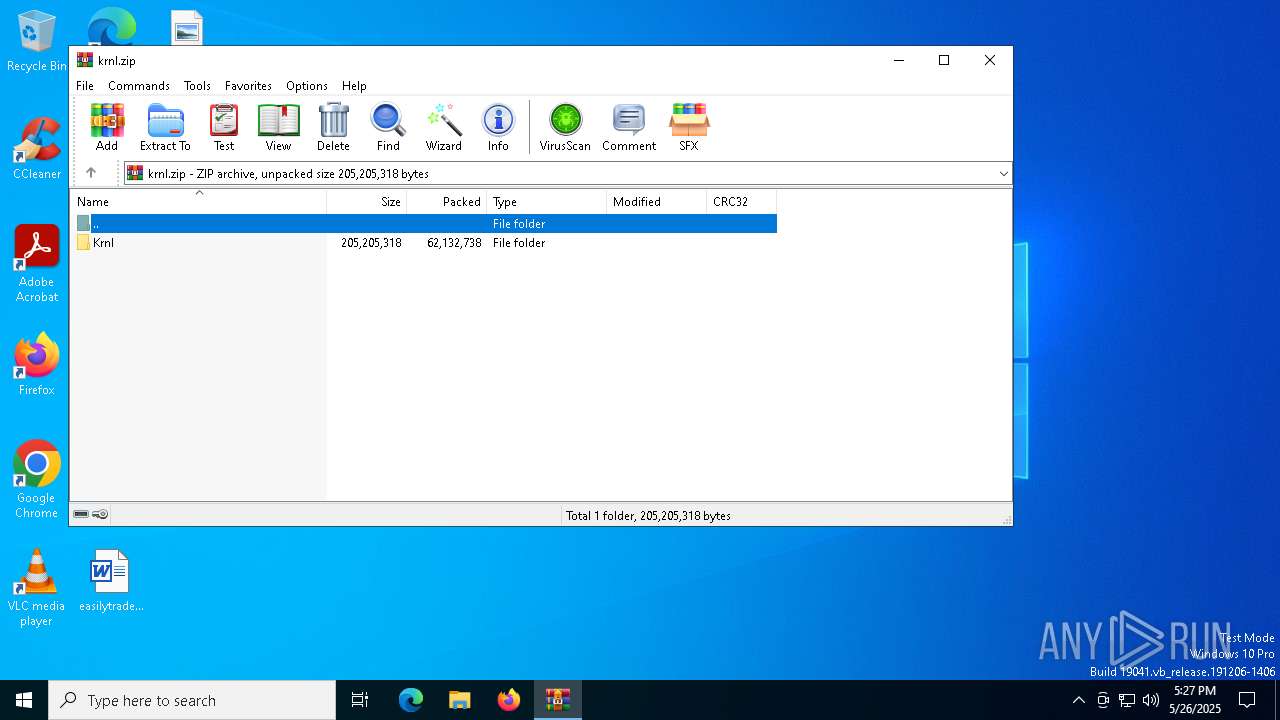
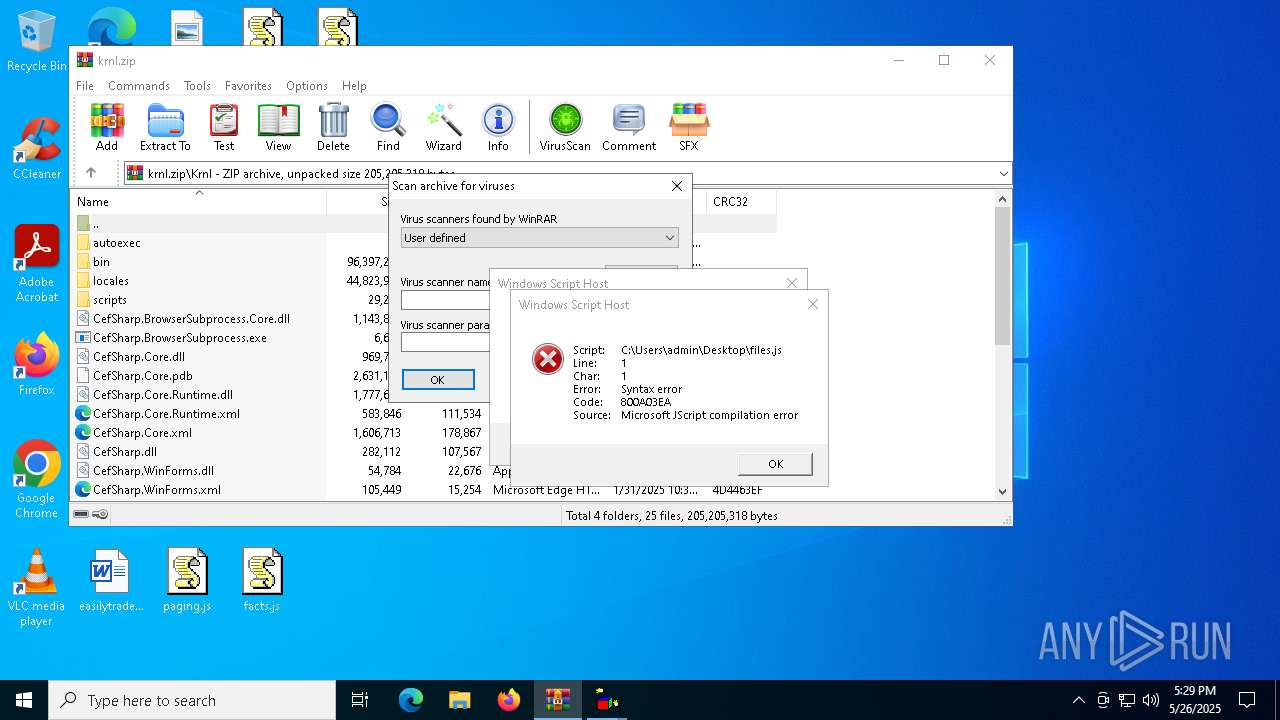
| File name: | krnl.zip |
| Full analysis: | https://app.any.run/tasks/62df36e9-c491-4049-b74d-e33bcc5fd01b |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2025, 17:26:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 22EAD08832806D07F2B4482A02D116B9 |
| SHA1: | BD8513F12DEC1830DAA0A35E33E142DB28781528 |
| SHA256: | 5550DA19F71401736EDA3E18EC93A4E1B3449946BE017FF41749E77AFE6EF5A6 |
| SSDEEP: | 1572864:qWipELgw/3f9+X6LaUgPasEdSDwL60W2i/HS:qWyix/TanSsE5L60Wh/S |
MALICIOUS
GENERIC has been found (auto)
- WinRAR.exe (PID: 7532)
SUSPICIOUS
No suspicious indicators.INFO
Manual execution by a user
- wscript.exe (PID: 7664)
- wscript.exe (PID: 7704)
- wscript.exe (PID: 7992)
- wscript.exe (PID: 7744)
- wscript.exe (PID: 8088)
- wscript.exe (PID: 7792)
- wscript.exe (PID: 7900)
- wscript.exe (PID: 7860)
- wscript.exe (PID: 7952)
- wscript.exe (PID: 8040)
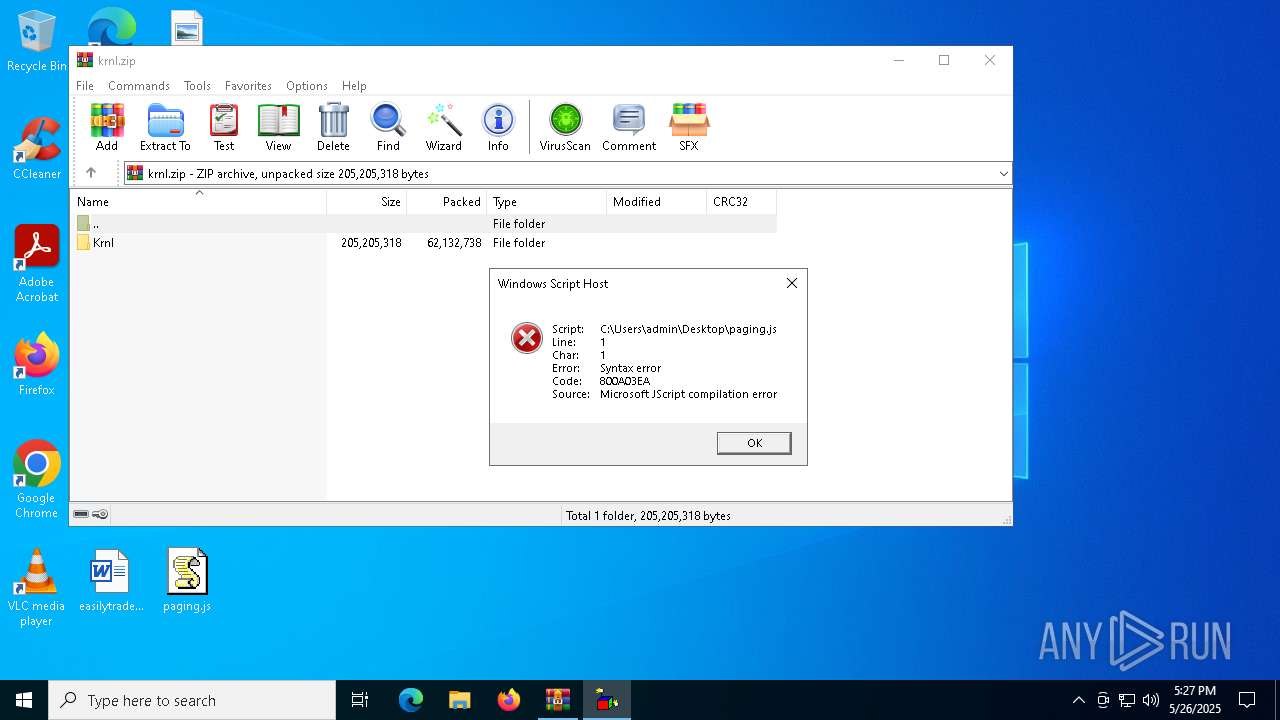
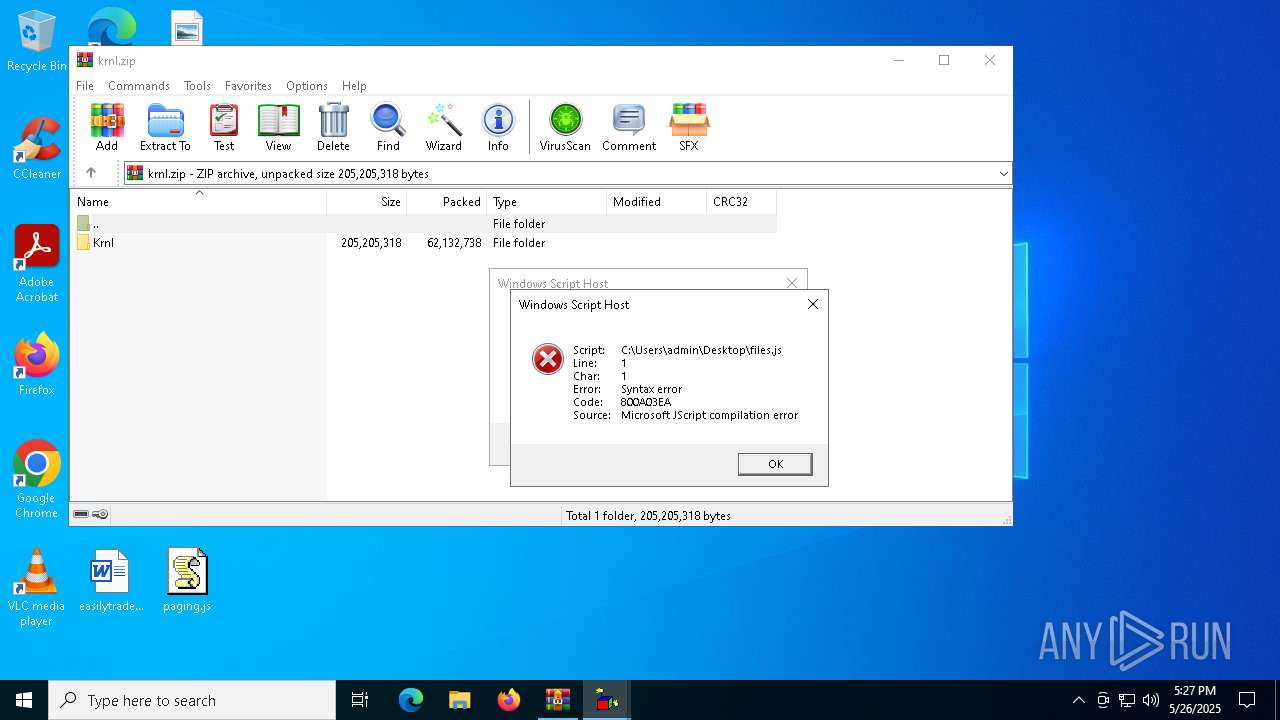
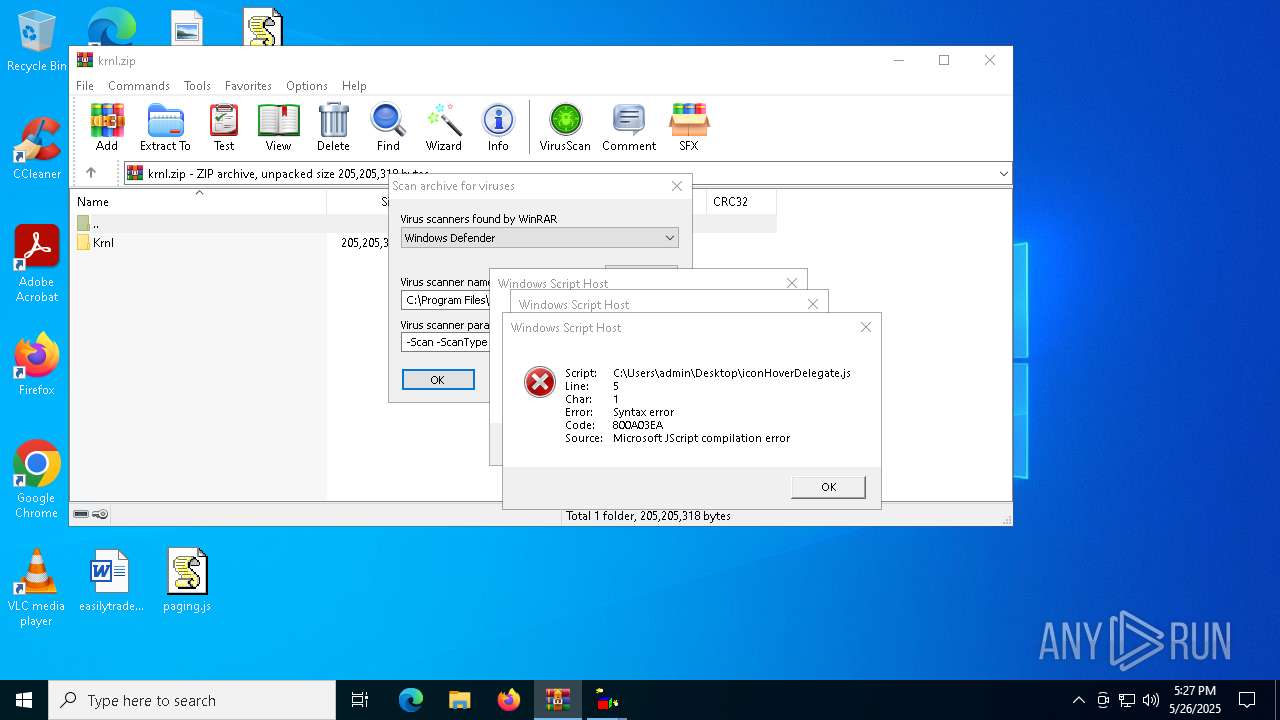
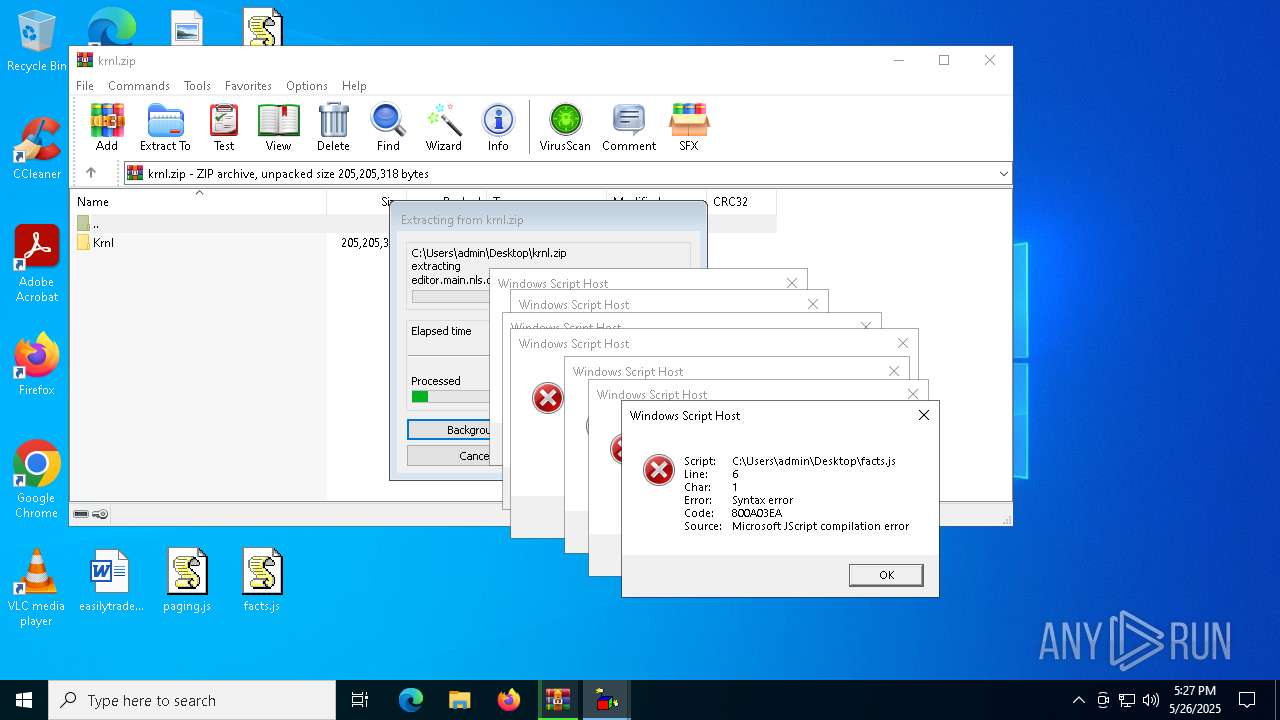
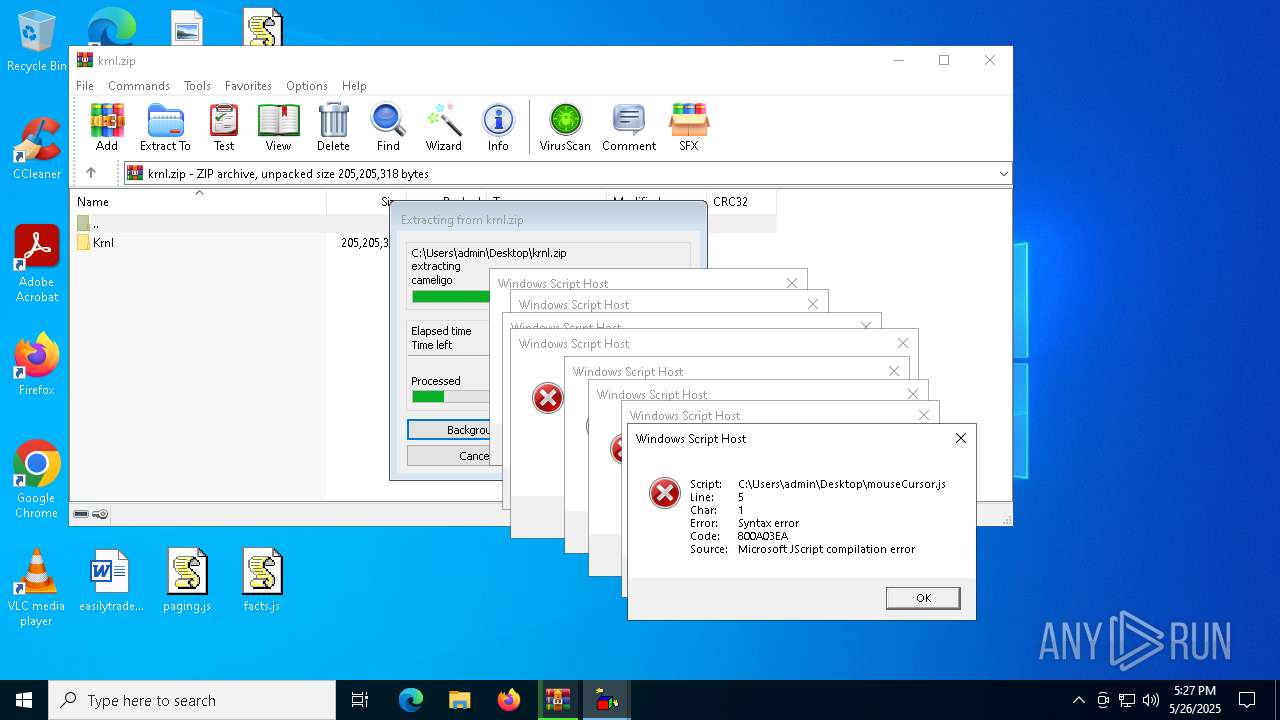
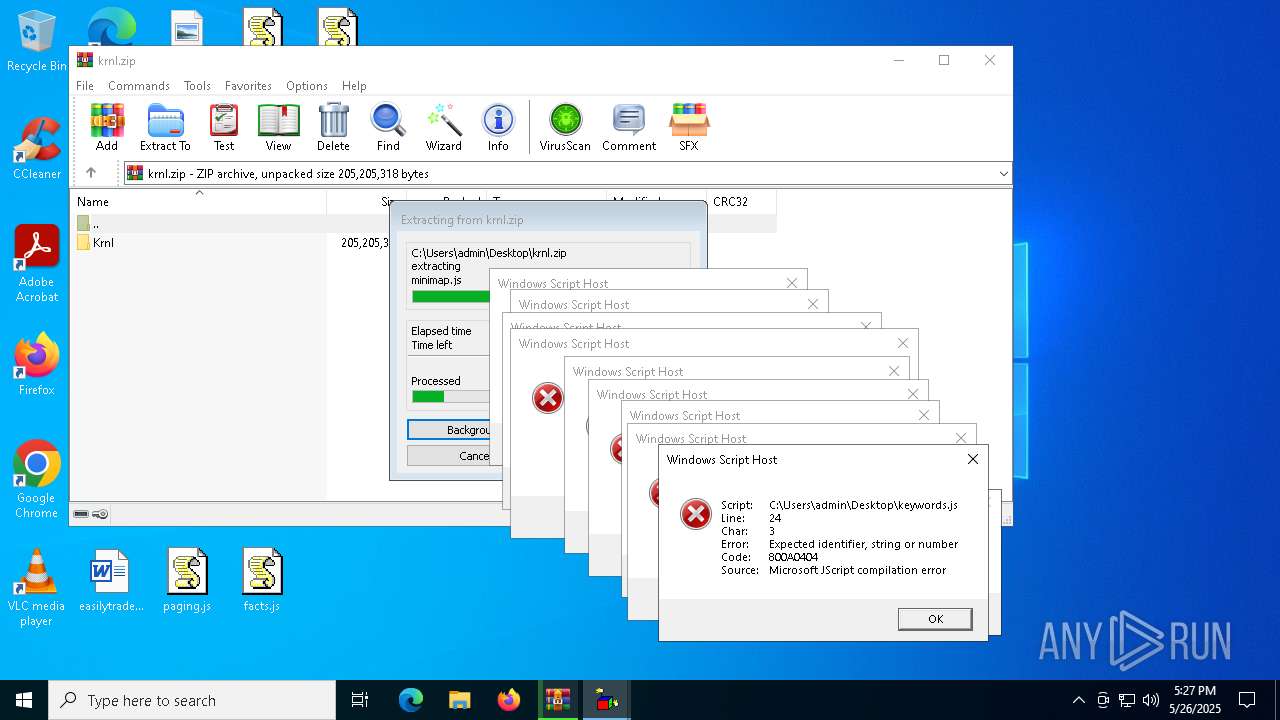
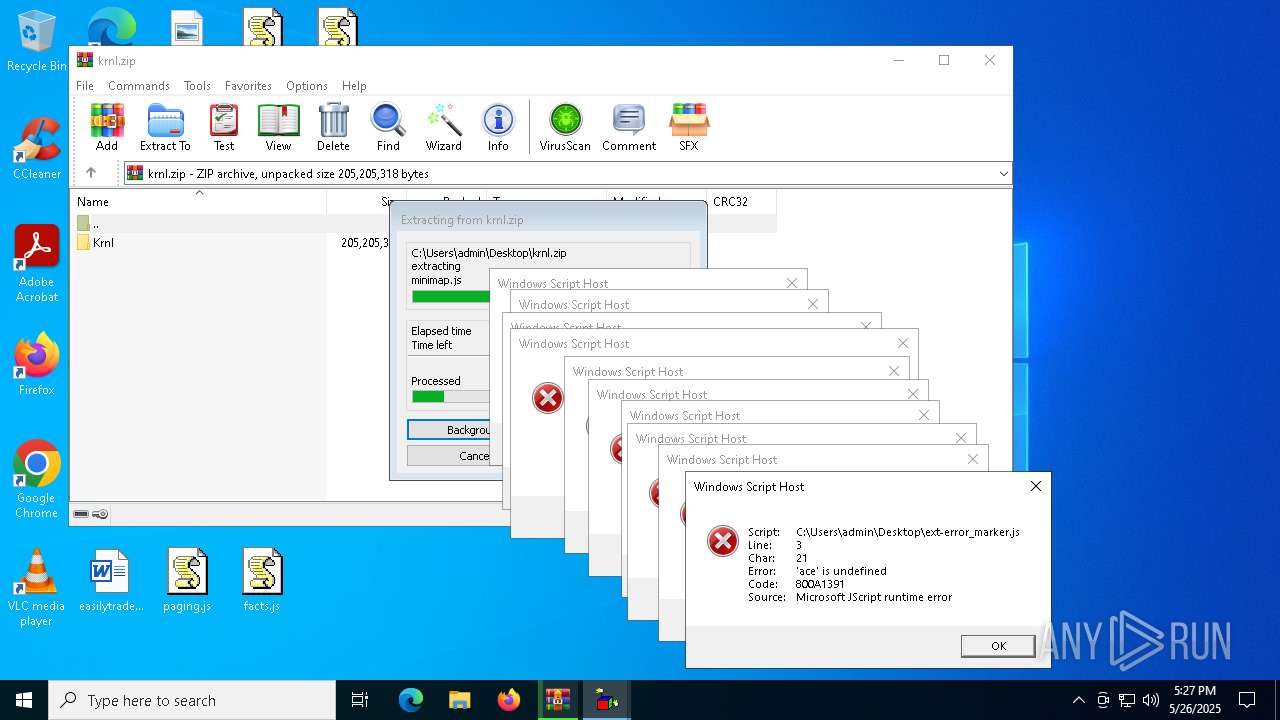
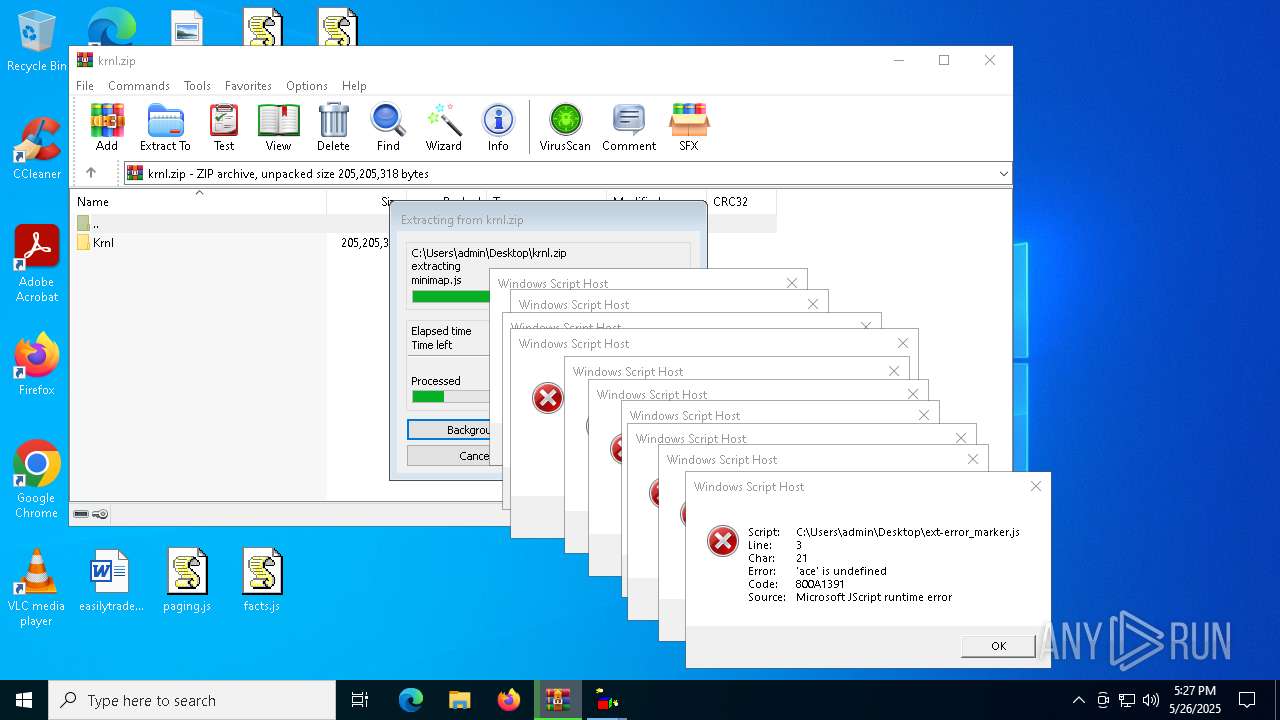
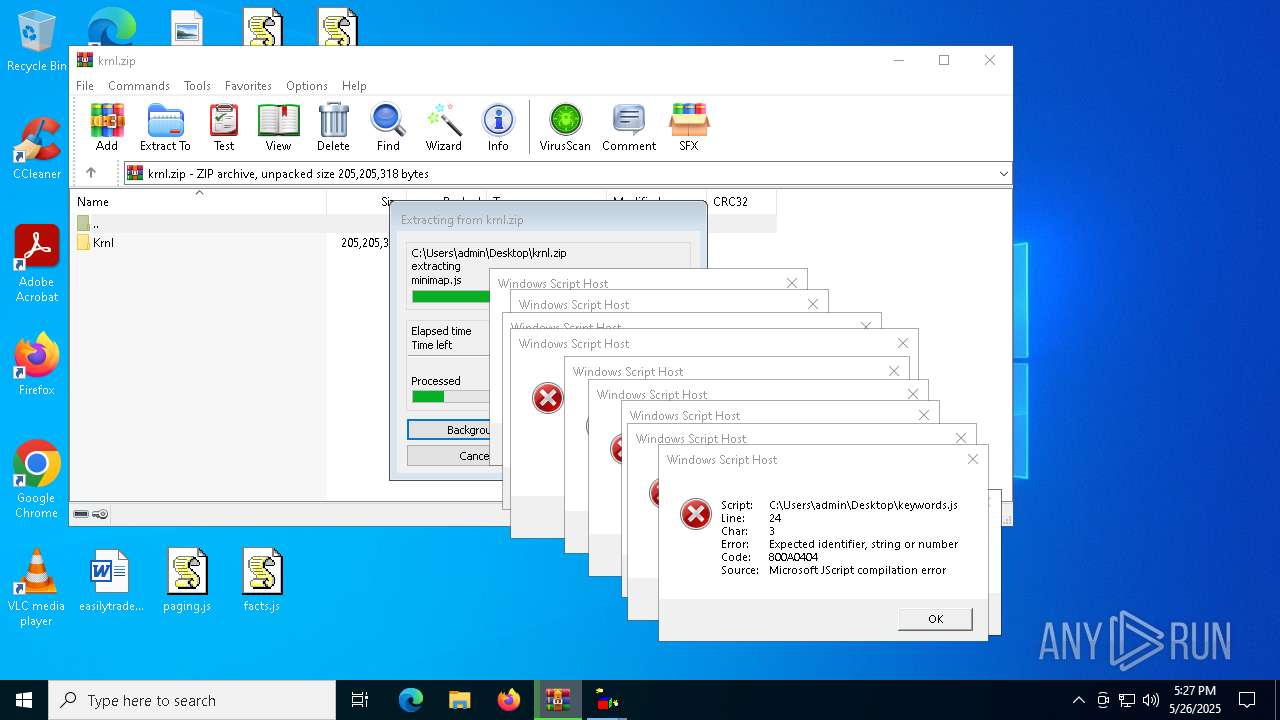
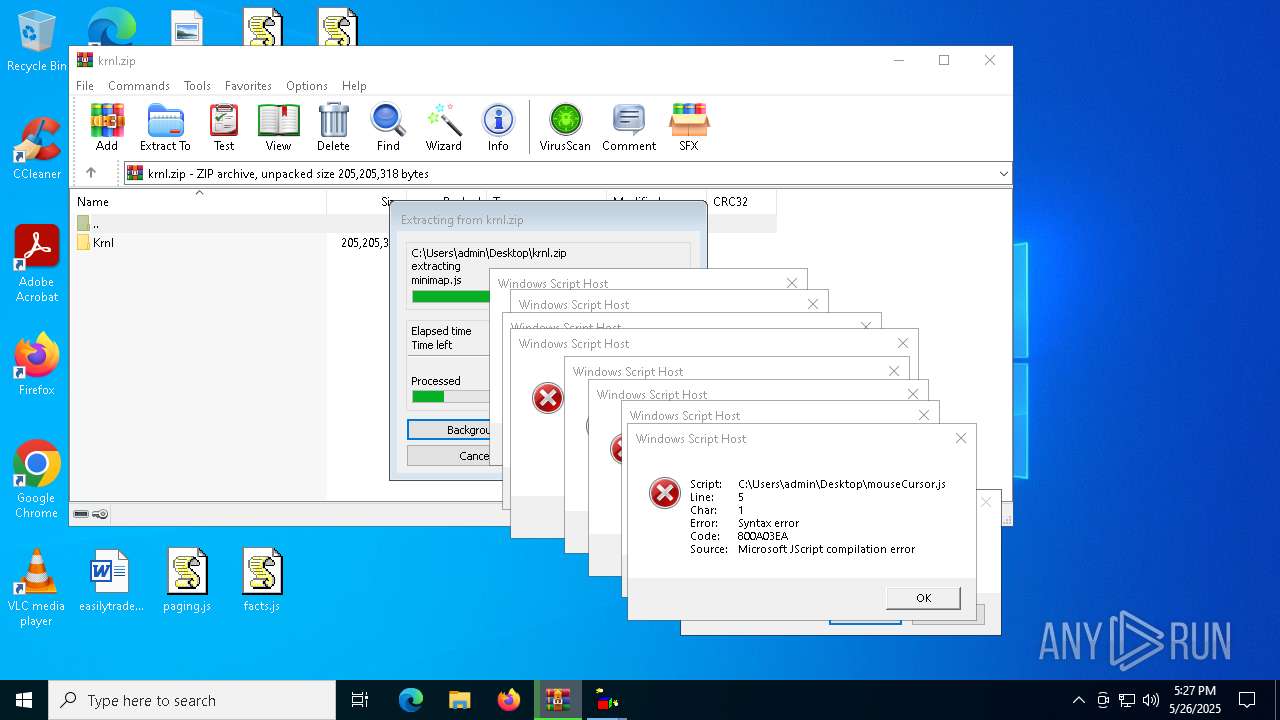
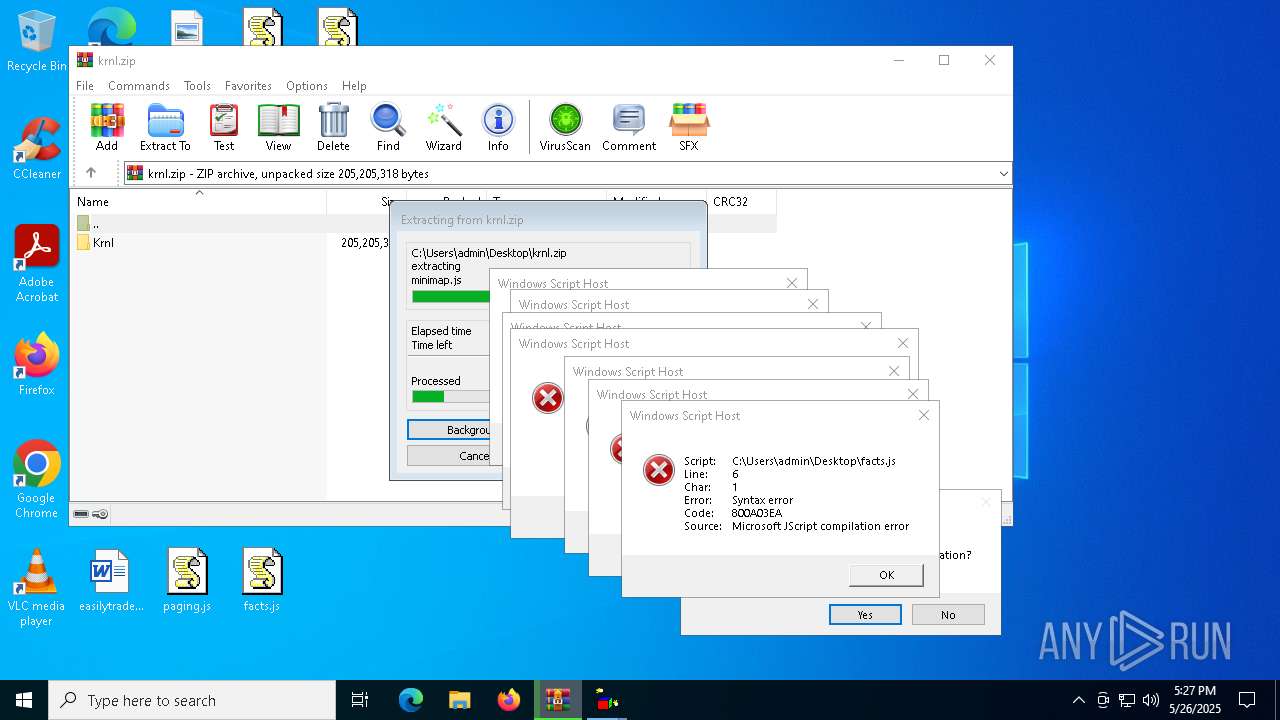
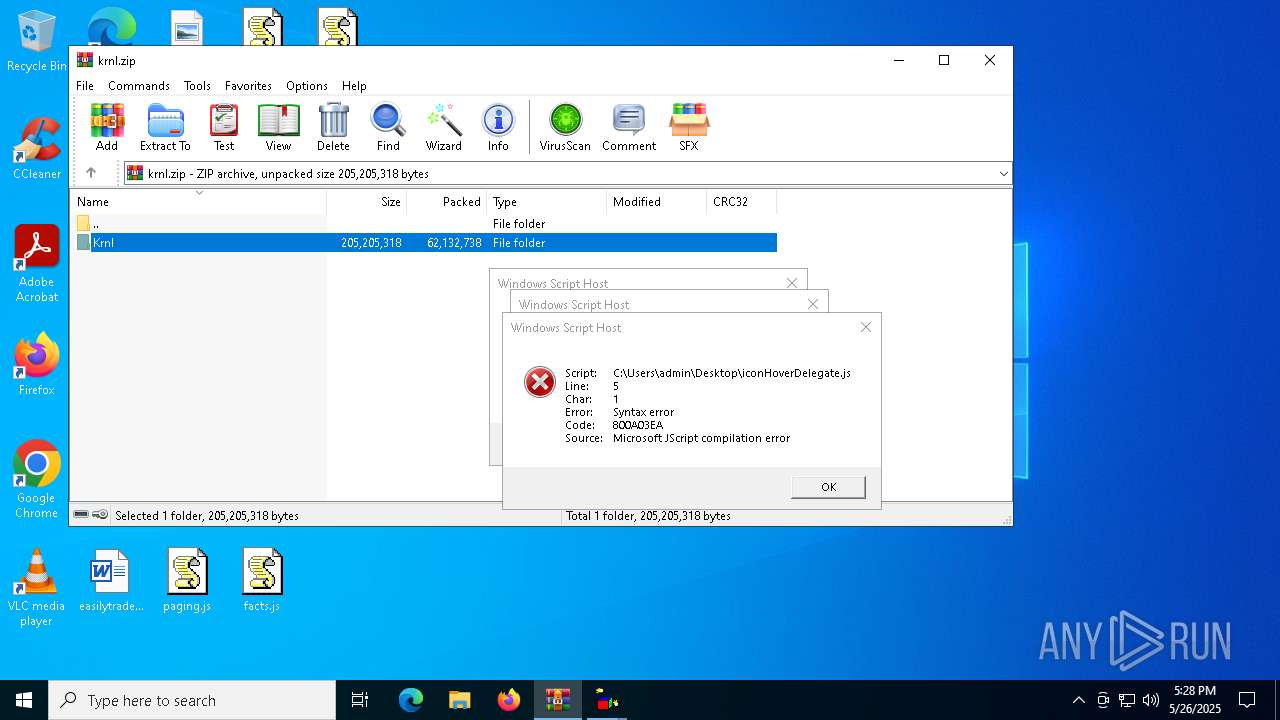
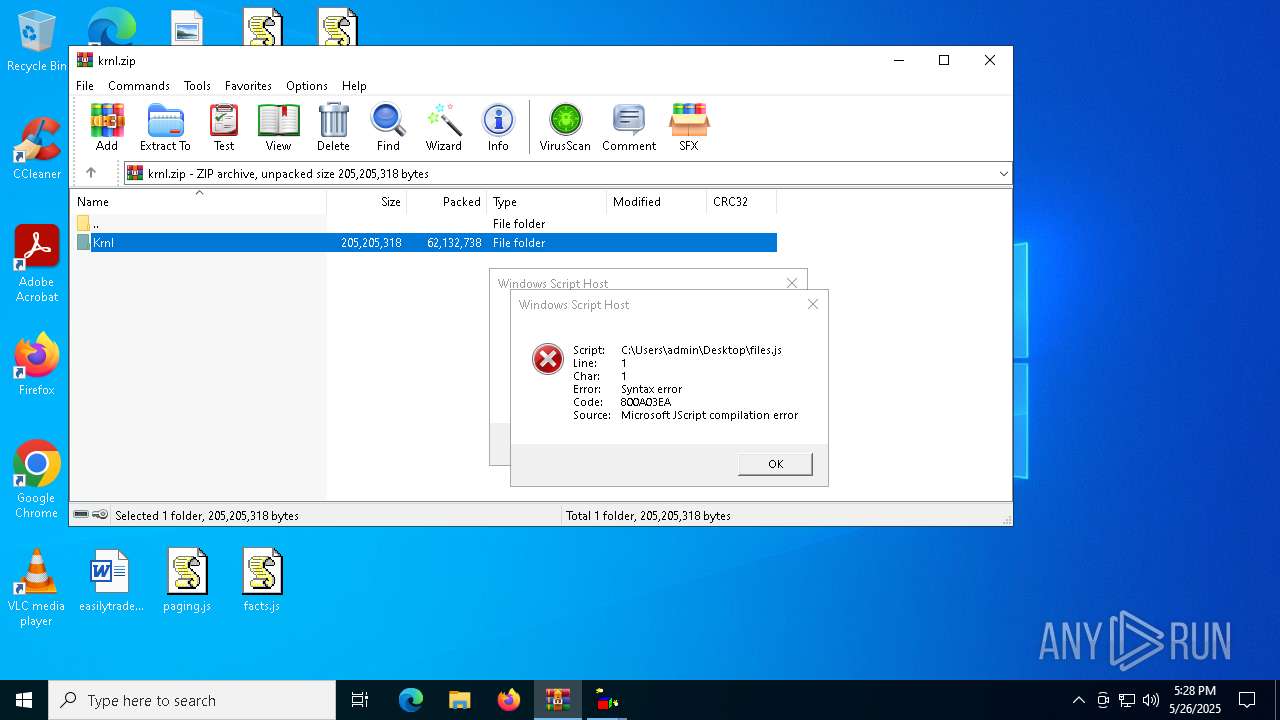
JScript runtime error (SCRIPT)
- wscript.exe (PID: 8088)
Checks proxy server information
- slui.exe (PID: 4608)
Reads the software policy settings
- slui.exe (PID: 4608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:02:19 05:39:38 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
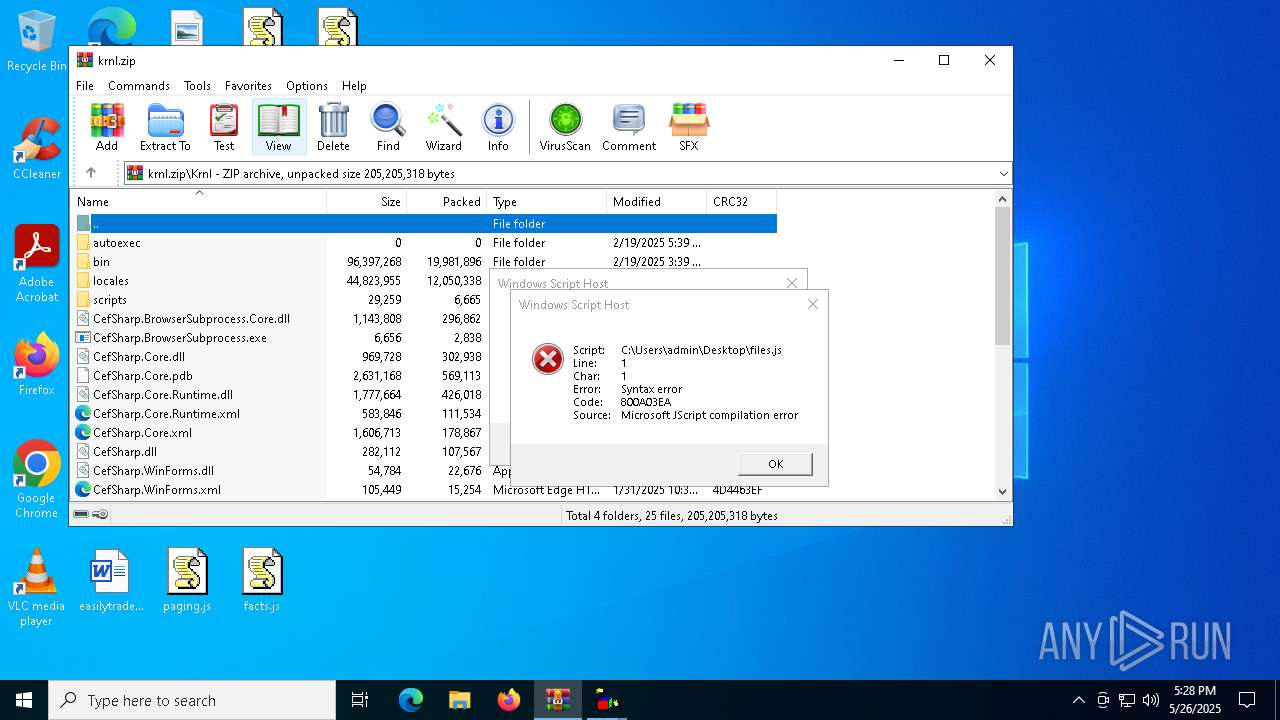
| ZipFileName: | Krnl/autoexec/ |
Total processes
133
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4608 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7532 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\krnl.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7664 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\paging.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7704 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\files.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7744 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\iconHoverDelegate.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
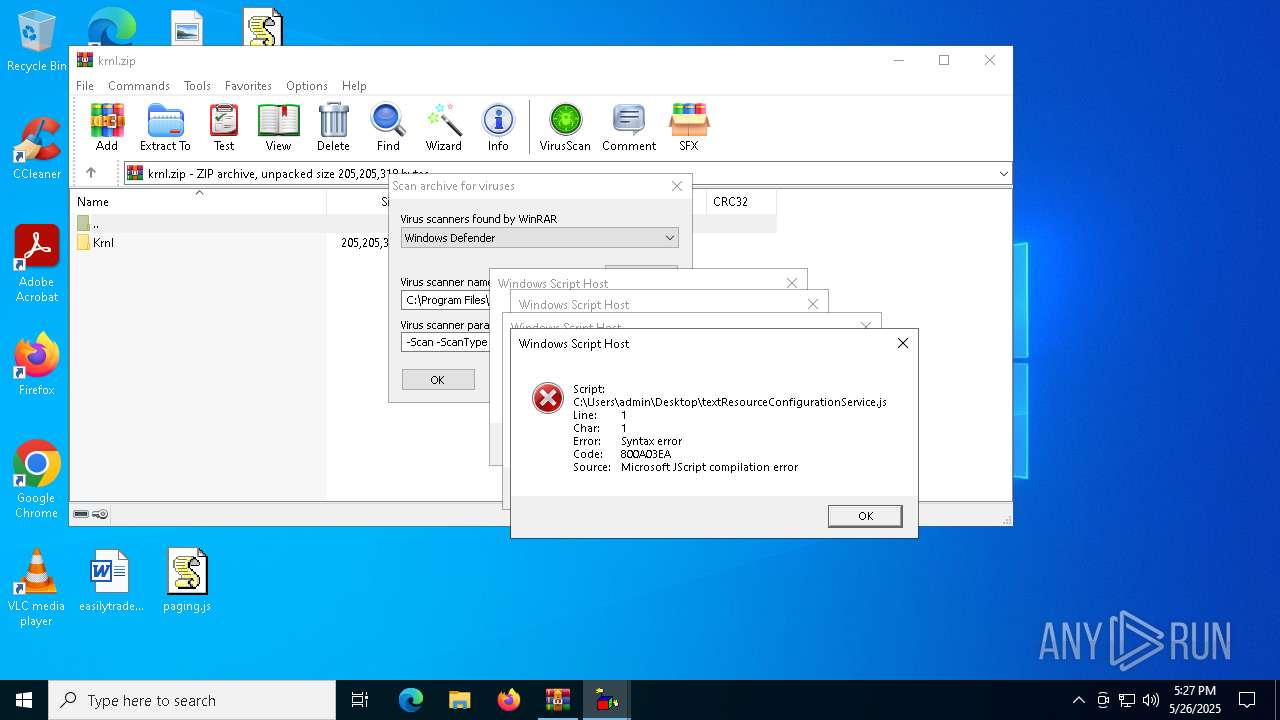
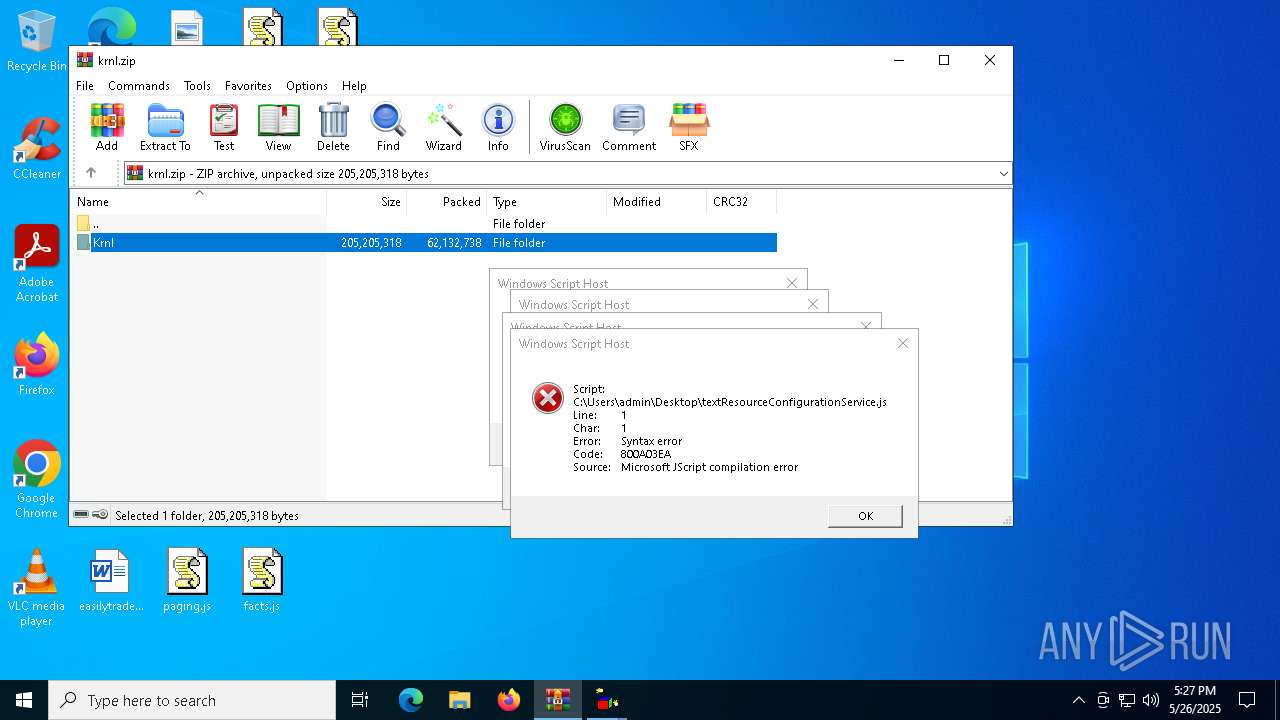
| 7792 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\textResourceConfigurationService.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
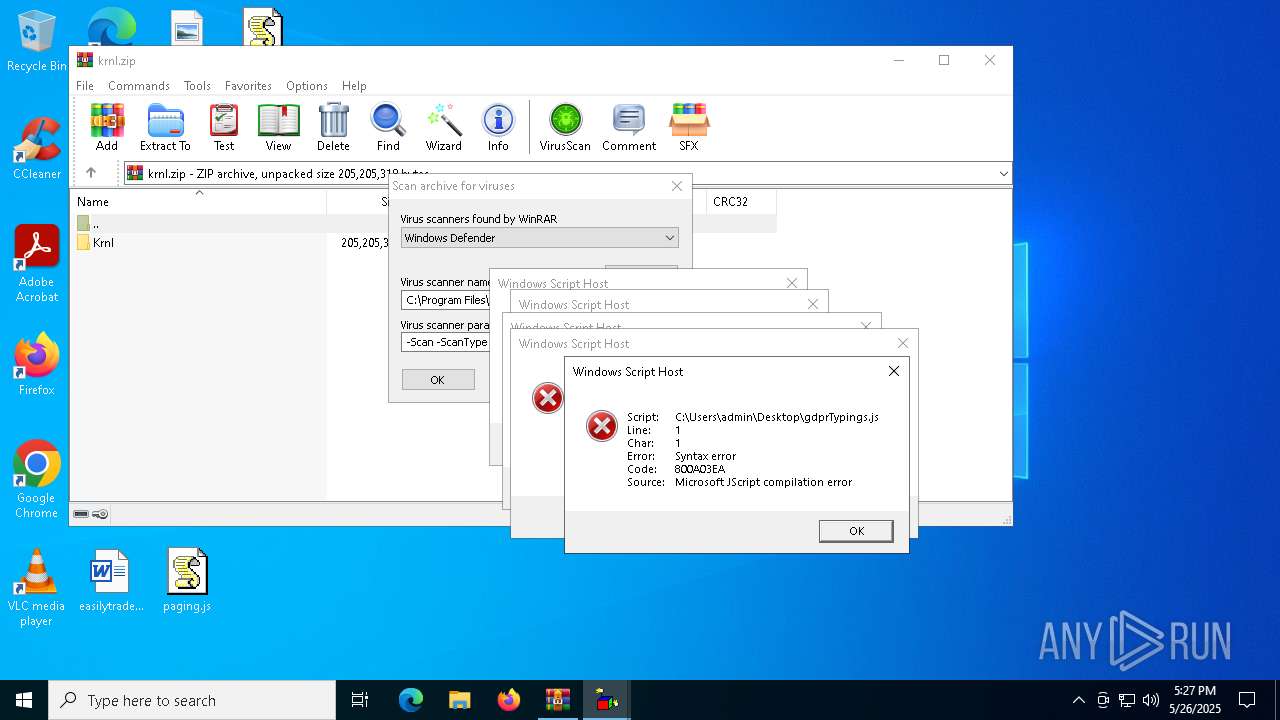
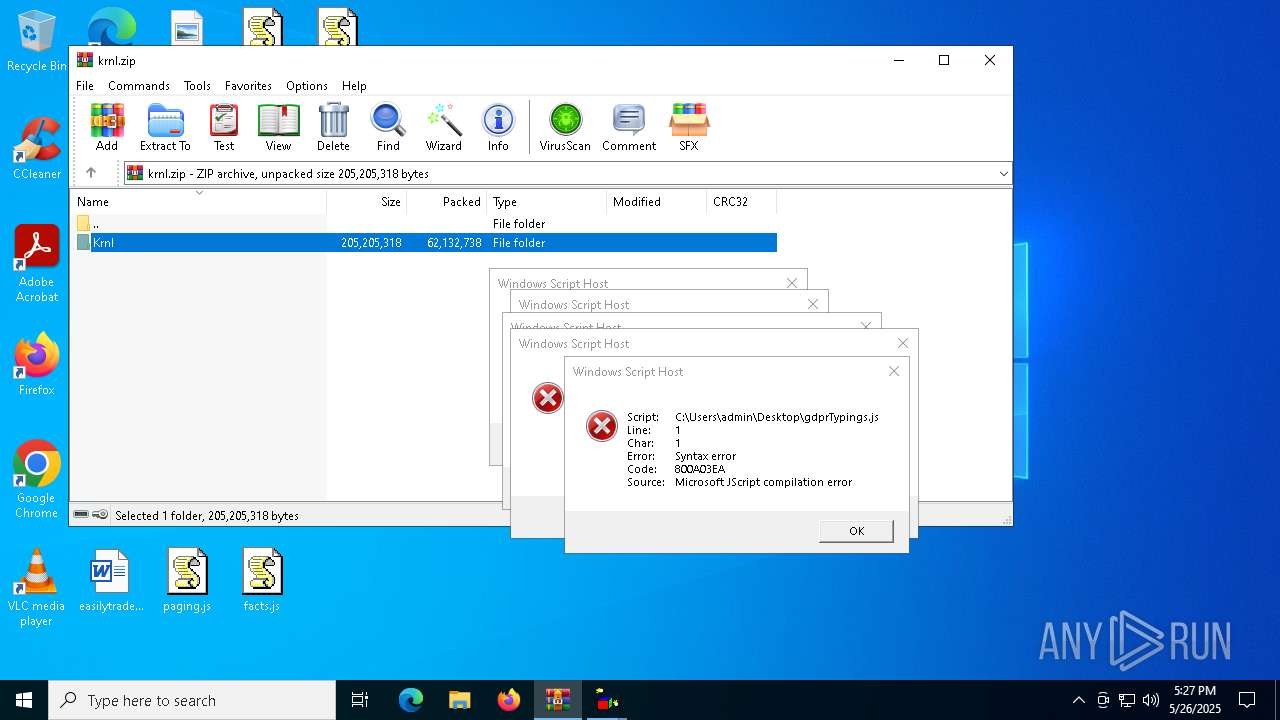
| 7860 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\gdprTypings.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
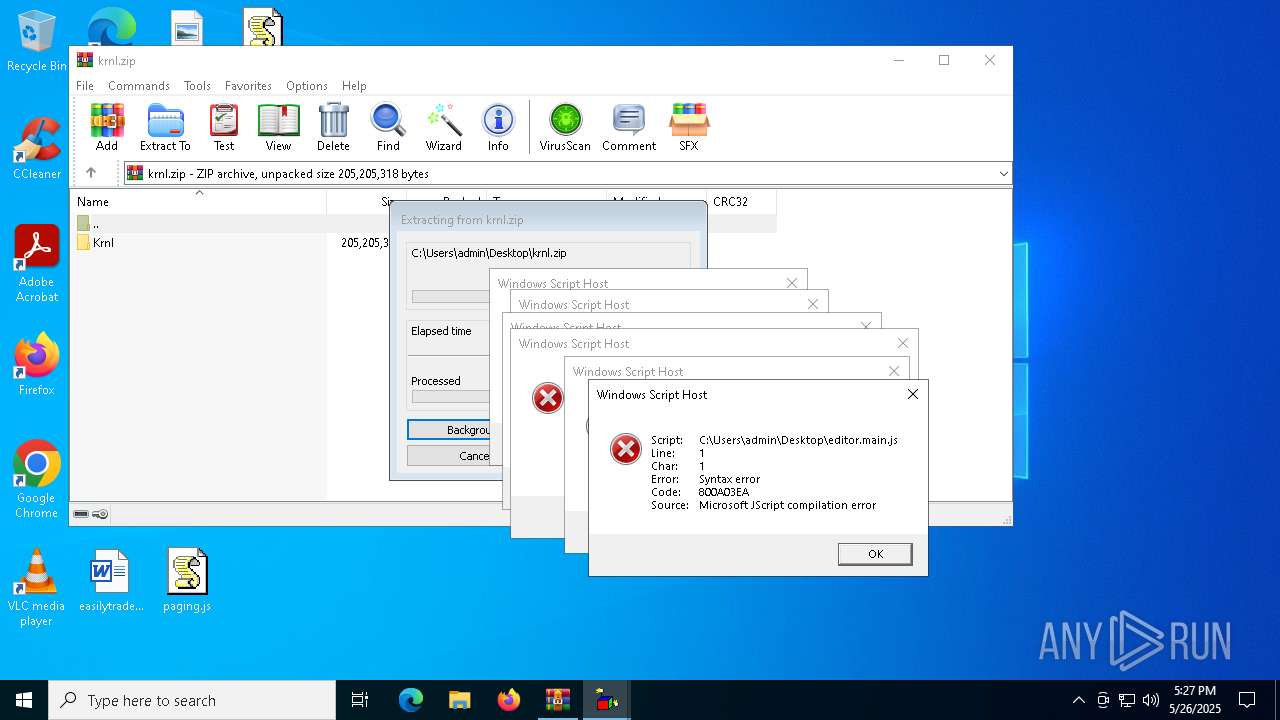
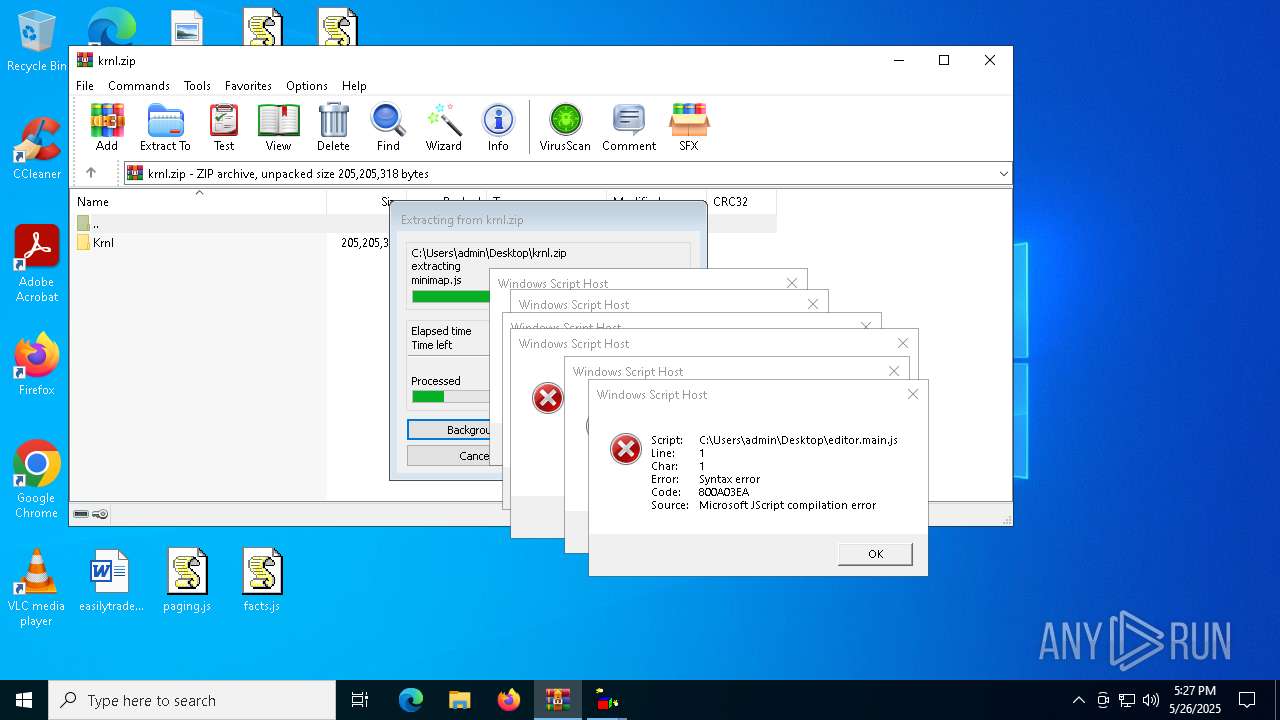
| 7900 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\editor.main.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7952 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\facts.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7992 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\mouseCursor.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
6 069
Read events
6 055
Write events
14
Delete events
0
Modification events
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\krnl.zip | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
| (PID) Process: | (8088) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\wscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 1820110000000000 | |||
Executable files
0
Suspicious files
427
Text files
75
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7532.24773\krnl.zip\Krnl\bin\DebugMonaco\.git\hooks\pre-commit.sample | text | |
MD5:305EADBBCD6F6D2567E033AD12AABBC4 | SHA256:F9AF7D95EB1231ECF2EBA9770FEDFA8D4797A12B02D7240E98D568201251244A | |||
| 7532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7532.24773\krnl.zip\Krnl\bin\DebugMonaco\.git\hooks\fsmonitor-watchman.sample | text | |
MD5:EA587B0FAE70333BCE92257152996E70 | SHA256:F3C0228D8E827F1C5260AC59FDD92C3D425C46E54711EF713C5A54AE0A4DB2B4 | |||
| 7532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7532.24773\krnl.zip\Krnl\bin\DebugMonaco\.git\config | text | |
MD5:920A11DE313BFB8D93D81F4A3A5B71B6 | SHA256:05BECDB83BB897F6103C8D91439E2E9092144EDF5B3955A746FCE4975C12BFDC | |||
| 7532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7532.24773\krnl.zip\Krnl\bin\DebugMonaco\.git\hooks\commit-msg.sample | text | |
MD5:579A3C1E12A1E74A98169175FB913012 | SHA256:1F74D5E9292979B573EBD59741D46CB93FF391ACDD083D340B94370753D92437 | |||
| 7532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7532.24773\krnl.zip\Krnl\bin\DebugMonaco\.git\hooks\pre-applypatch.sample | text | |
MD5:054F9FFB8BFE04A599751CC757226DDA | SHA256:E15C5B469EA3E0A695BEA6F2C82BCF8E62821074939DDD85B77E0007FF165475 | |||
| 7532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7532.24773\krnl.zip\Krnl\bin\DebugMonaco\.git\hooks\prepare-commit-msg.sample | text | |
MD5:2B5C047BDB474555E1787DB32B2D2FC5 | SHA256:E9DDCAA4189FDDD25ED97FC8C789ECA7B6CA16390B2392AE3276F0C8E1AA4619 | |||
| 7532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7532.24773\krnl.zip\Krnl\bin\DebugMonaco\.git\description | text | |
MD5:A0A7C3FFF21F2AEA3CFA1D0316DD816C | SHA256:85AB6C163D43A17EA9CF7788308BCA1466F1B0A8D1CC92E26E9BF63DA4062AEE | |||
| 7532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7532.24773\krnl.zip\Krnl\bin\DebugMonaco\.git\hooks\post-update.sample | text | |
MD5:2B7EA5CEE3C49FF53D41E00785EB974C | SHA256:81765AF2DAEF323061DCBC5E61FC16481CB74B3BAC9AD8A174B186523586F6C5 | |||
| 7532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7532.24773\krnl.zip\Krnl\bin\DebugMonaco\Fonts\JetBrainsMono-Regular.ttf | binary | |
MD5:0189ED701950C39ACA7664F1E9C3781F | SHA256:1F376439C75AB33392EB7A2F5EC999809493B378728D723327655C9FCB45CEA9 | |||
| 7532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7532.24773\krnl.zip\Krnl\bin\DebugMonaco\.git\hooks\applypatch-msg.sample | text | |
MD5:CE562E08D8098926A3862FC6E7905199 | SHA256:0223497A0B8B033AA58A3A521B8629869386CF7AB0E2F101963D328AA62193F7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
41
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 52.149.20.212:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 52.149.20.212:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
8176 | SIHClient.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
8176 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8176 | SIHClient.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
8176 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8176 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 52.149.20.212:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
8176 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8176 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
8176 | SIHClient.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |