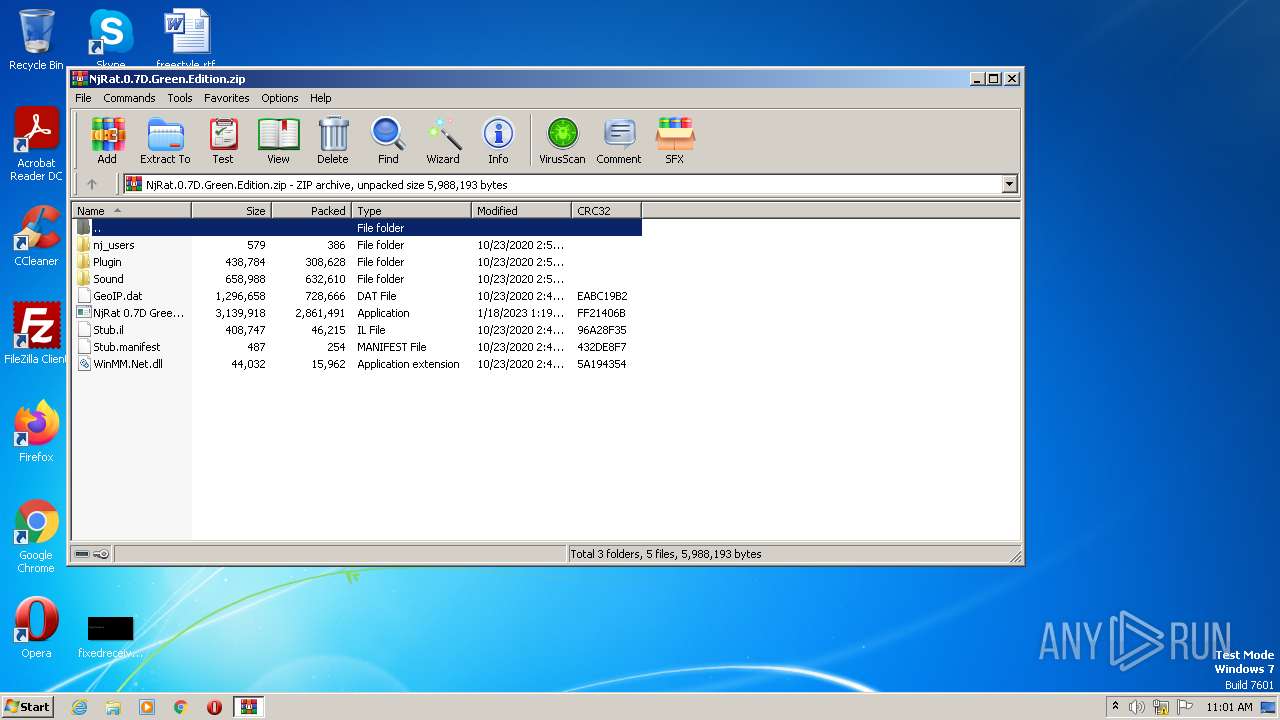
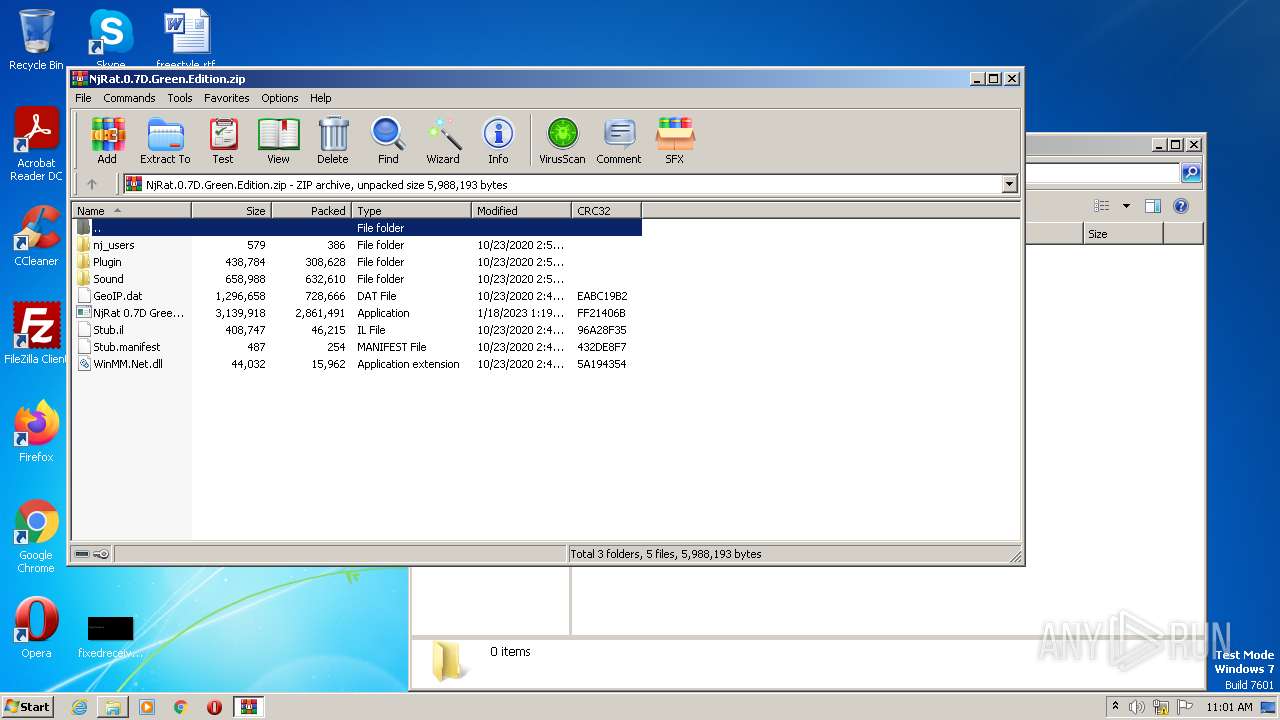
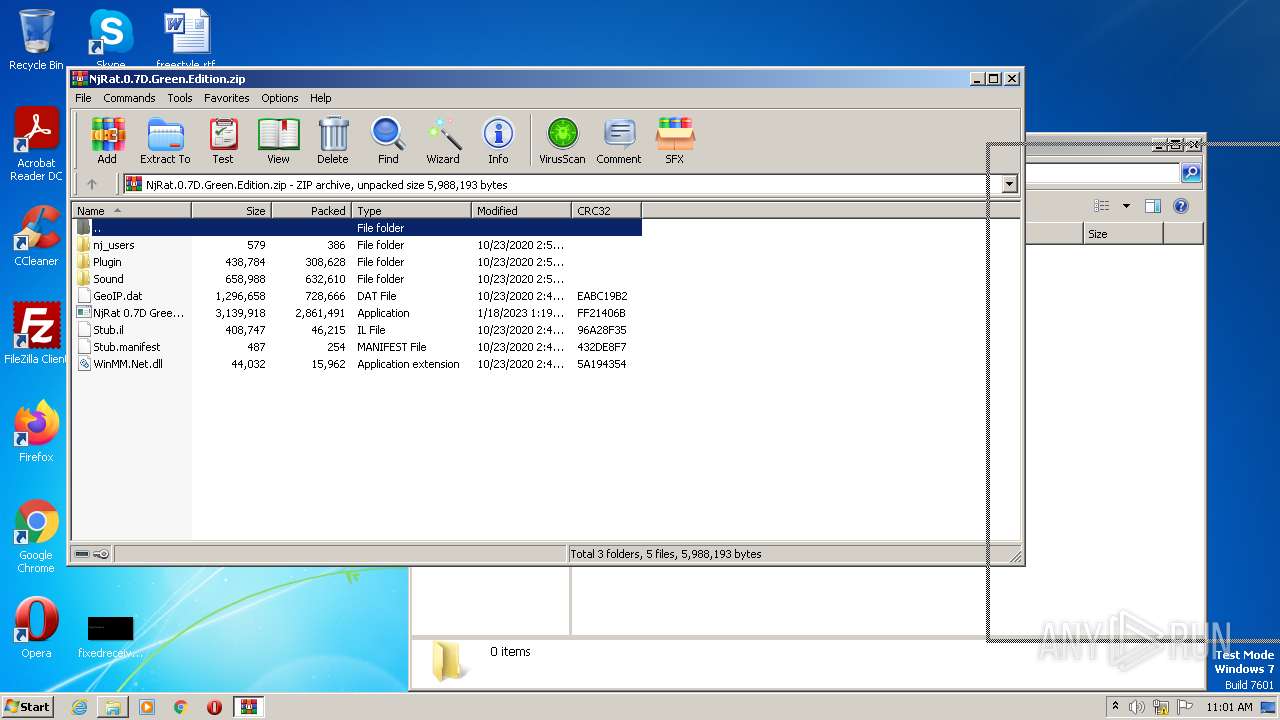
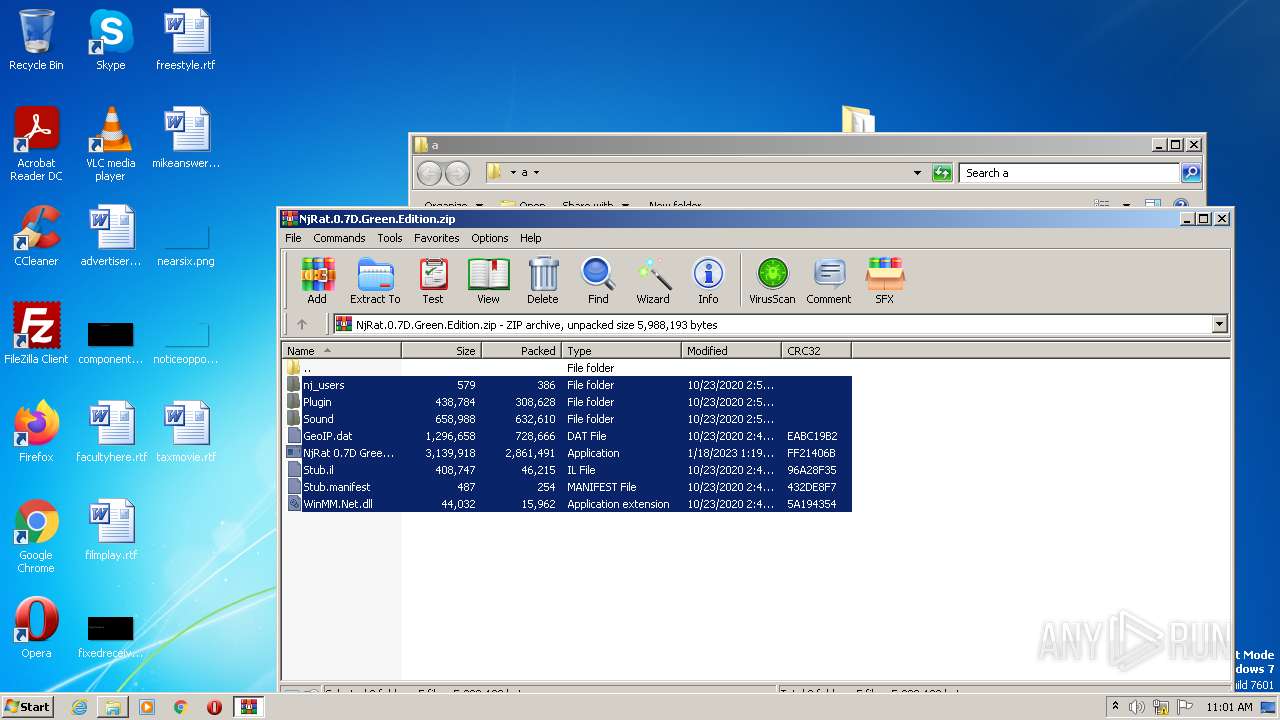
| File name: | NjRat.0.7D.Green.Edition.zip |
| Full analysis: | https://app.any.run/tasks/3fe9a43f-f22b-4fa4-83a0-4cfb58f46a3f |
| Verdict: | Malicious activity |
| Analysis date: | March 12, 2023, 11:01:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 24CDBAC5F3AB2AF691F1AD71C8354B29 |
| SHA1: | 8BBA6F29F8BFDB9328B0198890F5445584431E03 |
| SHA256: | 55E286565012CBE753A6A3083933F31BAAA7F50695B3774F0882311A4ACA6F8B |
| SSDEEP: | 98304:z91Hn80y/7KQyW4TGHYIHPODUhfxFsEP6kyXvFyXCAm+08M:zjHG7KQ74WHhdSkyf6C9+2 |
MALICIOUS
SecurityXploded is detected
- WinRAR.exe (PID: 2712)
Application was dropped or rewritten from another process
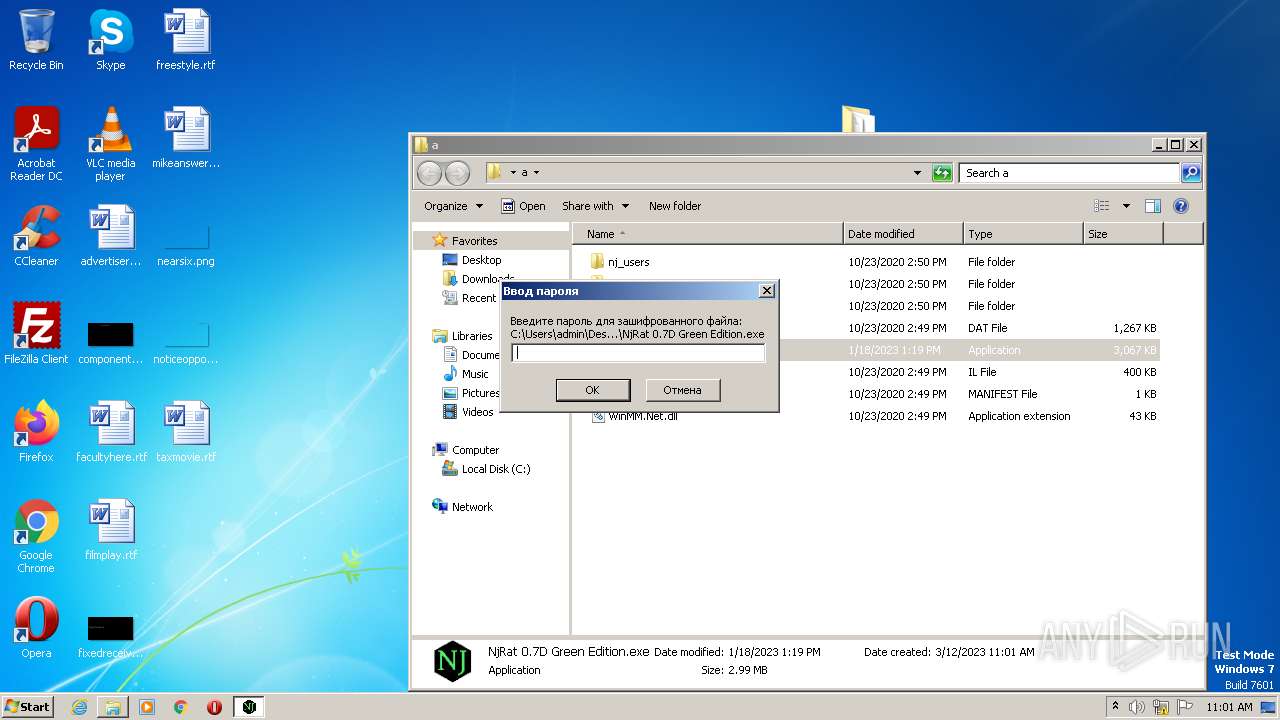
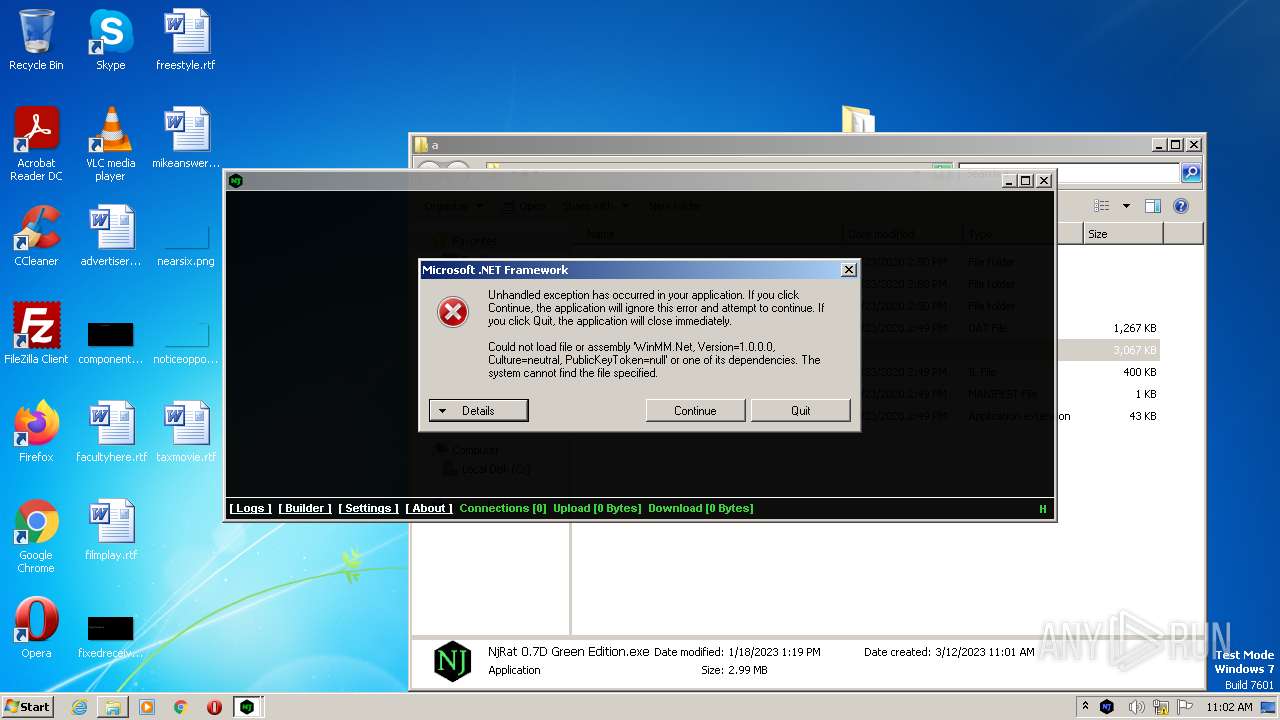
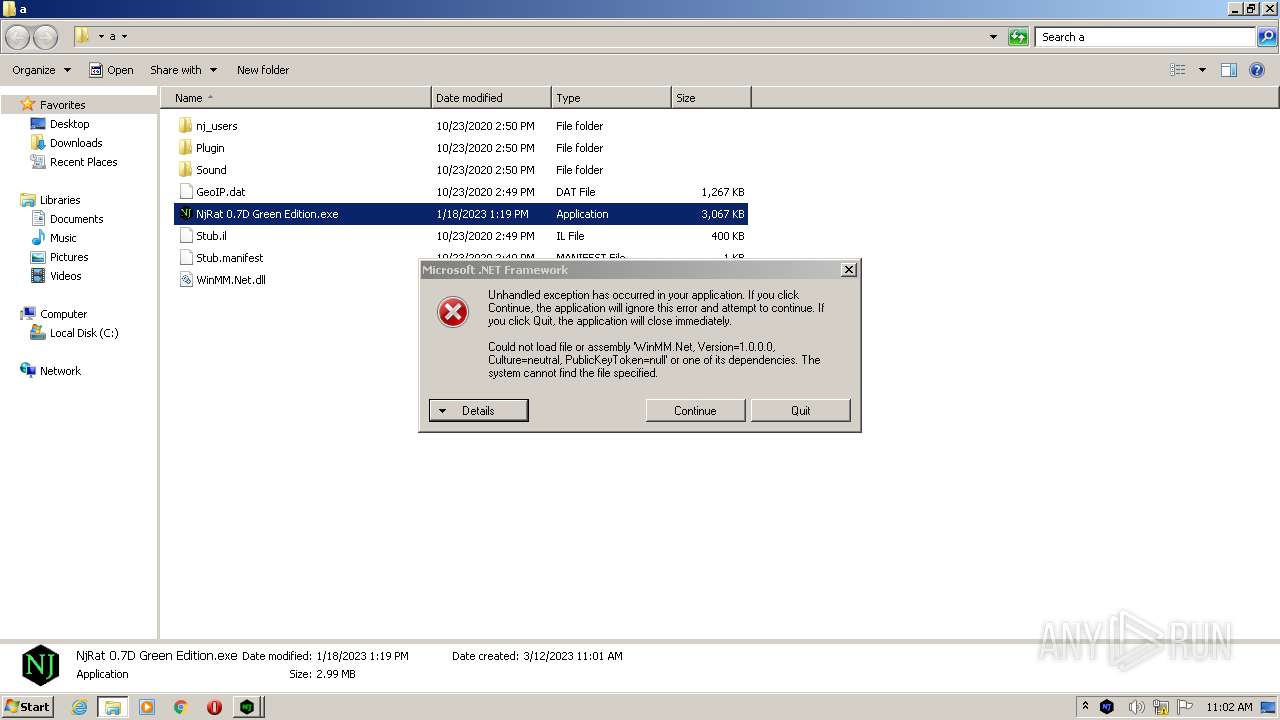
- NjRat 0.7D Green Edition.exe (PID: 2888)
- NjRat 0.7D Green Edition by im523.exe (PID: 3280)
Drops the executable file immediately after the start
- NjRat 0.7D Green Edition.exe (PID: 2888)
SUSPICIOUS
Executable content was dropped or overwritten
- NjRat 0.7D Green Edition.exe (PID: 2888)
Drops a file with too old compile date
- NjRat 0.7D Green Edition.exe (PID: 2888)
Reads the Internet Settings
- NjRat 0.7D Green Edition.exe (PID: 2888)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2712)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2712)
Manual execution by a user
- NjRat 0.7D Green Edition.exe (PID: 2888)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2712)
- NjRat 0.7D Green Edition.exe (PID: 2888)
Checks supported languages
- NjRat 0.7D Green Edition.exe (PID: 2888)
- NjRat 0.7D Green Edition by im523.exe (PID: 3280)
- dw20.exe (PID: 4040)
Reads the computer name
- NjRat 0.7D Green Edition.exe (PID: 2888)
- NjRat 0.7D Green Edition by im523.exe (PID: 3280)
- dw20.exe (PID: 4040)
The process checks LSA protection
- NjRat 0.7D Green Edition.exe (PID: 2888)
- NjRat 0.7D Green Edition by im523.exe (PID: 3280)
- dw20.exe (PID: 4040)
Create files in a temporary directory
- NjRat 0.7D Green Edition.exe (PID: 2888)
Reads the machine GUID from the registry
- NjRat 0.7D Green Edition by im523.exe (PID: 3280)
- dw20.exe (PID: 4040)
Creates files or folders in the user directory
- dw20.exe (PID: 4040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | nj_users/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2020:10:23 14:50:26 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
40
Monitored processes
4
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2712 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\NjRat.0.7D.Green.Edition.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
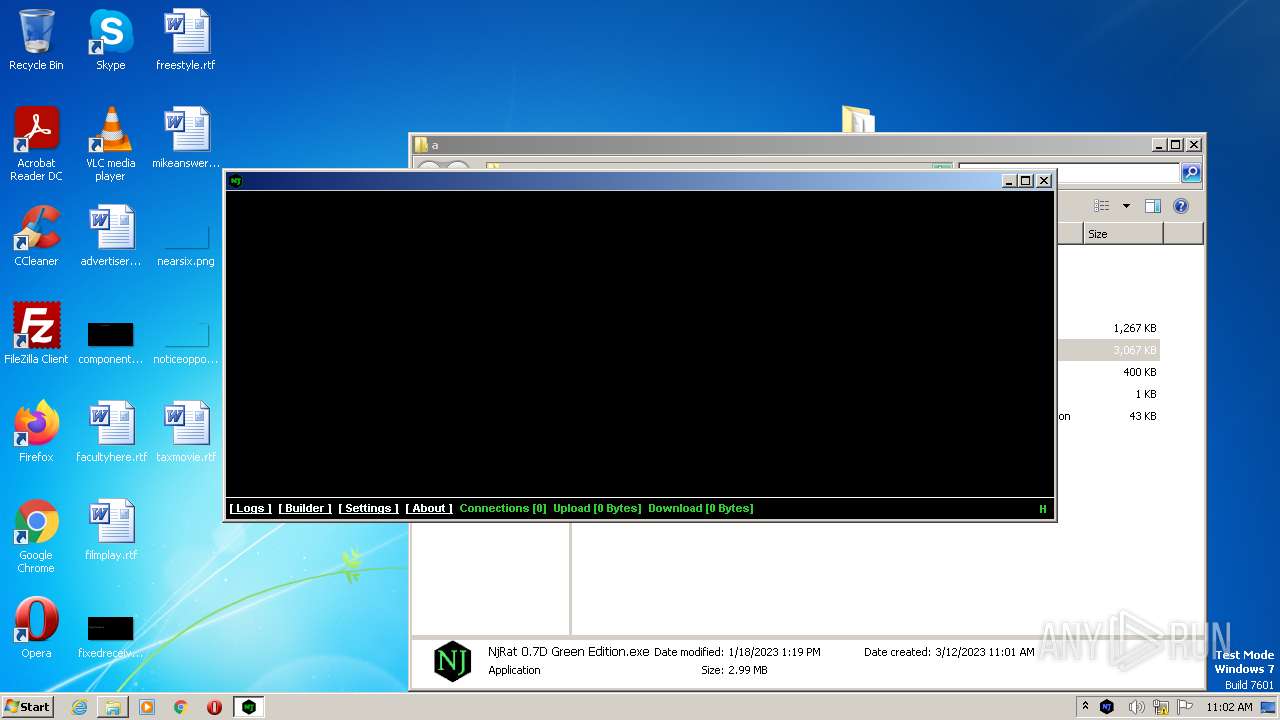
| 2888 | "C:\Users\admin\Desktop\a\NjRat 0.7D Green Edition.exe" | C:\Users\admin\Desktop\a\NjRat 0.7D Green Edition.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3280 | "C:\Users\admin\AppData\Local\Temp\NjRat 0.7D Green Edition by im523.exe" | C:\Users\admin\AppData\Local\Temp\NjRat 0.7D Green Edition by im523.exe | NjRat 0.7D Green Edition.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: NjRat 0.7D Green Edition by im523 Exit code: 3762507597 Version: 0.0.0.7 Modules
| |||||||||||||||
| 4040 | dw20.exe -x -s 676 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\dw20.exe | — | NjRat 0.7D Green Edition by im523.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Error Reporting Shim Exit code: 0 Version: 2.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
Total events
3 858
Read events
3 804
Write events
54
Delete events
0
Modification events
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
20
Suspicious files
2
Text files
8
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4040 | dw20.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportArchive\AppCrash_ARLL22EYCOOR4NJS_56ffd2ec7cd0f75230f6e43e165515da504bd686_0fedc446\Report.wer | — | |
MD5:— | SHA256:— | |||
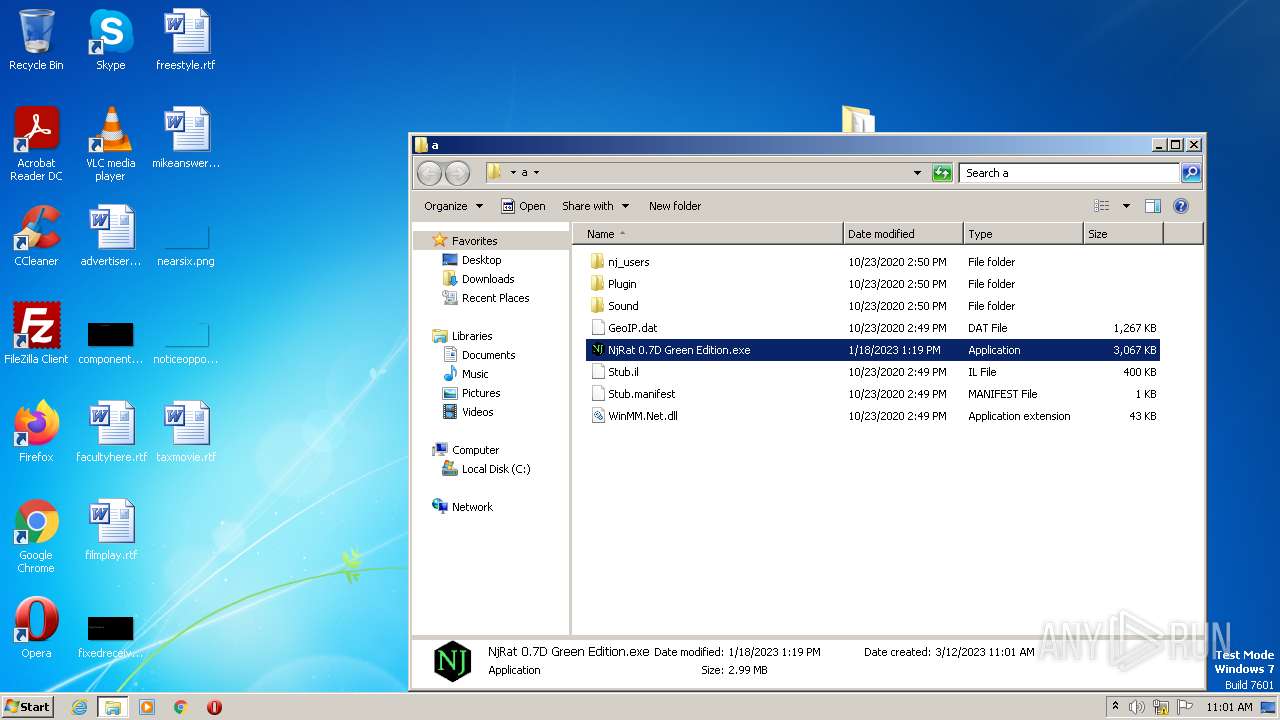
| 2712 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2712.37671\NjRat 0.7D Green Edition.exe | executable | |
MD5:— | SHA256:— | |||
| 2712 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2712.37671\Plugin\plg.dll | executable | |
MD5:0CBC2D9703FEEAD9783439E551C2B673 | SHA256:EA9ECF8723788FEEF6492BF938CDFAB1266A1558DFFE75E1F78A998320F96E39 | |||
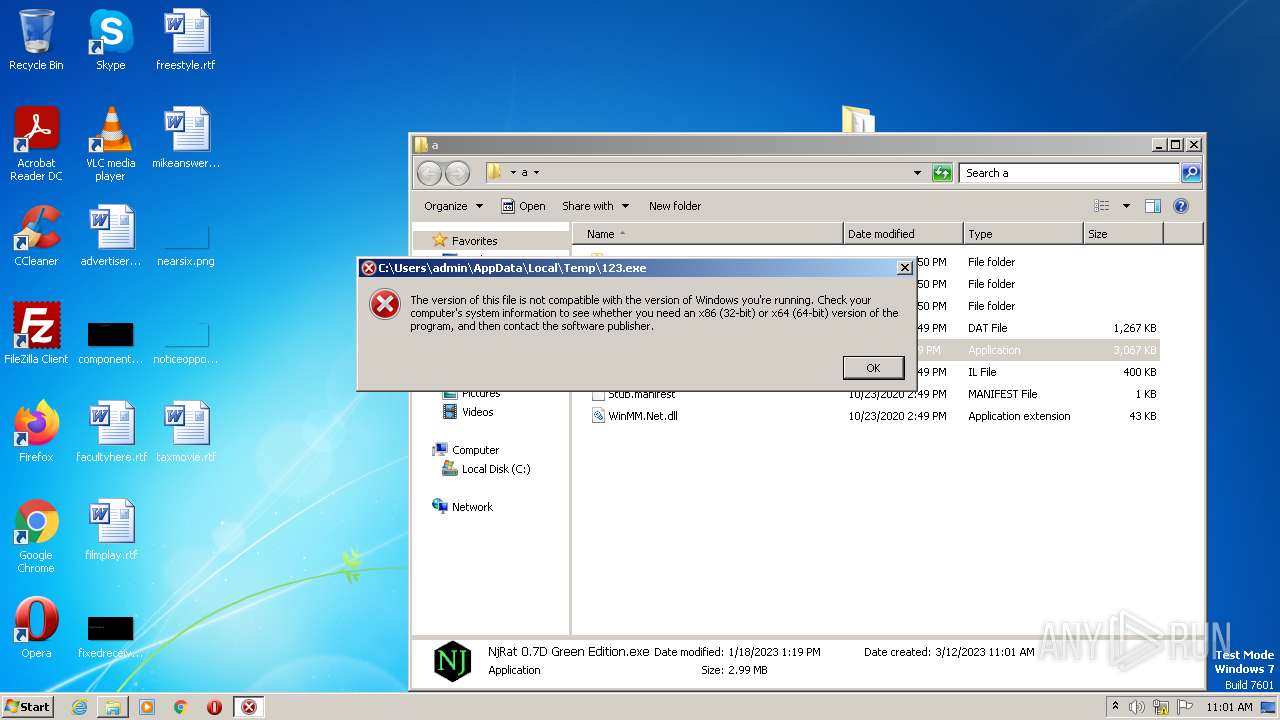
| 2888 | NjRat 0.7D Green Edition.exe | C:\Users\admin\AppData\Local\Temp\123.exe | executable | |
MD5:— | SHA256:— | |||
| 2712 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2712.37671\Plugin\cam.dll | executable | |
MD5:A73EDB60B80A2DFA86735D821BEA7B19 | SHA256:7A4977B024D048B71BCC8F1CC65FB06E4353821323F852DC6740B79B9AB75C98 | |||
| 2712 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2712.37671\Stub.manifest | xml | |
MD5:4D18AC38A92D15A64E2B80447B025B7E | SHA256:835A00D6E7C43DB49AE7B3FA12559F23C2920B7530F4D3F960FD285B42B1EFB5 | |||
| 2712 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2712.37671\nj_users\VM-РџРљ_vm_602F4037\Keylog.rtf | text | |
MD5:92122DA996C66CBD51D8C6EA868739C5 | SHA256:9A27937010FA2BE4C9F3634FEE0BF20CBDEB64BC7141AB1BEDA02C06DE27F869 | |||
| 2712 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2712.37671\Plugin\ch.dll | executable | |
MD5:73C8A5CD64FCF87186A6A9AC870DF509 | SHA256:7722206DBA0CFB290F33093F9430CB770A160947001715AE11E6DBBFAEF1C0EE | |||
| 2712 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2712.37671\Plugin\sc2.dll | executable | |
MD5:19967E886EDCD2F22F8D4A58C8EA3773 | SHA256:3E5141C75B7746C0EB2B332082A165DEACB943CEF26BD84668E6B79B47BDFD93 | |||
| 2712 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2712.37671\Plugin\pw.dll | executable | |
MD5:872401528FC94C90F3DE6658E776CC36 | SHA256:3A1CC072EFFD8C38406A6FDDF4D8F49C5366BB0E32071311D90DB669940987CE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report