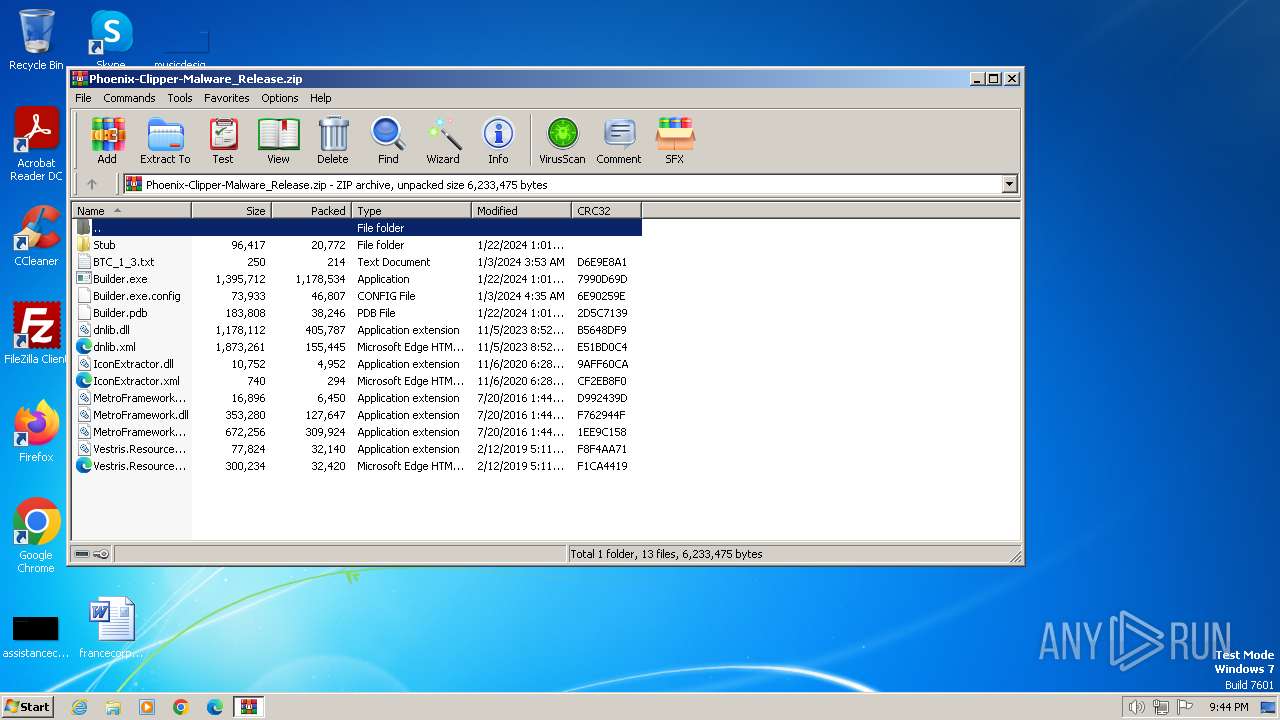
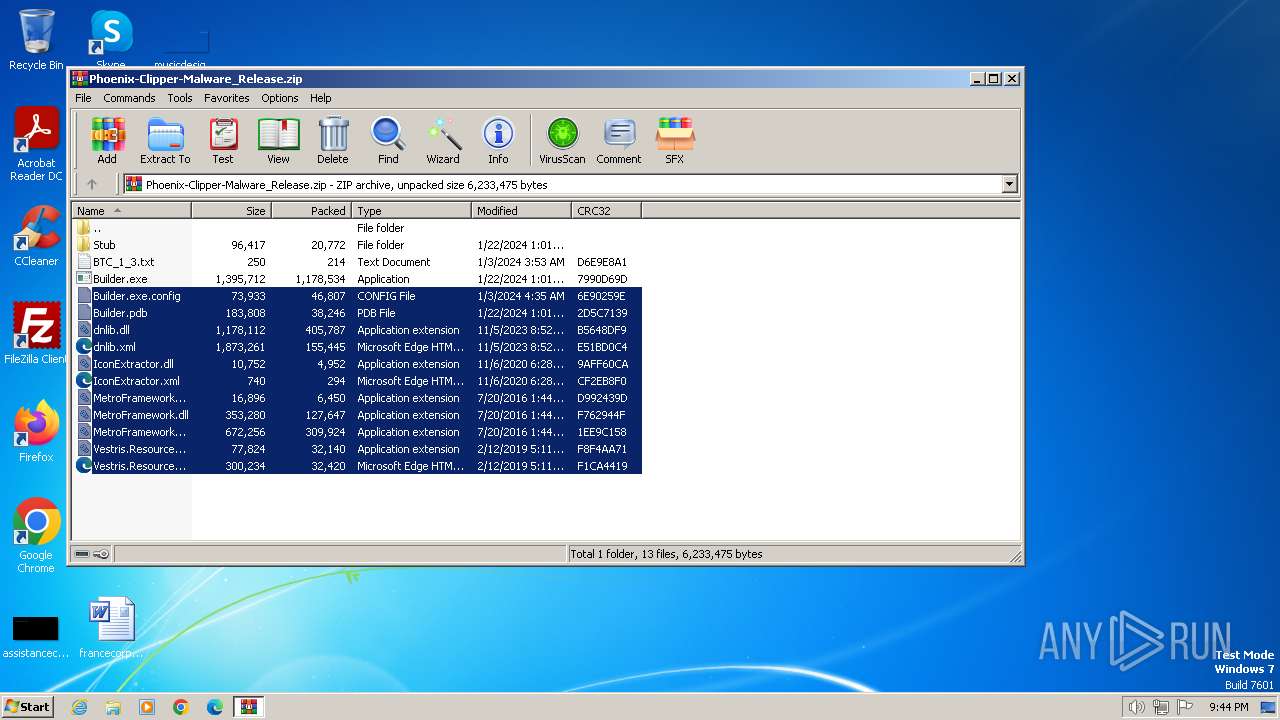
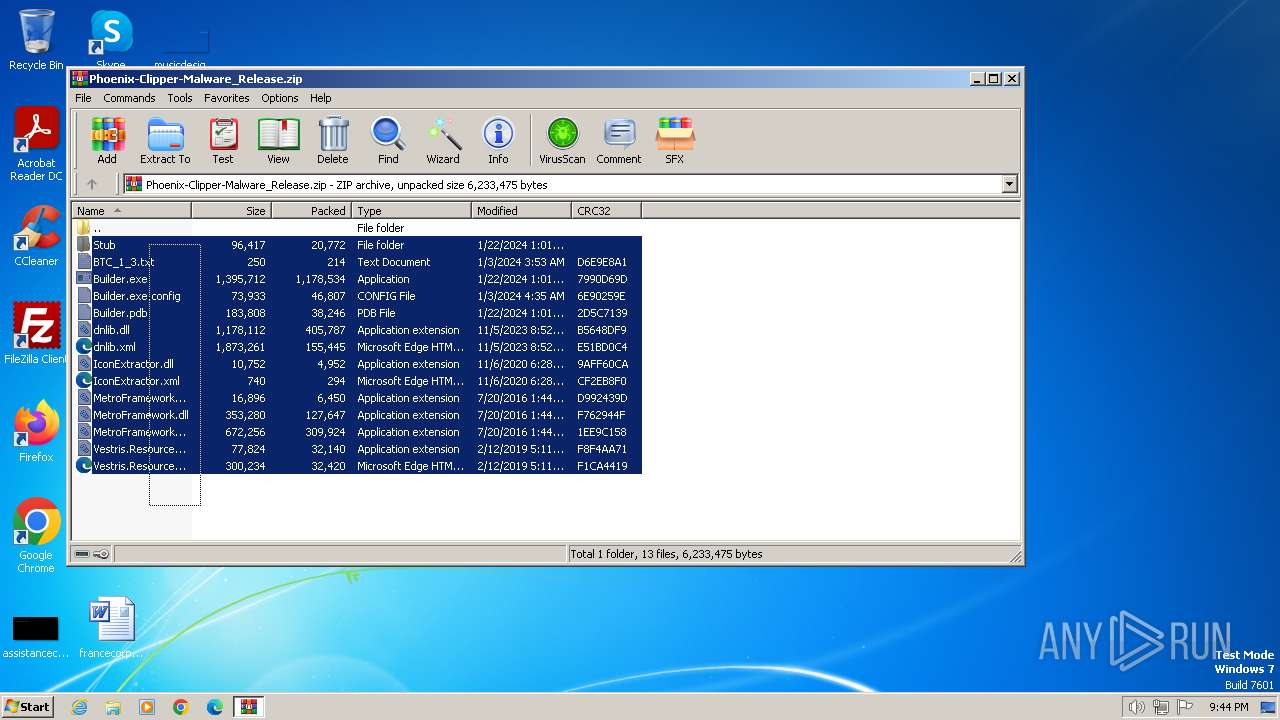
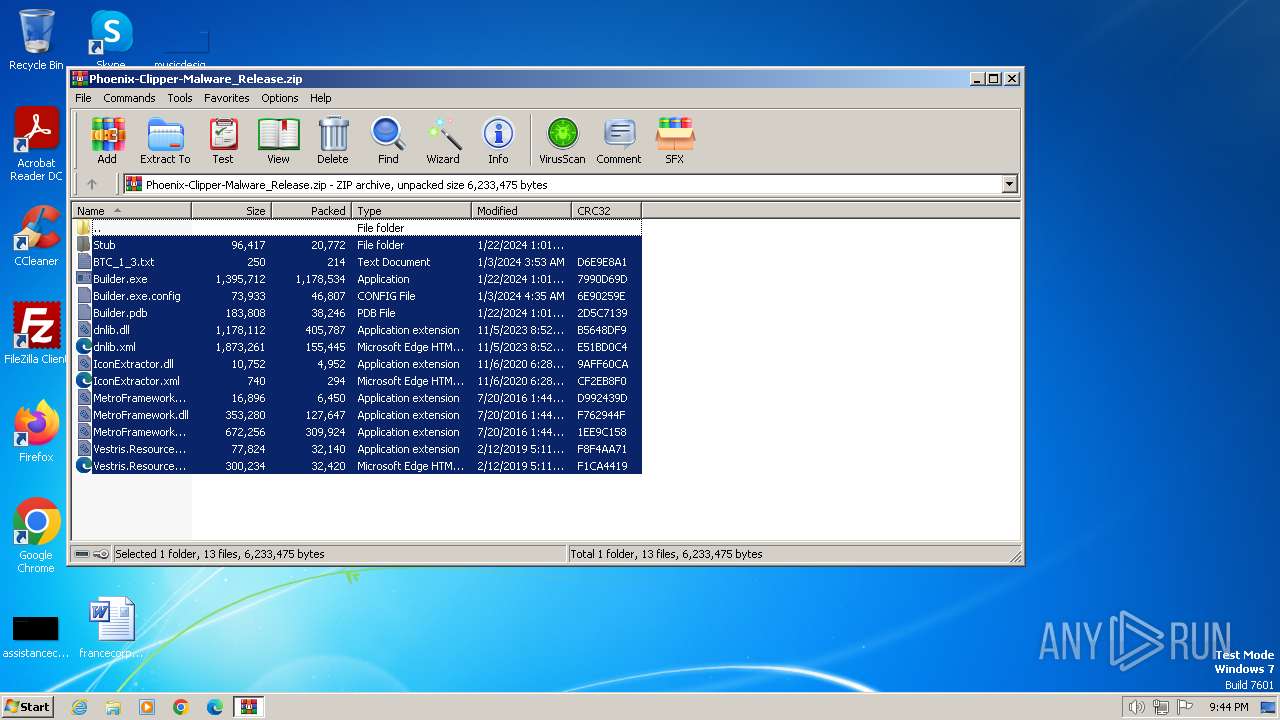
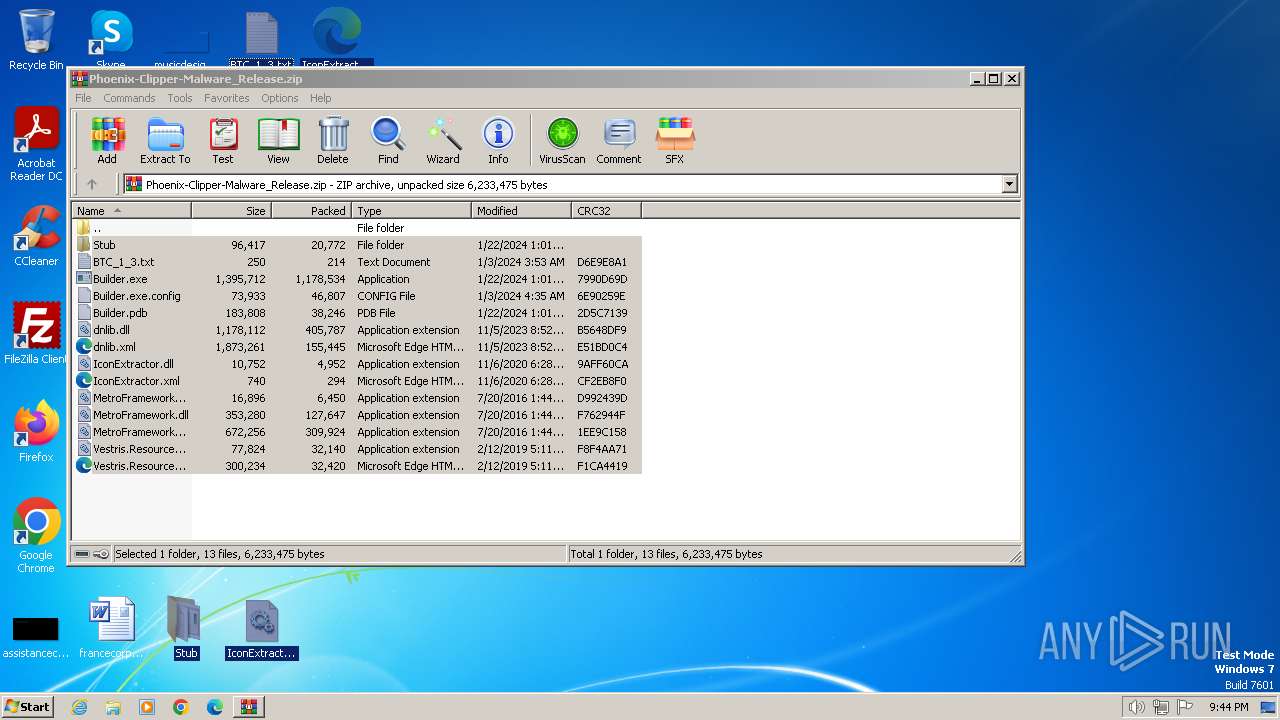
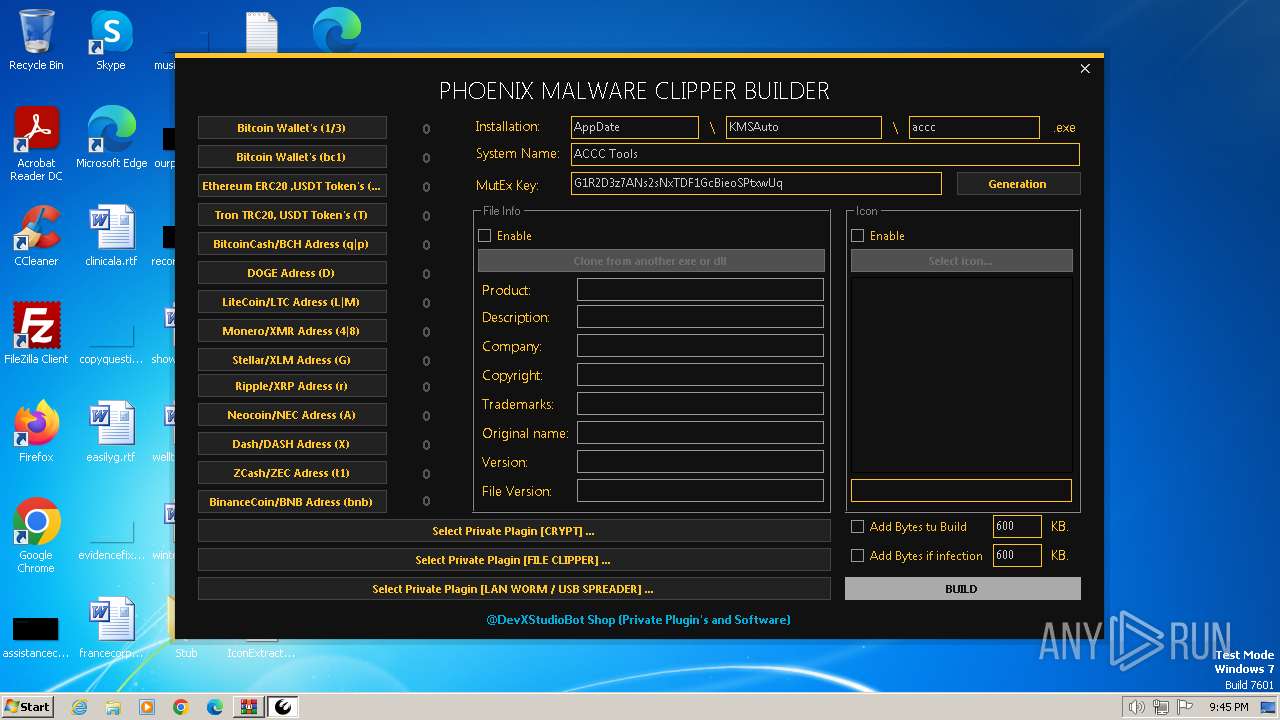
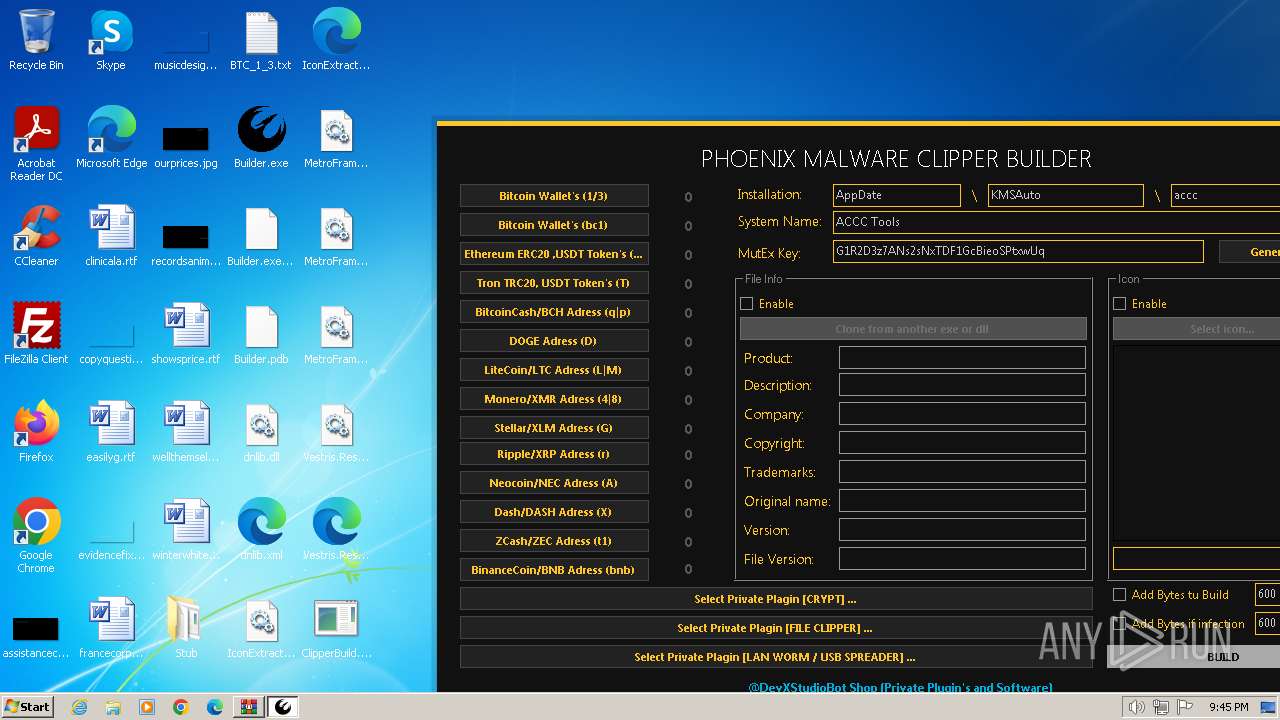
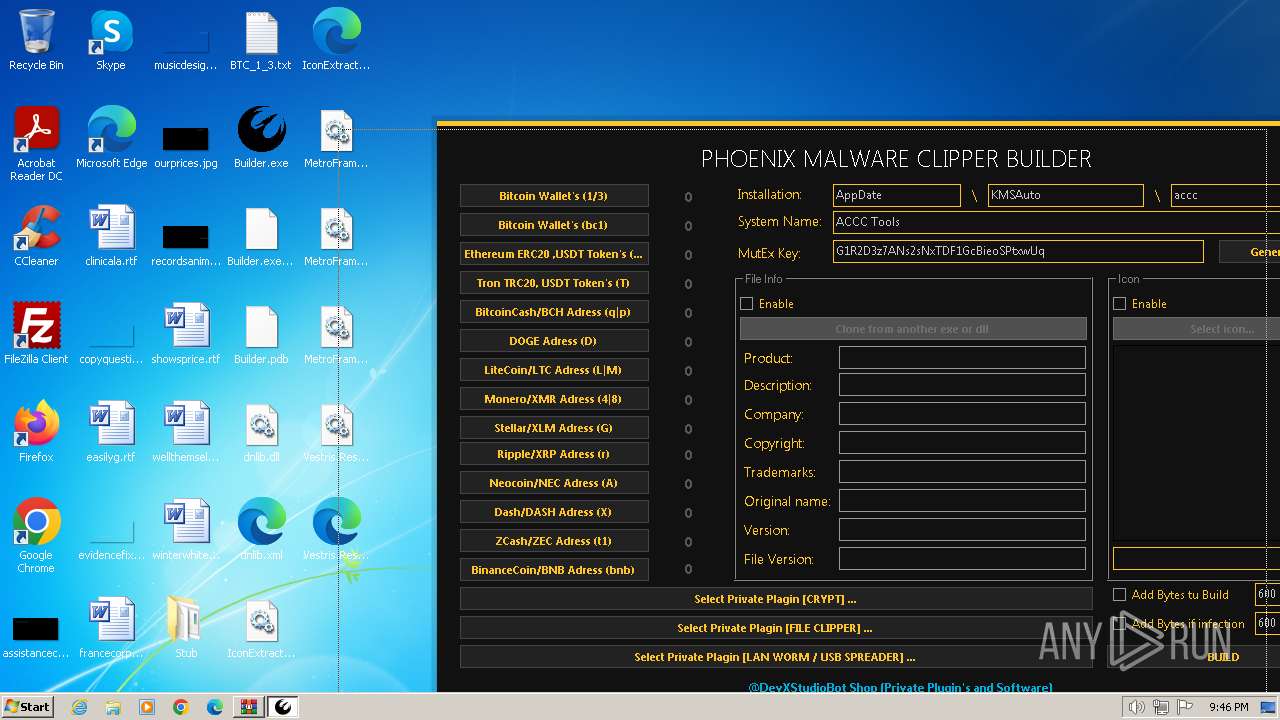
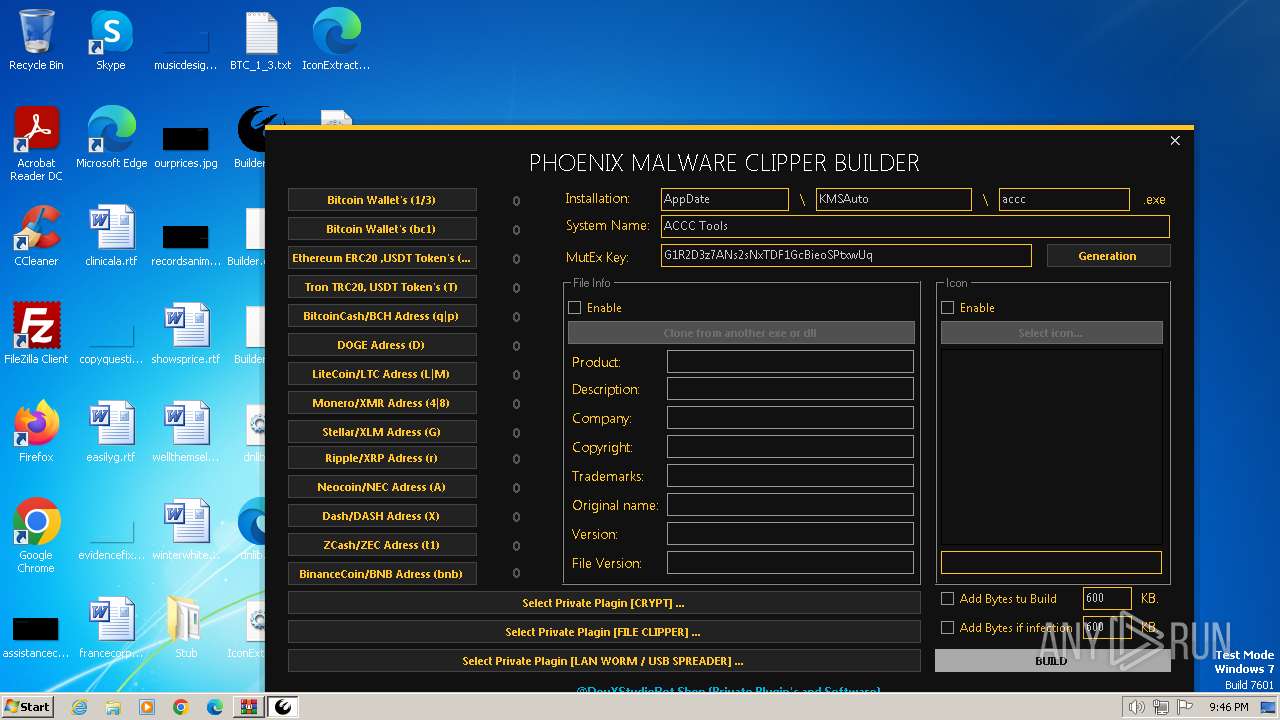
| download: | /DevxStudio/Phoenix-Clipper-Malware/releases/download/Clipper/Phoenix-Clipper-Malware_Release.zip |
| Full analysis: | https://app.any.run/tasks/499d7952-0527-4dfb-8ee4-dab7125e09a7 |
| Verdict: | Malicious activity |
| Analysis date: | February 09, 2024, 21:44:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 634630354A4E8E5488EFF6EB63516489 |
| SHA1: | B2FBB8BDF52C31CEC638FA7CE2AB83E7C29FE051 |
| SHA256: | 54BE168149A6B5C5F2D1B81DFC60E11EF3CAC237A5F9919DE1AD949E7365B723 |
| SSDEEP: | 98304:1vAMzEfBTvZ7KIBVG+Hl4RSk9+6pItNvWhLjOSbsvCAIWC6rYNk6Z+AFwaG2Xnzc:ouhLXB8rp |
MALICIOUS
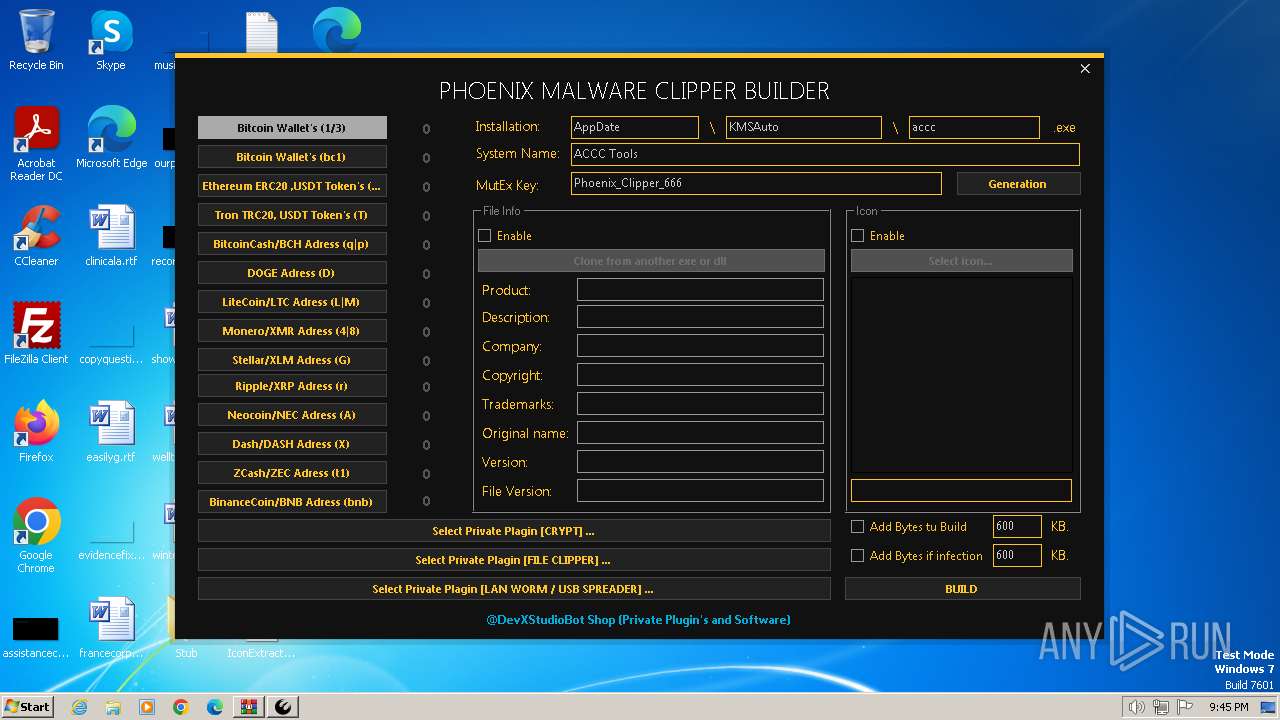
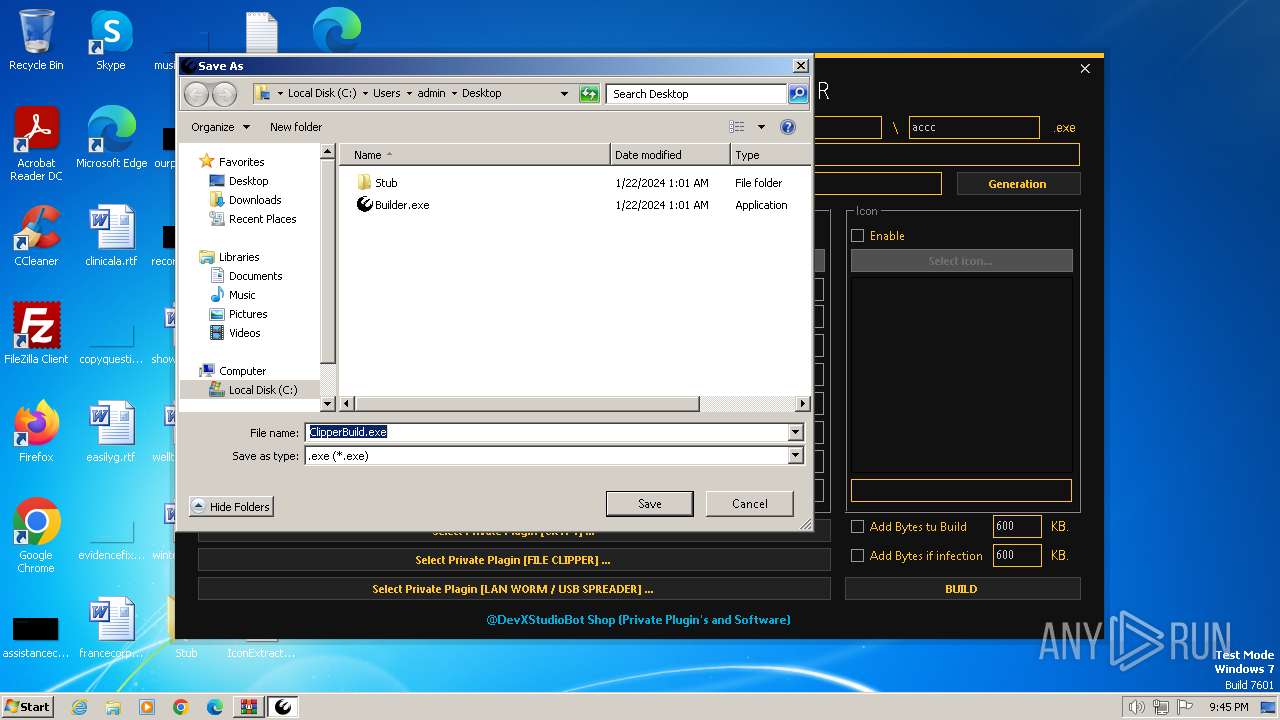
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3700)
- ClipperBuild.exe (PID: 1836)
SUSPICIOUS
Reads security settings of Internet Explorer
- ClipperBuild.exe (PID: 1836)
- Builder.exe (PID: 3660)
Executable content was dropped or overwritten
- ClipperBuild.exe (PID: 1836)
Starts itself from another location
- ClipperBuild.exe (PID: 1836)
Reads the Internet Settings
- ClipperBuild.exe (PID: 1836)
- Builder.exe (PID: 3660)
Executing commands from ".cmd" file
- ClipperBuild.exe (PID: 1836)
Starts CMD.EXE for commands execution
- ClipperBuild.exe (PID: 1836)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2896)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3700)
Manual execution by a user
- ClipperBuild.exe (PID: 1836)
- Builder.exe (PID: 3660)
Reads the machine GUID from the registry
- ClipperBuild.exe (PID: 1836)
- accc.exe (PID: 3996)
- Builder.exe (PID: 3660)
Checks supported languages
- ClipperBuild.exe (PID: 1836)
- accc.exe (PID: 3996)
- Builder.exe (PID: 3660)
Reads the computer name
- ClipperBuild.exe (PID: 1836)
- Builder.exe (PID: 3660)
- accc.exe (PID: 3996)
Creates files in the program directory
- ClipperBuild.exe (PID: 1836)
Create files in a temporary directory
- ClipperBuild.exe (PID: 1836)
Creates files or folders in the user directory
- Builder.exe (PID: 3660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:01:03 14:53:30 |
| ZipCRC: | 0xd6e9e8a1 |
| ZipCompressedSize: | 214 |
| ZipUncompressedSize: | 250 |
| ZipFileName: | BTC_1_3.txt |
Total processes
46
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1824 | timeout 6 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1836 | "C:\Users\admin\Desktop\ClipperBuild.exe" | C:\Users\admin\Desktop\ClipperBuild.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2896 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\tmp9C5A.tmp.cmd"" | C:\Windows\System32\cmd.exe | — | ClipperBuild.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3660 | "C:\Users\admin\Desktop\Builder.exe" | C:\Users\admin\Desktop\Builder.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Builder Exit code: 0 Version: 4.1.0.0 Modules
| |||||||||||||||
| 3700 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Phoenix-Clipper-Malware_Release.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3960 | "schtasks.exe" /create /tn ACCC Tools /tr "C:\ProgramData\KMSAuto\accc.exe" /st 21:50 /du 23:59 /sc daily /ri 1 /f | C:\Windows\System32\schtasks.exe | — | ClipperBuild.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 2147500037 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3996 | "C:\ProgramData\KMSAuto\accc.exe" | C:\ProgramData\KMSAuto\accc.exe | — | ClipperBuild.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
10 581
Read events
10 498
Write events
77
Delete events
6
Modification events
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Phoenix-Clipper-Malware_Release.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
9
Suspicious files
2
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3700.8078\Builder.exe | executable | |
MD5:4DDE43C7422B0AF5636E6379D9B51AC5 | SHA256:82E10DB2BE75B64854EAF32E5F4FCCC45362E5BCED01E45183E77EE15A2CC46A | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3700.8078\MetroFramework.dll | executable | |
MD5:34EA7F7D66563F724318E322FF08F4DB | SHA256:C2C12D31B4844E29DE31594FC9632A372A553631DE0A0A04C8AF91668E37CF49 | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3700.8078\IconExtractor.xml | xml | |
MD5:5DF1BC39DC11A928BE141EDF9A30270B | SHA256:ABD5B0ADC717DBA0D4B098FCEF362328D42301D8DC90718390E5CDBE5EB0C267 | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3700.8078\IconExtractor.dll | executable | |
MD5:7BCF61E29E5CBCD1B81D9AB72CBFED93 | SHA256:2C359CE857982F45B09AF49DBCCFB2AE302839ACF1956E8325E7F854B339A8C9 | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3700.8078\BTC_1_3.txt | text | |
MD5:482C2F6BFBF9A98D622B5544D222776F | SHA256:224ACDAD30B1CB7E6E977F44670BC237932E0878B15A4359E01ECAB7C611FCB6 | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3700.8078\Builder.pdb | pdb | |
MD5:579F1B3FE2D37E8278A1ABDBC5F24377 | SHA256:30F7FA476D90B6386C065D107C56AA309E2C70F1D733F8835F369A3EE7ECDE4C | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3700.8078\dnlib.xml | xml | |
MD5:4F66F6D14A67BBD0F70012557D88D17B | SHA256:F453807C0866BDB424541C9297A4C55107143C0103CB84F23D070044F62B7273 | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3700.8078\MetroFramework.Design.dll | executable | |
MD5:AB4C3529694FC8D2427434825F71B2B8 | SHA256:0A4A96082E25767E4697033649B16C76A652E120757A2CECAB8092AD0D716B65 | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3700.8078\Stub\Stub.pdb | pdb | |
MD5:05CFD880AD36D337ABD8D41CE721BA01 | SHA256:40B53A13A49023025D32B585EE766C4FE5DB0A73FF2689AF106687C7A9CC66C9 | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3700.8078\dnlib.dll | executable | |
MD5:B85694AE25765805B5E91B028FEF9BDD | SHA256:E638E008FD50DB70CAB8D564C5655A1F1148E65297FFE753EF55150CAEA23381 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |