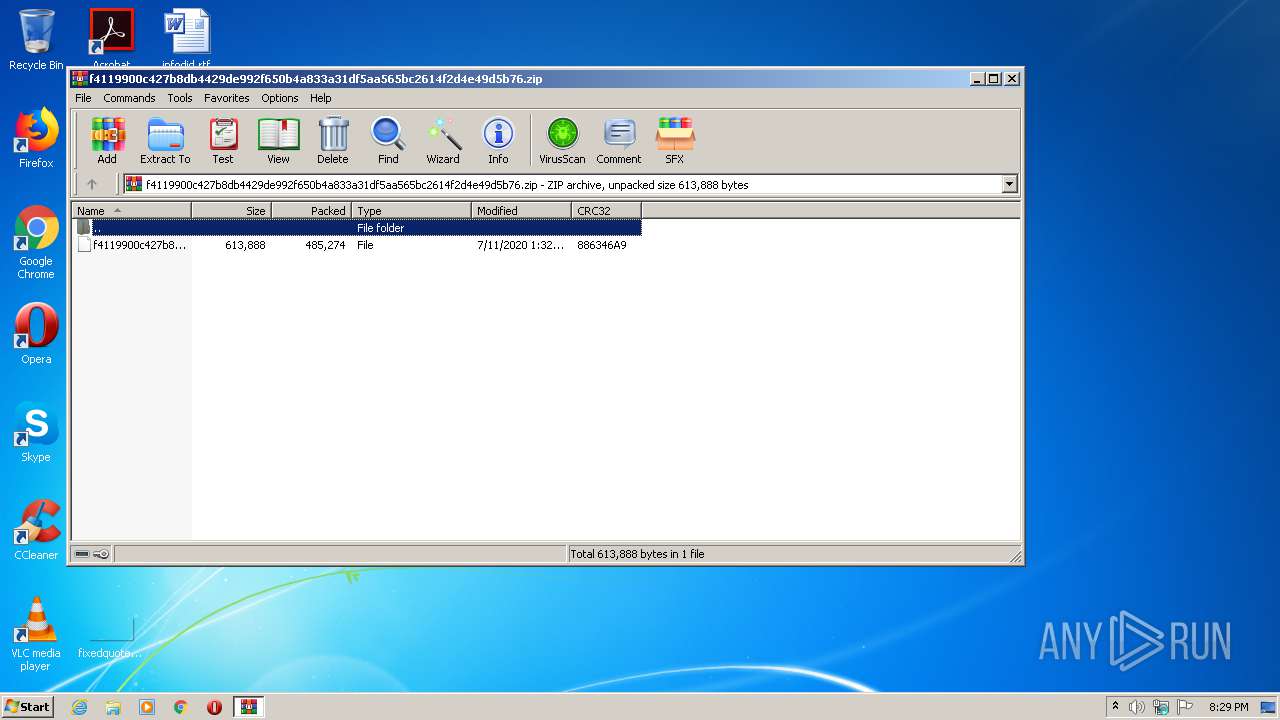
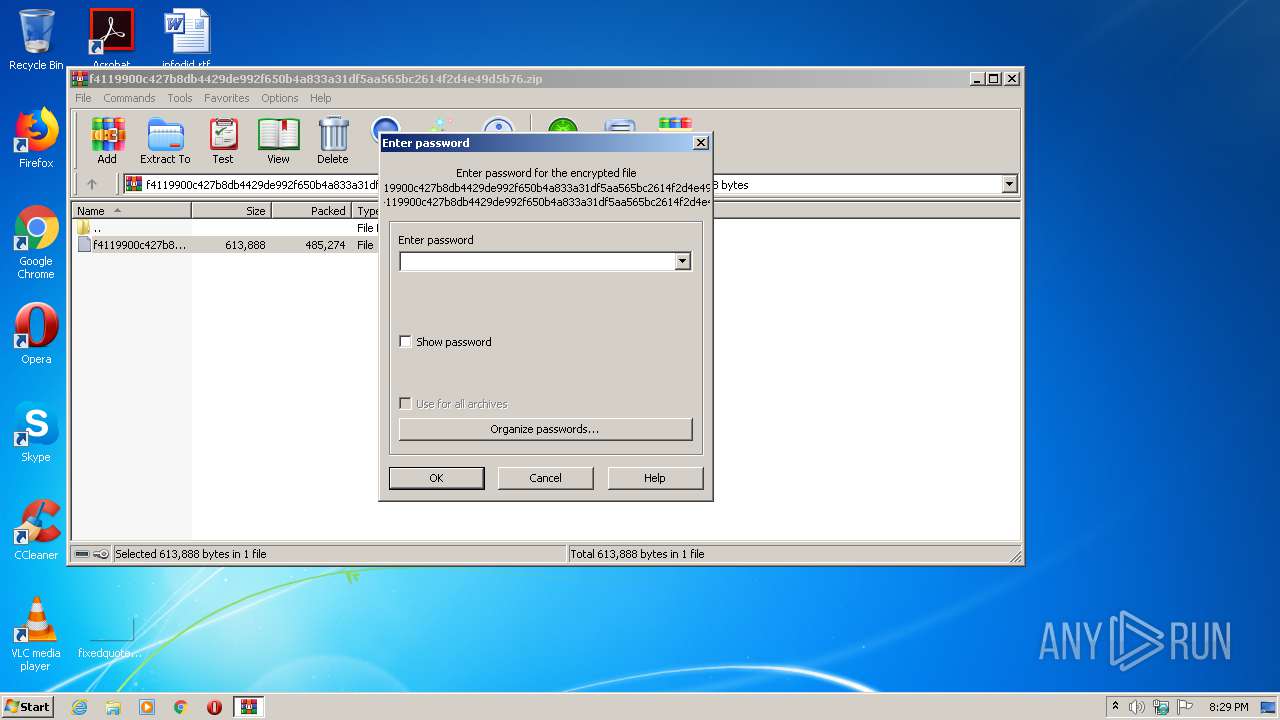
| File name: | f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.zip |
| Full analysis: | https://app.any.run/tasks/159a8b5b-0029-4d72-b500-89136743d4d2 |
| Verdict: | Malicious activity |
| Analysis date: | July 12, 2020, 19:28:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 2448D32F7822C7E2568F98CF471ED4CC |
| SHA1: | 26E131BDB54E83B44584982E328243DE0E1C9D99 |
| SHA256: | 561EA5C9BA256F8A217B12DE76412EA35A6902D0919669649CED334E920C62A0 |
| SSDEEP: | 12288:pWTL7So2EcqqkL0VHxd7KqJSiEs/CUkzF2CtVQpkE:pWX+XpqqRt7XJSDUkZdaj |
MALICIOUS
Application was dropped or rewritten from another process
- f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.exe (PID: 3644)
- f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.exe (PID: 2352)
Actions looks like stealing of personal data
- f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.exe (PID: 2352)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 184)
Application launched itself
- f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.exe (PID: 3644)
Reads Environment values
- f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.exe (PID: 2352)
INFO
Manual execution by user
- f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.exe (PID: 3644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
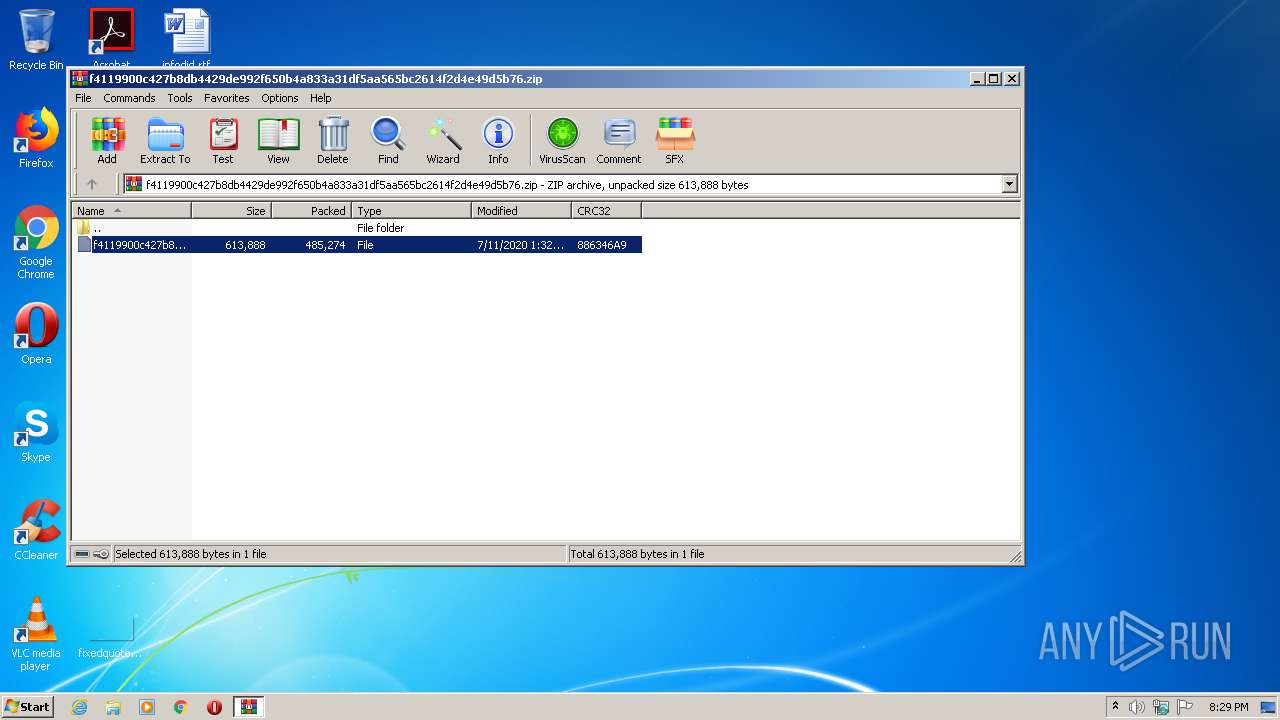
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:07:11 12:32:26 |
| ZipCRC: | 0x886346a9 |
| ZipCompressedSize: | 485274 |
| ZipUncompressedSize: | 613888 |
| ZipFileName: | f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76 |
Total processes
38
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2352 | "{path}" | C:\Users\admin\Desktop\f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.exe | f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: HotelManagementSystemRoom Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3644 | "C:\Users\admin\Desktop\f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.exe" | C:\Users\admin\Desktop\f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: HotelManagementSystemRoom Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
525
Read events
487
Write events
38
Delete events
0
Modification events
| (PID) Process: | (184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (184) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (184) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.zip | |||
| (PID) Process: | (184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 184 | WinRAR.exe | C:\Users\admin\Desktop\f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76 | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2352 | f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.exe | 67.21.94.15:587 | mail.mehatinfo.com | Sharktech | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mail.mehatinfo.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2352 | f4119900c427b8db4429de992f650b4a833a31df5aa565bc2614f2d4e49d5b76.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |