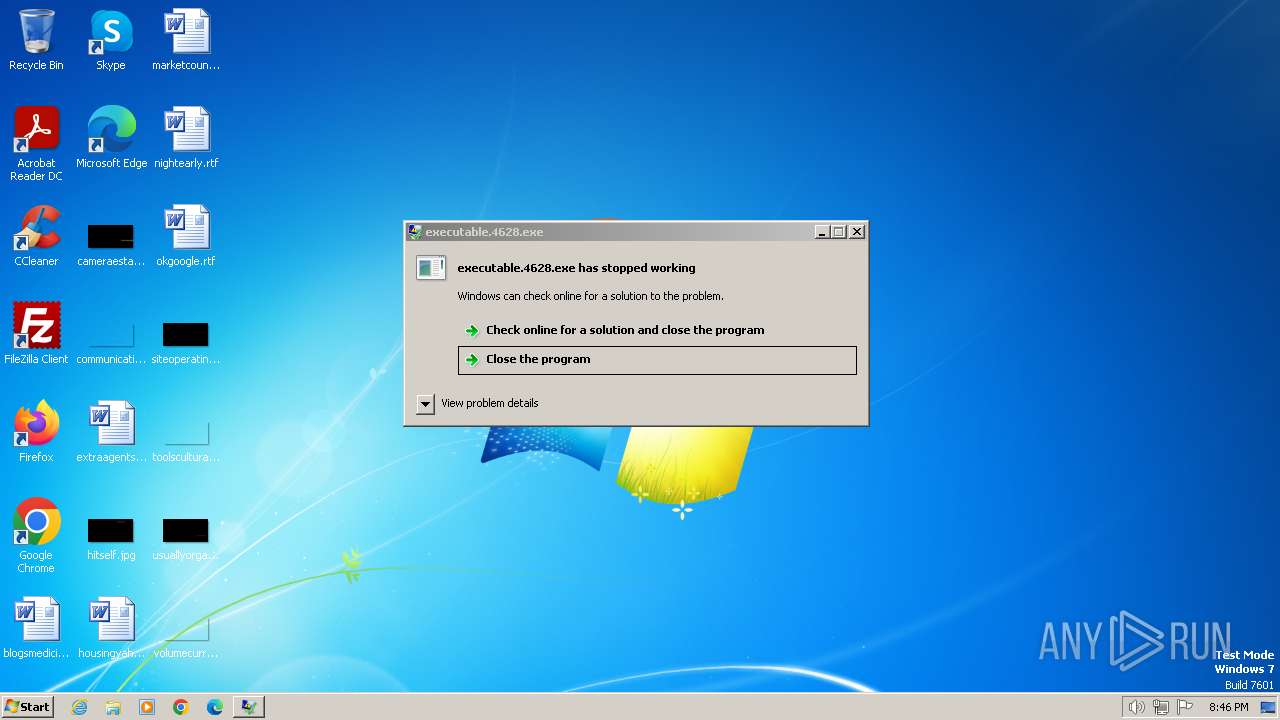
| File name: | executable.4628.exe |
| Full analysis: | https://app.any.run/tasks/2a6dbb9a-e833-446c-8cde-af146400ceba |
| Verdict: | Malicious activity |
| Analysis date: | March 09, 2024, 20:46:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 586C328AF60CDCA1A7FB20AFE46A29A9 |
| SHA1: | 84D0694CF4D0052B3A6FAB99DCFE6A08918CA907 |
| SHA256: | 55713E783586A37496C0F6BB7891DFCF22C3EDA867889AFFC83AE258592BFA60 |
| SSDEEP: | 12288:q6fKI8D2v9QGhY2ue1S1Sd54yPuLVI9g:q6iQveq1S1Sd54S9g |
MALICIOUS
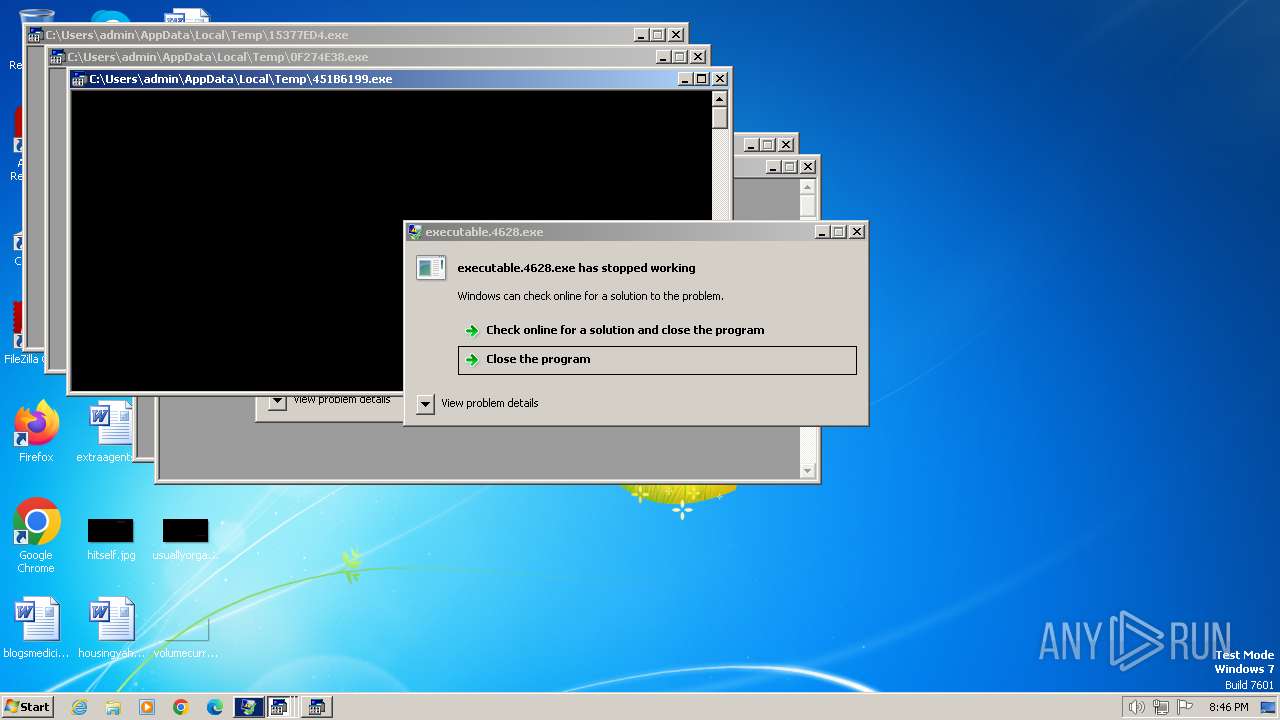
Drops the executable file immediately after the start
- executable.4628.exe (PID: 3864)
- hYMkrT.exe (PID: 4052)
Actions looks like stealing of personal data
- hYMkrT.exe (PID: 4052)
Connects to the CnC server
- hYMkrT.exe (PID: 4052)
BDAEJEC has been detected (SURICATA)
- hYMkrT.exe (PID: 4052)
SUSPICIOUS
Reads the Internet Settings
- hYMkrT.exe (PID: 4052)
Executable content was dropped or overwritten
- executable.4628.exe (PID: 3864)
- hYMkrT.exe (PID: 4052)
Reads security settings of Internet Explorer
- hYMkrT.exe (PID: 4052)
Creates file in the systems drive root
- ntvdm.exe (PID: 3212)
Connects to unusual port
- hYMkrT.exe (PID: 4052)
Executing commands from a ".bat" file
- hYMkrT.exe (PID: 4052)
Starts CMD.EXE for commands execution
- hYMkrT.exe (PID: 4052)
INFO
Checks supported languages
- executable.4628.exe (PID: 3864)
- hYMkrT.exe (PID: 4052)
Reads the computer name
- hYMkrT.exe (PID: 4052)
Create files in a temporary directory
- executable.4628.exe (PID: 3864)
- hYMkrT.exe (PID: 4052)
Checks proxy server information
- hYMkrT.exe (PID: 4052)
Reads the machine GUID from the registry
- hYMkrT.exe (PID: 4052)
Creates files or folders in the user directory
- hYMkrT.exe (PID: 4052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:12:01 08:36:04+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 782336 |
| InitializedDataSize: | 372736 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x116000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
56
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1824 | "C:\Windows\system32\ntvdm.exe" -i4 | C:\Windows\System32\ntvdm.exe | hYMkrT.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2168 | "C:\Windows\system32\ntvdm.exe" -i5 | C:\Windows\System32\ntvdm.exe | hYMkrT.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2184 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\3f0b30fd.bat" " | C:\Windows\System32\cmd.exe | — | hYMkrT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2232 | "C:\Windows\system32\ntvdm.exe" -i2 | C:\Windows\System32\ntvdm.exe | hYMkrT.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2292 | "C:\Windows\system32\ntvdm.exe" -i3 | C:\Windows\System32\ntvdm.exe | hYMkrT.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3212 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\System32\ntvdm.exe | hYMkrT.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3864 | "C:\Users\admin\AppData\Local\Temp\executable.4628.exe" | C:\Users\admin\AppData\Local\Temp\executable.4628.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4052 | C:\Users\admin\AppData\Local\Temp\hYMkrT.exe | C:\Users\admin\AppData\Local\Temp\hYMkrT.exe | executable.4628.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 111
Read events
3 071
Write events
31
Delete events
9
Modification events
| (PID) Process: | (4052) hYMkrT.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4052) hYMkrT.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4052) hYMkrT.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4052) hYMkrT.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4052) hYMkrT.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (4052) hYMkrT.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (4052) hYMkrT.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (4052) hYMkrT.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (4052) hYMkrT.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (4052) hYMkrT.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005C010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
2
Suspicious files
0
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3864 | executable.4628.exe | C:\Users\admin\AppData\Local\Temp\hYMkrT.exe | executable | |
MD5:56B2C3810DBA2E939A8BB9FA36D3CF96 | SHA256:4354970CCC7CD6BB16318F132C34F6A1B3D5C2EA7FF53E1C9271905527F2DB07 | |||
| 1824 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs11FC.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 4052 | hYMkrT.exe | C:\Users\admin\AppData\Local\Temp\65521C0F.exe | text | |
MD5:D3B07384D113EDEC49EAA6238AD5FF00 | SHA256:B5BB9D8014A0F9B1D61E21E796D78DCCDF1352F23CD32812F4850B878AE4944C | |||
| 4052 | hYMkrT.exe | C:\Users\admin\AppData\Local\Temp\15377ED4.exe | text | |
MD5:D3B07384D113EDEC49EAA6238AD5FF00 | SHA256:B5BB9D8014A0F9B1D61E21E796D78DCCDF1352F23CD32812F4850B878AE4944C | |||
| 4052 | hYMkrT.exe | C:\Users\admin\AppData\Local\Temp\0F274E38.exe | text | |
MD5:D3B07384D113EDEC49EAA6238AD5FF00 | SHA256:B5BB9D8014A0F9B1D61E21E796D78DCCDF1352F23CD32812F4850B878AE4944C | |||
| 3212 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsE15.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 2232 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsF5C.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 3212 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsE05.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 4052 | hYMkrT.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\k2[1].rar | text | |
MD5:D3B07384D113EDEC49EAA6238AD5FF00 | SHA256:B5BB9D8014A0F9B1D61E21E796D78DCCDF1352F23CD32812F4850B878AE4944C | |||
| 2292 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs10B5.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
10
DNS requests
1
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4052 | hYMkrT.exe | GET | — | 34.174.61.199:799 | http://ddos.dnsnb8.net:799/cj//k1.rar | unknown | — | — | unknown |
4052 | hYMkrT.exe | GET | — | 34.174.61.199:799 | http://ddos.dnsnb8.net:799/cj//k1.rar | unknown | — | — | unknown |
— | — | GET | — | 34.174.61.199:799 | http://ddos.dnsnb8.net:799/cj//k2.rar | unknown | — | — | unknown |
4052 | hYMkrT.exe | GET | — | 34.174.61.199:799 | http://ddos.dnsnb8.net:799/cj//k3.rar | unknown | — | — | unknown |
4052 | hYMkrT.exe | GET | — | 34.174.61.199:799 | http://ddos.dnsnb8.net:799/cj//k4.rar | unknown | — | — | unknown |
4052 | hYMkrT.exe | GET | — | 34.174.61.199:799 | http://ddos.dnsnb8.net:799/cj//k5.rar | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4052 | hYMkrT.exe | 34.174.61.199:799 | ddos.dnsnb8.net | GOOGLE-CLOUD-PLATFORM | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ddos.dnsnb8.net |
| unknown |
Threats
2 ETPRO signatures available at the full report