| URL: | http://techomap.com/DbEPdXiz |
| Full analysis: | https://app.any.run/tasks/7e23699e-80b7-4896-865c-79289e0d15bc |
| Verdict: | Malicious activity |
| Analysis date: | March 08, 2020, 00:48:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 593AE92CA92B6109C90434158DE17D03 |
| SHA1: | F59AC799D4309BD2E78B65FD5E4E498F54B99E40 |
| SHA256: | 55F87A485C039ADA448A0928B9A97C73618A821B9D074B06B9643775387747D3 |
| SSDEEP: | 3:N1KKAB5VZRl:CKM5VZD |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 1488)
Executable content was dropped or overwritten
- iexplore.exe (PID: 1460)
INFO
Reads internet explorer settings
- iexplore.exe (PID: 2380)
- iexplore.exe (PID: 1460)
- iexplore.exe (PID: 3040)
Reads Internet Cache Settings
- iexplore.exe (PID: 2380)
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 3232)
- iexplore.exe (PID: 1460)
Changes internet zones settings
- iexplore.exe (PID: 3232)
Application launched itself
- iexplore.exe (PID: 3232)
Creates files in the user directory
- iexplore.exe (PID: 1460)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 1488)
- iexplore.exe (PID: 2380)
- iexplore.exe (PID: 3232)
- iexplore.exe (PID: 3040)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3232)
Reads settings of System Certificates
- iexplore.exe (PID: 3040)
- iexplore.exe (PID: 1460)
- iexplore.exe (PID: 3232)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3232)
Changes settings of System certificates
- iexplore.exe (PID: 3232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1460 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3232 CREDAT:1316110 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1488 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 2380 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3232 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3040 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3232 CREDAT:595227 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
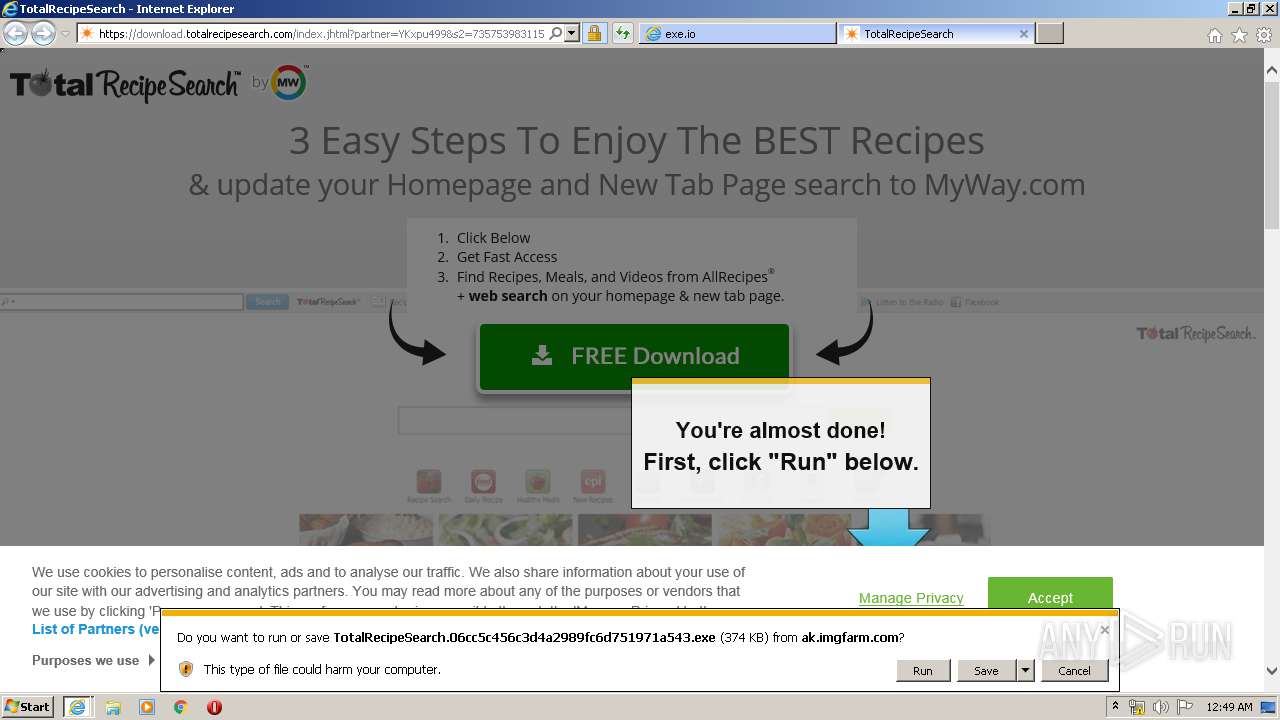
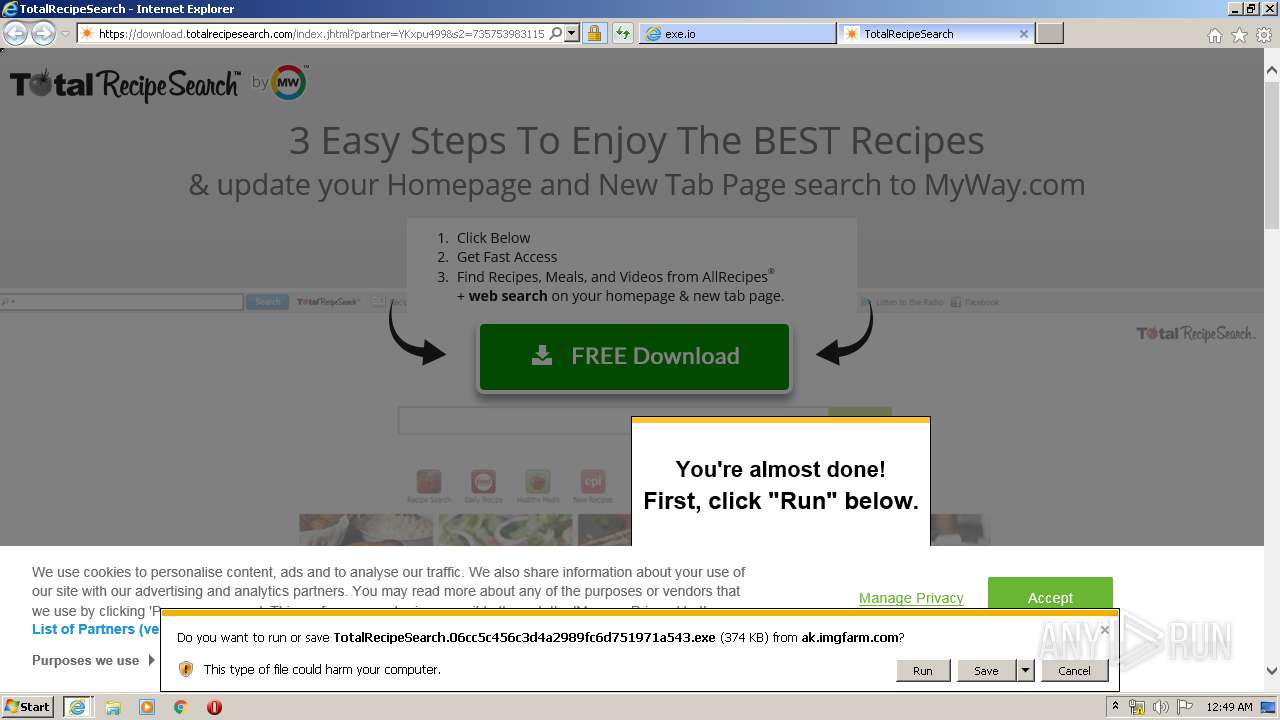
| 3232 | "C:\Program Files\Internet Explorer\iexplore.exe" http://techomap.com/DbEPdXiz | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
7 700
Read events
1 581
Write events
4 150
Delete events
1 969
Modification events
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1565060050 | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30799075 | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
1
Suspicious files
166
Text files
219
Unknown types
86
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2380 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab6F4C.tmp | — | |
MD5:— | SHA256:— | |||
| 2380 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar6F4D.tmp | — | |
MD5:— | SHA256:— | |||
| 2380 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_74167E25E5476CCA2A5946AAA61BF9E1 | der | |
MD5:— | SHA256:— | |||
| 2380 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_74167E25E5476CCA2A5946AAA61BF9E1 | binary | |
MD5:— | SHA256:— | |||
| 2380 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C1B3CC7FF1466C71640A202F8258105B_17C6FDBF2E14A0D68CF198FE1D16D9F5 | binary | |
MD5:— | SHA256:— | |||
| 2380 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\DbEPdXiz[2].htm | html | |
MD5:— | SHA256:— | |||
| 2380 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C1B3CC7FF1466C71640A202F8258105B_17C6FDBF2E14A0D68CF198FE1D16D9F5 | der | |
MD5:— | SHA256:— | |||
| 2380 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\8QU1CQCK.txt | text | |
MD5:— | SHA256:— | |||
| 2380 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\DbEPdXiz[1].htm | html | |
MD5:— | SHA256:— | |||
| 2380 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\BSTVR2RZ.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
86
TCP/UDP connections
235
DNS requests
76
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2380 | iexplore.exe | GET | 301 | 104.18.49.128:80 | http://techomap.com/DbEPdXiz | US | — | — | unknown |
2380 | iexplore.exe | GET | 200 | 143.204.208.79:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2380 | iexplore.exe | GET | 200 | 172.217.22.67:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2380 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
2380 | iexplore.exe | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
2380 | iexplore.exe | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
2380 | iexplore.exe | GET | 200 | 172.217.22.67:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCSaJP2bCz9oAgAAAAALnFI | US | der | 472 b | whitelisted |
2380 | iexplore.exe | GET | 200 | 2.21.242.204:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgMPIBlarex%2BUQfZqXbMwhzimQ%3D%3D | NL | der | 527 b | whitelisted |
2380 | iexplore.exe | GET | 200 | 2.21.242.221:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | NL | der | 1.37 Kb | whitelisted |
2380 | iexplore.exe | GET | 200 | 172.217.22.67:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCSaJP2bCz9oAgAAAAALnFI | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2380 | iexplore.exe | 104.18.49.128:443 | techomap.com | Cloudflare Inc | US | unknown |
2380 | iexplore.exe | 143.204.202.113:443 | cdn.linearicons.com | — | US | suspicious |
2380 | iexplore.exe | 212.129.18.61:443 | sayfibhat.club | Online S.a.s. | FR | unknown |
2380 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3232 | iexplore.exe | 104.18.49.128:443 | techomap.com | Cloudflare Inc | US | unknown |
2380 | iexplore.exe | 104.18.49.128:80 | techomap.com | Cloudflare Inc | US | unknown |
— | — | 172.217.23.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
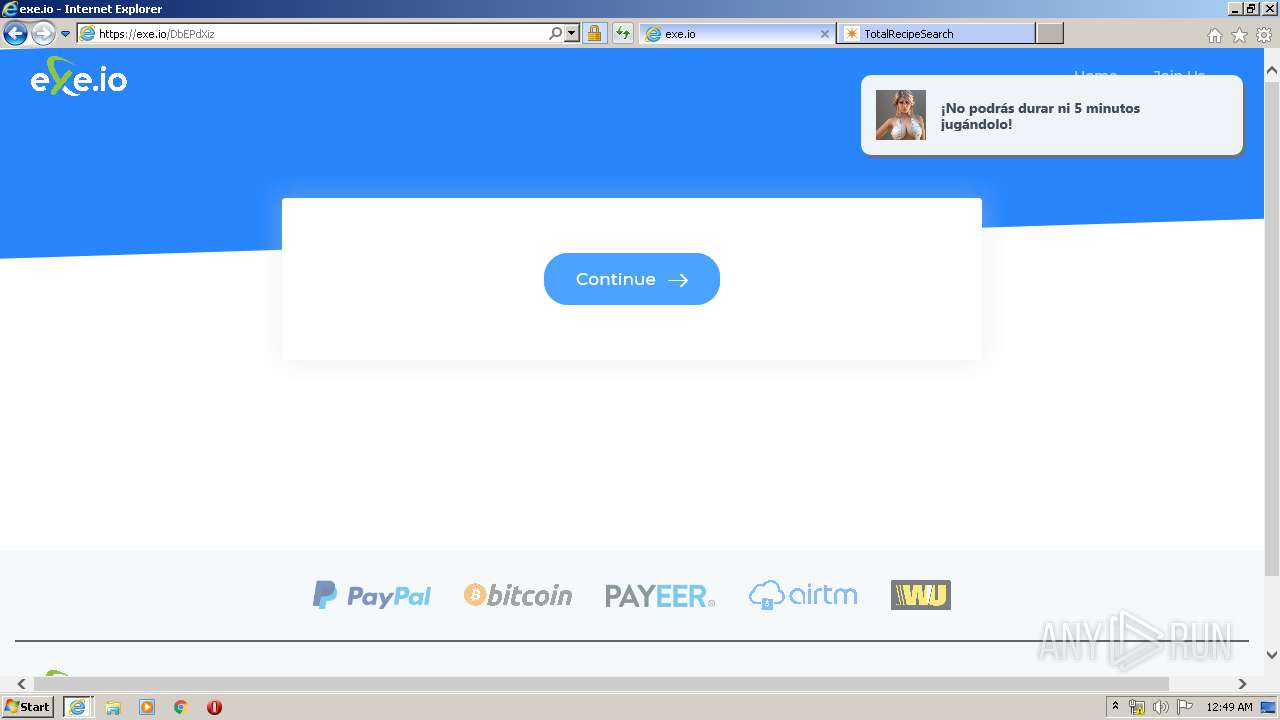
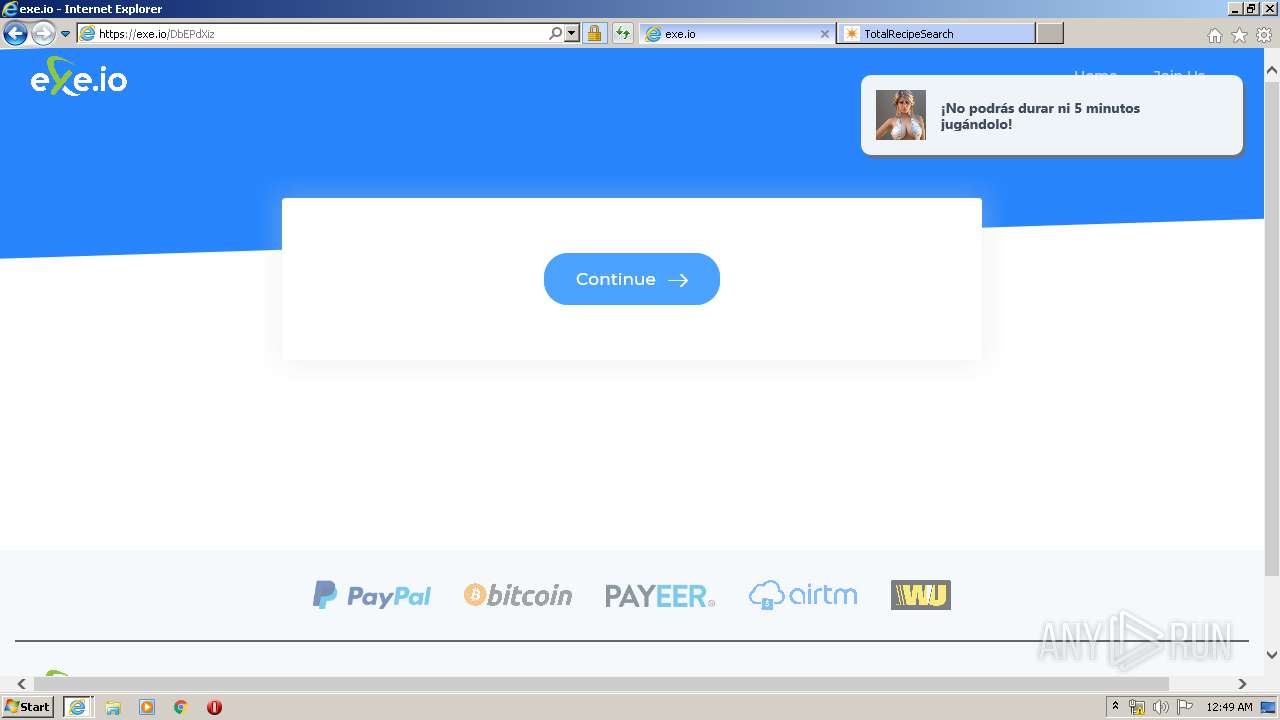
2380 | iexplore.exe | 104.26.2.103:443 | exe.io | Cloudflare Inc | US | shared |
2380 | iexplore.exe | 143.204.208.110:443 | d141wsrw9m4as6.cloudfront.net | — | US | malicious |
2380 | iexplore.exe | 172.217.23.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
techomap.com |
| unknown |
ocsp.digicert.com |
| whitelisted |
exe.io |
| malicious |
fonts.googleapis.com |
| whitelisted |
cdn.linearicons.com |
| shared |
sayfibhat.club |
| suspicious |
d141wsrw9m4as6.cloudfront.net |
| shared |
dc5k8fg5ioc8s.cloudfront.net |
| shared |
www.googletagmanager.com |
| whitelisted |
www.recaptcha.net |
| whitelisted |