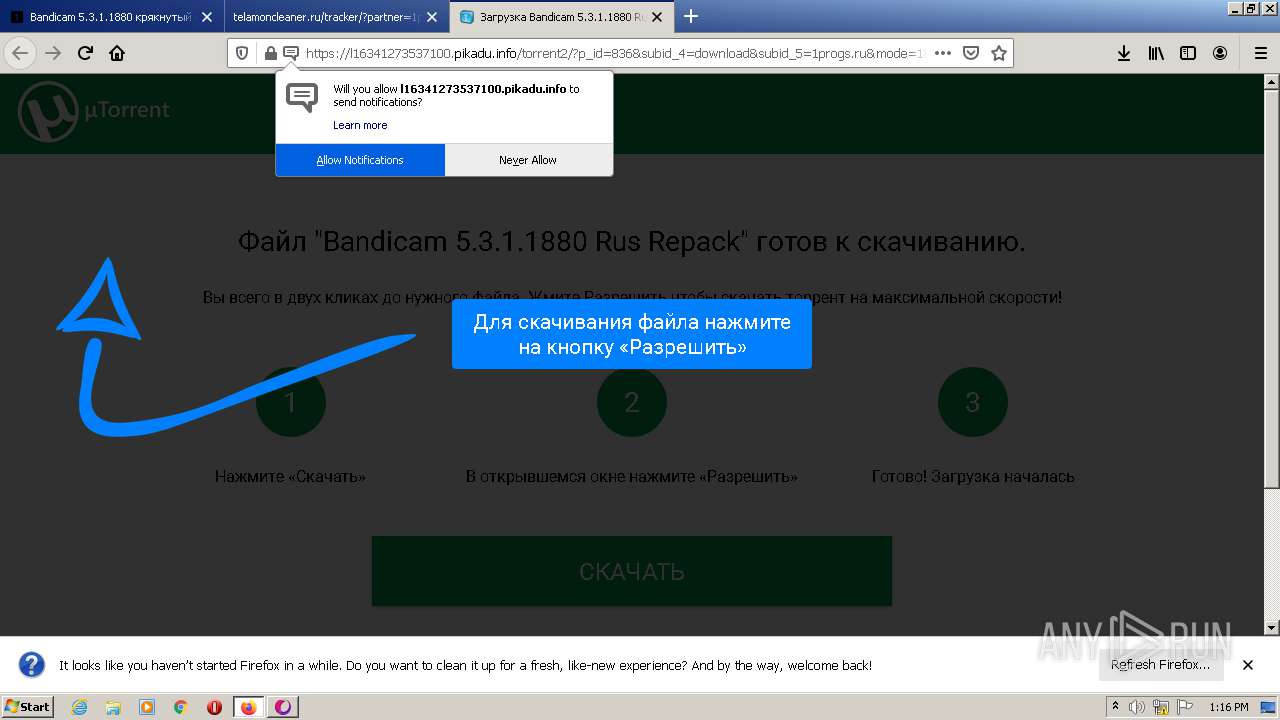
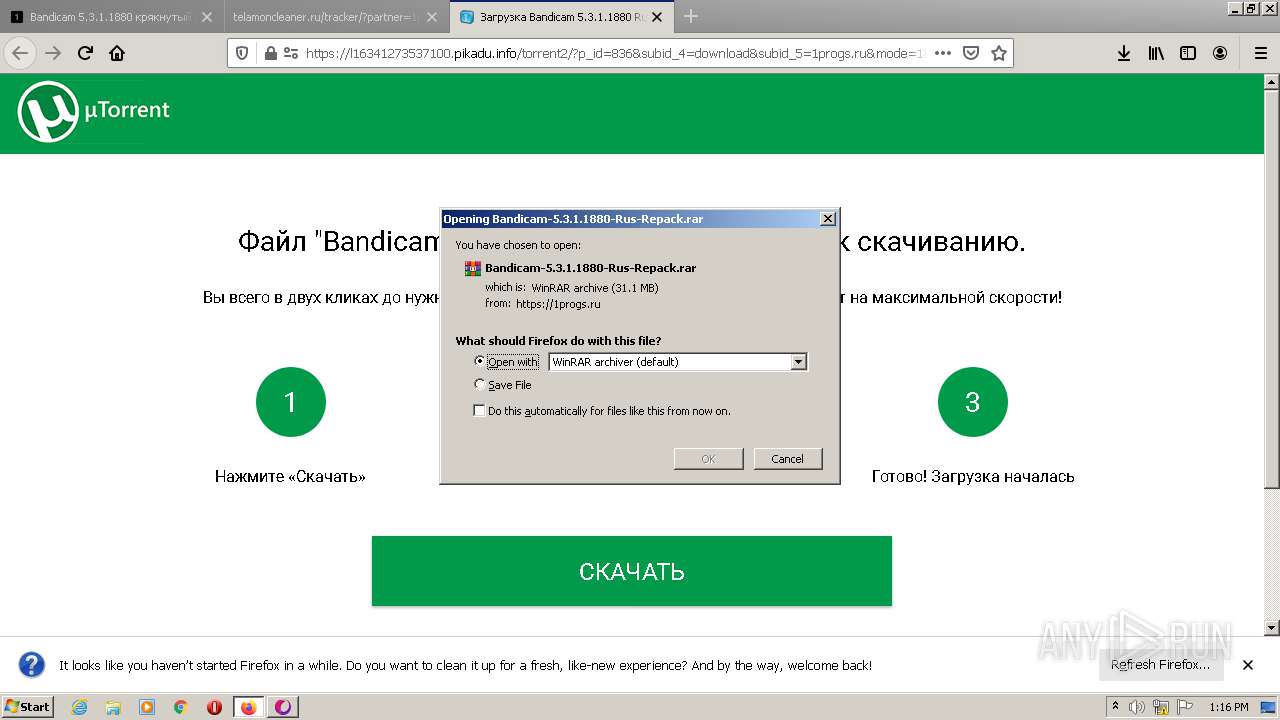
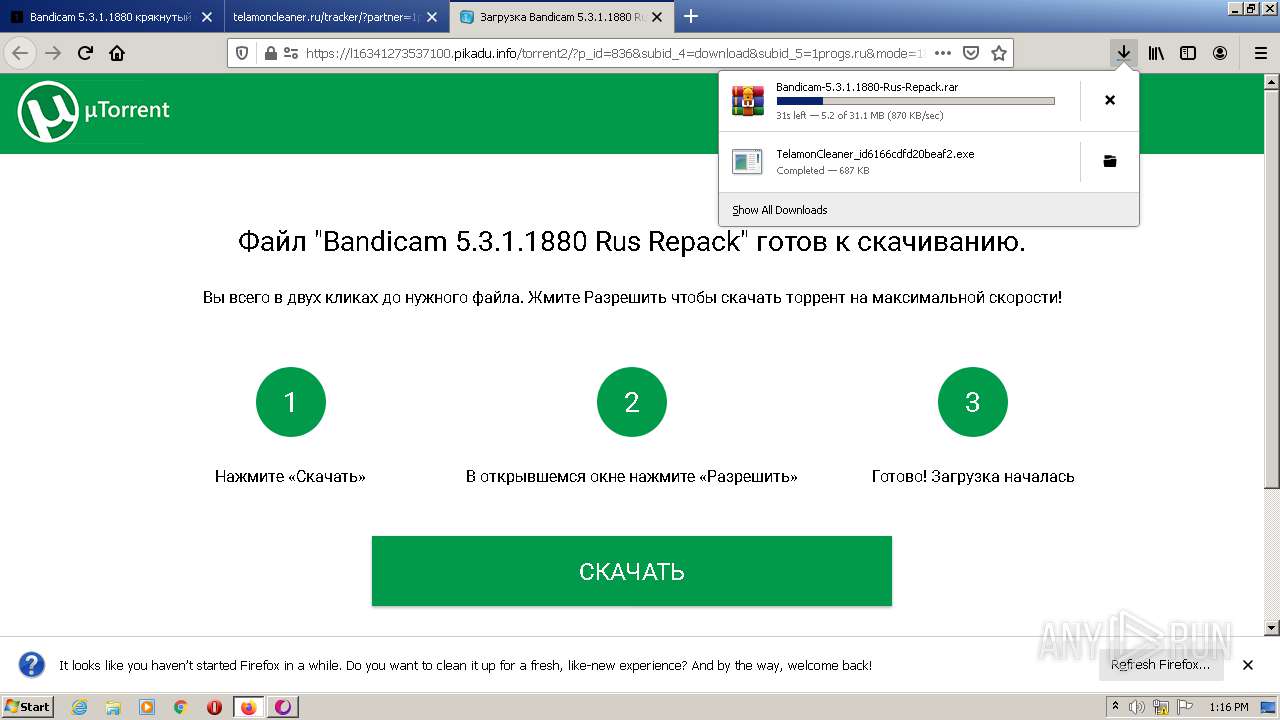
| URL: | https://1progs.ru/bandicam-polnaya-versiya-crack/ |
| Full analysis: | https://app.any.run/tasks/45d0a337-712e-48f7-ac3e-bff0d0353714 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | October 13, 2021, 12:15:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 07B9167E4648651FB995C5BC28616824 |
| SHA1: | A3A9C7A897A75F9DD2941ED529C236CDDB67F371 |
| SHA256: | 556241E222A20709AB78A15CAB81997FBE521C29AC8C3C00752EC71767636A9A |
| SSDEEP: | 3:N8+aCMv7ff4QXN:2+aCa7ffxN |
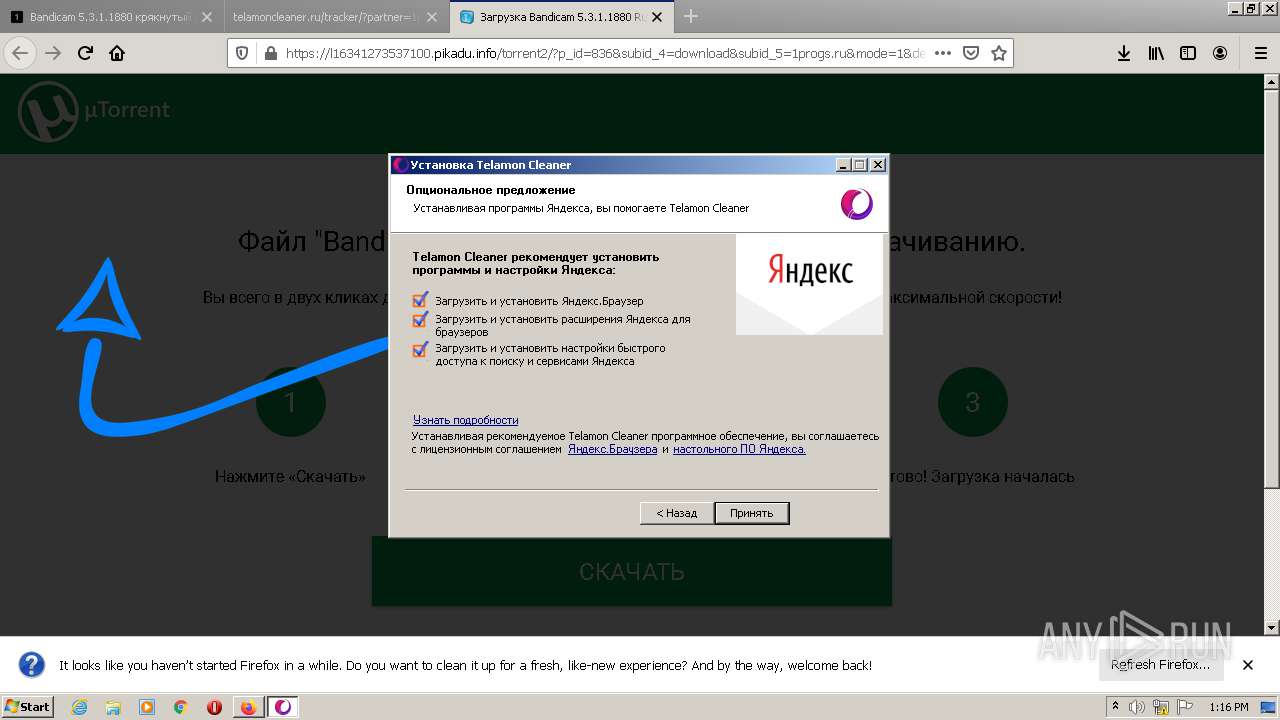
MALICIOUS
Application was dropped or rewritten from another process
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2516)
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
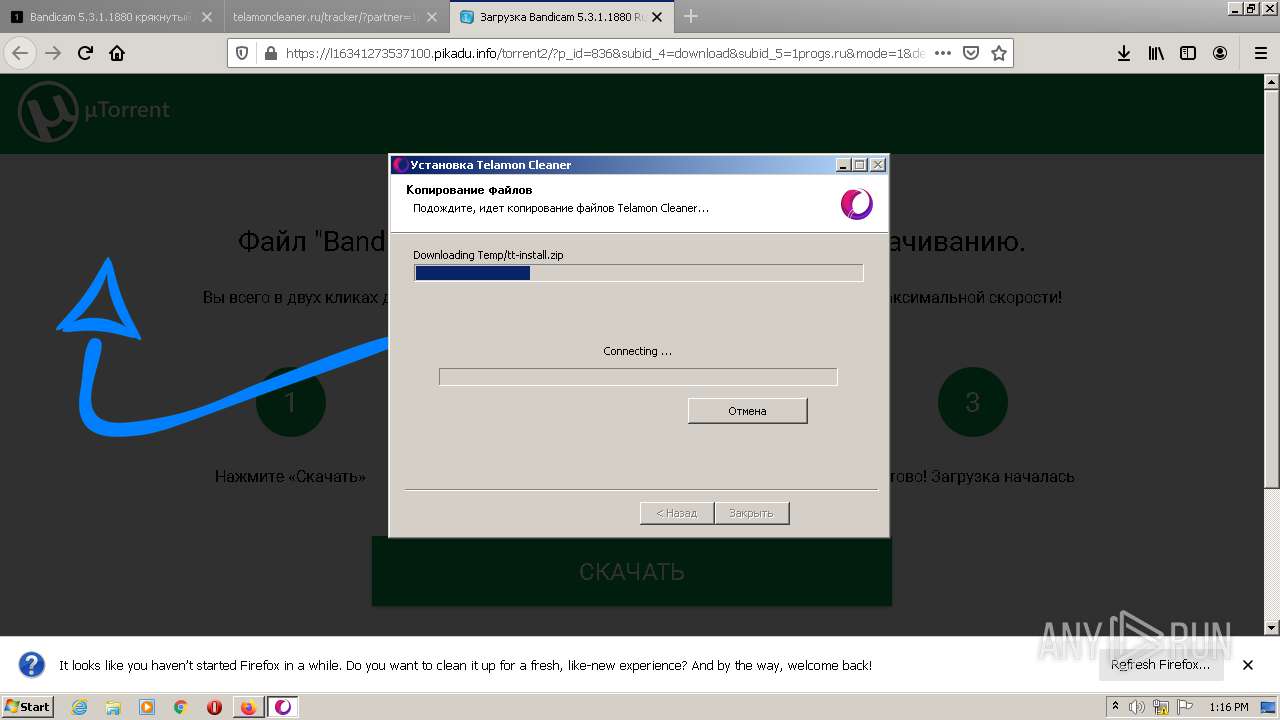
- tt-installer-helper.exe (PID: 2980)
- tt-installer-helper.exe (PID: 2652)
- Bandicam.5.3.1.1880.exe (PID: 2552)
- Bandicam.5.3.1.1880.exe (PID: 3448)
- tt-installer-helper.exe (PID: 3384)
- tt-cleaner.exe (PID: 116)
- downloader.exe (PID: 2372)
- tt-cleaner.exe (PID: 4004)
- downloader.exe (PID: 1104)
- YandexPackSetup.exe (PID: 4084)
- QtWebEngineProcess.exe (PID: 412)
- sender.exe (PID: 4532)
- seederexe.exe (PID: 4408)
- Yandex.exe (PID: 5572)
- lite_installer.exe (PID: 3240)
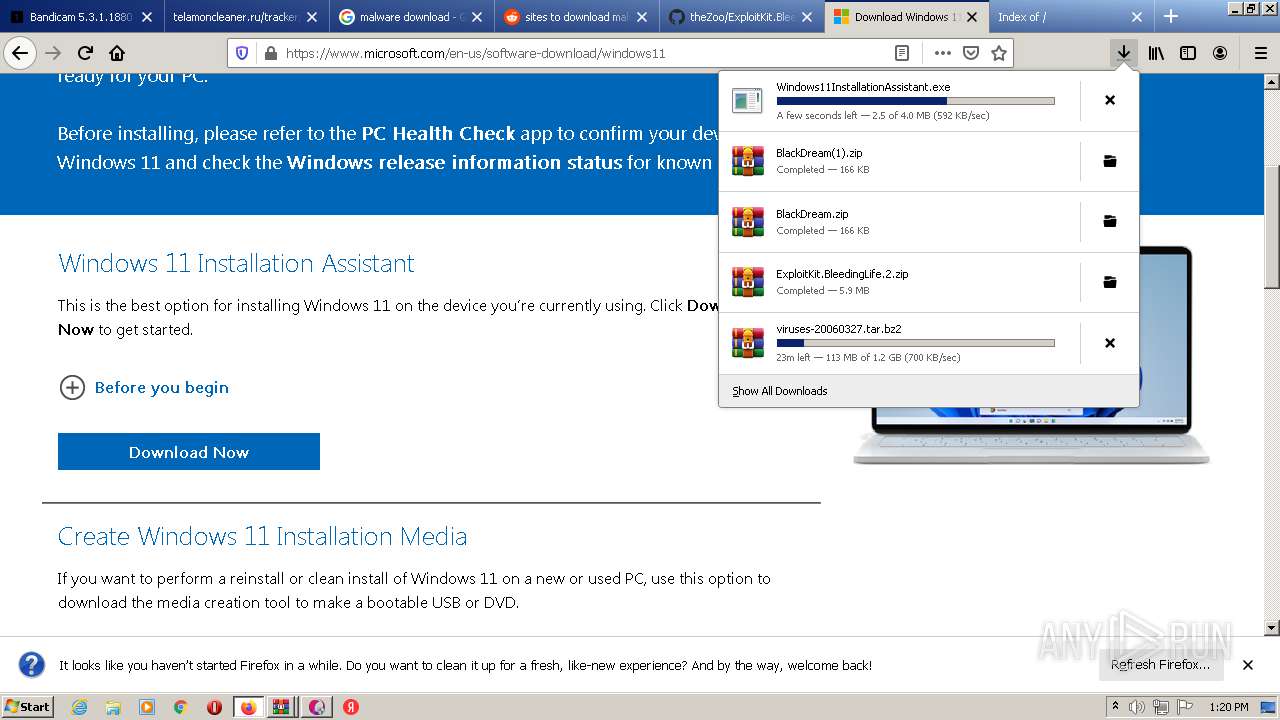
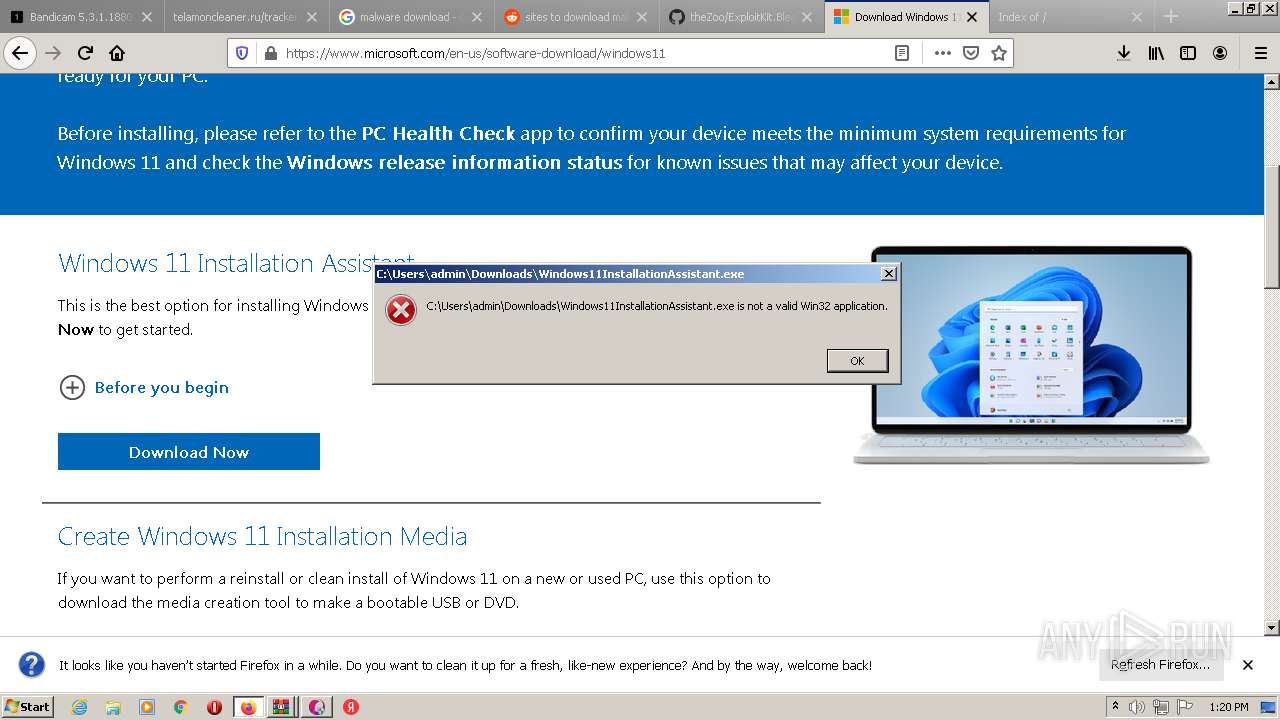
- Windows11InstallationAssistant.exe (PID: 5716)
Drops executable file immediately after starts
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
- Bandicam.5.3.1.1880.exe (PID: 2552)
- Bandicam.5.3.1.1880.tmp (PID: 1988)
Loads dropped or rewritten executable
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
- tt-cleaner.exe (PID: 116)
- tt-cleaner.exe (PID: 4004)
- QtWebEngineProcess.exe (PID: 412)
Changes settings of System certificates
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
- downloader.exe (PID: 2372)
Uses Task Scheduler to run other applications
- tt-cleaner.exe (PID: 116)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3056)
- tt-cleaner.exe (PID: 4004)
Actions looks like stealing of personal data
- tt-cleaner.exe (PID: 4004)
- lite_installer.exe (PID: 3240)
- seederexe.exe (PID: 4408)
Steals credentials from Web Browsers
- seederexe.exe (PID: 4408)
- tt-cleaner.exe (PID: 4004)
Disables Windows Defender
- tt-cleaner.exe (PID: 4004)
Changes Windows auto-update feature
- tt-cleaner.exe (PID: 4004)
SUSPICIOUS
Reads the computer name
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
- tt-installer-helper.exe (PID: 2980)
- WinRAR.exe (PID: 3544)
- Bandicam.5.3.1.1880.tmp (PID: 1988)
- downloader.exe (PID: 2372)
- tt-cleaner.exe (PID: 116)
- tt-cleaner.exe (PID: 4004)
- YandexPackSetup.exe (PID: 4084)
- lite_installer.exe (PID: 3240)
- seederexe.exe (PID: 4408)
- downloader.exe (PID: 1104)
- Yandex.exe (PID: 5572)
- sender.exe (PID: 4532)
- WinRAR.exe (PID: 5372)
- WinRAR.exe (PID: 4284)
Drops a file that was compiled in debug mode
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
- Bandicam.5.3.1.1880.tmp (PID: 1988)
- downloader.exe (PID: 2372)
- msiexec.exe (PID: 3788)
- MsiExec.exe (PID: 2560)
- lite_installer.exe (PID: 3240)
- firefox.exe (PID: 4060)
Executable content was dropped or overwritten
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
- firefox.exe (PID: 4060)
- WinRAR.exe (PID: 3544)
- Bandicam.5.3.1.1880.exe (PID: 2552)
- Bandicam.5.3.1.1880.tmp (PID: 1988)
- downloader.exe (PID: 2372)
- msiexec.exe (PID: 3788)
- MsiExec.exe (PID: 2560)
- lite_installer.exe (PID: 3240)
Starts application with an unusual extension
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
Checks supported languages
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
- ns7A27.tmp (PID: 3176)
- tt-installer-helper.exe (PID: 2980)
- ns7CF7.tmp (PID: 2620)
- tt-installer-helper.exe (PID: 2652)
- WinRAR.exe (PID: 3544)
- Bandicam.5.3.1.1880.exe (PID: 2552)
- Bandicam.5.3.1.1880.tmp (PID: 1988)
- nsD804.tmp (PID: 3296)
- tt-installer-helper.exe (PID: 3384)
- tt-cleaner.exe (PID: 116)
- downloader.exe (PID: 2372)
- tt-cleaner.exe (PID: 4004)
- YandexPackSetup.exe (PID: 4084)
- downloader.exe (PID: 1104)
- QtWebEngineProcess.exe (PID: 412)
- lite_installer.exe (PID: 3240)
- seederexe.exe (PID: 4408)
- Yandex.exe (PID: 5572)
- sender.exe (PID: 4532)
- WinRAR.exe (PID: 4284)
- WinRAR.exe (PID: 5372)
Drops a file with a compile date too recent
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
- lite_installer.exe (PID: 3240)
Creates a directory in Program Files
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
- tt-cleaner.exe (PID: 116)
- tt-cleaner.exe (PID: 4004)
Adds / modifies Windows certificates
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
- downloader.exe (PID: 2372)
Drops a file with too old compile date
- WinRAR.exe (PID: 3544)
- Bandicam.5.3.1.1880.exe (PID: 2552)
- Bandicam.5.3.1.1880.tmp (PID: 1988)
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
- firefox.exe (PID: 4060)
Reads the Windows organization settings
- Bandicam.5.3.1.1880.tmp (PID: 1988)
- msiexec.exe (PID: 3788)
Reads Windows owner or organization settings
- Bandicam.5.3.1.1880.tmp (PID: 1988)
- msiexec.exe (PID: 3788)
Reads Environment values
- Bandicam.5.3.1.1880.tmp (PID: 1988)
- MsiExec.exe (PID: 2560)
Creates files in the program directory
- tt-cleaner.exe (PID: 116)
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
- tt-cleaner.exe (PID: 4004)
- regedit.exe (PID: 5772)
- regedit.exe (PID: 5876)
- regedit.exe (PID: 6132)
- regedit.exe (PID: 5984)
- regedit.exe (PID: 4228)
- regedit.exe (PID: 4692)
- regedit.exe (PID: 4504)
- regedit.exe (PID: 4716)
- regedit.exe (PID: 2424)
- regedit.exe (PID: 4944)
- regedit.exe (PID: 1268)
- regedit.exe (PID: 5216)
- regedit.exe (PID: 5472)
- regedit.exe (PID: 5388)
- regedit.exe (PID: 5612)
- regedit.exe (PID: 5792)
- regedit.exe (PID: 5924)
- regedit.exe (PID: 6008)
- regedit.exe (PID: 6128)
- regedit.exe (PID: 4344)
- regedit.exe (PID: 4588)
- regedit.exe (PID: 4796)
- regedit.exe (PID: 4000)
- regedit.exe (PID: 3212)
- regedit.exe (PID: 5276)
- regedit.exe (PID: 5140)
- regedit.exe (PID: 4736)
Reads the date of Windows installation
- tt-cleaner.exe (PID: 116)
- Yandex.exe (PID: 5572)
Creates files in the user directory
- tt-cleaner.exe (PID: 116)
- MsiExec.exe (PID: 2560)
- seederexe.exe (PID: 4408)
- Yandex.exe (PID: 5572)
Creates a software uninstall entry
- tt-cleaner.exe (PID: 116)
- Yandex.exe (PID: 5572)
Application launched itself
- tt-cleaner.exe (PID: 116)
- downloader.exe (PID: 2372)
- msiexec.exe (PID: 3788)
Executed as Windows Service
- msiexec.exe (PID: 3788)
Changes the started page of IE
- seederexe.exe (PID: 4408)
Searches for installed software
- seederexe.exe (PID: 4408)
- tt-cleaner.exe (PID: 4004)
Reads default file associations for system extensions
- Yandex.exe (PID: 5572)
INFO
Checks supported languages
- firefox.exe (PID: 3948)
- firefox.exe (PID: 3008)
- firefox.exe (PID: 1776)
- firefox.exe (PID: 4060)
- firefox.exe (PID: 1200)
- firefox.exe (PID: 4012)
- firefox.exe (PID: 3732)
- firefox.exe (PID: 1208)
- firefox.exe (PID: 1492)
- firefox.exe (PID: 3184)
- firefox.exe (PID: 2960)
- firefox.exe (PID: 2184)
- firefox.exe (PID: 2252)
- schtasks.exe (PID: 3056)
- firefox.exe (PID: 3480)
- msiexec.exe (PID: 3788)
- MsiExec.exe (PID: 2560)
- firefox.exe (PID: 712)
- firefox.exe (PID: 5728)
- regedit.exe (PID: 5664)
- regedit.exe (PID: 5772)
- regedit.exe (PID: 5876)
- regedit.exe (PID: 6132)
- regedit.exe (PID: 4228)
- regedit.exe (PID: 5984)
- regedit.exe (PID: 4504)
- regedit.exe (PID: 4692)
- regedit.exe (PID: 4716)
- regedit.exe (PID: 2424)
- regedit.exe (PID: 1268)
- regedit.exe (PID: 4944)
- regedit.exe (PID: 5388)
- regedit.exe (PID: 5216)
- regedit.exe (PID: 5472)
- regedit.exe (PID: 5612)
- regedit.exe (PID: 5792)
- regedit.exe (PID: 5924)
- regedit.exe (PID: 6008)
- regedit.exe (PID: 4344)
- regedit.exe (PID: 6128)
- regedit.exe (PID: 4588)
- regedit.exe (PID: 4796)
- regedit.exe (PID: 4736)
- regedit.exe (PID: 4000)
- regedit.exe (PID: 3212)
- regedit.exe (PID: 5140)
- regedit.exe (PID: 5276)
Reads the computer name
- firefox.exe (PID: 4060)
- firefox.exe (PID: 3008)
- firefox.exe (PID: 1200)
- firefox.exe (PID: 3732)
- firefox.exe (PID: 1776)
- firefox.exe (PID: 4012)
- firefox.exe (PID: 1208)
- firefox.exe (PID: 1492)
- firefox.exe (PID: 3184)
- firefox.exe (PID: 2960)
- firefox.exe (PID: 2184)
- firefox.exe (PID: 2252)
- schtasks.exe (PID: 3056)
- firefox.exe (PID: 3480)
- msiexec.exe (PID: 3788)
- MsiExec.exe (PID: 2560)
- firefox.exe (PID: 712)
- firefox.exe (PID: 5728)
Application launched itself
- firefox.exe (PID: 3948)
- firefox.exe (PID: 4060)
Creates files in the program directory
- firefox.exe (PID: 4060)
Reads CPU info
- firefox.exe (PID: 4060)
Reads settings of System Certificates
- firefox.exe (PID: 4060)
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
- downloader.exe (PID: 2372)
- msiexec.exe (PID: 3788)
Checks Windows Trust Settings
- firefox.exe (PID: 4060)
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
- downloader.exe (PID: 2372)
- msiexec.exe (PID: 3788)
- lite_installer.exe (PID: 3240)
Creates files in the user directory
- firefox.exe (PID: 4060)
Dropped object may contain Bitcoin addresses
- firefox.exe (PID: 4060)
- TelamonCleaner_id6166cdfd20beaf2.exe (PID: 2424)
Reads the date of Windows installation
- firefox.exe (PID: 4060)
Manual execution by user
- WinRAR.exe (PID: 3544)
- WinRAR.exe (PID: 4284)
- WinRAR.exe (PID: 5372)
Loads dropped or rewritten executable
- Bandicam.5.3.1.1880.tmp (PID: 1988)
Application was dropped or rewritten from another process
- Bandicam.5.3.1.1880.tmp (PID: 1988)
Reads the hosts file
- tt-cleaner.exe (PID: 4004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
125
Monitored processes
72
Malicious processes
13
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Telamon Cleaner\tt-cleaner.exe" --install --l=t | C:\Program Files\Telamon Cleaner\tt-cleaner.exe | TelamonCleaner_id6166cdfd20beaf2.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 412 | "C:\Program Files\Telamon Cleaner\QtWebEngineProcess.exe" --type=renderer --no-sandbox --disable-gpu-memory-buffer-video-frames --enable-threaded-compositing --enable-features=AllowContentInitiatedDataUrlNavigations,TracingServiceInProcess --disable-features=BackgroundFetch,BlinkGenPropertyTrees,MojoVideoCapture,NetworkServiceNotSupported,OriginTrials,SmsReceiver,UsePdfCompositorServiceForPrint,UseSurfaceLayerForVideo,VizDisplayCompositor,WebAuthentication,WebAuthenticationCable,WebPayments,WebUSB --disable-gpu-compositing --lang=en-US --webengine-schemes=qrc:sLV --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9663699920617863324 --renderer-client-id=2 --mojo-platform-channel-handle=1600 /prefetch:1 | C:\Program Files\Telamon Cleaner\QtWebEngineProcess.exe | — | tt-cleaner.exe | |||||||||||
User: admin Company: The Qt Company Ltd. Integrity Level: HIGH Description: Qt Qtwebengineprocess Exit code: 0 Version: 5.14.0.0 Modules
| |||||||||||||||
| 712 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4060.83.1324388935\625370998" -childID 12 -isForBrowser -prefsHandle 6140 -prefMapHandle 7788 -prefsLen 9654 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 4060 "\\.\pipe\gecko-crash-server-pipe.4060" 6084 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1104 | C:\Users\admin\AppData\Local\Temp\nsa791D.tmp\downloader.exe --stat dwnldr/p=19568/cnt=0/dt=5/ct=1/rt=0 --dh 1416 --st 1634127460 | C:\Users\admin\AppData\Local\Temp\nsa791D.tmp\downloader.exe | downloader.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup Downloader Exit code: 0 Version: 0.1.0.32 Modules
| |||||||||||||||
| 1200 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4060.6.1043080404\515274368" -childID 1 -isForBrowser -prefsHandle 2796 -prefMapHandle 2792 -prefsLen 245 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 4060 "\\.\pipe\gecko-crash-server-pipe.4060" 2808 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1208 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4060.22.1799312795\1277640531" -childID 5 -isForBrowser -prefsHandle 3864 -prefMapHandle 1684 -prefsLen 7378 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 4060 "\\.\pipe\gecko-crash-server-pipe.4060" 3868 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1268 | "regedit" /s /e "C:\Program Files\Telamon Cleaner\Quarantine\2021-10-13-13-17-38\Registry\4ad53d87-295b-4f9f-a5e3-dcdd4b472f39.reg" "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDlls" | C:\Windows\regedit.exe | — | tt-cleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1492 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4060.41.297289172\2056073893" -childID 6 -isForBrowser -prefsHandle 7760 -prefMapHandle 7732 -prefsLen 8818 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 4060 "\\.\pipe\gecko-crash-server-pipe.4060" 7720 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1776 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4060.13.6396446\1212562223" -childID 2 -isForBrowser -prefsHandle 3108 -prefMapHandle 3104 -prefsLen 6644 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 4060 "\\.\pipe\gecko-crash-server-pipe.4060" 3120 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1988 | "C:\Users\admin\AppData\Local\Temp\is-R52F3.tmp\Bandicam.5.3.1.1880.tmp" /SL5="$600E8,32243398,93696,C:\Users\admin\AppData\Local\Temp\Rar$EXb3544.9301\Bandicam 5.3.1.1880 Rus Repack\Bandicam.5.3.1.1880.exe" | C:\Users\admin\AppData\Local\Temp\is-R52F3.tmp\Bandicam.5.3.1.1880.tmp | Bandicam.5.3.1.1880.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 2 Version: 51.52.0.0 Modules
| |||||||||||||||
Total events
73 988
Read events
72 933
Write events
979
Delete events
76
Modification events
| (PID) Process: | (3948) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 424D2F1CC8000000 | |||
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: C3562F1CC8000000 | |||
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|ServicesSettingsServer |
Value: https://firefox.settings.services.mozilla.com/v1 | |||
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SecurityContentSignatureRootHash |
Value: 97:E8:BA:9C:F1:2F:B3:DE:53:CC:42:A4:E6:57:7E:D6:4D:F4:93:C2:47:B4:14:FE:A0:36:81:8D:38:23:56:0E | |||
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (4060) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
114
Suspicious files
296
Text files
332
Unknown types
115
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4060 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Local\Temp\mz_etilqs_6mEpfaKLg6ABzKb | binary | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Local\Temp\mz_etilqs_zw3B5vdUsvBiJUs | binary | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\settings\main\ms-language-packs\asrouter.ftl | text | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-wal | binary | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\settings\main\ms-language-packs\asrouter.ftl.tmp | text | |
MD5:— | SHA256:— | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:994A33896BB41A278A315D0D796422B6 | SHA256:54EC50A20FFF8CC016710E49437CF6A11D3FE5EE7B28C185E4A9AAFEE2908B63 | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4060 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
69
TCP/UDP connections
243
DNS requests
370
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4060 | firefox.exe | POST | 200 | 2.16.186.33:80 | http://r3.o.lencr.org/ | unknown | der | 503 b | shared |
4060 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
4060 | firefox.exe | POST | 200 | 5.45.205.241:80 | http://yandex.ocsp-responder.com/ | RU | der | 1.48 Kb | whitelisted |
4060 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
2424 | TelamonCleaner_id6166cdfd20beaf2.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
4060 | firefox.exe | POST | 200 | 2.16.186.33:80 | http://r3.o.lencr.org/ | unknown | der | 503 b | shared |
4060 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
4060 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
2424 | TelamonCleaner_id6166cdfd20beaf2.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
2424 | TelamonCleaner_id6166cdfd20beaf2.exe | GET | 200 | 104.18.30.182:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECED7mcD26FWvlZ%2BluOA9T1P0%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4060 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | — | US | whitelisted |
— | — | 51.124.78.146:443 | — | Microsoft Corporation | GB | whitelisted |
4060 | firefox.exe | 2.16.186.33:80 | r3.o.lencr.org | Akamai International B.V. | — | whitelisted |
4060 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4060 | firefox.exe | 142.250.185.202:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
4060 | firefox.exe | 142.250.186.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
4060 | firefox.exe | 18.66.139.125:443 | content-signature-2.cdn.mozilla.net | Massachusetts Institute of Technology | US | malicious |
4060 | firefox.exe | 35.163.208.27:443 | push.services.mozilla.com | Amazon.com, Inc. | US | unknown |
4060 | firefox.exe | 52.222.236.127:443 | firefox-settings-attachments.cdn.mozilla.net | Amazon.com, Inc. | US | suspicious |
4060 | firefox.exe | 5.45.205.241:80 | yandex.ocsp-responder.com | YANDEX LLC | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
1progs.ru |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
firefox.settings.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
location.services.mozilla.com |
| whitelisted |
locprod2-elb-us-west-2.prod.mozaws.net |
| whitelisted |
r3.o.lencr.org |
| shared |
a1887.dscq.akamai.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2424 | TelamonCleaner_id6166cdfd20beaf2.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2424 | TelamonCleaner_id6166cdfd20beaf2.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2424 | TelamonCleaner_id6166cdfd20beaf2.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2424 | TelamonCleaner_id6166cdfd20beaf2.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2424 | TelamonCleaner_id6166cdfd20beaf2.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2372 | downloader.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1104 | downloader.exe | Attempted Information Leak | ET POLICY curl User-Agent Outbound |
3240 | lite_installer.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
tt-installer-helper.exe | [2021-10-13 13:16:04] E regstorage.cpp:62 [RegStorage] get<std::wstring>() RegOpenKeyEx failed. 2
|
tt-cleaner.exe | [2021-10-13 13:17:34] M log.cpp:93 Logging to C:\Program Files\Telamon Cleaner\logs\tt-cln-app-2021-10-13-13-17-34.log
|
tt-cleaner.exe | [2021-10-13 13:17:34] M main.cpp:43 Start main: "C:\Program Files\Telamon Cleaner\tt-cleaner.exe" --install --l=t thread id: 3388 process id: 116
|
tt-cleaner.exe | [2021-10-13 13:17:34] M main.cpp:44 Version: 1.0.189
|
tt-cleaner.exe | [2021-10-13 13:17:34] M main.cpp:110 Running app with options:
====================
isInstall: true
clid:
isUninstall: false
isAutorun: false
isFinishUpdate: false
prevAppId: 0
updateId:
updateDelay: 1200
updatePeriod: 1200
====================
|
tt-cleaner.exe | [2021-10-13 13:17:34] M app.cpp:470 Found installer_path: C:\Users\admin\Downloads\TelamonCleaner_id6166cdfd20beaf2.exe
|
tt-cleaner.exe | [2021-10-13 13:17:34] E regstorage.cpp:62 [RegStorage] get<std::wstring>() Cannot get size of string value: RegGetValue failed. 2
|
tt-cleaner.exe | [2021-10-13 13:17:35] M main.cpp:114 App exit code: 0
|
tt-cleaner.exe | [2021-10-13 13:17:35] M log.cpp:93 Logging to C:\Program Files\Telamon Cleaner\logs\tt-cln-app-2021-10-13-13-17-35.log
|
tt-cleaner.exe | [2021-10-13 13:17:35] M main.cpp:43 Start main: "C:\Program Files\Telamon Cleaner\tt-cleaner.exe" thread id: 576 process id: 4004
|