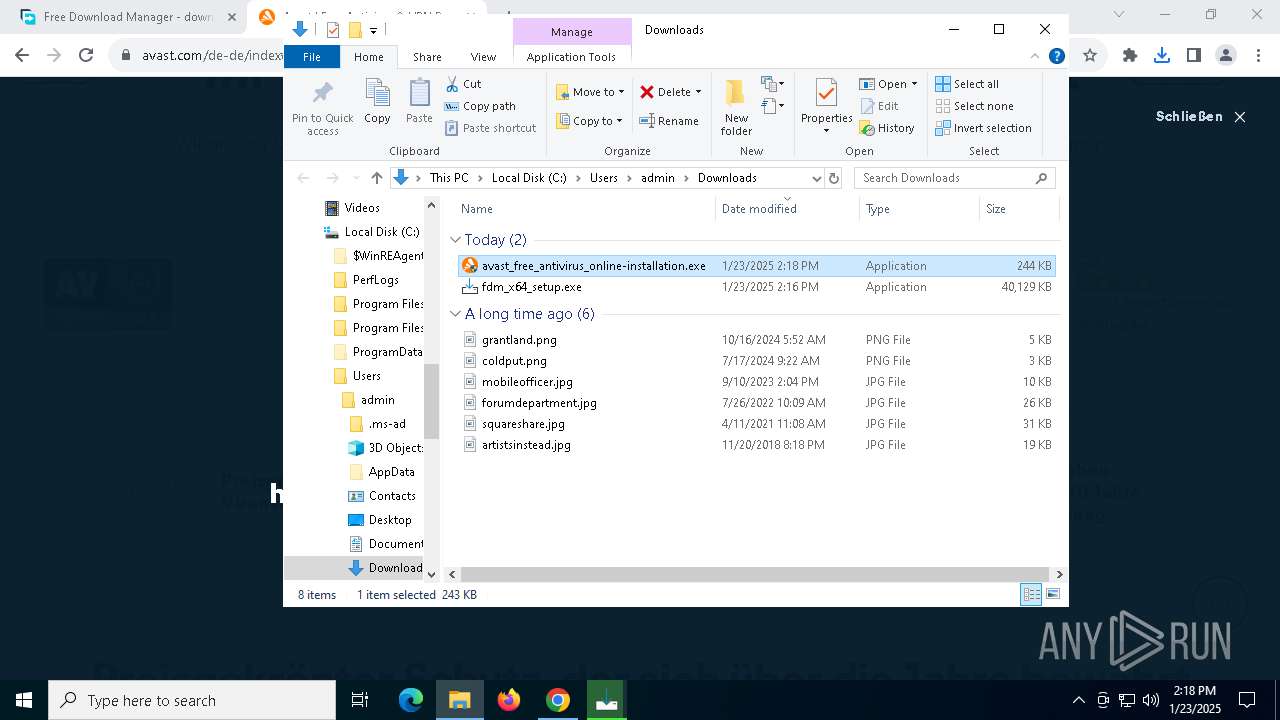
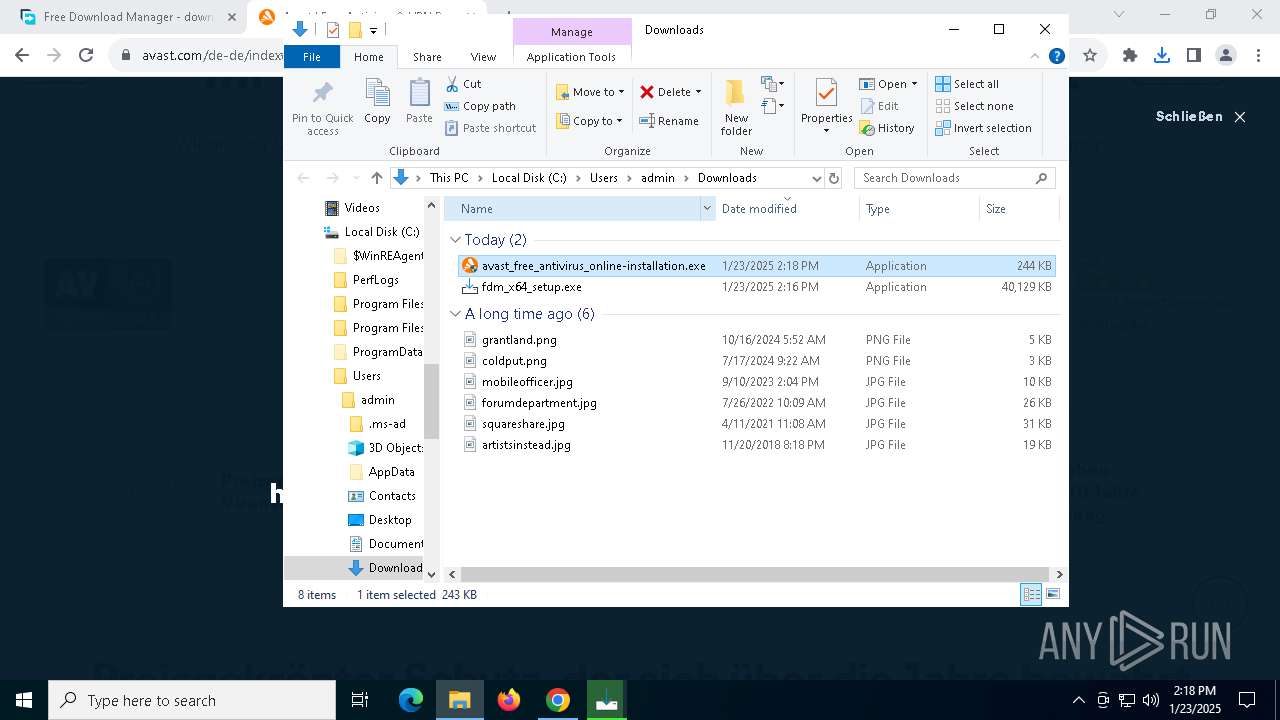
| URL: | https://www.freedownloadmanager.org/ |
| Full analysis: | https://app.any.run/tasks/0c7cf049-6f11-4f39-b28b-de15f6eb287d |
| Verdict: | Malicious activity |
| Analysis date: | January 23, 2025, 14:16:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 4D56C38C28CC8A5360D672DC2BB14B56 |
| SHA1: | 50D32BA1CCA503765861B2B934F785C4E505966D |
| SHA256: | 553FD82D9FD1A3D4B98D5F989095345361F9B33EA579FDF5C4D113AA79AB39B7 |
| SSDEEP: | 3:N8DSLLHKVELUXoCKn:2OLHwXin |
MALICIOUS
Changes the autorun value in the registry
- fdm.exe (PID: 5300)
Starts CMD.EXE for commands execution
- chrome.exe (PID: 556)
SUSPICIOUS
Creates file in the systems drive root
- explorer.exe (PID: 4488)
Executable content was dropped or overwritten
- fdm_x64_setup.exe (PID: 1864)
- fdm_x64_setup.tmp (PID: 6980)
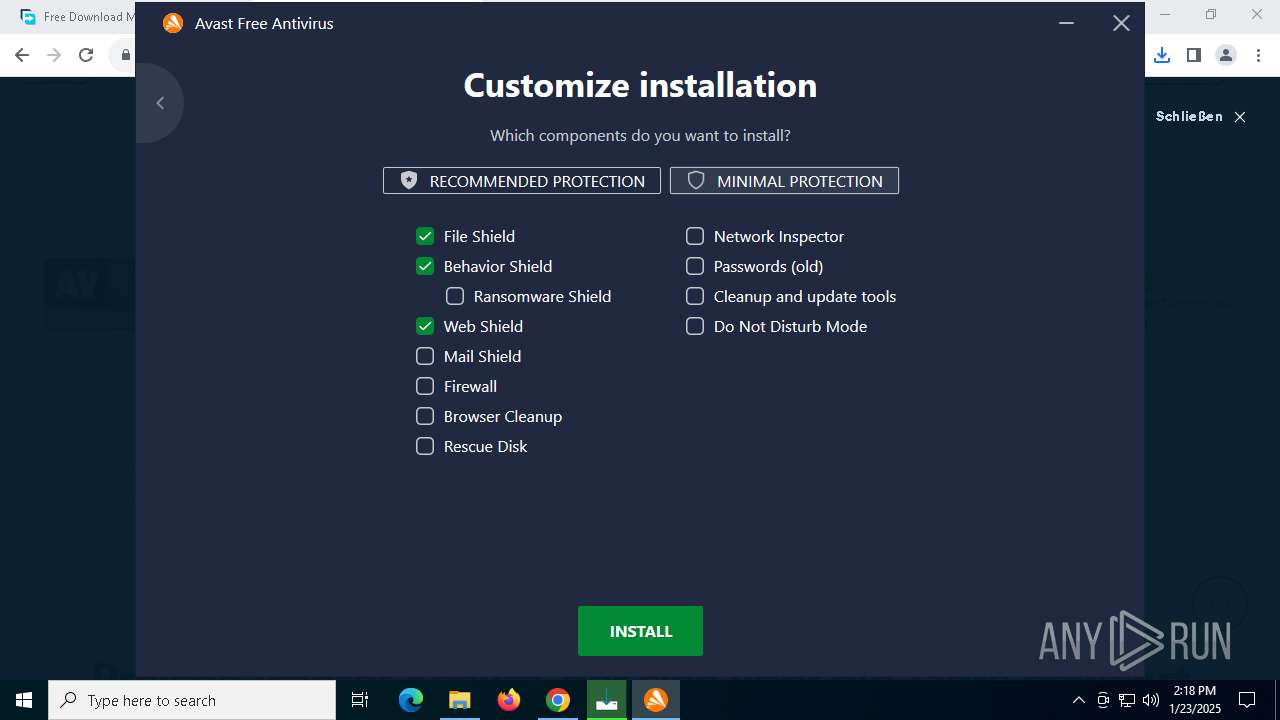
- avast_free_antivirus_online-installation.exe (PID: 5872)
- avast_free_antivirus_online_setup.exe (PID: 6900)
- icarus.exe (PID: 4280)
- icarus.exe (PID: 6784)
- fdm.exe (PID: 7600)
- icarus.exe (PID: 6300)
Reads the Windows owner or organization settings
- fdm_x64_setup.tmp (PID: 6980)
Process drops legitimate windows executable
- fdm_x64_setup.tmp (PID: 6980)
- icarus.exe (PID: 6784)
The process drops C-runtime libraries
- fdm_x64_setup.tmp (PID: 6980)
- icarus.exe (PID: 6784)
Starts itself from another location
- icarus.exe (PID: 4280)
Checks for external IP
- avast_free_antivirus_online-installation.exe (PID: 5872)
Reads security settings of Internet Explorer
- icarus_ui.exe (PID: 7108)
Checks Windows Trust Settings
- icarus_ui.exe (PID: 7108)
The process creates files with name similar to system file names
- icarus.exe (PID: 6784)
Uses NETSH.EXE to add a firewall rule or allowed programs
- fdm_x64_setup.tmp (PID: 6980)
Searches for installed software
- fdm5rhwin.exe (PID: 7124)
Detected use of alternative data streams (AltDS)
- fdm.exe (PID: 7600)
Drops a system driver (possible attempt to evade defenses)
- icarus.exe (PID: 6784)
Starts application with an unusual extension
- idman642build26.exe (PID: 5256)
The executable file from the user directory is run by the CMD process
- wenativehost.exe (PID: 2040)
The process verifies whether the antivirus software is installed
- icarus.exe (PID: 6784)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 4488)
Creates files or folders in the user directory
- explorer.exe (PID: 4488)
- fdm_x64_setup.tmp (PID: 6980)
- icarus_ui.exe (PID: 7108)
- importwizard.exe (PID: 3896)
- fdm.exe (PID: 5300)
- fdm.exe (PID: 7600)
The process uses the downloaded file
- chrome.exe (PID: 5992)
- explorer.exe (PID: 4488)
- chrome.exe (PID: 3888)
Checks proxy server information
- explorer.exe (PID: 4488)
- avast_free_antivirus_online_setup.exe (PID: 6900)
- icarus_ui.exe (PID: 7108)
Executable content was dropped or overwritten
- chrome.exe (PID: 556)
- chrome.exe (PID: 6240)
Create files in a temporary directory
- fdm_x64_setup.exe (PID: 1864)
- fdm_x64_setup.tmp (PID: 6980)
Reads the computer name
- fdm_x64_setup.tmp (PID: 6980)
- avast_free_antivirus_online-installation.exe (PID: 5872)
- avast_free_antivirus_online_setup.exe (PID: 6900)
- icarus.exe (PID: 6300)
- icarus.exe (PID: 6784)
- icarus.exe (PID: 4280)
- fdm.exe (PID: 7600)
- IDM1.tmp (PID: 8004)
Checks supported languages
- fdm_x64_setup.exe (PID: 1864)
- fdm_x64_setup.tmp (PID: 6980)
- avast_free_antivirus_online-installation.exe (PID: 5872)
- avast_free_antivirus_online_setup.exe (PID: 6900)
- icarus_ui.exe (PID: 7108)
- icarus.exe (PID: 4280)
- fdm.exe (PID: 5300)
- importwizard.exe (PID: 3896)
- fdm5rhwin.exe (PID: 236)
- fdm5rhwin.exe (PID: 7124)
- fdm.exe (PID: 7600)
- importwizard.exe (PID: 3820)
- identity_helper.exe (PID: 7836)
The sample compiled with english language support
- fdm_x64_setup.tmp (PID: 6980)
- chrome.exe (PID: 6240)
- chrome.exe (PID: 556)
- avast_free_antivirus_online-installation.exe (PID: 5872)
- avast_free_antivirus_online_setup.exe (PID: 6900)
- icarus.exe (PID: 4280)
- icarus.exe (PID: 6784)
- fdm.exe (PID: 7600)
- icarus.exe (PID: 6300)
Reads the software policy settings
- explorer.exe (PID: 4488)
- avast_free_antivirus_online-installation.exe (PID: 5872)
- avast_free_antivirus_online_setup.exe (PID: 6900)
- icarus_ui.exe (PID: 7108)
Detects InnoSetup installer (YARA)
- fdm_x64_setup.exe (PID: 1864)
- fdm_x64_setup.tmp (PID: 6980)
Compiled with Borland Delphi (YARA)
- fdm_x64_setup.exe (PID: 1864)
- fdm_x64_setup.tmp (PID: 6980)
Application launched itself
- chrome.exe (PID: 556)
- msedge.exe (PID: 6016)
- msedge.exe (PID: 7820)
Reads the machine GUID from the registry
- avast_free_antivirus_online-installation.exe (PID: 5872)
- avast_free_antivirus_online_setup.exe (PID: 6900)
- icarus.exe (PID: 4280)
- icarus.exe (PID: 6300)
- icarus.exe (PID: 6784)
- icarus_ui.exe (PID: 7108)
- importwizard.exe (PID: 3896)
- fdm.exe (PID: 5300)
- fdm.exe (PID: 7600)
Creates files in the program directory
- icarus.exe (PID: 4280)
- icarus_ui.exe (PID: 7108)
- icarus.exe (PID: 6784)
Reads CPU info
- icarus.exe (PID: 6784)
Reads Environment values
- icarus.exe (PID: 6784)
The sample compiled with czech language support
- icarus.exe (PID: 6784)
Process checks computer location settings
- fdm.exe (PID: 7600)
Reads the time zone
- fdm.exe (PID: 7600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
253
Monitored processes
117
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4956 --field-trial-handle=1848,i,3227893714878804850,6567965019982432808,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 | |||||||||||||||
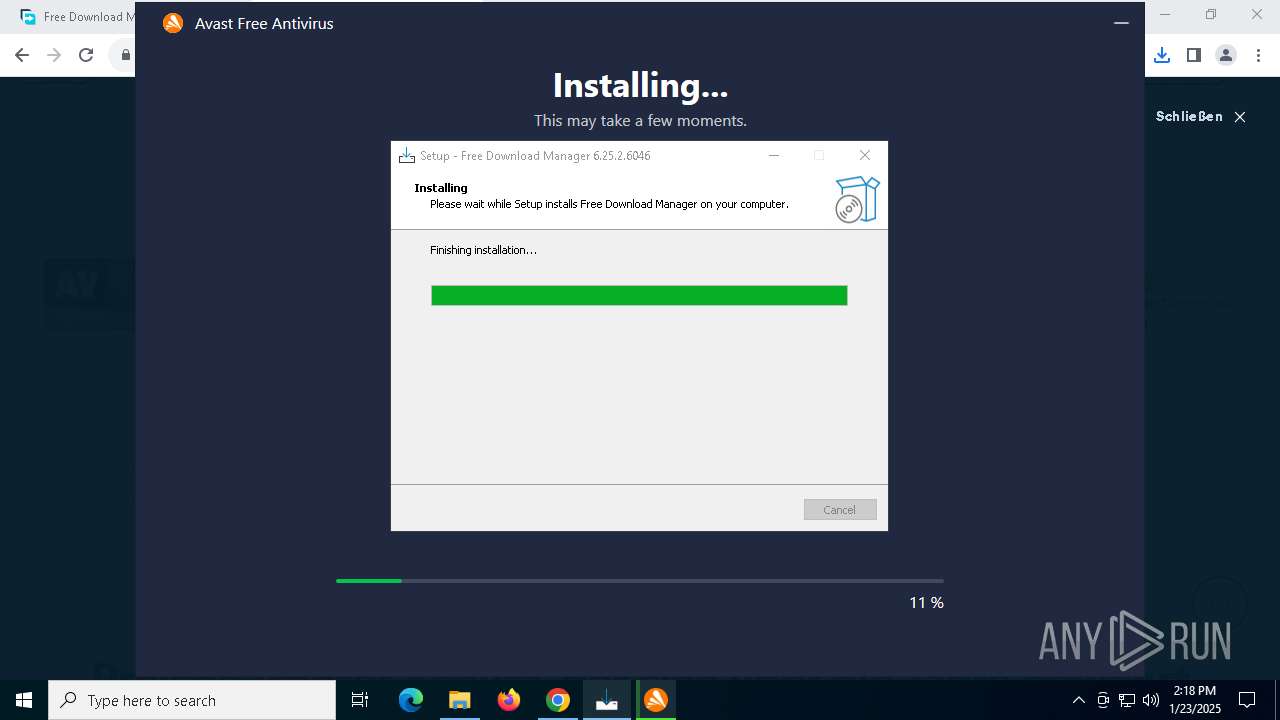
| 236 | "C:\Users\admin\AppData\Local\Softdeluxe\Free Download Manager\fdm5rhwin.exe" 21907CB0205CFF989F82C03684A01B86 phase1 | C:\Users\admin\AppData\Local\Softdeluxe\Free Download Manager\fdm5rhwin.exe | — | fdm_x64_setup.tmp | |||||||||||
User: admin Company: Softdeluxe Integrity Level: MEDIUM Description: Free Download Manager Exit code: 1 Version: 6.25.2.6046 Modules
| |||||||||||||||
| 372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=7332 --field-trial-handle=1848,i,3227893714878804850,6567965019982432808,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 | |||||||||||||||
| 556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://www.freedownloadmanager.org/" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1192 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=6856 --field-trial-handle=1848,i,3227893714878804850,6567965019982432808,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 | |||||||||||||||
| 1488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | importwizard.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=7128 --field-trial-handle=1848,i,3227893714878804850,6567965019982432808,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 | |||||||||||||||
| 1620 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --mojo-platform-channel-handle=5304 --field-trial-handle=1848,i,3227893714878804850,6567965019982432808,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
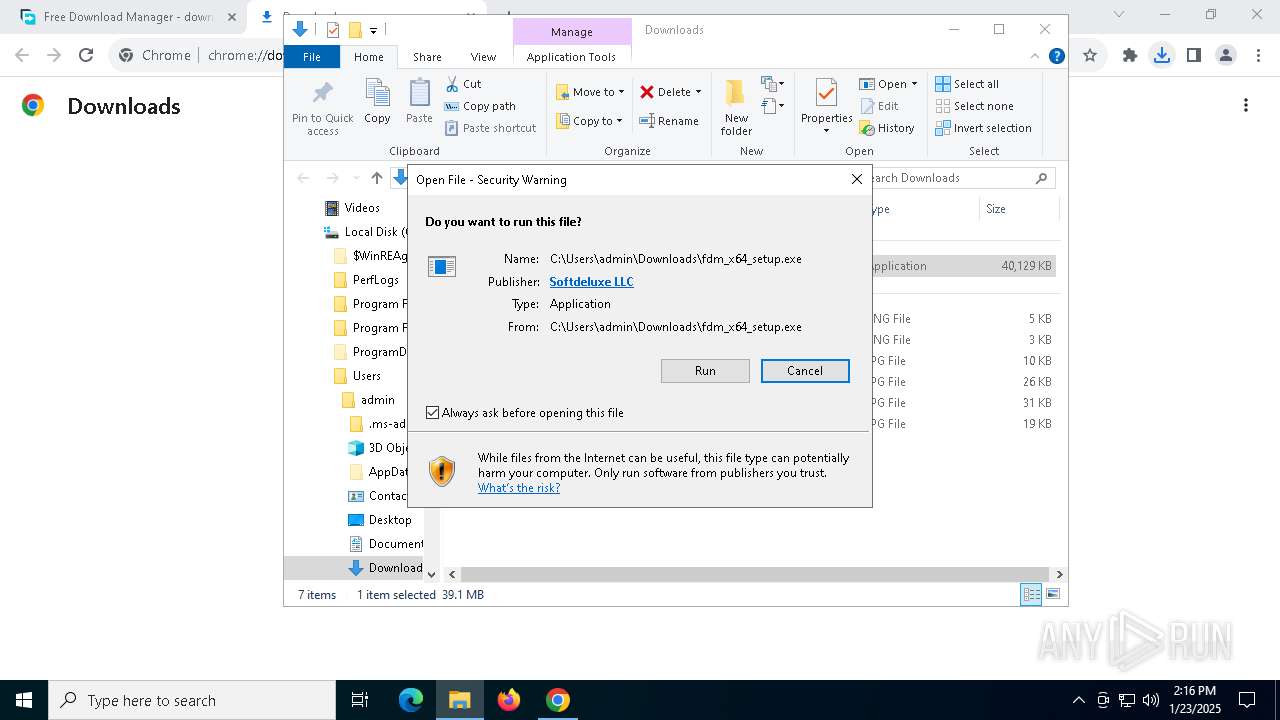
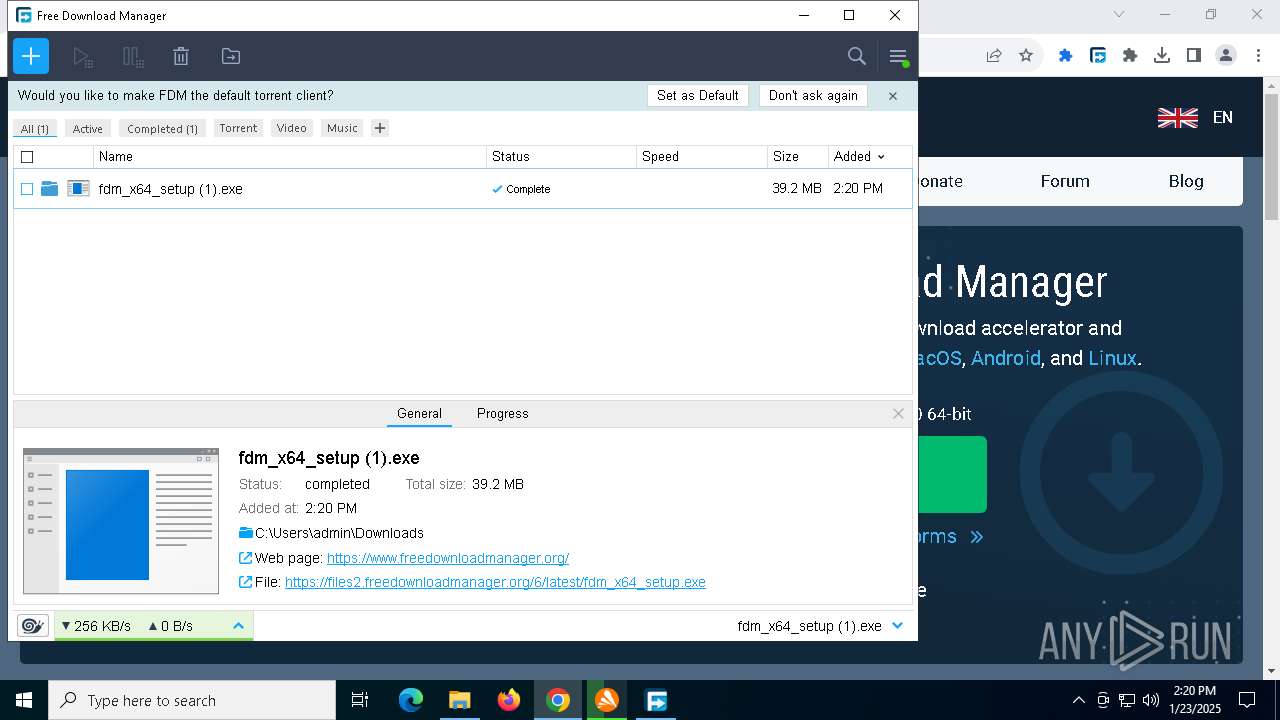
| 1864 | "C:\Users\admin\Downloads\fdm_x64_setup.exe" | C:\Users\admin\Downloads\fdm_x64_setup.exe | explorer.exe | ||||||||||||
User: admin Company: Softdeluxe Integrity Level: MEDIUM Description: Free Download Manager Setup Exit code: 0 Version: 6.25.2.6046 Modules
| |||||||||||||||
| 2040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | fdm5rhwin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
91 293
Read events
90 935
Write events
337
Delete events
21
Modification events
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000000000000072005D00 | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000040206 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456A48A294F7A40804AB924005FF030B61F | |||
| (PID) Process: | (556) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (556) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (556) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (556) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (556) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppBadgeUpdated |
| Operation: | write | Name: | Chrome |
Value: 6 | |||
| (PID) Process: | (5992) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000B87ACE6BA16DDB01 | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
Executable files
912
Suspicious files
2 105
Text files
1 240
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF136610.TMP | — | |
MD5:— | SHA256:— | |||
| 556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF136610.TMP | — | |
MD5:— | SHA256:— | |||
| 556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF136610.TMP | — | |
MD5:— | SHA256:— | |||
| 556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF136610.TMP | — | |
MD5:— | SHA256:— | |||
| 556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF136610.TMP | — | |
MD5:— | SHA256:— | |||
| 556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
292
DNS requests
323
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3912 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
3912 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
3912 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
3912 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7096 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7096 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6172 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4488 | explorer.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHgDGEJFcIpBz28BuO60qVQ%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6068 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 104.126.37.147:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
556 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1076 | svchost.exe | 184.30.18.9:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6424 | chrome.exe | 74.117.181.203:443 | www.freedownloadmanager.org | WZCOM | US | whitelisted |
6424 | chrome.exe | 173.194.69.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
6424 | chrome.exe | 172.217.18.8:443 | www.googletagmanager.com | GOOGLE | US | whitelisted |
6424 | chrome.exe | 172.217.16.138:443 | content-autofill.googleapis.com | GOOGLE | US | whitelisted |
6424 | chrome.exe | 216.239.32.36:443 | region1.google-analytics.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.freedownloadmanager.org |
| whitelisted |
accounts.google.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
region1.google-analytics.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
files2.freedownloadmanager.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6424 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6424 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6424 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6424 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6424 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6424 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
5872 | avast_free_antivirus_online-installation.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |