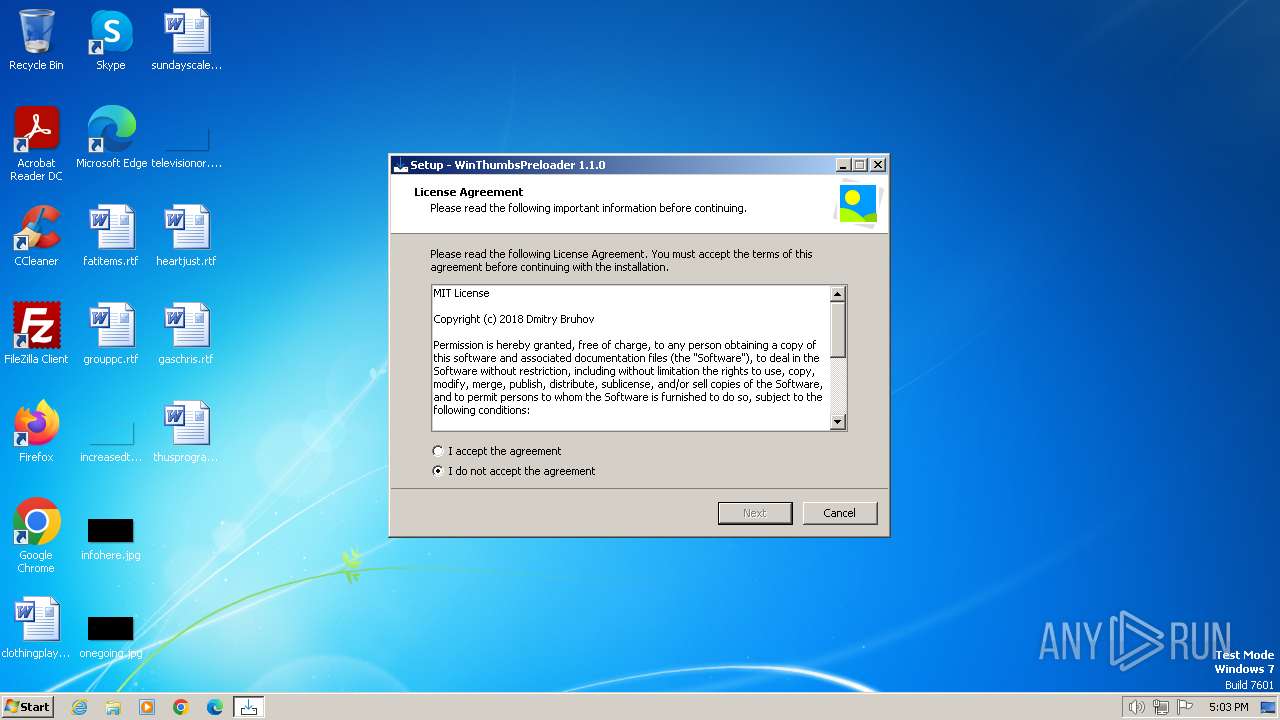
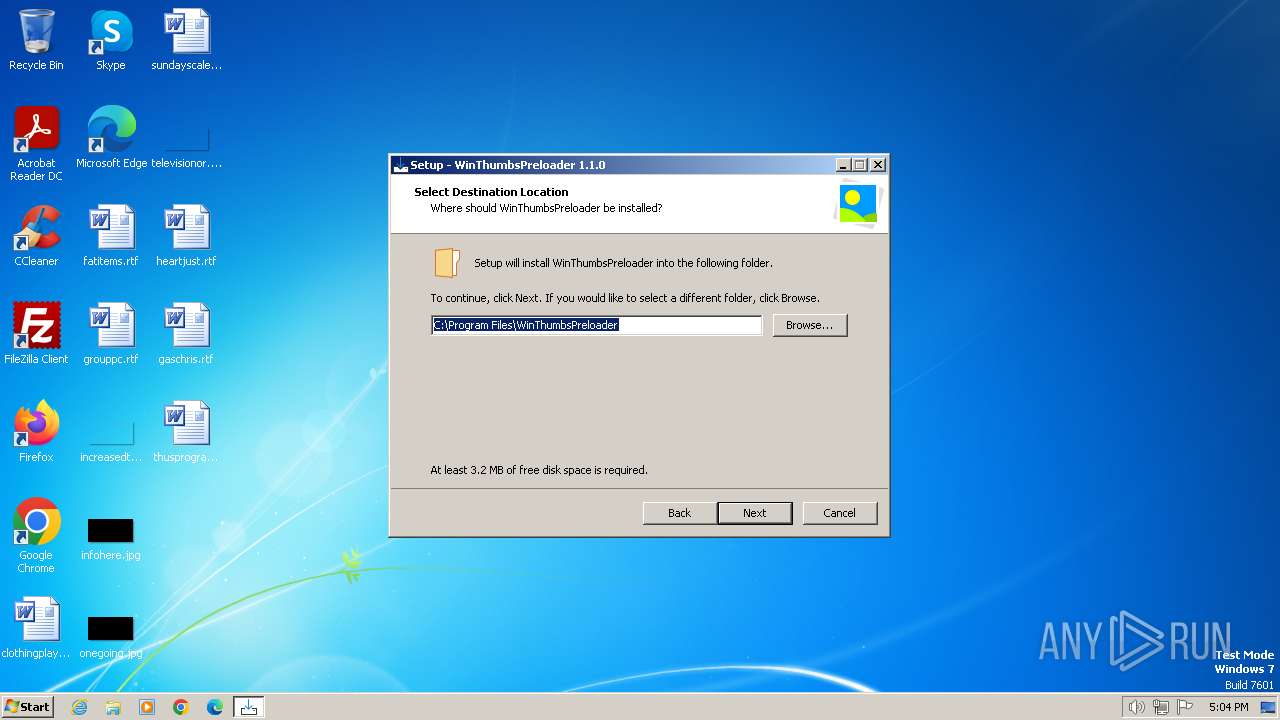
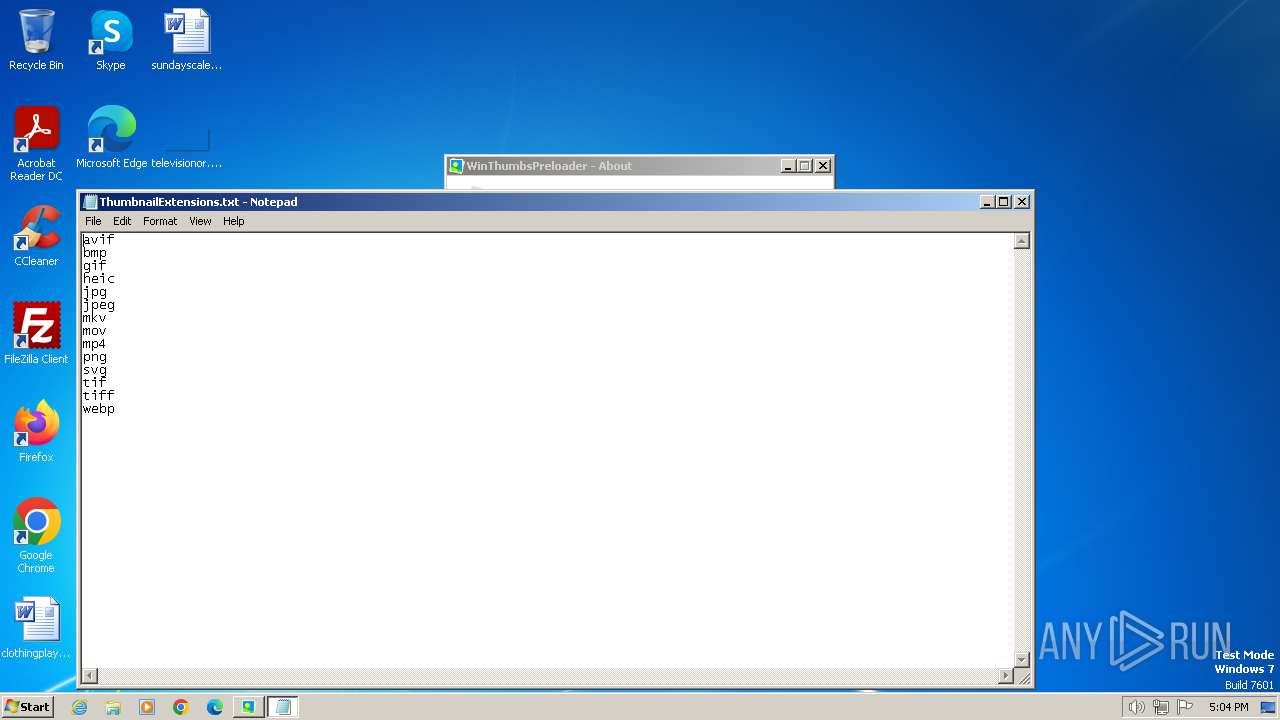
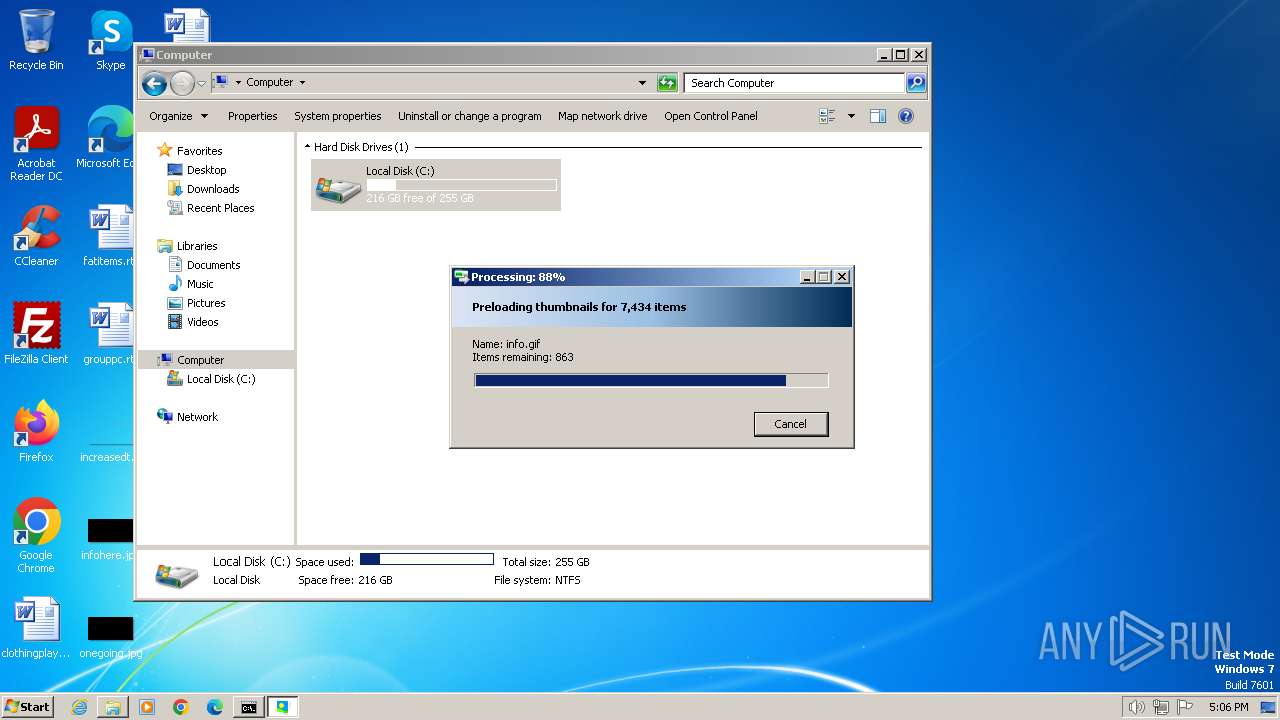
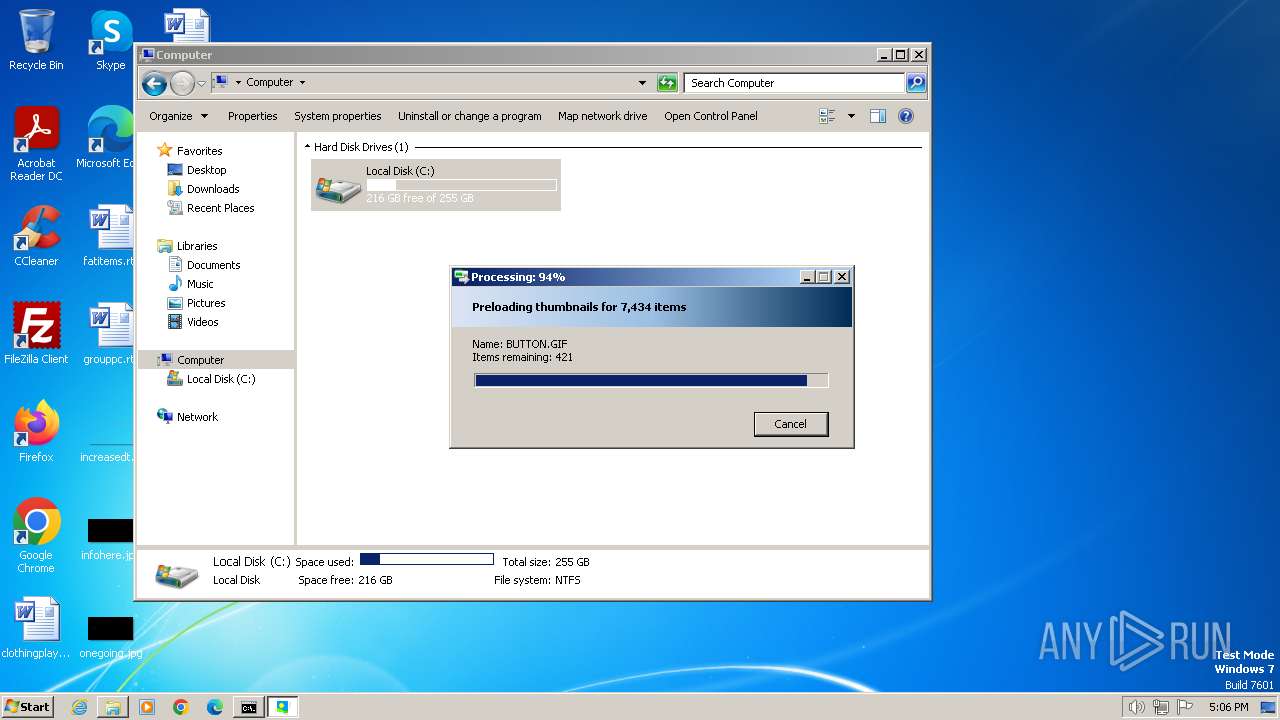
| File name: | WinThumbsPreloader-1.1.0-setup.exe |
| Full analysis: | https://app.any.run/tasks/8a629b60-2d5b-4117-af3f-877f049dabca |
| Verdict: | Malicious activity |
| Analysis date: | January 23, 2024, 17:03:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 02506D32266F22F1960F08A63F1DCA4F |
| SHA1: | 75D1E8A35BCA7970DFBDDE0344F543A7472EB464 |
| SHA256: | 54E7F711788EE71D71BA7F5D80E92FE7C340CF55524282480F4D2F4025ED6227 |
| SSDEEP: | 49152:+7HecD4dnbibBlscjsbmLApne0Fop4R2uXB3iyLT/ex4XrL7P42DpJXWZn80cweb:m+cD4dnNcIkWnXFopLQ3iUrex4vkY7mw |
MALICIOUS
Drops the executable file immediately after the start
- WinThumbsPreloader-1.1.0-setup.exe (PID: 2580)
- WinThumbsPreloader-1.1.0-setup.exe (PID: 2100)
- WinThumbsPreloader-1.1.0-setup.tmp (PID: 1268)
Actions looks like stealing of personal data
- WinThumbsPreloader.exe (PID: 2784)
SUSPICIOUS
Executable content was dropped or overwritten
- WinThumbsPreloader-1.1.0-setup.exe (PID: 2100)
- WinThumbsPreloader-1.1.0-setup.exe (PID: 2580)
- WinThumbsPreloader-1.1.0-setup.tmp (PID: 1268)
Reads the Windows owner or organization settings
- WinThumbsPreloader-1.1.0-setup.tmp (PID: 1268)
Reads the Internet Settings
- WinThumbsPreloader.exe (PID: 2320)
Reads settings of System Certificates
- WinThumbsPreloader.exe (PID: 2320)
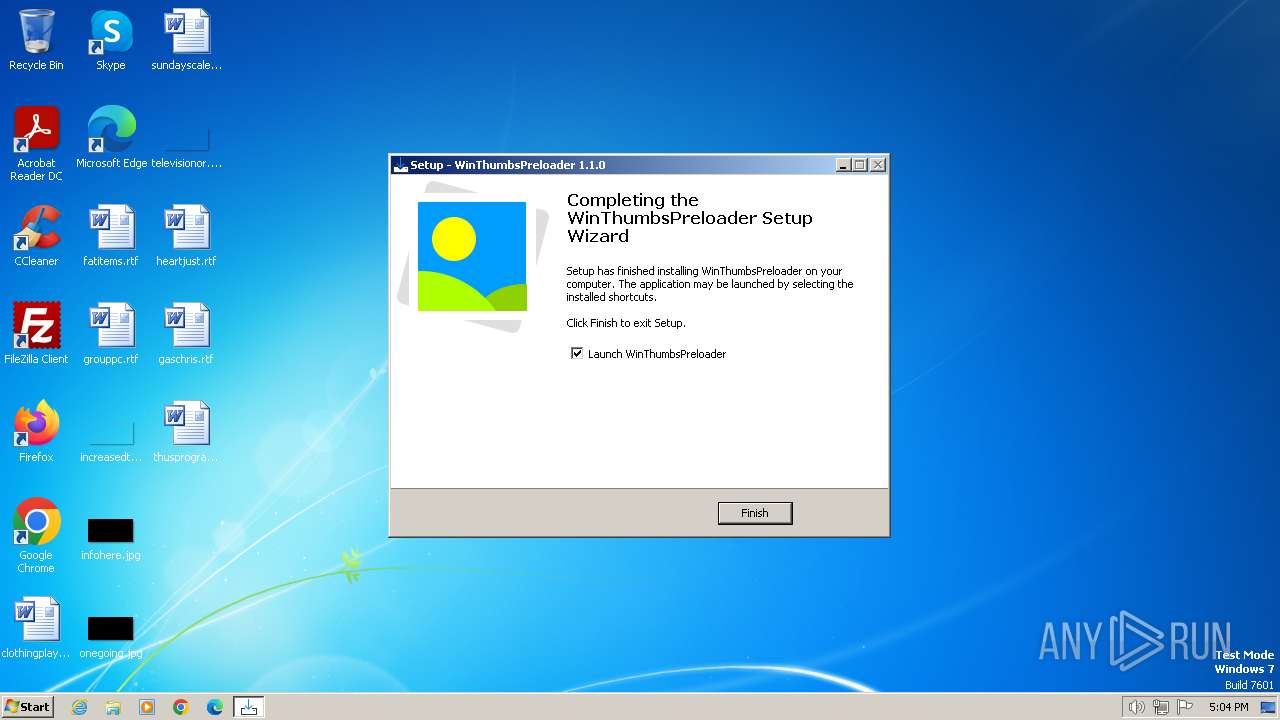
Start notepad (likely ransomware note)
- WinThumbsPreloader.exe (PID: 2320)
Application launched itself
- cmd.exe (PID: 2496)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2496)
INFO
Create files in a temporary directory
- WinThumbsPreloader-1.1.0-setup.exe (PID: 2100)
- WinThumbsPreloader-1.1.0-setup.exe (PID: 2580)
Checks supported languages
- WinThumbsPreloader-1.1.0-setup.exe (PID: 2580)
- WinThumbsPreloader-1.1.0-setup.exe (PID: 2100)
- WinThumbsPreloader-1.1.0-setup.tmp (PID: 2808)
- WinThumbsPreloader-1.1.0-setup.tmp (PID: 1268)
- WinThumbsPreloader.exe (PID: 2320)
- WinThumbsPreloader.exe (PID: 2784)
Reads the computer name
- WinThumbsPreloader-1.1.0-setup.tmp (PID: 2808)
- WinThumbsPreloader-1.1.0-setup.tmp (PID: 1268)
- WinThumbsPreloader.exe (PID: 2320)
- WinThumbsPreloader.exe (PID: 2784)
Creates files in the program directory
- WinThumbsPreloader-1.1.0-setup.tmp (PID: 1268)
- WinThumbsPreloader.exe (PID: 2320)
Reads the machine GUID from the registry
- WinThumbsPreloader.exe (PID: 2320)
- WinThumbsPreloader.exe (PID: 2784)
Reads Environment values
- WinThumbsPreloader.exe (PID: 2320)
Manual execution by a user
- explorer.exe (PID: 2620)
- cmd.exe (PID: 2496)
- WinThumbsPreloader.exe (PID: 2124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 15:54:16+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.1.0.0 |
| ProductVersionNumber: | 1.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Dmitry Bruhov, inthebrilliantblue, arturdd, Mfarooq360 |
| FileDescription: | WinThumbsPreloader Setup |
| FileVersion: | 1.1.0 |
| LegalCopyright: | Copyright (c) 2023 Dmitry Bruhov, inthebrilliantblue, arturdd, Mfarooq360 |
| OriginalFileName: | |
| ProductName: | WinThumbsPreloader |
| ProductVersion: | 1.1.0 |
Total processes
55
Monitored processes
11
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1268 | "C:\Users\admin\AppData\Local\Temp\is-VH6O5.tmp\WinThumbsPreloader-1.1.0-setup.tmp" /SL5="$E0176,861122,832512,C:\Users\admin\AppData\Local\Temp\WinThumbsPreloader-1.1.0-setup.exe" /SPAWNWND=$1700E6 /NOTIFYWND=$8010A | C:\Users\admin\AppData\Local\Temp\is-VH6O5.tmp\WinThumbsPreloader-1.1.0-setup.tmp | WinThumbsPreloader-1.1.0-setup.exe | ||||||||||||
User: admin Company: Dmitry Bruhov, inthebrilliantblue, arturdd, Mfarooq360 Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1576 | "C:\Windows\system32\NOTEPAD.EXE" C:\Program Files\WinThumbsPreloader\ThumbnailExtensions.txt | C:\Windows\System32\notepad.exe | — | WinThumbsPreloader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2100 | "C:\Users\admin\AppData\Local\Temp\WinThumbsPreloader-1.1.0-setup.exe" /SPAWNWND=$1700E6 /NOTIFYWND=$8010A | C:\Users\admin\AppData\Local\Temp\WinThumbsPreloader-1.1.0-setup.exe | WinThumbsPreloader-1.1.0-setup.tmp | ||||||||||||
User: admin Company: Dmitry Bruhov, inthebrilliantblue, arturdd, Mfarooq360 Integrity Level: HIGH Description: WinThumbsPreloader Setup Exit code: 0 Version: 1.1.0 Modules
| |||||||||||||||
| 2124 | "C:\Program Files\WinThumbsPreloader\WinThumbsPreloader.exe" -m -r "C:\Users\admin\Downloads" | C:\Program Files\WinThumbsPreloader\WinThumbsPreloader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: WinThumbsPreloader Exit code: 0 Version: 1.1.0 | |||||||||||||||
| 2320 | "C:\Program Files\WinThumbsPreloader\WinThumbsPreloader.exe" | C:\Program Files\WinThumbsPreloader\WinThumbsPreloader.exe | WinThumbsPreloader-1.1.0-setup.tmp | ||||||||||||
User: admin Integrity Level: HIGH Description: WinThumbsPreloader Exit code: 0 Version: 1.1.0 Modules
| |||||||||||||||
| 2496 | "cmd.exe" /c start /min cmd /c "WinThumbsPreloader.exe -m -r C:\ | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2580 | "C:\Users\admin\AppData\Local\Temp\WinThumbsPreloader-1.1.0-setup.exe" | C:\Users\admin\AppData\Local\Temp\WinThumbsPreloader-1.1.0-setup.exe | explorer.exe | ||||||||||||
User: admin Company: Dmitry Bruhov, inthebrilliantblue, arturdd, Mfarooq360 Integrity Level: MEDIUM Description: WinThumbsPreloader Setup Exit code: 0 Version: 1.1.0 Modules
| |||||||||||||||
| 2620 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2784 | WinThumbsPreloader.exe -m -r C:\ | C:\Program Files\WinThumbsPreloader\WinThumbsPreloader.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: WinThumbsPreloader Exit code: 0 Version: 1.1.0 Modules
| |||||||||||||||
| 2808 | "C:\Users\admin\AppData\Local\Temp\is-HGC9H.tmp\WinThumbsPreloader-1.1.0-setup.tmp" /SL5="$8010A,861122,832512,C:\Users\admin\AppData\Local\Temp\WinThumbsPreloader-1.1.0-setup.exe" | C:\Users\admin\AppData\Local\Temp\is-HGC9H.tmp\WinThumbsPreloader-1.1.0-setup.tmp | — | WinThumbsPreloader-1.1.0-setup.exe | |||||||||||
User: admin Company: Dmitry Bruhov, inthebrilliantblue, arturdd, Mfarooq360 Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
10 575
Read events
10 551
Write events
18
Delete events
6
Modification events
| (PID) Process: | (1268) WinThumbsPreloader-1.1.0-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager\Environment |
| Operation: | write | Name: | Path |
Value: C:\Program Files\Common Files\Oracle\Java\javapath;C:\ProgramData\Oracle\Java\javapath;%SystemRoot%\system32;%SystemRoot%;%SystemRoot%\System32\Wbem;%SYSTEMROOT%\System32\WindowsPowerShell\v1.0\;%systemroot%\System32\WindowsPowerShell\v1.0\;C:\Program Files\PowerShell\7\;%systemroot%\System32\WindowsPowerShell\v1.0\ | |||
| (PID) Process: | (1268) WinThumbsPreloader-1.1.0-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: 1F3DEBD499C6C7B5F9946E63719BE9C3596BE4FF2CDC93BC044E218DD786B4A2 | |||
| (PID) Process: | (1268) WinThumbsPreloader-1.1.0-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFiles0000 |
Value: C:\Program Files\WinThumbsPreloader\WinThumbsPreloader.exe | |||
| (PID) Process: | (1268) WinThumbsPreloader-1.1.0-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (1268) WinThumbsPreloader-1.1.0-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: 0B929A4432C1CF2AC71834BAAB2D49FA6AF66D02DC08C3F855FFF91D90756B89 | |||
| (PID) Process: | (1268) WinThumbsPreloader-1.1.0-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: F404000090832F241E4EDA01 | |||
| (PID) Process: | (1268) WinThumbsPreloader-1.1.0-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2320) WinThumbsPreloader.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2320) WinThumbsPreloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates\9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
| Operation: | write | Name: | Blob |
Value: 0300000001000000140000009F6134C5FA75E4FDDE631B232BE961D6D4B97DB6200000000100000047030000308203433082022BA00302010202147327B7C17D5AE708EF73F1F45A79D78B4E99A29F300D06092A864886F70D01010B05003031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C084469676943657274301E170D3233303932393130353030335A170D3339303530383130353030335A3031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C08446967694365727430820122300D06092A864886F70D01010105000382010F003082010A0282010100D91B7A55548F44F3E97C493153B75B055695736B184640D7335A2E6218083B5A1BEE2695209350E57A3EB76FBC604CB3B250DF3D9D0C560D1FBDFE30108D233A3C555100BE1A3F8E543C0B253E06E91B6D5F9CB3A093009BC8B4D3A0EB19DB59E56DA7E3D637847970D6C2AEB4A1FCF3896A7C080FE68759BAA62E6AAA8B7C7CBDA176DDC72F8D259A16D3469E31F19D2959904611D730D7D26FCFED789A0C49698FDFABF3F6727D08C61A073BB11E85C96486D49B0E0D38364C008A5EB964F8813C5DF004F9E76D2F8DB90702D800032674959BF0DF823785419101CEA928A10ACBAE7E48FE19202F3CB7BCF416476D17CB64C5570FCED443BD75D9F2C632FF0203010001A3533051301D0603551D0E041604145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7301F0603551D230418301680145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7300F0603551D130101FF040530030101FF300D06092A864886F70D01010B05000382010100AF2218E4CA18144728FCC76EA14958061522FD4A018BED1A4BFCC5CCE70BC6AE9DF7D3795C9A010D53628E2B6E7C10D6B07E53546235A5EE480E5A434E312154BF1E39AAC27D2C18D4F41CBBECFE4538CEF93EF62C17D187A7F720F4A9478410D09620C9F8B293B5786A5440BC0743B7B7753CF66FBA498B7E083BC267597238DC031B9BB131F997D9B8164AAED0D6E328420E53E1969DA6CD035078179677A7177BB2BF9C87CF592910CD380E8501B92040A39469C782BA383BEAE498C060FCC7C429BC10B7B6B7A0659C9BE03DC13DB46C638CF5E3B22A303726906DC8DD91C64501EBFC282A3A497EC430CACC066EE4BF9C5C8F2F2A05D0C1921A9E3E85E3 | |||
| (PID) Process: | (2320) WinThumbsPreloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates\9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
| Operation: | write | Name: | Blob |
Value: 0F00000001000000200000009065F32AFC2CFEA7F452D2D6BE94D20C877EFC1C05433D9935696193FDCC05D80300000001000000140000009F6134C5FA75E4FDDE631B232BE961D6D4B97DB6200000000100000047030000308203433082022BA00302010202147327B7C17D5AE708EF73F1F45A79D78B4E99A29F300D06092A864886F70D01010B05003031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C084469676943657274301E170D3233303932393130353030335A170D3339303530383130353030335A3031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C08446967694365727430820122300D06092A864886F70D01010105000382010F003082010A0282010100D91B7A55548F44F3E97C493153B75B055695736B184640D7335A2E6218083B5A1BEE2695209350E57A3EB76FBC604CB3B250DF3D9D0C560D1FBDFE30108D233A3C555100BE1A3F8E543C0B253E06E91B6D5F9CB3A093009BC8B4D3A0EB19DB59E56DA7E3D637847970D6C2AEB4A1FCF3896A7C080FE68759BAA62E6AAA8B7C7CBDA176DDC72F8D259A16D3469E31F19D2959904611D730D7D26FCFED789A0C49698FDFABF3F6727D08C61A073BB11E85C96486D49B0E0D38364C008A5EB964F8813C5DF004F9E76D2F8DB90702D800032674959BF0DF823785419101CEA928A10ACBAE7E48FE19202F3CB7BCF416476D17CB64C5570FCED443BD75D9F2C632FF0203010001A3533051301D0603551D0E041604145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7301F0603551D230418301680145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7300F0603551D130101FF040530030101FF300D06092A864886F70D01010B05000382010100AF2218E4CA18144728FCC76EA14958061522FD4A018BED1A4BFCC5CCE70BC6AE9DF7D3795C9A010D53628E2B6E7C10D6B07E53546235A5EE480E5A434E312154BF1E39AAC27D2C18D4F41CBBECFE4538CEF93EF62C17D187A7F720F4A9478410D09620C9F8B293B5786A5440BC0743B7B7753CF66FBA498B7E083BC267597238DC031B9BB131F997D9B8164AAED0D6E328420E53E1969DA6CD035078179677A7177BB2BF9C87CF592910CD380E8501B92040A39469C782BA383BEAE498C060FCC7C429BC10B7B6B7A0659C9BE03DC13DB46C638CF5E3B22A303726906DC8DD91C64501EBFC282A3A497EC430CACC066EE4BF9C5C8F2F2A05D0C1921A9E3E85E3 | |||
Executable files
8
Suspicious files
3
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1268 | WinThumbsPreloader-1.1.0-setup.tmp | C:\Program Files\WinThumbsPreloader\WinThumbsPreloader.exe | executable | |
MD5:14FE67671FE6AD1E8C9EE0E0175FC8B6 | SHA256:802A8488EA8FE6C9CC493D633CC57BBECC6EB1267563F64A2371D67F6D891092 | |||
| 1268 | WinThumbsPreloader-1.1.0-setup.tmp | C:\Program Files\WinThumbsPreloader\unins000.exe | executable | |
MD5:BF6B97015C5155D5E403DD74733C509B | SHA256:D727DE45009137D666578E78C3C2238D96492823EEB45AC65F9F221BB0BBA230 | |||
| 1268 | WinThumbsPreloader-1.1.0-setup.tmp | C:\Program Files\WinThumbsPreloader\is-705GT.tmp | text | |
MD5:F8091CBE567C3F4F6F429652555B5952 | SHA256:D8B4F93F399B6B7DEC434DEC3F8DB0B6AE7EDB8285290C424F39D61D51D22824 | |||
| 1268 | WinThumbsPreloader-1.1.0-setup.tmp | C:\Program Files\WinThumbsPreloader\WinThumbsPreloader.exe.config | xml | |
MD5:1A843EB7C99248BBFBB89CFEEB1DC490 | SHA256:3244CFA11CDBD4A0217D5830FBA0F283CC5BDFD3D3832D289182BF0C42969856 | |||
| 1268 | WinThumbsPreloader-1.1.0-setup.tmp | C:\Program Files\WinThumbsPreloader\is-91SU3.tmp | executable | |
MD5:14FE67671FE6AD1E8C9EE0E0175FC8B6 | SHA256:802A8488EA8FE6C9CC493D633CC57BBECC6EB1267563F64A2371D67F6D891092 | |||
| 1268 | WinThumbsPreloader-1.1.0-setup.tmp | C:\Program Files\WinThumbsPreloader\is-3071P.tmp | executable | |
MD5:BF6B97015C5155D5E403DD74733C509B | SHA256:D727DE45009137D666578E78C3C2238D96492823EEB45AC65F9F221BB0BBA230 | |||
| 2100 | WinThumbsPreloader-1.1.0-setup.exe | C:\Users\admin\AppData\Local\Temp\is-VH6O5.tmp\WinThumbsPreloader-1.1.0-setup.tmp | executable | |
MD5:717BD1DBF0EFAF41AB8A95289AA6D6DF | SHA256:395B3951215DCA645919777C7996C849755E27875458E5BBC5DFCCBE4BA0421F | |||
| 1268 | WinThumbsPreloader-1.1.0-setup.tmp | C:\Program Files\WinThumbsPreloader\LICENSE.txt | text | |
MD5:F8091CBE567C3F4F6F429652555B5952 | SHA256:D8B4F93F399B6B7DEC434DEC3F8DB0B6AE7EDB8285290C424F39D61D51D22824 | |||
| 1268 | WinThumbsPreloader-1.1.0-setup.tmp | C:\Program Files\WinThumbsPreloader\is-JAT8R.tmp | xml | |
MD5:1A843EB7C99248BBFBB89CFEEB1DC490 | SHA256:3244CFA11CDBD4A0217D5830FBA0F283CC5BDFD3D3832D289182BF0C42969856 | |||
| 2320 | WinThumbsPreloader.exe | C:\Program Files\WinThumbsPreloader\ThumbnailExtensions.txt | text | |
MD5:83FA1BB6EB70B9D6BD11C08A88D52DCE | SHA256:B499713AF625C6363DD6A112E37BD5CB24C136BB3D7738F82687A71ECCCC7D6D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2320 | WinThumbsPreloader.exe | 140.82.121.5:443 | api.github.com | GITHUB | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.github.com |
| whitelisted |