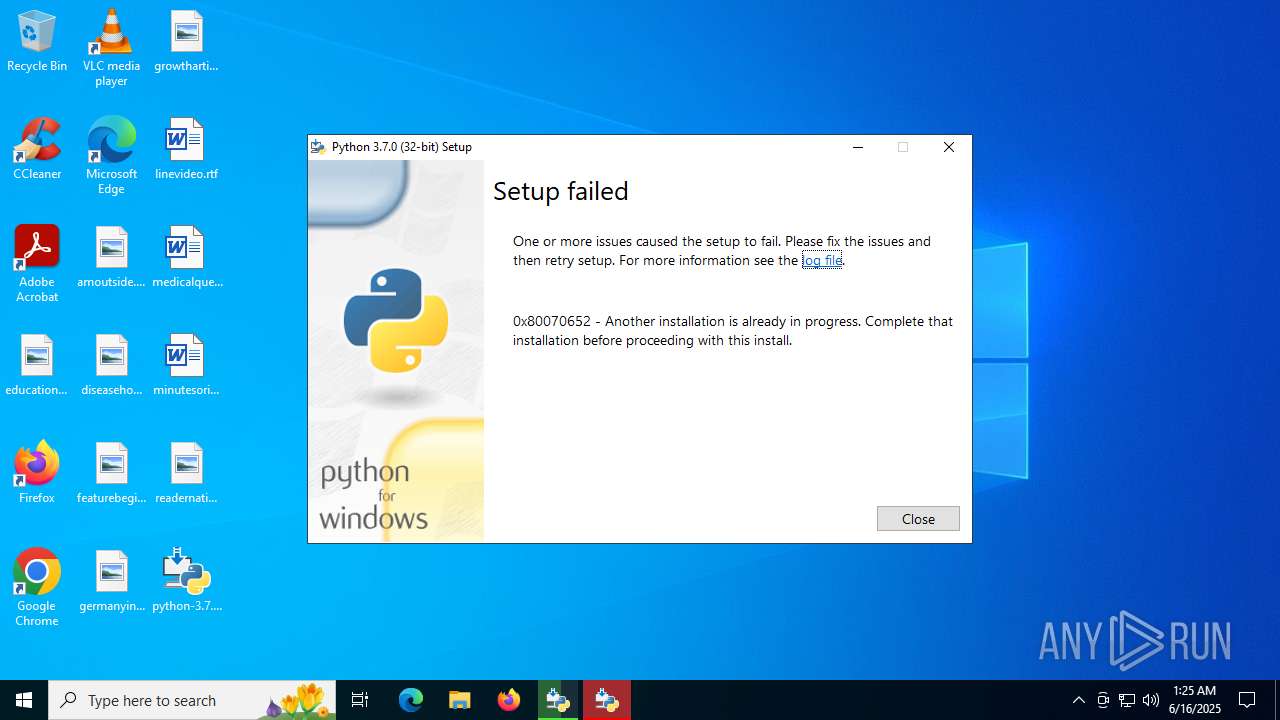
| File name: | python-3.7.0.exe |
| Full analysis: | https://app.any.run/tasks/dd93f0a7-4cb8-4f46-804f-33580cf55ee1 |
| Verdict: | Malicious activity |
| Analysis date: | June 16, 2025, 01:24:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | EBB6444C284C1447E902E87381AFEFF0 |
| SHA1: | FC827B7E37C3F96936FCB57C53738F5A265125BD |
| SHA256: | 559E56D293E05FF6159C3676DA2B5A93081EFAD7A8ACC74C12BB757E2B93DABA |
| SSDEEP: | 786432:QvJkjdBCp3HGXUh2mQfGG5s/FZBrr+so3n8h1Lsk8/Ph2M:iCjLCp3HGXUh2mYGLtrrBo38h6k8/52M |
MALICIOUS
Executing a file with an untrusted certificate
- python-3.7.0.exe (PID: 2120)
- python-3.7.0.exe (PID: 1816)
- python-3.7.0.exe (PID: 5284)
- python-3.7.0.exe (PID: 6528)
- python-3.7.0.exe (PID: 3636)
Changes the autorun value in the registry
- python-3.7.0.exe (PID: 1816)
- python-3.7.0.exe (PID: 3636)
SUSPICIOUS
Executable content was dropped or overwritten
- python-3.7.0.exe (PID: 2120)
- python-3.7.0.exe (PID: 1816)
- python-3.7.0.exe (PID: 3636)
Searches for installed software
- python-3.7.0.exe (PID: 1816)
- python-3.7.0.exe (PID: 6528)
- python-3.7.0.exe (PID: 3636)
Creates a software uninstall entry
- python-3.7.0.exe (PID: 1816)
- python-3.7.0.exe (PID: 3636)
The process drops C-runtime libraries
- python-3.7.0.exe (PID: 1816)
- msiexec.exe (PID: 3704)
Process drops legitimate windows executable
- python-3.7.0.exe (PID: 1816)
- msiexec.exe (PID: 3704)
Application launched itself
- python-3.7.0.exe (PID: 6528)
- python-3.7.0.exe (PID: 5284)
- updater.exe (PID: 3640)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3704)
Process drops python dynamic module
- msiexec.exe (PID: 3704)
There is functionality for taking screenshot (YARA)
- python-3.7.0.exe (PID: 1816)
- python-3.7.0.exe (PID: 3636)
The process executes via Task Scheduler
- updater.exe (PID: 3640)
INFO
Checks supported languages
- python-3.7.0.exe (PID: 2120)
- python-3.7.0.exe (PID: 1816)
- msiexec.exe (PID: 3704)
- python-3.7.0.exe (PID: 6528)
- python-3.7.0.exe (PID: 5284)
- python-3.7.0.exe (PID: 3636)
The sample compiled with english language support
- python-3.7.0.exe (PID: 2120)
- python-3.7.0.exe (PID: 1816)
- msiexec.exe (PID: 3704)
- python-3.7.0.exe (PID: 3636)
Create files in a temporary directory
- python-3.7.0.exe (PID: 2120)
- python-3.7.0.exe (PID: 1816)
- python-3.7.0.exe (PID: 3636)
Reads the computer name
- python-3.7.0.exe (PID: 1816)
- msiexec.exe (PID: 3704)
- python-3.7.0.exe (PID: 3636)
Launching a file from a Registry key
- python-3.7.0.exe (PID: 1816)
- python-3.7.0.exe (PID: 3636)
Creates files or folders in the user directory
- python-3.7.0.exe (PID: 1816)
- msiexec.exe (PID: 3704)
Reads the machine GUID from the registry
- python-3.7.0.exe (PID: 1816)
- msiexec.exe (PID: 3704)
- python-3.7.0.exe (PID: 3636)
Manual execution by a user
- python-3.7.0.exe (PID: 6528)
Reads the software policy settings
- msiexec.exe (PID: 3704)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3704)
Creates a software uninstall entry
- msiexec.exe (PID: 3704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:11:18 22:00:38+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit, Removable run from swap, Net run from swap |
| PEType: | PE32 |
| LinkerVersion: | 14.11 |
| CodeSize: | 301568 |
| InitializedDataSize: | 237056 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2e2a6 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.7.150.0 |
| ProductVersionNumber: | 3.7.150.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Python Software Foundation |
| FileDescription: | Python 3.7.0 (32-bit) |
| FileVersion: | 3.7.150.0 |
| InternalName: | setup |
| LegalCopyright: | Copyright (c) Python Software Foundation. All rights reserved. |
| OriginalFileName: | python-3.7.0.exe |
| ProductName: | Python 3.7.0 (32-bit) |
| ProductVersion: | 3.7.150.0 |
Total processes
139
Monitored processes
9
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1564 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --crash-handler --system "--database=C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\Crashpad" --url=https://clients2.google.com/cr/report --annotation=prod=Update4 --annotation=ver=134.0.6985.0 "--attachment=C:\Program Files (x86)\Google\GoogleUpdater\updater.log" --initial-client-data=0x298,0x29c,0x2a0,0x274,0x2a4,0x111c460,0x111c46c,0x111c478 | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | updater.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
| 1816 | "C:\Users\admin\AppData\Local\Temp\{2EFA1C6F-DAF5-4FAC-BB5D-AA7316D70250}\.cr\python-3.7.0.exe" -burn.clean.room="C:\Users\admin\Desktop\python-3.7.0.exe" -burn.filehandle.attached=740 -burn.filehandle.self=696 | C:\Users\admin\AppData\Local\Temp\{2EFA1C6F-DAF5-4FAC-BB5D-AA7316D70250}\.cr\python-3.7.0.exe | python-3.7.0.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python 3.7.0 (32-bit) Version: 3.7.150.0 Modules
| |||||||||||||||
| 2120 | "C:\Users\admin\Desktop\python-3.7.0.exe" | C:\Users\admin\Desktop\python-3.7.0.exe | explorer.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python 3.7.0 (32-bit) Version: 3.7.150.0 Modules
| |||||||||||||||
| 3636 | "C:\Users\admin\AppData\Local\Package Cache\{ece37911-ffeb-4f29-95d6-abcf555d7364}\python-3.7.0.exe" -burn.clean.room="C:\Users\admin\AppData\Local\Package Cache\{ece37911-ffeb-4f29-95d6-abcf555d7364}\python-3.7.0.exe" -burn.filehandle.attached=520 -burn.filehandle.self=548 /burn.log.append "C:\Users\admin\AppData\Local\Temp\Python 3.7.0 (32-bit)_20250616012417.log" | C:\Users\admin\AppData\Local\Package Cache\{ece37911-ffeb-4f29-95d6-abcf555d7364}\python-3.7.0.exe | python-3.7.0.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python 3.7.0 (32-bit) Exit code: 1618 Version: 3.7.150.0 Modules
| |||||||||||||||
| 3640 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --wake --system | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
| 3704 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5284 | "C:\Users\admin\AppData\Local\Package Cache\{ece37911-ffeb-4f29-95d6-abcf555d7364}\python-3.7.0.exe" /burn.log.append "C:\Users\admin\AppData\Local\Temp\Python 3.7.0 (32-bit)_20250616012417.log" | C:\Users\admin\AppData\Local\Package Cache\{ece37911-ffeb-4f29-95d6-abcf555d7364}\python-3.7.0.exe | — | python-3.7.0.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python 3.7.0 (32-bit) Exit code: 1618 Version: 3.7.150.0 Modules
| |||||||||||||||
| 6224 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6528 | "C:\Users\admin\AppData\Local\Package Cache\{ece37911-ffeb-4f29-95d6-abcf555d7364}\python-3.7.0.exe" /burn.runonce | C:\Users\admin\AppData\Local\Package Cache\{ece37911-ffeb-4f29-95d6-abcf555d7364}\python-3.7.0.exe | — | explorer.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python 3.7.0 (32-bit) Exit code: 0 Version: 3.7.150.0 Modules
| |||||||||||||||
Total events
37 378
Read events
32 855
Write events
4 426
Delete events
97
Modification events
| (PID) Process: | (1816) python-3.7.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ece37911-ffeb-4f29-95d6-abcf555d7364} |
| Operation: | write | Name: | BundleCachePath |
Value: C:\Users\admin\AppData\Local\Package Cache\{ece37911-ffeb-4f29-95d6-abcf555d7364}\python-3.7.0.exe | |||
| (PID) Process: | (1816) python-3.7.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ece37911-ffeb-4f29-95d6-abcf555d7364} |
| Operation: | write | Name: | BundleUpgradeCode |
Value: {5C464E87-58D7-5592-B004-12ED93D23716} | |||
| (PID) Process: | (1816) python-3.7.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ece37911-ffeb-4f29-95d6-abcf555d7364} |
| Operation: | write | Name: | BundleAddonCode |
Value: | |||
| (PID) Process: | (1816) python-3.7.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ece37911-ffeb-4f29-95d6-abcf555d7364} |
| Operation: | write | Name: | BundleDetectCode |
Value: | |||
| (PID) Process: | (1816) python-3.7.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ece37911-ffeb-4f29-95d6-abcf555d7364} |
| Operation: | write | Name: | BundlePatchCode |
Value: | |||
| (PID) Process: | (1816) python-3.7.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ece37911-ffeb-4f29-95d6-abcf555d7364} |
| Operation: | write | Name: | BundleVersion |
Value: 3.7.150.0 | |||
| (PID) Process: | (1816) python-3.7.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ece37911-ffeb-4f29-95d6-abcf555d7364} |
| Operation: | write | Name: | VersionMajor |
Value: 3 | |||
| (PID) Process: | (1816) python-3.7.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ece37911-ffeb-4f29-95d6-abcf555d7364} |
| Operation: | write | Name: | VersionMinor |
Value: 7 | |||
| (PID) Process: | (1816) python-3.7.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ece37911-ffeb-4f29-95d6-abcf555d7364} |
| Operation: | write | Name: | BundleProviderKey |
Value: CPython-3.7-32 | |||
| (PID) Process: | (1816) python-3.7.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{ece37911-ffeb-4f29-95d6-abcf555d7364} |
| Operation: | write | Name: | BundleTag |
Value: | |||
Executable files
87
Suspicious files
202
Text files
2 198
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1816 | python-3.7.0.exe | C:\Users\admin\AppData\Local\Temp\{B54E6B39-0B1C-4925-8C00-D3AF13AF326B}\lib_JustForMe | — | |
MD5:— | SHA256:— | |||
| 1816 | python-3.7.0.exe | C:\Users\admin\AppData\Local\Temp\{B54E6B39-0B1C-4925-8C00-D3AF13AF326B}\doc_JustForMe | — | |
MD5:— | SHA256:— | |||
| 1816 | python-3.7.0.exe | C:\Users\admin\AppData\Local\Temp\{B54E6B39-0B1C-4925-8C00-D3AF13AF326B}\.ba\Default.thm | xml | |
MD5:7CC2F43E47DA58F63DB7CC62C2D040B8 | SHA256:B619AE6E9C7E352624F0B491AFF9588D7B8C9E83092B2B6B84D1DE8F719962D4 | |||
| 1816 | python-3.7.0.exe | C:\Users\admin\AppData\Local\Temp\{B54E6B39-0B1C-4925-8C00-D3AF13AF326B}\.ba\BootstrapperApplicationData.xml | xml | |
MD5:3BF49DD8075A485DAB6B1860CCDDDB17 | SHA256:56AFBA279807312AA3B4623A8A85DADDD97FF2E375FCB467F70FDF37A9A9CBAD | |||
| 1816 | python-3.7.0.exe | C:\Users\admin\AppData\Local\Temp\{B54E6B39-0B1C-4925-8C00-D3AF13AF326B}\.ba\Default.wxl | xml | |
MD5:CDA499CD6042FBD5F94F38DDBE917F55 | SHA256:9B407D19166490E6B1E25DD0FD9CEE8782C78894CE200958D13A2F2E452FC715 | |||
| 2120 | python-3.7.0.exe | C:\Users\admin\AppData\Local\Temp\{2EFA1C6F-DAF5-4FAC-BB5D-AA7316D70250}\.cr\python-3.7.0.exe | executable | |
MD5:C8284F4FB389C03873B541095B865B13 | SHA256:5CA97C7249EC99E1260DA62C3DD805F1EC60A3CEA49EFD9A4538BC034C2AC0AE | |||
| 1816 | python-3.7.0.exe | C:\Users\admin\AppData\Local\Package Cache\.unverified\lib_JustForMe | — | |
MD5:— | SHA256:— | |||
| 1816 | python-3.7.0.exe | C:\Users\admin\AppData\Local\Package Cache\{09160A5D-8B99-4A89-9E9D-8A6D8E9C7EC1}v3.7.150.0\lib.msi | — | |
MD5:— | SHA256:— | |||
| 1816 | python-3.7.0.exe | C:\Users\admin\AppData\Local\Package Cache\{ece37911-ffeb-4f29-95d6-abcf555d7364}\state.rsm | binary | |
MD5:707804655B71B51B8541D9B560648AF0 | SHA256:7855FFFA6FC646EAE4676C3321CDCD561EB911E2F29DE09D0AF89154163BF173 | |||
| 1816 | python-3.7.0.exe | C:\Users\admin\AppData\Local\Temp\{B54E6B39-0B1C-4925-8C00-D3AF13AF326B}\.ba\PythonBA.dll | executable | |
MD5:0D97E06337ACC63A676301EB0B0F96E9 | SHA256:909206828BC02754CF386FDF03EF3B3313D2B1744997C17838A7889066855D4B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
26
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3704 | msiexec.exe | GET | 503 | 23.48.23.23:80 | http://ocsp.startssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRBc6bT2N9qzRkeiWvn5WI5MHBpNQQUTgvvGqRAW6UXaYcwyjRoQ9BBrvICEHgiQ6FT3ygKH%2FrhXNAoTIY%3D | unknown | — | — | whitelisted |
3704 | msiexec.exe | GET | 503 | 23.48.23.23:80 | http://ocsp.startssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRaDa32uvZMCTCyY9fJ5x%2BLW4U9vQQUZnqezZxzhmppoK76jLsYjwjs1QQCEGmnCkGID2u%2FaD43Ztan5vQ%3D | unknown | — | — | whitelisted |
3704 | msiexec.exe | GET | 200 | 23.48.23.27:80 | http://crl.startssl.com/sca-code3.crl | unknown | — | — | whitelisted |
3704 | msiexec.exe | GET | 200 | 23.48.23.27:80 | http://crl.startssl.com/sca-code3.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ocsp.startssl.com |
| whitelisted |
crl.startssl.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |