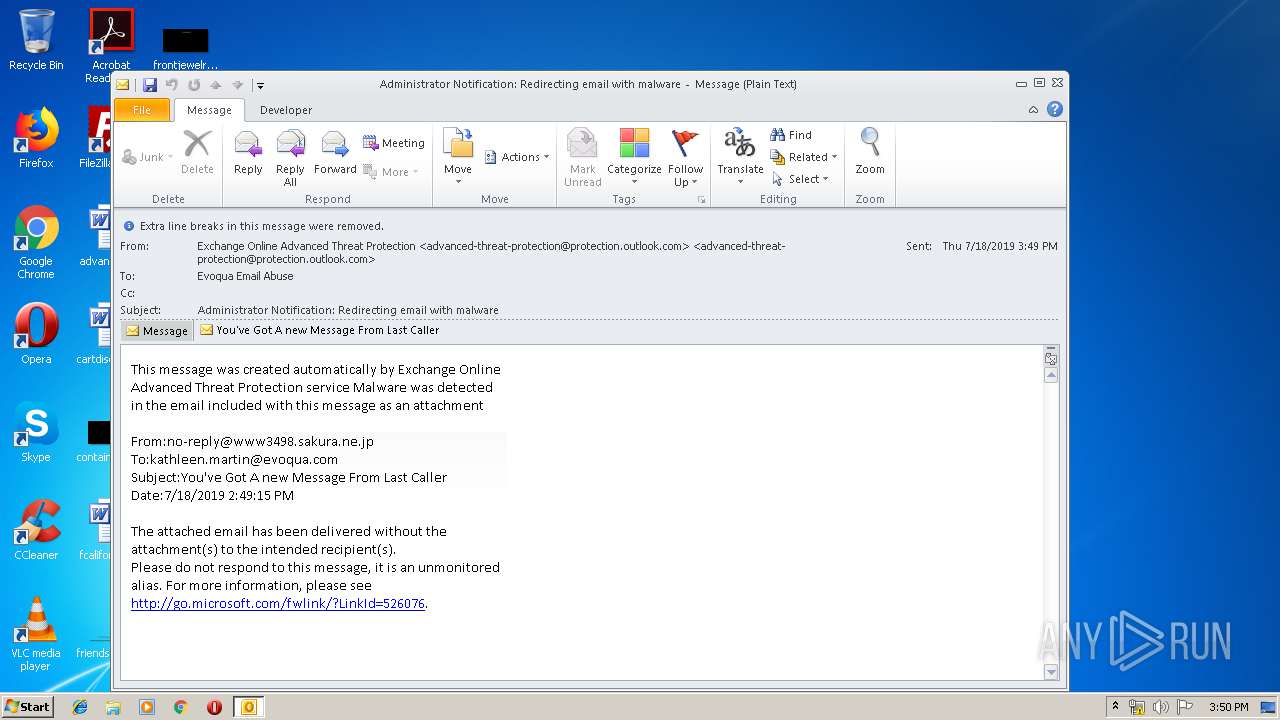
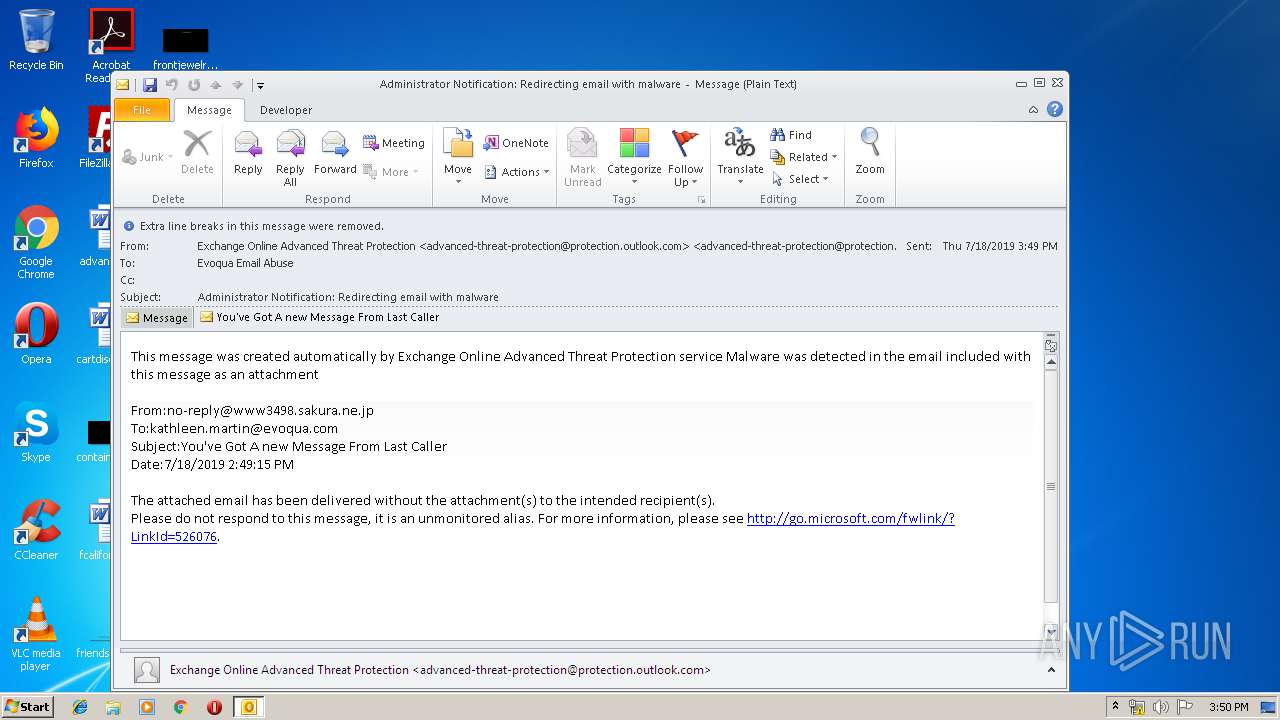
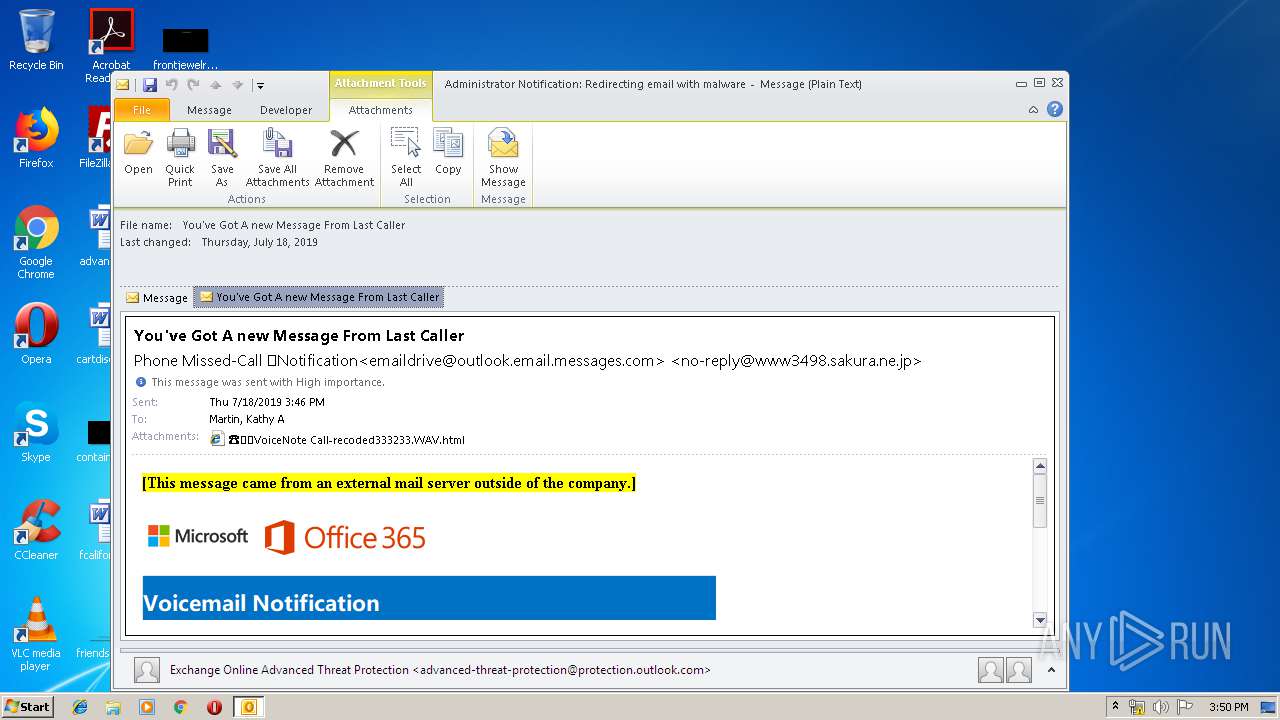
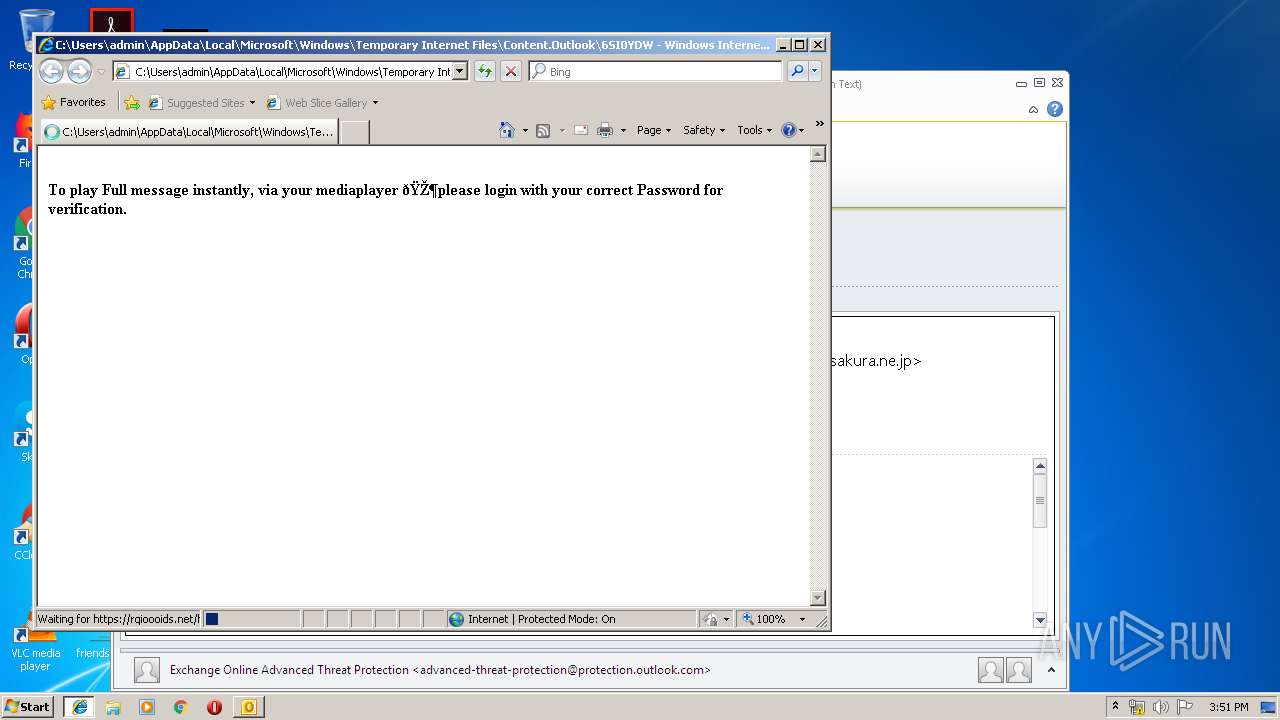
| File name: | Administrator Notification_ Redirecting email with malware.msg |
| Full analysis: | https://app.any.run/tasks/cf684972-3e1c-4884-aad7-398212899927 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2019, 14:50:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 1744A3145D35AE27A7B9761055B2137F |
| SHA1: | B5D4D0CB67B50B901EE7A437D4BE6F23A7D518C6 |
| SHA256: | 54D5A9A5CEB6AD4F5E7D33474409F98AA9A43E4A77D4AB70CFD1EC6E10561127 |
| SSDEEP: | 3072:h3DMiZhXKu4pBIFOqeB8OuqCmIE21Gc8xXTRkJupW:hTIcTOuqCmIE21Gc85TRkkpW |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 3896)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 3896)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3896)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 3896)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3708)
Reads internet explorer settings
- iexplore.exe (PID: 2256)
Reads Internet Cache Settings
- iexplore.exe (PID: 2256)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2256 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3708 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
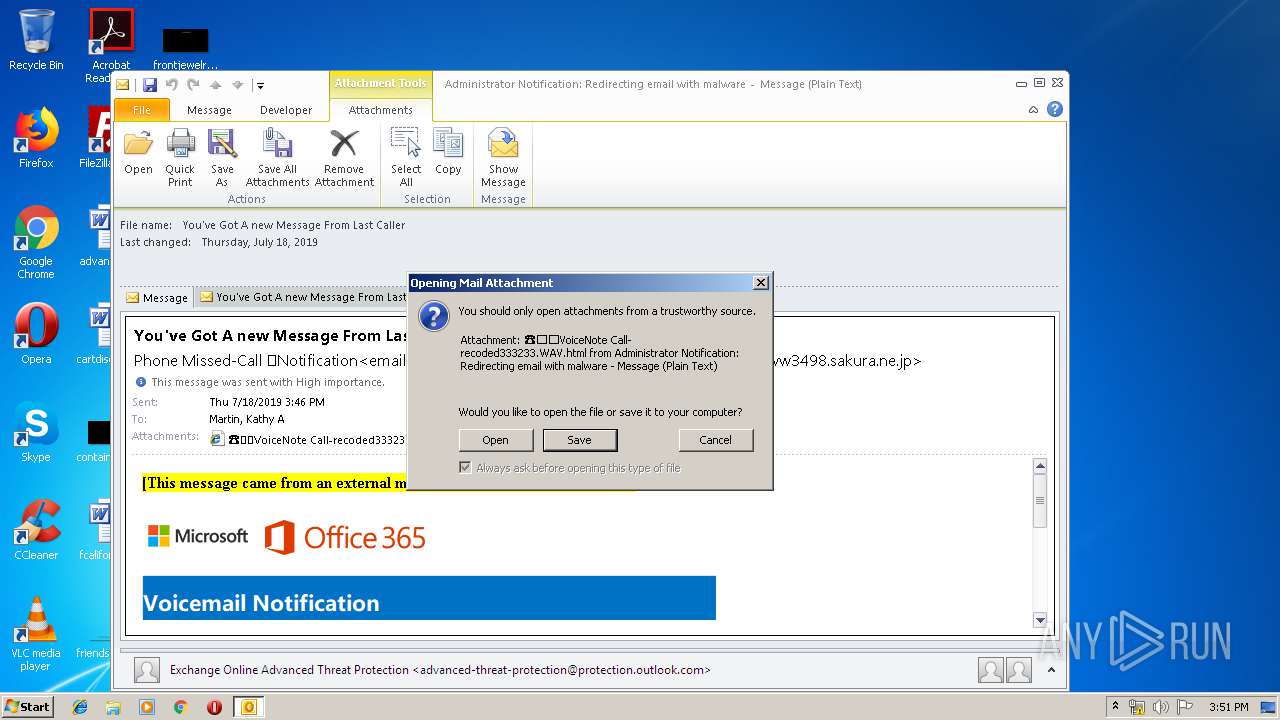
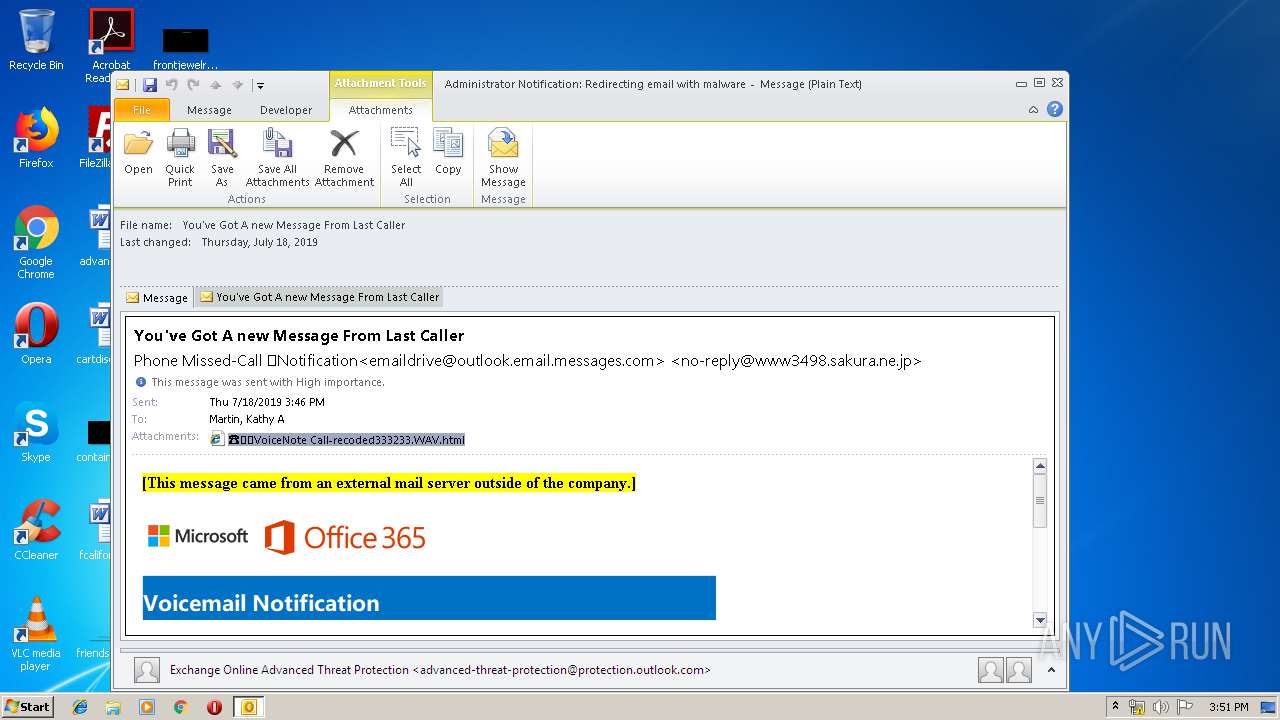
| 3708 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\6SI0YDWO\☎️📞VoiceNote Call-recoded333233 WAV.html | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3896 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Administrator Notification_ Redirecting email with malware.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
2 207
Read events
1 449
Write events
735
Delete events
23
Modification events
| (PID) Process: | (3896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | 5*= |
Value: 352A3D00380F0000010000000000000000000000 | |||
| (PID) Process: | (3896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 380F00000E94F12F783DD50100000000 | |||
| (PID) Process: | (3896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220131360 | |||
| (PID) Process: | (3896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3896) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3896) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1324482581 | |||
Executable files
0
Suspicious files
0
Text files
37
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3896 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRF6A5.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3896 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF34EF97A6F0C2EF21.TMP | — | |
MD5:— | SHA256:— | |||
| 3896 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\6SI0YDWO\☎️📞VoiceNote Call-recoded333233 WAV (2).html\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3708 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3708 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3896 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3896 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_4B2D9CFE8A328C4B8358F97F12661430.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
| 3896 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_WorkHours_1_F34BE2B4C28CF44E89E1802CD4D1A11D.dat | xml | |
MD5:807EF0FC900FEB3DA82927990083D6E7 | SHA256:4411E7DC978011222764943081500FFF0E43CBF7CCD44264BD1AB6306CA68913 | |||
| 3896 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_AvailabilityOptions_2_02EBD117E6493B4CA74143ED49B9C7C6.dat | xml | |
MD5:EEAA832C12F20DE6AAAA9C7B77626E72 | SHA256:C4C9A90F2C961D9EE79CF08FBEE647ED7DE0202288E876C7BAAD00F4CA29CA16 | |||
| 3896 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_RssRule_2_9646E147EA2E4A459D5FE90B18A59933.dat | xml | |
MD5:D8B37ED0410FB241C283F72B76987F18 | SHA256:31E68049F6B7F21511E70CD7F2D95B9CF1354CF54603E8F47C1FC40F40B7A114 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3708 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3708 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
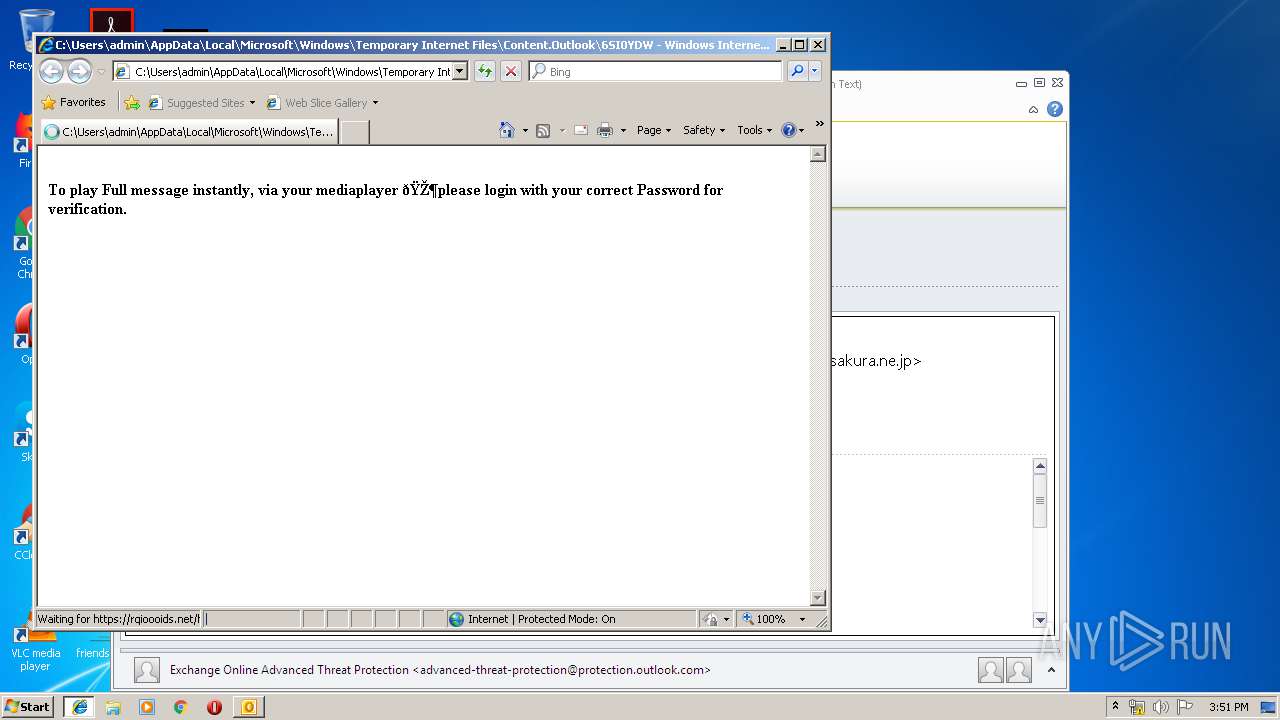
2256 | iexplore.exe | 194.34.247.30:443 | rqioooids.net | — | — | unknown |
3896 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
rqioooids.net |
| unknown |