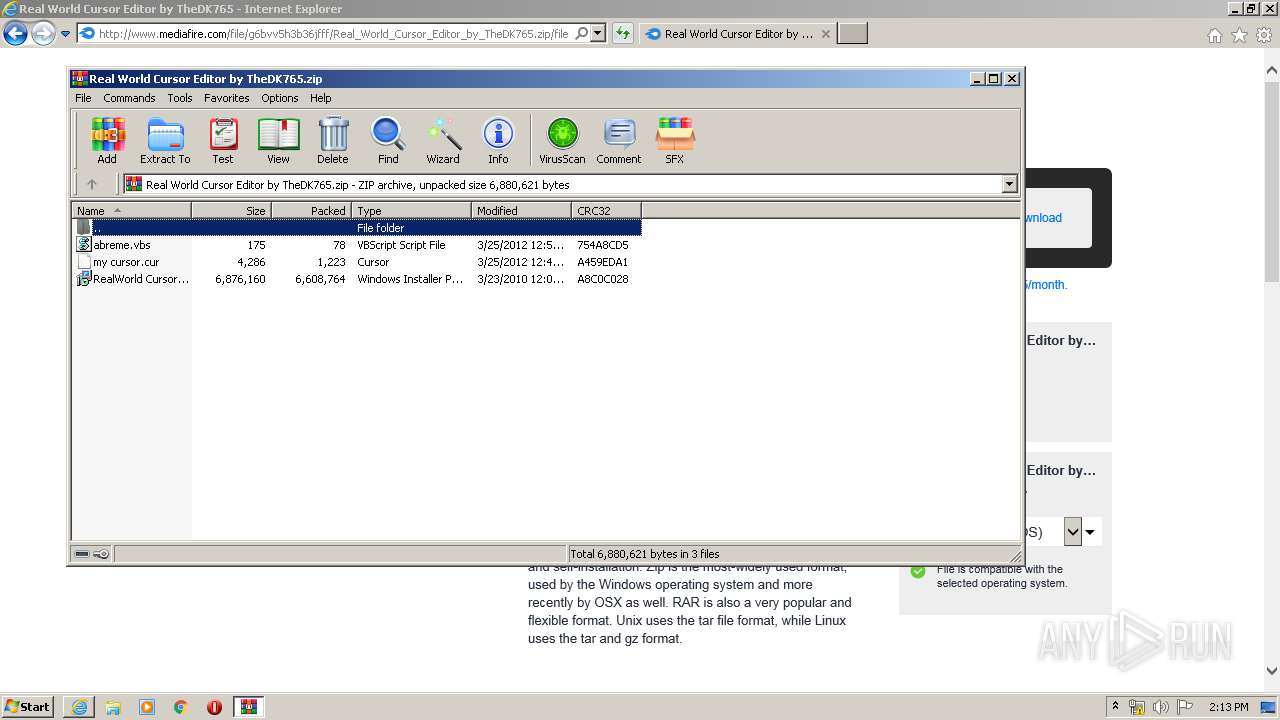
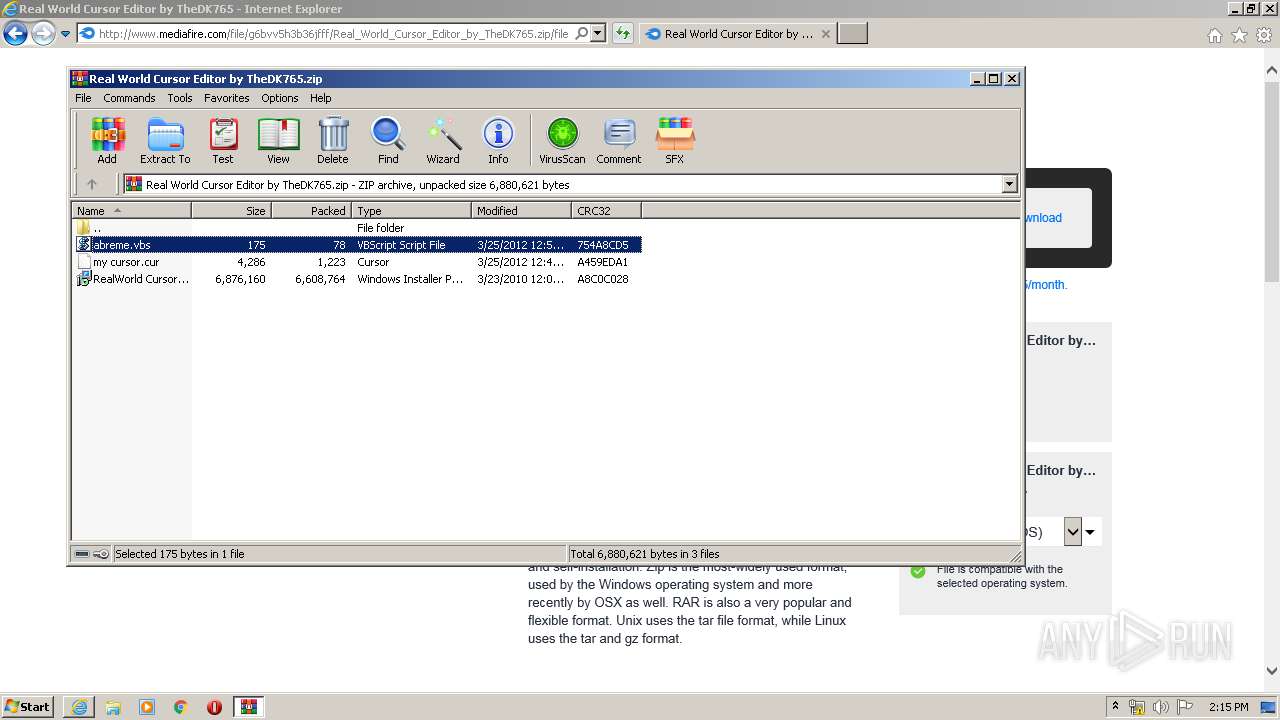
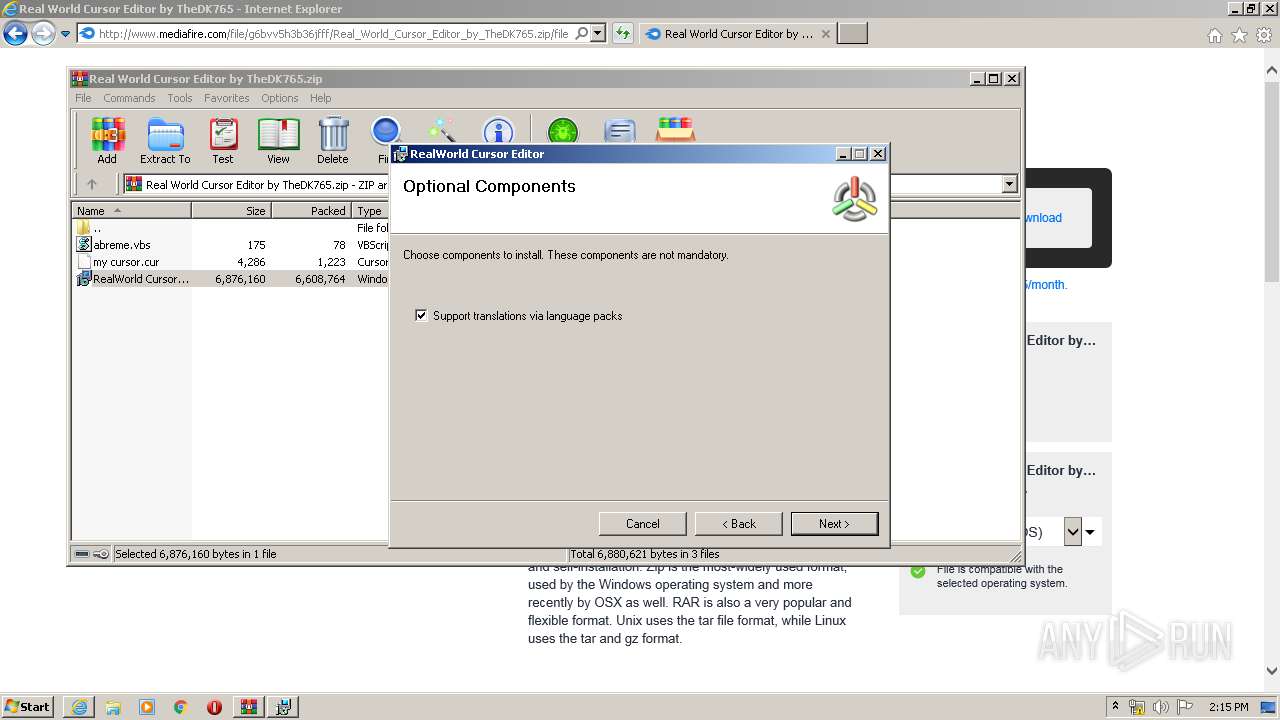
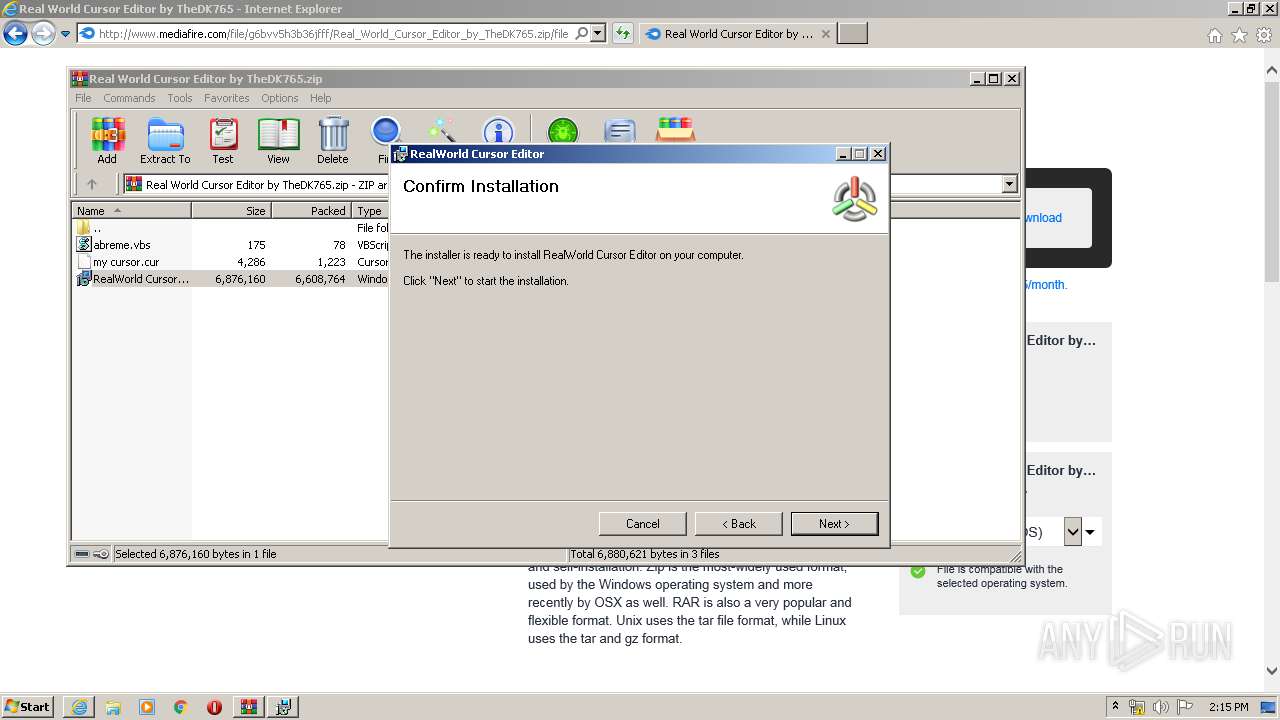
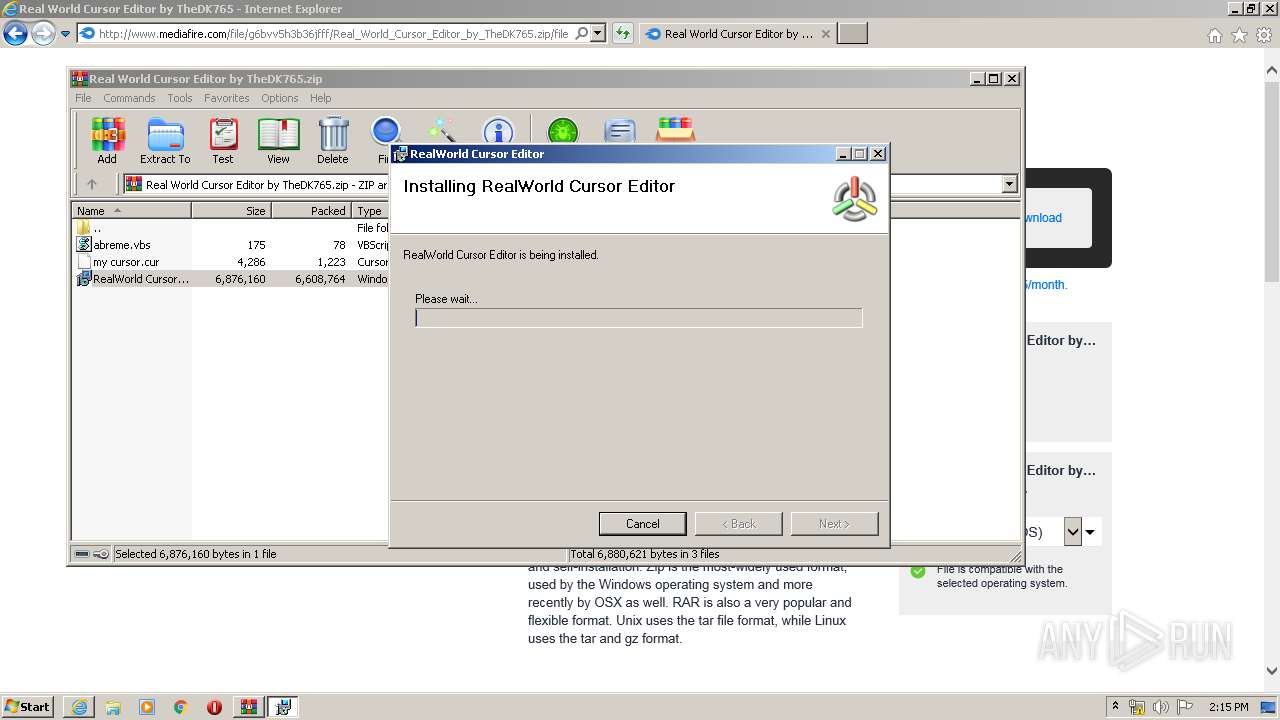
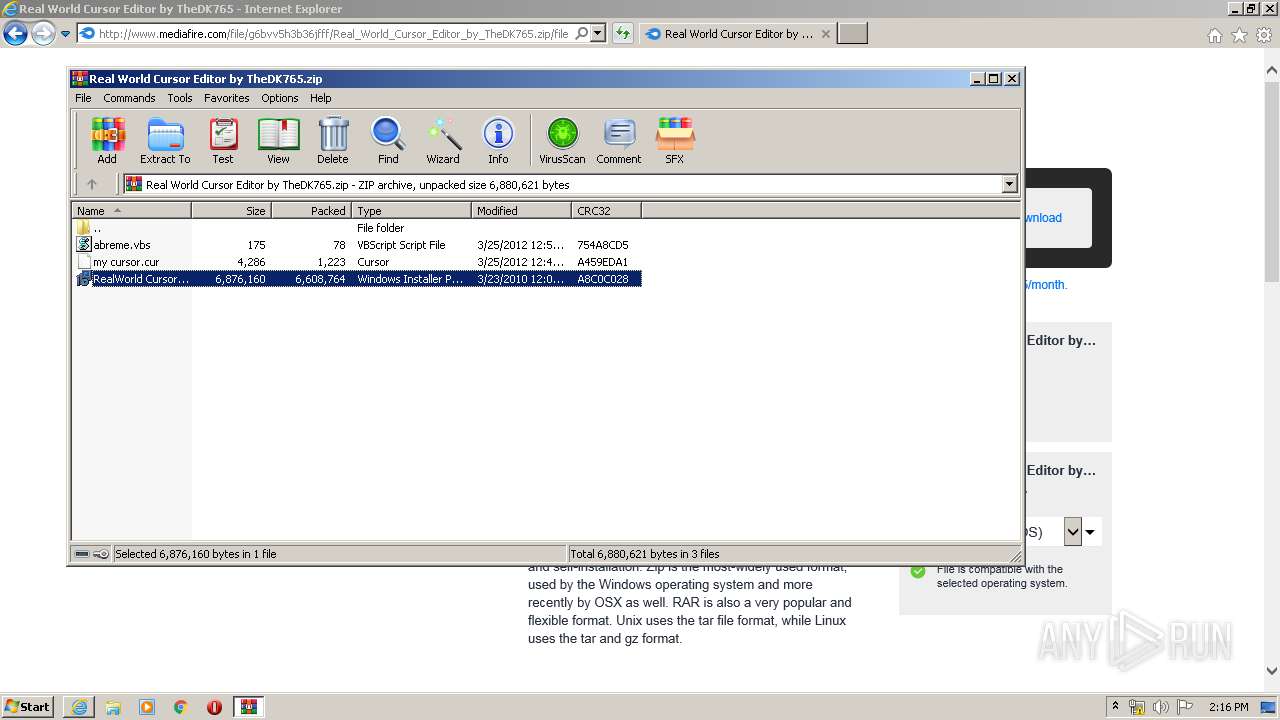
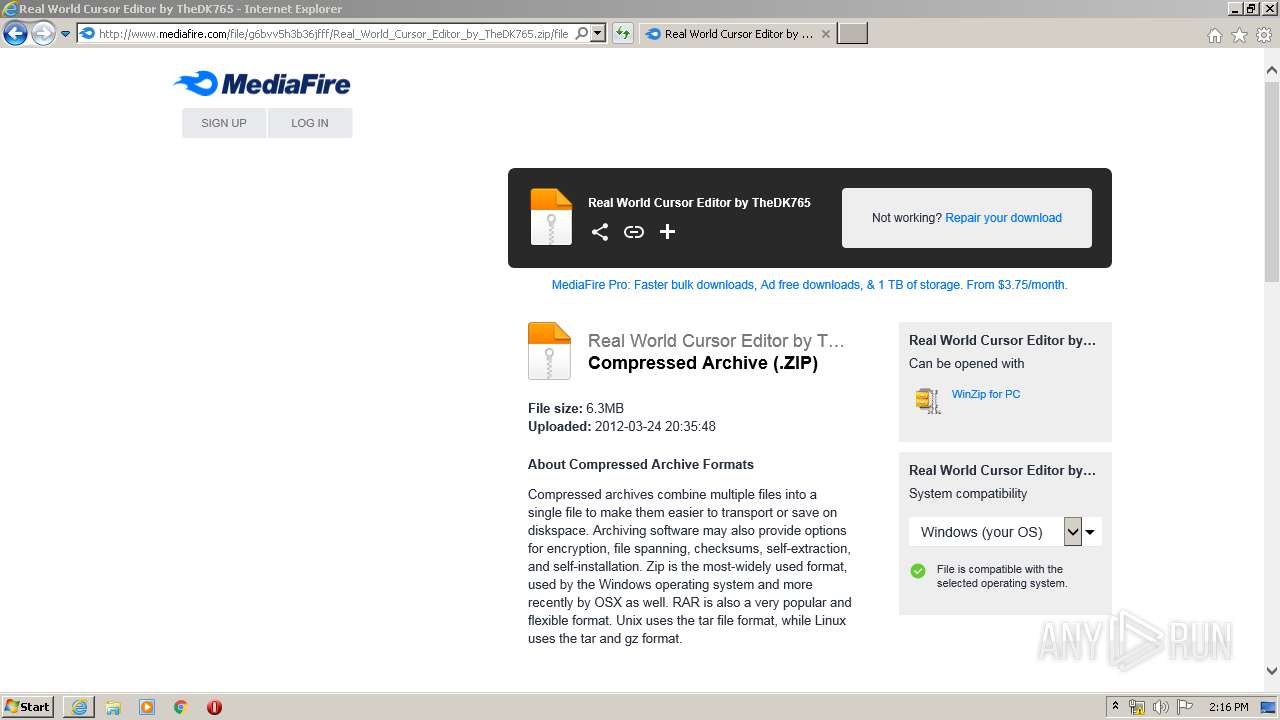
| URL: | http://download1509.mediafire.com/6u99o8lz2exg/g6bvv5h3b36jfff/Real+World+Cursor+Editor+by+TheDK765.zip |
| Full analysis: | https://app.any.run/tasks/c2f886ee-bbc5-4e8b-91e8-50b5fbe3633a |
| Verdict: | Malicious activity |
| Analysis date: | January 29, 2020, 14:12:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 73324D487DF3C0839FDC2D08B658CD72 |
| SHA1: | 0D03FE9856981EF9FF46118CE63E8459494179D6 |
| SHA256: | 5487568758F643521A462B09B22CDF09527DE3131D7ACD09F18330B52A41A139 |
| SSDEEP: | 3:N1KaKE6QV8oeGC7cA1TH2oAgOBOnXNJMsYcOxdSf:CanjeGs1z3AgOLpceQf |
MALICIOUS
Application was dropped or rewritten from another process
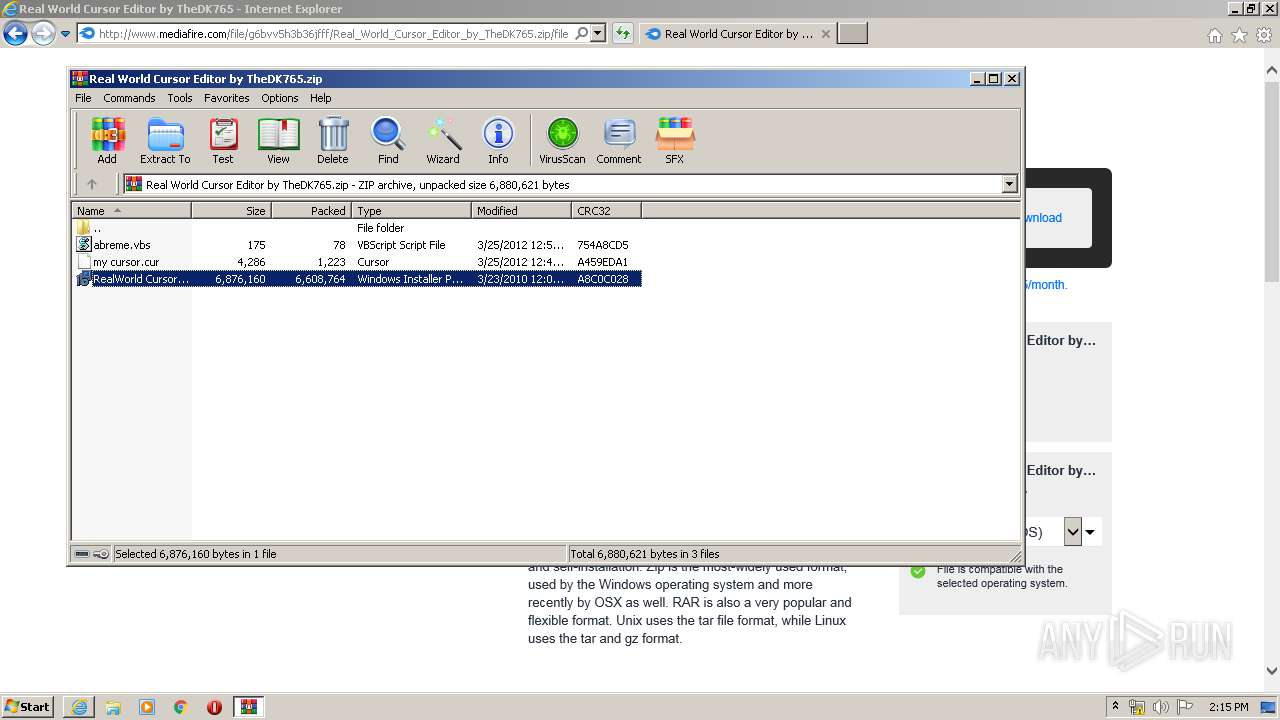
- RWCursorEditor.exe (PID: 3636)
Loads dropped or rewritten executable
- RWCursorEditor.exe (PID: 3636)
SUSPICIOUS
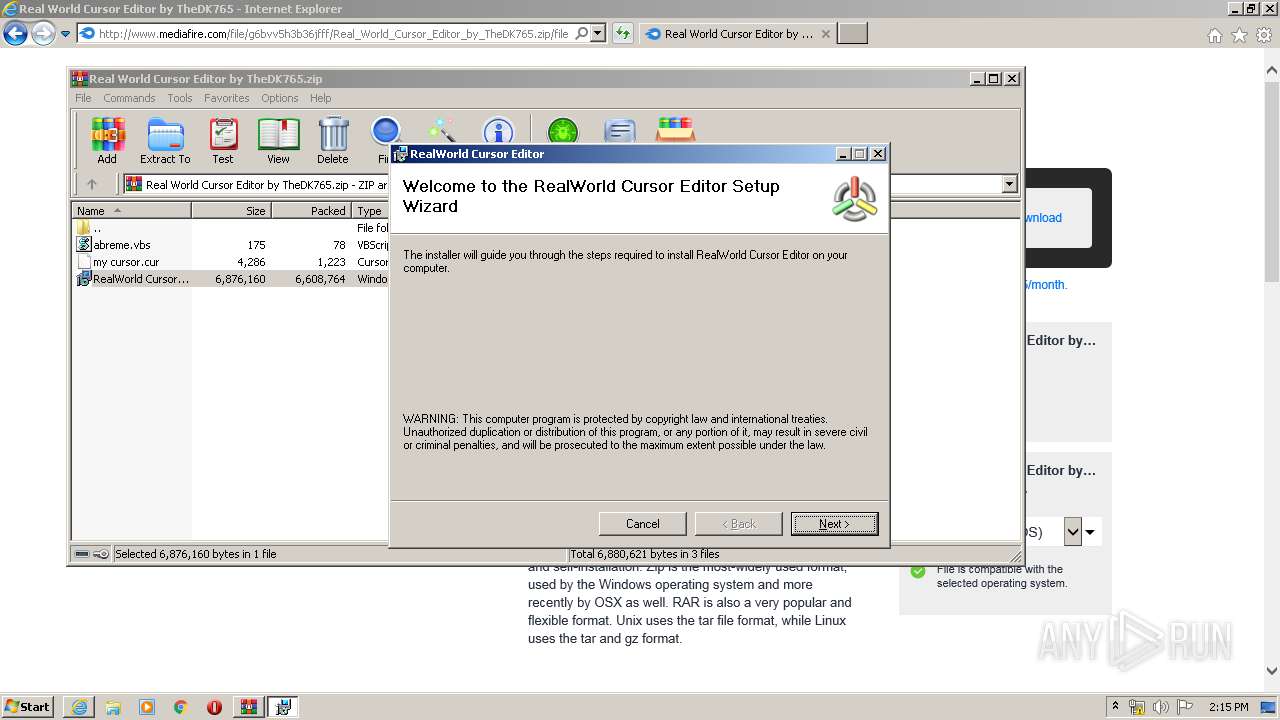
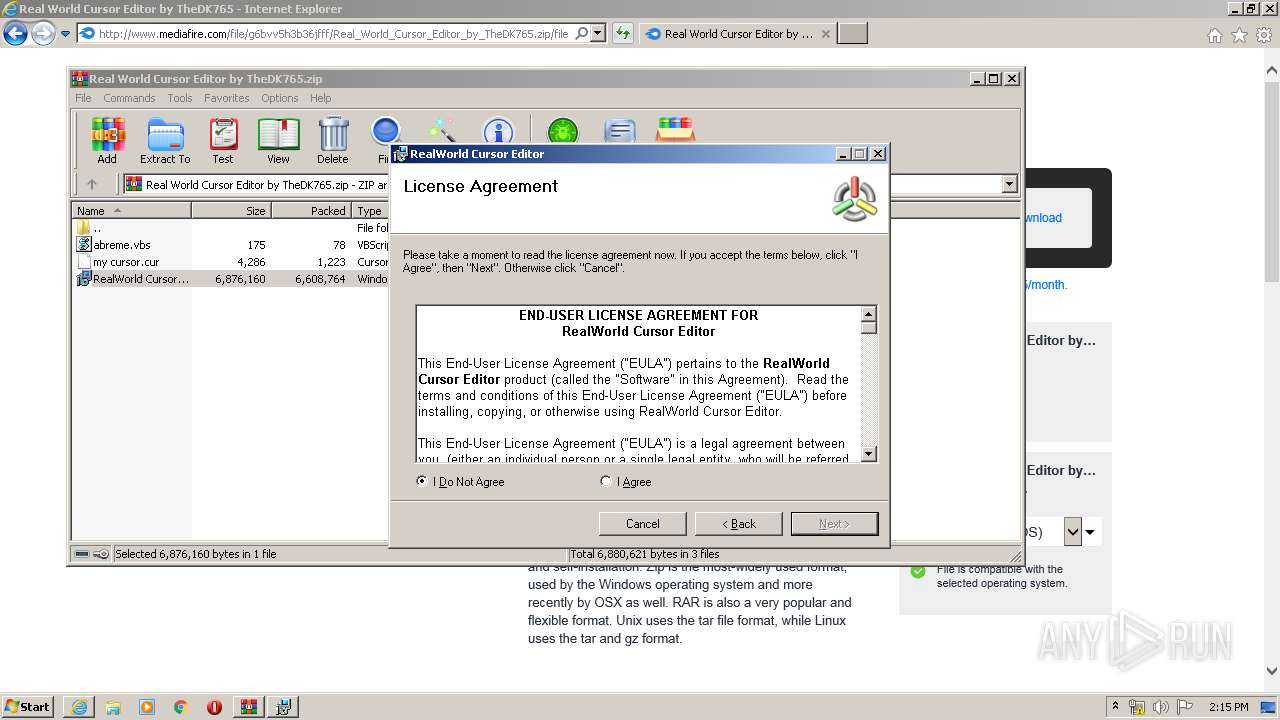
Starts Microsoft Installer
- WinRAR.exe (PID: 2892)
Executed as Windows Service
- vssvc.exe (PID: 3104)
Creates files in the user directory
- msiexec.exe (PID: 2604)
- RWCursorEditor.exe (PID: 3636)
Executes scripts
- WinRAR.exe (PID: 2892)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2604)
Reads Internet Cache Settings
- RWCursorEditor.exe (PID: 3636)
Reads internet explorer settings
- RWCursorEditor.exe (PID: 3636)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 1168)
- iexplore.exe (PID: 3144)
Changes internet zones settings
- iexplore.exe (PID: 3144)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3144)
Creates files in the user directory
- iexplore.exe (PID: 3144)
- iexplore.exe (PID: 1168)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3104)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 2604)
Creates files in the program directory
- msiexec.exe (PID: 2604)
Reads internet explorer settings
- iexplore.exe (PID: 1168)
Creates a software uninstall entry
- msiexec.exe (PID: 2604)
Manual execution by user
- RWCursorEditor.exe (PID: 3636)
Reads settings of System Certificates
- iexplore.exe (PID: 3144)
- iexplore.exe (PID: 1168)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3144)
Changes settings of System certificates
- iexplore.exe (PID: 3144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
9
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa2892.27568\abreme.vbs" | C:\Windows\System32\WScript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3144 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2004 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa2892.28696\abreme.vbs" | C:\Windows\System32\WScript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2604 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2892 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Real World Cursor Editor by TheDK765.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3104 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3144 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://download1509.mediafire.com/6u99o8lz2exg/g6bvv5h3b36jfff/Real+World+Cursor+Editor+by+TheDK765.zip" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3604 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\Rar$EXa2892.30813\RealWorld Cursor Editor.msi" | C:\Windows\System32\msiexec.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3636 | "C:\Program Files\RealWorld Cursor Editor\RWCursorEditor.exe" | C:\Program Files\RealWorld Cursor Editor\RWCursorEditor.exe | explorer.exe | ||||||||||||
User: admin Company: RealWorld Graphics Integrity Level: MEDIUM Description: RealWorld Cursor Editor Exit code: 0 Version: 9.1.7.1 Modules
| |||||||||||||||
Total events
10 580
Read events
3 939
Write events
4 557
Delete events
2 084
Modification events
| (PID) Process: | (3144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 923670018 | |||
| (PID) Process: | (3144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30791342 | |||
| (PID) Process: | (3144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3144) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
38
Suspicious files
109
Text files
127
Unknown types
60
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3144 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1168 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\8QU1CQCK.txt | — | |
MD5:— | SHA256:— | |||
| 1168 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\1UAOJV3W.txt | — | |
MD5:— | SHA256:— | |||
| 1168 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabD828.tmp | — | |
MD5:— | SHA256:— | |||
| 1168 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarD829.tmp | — | |
MD5:— | SHA256:— | |||
| 1168 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\453HF2UZ.txt | text | |
MD5:— | SHA256:— | |||
| 1168 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\master_121423[1].js | text | |
MD5:— | SHA256:— | |||
| 1168 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\mfv3_121423[1].css | text | |
MD5:— | SHA256:— | |||
| 1168 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\download_repair[1].htm | html | |
MD5:— | SHA256:— | |||
| 1168 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
107
TCP/UDP connections
131
DNS requests
61
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1168 | iexplore.exe | GET | 302 | 205.196.123.197:80 | http://download1509.mediafire.com/6u99o8lz2exg/g6bvv5h3b36jfff/Real+World+Cursor+Editor+by+TheDK765.zip | US | — | — | suspicious |
1168 | iexplore.exe | GET | 200 | 104.16.202.237:80 | http://static.mediafire.com/js/master_121423.js | US | text | 152 Kb | shared |
1168 | iexplore.exe | GET | 200 | 216.58.208.35:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
1168 | iexplore.exe | GET | 200 | 216.58.208.35:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
1168 | iexplore.exe | GET | 200 | 216.58.208.35:80 | http://ocsp.pki.goog/gts1o1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEApJpWdKa1WWCAAAAAAoea4%3D | US | der | 471 b | whitelisted |
1168 | iexplore.exe | GET | 200 | 216.58.208.35:80 | http://ocsp.pki.goog/gts1o1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCECI6r%2FoQ2EAVAgAAAABUmZE%3D | US | der | 471 b | whitelisted |
1168 | iexplore.exe | GET | 200 | 216.58.208.35:80 | http://ocsp.pki.goog/gts1o1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEBCnxi%2BvnQqUCAAAAAAoehM%3D | US | der | 471 b | whitelisted |
1168 | iexplore.exe | GET | 200 | 104.16.202.237:80 | http://static.mediafire.com/css/mfv4_121423.php?ver=nonssl&date=2020-01-29 | US | text | 66.1 Kb | shared |
1168 | iexplore.exe | GET | 200 | 104.16.202.237:80 | http://static.mediafire.com/css/mfv3_121423.php?ver=nonssl | US | text | 62.1 Kb | shared |
1168 | iexplore.exe | GET | 200 | 216.58.208.35:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1168 | iexplore.exe | 205.196.123.197:80 | — | MediaFire, LLC | US | unknown |
3144 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1168 | iexplore.exe | 216.58.205.234:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3144 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1168 | iexplore.exe | 216.58.208.35:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
1168 | iexplore.exe | 172.217.22.99:443 | www.gstatic.com | Google Inc. | US | whitelisted |
1168 | iexplore.exe | 172.217.22.35:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
1168 | iexplore.exe | 216.58.208.46:80 | translate.google.com | Google Inc. | US | whitelisted |
1168 | iexplore.exe | 185.60.216.19:80 | connect.facebook.net | Facebook, Inc. | IE | whitelisted |
1168 | iexplore.exe | 216.58.205.238:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download1509.mediafire.com |
| suspicious |
www.mediafire.com |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
static.mediafire.com |
| shared |
fonts.googleapis.com |
| whitelisted |
www.google.com |
| malicious |
ajax.googleapis.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |