| File name: | Spark.exe |
| Full analysis: | https://app.any.run/tasks/0d2c77ed-7c86-422b-b906-ef200f87b9c0 |
| Verdict: | Malicious activity |
| Analysis date: | January 27, 2024, 22:38:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 181EE63003E5C3EC8C378030286ED7A2 |
| SHA1: | 6707F3A0906AB6D201EDC5B6389F9E66E345F174 |
| SHA256: | 55BFCB784904477EF62EF7E4994DEE42F03D69BFEC3591989513CCCBBA3FC8FE |
| SSDEEP: | 12288:ehny10sOqEl5yD4UmxYV1g1bT2kdSOSGL84UmxbJ:exZ5vYORMOJ/bJ |
MALICIOUS
Changes image file execution options
- Spark.exe (PID: 876)
- Spark.exe (PID: 1464)
Drops the executable file immediately after the start
- Spark.exe (PID: 876)
- Spark.exe (PID: 1464)
Actions looks like stealing of personal data
- Spark.exe (PID: 876)
- Spark.exe (PID: 1464)
Changes the autorun value in the registry
- Spark.exe (PID: 1464)
Changes the Windows auto-update feature
- Spark.exe (PID: 1464)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- Spark.exe (PID: 876)
- Spark.exe (PID: 1464)
Executable content was dropped or overwritten
- Spark.exe (PID: 876)
- Spark.exe (PID: 1464)
Creates or modifies Windows services
- Spark.exe (PID: 876)
- Spark.exe (PID: 1464)
Reads settings of System Certificates
- sipnotify.exe (PID: 120)
- Spark.exe (PID: 1464)
The process executes via Task Scheduler
- ctfmon.exe (PID: 1944)
- sipnotify.exe (PID: 120)
- Spark.exe (PID: 1464)
Reads the Internet Settings
- sipnotify.exe (PID: 120)
- runonce.exe (PID: 456)
- Spark.exe (PID: 1464)
Application launched itself
- WerFault.exe (PID: 2072)
Checks for Java to be installed
- Spark.exe (PID: 1464)
Detected use of alternative data streams (AltDS)
- WerFault.exe (PID: 2080)
Modifies the phishing filter of IE
- Spark.exe (PID: 1464)
Reads security settings of Internet Explorer
- Spark.exe (PID: 1464)
Reads Internet Explorer settings
- Spark.exe (PID: 1464)
Adds/modifies Windows certificates
- Spark.exe (PID: 1464)
Changes internet zones settings
- Spark.exe (PID: 1464)
Checks Windows Trust Settings
- Spark.exe (PID: 1464)
Changes Internet Explorer settings (feature browser emulation)
- Spark.exe (PID: 1464)
Process changes security settings for the VBA macro
- Spark.exe (PID: 1464)
Accesses Microsoft Outlook profiles
- Spark.exe (PID: 1464)
Creates/Modifies COM task schedule object
- Spark.exe (PID: 1464)
INFO
Checks supported languages
- Spark.exe (PID: 876)
- Spark.exe (PID: 1464)
- IMEKLMG.EXE (PID: 2152)
- IMEKLMG.EXE (PID: 2164)
- wmpnscfg.exe (PID: 2580)
- wmpnscfg.exe (PID: 2508)
Reads the computer name
- Spark.exe (PID: 876)
- IMEKLMG.EXE (PID: 2152)
- IMEKLMG.EXE (PID: 2164)
- wmpnscfg.exe (PID: 2508)
- wmpnscfg.exe (PID: 2580)
- Spark.exe (PID: 1464)
Reads the machine GUID from the registry
- Spark.exe (PID: 876)
Reads the time zone
- runonce.exe (PID: 456)
Manual execution by a user
- runonce.exe (PID: 456)
- IMEKLMG.EXE (PID: 2152)
- IMEKLMG.EXE (PID: 2164)
- wmpnscfg.exe (PID: 2580)
- wmpnscfg.exe (PID: 2508)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2152)
- IMEKLMG.EXE (PID: 2164)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 120)
Create files in a temporary directory
- WerFault.exe (PID: 2080)
Process checks computer location settings
- Spark.exe (PID: 1464)
Reads Microsoft Office registry keys
- Spark.exe (PID: 1464)
Reads mouse settings
- Spark.exe (PID: 1464)
Process checks Internet Explorer phishing filters
- Spark.exe (PID: 1464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:09:14 22:54:18+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 441856 |
| InitializedDataSize: | 65024 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6ddee |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | Spark.exe |
| LegalCopyright: | |
| OriginalFileName: | Spark.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
94
Monitored processes
12
Malicious processes
3
Suspicious processes
1
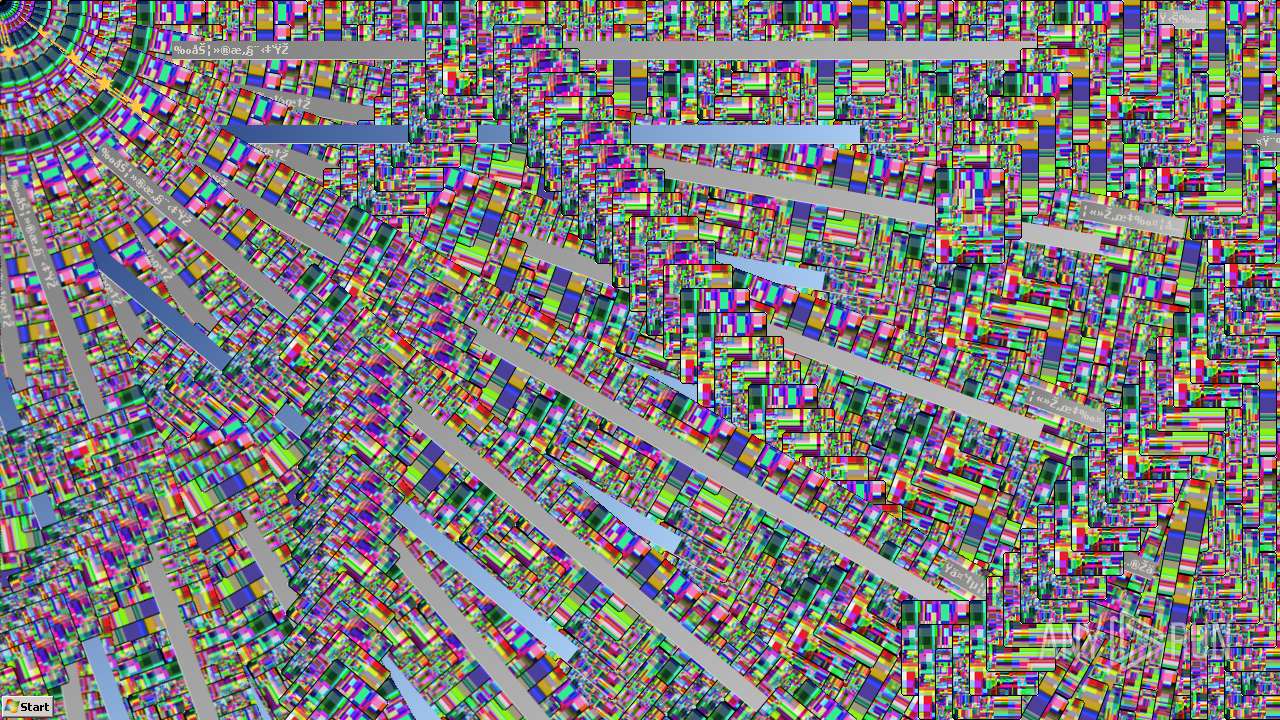
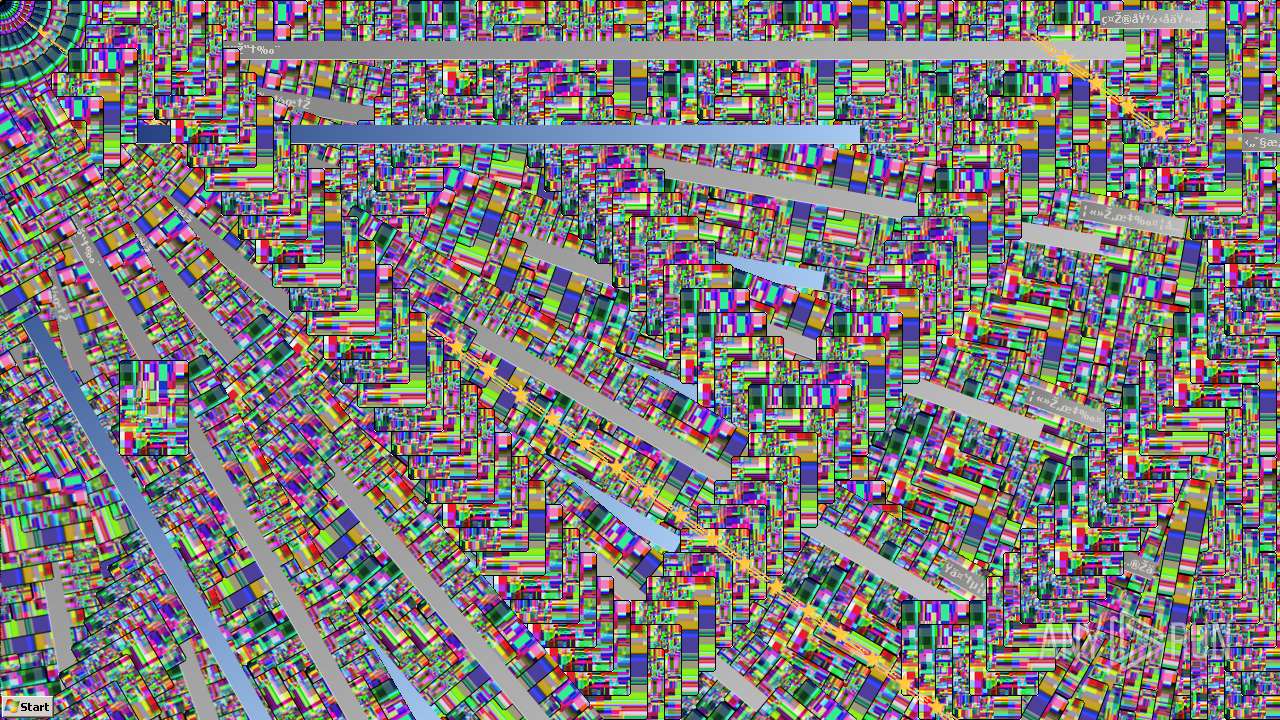
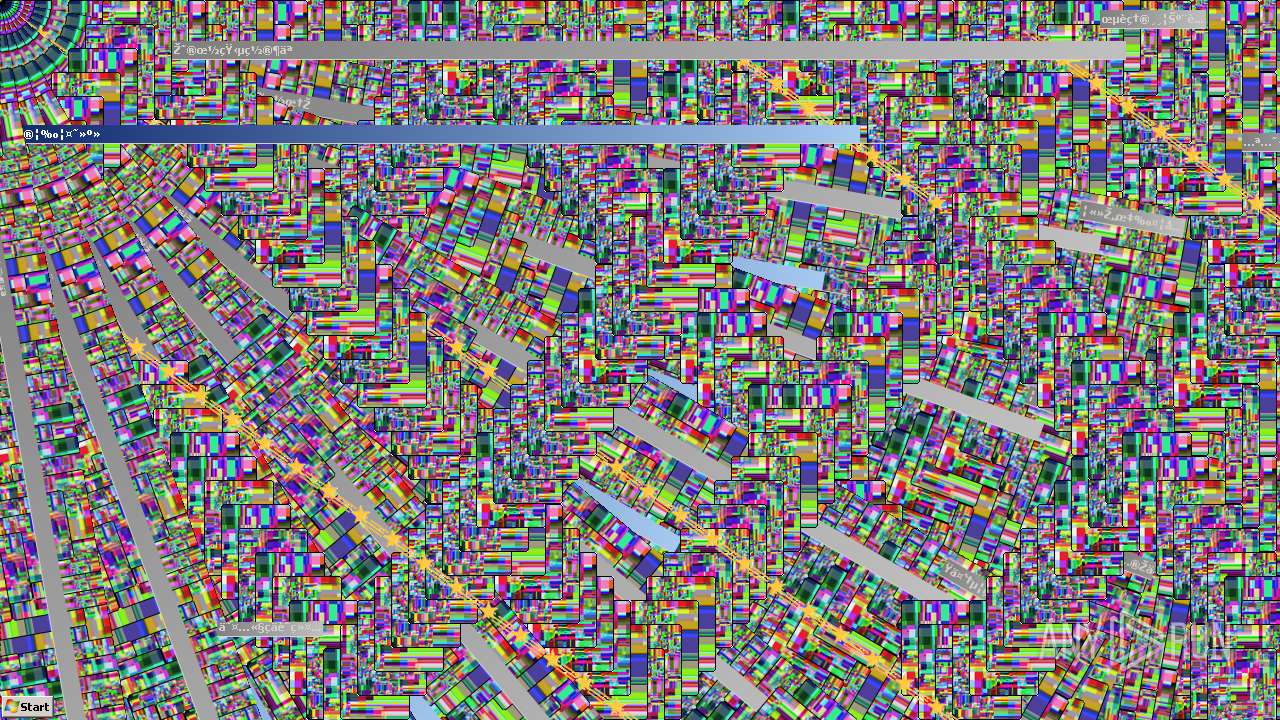
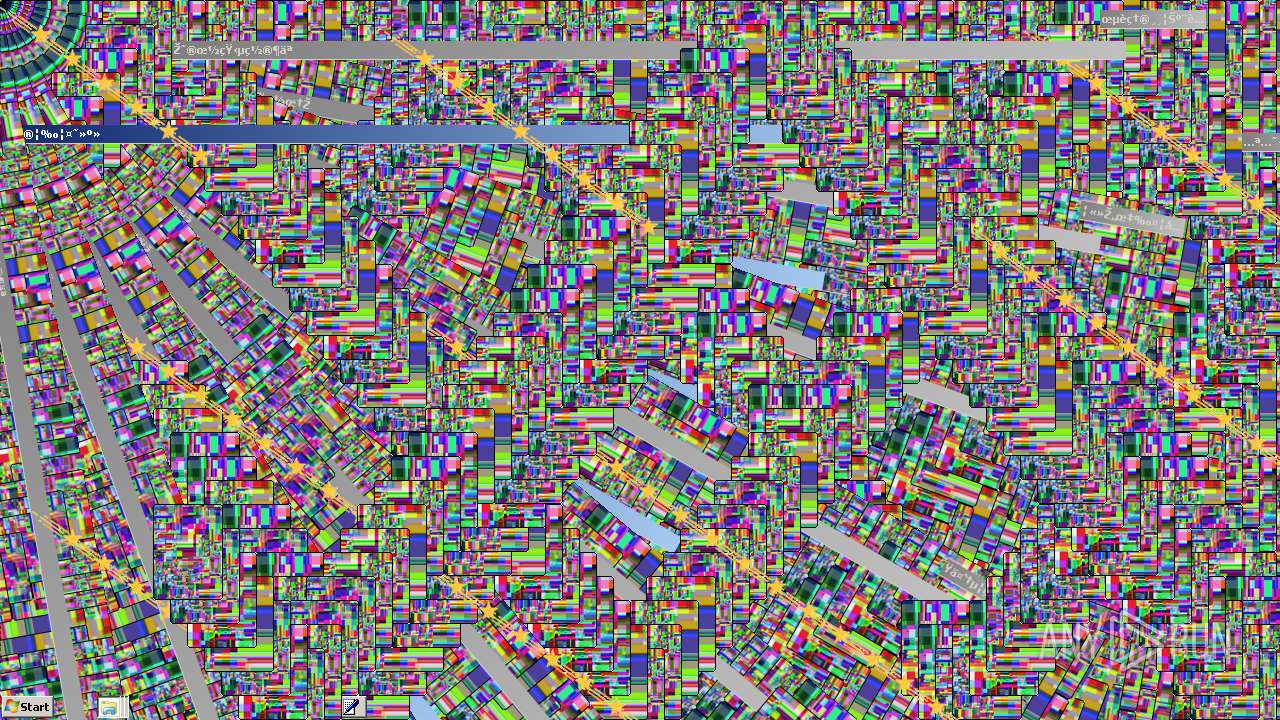
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 456 | runonce.exe /Explorer | C:\Windows\System32\runonce.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 876 | "C:\Users\admin\AppData\Local\Temp\Spark.exe" | C:\Users\admin\AppData\Local\Temp\Spark.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1464 | "C:\Windows\File Cache\Spark.exe" | C:\Windows\File Cache\Spark.exe | taskeng.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1944 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2072 | "C:\Windows\System32\WerFault.exe" -k -rq | C:\Windows\System32\WerFault.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2080 | C:\Windows\System32\WerFault.exe -k -q | C:\Windows\System32\WerFault.exe | — | WerFault.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2152 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2164 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2508 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
55 054
Read events
47 794
Write events
7 254
Delete events
6
Modification events
| (PID) Process: | (876) Spark.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | legalnoticecaption |
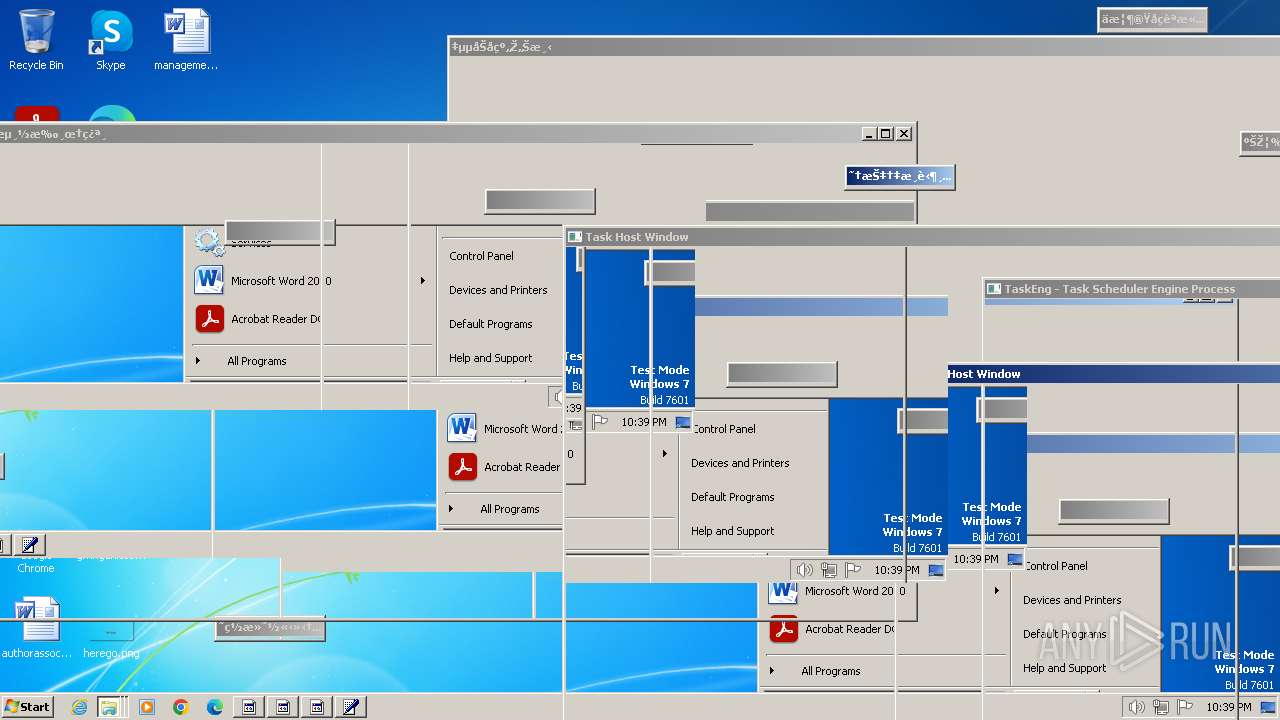
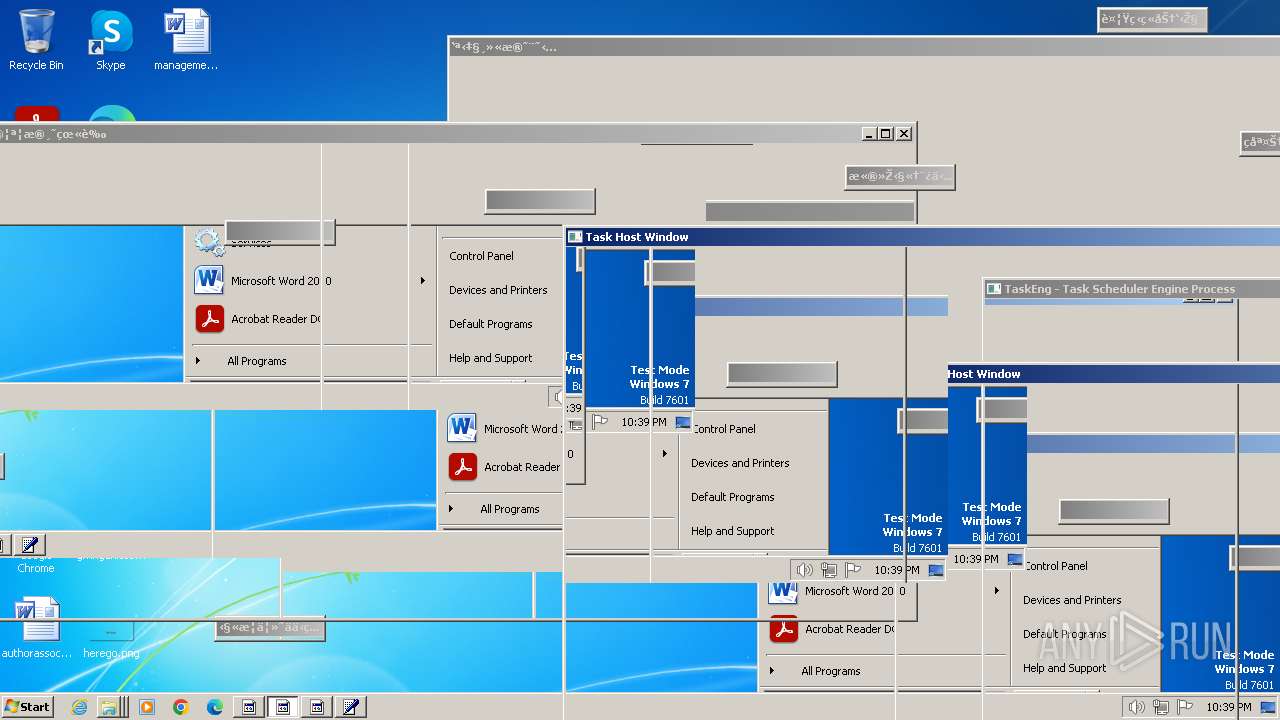
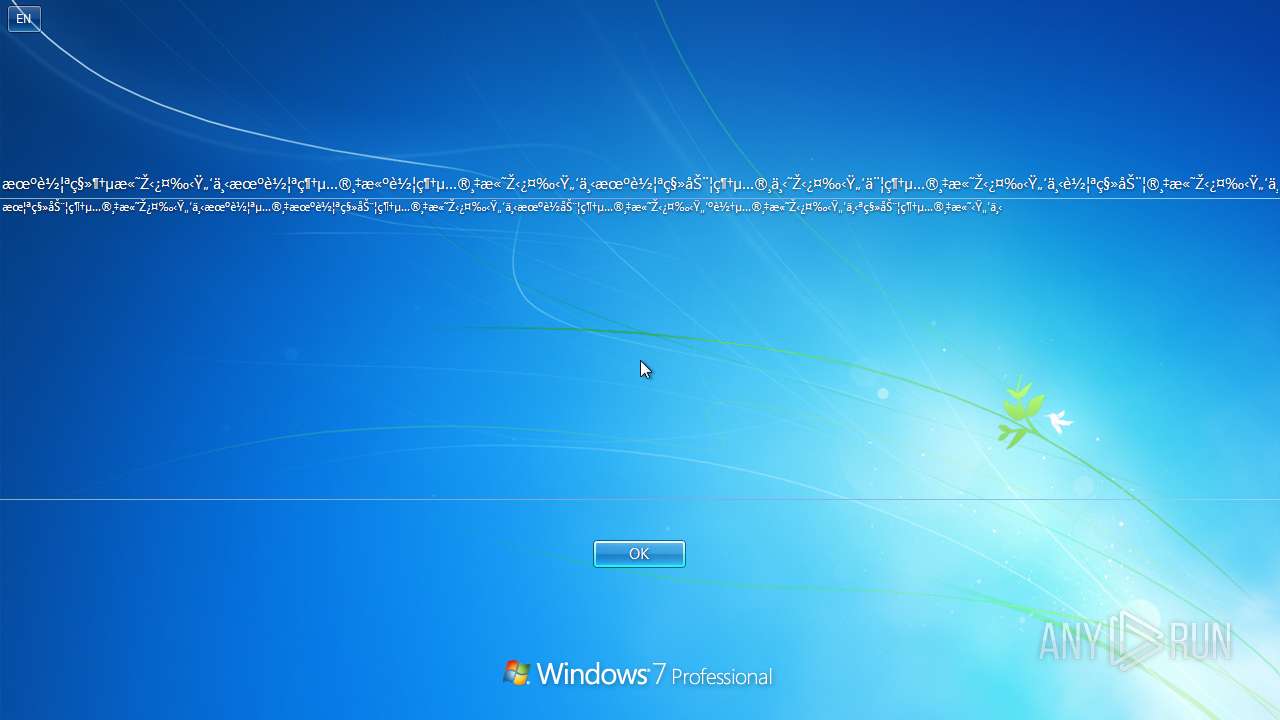
Value: 机车ªç§»¶†µæ«˜Ž‹¿¤‰‹Ÿ„‘下机车ªç¶†µ…®¸‡æ«ºè½¦ç¶†µ…®¸‡æ«˜Ž‹¿¤‰‹Ÿ„‘下机车ªç§»åŠ¨¦ç¶†µ…®¸ä¸‹˜Ž‹¿¤‰‹Ÿ„‘䨦綆µ…®¸‡æ«˜Ž‹¿¤‰‹Ÿ„‘下车ªç§»åŠ¨¦®¸‡æ«˜Ž‹¿¤‰‹Ÿ„‘下 | |||
| (PID) Process: | (876) Spark.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | legalnoticetext |
Value: 朦ªç§»åŠ¨¦ç¶†µ…®¸‡æ«˜Ž¿¤‰‹Ÿ„‘下机车ªµ…®¸‡æœºè½¦ªç§»åŠ¨¦ç¶†µ…®¸‡æ«˜Ž‹¿¤‰‹Ÿ„‘下机è½åŠ¨¦ç¶†µ…®¸‡æ«˜Ž‹¿¤‰‹Ÿ„‘ºè½†µ…®¸‡æ«˜Ž‹¿¤‰‹Ÿ„‘下ªç§»åŠ¨¦ç¶†µ…®¸‡æ«˜‹Ÿ„‘下 | |||
| (PID) Process: | (876) Spark.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mmc.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Windows\File Cache\IFEO.exe | |||
| (PID) Process: | (876) Spark.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\regedit.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Windows\File Cache\IFEO.exe | |||
| (PID) Process: | (876) Spark.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Windows\File Cache\IFEO.exe | |||
| (PID) Process: | (876) Spark.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\taskschd.msc |
| Operation: | write | Name: | Debugger |
Value: C:\Windows\File Cache\IFEO.exe | |||
| (PID) Process: | (876) Spark.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\Driver |
| Operation: | write | Name: | ImagePath |
Value: \??\C:\Windows\File Cache\Driver.sys | |||
| (PID) Process: | (876) Spark.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\Driver |
| Operation: | write | Name: | DisplayName |
Value: Driver | |||
| (PID) Process: | (876) Spark.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\Driver |
| Operation: | write | Name: | Start |
Value: 3 | |||
| (PID) Process: | (876) Spark.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\Driver |
| Operation: | write | Name: | Type |
Value: 1 | |||
Executable files
7
Suspicious files
8
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 456 | runonce.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Explorer\ExplorerStartupLog_RunOnce.etl | binary | |
MD5:8CE16DE01CB12EA59606391FDC3C6D44 | SHA256:8EFFB83F2B93151834A7168E48A2409CCB092AB699EFFE59987FE4EAC9174BAD | |||
| 2080 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\Kernel_0_0_cab_08207d9c\Report.wer | — | |
MD5:— | SHA256:— | |||
| 120 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\metadata.json | binary | |
MD5:E8A970BA6CE386EED9A5E724F26212A6 | SHA256:7E06107D585D8FC7870998F3856DCC3E35800AA97E4406AAB83BC8444B6CBDE3 | |||
| 120 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\styles.css | text | |
MD5:3383EEF350240253D7C2C2564381B3CB | SHA256:85443493D86D6D7FB0E07BC9705DFC9C858086FBA1B0E508092AB328D5F145E8 | |||
| 120 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\script.js | text | |
MD5:A2682382967C351F7ED21762F9E5DE9E | SHA256:36B1D26F1EC69685648C0528C2FCE95A3C2DBECF828CDFA4A8B4239A15B644A2 | |||
| 120 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\main.jpg | image | |
MD5:B342ACE63F77961249A084C61EABC884 | SHA256:E5067BBA2095B5DA7C3171EC116E9A92337E24E471339B0860A160076EFE49B9 | |||
| 1464 | Spark.exe | C:\Windows\File Cache\Driver.sys | executable | |
MD5:9579540F9FB9004D7C46F240BB9301EF | SHA256:3F4D386C8CF7C8936AEDAA28DE5DAC15139E9762079DEB97E13E5E42EBC99B18 | |||
| 120 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\microsoft-logo.png | image | |
MD5:B7C73A0CFBA68CC70C35EF9C63703CE4 | SHA256:1D8B27A0266FF526CF95447F3701592A908848467D37C09A00A2516C1F29A013 | |||
| 1464 | Spark.exe | C:\Windows\File Cache\DLL.dll | executable | |
MD5:A61C26B360471C8258C7571037C4BCA0 | SHA256:E77316A1FD682E1AF8AF3CCD03C170F886B9EC8EDF7013E1BE6A6207CB5A6F16 | |||
| 876 | Spark.exe | C:\Windows\File Cache\Spark.exe | executable | |
MD5:181EE63003E5C3EC8C378030286ED7A2 | SHA256:55BFCB784904477EF62EF7E4994DEE42F03D69BFEC3591989513CCCBBA3FC8FE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
9
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
120 | sipnotify.exe | HEAD | 200 | 23.199.215.176:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133508689539210000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1128 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
120 | sipnotify.exe | 23.199.215.176:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |