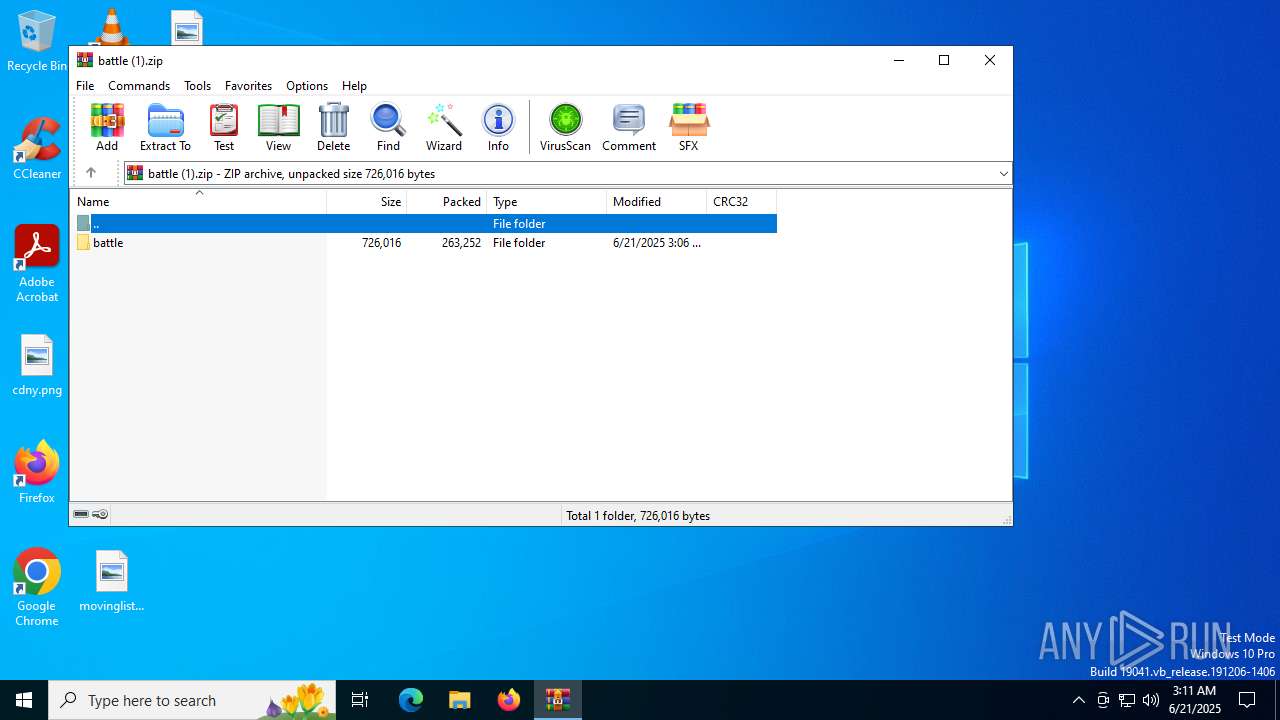
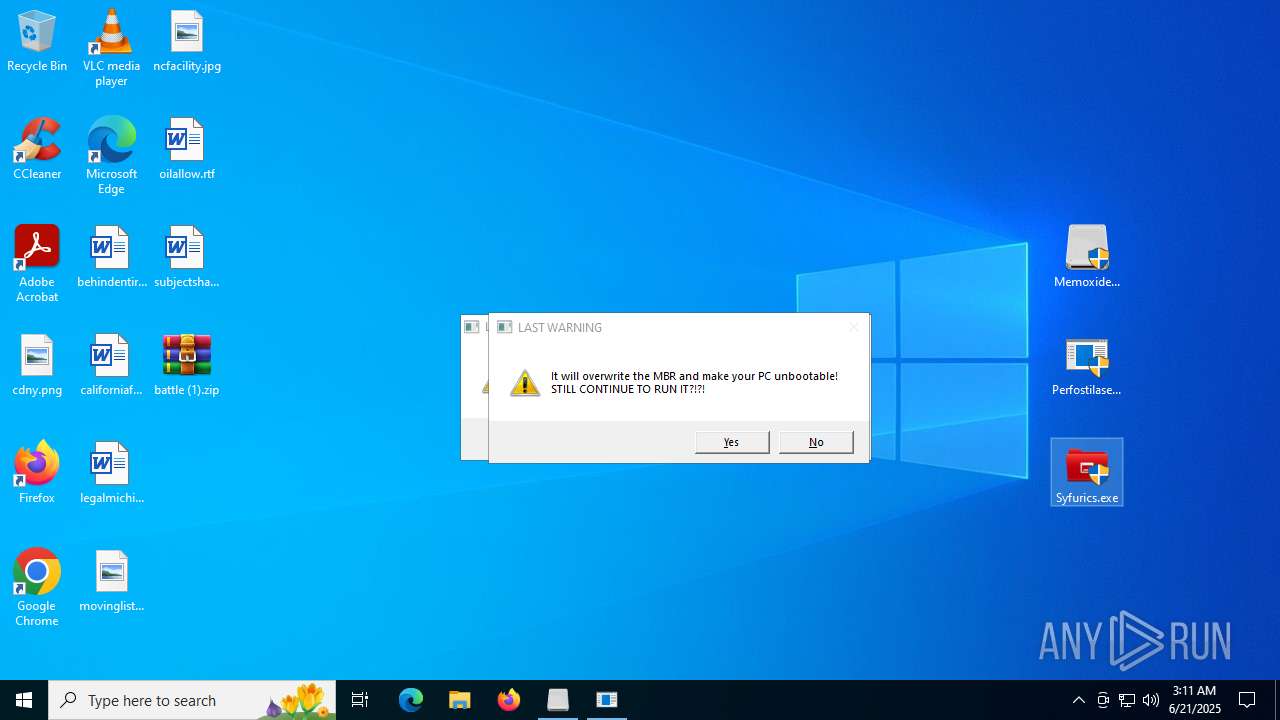
| File name: | battle (1).zip |
| Full analysis: | https://app.any.run/tasks/e98c1b6d-8c41-4ccd-a2a7-ba4201432d7d |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 03:11:06 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | 0F5DF3F59E5BE3083C7C1DDC8A5FBBBE |
| SHA1: | C45830839301DCB4E71C1F308F613C7ED20A08A7 |
| SHA256: | 5526CBEA9B60D0C5622A70E3E14ED9C55C263E4EEE6B791884A5F9B977D271E2 |
| SSDEEP: | 12288:a3x8VCYHPaC429EdYRnOTjFazKfqHpD4b4h:a3x8VBHCC429EdYRnOTjFazKSHpDD |
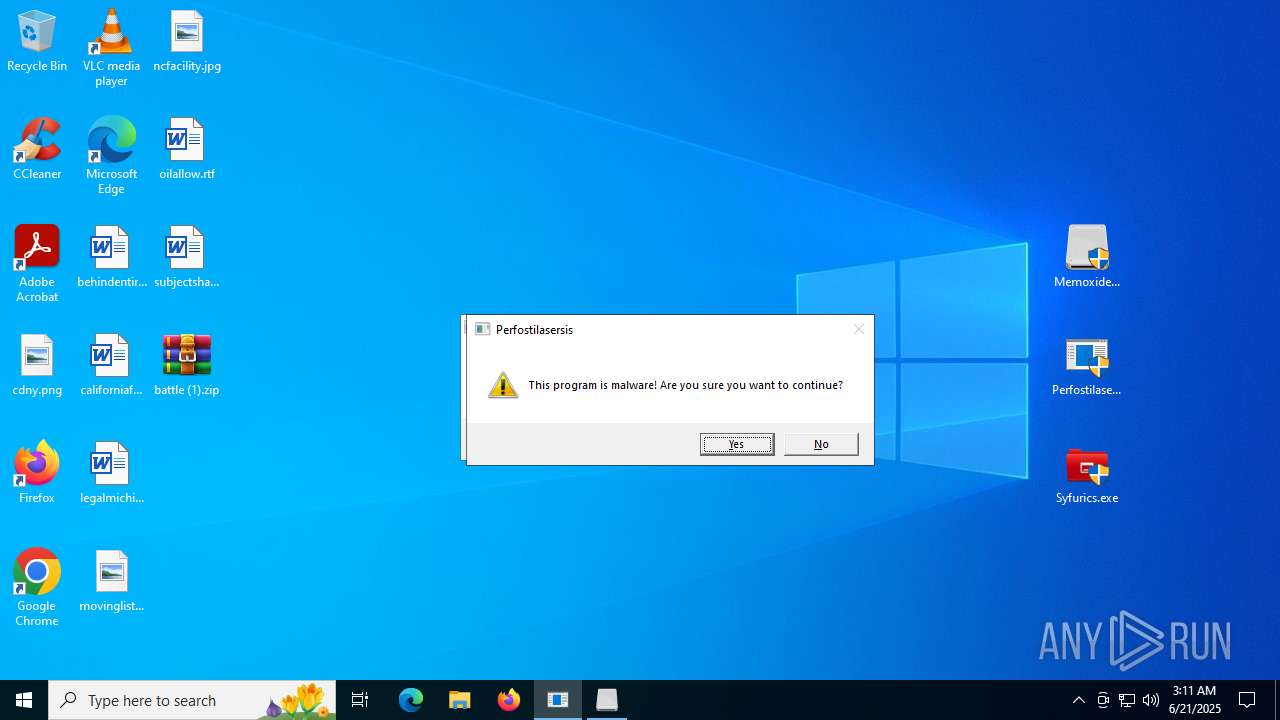
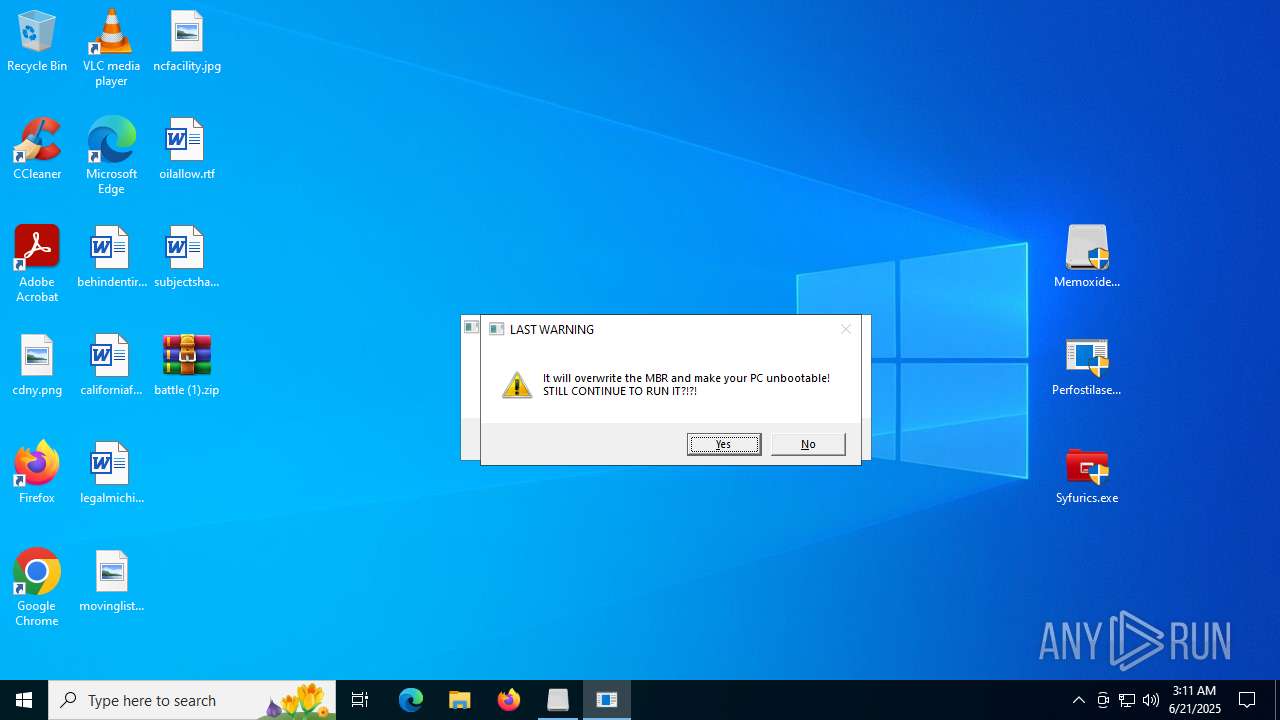
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2708)
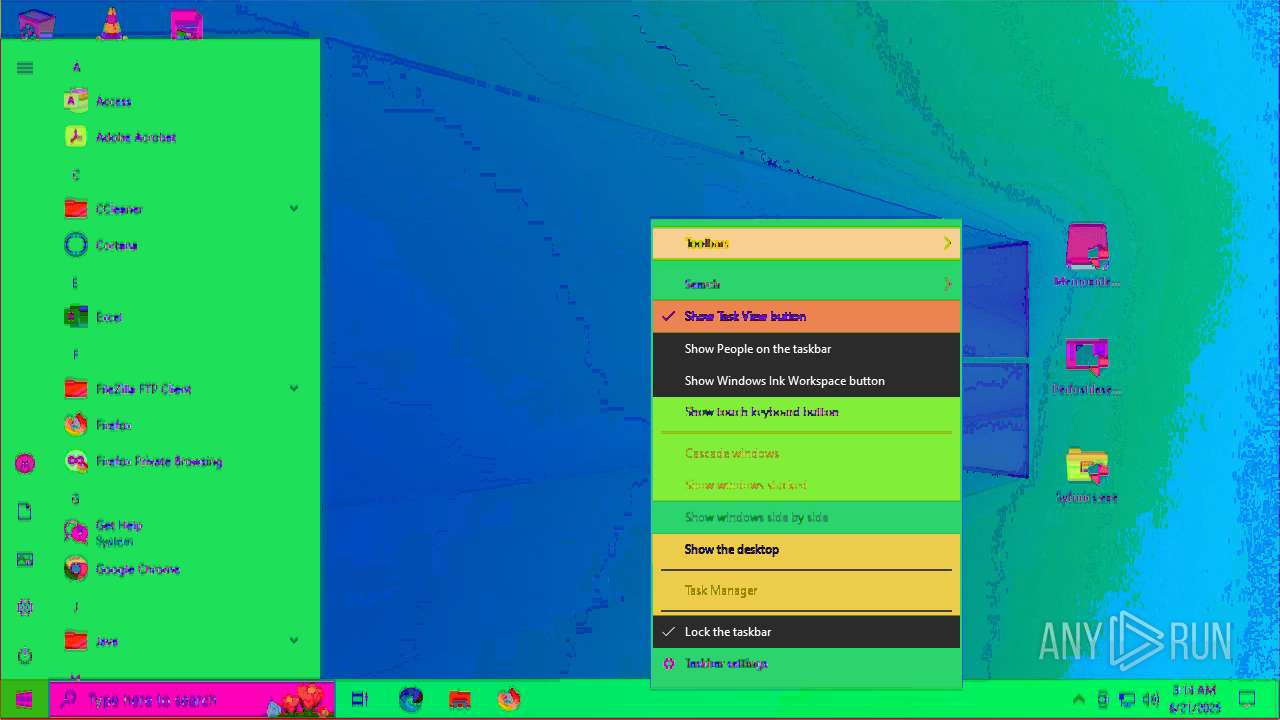
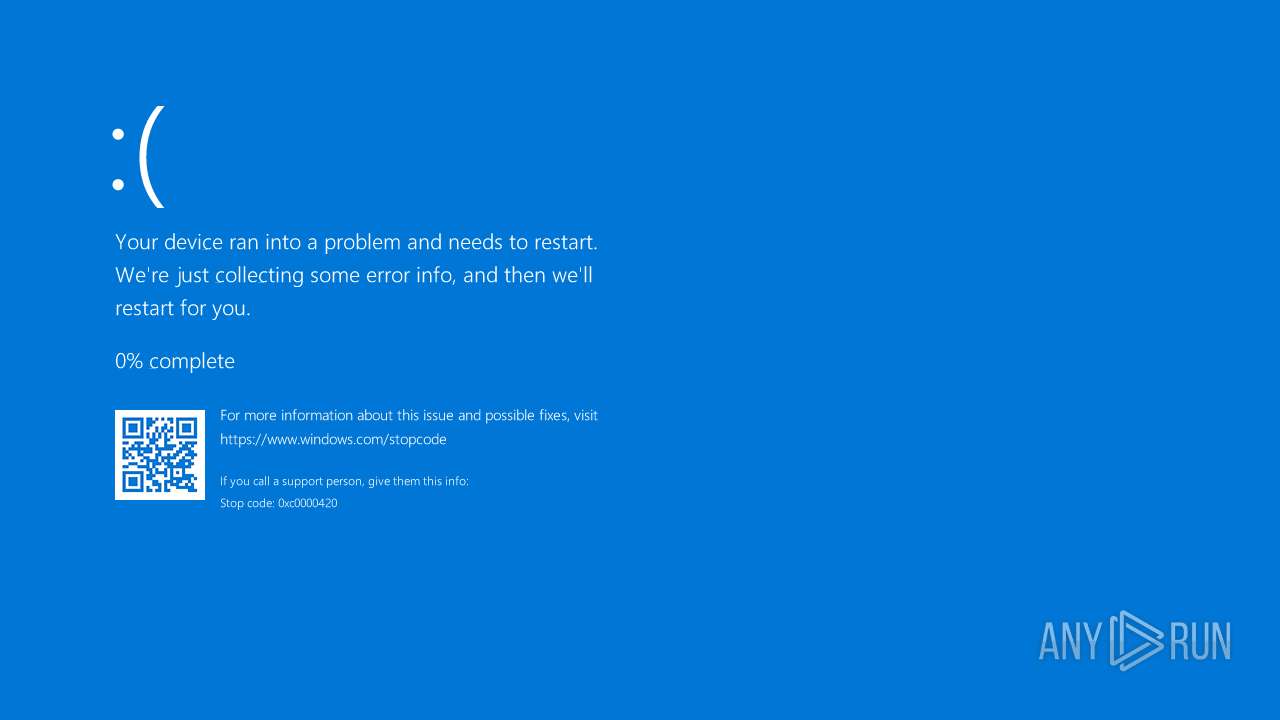
Disables task manager
- reg.exe (PID: 2320)
SUSPICIOUS
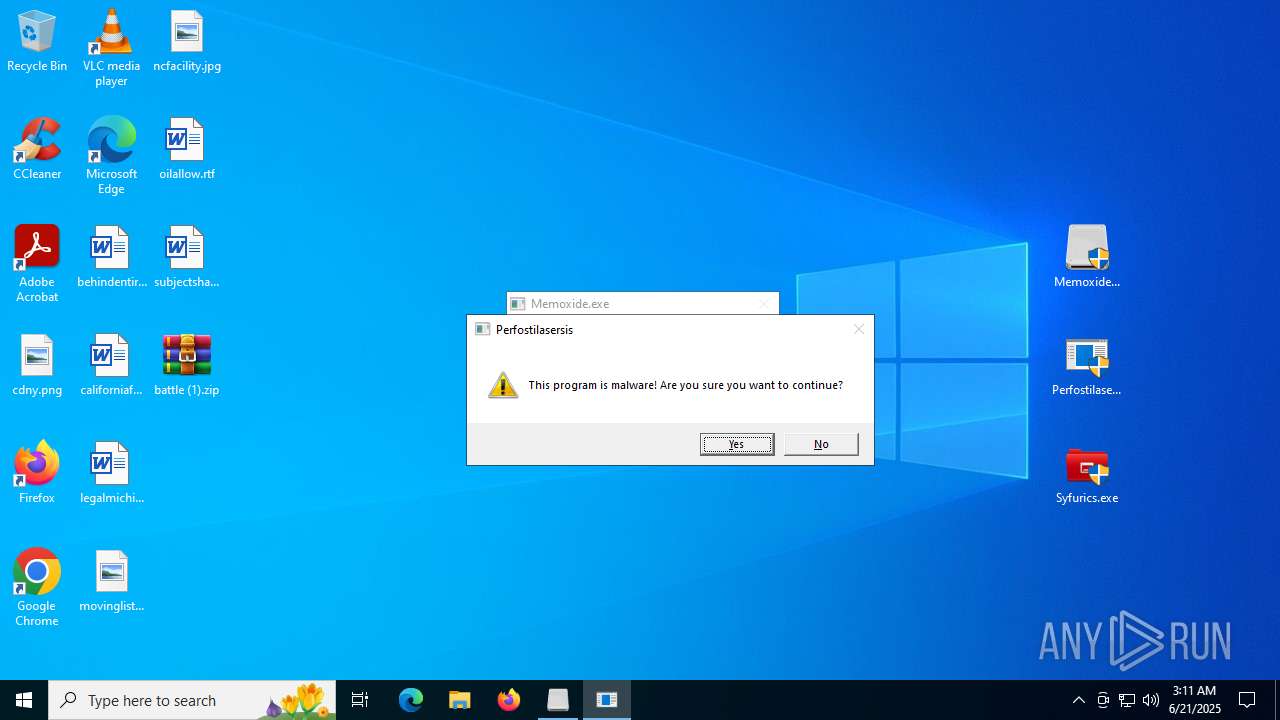
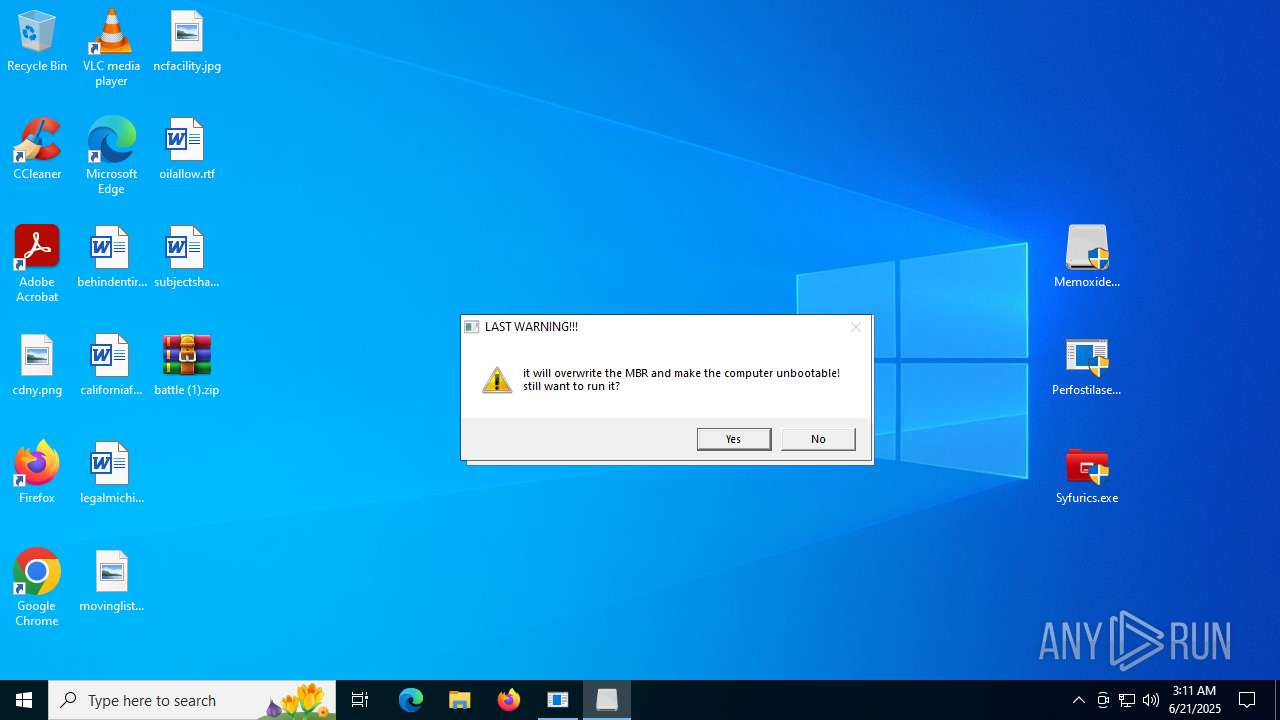
There is functionality for taking screenshot (YARA)
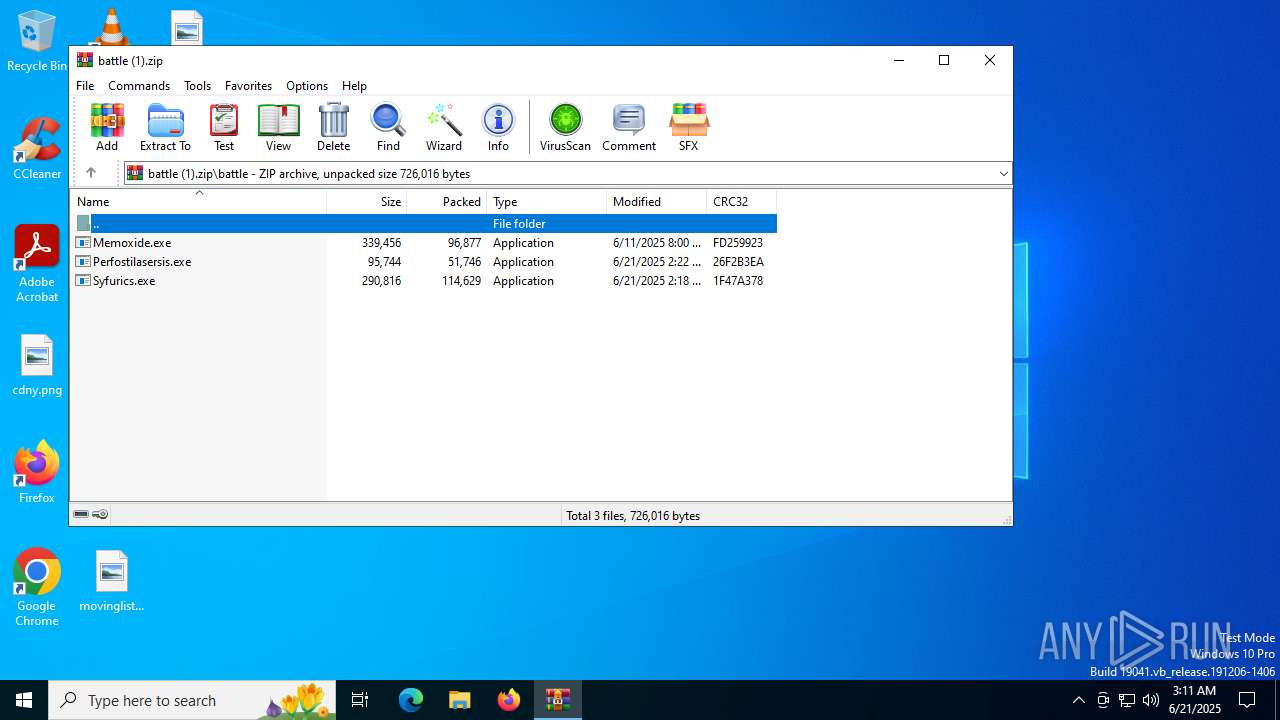
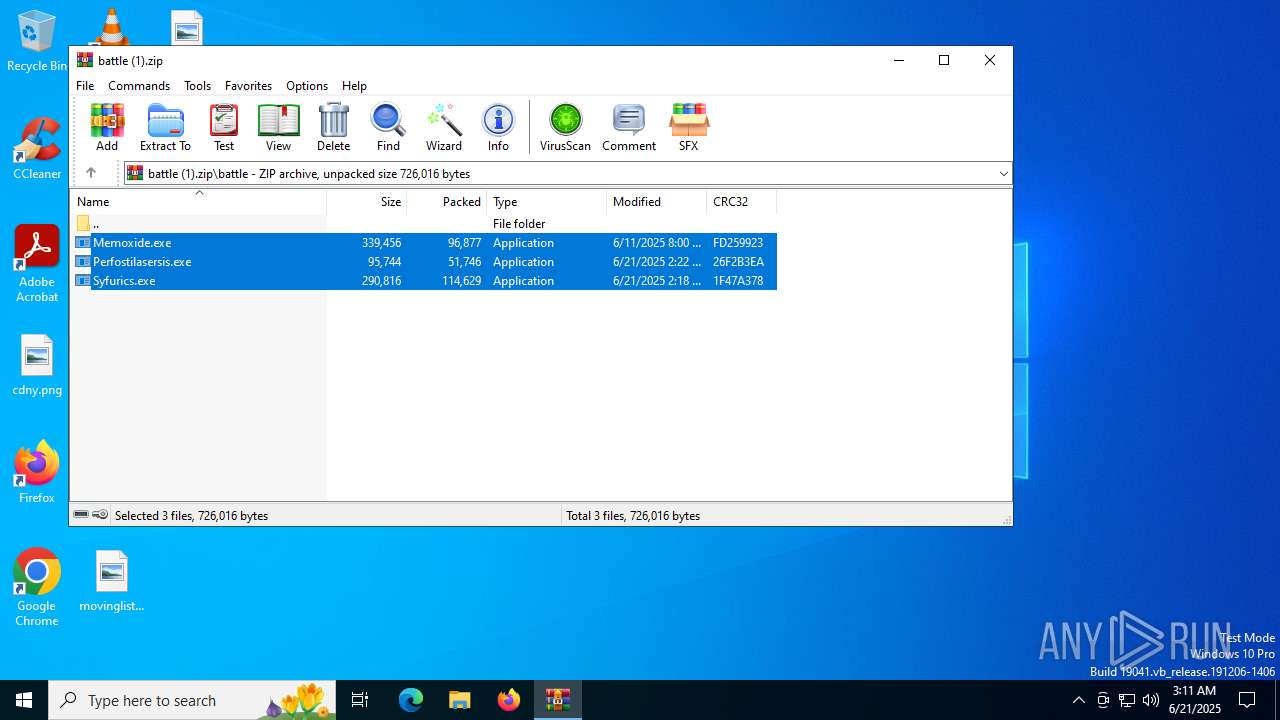
- Memoxide.exe (PID: 4156)
- Perfostilasersis.exe (PID: 3620)
- Syfurics.exe (PID: 6492)
Starts CMD.EXE for commands execution
- Memoxide.exe (PID: 4156)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3788)
- cmd.exe (PID: 5528)
INFO
Manual execution by a user
- Memoxide.exe (PID: 4960)
- Memoxide.exe (PID: 4156)
- Perfostilasersis.exe (PID: 1328)
- Perfostilasersis.exe (PID: 3620)
- Syfurics.exe (PID: 6492)
Checks supported languages
- Memoxide.exe (PID: 4156)
- Perfostilasersis.exe (PID: 3620)
- Syfurics.exe (PID: 6492)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2708)
Reads the computer name
- Memoxide.exe (PID: 4156)
- Perfostilasersis.exe (PID: 3620)
Checks proxy server information
- slui.exe (PID: 1380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 45 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:21 03:06:52 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 2 |
| ZipUncompressedSize: | - |
| ZipFileName: | battle/ |
Total processes
154
Monitored processes
13
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1328 | "C:\Users\admin\Desktop\Perfostilasersis.exe" | C:\Users\admin\Desktop\Perfostilasersis.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1380 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | REG ADD hkcu\Software\Microsoft\Windows\CurrentVersion\policies\system /v DisableTaskMgr /t reg_dword /d 1 /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2708 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\battle (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3108 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableRegistryTools /t REG_DWORD /d 1 /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | "C:\Users\admin\Desktop\Perfostilasersis.exe" | C:\Users\admin\Desktop\Perfostilasersis.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 3788 | C:\WINDOWS\system32\cmd.exe /c REG ADD hkcu\Software\Microsoft\Windows\CurrentVersion\policies\system /v DisableTaskMgr /t reg_dword /d 1 /f | C:\Windows\SysWOW64\cmd.exe | — | Memoxide.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4156 | "C:\Users\admin\Desktop\Memoxide.exe" | C:\Users\admin\Desktop\Memoxide.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 4680 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4960 | "C:\Users\admin\Desktop\Memoxide.exe" | C:\Users\admin\Desktop\Memoxide.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
2 362
Read events
2 342
Write events
20
Delete events
0
Modification events
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\battle (1).zip | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (2708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
3
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6492 | Syfurics.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 2708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2708.29458\battle\Syfurics.exe | executable | |
MD5:24D2A4B8A87A66F93F3EB54DB827791E | SHA256:2AA11C5484A870B694B48B22834C39AA3EE36A207DC1E2A136B98B8B553E09BE | |||
| 2708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2708.29458\battle\Memoxide.exe | executable | |
MD5:A349AB8E1679E3131CFCEFB0EBBEC958 | SHA256:5783B24D3D6EB613D07B06E83960B37E8C2FD4F52258FFE756186CB2EEEC4F4C | |||
| 2708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2708.29458\battle\Perfostilasersis.exe | executable | |
MD5:DB4888DCD466CC4ACE986340BA8396B5 | SHA256:C71D71894CAF89F158B10DE5ABA0AF0E69DC5EAE05581778740B2C618B4540F4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report