| File name: | 4a3e496581bc6ca886da55e67c566441 |
| Full analysis: | https://app.any.run/tasks/d9b5fc9d-1376-4918-ab8b-6fe79df67b31 |
| Verdict: | Malicious activity |
| Analysis date: | September 11, 2019, 07:55:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 5.1, Code page: 936, Author: User, Template: Normal.dot, Last Saved By: User, Revision Number: 2, Name of Creating Application: Microsoft Office Word, Total Editing Time: 03:00, Create Time/Date: Thu Sep 28 18:06:00 2006, Last Saved Time/Date: Thu Sep 28 18:09:00 2006, Number of Pages: 1, Number of Words: 5, Number of Characters: 35, Security: 0 |
| MD5: | 4A3E496581BC6CA886DA55E67C566441 |
| SHA1: | 6376C63BAE114D171AB1B0557D7CEDD8EA5382B9 |
| SHA256: | 55EC9749E0692951CE38C02A3410A99CC38EAB94724649851744FF3B5268E3FC |
| SSDEEP: | 3072:P84pq6AmakExyrsWl4h3QNycFlKEWUmGCv3ZLyqGq:JOzkExyuQNycFlKEWUmj3Zh |
MALICIOUS
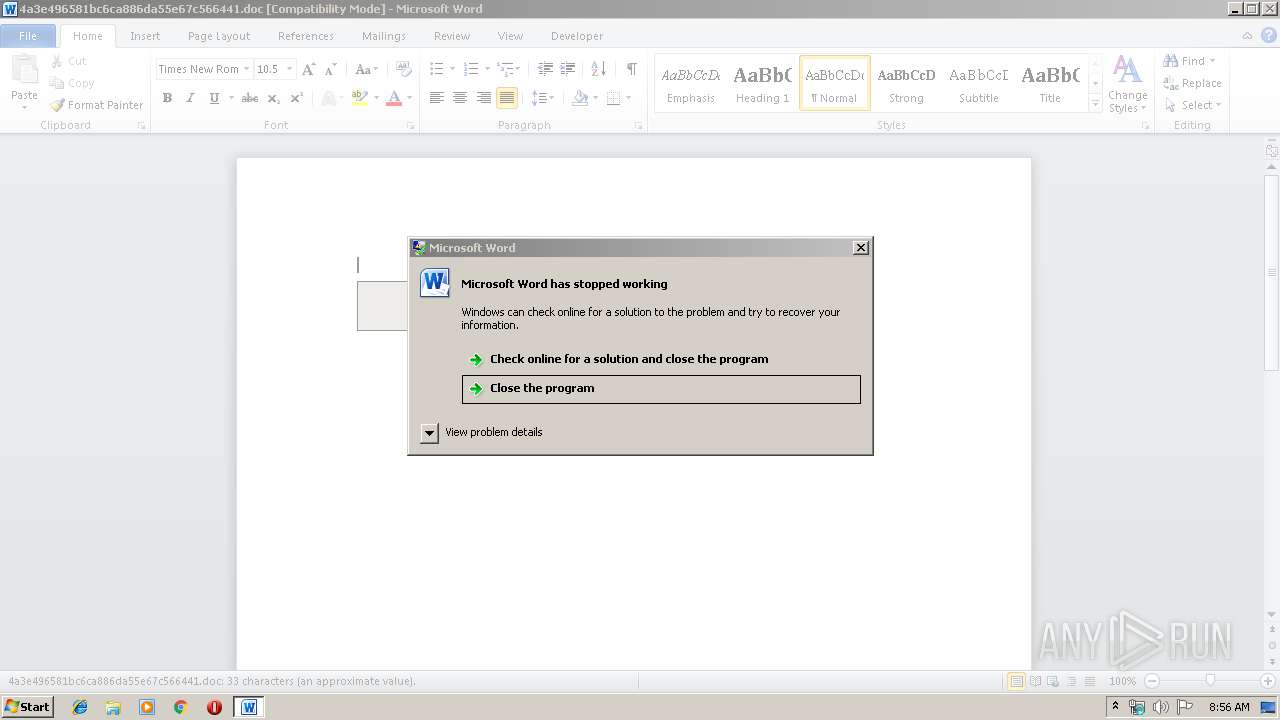
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3424)
SUSPICIOUS
No suspicious indicators.INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3424)
Creates files in the user directory
- WINWORD.EXE (PID: 3424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (80) |
|---|
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | User |
| Keywords: | - |
| Template: | Normal.dot |
| LastModifiedBy: | User |
| RevisionNumber: | 2 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 3.0 minutes |
| CreateDate: | 2006:09:28 17:06:00 |
| ModifyDate: | 2006:09:28 17:09:00 |
| Pages: | 1 |
| Words: | 5 |
| Characters: | 35 |
| Security: | None |
| CodePage: | Windows Simplified Chinese (PRC, Singapore) |
| Company: | HOME |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 39 |
| AppVersion: | 11.9999 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 31 |
| CompObjUserType: | Microsoft Office Word Document |
Total processes
34
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2516 | "C:\PROGRA~1\COMMON~1\MICROS~1\DW\DW20.EXE" -x -s 1356 | C:\PROGRA~1\COMMON~1\MICROS~1\DW\DW20.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Application Error Reporting Exit code: 0 Version: 14.0.6015.1000 Modules
| |||||||||||||||
| 3424 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\4a3e496581bc6ca886da55e67c566441.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3632 | C:\Windows\system32\dwwin.exe -x -s 1356 | C:\Windows\system32\dwwin.exe | — | DW20.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Watson Client Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 074
Read events
989
Write events
80
Delete events
5
Modification events
| (PID) Process: | (3424) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | m~# |
Value: 6D7E2300600D0000010000000000000000000000 | |||
| (PID) Process: | (3424) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3424) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3424) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1328218142 | |||
| (PID) Process: | (3424) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1328218256 | |||
| (PID) Process: | (3424) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1328218257 | |||
| (PID) Process: | (3424) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 600D000032F0B95E7668D50100000000 | |||
| (PID) Process: | (3424) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | t $ |
Value: 74202400600D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3424) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | t $ |
Value: 74202400600D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3424) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3424 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9ADD.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3424 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFDE7B1D201A6DFA0C.TMP | — | |
MD5:— | SHA256:— | |||
| 3424 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF8D56CCC2117E03B8.TMP | — | |
MD5:— | SHA256:— | |||
| 3424 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\1484687.cvr | sqm | |
MD5:— | SHA256:— | |||
| 3424 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3424 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$3e496581bc6ca886da55e67c566441.doc | pgc | |
MD5:— | SHA256:— | |||
| 3424 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSComctlLib.exd | tlb | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report