| download: | index.html |
| Full analysis: | https://app.any.run/tasks/3e1388b4-a9a5-4aec-8d33-fbe27a6f1a0e |
| Verdict: | Malicious activity |
| Analysis date: | January 23, 2019, 05:14:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines, with CRLF, LF line terminators |
| MD5: | A31C803A4A5E2BBF702052800FFDE391 |
| SHA1: | 46C9562AEBDAA33B263FFB9F759F87962546E129 |
| SHA256: | 55E82097F0BD67397484CAA3D061DDDC38058A84638C10F36FFB9DF80DDC5A14 |
| SSDEEP: | 6144:ph71hIOiOmxxb7TI+uw2LPmYikbVMIKy1NFoM72rdA7yJUpx+Qz9KmlTUtGJiJs3:pmLIDaw/CtrUMtQu+TOWjNwxQTQbGj |
MALICIOUS
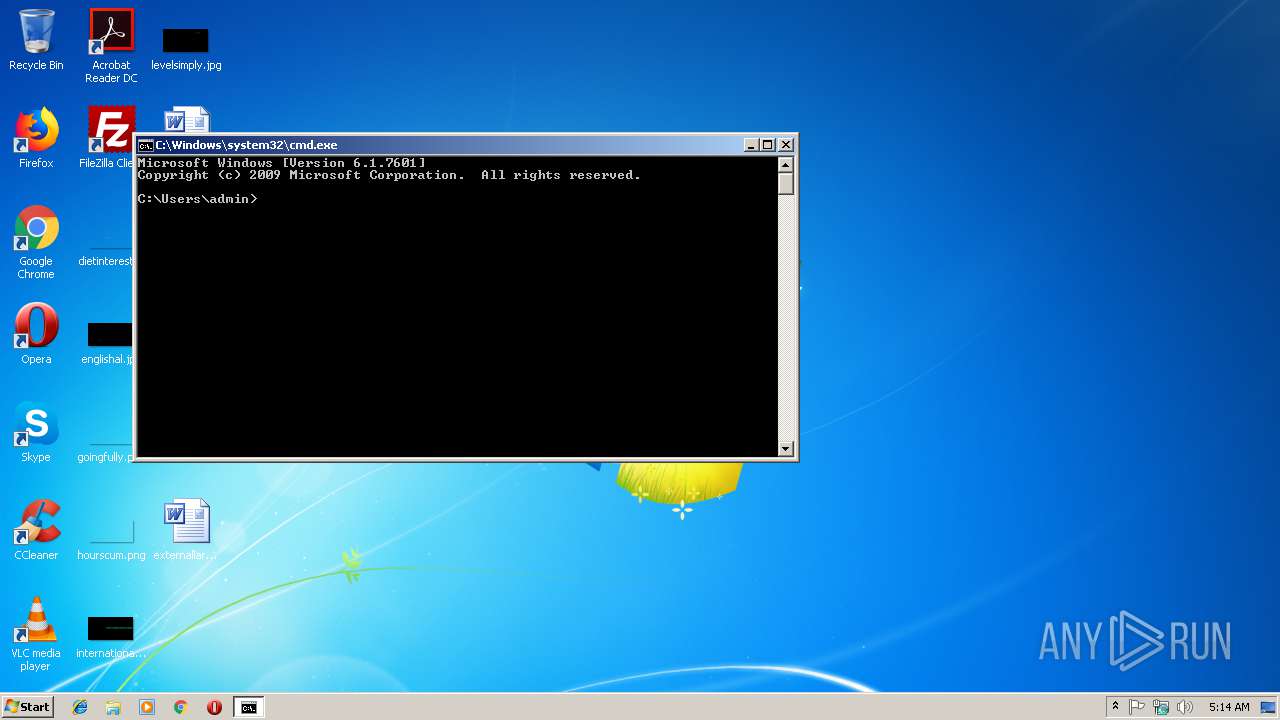
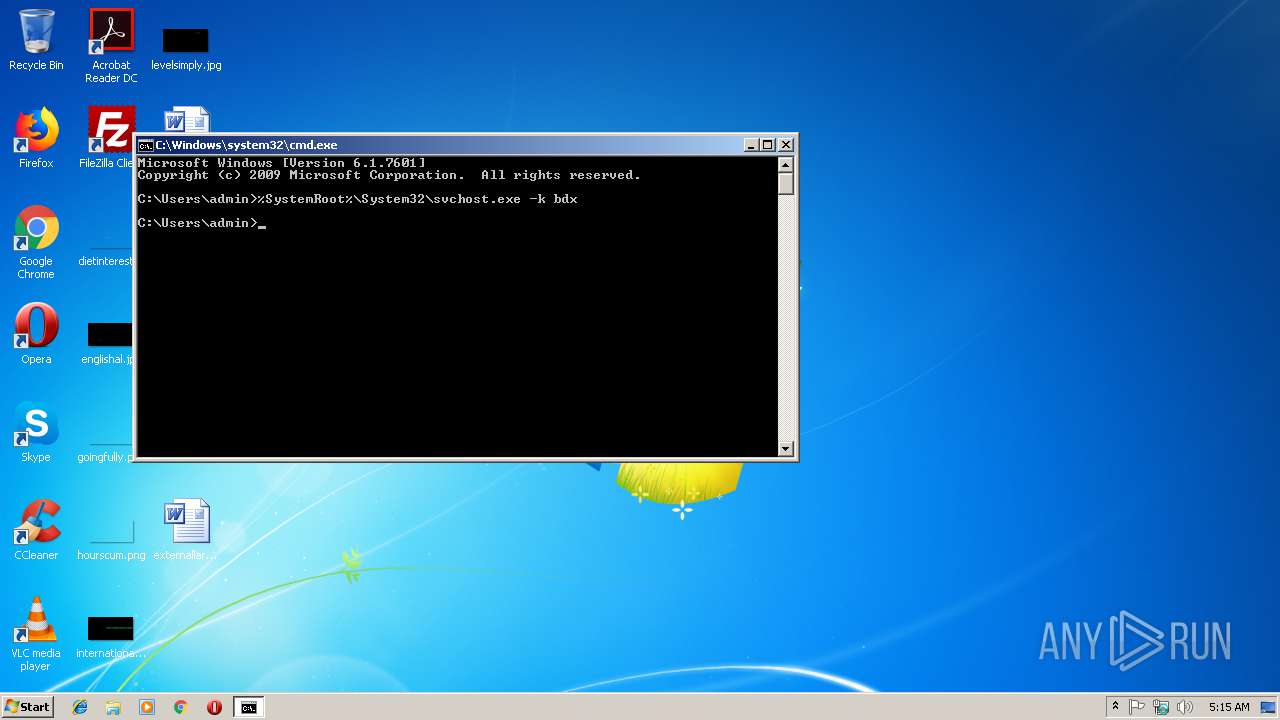
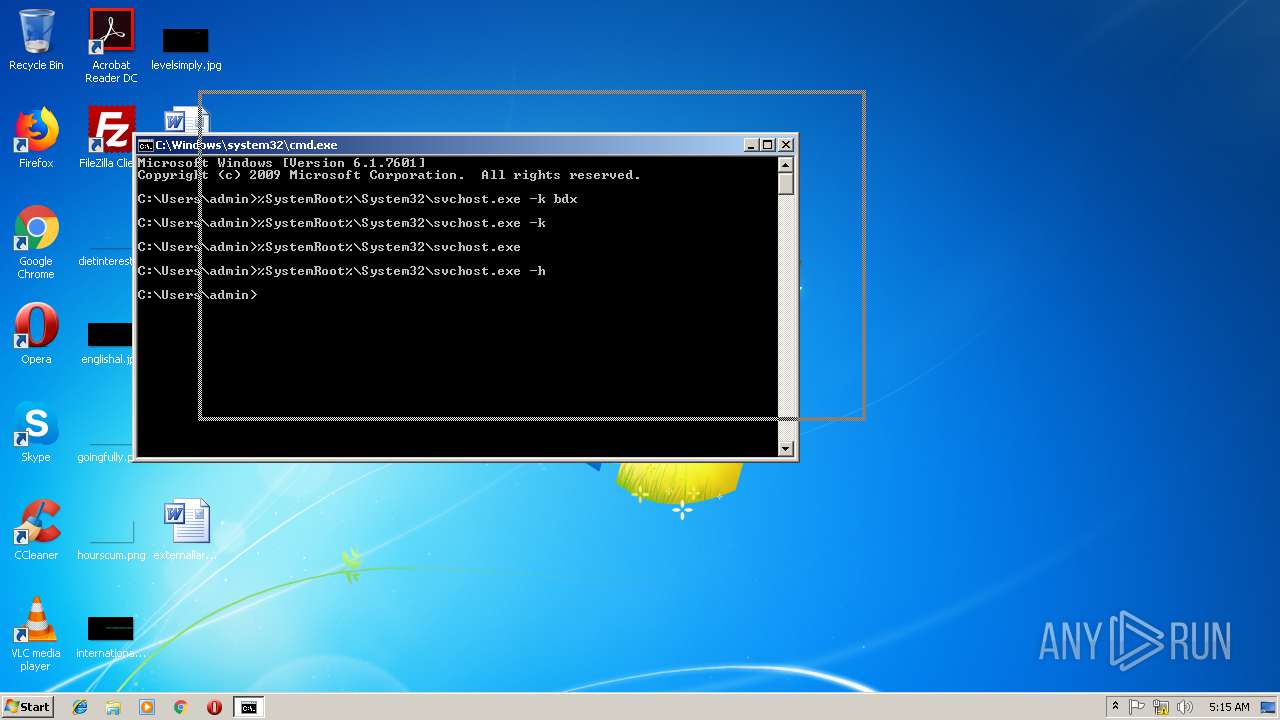
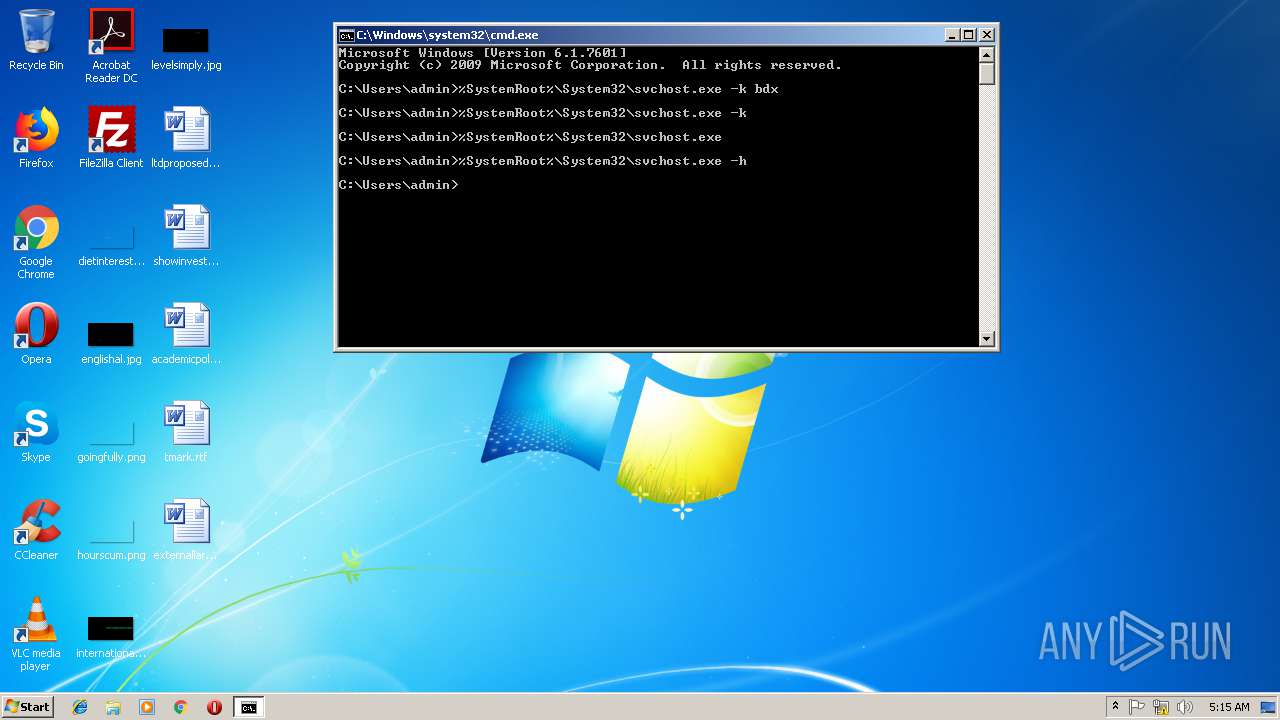
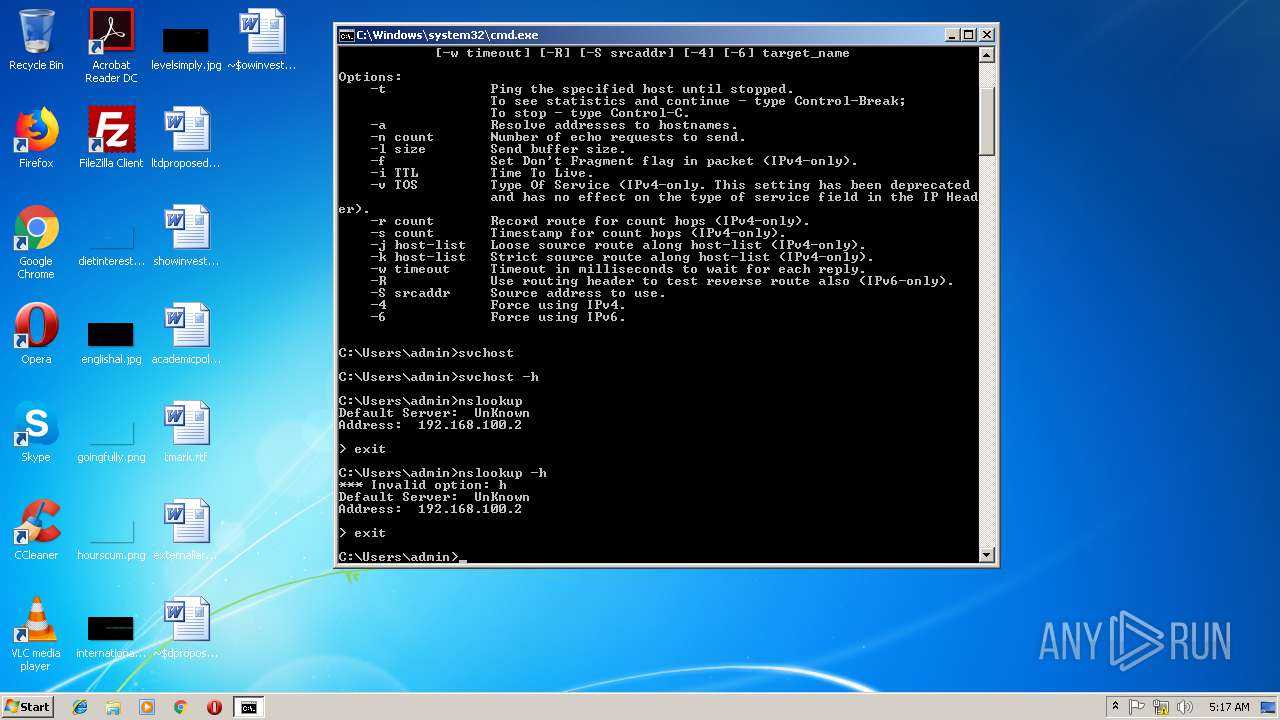
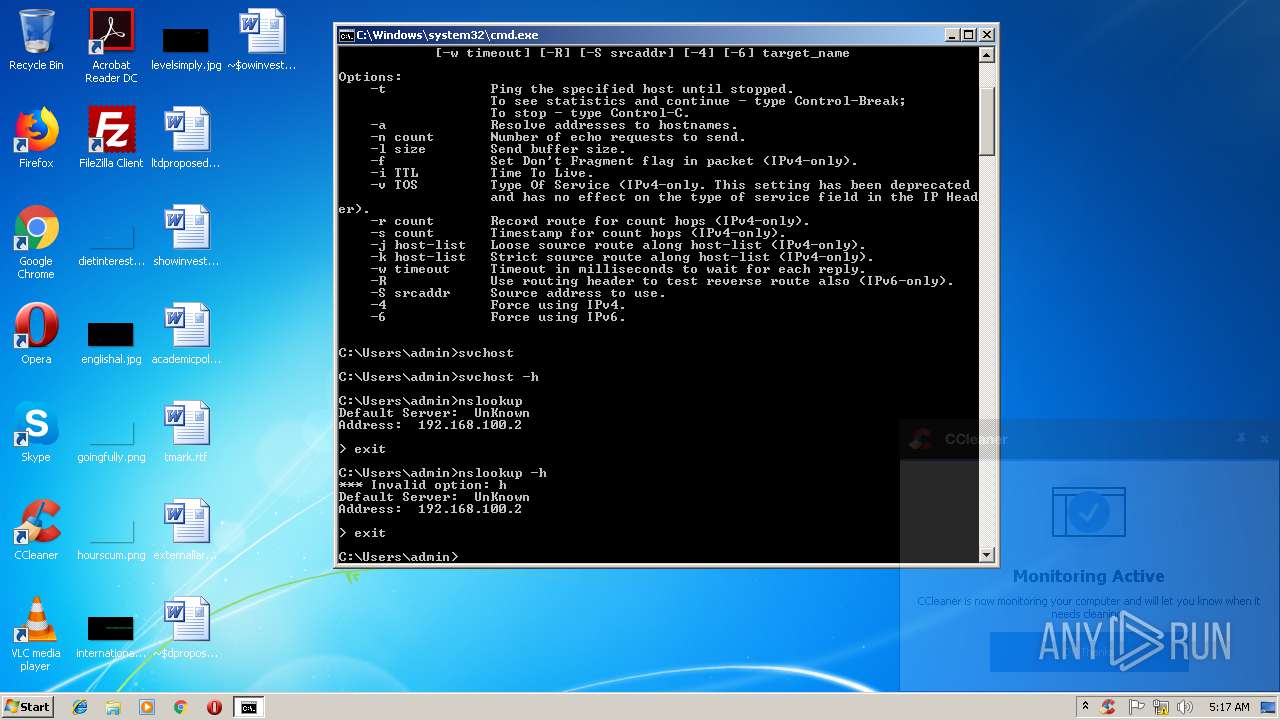
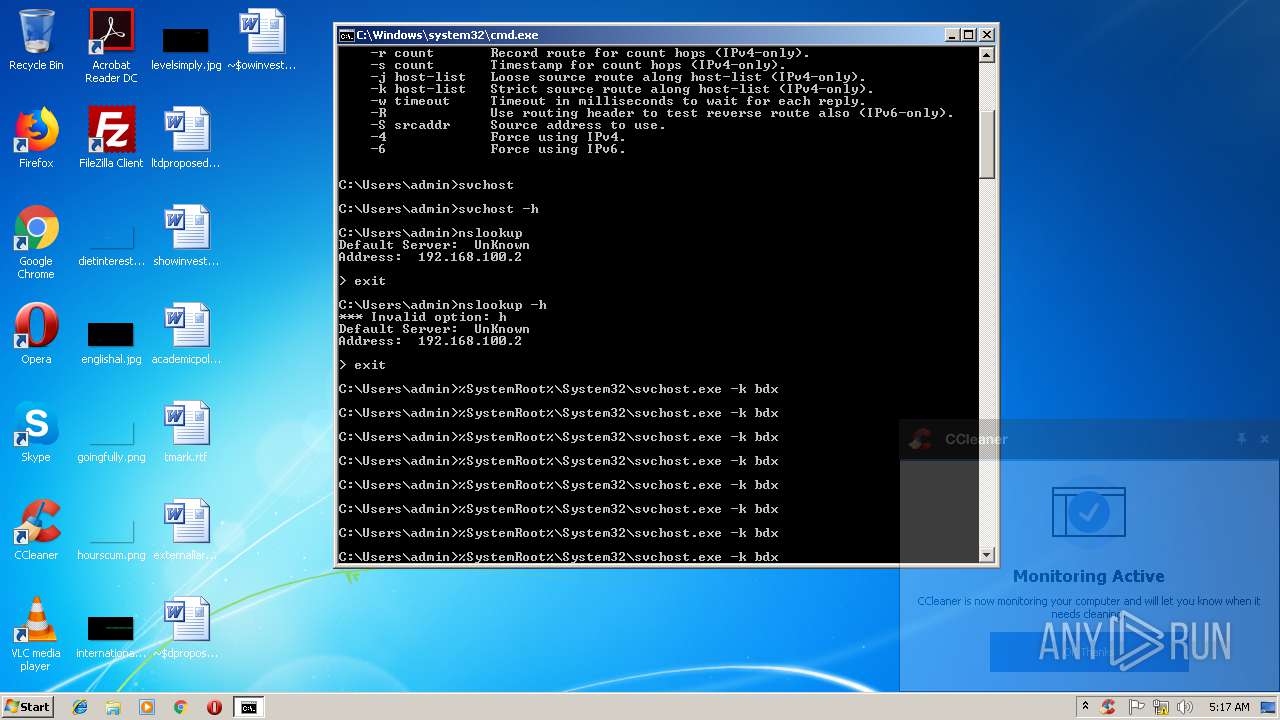
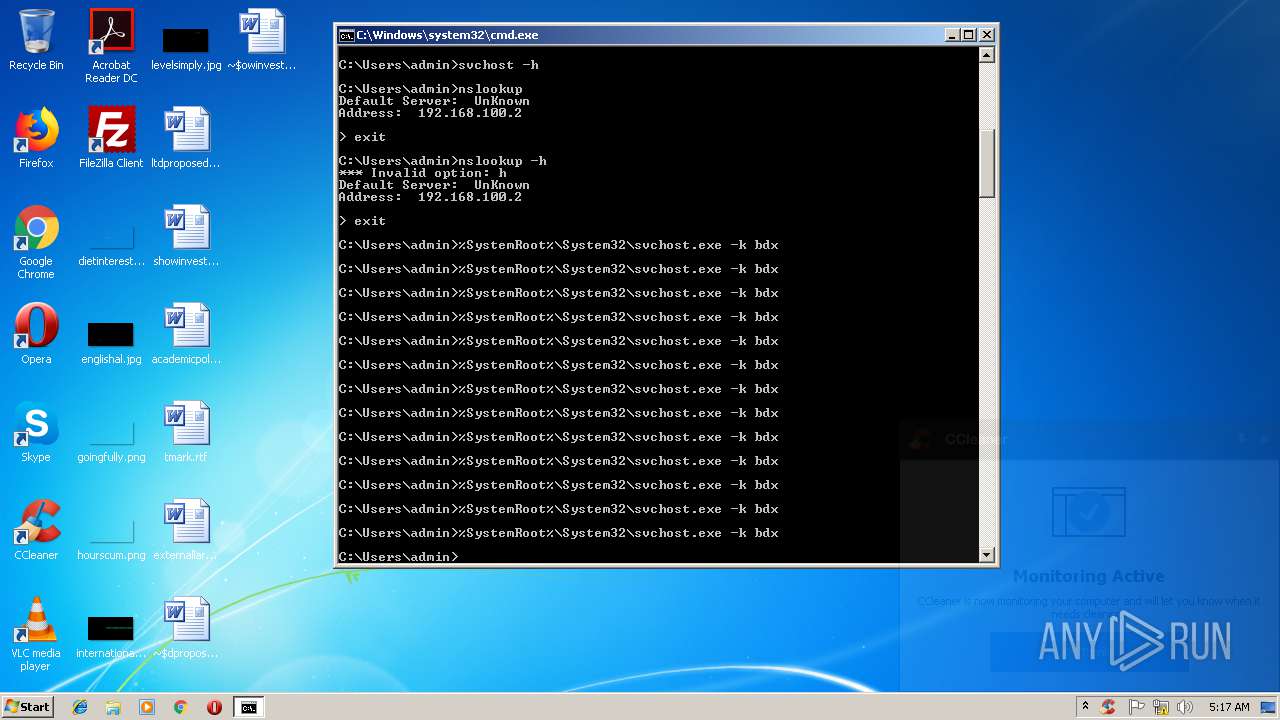
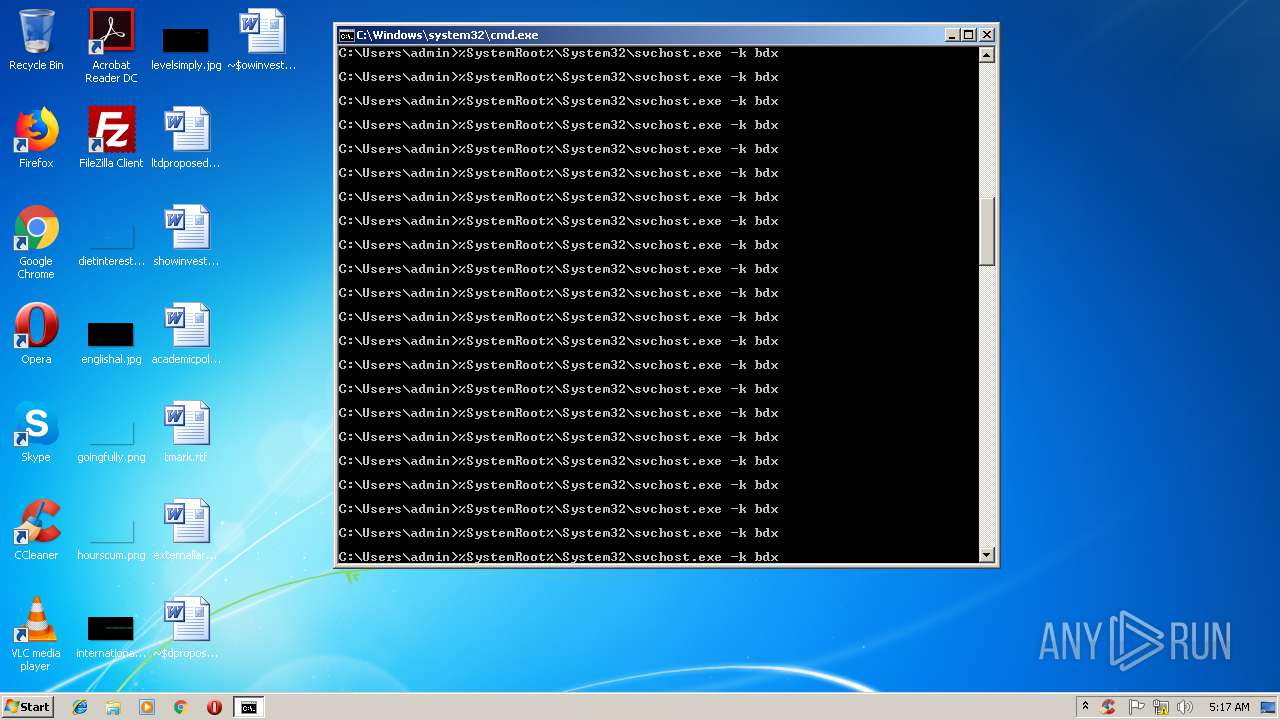
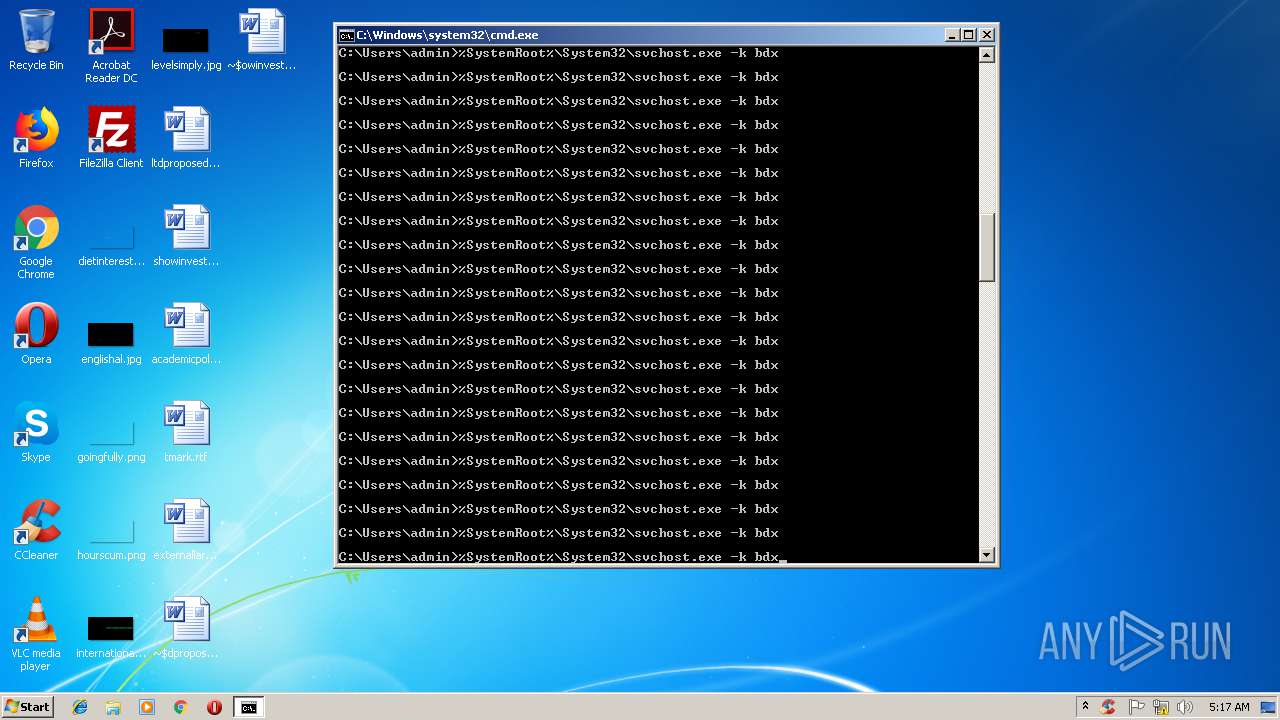
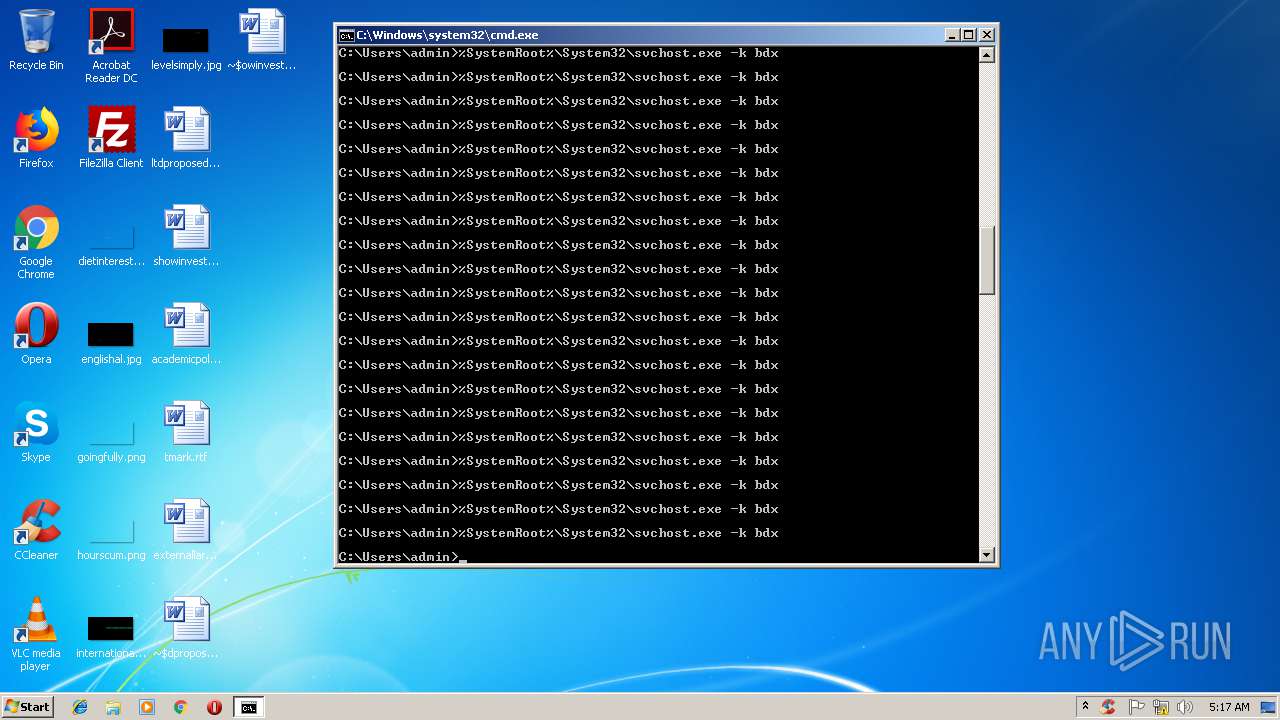
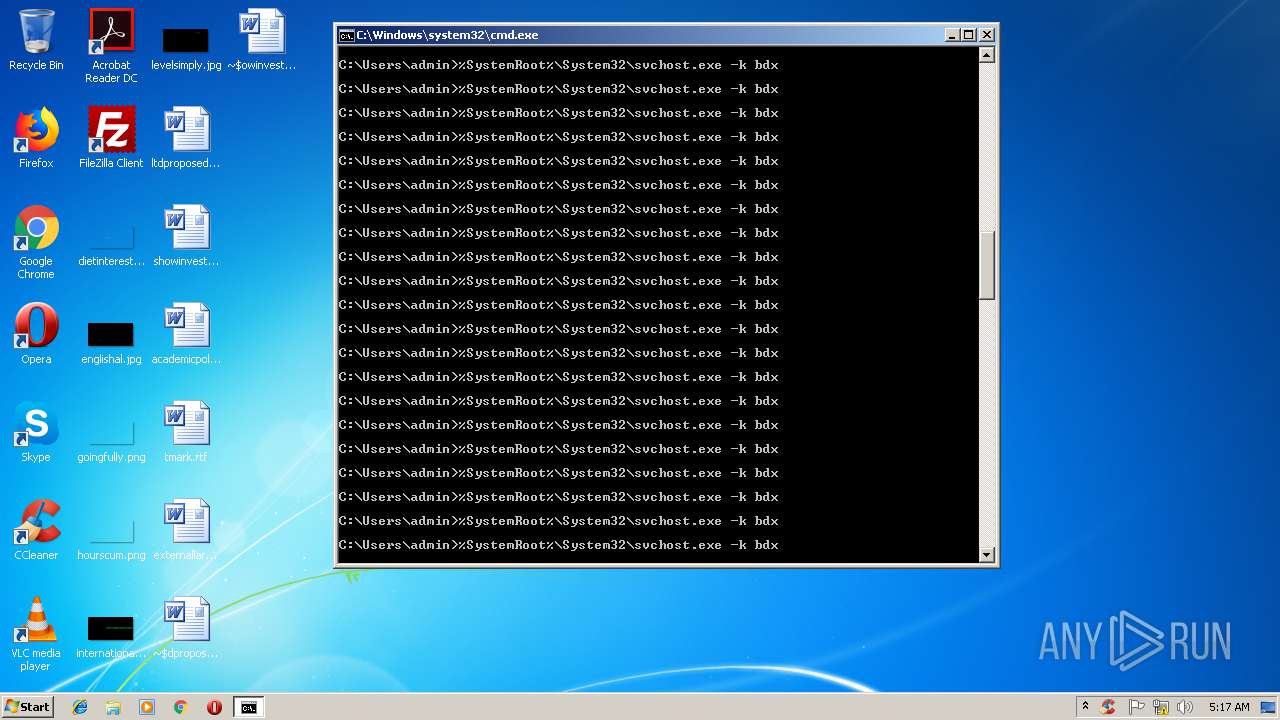
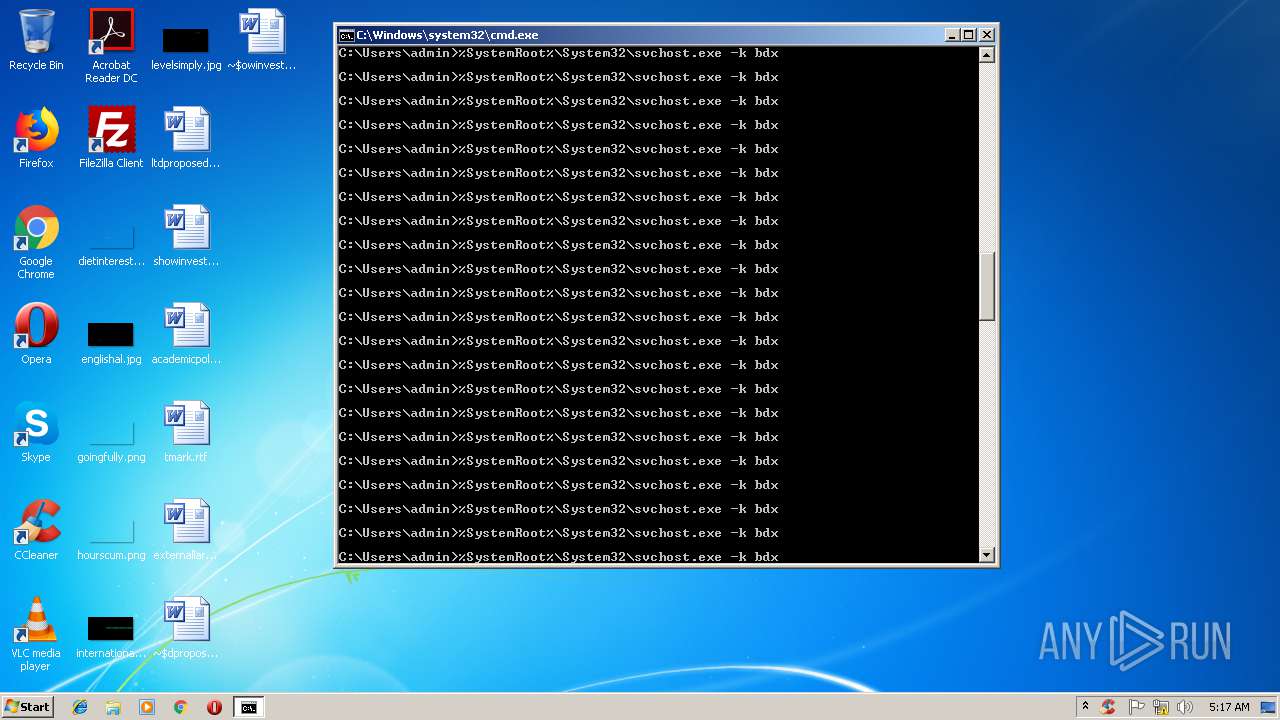
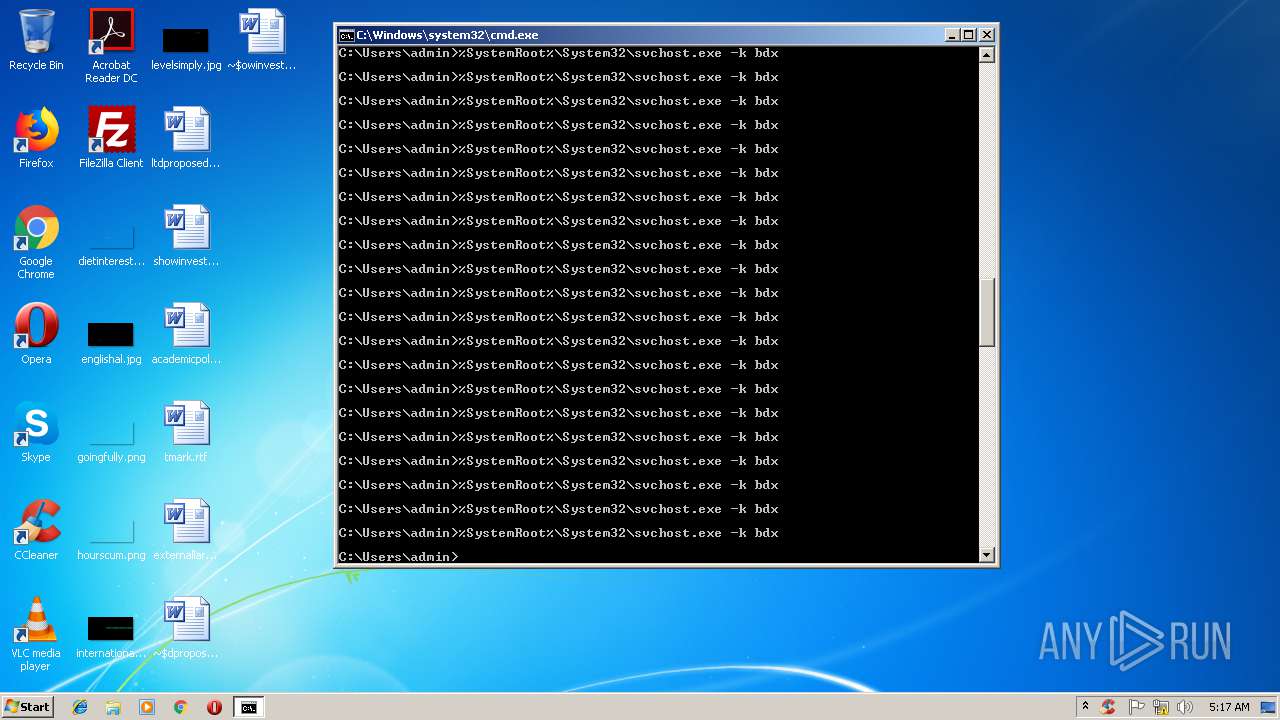
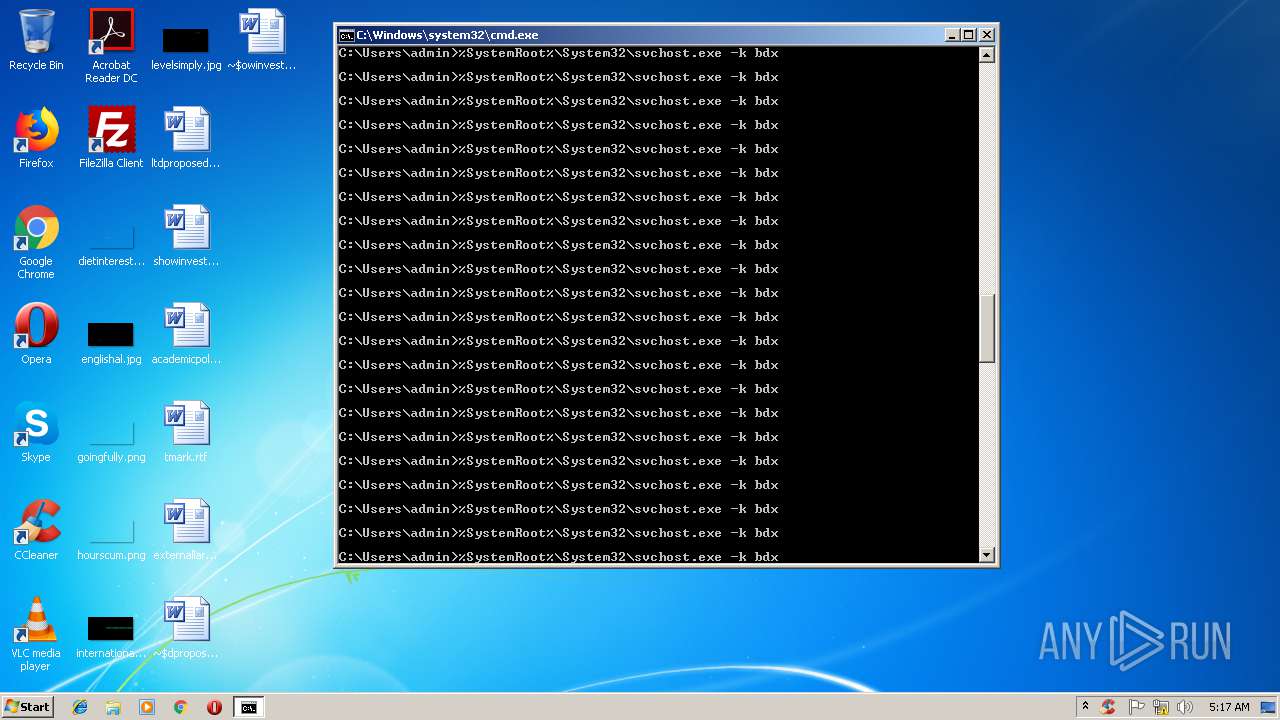
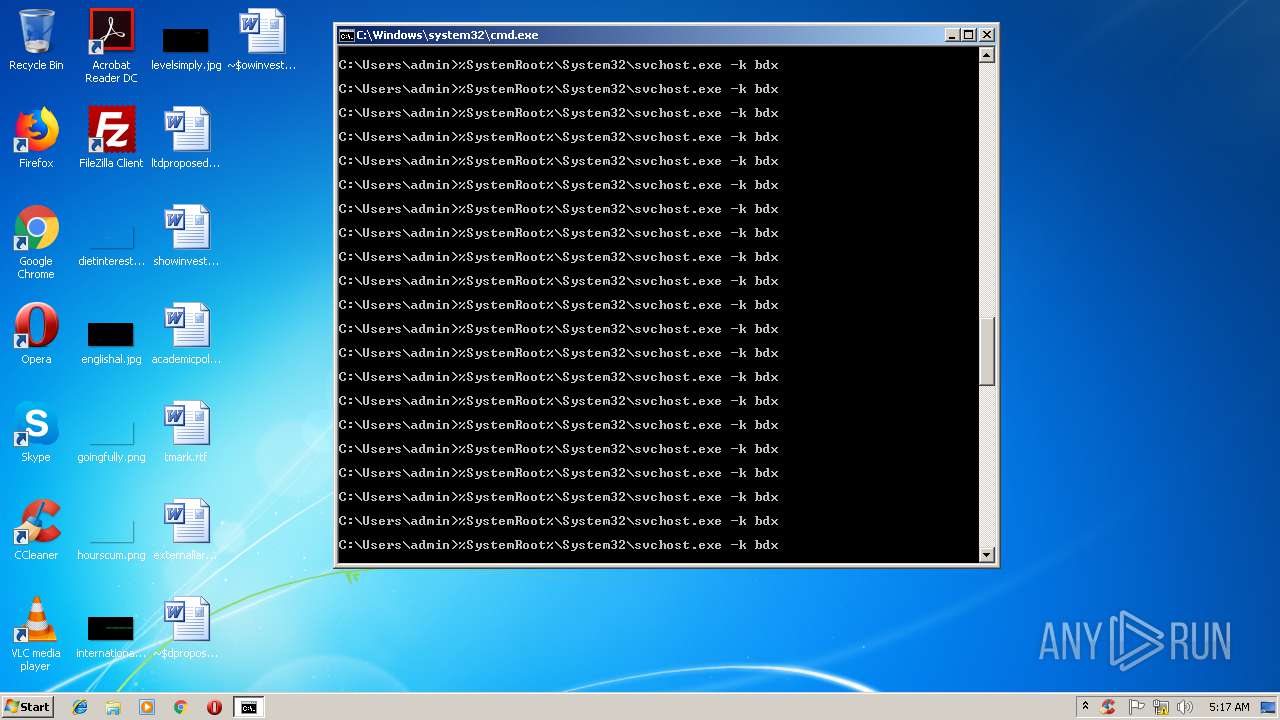
Runs app for hidden code execution
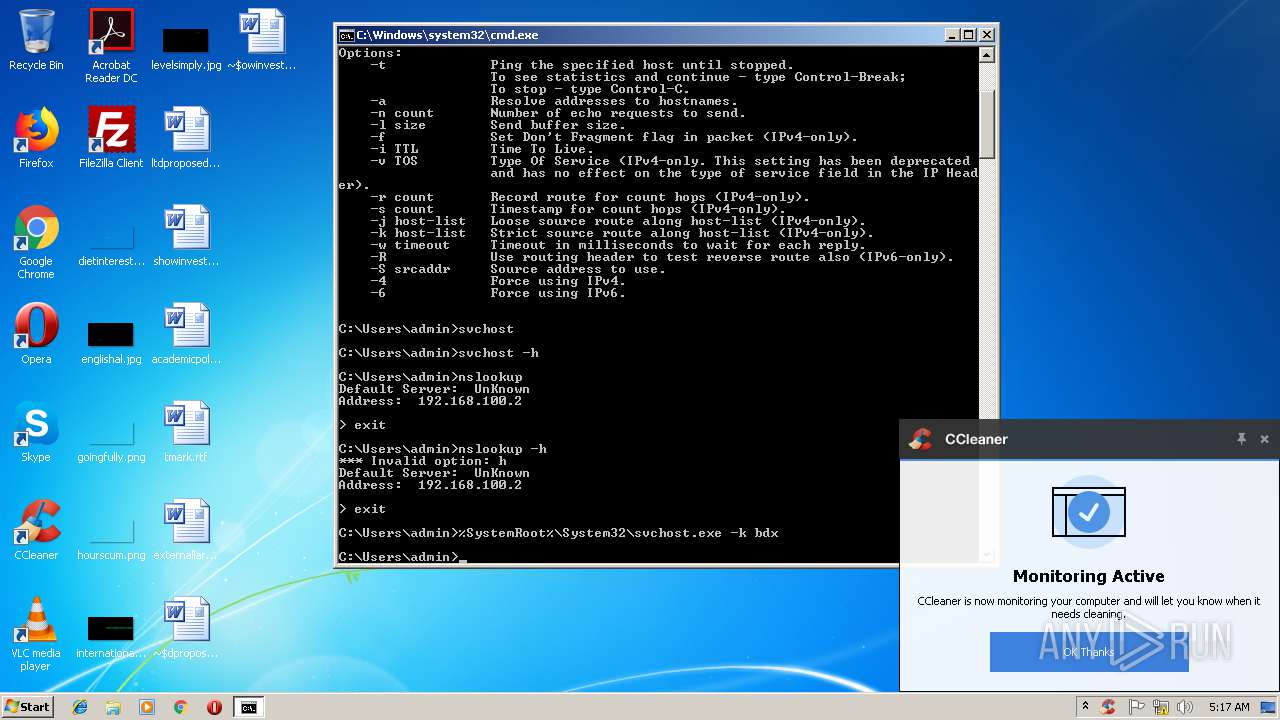
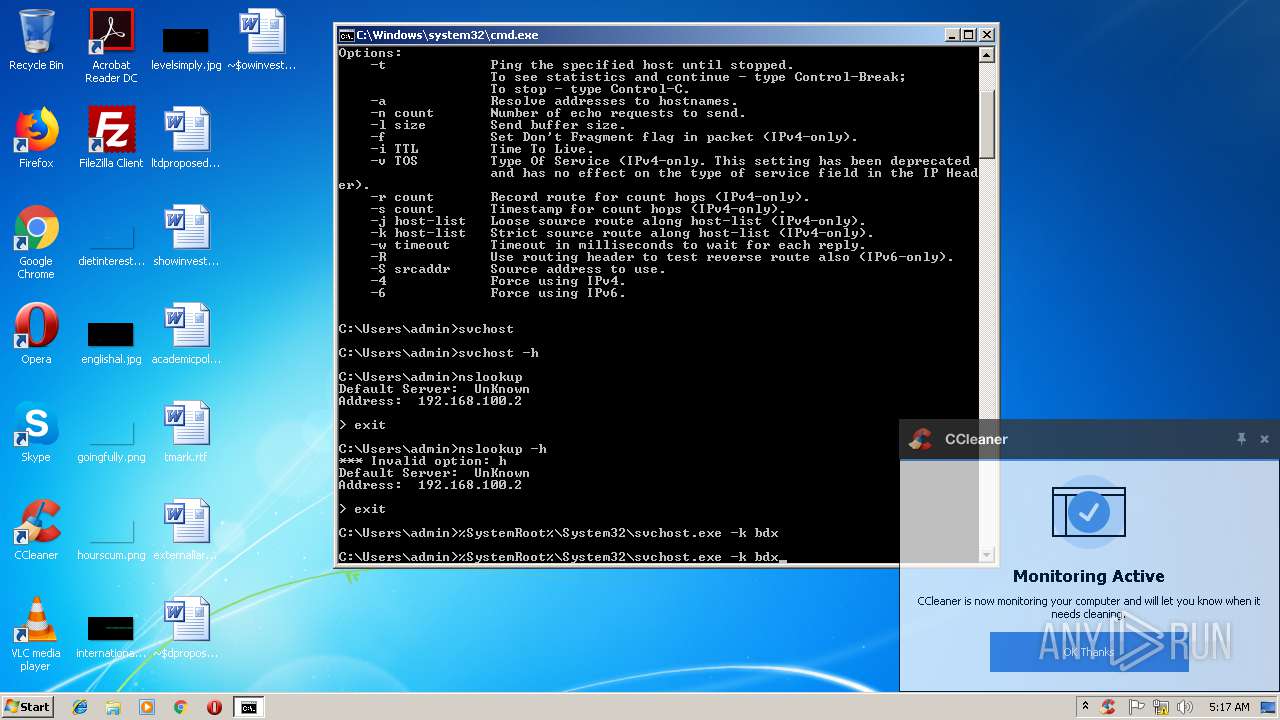
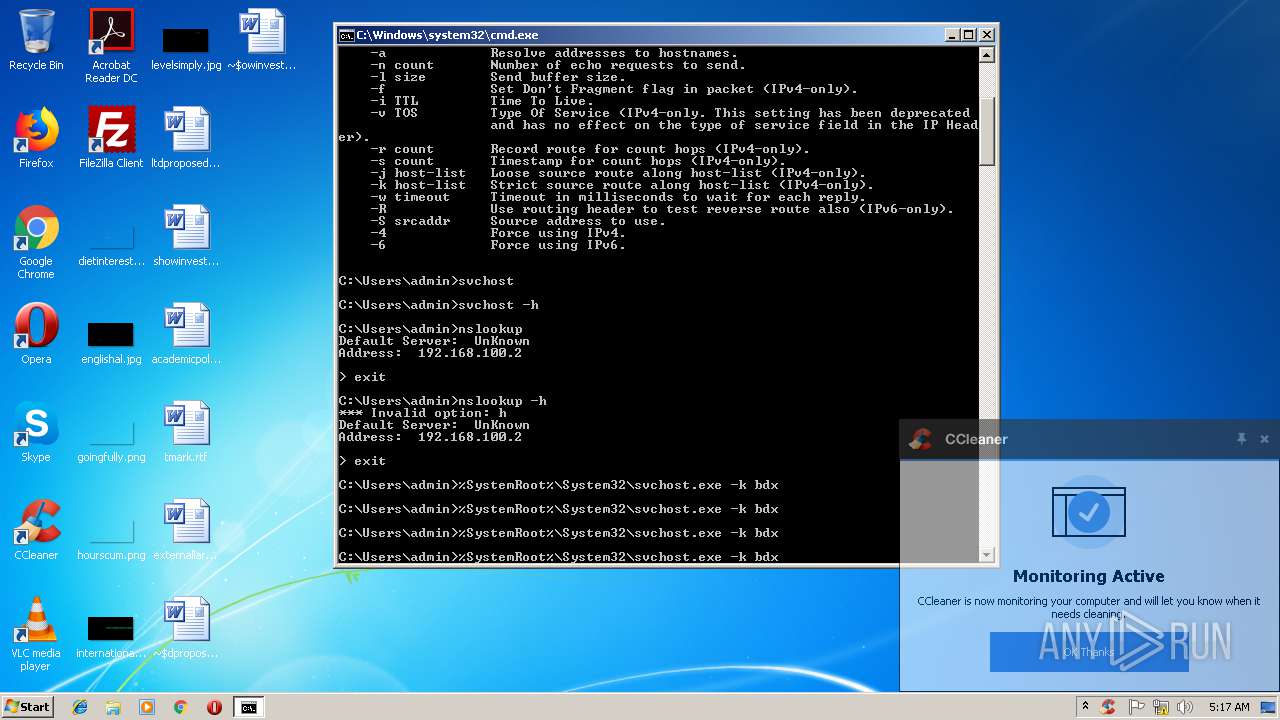
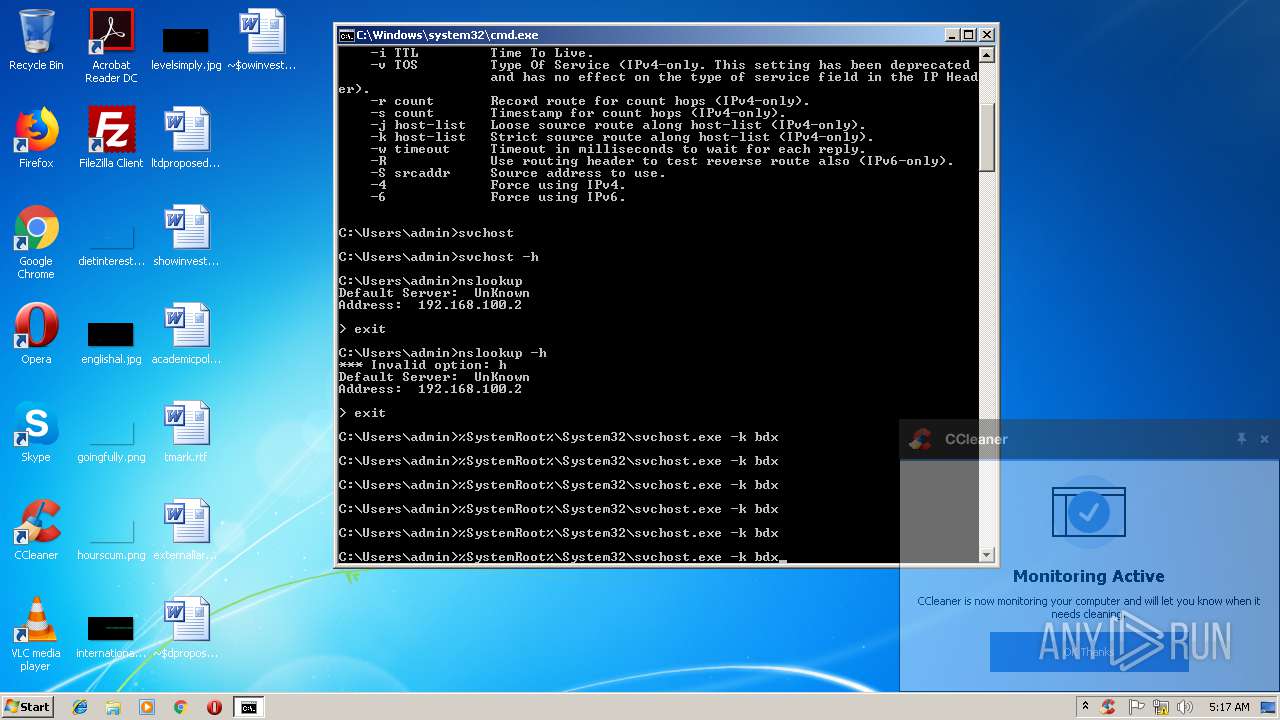
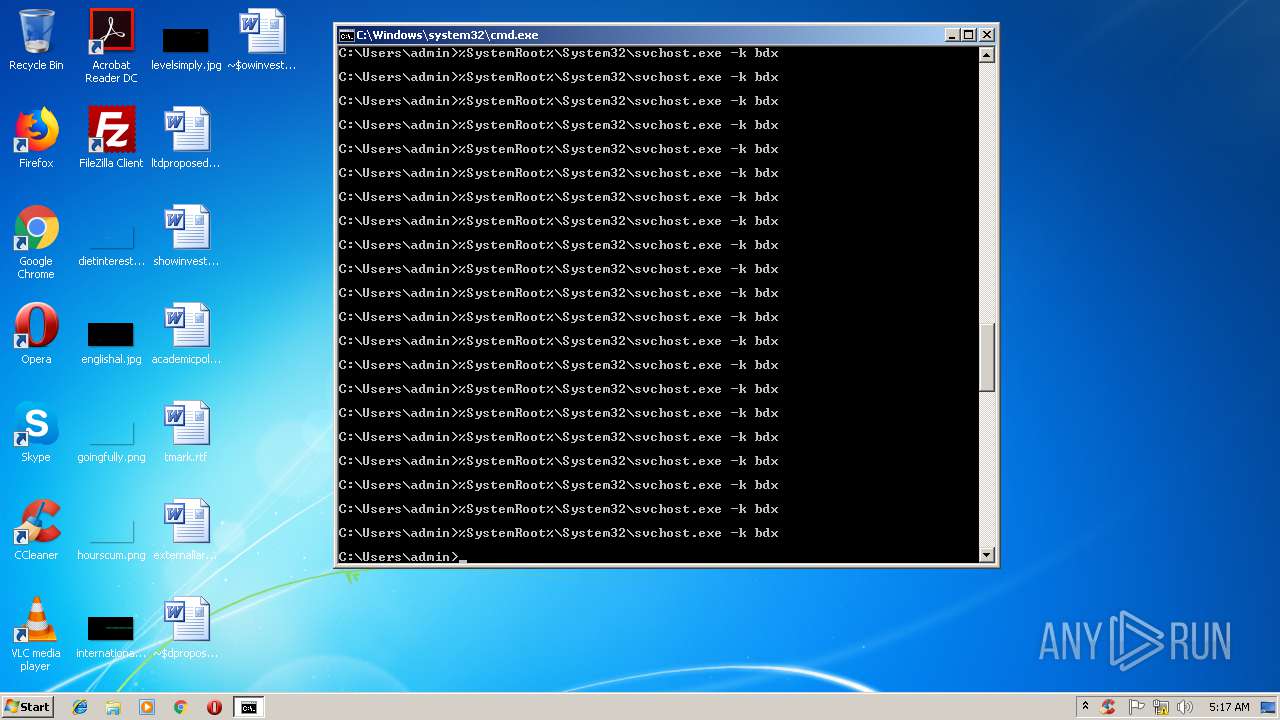
- cmd.exe (PID: 3164)
Uses SVCHOST.EXE for hidden code execution
- cmd.exe (PID: 3164)
Loads the Task Scheduler COM API
- CCleaner.exe (PID: 2988)
- CCleaner.exe (PID: 3760)
Changes the autorun value in the registry
- CCleaner.exe (PID: 3760)
Actions looks like stealing of personal data
- CCleaner.exe (PID: 3760)
- CCleaner.exe (PID: 3040)
SUSPICIOUS
Reads the cookies of Google Chrome
- CCleaner.exe (PID: 3040)
Creates files in the user directory
- CCleaner.exe (PID: 3040)
- filezilla.exe (PID: 2504)
Application launched itself
- CCleaner.exe (PID: 3040)
- cmd.exe (PID: 3164)
Low-level read access rights to disk partition
- CCleaner.exe (PID: 3040)
Reads internet explorer settings
- CCleaner.exe (PID: 3760)
- CCleaner.exe (PID: 3040)
Starts application with an unusual extension
- cmd.exe (PID: 3164)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3164)
Reads the cookies of Mozilla Firefox
- CCleaner.exe (PID: 3040)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3004)
Reads internet explorer settings
- iexplore.exe (PID: 3300)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3300)
Reads settings of System Certificates
- iexplore.exe (PID: 3004)
- iexplore.exe (PID: 3300)
- CCleaner.exe (PID: 3040)
Reads Internet Cache Settings
- iexplore.exe (PID: 3004)
- iexplore.exe (PID: 3300)
Creates files in the user directory
- iexplore.exe (PID: 3300)
- WINWORD.EXE (PID: 3828)
- WINWORD.EXE (PID: 2036)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2036)
- WINWORD.EXE (PID: 3828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .aiml | | | Artificial Intelligence Markup Language (48.3) |
|---|---|---|
| .htm/html | | | HyperText Markup Language with DOCTYPE (41.6) |
| .html | | | HyperText Markup Language (9.9) |
EXIF
HTML
| Title: | Yahoo |
|---|---|
| HTTPEquivXDnsPrefetchControl: | on |
| ContentType: | text/html; charset=utf-8 |
| HTTPEquivXUACompatible: | chrome=1 |
| Description: | Nachrichten, E-Mails und die Suche sind nur der Anfang. Jeden Tag gibt es mehr zu entdecken. Finden Sie genau das, was Sie suchen. |
| Keywords: | Yahoo, Yahoo Startseite, yahoo startseite, Yahoo Suche, Yahoo Mail, Yahoo Messenger, Yahoo Spiele, Nachrichten, Finanzen, Sport, Unterhaltung |
| formatDetection: | telephone=no |
| themeColor: | #400090 |
| referrer: | unsafe-url |
| oathGuceConsentHost: | guce.yahoo.com |
Total processes
136
Monitored processes
97
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | C:\Windows\System32\svchost.exe -k bdx | C:\Windows\System32\svchost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 356 | C:\Windows\System32\svchost.exe -k bdx | C:\Windows\System32\svchost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 696 | C:\Windows\System32\svchost.exe -k bdx | C:\Windows\System32\svchost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1076 | C:\Windows\system32\cmd.exe /S /D /c" color CC" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1100 | C:\Windows\System32\svchost.exe -k bdx | C:\Windows\System32\svchost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1208 | C:\Windows\System32\svchost.exe | C:\Windows\System32\svchost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1236 | C:\Windows\System32\svchost.exe -k bdx | C:\Windows\System32\svchost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1236 | C:\Windows\System32\svchost.exe -k bdx | C:\Windows\System32\svchost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1356 | C:\Windows\System32\svchost.exe -k bdx | C:\Windows\System32\svchost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1416 | C:\Windows\System32\svchost.exe -k bdx | C:\Windows\System32\svchost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 863
Read events
2 464
Write events
368
Delete events
31
Modification events
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {BB94D7F9-1ECD-11E9-91D7-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E30701000300170005000E001300F500 | |||
Executable files
0
Suspicious files
7
Text files
55
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3004 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3004 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\atomic-css.2a854c7f[1].css | text | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\yglyphs[1].eot | eot | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\font_rc4_0.0.91[1].css | text | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\yglyphs[1].eot | eot | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2YPIJ90\sda_advance_0.0.39[1].css | text | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\advance_0.0.26[1].css | text | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\advance_base_rc4_0.0.91[1].css | text | |
MD5:— | SHA256:— | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\yahoo20_fixed_grid_0.0.33[1].css | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
21
DNS requests
7
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3040 | CCleaner.exe | GET | 301 | 151.101.0.64:80 | http://www.piriform.com/auto?a=0&p=cc&v=5.35.6210&l=1033&lk=&mk=IJR6-W5SV-5KYR-QBZD-6BY4-RN5Z-WAV9-RVK2-VJCA&o=6.1W3&au=1&mx=97B7721C4994E2556FF6A439510F665DB45337A341A47E15F4997584423BF714&gu=00000000-0000-4000-8000-d6f7f2be5127 | US | — | — | whitelisted |
3004 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3300 | iexplore.exe | 87.248.114.12:443 | s.yimg.com | Yahoo! UK Services Limited | GB | shared |
3004 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3300 | iexplore.exe | 104.111.214.103:443 | sb.scorecardresearch.com | Akamai International B.V. | NL | whitelisted |
3004 | iexplore.exe | 212.82.100.137:443 | de.search.yahoo.com | Yahoo! UK Services Limited | CH | shared |
3040 | CCleaner.exe | 151.101.0.64:80 | www.piriform.com | Fastly | US | whitelisted |
3040 | CCleaner.exe | 151.101.0.64:443 | www.piriform.com | Fastly | US | whitelisted |
3040 | CCleaner.exe | 151.101.2.202:443 | www.ccleaner.com | Fastly | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
s.yimg.com |
| shared |
www.bing.com |
| whitelisted |
beap-bc.yahoo.com |
| whitelisted |
sb.scorecardresearch.com |
| shared |
de.search.yahoo.com |
| whitelisted |
www.piriform.com |
| whitelisted |
www.ccleaner.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3040 | CCleaner.exe | A Network Trojan was detected | SC MINER Miner Possible Bitcoin Miner Windows |