| File name: | Adobe Reader Setup.exe |
| Full analysis: | https://app.any.run/tasks/80c13a03-3eb6-4b46-b3af-ded52fa81704 |
| Verdict: | Malicious activity |
| Analysis date: | November 25, 2024, 10:57:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | E81DF5334921ED67EF277588C6627D18 |
| SHA1: | 83A04AA927874040C126E8F31E25B1F943D06EDA |
| SHA256: | 54AAA2380578133BE0ACD50D2ED1C74E5E35E40AF54F1ED7B7B0B2A421D2602A |
| SSDEEP: | 12288:XZsmVaQ3xUUfErufMv1ZcTjGj9kP9sv9Y:JsmZAZcTjGj9k8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- Adobe Reader Setup.exe (PID: 3544)
Reads security settings of Internet Explorer
- Adobe Reader Setup.exe (PID: 3544)
Reads Internet Explorer settings
- Adobe Reader Setup.exe (PID: 3544)
INFO
Checks supported languages
- Adobe Reader Setup.exe (PID: 3544)
The process uses the downloaded file
- Adobe Reader Setup.exe (PID: 3544)
Reads the computer name
- Adobe Reader Setup.exe (PID: 3544)
Reads the machine GUID from the registry
- Adobe Reader Setup.exe (PID: 3544)
Create files in a temporary directory
- Adobe Reader Setup.exe (PID: 3544)
Checks proxy server information
- Adobe Reader Setup.exe (PID: 3544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:04:12 04:02:13+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 326144 |
| InitializedDataSize: | 201216 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1335c |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.1.0.201 |
| ProductVersionNumber: | 3.1.0.201 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Russian |
| CharacterSet: | Unicode |
| FileVersion: | 3.1.0.201 |
Total processes
129
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3544 | "C:\Users\admin\Desktop\Adobe Reader Setup.exe" | C:\Users\admin\Desktop\Adobe Reader Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3544 | "C:\Users\admin\Desktop\Adobe Reader Setup.exe" | C:\Users\admin\Desktop\Adobe Reader Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
1 474
Read events
1 459
Write events
7
Delete events
8
Modification events
| (PID) Process: | (3544) Adobe Reader Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings |
| Operation: | write | Name: | JITDebug |
Value: 0 | |||
| (PID) Process: | (3544) Adobe Reader Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\adobe reader setup.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 0955130000000000 | |||
| (PID) Process: | (3544) Adobe Reader Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3544) Adobe Reader Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3544) Adobe Reader Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3544) Adobe Reader Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main\WindowsSearch |
| Operation: | write | Name: | Version |
Value: WS not running | |||
| (PID) Process: | (3544) Adobe Reader Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (3544) Adobe Reader Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (3544) Adobe Reader Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
Executable files
0
Suspicious files
2
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3544 | Adobe Reader Setup.exe | C:\Users\admin\AppData\Local\Temp\DLG\dlgres\DLG-Product-Logo.png | image | |
MD5:69E4FB88F38472E651F3B4169879C47F | SHA256:BD284633E72034F963AE0DB7BBF7714CD735DCB51D905969F1D8B03B73952033 | |||
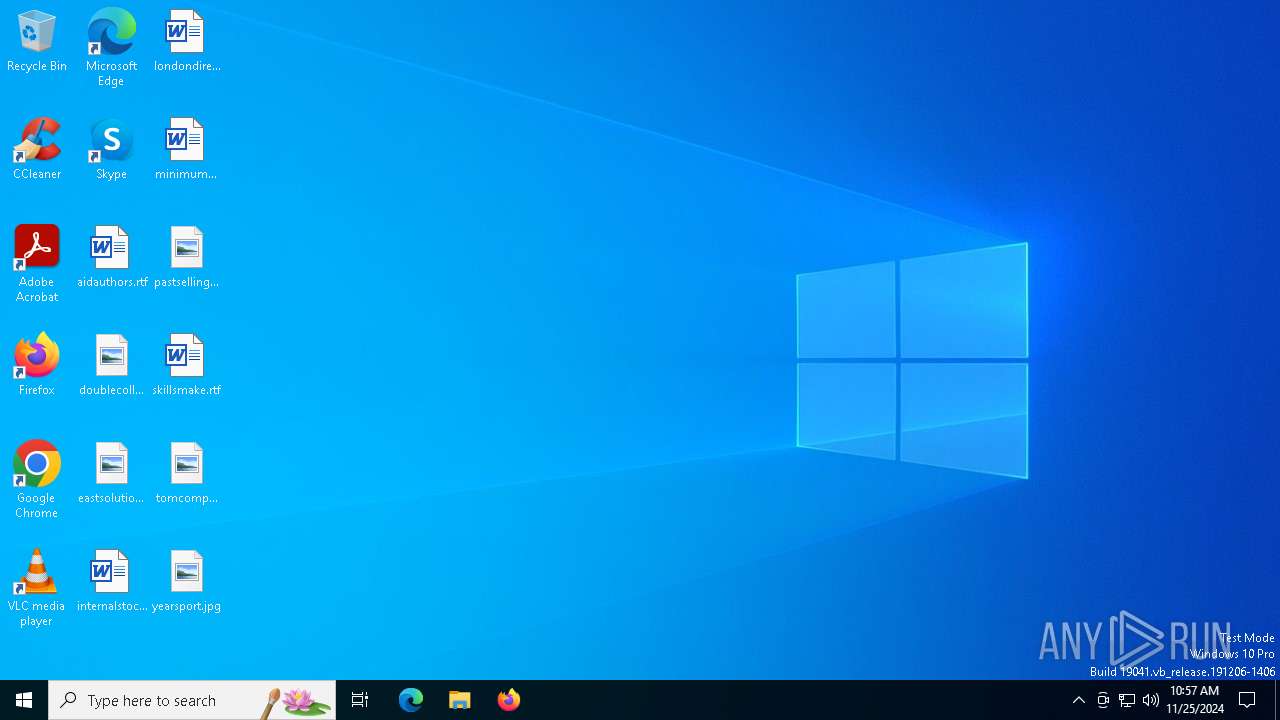
| 3544 | Adobe Reader Setup.exe | C:\Users\admin\AppData\Local\Temp\DLG\initWindow\noconnection.html | html | |
MD5:A0EE32DC4FFC79FDEF2DC0467DA538C5 | SHA256:B4508B7DCC08B2B93CD64BEE68BD5174FE48F48280E59F9A81D4861C3EF0431D | |||
| 3544 | Adobe Reader Setup.exe | C:\Users\admin\AppData\Local\Temp\DLG\initWindow\css\style.css | text | |
MD5:BF4625507C1D35CAABDB3E9D9BA584A0 | SHA256:491ACCAFCF5A3997FD2B8B6D3A91153773DB8CA0DF10B248A19EE51516C403A8 | |||
| 3544 | Adobe Reader Setup.exe | C:\Users\admin\AppData\Local\Temp\DLG\initWindow\progress.html | html | |
MD5:2C68017C4EA6EE541E285AAAE8840BA9 | SHA256:6C926310DC1495EF47E07EFD9B695F34C7D4F755FA011CD73455B5E4ED93898B | |||
| 3544 | Adobe Reader Setup.exe | C:\Users\admin\AppData\Local\Temp\DLG5509.tmp | binary | |
MD5:FC9B7AC4CE5EBACC362E47E19CA0B2C8 | SHA256:F8214BC37CF67D62AA1365B5936A6828FEEB7858DBC6F9877FFF048FA67FD640 | |||
| 3544 | Adobe Reader Setup.exe | C:\Users\admin\AppData\Local\Temp\DLG\loadingImage\loadingImage.bmp | binary | |
MD5:002AB0273D3F8F0575A09DC4392B1905 | SHA256:57F3C81751562F8327A62E3381B93367755A2DDDC18BECC6FEDEFE6CA6554D63 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
33
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7124 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7124 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6224 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5448 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.32.238.107:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.200.189.225:80 | www.microsoft.com | Moratelindo Internet Exchange Point | ID | whitelisted |
5064 | SearchApp.exe | 2.16.106.215:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
dlg-configs.buzzrin.de |
| unknown |
dlg-messages.buzzrin.de |
| unknown |
go.microsoft.com |
| whitelisted |