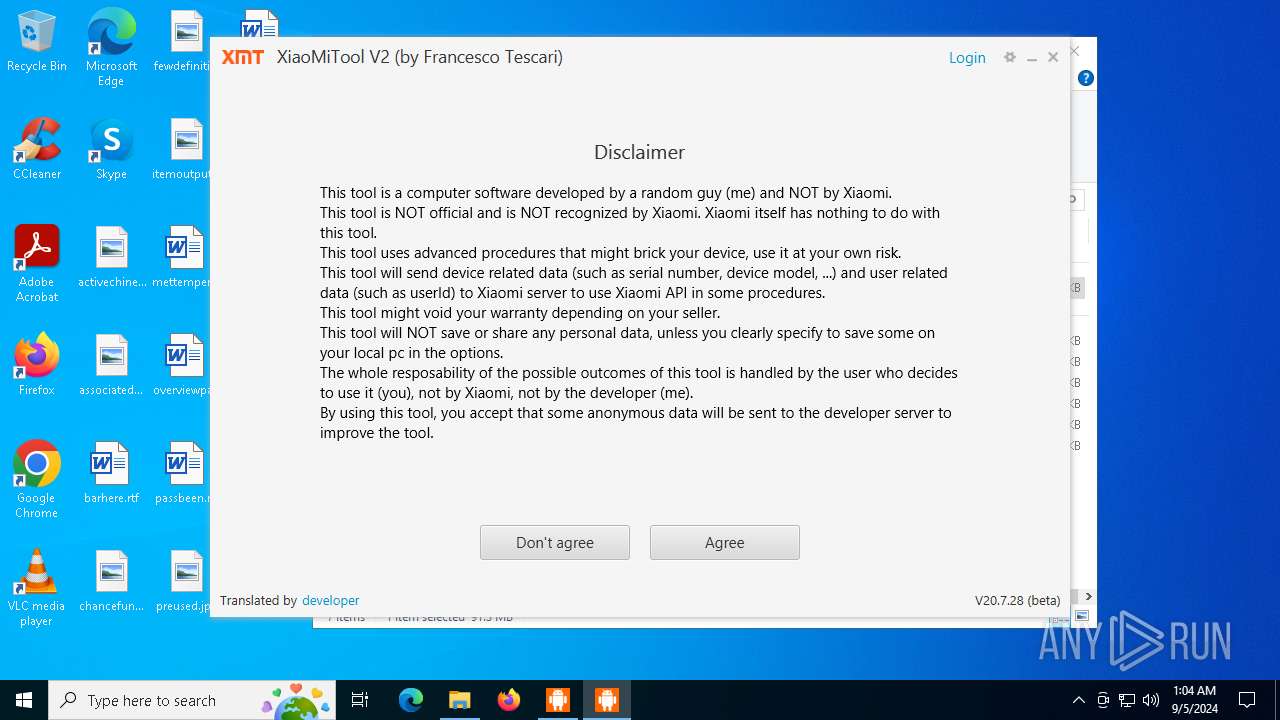
- XiaoMiTool.exe (PID: 6640)
- XiaoMiTool.exe (PID: 2684)
Create files in a temporary directory
- XMT2_Win_Setup_20.7.28.exe (PID: 6920)
- javaw.exe (PID: 3840)
- driver.exe (PID: 3352)
- driver.exe (PID: 5220)
- driver.exe (PID: 1480)
- driver.exe (PID: 6748)
- adb.exe (PID: 940)
- XMT2_Win_Setup_20.7.28.exe (PID: 4084)
- driver.exe (PID: 2508)
- driver.exe (PID: 3548)
- driver.exe (PID: 6648)
- driver.exe (PID: 3036)
- javaw.exe (PID: 5116)
The process uses the downloaded file
- firefox.exe (PID: 5624)
Reads the computer name
- XMT2_Win_Setup_20.7.28.exe (PID: 6920)
- javaw.exe (PID: 3840)
- driver.exe (PID: 3352)
- driver.exe (PID: 5220)
- drvinst.exe (PID: 4084)
- driver.exe (PID: 2508)
- driver.exe (PID: 1480)
- driver.exe (PID: 6748)
- drvinst.exe (PID: 3812)
- adb.exe (PID: 7040)
- adb.exe (PID: 940)
- XMT2_Win_Setup_20.7.28.exe (PID: 4084)
- javaw.exe (PID: 5116)
- driver.exe (PID: 3036)
- driver.exe (PID: 3548)
- adb.exe (PID: 6996)
- driver.exe (PID: 6648)
Creates files or folders in the user directory
- XMT2_Win_Setup_20.7.28.exe (PID: 6920)
- javaw.exe (PID: 3840)
- WerFault.exe (PID: 6724)
Reads the machine GUID from the registry
- javaw.exe (PID: 3840)
- drvinst.exe (PID: 4084)
- driver.exe (PID: 5220)
- driver.exe (PID: 2508)
- driver.exe (PID: 1480)
- drvinst.exe (PID: 3812)
- javaw.exe (PID: 5116)
- driver.exe (PID: 3548)
- driver.exe (PID: 6648)
- driver.exe (PID: 3036)
Process checks computer location settings
- javaw.exe (PID: 3840)
- javaw.exe (PID: 5116)
Reads the software policy settings
- slui.exe (PID: 4076)
- drvinst.exe (PID: 4084)
- driver.exe (PID: 5220)
- driver.exe (PID: 2508)
- driver.exe (PID: 1480)
- drvinst.exe (PID: 3812)
- WerFault.exe (PID: 6724)
- slui.exe (PID: 1220)
- driver.exe (PID: 3036)
- driver.exe (PID: 3548)
- driver.exe (PID: 6648)
Checks proxy server information
- WerFault.exe (PID: 6724)
- slui.exe (PID: 1220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
349
Monitored processes
210
Malicious processes
6
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 376 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | fastboot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | fastboot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 460 | C:\Xiaomi\XiaomiTool2\res\tools\adb.exe devices | C:\Xiaomi\XiaomiTool2\res\tools\adb.exe | — | javaw.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 508 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 508 | C:\Xiaomi\XiaomiTool2\res\tools\adb.exe devices | C:\Xiaomi\XiaomiTool2\res\tools\adb.exe | — | javaw.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 608 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | fastboot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 608 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | fastboot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 940 | adb -L tcp:5037 fork-server server --reply-fd 588 | C:\Xiaomi\XiaomiTool2\res\tools\adb.exe | — | adb.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 940 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
45 435
Read events
45 406
Write events
26
Delete events
3
Modification events
| (PID) Process: | (5624) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (3352) driver.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
| (PID) Process: | (6724) WerFault.exe | Key: | \REGISTRY\A\{29b55553-a43e-a377-af60-75556854e665}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (6724) WerFault.exe | Key: | \REGISTRY\A\{29b55553-a43e-a377-af60-75556854e665}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6724) WerFault.exe | Key: | \REGISTRY\A\{29b55553-a43e-a377-af60-75556854e665}\Root\InventoryApplicationFile\adb.exe|6226c1944d12bb48 |
| Operation: | write | Name: | ProgramId |
Value: 000604f0e2dab6cb70449736bcc7f3d604b80000ffff | |||
| (PID) Process: | (6724) WerFault.exe | Key: | \REGISTRY\A\{29b55553-a43e-a377-af60-75556854e665}\Root\InventoryApplicationFile\adb.exe|6226c1944d12bb48 |
| Operation: | write | Name: | FileId |
Value: 00001d8204c1437567f5768752ded39b97dc1fd068f5 | |||
| (PID) Process: | (6724) WerFault.exe | Key: | \REGISTRY\A\{29b55553-a43e-a377-af60-75556854e665}\Root\InventoryApplicationFile\adb.exe|6226c1944d12bb48 |
| Operation: | write | Name: | LowerCaseLongPath |
Value: c:\xiaomi\xiaomitool2\res\tools\adb.exe | |||
| (PID) Process: | (6724) WerFault.exe | Key: | \REGISTRY\A\{29b55553-a43e-a377-af60-75556854e665}\Root\InventoryApplicationFile\adb.exe|6226c1944d12bb48 |
| Operation: | write | Name: | LongPathHash |
Value: adb.exe|6226c1944d12bb48 | |||
| (PID) Process: | (6724) WerFault.exe | Key: | \REGISTRY\A\{29b55553-a43e-a377-af60-75556854e665}\Root\InventoryApplicationFile\adb.exe|6226c1944d12bb48 |
| Operation: | write | Name: | Name |
Value: adb.exe | |||
| (PID) Process: | (6724) WerFault.exe | Key: | \REGISTRY\A\{29b55553-a43e-a377-af60-75556854e665}\Root\InventoryApplicationFile\adb.exe|6226c1944d12bb48 |
| Operation: | write | Name: | OriginalFileName |
Value: | |||
Executable files
162
Suspicious files
244
Text files
81
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5624 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 5624 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 5624 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5624 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 5624 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5624 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5624 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 5624 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:DBA503C29091328C921C0D99A9B84222 | SHA256:5F86884A121337DFF13838017442BBF1E3606B2367CE7AF021060BC8834AA572 | |||
| 5624 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5624 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:031090C371CE3D93B600D2CAD522D9A4 | SHA256:377F24CB377339DEC93A56F6AAB2B453CA761EDB27AED73157F08C3E9A6A8401 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
120
DNS requests
149
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5624 | firefox.exe | POST | 200 | 95.101.54.131:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
5624 | firefox.exe | POST | 200 | 95.101.54.131:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
5624 | firefox.exe | POST | 200 | 95.101.54.131:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
6020 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5624 | firefox.exe | POST | 200 | 95.101.54.131:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
5624 | firefox.exe | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | — | — | unknown |
5624 | firefox.exe | POST | 200 | 95.101.54.131:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
8 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6252 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6252 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6020 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1148 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 142.250.184.234:443 | safebrowsing.googleapis.com | — | — | whitelisted |
5624 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
— | — | 172.67.168.167:443 | www.xiaomitool.com | — | — | suspicious |
— | — | 34.117.188.166:443 | contile.services.mozilla.com | — | — | whitelisted |
— | — | 216.58.206.67:80 | o.pki.goog | GOOGLE | US | whitelisted |
5624 | firefox.exe | 172.67.168.167:443 | www.xiaomitool.com | CLOUDFLARENET | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.xiaomitool.com |
| unknown |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
prod.ads.prod.webservices.mozgcp.net |
| unknown |