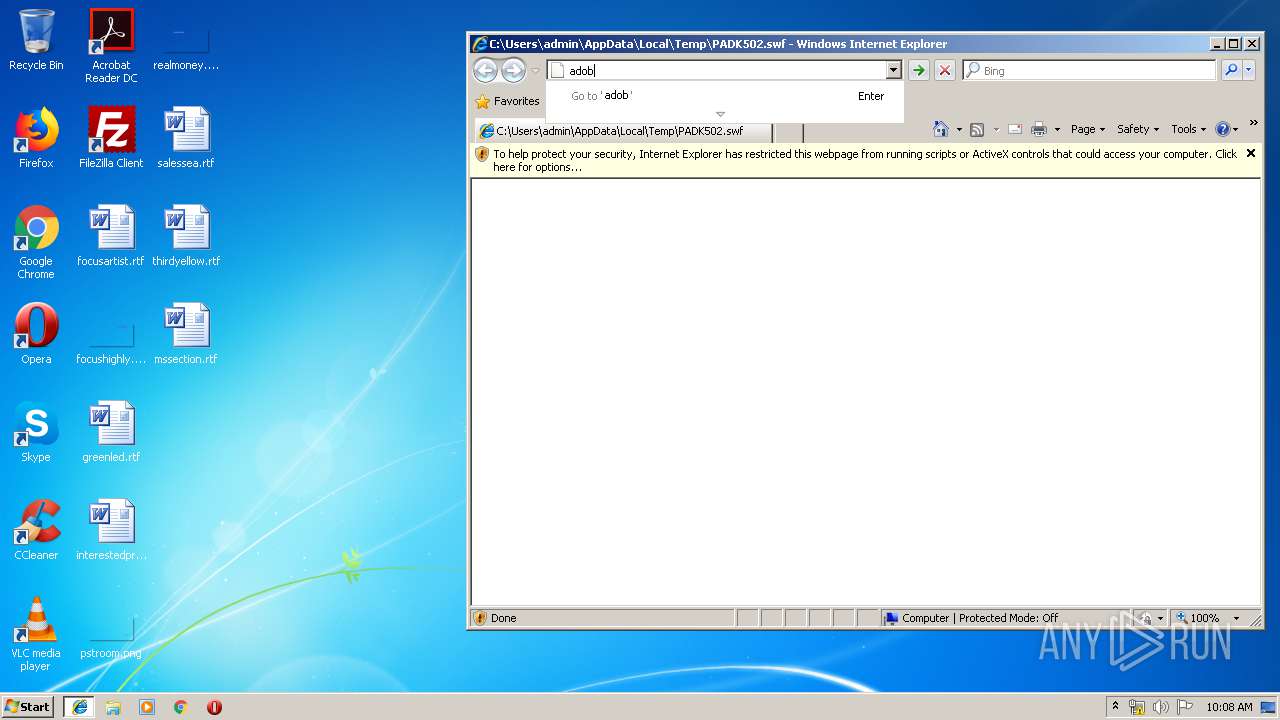
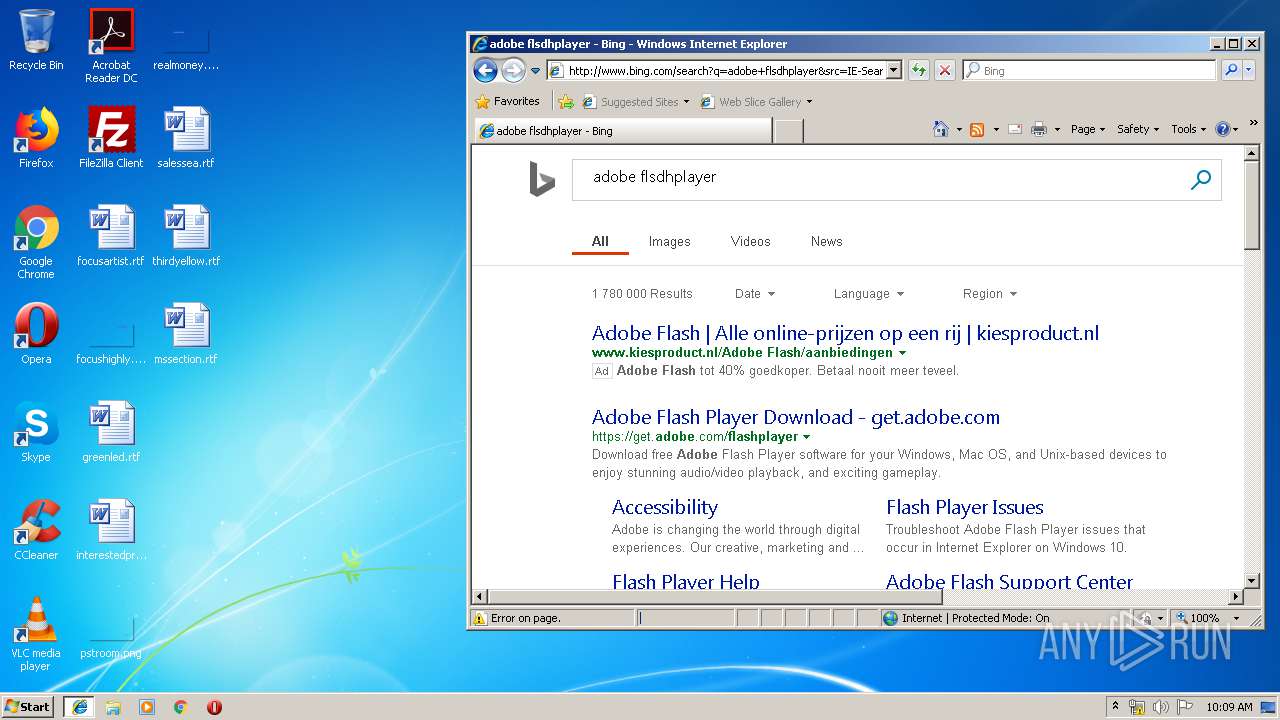
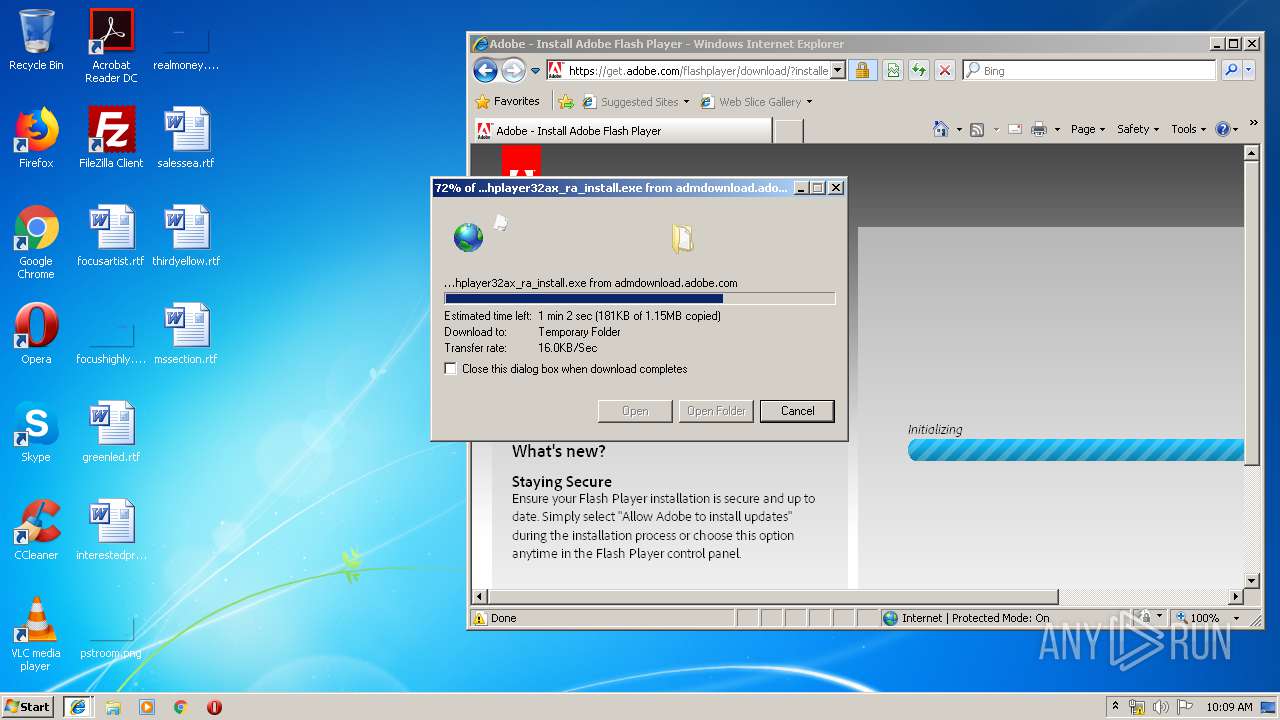
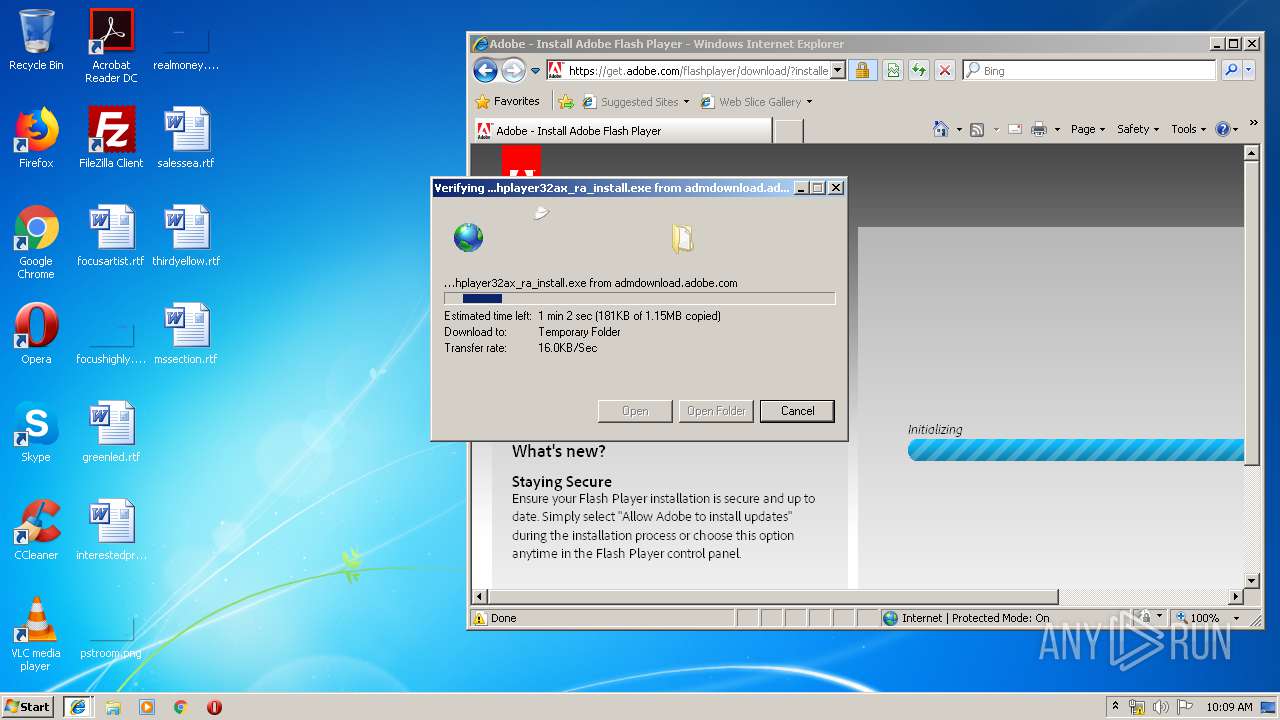
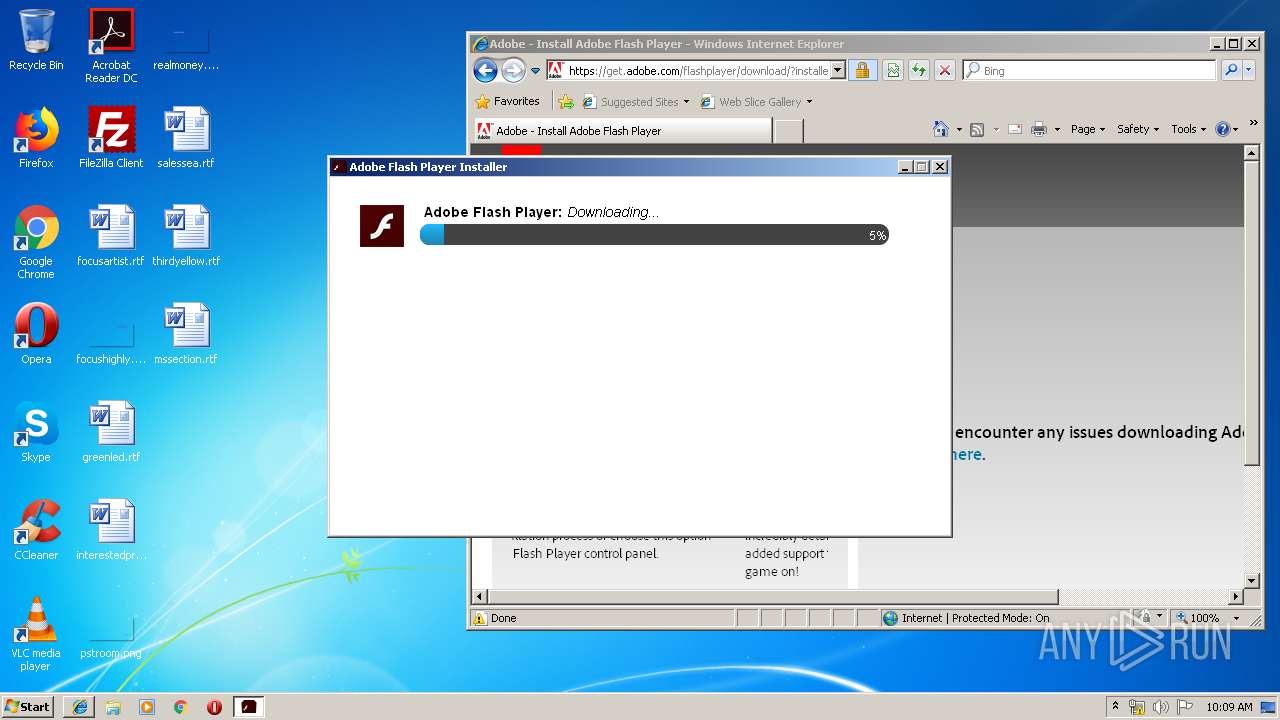
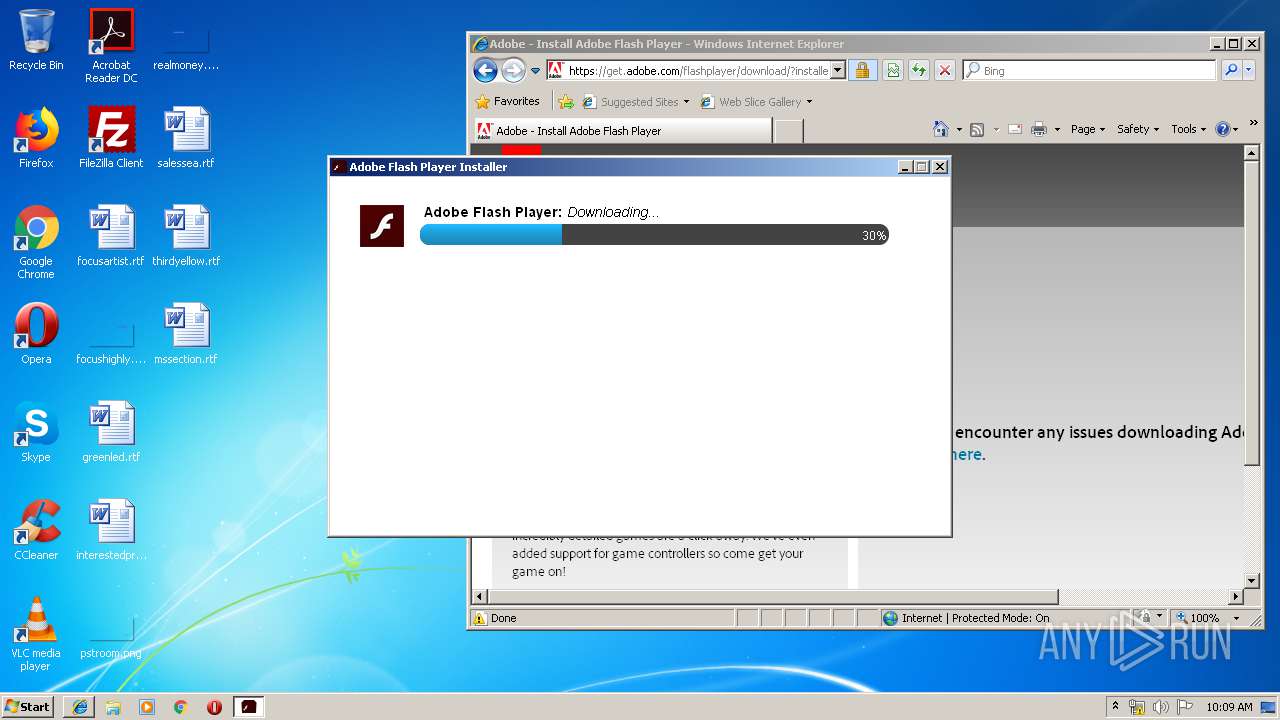
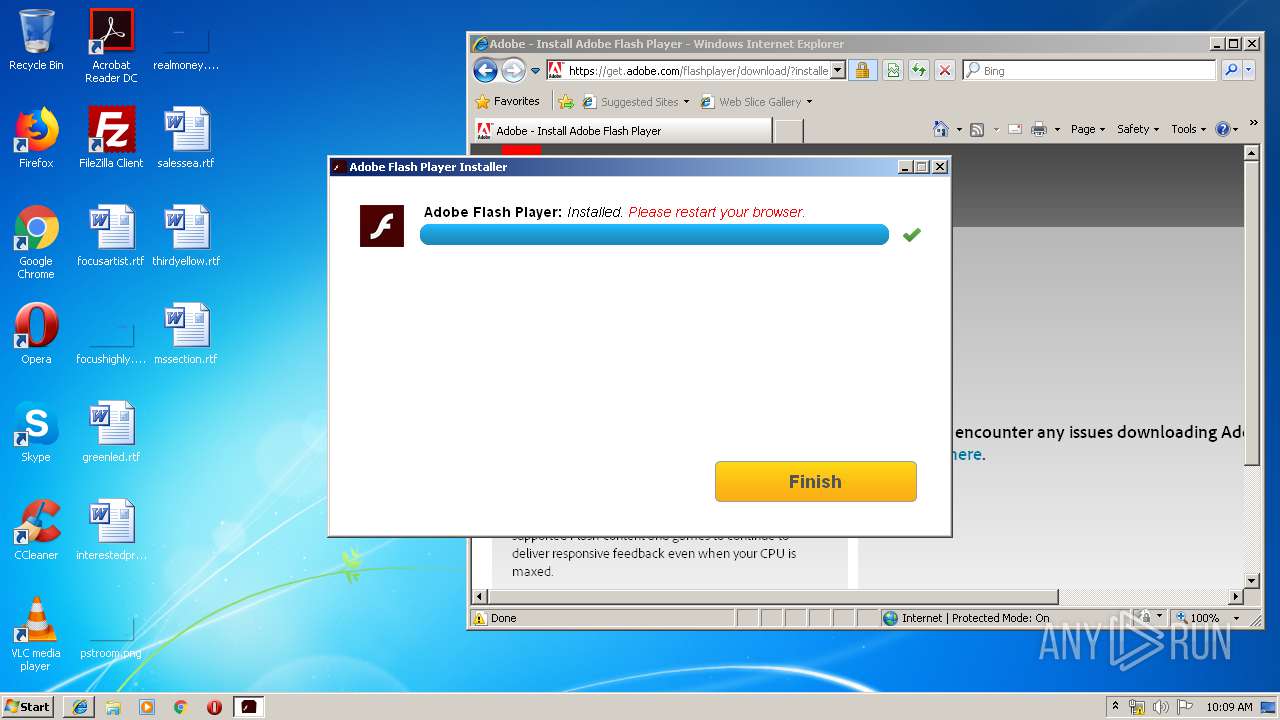
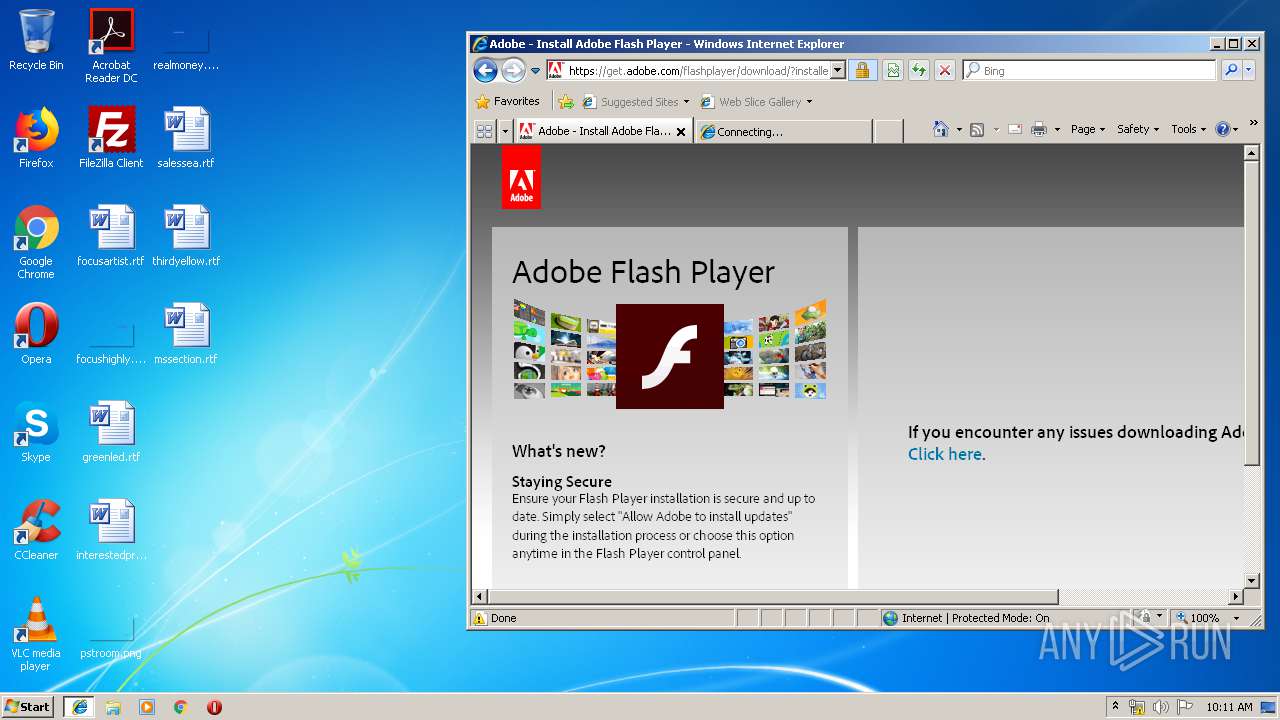
| download: | PADK502.swf |
| Full analysis: | https://app.any.run/tasks/b6e00dc2-66d6-40de-94c8-0d21829f17d1 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 09:08:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-shockwave-flash |
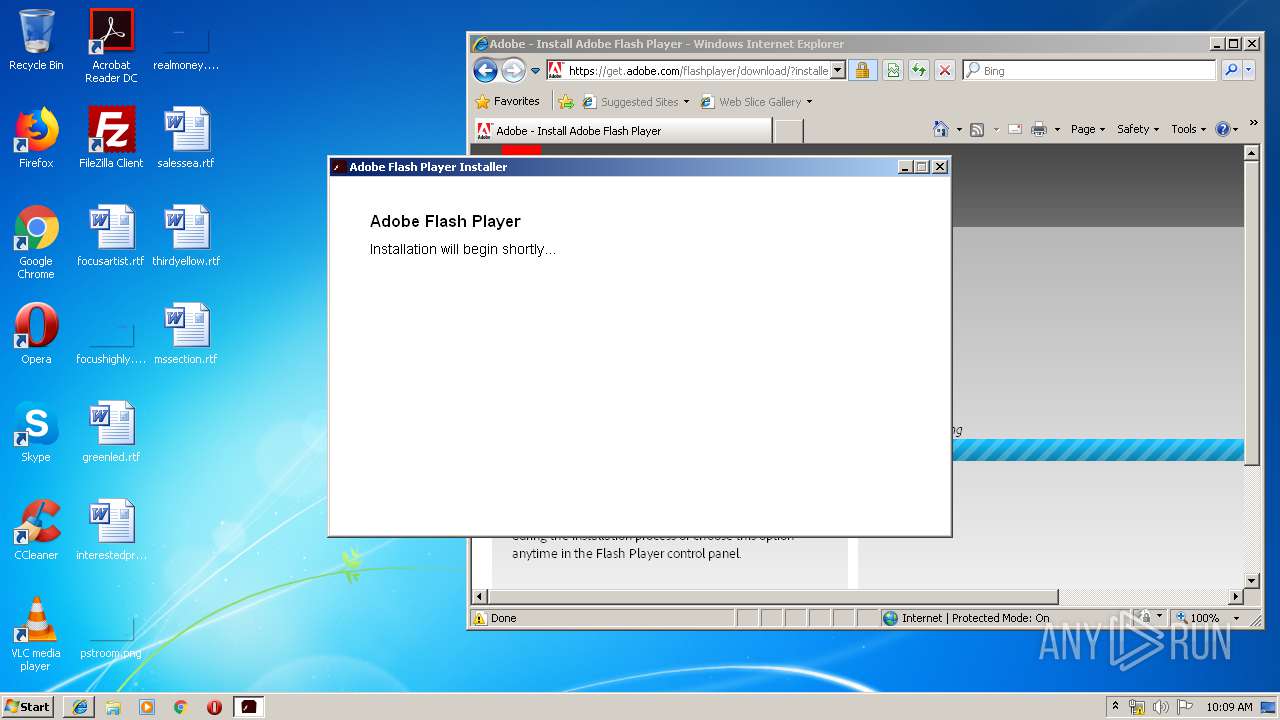
| File info: | Macromedia Flash data (compressed), version 10 |
| MD5: | E79CF4C5C86DBC2F73BCDE1278200E03 |
| SHA1: | BDAEF65E1976349FC8792F1D1D6CB0C092C39612 |
| SHA256: | 556D83AF693316581F10690966943863DD05CA3FFEFC97424BB8F087D2FB5E50 |
| SSDEEP: | 384:1ENPr4gA/BtrNmp8dssbesk5mzaIWhcvYqGGQqUFcc75sIhfbJfUy5+:1ENPs/XRmSdgs+IcgYqGDqhcKiJfB+ |
MALICIOUS
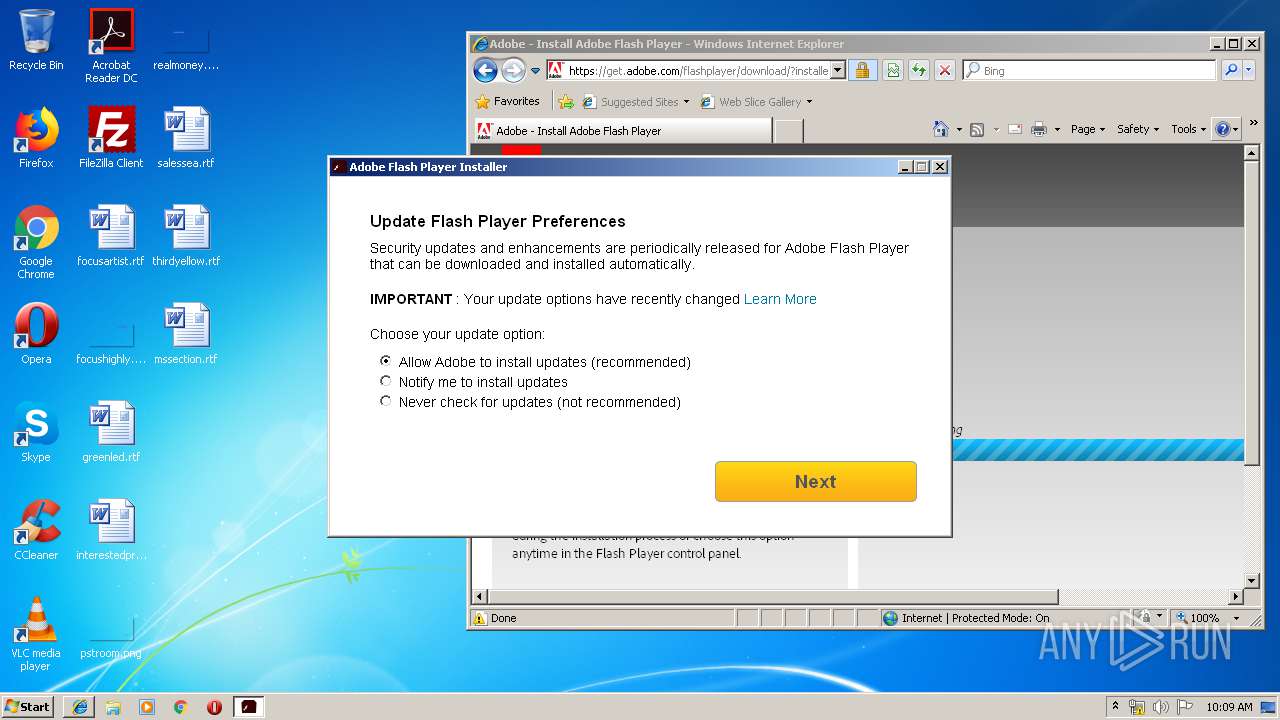
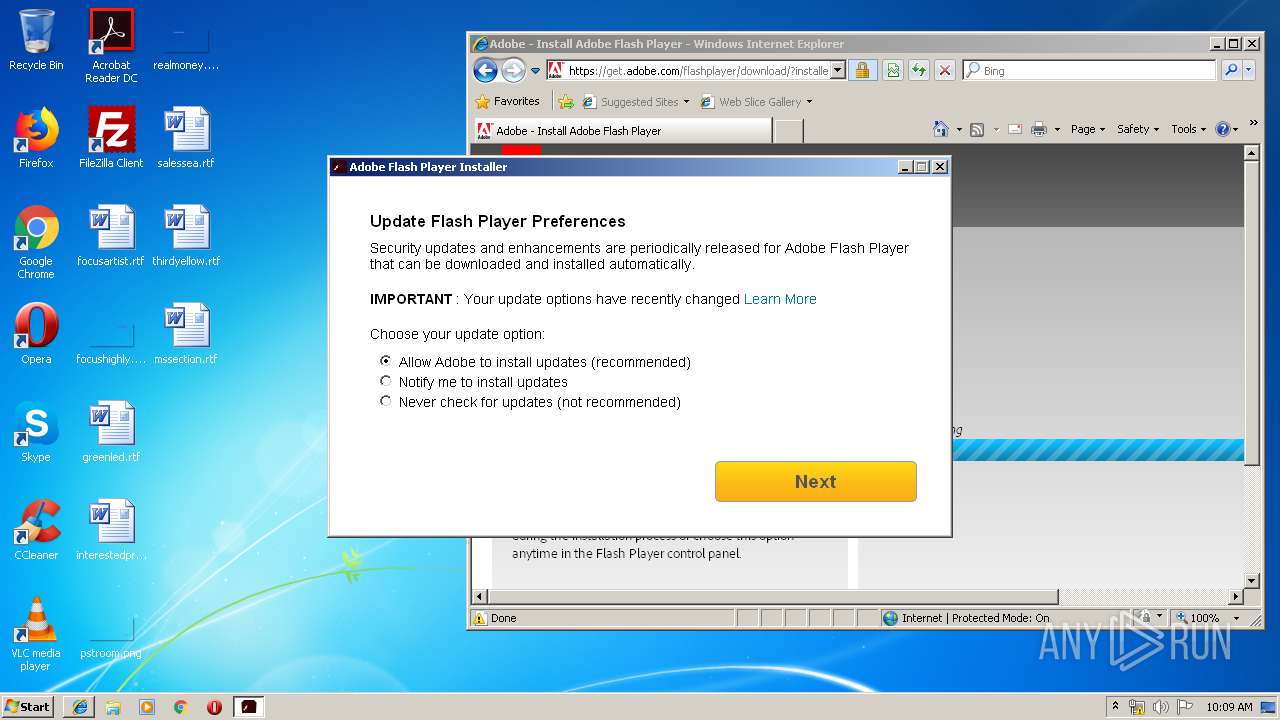
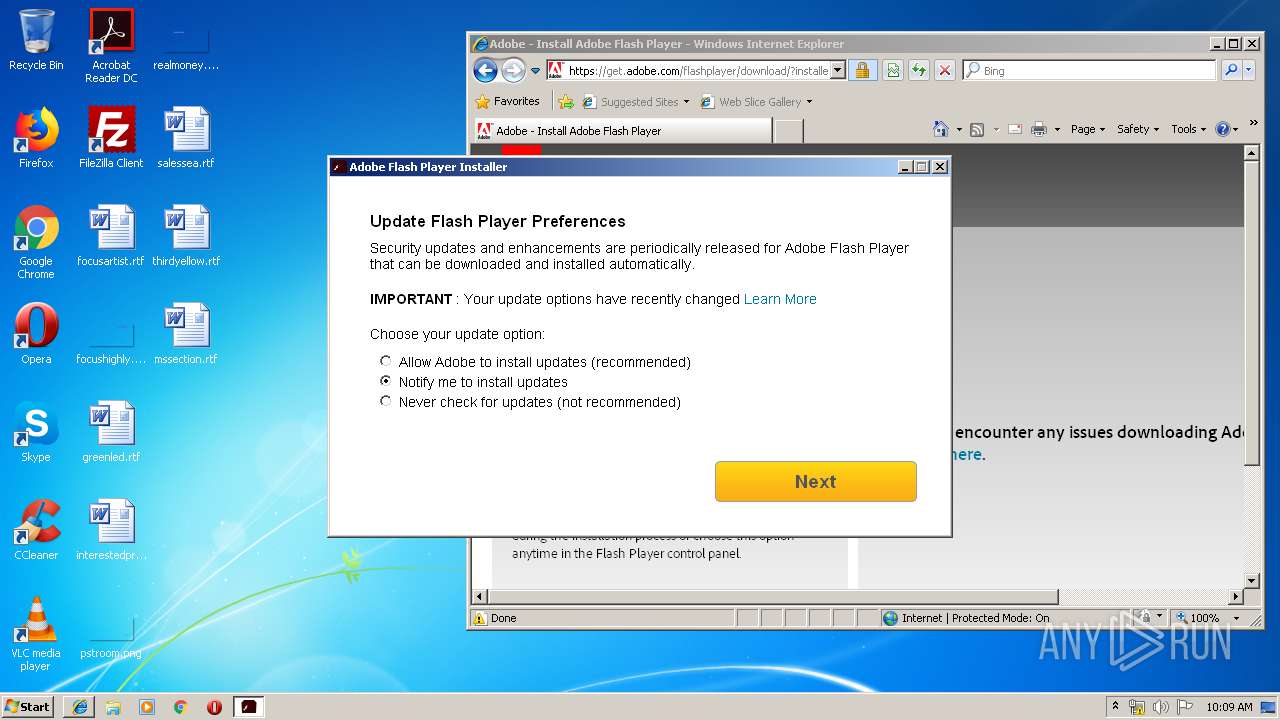
Application was dropped or rewritten from another process
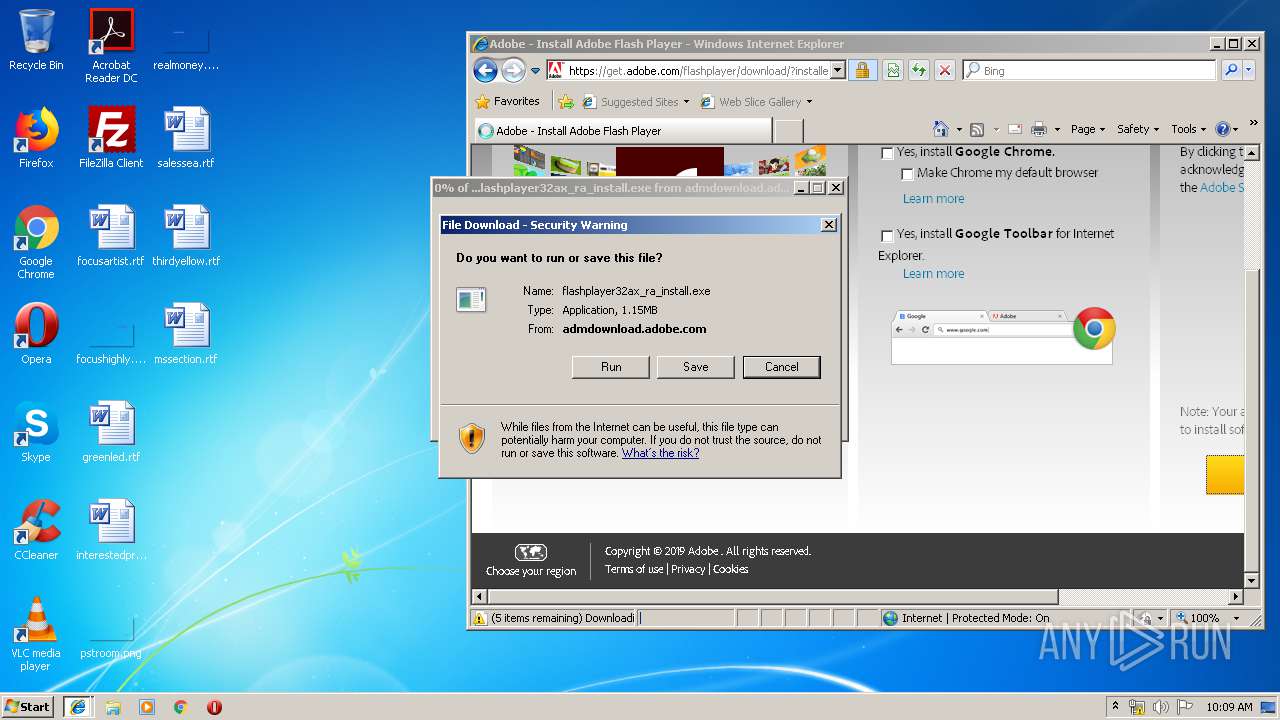
- flashplayer32ax_ra_install[1].exe (PID: 2820)
- flashplayer32ax_ra_install[1].exe (PID: 3456)
- gccheck_small.exe (PID: 1900)
- gtcheck.exe (PID: 1860)
- gccheck_small.exe (PID: 2724)
- 4D8D4B61-8366-40E4-AD80-4F50E7E2AC27 (PID: 2576)
- FlashPlayerUpdateService.exe (PID: 2912)
- FlashPlayerUpdateService.exe (PID: 1244)
- FlashPlayerUpdateService.exe (PID: 1520)
Changes settings of System certificates
- flashplayer32ax_ra_install[1].exe (PID: 3456)
Loads the Task Scheduler COM API
- FlashPlayerUpdateService.exe (PID: 1244)
- FlashPlayerUpdateService.exe (PID: 2912)
Loads dropped or rewritten executable
- 4D8D4B61-8366-40E4-AD80-4F50E7E2AC27 (PID: 2576)
- iexplore.exe (PID: 3680)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 1088)
- iexplore.exe (PID: 3336)
- flashplayer32ax_ra_install[1].exe (PID: 2820)
- 4D8D4B61-8366-40E4-AD80-4F50E7E2AC27 (PID: 2576)
Application launched itself
- flashplayer32ax_ra_install[1].exe (PID: 2820)
Reads internet explorer settings
- flashplayer32ax_ra_install[1].exe (PID: 2820)
Adds / modifies Windows certificates
- flashplayer32ax_ra_install[1].exe (PID: 3456)
Starts application with an unusual extension
- flashplayer32ax_ra_install[1].exe (PID: 3456)
Creates files in the Windows directory
- 4D8D4B61-8366-40E4-AD80-4F50E7E2AC27 (PID: 2576)
Removes files from Windows directory
- 4D8D4B61-8366-40E4-AD80-4F50E7E2AC27 (PID: 2576)
Disables SEHOP
- 4D8D4B61-8366-40E4-AD80-4F50E7E2AC27 (PID: 2576)
Starts CMD.EXE for commands execution
- 4D8D4B61-8366-40E4-AD80-4F50E7E2AC27 (PID: 2576)
Creates files in the user directory
- flashplayer32ax_ra_install[1].exe (PID: 2820)
Modifies the open verb of a shell class
- 4D8D4B61-8366-40E4-AD80-4F50E7E2AC27 (PID: 2576)
Creates a software uninstall entry
- 4D8D4B61-8366-40E4-AD80-4F50E7E2AC27 (PID: 2576)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3336)
- iexplore.exe (PID: 4076)
Reads internet explorer settings
- iexplore.exe (PID: 392)
- iexplore.exe (PID: 1088)
- iexplore.exe (PID: 3680)
- iexplore.exe (PID: 1892)
Application launched itself
- iexplore.exe (PID: 3336)
- iexplore.exe (PID: 4076)
Reads Internet Cache Settings
- iexplore.exe (PID: 392)
- iexplore.exe (PID: 1088)
- iexplore.exe (PID: 3680)
- iexplore.exe (PID: 1892)
Creates files in the user directory
- iexplore.exe (PID: 1088)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 1812)
- iexplore.exe (PID: 3336)
- iexplore.exe (PID: 3680)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 1088)
Reads settings of System Certificates
- iexplore.exe (PID: 3336)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3336)
Changes settings of System certificates
- iexplore.exe (PID: 3336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .swf | | | Macromedia Flash Player Compressed Movie (100) |
|---|
EXIF
Flash
| FlashVersion: | 10 |
|---|---|
| Compressed: | |
| ImageWidth: | 660 |
| ImageHeight: | 390 |
| FrameRate: | 1 |
| FrameCount: | 1 |
| Duration: | 1.00 s |
| FlashAttributes: | ActionScript3 |
Composite
| ImageSize: | 660x390 |
|---|---|
| Megapixels: | 0.257 |
Total processes
66
Monitored processes
19
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3336 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 764 | "C:\Windows\system32\cmd.exe" /c del "C:\Users\admin\AppData\Local\Adobe\950EE43E-8831-4F28-9D72-2AD52B1A19C1\50B9A6D2-E1BA-4023-808D-1ABCE0BFF518\4D8D4B61-8366-40E4-AD80-4F50E7E2AC27" >> NUL | C:\Windows\system32\cmd.exe | — | 4D8D4B61-8366-40E4-AD80-4F50E7E2AC27 | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3336 CREDAT:203009 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1244 | C:\Windows\system32\Macromed\Flash\FlashPlayerUpdateService.exe -uninstall | C:\Windows\system32\Macromed\Flash\FlashPlayerUpdateService.exe | — | 4D8D4B61-8366-40E4-AD80-4F50E7E2AC27 | |||||||||||
User: admin Company: Adobe Integrity Level: HIGH Description: Adobe® Flash® Player Update Service 32.0 r0 Exit code: 0 Version: 32,0,0,192 Modules
| |||||||||||||||
| 1520 | C:\Windows\system32\Macromed\Flash\FlashPlayerUpdateService.exe -setNotifyAutoUpdate | C:\Windows\system32\Macromed\Flash\FlashPlayerUpdateService.exe | — | 4D8D4B61-8366-40E4-AD80-4F50E7E2AC27 | |||||||||||
User: admin Company: Adobe Integrity Level: HIGH Description: Adobe® Flash® Player Update Service 32.0 r0 Exit code: 0 Version: 32,0,0,192 Modules
| |||||||||||||||
| 1812 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 1860 | "C:\Users\admin\AppData\Local\Adobe\950EE43E-8831-4F28-9D72-2AD52B1A19C1\gtcheck.exe" | C:\Users\admin\AppData\Local\Adobe\950EE43E-8831-4F28-9D72-2AD52B1A19C1\gtcheck.exe | — | flashplayer32ax_ra_install[1].exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1892 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:4076 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1900 | "C:\Users\admin\AppData\Local\Adobe\950EE43E-8831-4F28-9D72-2AD52B1A19C1\gccheck_small.exe" -canOfferReactivation -shellMode:standard -brandCode:AFRC | C:\Users\admin\AppData\Local\Adobe\950EE43E-8831-4F28-9D72-2AD52B1A19C1\gccheck_small.exe | — | flashplayer32ax_ra_install[1].exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Pre-Install Exit code: 0 Version: 1.0 Modules
| |||||||||||||||
| 2576 | "C:\Users\admin\AppData\Local\Adobe\950EE43E-8831-4F28-9D72-2AD52B1A19C1\50B9A6D2-E1BA-4023-808D-1ABCE0BFF518\4D8D4B61-8366-40E4-AD80-4F50E7E2AC27" -install -iv 8 -au 1 | C:\Users\admin\AppData\Local\Adobe\950EE43E-8831-4F28-9D72-2AD52B1A19C1\50B9A6D2-E1BA-4023-808D-1ABCE0BFF518\4D8D4B61-8366-40E4-AD80-4F50E7E2AC27 | flashplayer32ax_ra_install[1].exe | ||||||||||||
User: admin Company: Adobe Integrity Level: HIGH Description: Adobe® Flash® Player Installer/Uninstaller 32.0 r0 Exit code: 3 Version: 32,0,0,192 Modules
| |||||||||||||||
Total events
2 710
Read events
2 055
Write events
491
Delete events
164
Modification events
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {06871909-76F1-11E9-A09E-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307050003000F00090008002700BC01 | |||
Executable files
12
Suspicious files
10
Text files
177
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1088 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@bing[2].txt | — | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFC5E71333000664DB.TMP | — | |
MD5:— | SHA256:— | |||
| 1088 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\1803SA0H\search[1].txt | — | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1088 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012019051520190516\index.dat | dat | |
MD5:— | SHA256:— | |||
| 1088 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\MSIMGSIZ.DAT | smt | |
MD5:— | SHA256:— | |||
| 1088 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\POOSVBPM\cc8437ad[1].js | — | |
MD5:— | SHA256:— | |||
| 1088 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
75
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1088 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/sa/simg/SharedSpriteDesktopRewards_022118.png | US | image | 5.73 Kb | whitelisted |
1088 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rb/5n/cj,nj/c44ec255/9a358300.js?bu=Eq0fzB_wHvUe4wSDH4Uf2B-HH44fmR_EH8Ifth-jHqwdrx2mHg | US | text | 4.95 Kb | whitelisted |
1088 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/search?q=adobe+flsdhplayer&src=IE-SearchBox&FORM=IE8SRC | US | html | 36.9 Kb | whitelisted |
1088 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/6q/4N/cj,nj/347afee2/33036ea1.js | US | text | 1.77 Kb | whitelisted |
1088 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/fd/ls/l?IG=EBAF39316088469E89B66EDC3C52C015&CID=0425E5ADAD1F6CC809C7E8F0ACD56D28&Type=Event.CPT&DATA={"pp":{"S":"L","FC":129,"BC":209,"SE":-1,"TC":-1,"H":287,"BP":365,"CT":381,"IL":3},"ad":[164,82,772,444,1089,498,0]}&P=SERP&DA=DUB02 | US | image | 5.73 Kb | whitelisted |
1088 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/fd/ls/l?IG=EBAF39316088469E89B66EDC3C52C015&CID=0425E5ADAD1F6CC809C7E8F0ACD56D28&Type=Event.ClientInst&DATA=[{"T":"CI.GetError","FID":"CI","Name":"JSGetError","Text":"%27SVGElement%27%20is%20undefined","Meta":"http%3A//www.bing.com/search%3Fq%3Dadobe+flsdhplayer%26src%3DIE-SearchBox%26FORM%3DIE8SRC","Line":9731743,"Char":%20undefined}] | US | compressed | 181 b | whitelisted |
1088 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rb/16/cj,nj/1b7dfb88/cc8437ad.js?bu=DikuX29zd2tjZ68BswEuowEu | US | text | 7.54 Kb | whitelisted |
1088 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/5e/2p/cj,nj/8bb625e8/37529936.js | US | text | 2.85 Kb | whitelisted |
1088 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/32/21/cj,nj/4c7364c5/40e1b425.js | US | text | 816 b | whitelisted |
1088 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/5n/1nw/cj,nj/e90431ed/b2fe50be.js | US | text | 171 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3336 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1088 | iexplore.exe | 192.147.130.63:443 | get.adobe.com | Adobe Systems Inc. | US | whitelisted |
1088 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
1088 | iexplore.exe | 2.16.123.22:443 | wwwimages2.adobe.com | Akamai International B.V. | — | whitelisted |
1088 | iexplore.exe | 65.52.7.224:80 | 5b3c6d009643ee5d830d0002a089f09c.clo.footprintdns.com | Microsoft Corporation | US | whitelisted |
1088 | iexplore.exe | 65.55.163.90:443 | login.live.com | Microsoft Corporation | US | unknown |
1088 | iexplore.exe | 2.20.160.99:443 | p.typekit.net | Akamai Technologies, Inc. | — | whitelisted |
1088 | iexplore.exe | 204.79.197.222:80 | e25ad161165f1be2e25b8353d58ce8bc.clo.footprintdns.com | Microsoft Corporation | US | whitelisted |
1088 | iexplore.exe | 184.51.8.204:443 | get3.adobe.com | Akamai Technologies, Inc. | US | whitelisted |
1088 | iexplore.exe | 23.38.53.224:443 | static-fonts.adobe.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
7a6aa7eead06b11d8c9098bb3330b189.clo.footprintdns.com |
| unknown |
5b3c6d009643ee5d830d0002a089f09c.clo.footprintdns.com |
| unknown |
e25ad161165f1be2e25b8353d58ce8bc.clo.footprintdns.com |
| suspicious |
fp.msedge.net |
| whitelisted |
get.adobe.com |
| whitelisted |
wwwimages2.adobe.com |
| whitelisted |
fonts.adobe.com |
| whitelisted |
assets.adobedtm.com |
| whitelisted |