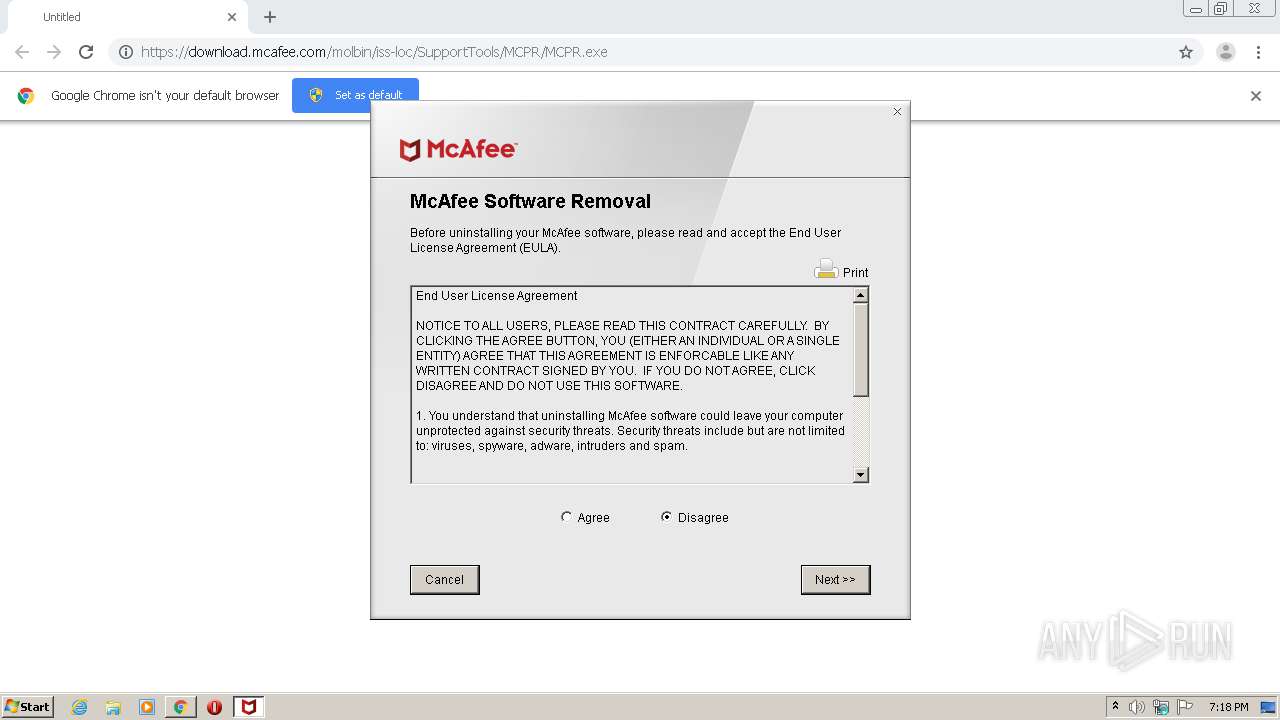
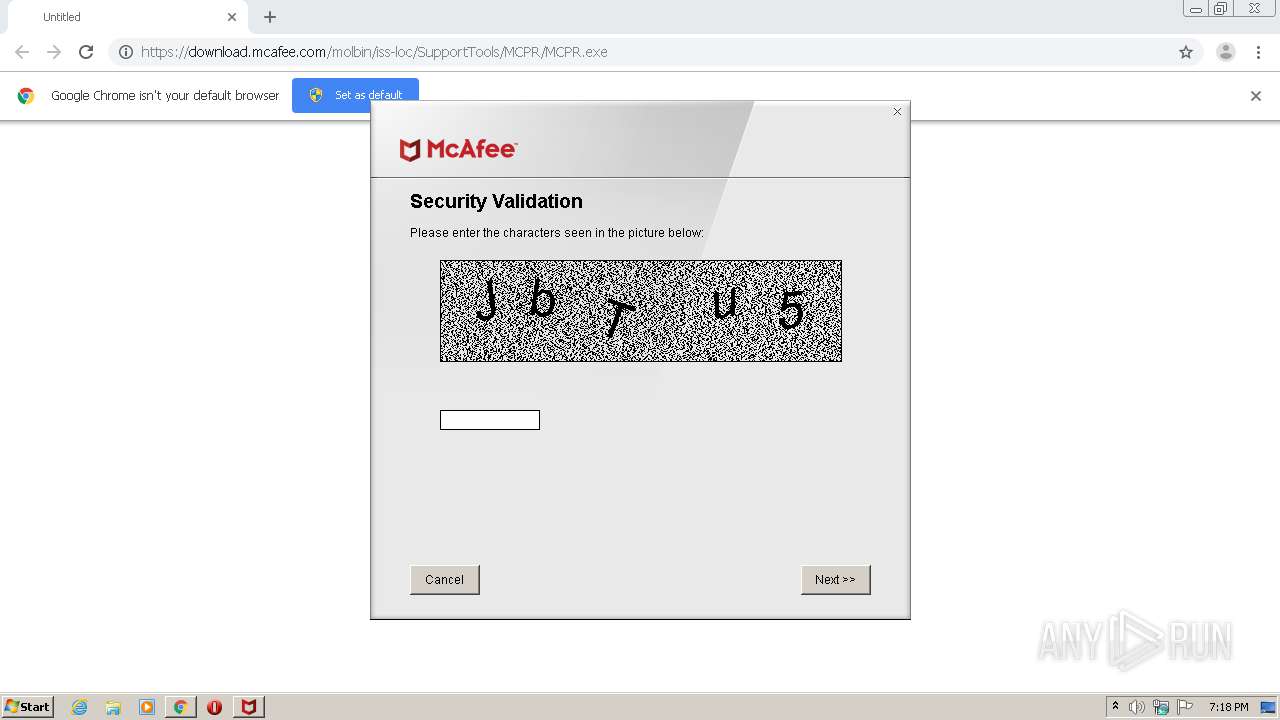
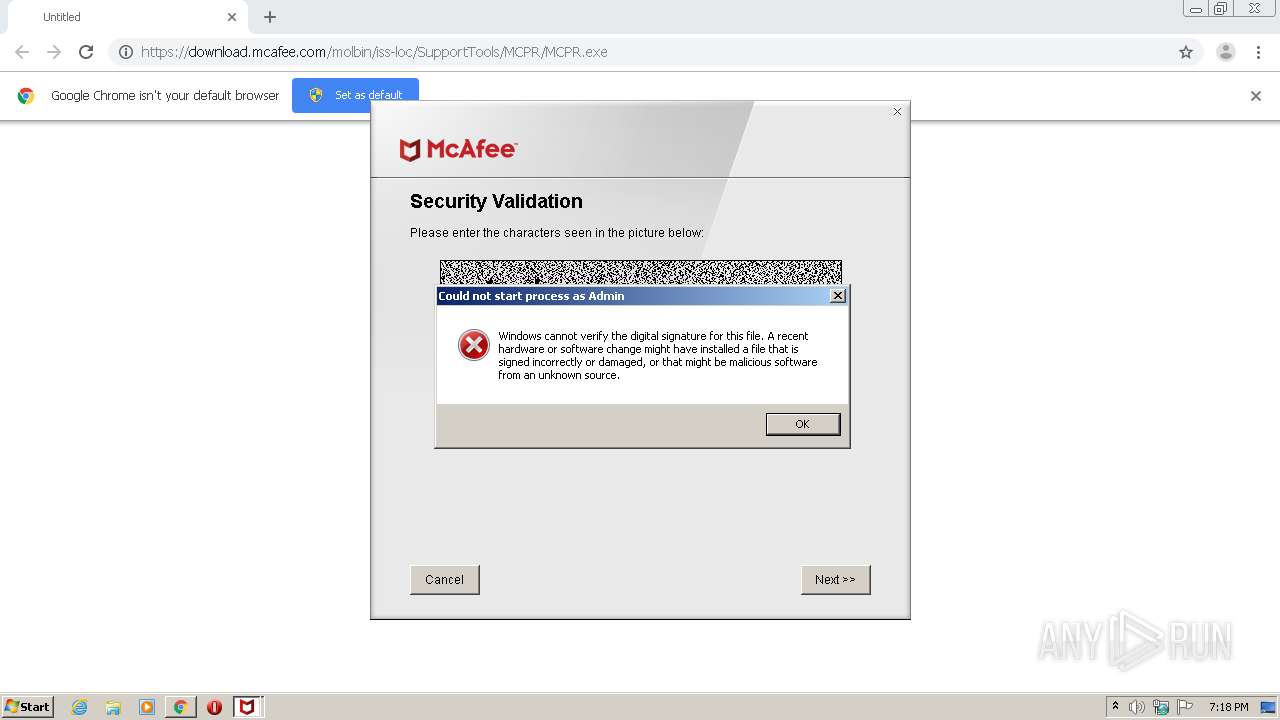
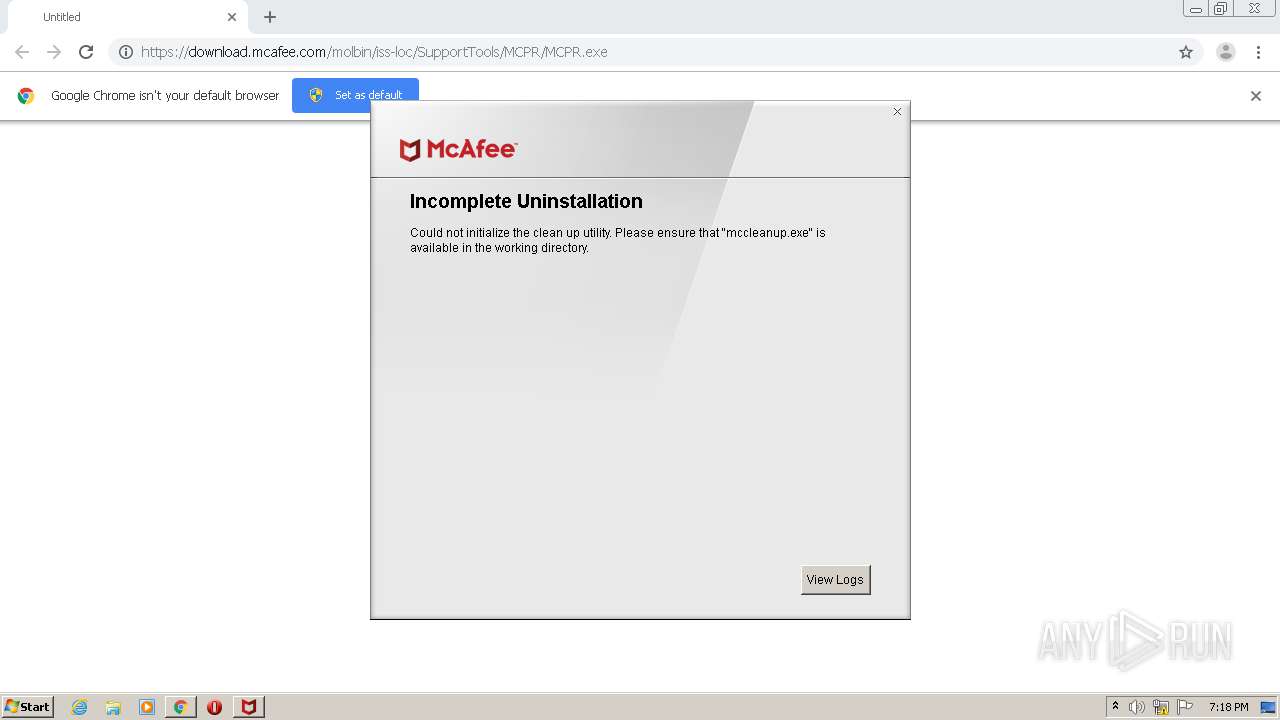
| URL: | https://download.mcafee.com/molbin/iss-loc/SupportTools/MCPR/MCPR.exe |
| Full analysis: | https://app.any.run/tasks/1d125e7b-f091-4e7d-a5fb-d7315c4915af |
| Verdict: | Malicious activity |
| Analysis date: | April 30, 2021, 18:17:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 545DD632E261853E45A85ABCEBCDE157 |
| SHA1: | 5EC2348C64E058853869B464E262E7A24A38ADE4 |
| SHA256: | 544B300BE41DEAD4D0908E956D332B1BB43689DDB9E0C965B610A1DAC8F1D596 |
| SSDEEP: | 3:N8SEl3AyKIT0KKGlVVkvWb9LN:2SK5KIT9VSv69J |
MALICIOUS
Application was dropped or rewritten from another process
- McClnUI.exe (PID: 2452)
- MCPR.exe (PID: 3504)
- MCPR.exe (PID: 1760)
Changes settings of System certificates
- MCPR.exe (PID: 1760)
- McClnUI.exe (PID: 2452)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 868)
- MCPR.exe (PID: 1760)
Adds / modifies Windows certificates
- McClnUI.exe (PID: 2452)
- MCPR.exe (PID: 1760)
Drops a file with too old compile date
- MCPR.exe (PID: 1760)
Drops a file that was compiled in debug mode
- MCPR.exe (PID: 1760)
INFO
Application launched itself
- chrome.exe (PID: 868)
Dropped object may contain Bitcoin addresses
- MCPR.exe (PID: 1760)
Reads the hosts file
- chrome.exe (PID: 868)
- chrome.exe (PID: 2348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
54
Monitored processes
13
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 868 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking "https://download.mcafee.com/molbin/iss-loc/SupportTools/MCPR/MCPR.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
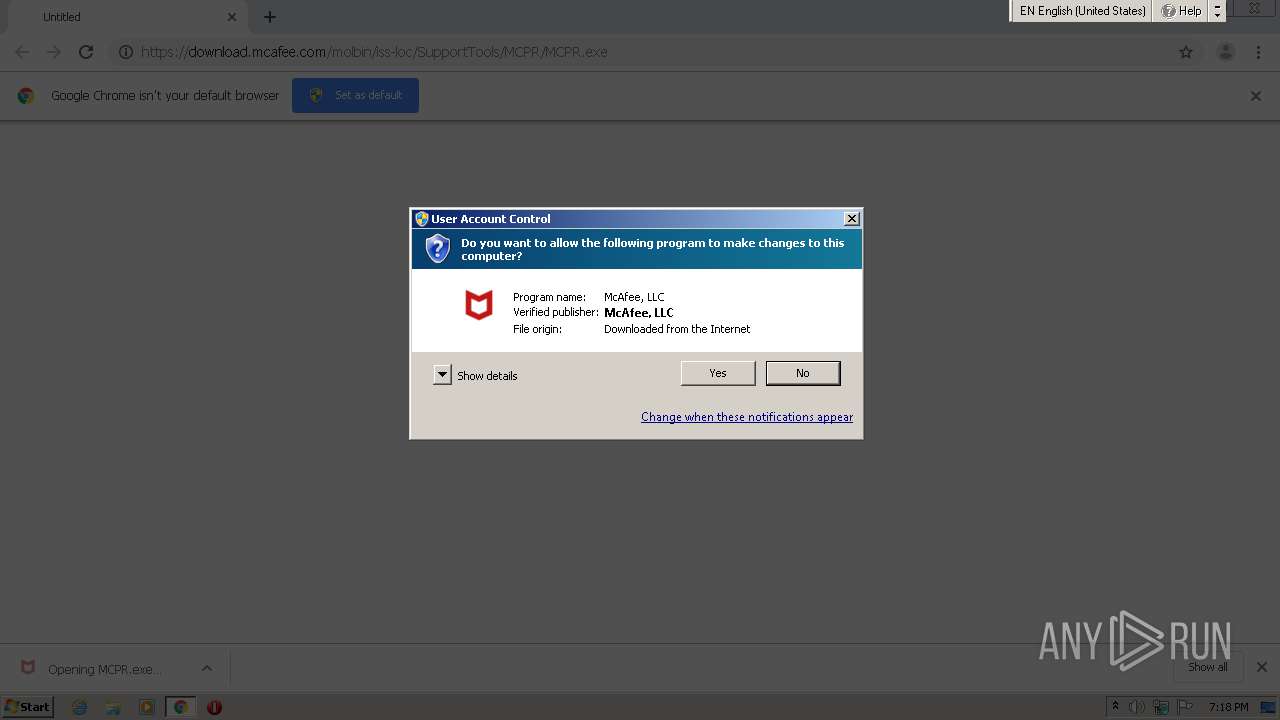
| 1760 | "C:\Users\admin\Downloads\MCPR.exe" | C:\Users\admin\Downloads\MCPR.exe | chrome.exe | ||||||||||||
User: admin Company: McAfee, LLC Integrity Level: HIGH Description: McAfee ESD Package Exit code: 0 Version: 10.3 Modules
| |||||||||||||||
| 1892 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,12920732451611970172,15144806938555574943,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2396332308930051633 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2100 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2348 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,12920732451611970172,15144806938555574943,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=4957249966413071044 --mojo-platform-channel-handle=1496 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2452 | C:\Users\admin\AppData\Local\Temp\MCPR\McClnUI.exe -p StopServices,MFSY,PEF,MXD,CSP,Sustainability,MOCP,MFP,APPSTATS,Auth,EMproxy,FWdiver,HW,MAS,MAT,MBK,MCPR,McProxy,McSvcHost,VUL,MHN,MNA,MOBK,MPFP,MPFPCU,MPS,SHRED,MPSCU,MQC,MQCCU,MSAD,MSHR,MSK,MSKCU,MWL,NMC,RedirSvc,VS,REMEDIATION,MSC,YAP,TRUEKEY,LAM,PCB,MGS,Symlink,SafeConnect,MGS,RESIDUE | C:\Users\admin\AppData\Local\Temp\MCPR\McClnUI.exe | MCPR.exe | ||||||||||||
User: admin Company: McAfee, LLC Integrity Level: HIGH Description: McAfee CleanUp Tool Exit code: 0 Version: 10.3.115.0 Modules
| |||||||||||||||
| 2652 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,12920732451611970172,15144806938555574943,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=4217928837817619389 --mojo-platform-channel-handle=1108 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2664 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1012,12920732451611970172,15144806938555574943,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=15445607864000209815 --mojo-platform-channel-handle=1024 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=960 --on-initialized-event-handle=316 --parent-handle=320 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 3348 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6f93a9d0,0x6f93a9e0,0x6f93a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 3504 | "C:\Users\admin\Downloads\MCPR.exe" | C:\Users\admin\Downloads\MCPR.exe | — | chrome.exe | |||||||||||
User: admin Company: McAfee, LLC Integrity Level: MEDIUM Description: McAfee ESD Package Exit code: 3221226540 Version: 10.3 Modules
| |||||||||||||||
Total events
1 323
Read events
1 235
Write events
85
Delete events
3
Modification events
| (PID) Process: | (868) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (868) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (868) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (868) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (868) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 868-13264280271417500 |
Value: 259 | |||
| (PID) Process: | (868) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (868) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (868) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (868) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
34
Suspicious files
105
Text files
468
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 868 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-608C49D0-364.pma | — | |
MD5:— | SHA256:— | |||
| 868 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 868 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
| 868 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF14fb46.TMP | — | |
MD5:— | SHA256:— | |||
| 868 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\71565e90-5fc7-462a-a9d6-c02a4ee0d8ff.tmp | — | |
MD5:— | SHA256:— | |||
| 868 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 868 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old | — | |
MD5:— | SHA256:— | |||
| 868 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old | — | |
MD5:— | SHA256:— | |||
| 868 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 868 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF14fe06.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
13
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2452 | McClnUI.exe | GET | 200 | 8.248.145.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.2 Kb | whitelisted |
2452 | McClnUI.exe | GET | 304 | 8.248.145.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.2 Kb | whitelisted |
2452 | McClnUI.exe | GET | 304 | 8.248.145.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.2 Kb | whitelisted |
2452 | McClnUI.exe | GET | 304 | 8.248.145.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.2 Kb | whitelisted |
2452 | McClnUI.exe | GET | 304 | 8.248.145.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.2 Kb | whitelisted |
2452 | McClnUI.exe | GET | 304 | 8.248.145.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.2 Kb | whitelisted |
2452 | McClnUI.exe | GET | 304 | 8.248.145.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.2 Kb | whitelisted |
2452 | McClnUI.exe | GET | 304 | 8.248.145.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.2 Kb | whitelisted |
2452 | McClnUI.exe | GET | 304 | 8.248.145.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.2 Kb | whitelisted |
2452 | McClnUI.exe | GET | 304 | 8.248.145.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.2 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2452 | McClnUI.exe | 8.248.145.254:80 | www.download.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
2452 | McClnUI.exe | 104.40.53.219:443 | prd-mcafee-mosaic-pub.azurewebsites.net | Microsoft Corporation | US | suspicious |
2348 | chrome.exe | 104.79.88.7:443 | download.mcafee.com | Time Warner Cable Internet LLC | US | malicious |
2348 | chrome.exe | 142.250.74.195:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2452 | McClnUI.exe | 104.79.88.184:443 | sadownload.mcafee.com | Time Warner Cable Internet LLC | US | unknown |
— | — | 104.208.16.0:443 | cu1pehnswss01.servicebus.windows.net | Microsoft Corporation | US | unknown |
2348 | chrome.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.mcafee.com |
| malicious |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
sadownload.mcafee.com |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
prd-mcafee-mosaic-pub.azurewebsites.net |
| suspicious |
cu1pehnswss01.servicebus.windows.net |
| unknown |