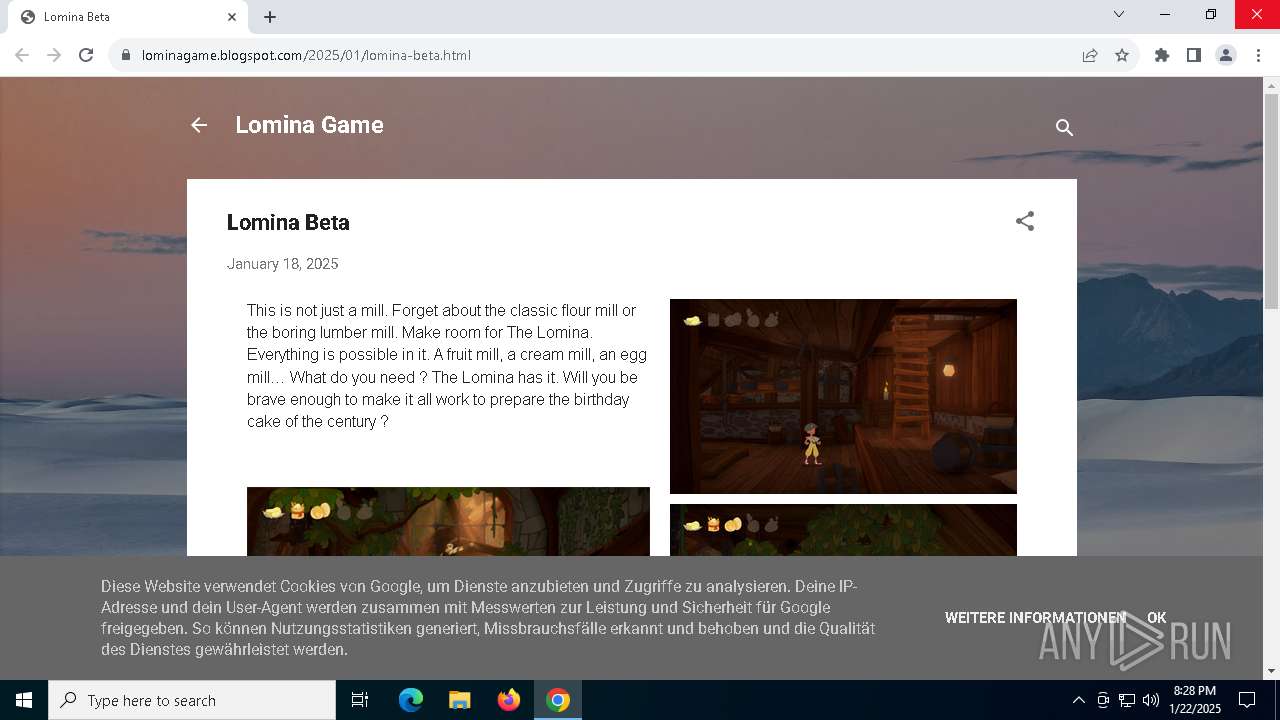
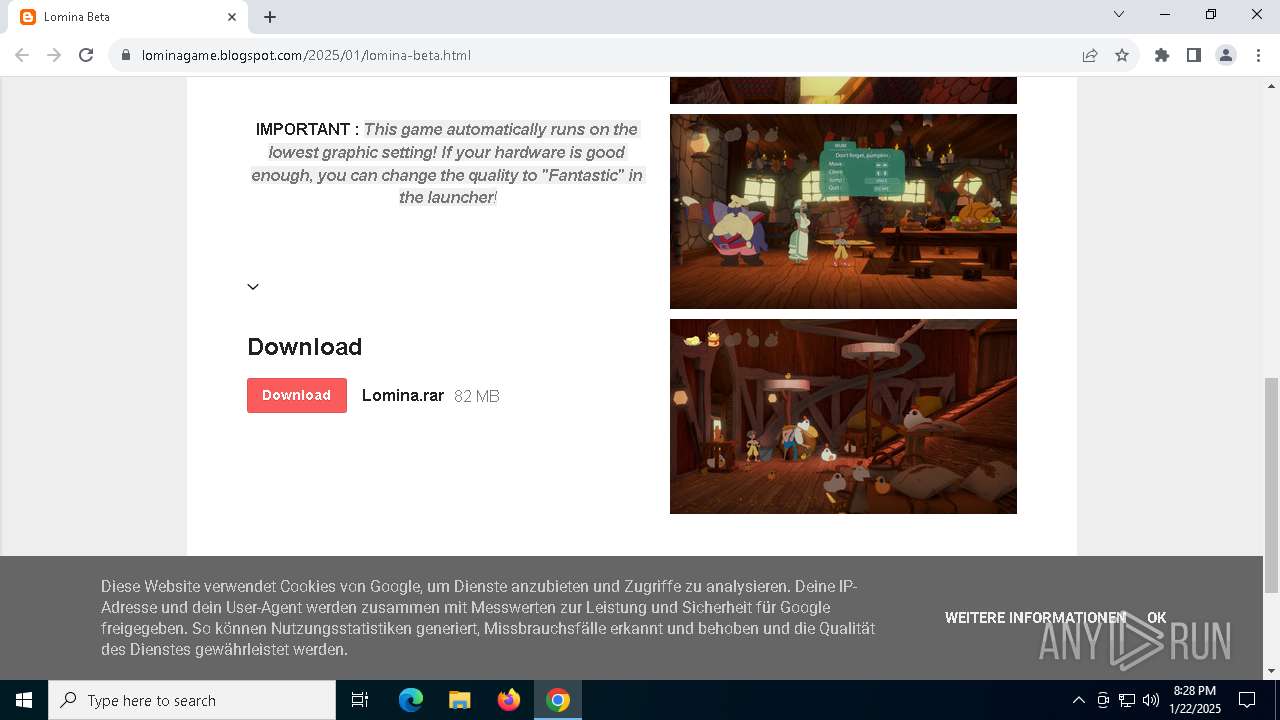
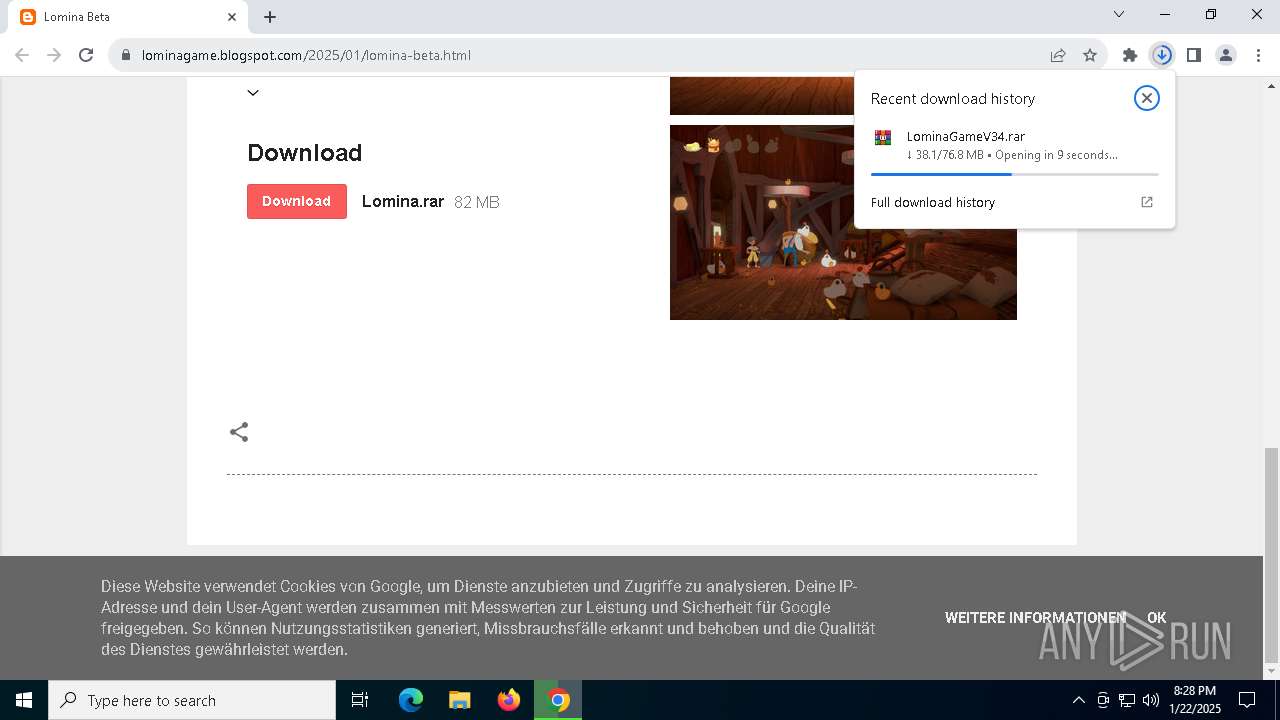
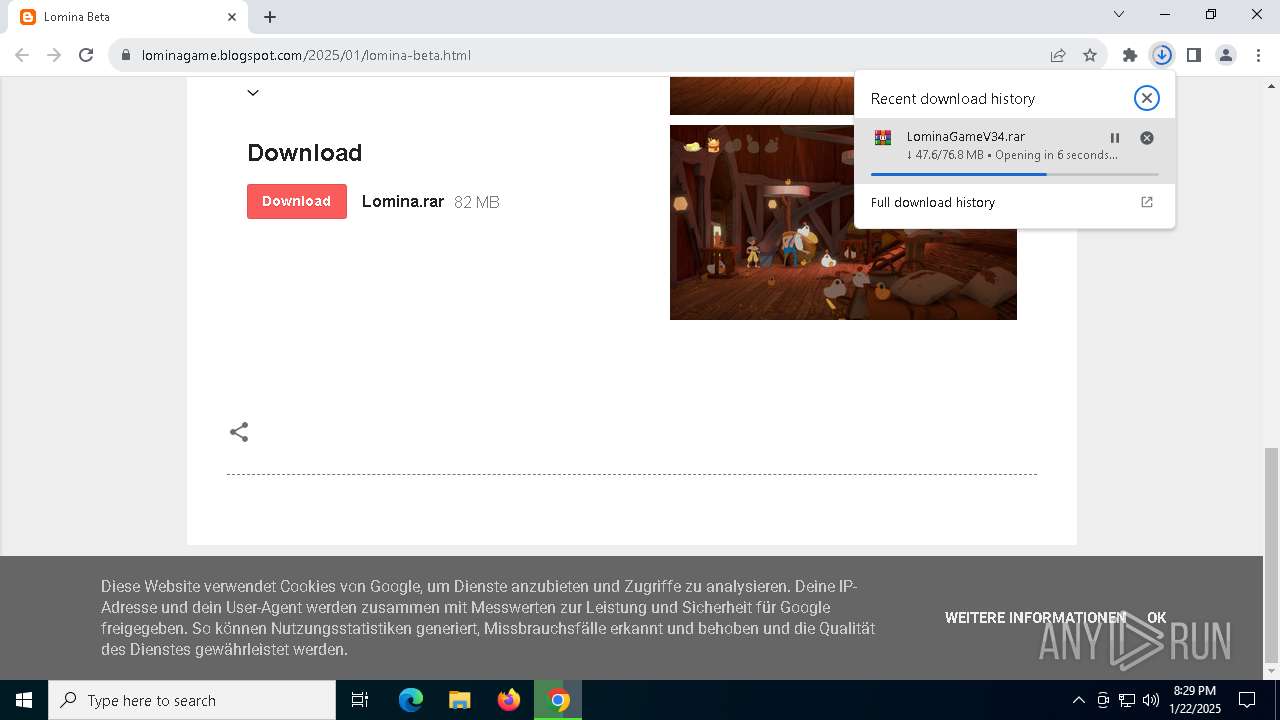
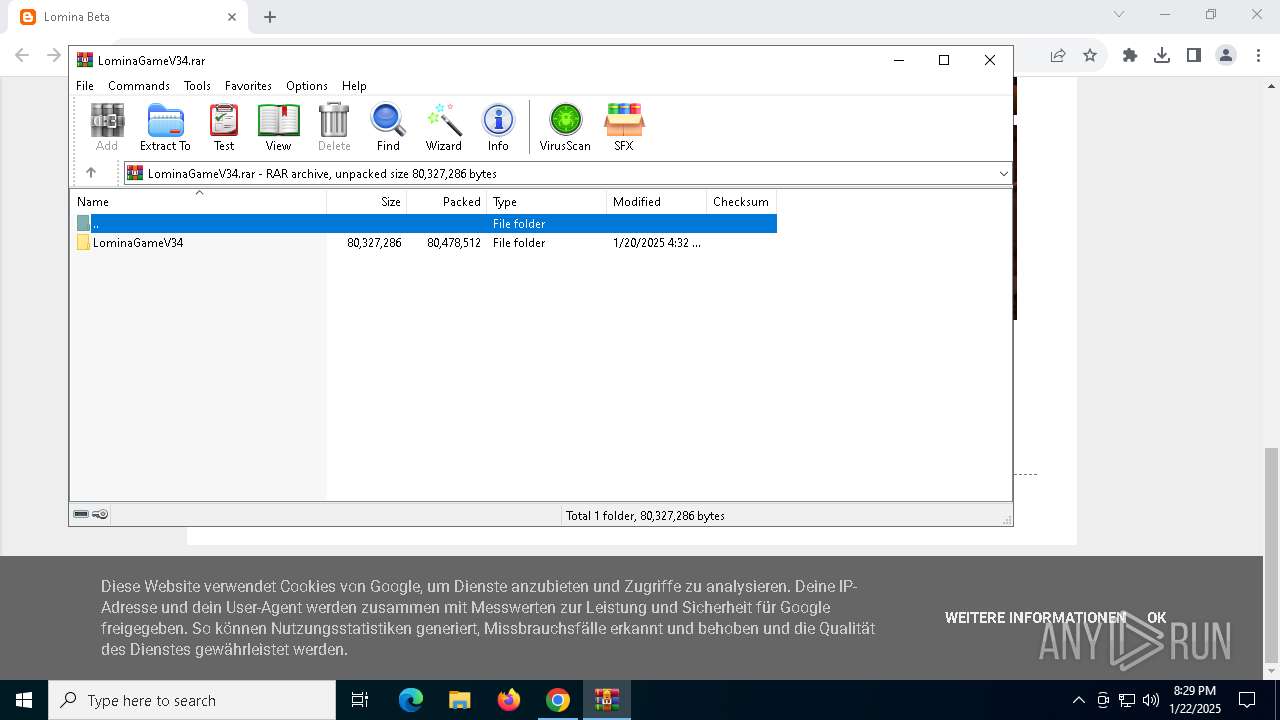
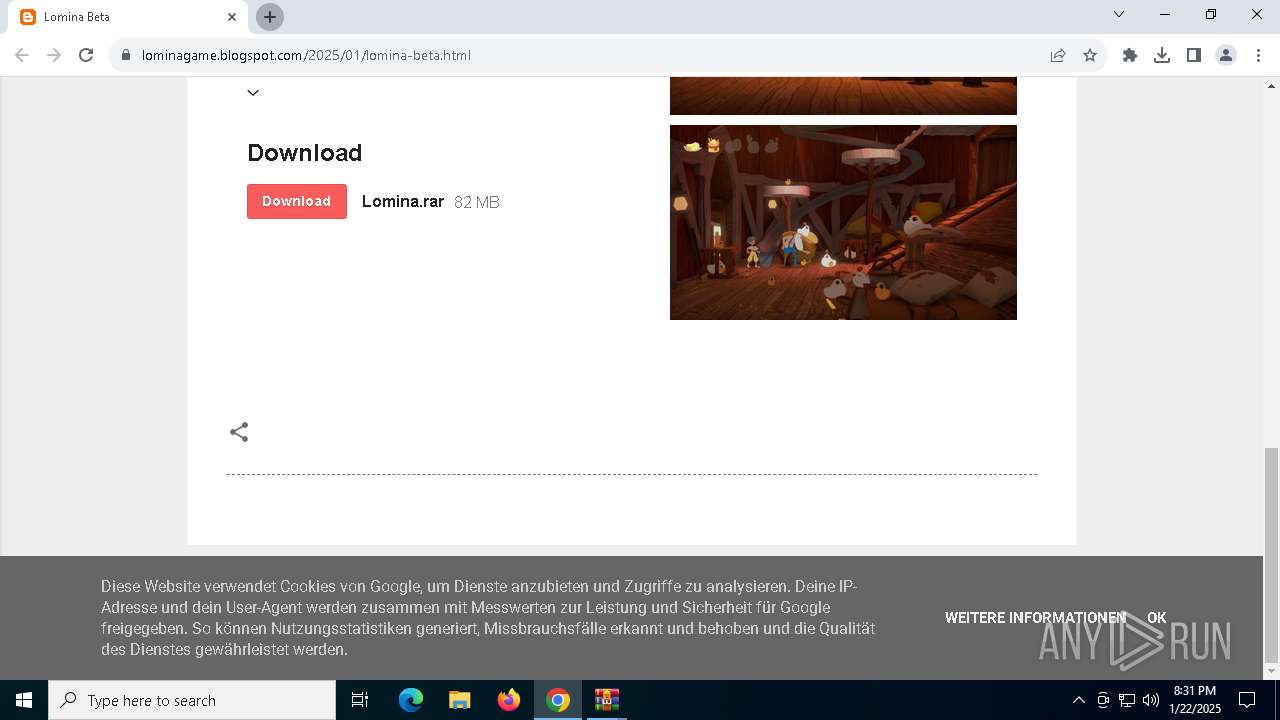
| URL: | https://lominagame.blogspot.com/2025/01/lomina-beta.html |
| Full analysis: | https://app.any.run/tasks/ddb50afb-fc81-439d-b14e-8329cd65ca94 |
| Verdict: | Malicious activity |
| Analysis date: | January 22, 2025, 20:28:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C331D5D21C9142822B6FAF671A6AC5F6 |
| SHA1: | C333A0448CD0D3E93C05F92F2FBB7F66C75FBF56 |
| SHA256: | 5512B4AEA3450382B9C65995E86A40796ABE8F5F05D896B32B893C489CA0DAF9 |
| SSDEEP: | 3:N8KFeZzKMy75PgoNuJ:2K+zKVIoUJ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
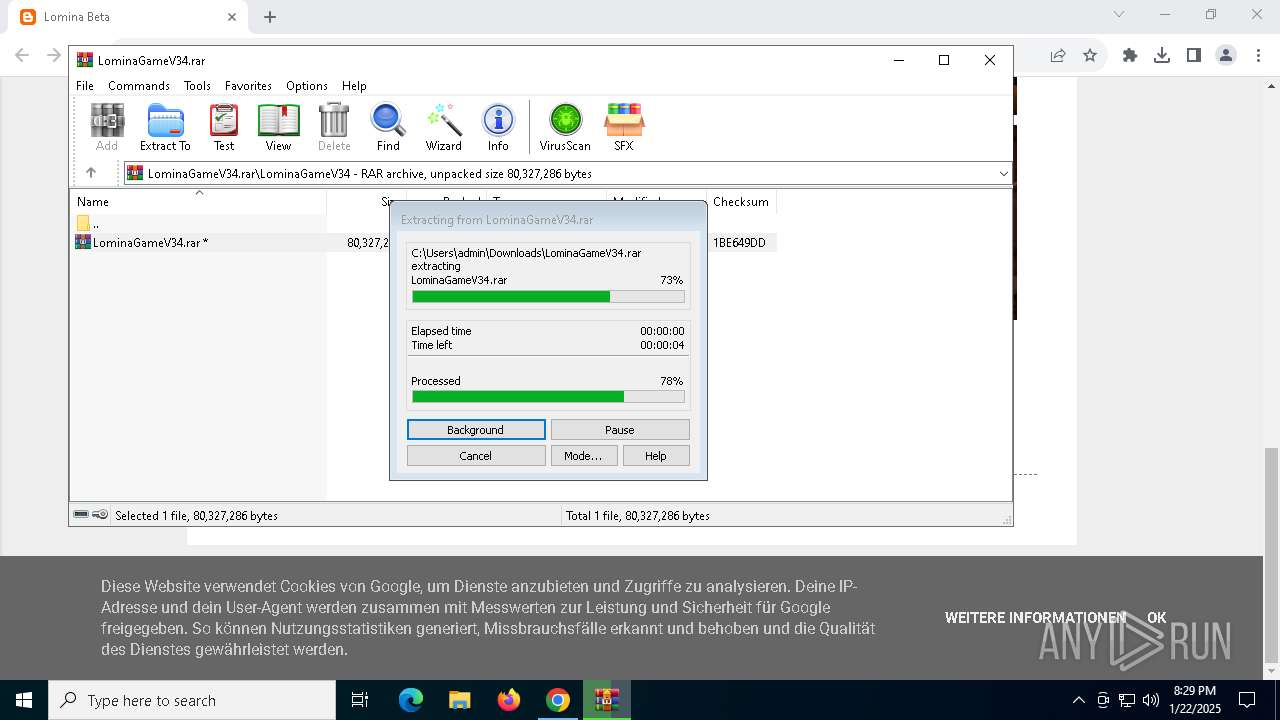
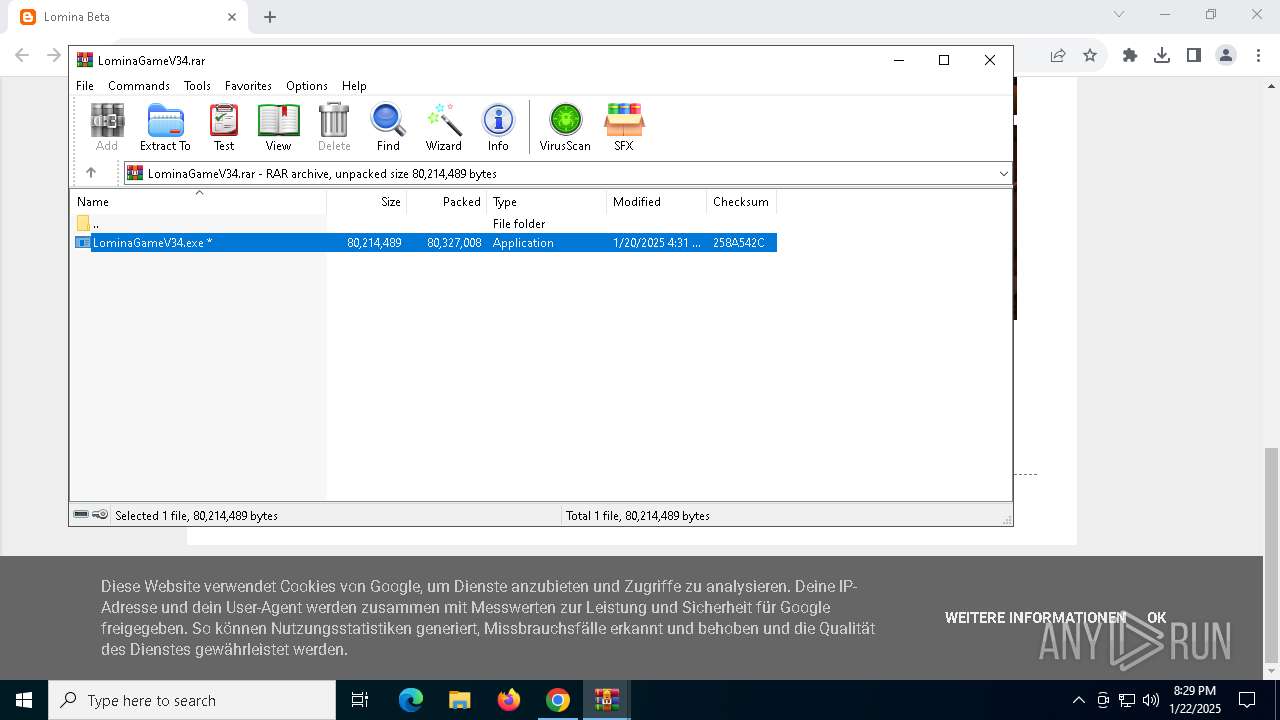
- WinRAR.exe (PID: 3080)
- WinRAR.exe (PID: 6848)
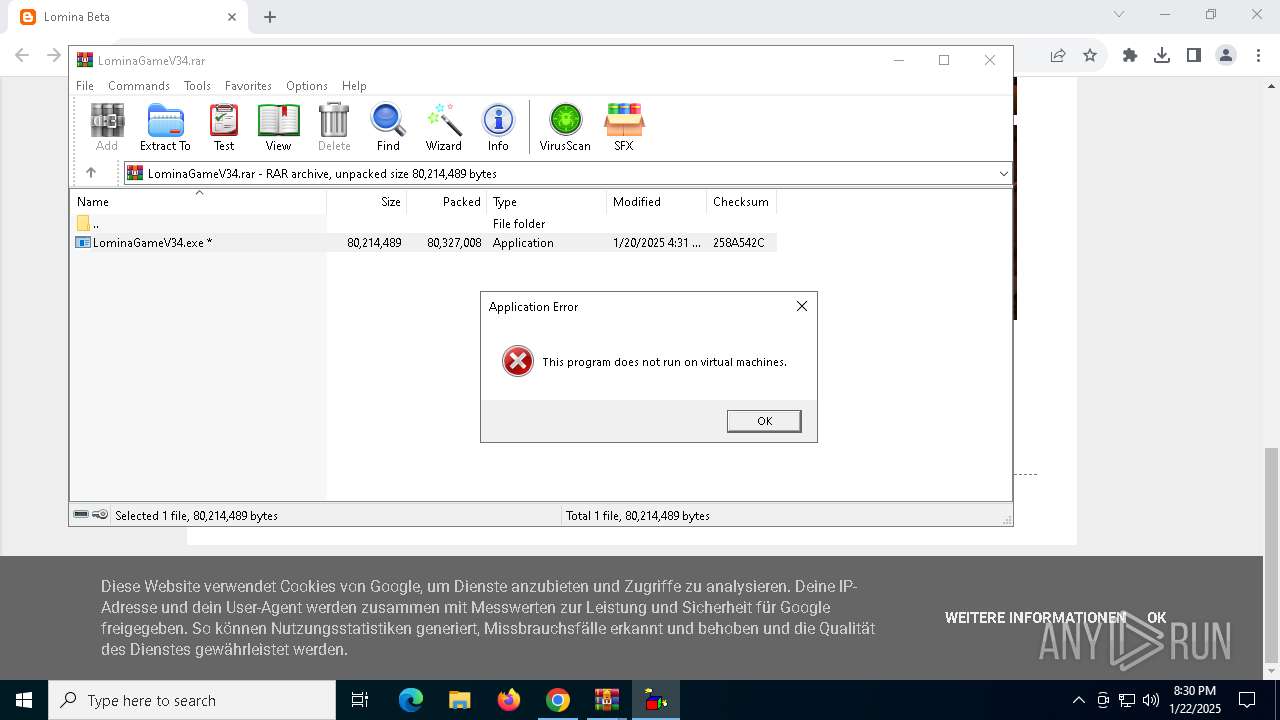
- LominaGameV34.exe (PID: 3416)
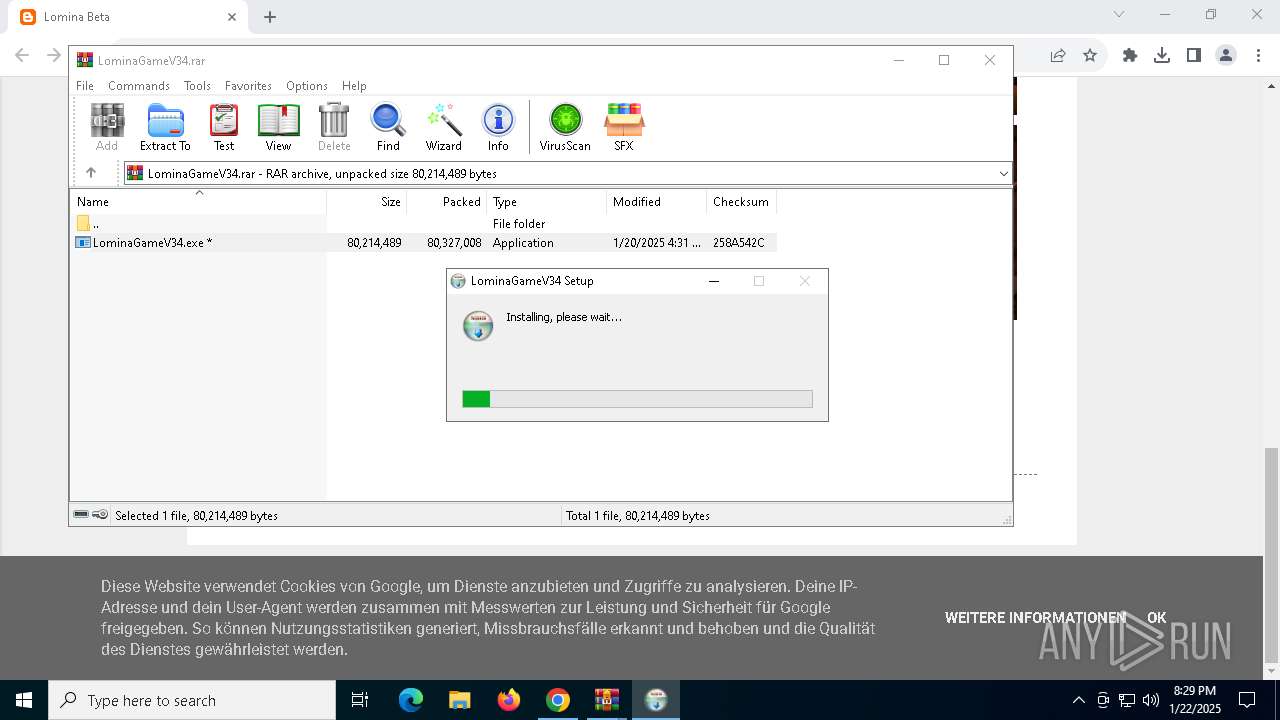
Application launched itself
- WinRAR.exe (PID: 3080)
- LominaGameV34.exe (PID: 7060)
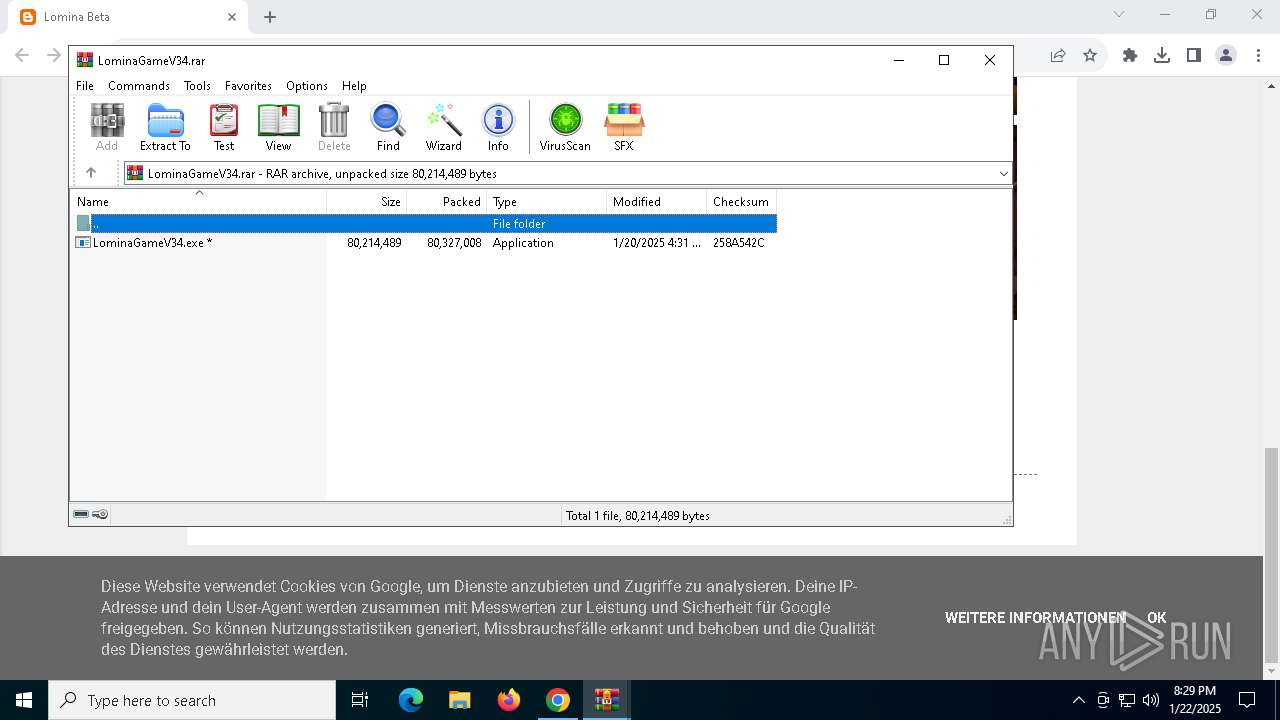
The process creates files with name similar to system file names
- LominaGameV34.exe (PID: 3416)
Executable content was dropped or overwritten
- LominaGameV34.exe (PID: 3416)
Malware-specific behavior (creating "System.dll" in Temp)
- LominaGameV34.exe (PID: 3416)
Process drops legitimate windows executable
- LominaGameV34.exe (PID: 3416)
Drops 7-zip archiver for unpacking
- LominaGameV34.exe (PID: 3416)
There is functionality for taking screenshot (YARA)
- LominaGameV34.exe (PID: 3416)
Starts CMD.EXE for commands execution
- LominaGameV34.exe (PID: 7060)
Get information on the list of running processes
- cmd.exe (PID: 1572)
- LominaGameV34.exe (PID: 7060)
Uses WMIC.EXE to obtain BIOS management information
- cmd.exe (PID: 3888)
Uses WMIC.EXE to obtain memory chip information
- cmd.exe (PID: 6980)
The process executes VB scripts
- cmd.exe (PID: 6028)
Checks for external IP
- curl.exe (PID: 6840)
INFO
Application launched itself
- chrome.exe (PID: 6184)
- chrome.exe (PID: 6384)
Manual execution by a user
- chrome.exe (PID: 6384)
- LominaGameV34.exe (PID: 7060)
The process uses the downloaded file
- chrome.exe (PID: 6900)
- WinRAR.exe (PID: 6848)
- WinRAR.exe (PID: 3080)
- chrome.exe (PID: 6184)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6184)
Checks supported languages
- LominaGameV34.exe (PID: 3416)
- LominaGameV34.exe (PID: 7060)
- LominaGameV34.exe (PID: 4840)
- LominaGameV34.exe (PID: 1348)
- curl.exe (PID: 6840)
Create files in a temporary directory
- LominaGameV34.exe (PID: 3416)
- LominaGameV34.exe (PID: 7060)
The sample compiled with english language support
- LominaGameV34.exe (PID: 3416)
Reads the computer name
- LominaGameV34.exe (PID: 3416)
- LominaGameV34.exe (PID: 7060)
- curl.exe (PID: 6840)
- LominaGameV34.exe (PID: 4840)
- LominaGameV34.exe (PID: 1348)
Creates files or folders in the user directory
- LominaGameV34.exe (PID: 3416)
- LominaGameV34.exe (PID: 7060)
Checks proxy server information
- LominaGameV34.exe (PID: 7060)
Reads the machine GUID from the registry
- LominaGameV34.exe (PID: 7060)
Execution of CURL command
- cmd.exe (PID: 4912)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6896)
- WMIC.exe (PID: 3208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
183
Monitored processes
49
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=19 --mojo-platform-channel-handle=5660 --field-trial-handle=1904,i,14609624703218587933,7264483824575390054,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1348 | "C:\Users\admin\AppData\Local\Programs\unrealgame\LominaGameV34.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --user-data-dir="C:\Users\admin\AppData\Roaming\unrealgame" --mojo-platform-channel-handle=2100 --field-trial-handle=1920,i,1098787564749685849,17485210182077261806,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand /prefetch:8 | C:\Users\admin\AppData\Local\Programs\unrealgame\LominaGameV34.exe | — | LominaGameV34.exe | |||||||||||
User: admin Company: Unreal Game Inc. Integrity Level: MEDIUM Description: LominaGameV34 Exit code: 0 Version: 1.0.0 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=4760 --field-trial-handle=1904,i,14609624703218587933,7264483824575390054,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1480 | wscript "C:\Users\admin\AppData\Local\Temp\fakeError_xbisj6la5m.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1572 | C:\WINDOWS\system32\cmd.exe /d /s /c "tasklist" | C:\Windows\System32\cmd.exe | — | LominaGameV34.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1944 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2092 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=4752 --field-trial-handle=1904,i,14609624703218587933,7264483824575390054,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2976 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --mojo-platform-channel-handle=3448 --field-trial-handle=1904,i,14609624703218587933,7264483824575390054,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3080 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\LominaGameV34.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | chrome.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3208 | wmic MemoryChip get /format:list | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 459
Read events
14 392
Write events
60
Delete events
7
Modification events
| (PID) Process: | (6184) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6184) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6184) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6184) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6384) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6384) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6384) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6184) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6184) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithProgids |
| Operation: | write | Name: | WinRAR |
Value: | |||
| (PID) Process: | (6900) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 010000000000000021B4A74A0C6DDB01 | |||
Executable files
25
Suspicious files
256
Text files
74
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6184 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF13b019.TMP | — | |
MD5:— | SHA256:— | |||
| 6184 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF13b019.TMP | — | |
MD5:— | SHA256:— | |||
| 6184 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6184 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6184 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF13b019.TMP | — | |
MD5:— | SHA256:— | |||
| 6184 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6184 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF13b029.TMP | — | |
MD5:— | SHA256:— | |||
| 6184 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6184 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF13b038.TMP | — | |
MD5:— | SHA256:— | |||
| 6184 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF13b038.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
111
DNS requests
114
Threats
26
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6148 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
2132 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6148 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
6840 | curl.exe | GET | 200 | 172.67.74.152:80 | http://api.ipify.org/ | unknown | — | — | malicious |
6148 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2132 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3560 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 2.23.227.215:443 | — | Ooredoo Q.S.C. | QA | unknown |
5064 | SearchApp.exe | 2.23.227.215:443 | — | Ooredoo Q.S.C. | QA | unknown |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6184 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
lominagame.blogspot.com |
| whitelisted |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
6840 | curl.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
6840 | curl.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
6840 | curl.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
6556 | chrome.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
6556 | chrome.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
6556 | chrome.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
6556 | chrome.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
6556 | chrome.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
6556 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |