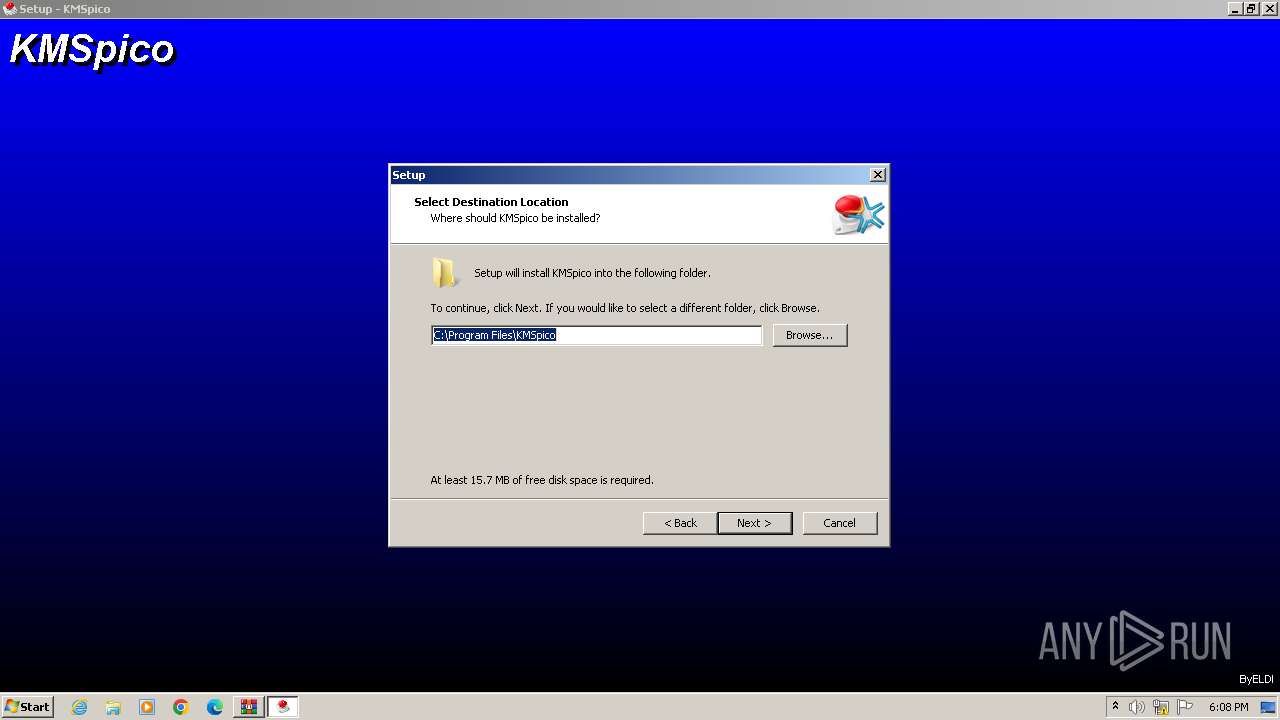
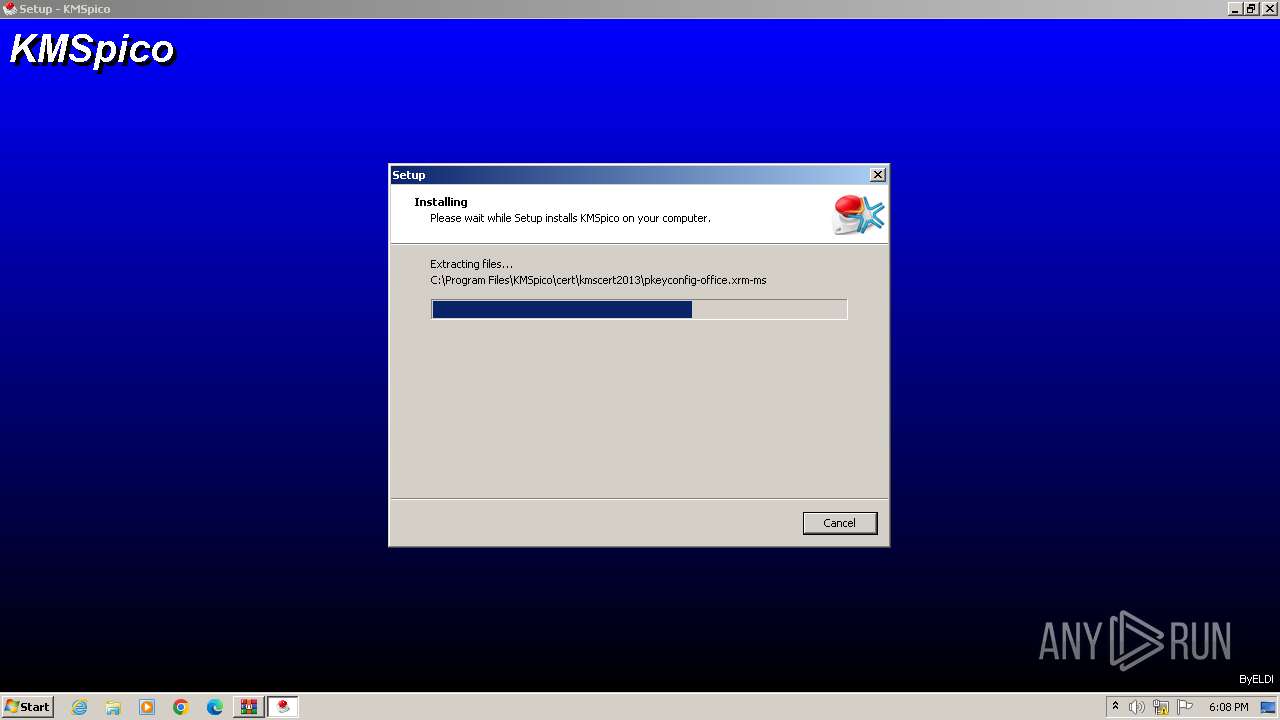
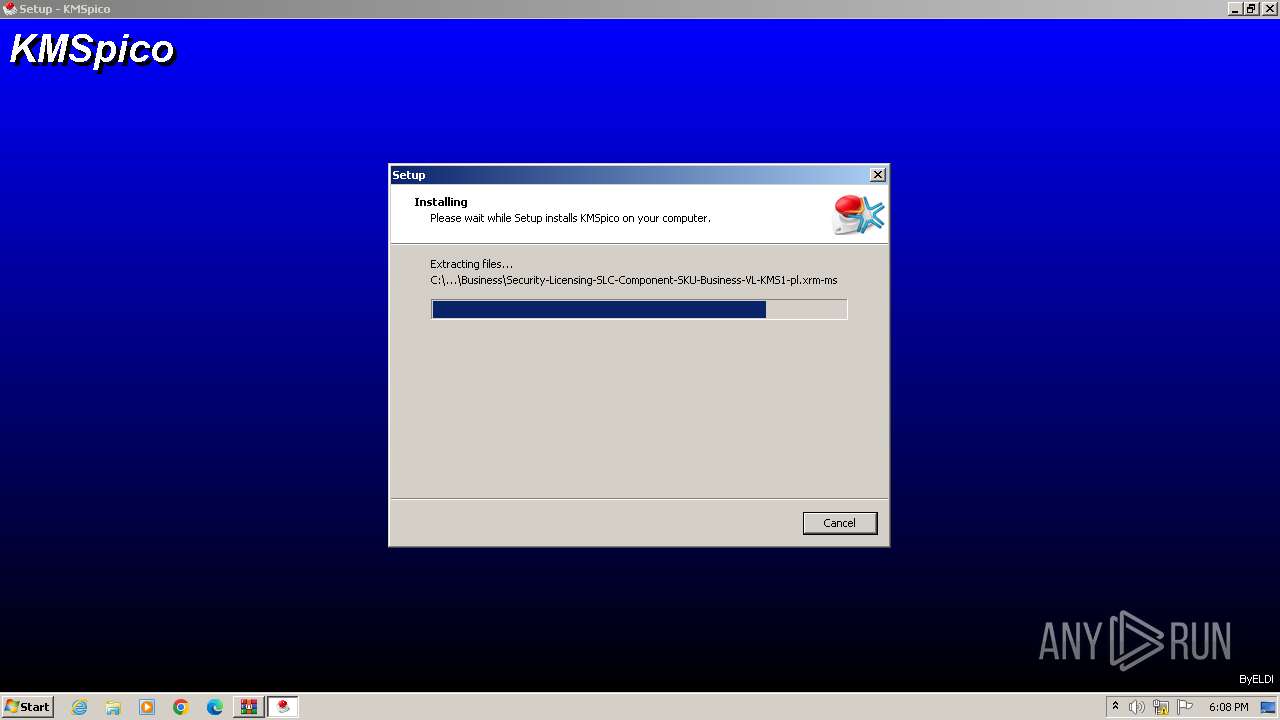
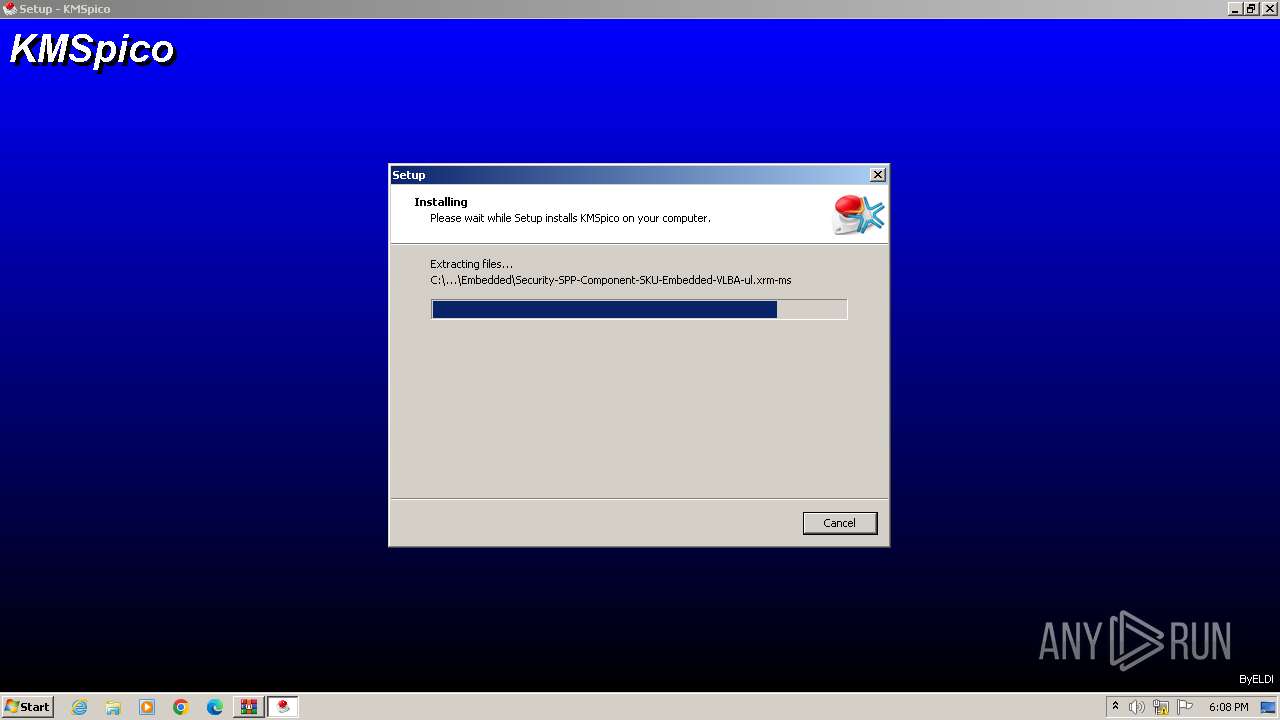
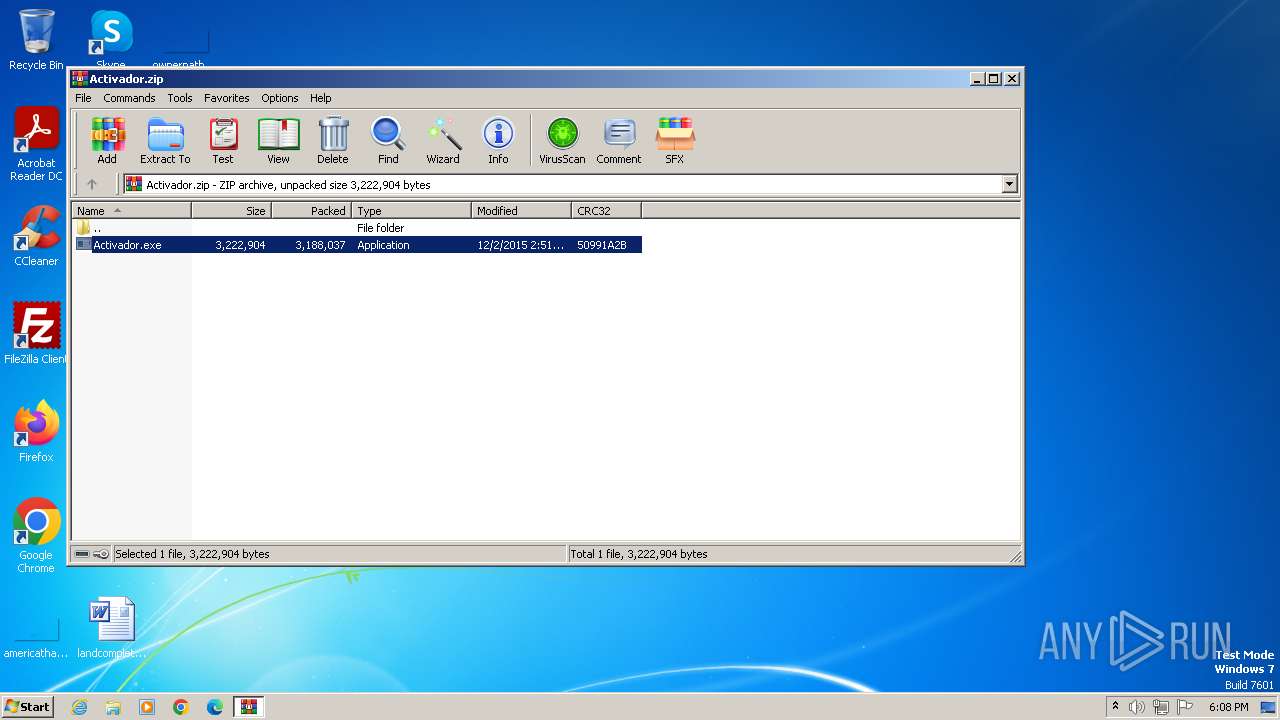
| File name: | Activador.zip |
| Full analysis: | https://app.any.run/tasks/c8bccfba-3d36-4095-b6bd-c8ccd7011194 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2023, 18:07:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 912C65FBF54CECB90F398BF79A3635A8 |
| SHA1: | 50E32E41E053390D112A0D16A9C6F8E58029A18B |
| SHA256: | 543EA9BBFF390B77E7C45B645AD7EA1C6F52838A788F6A92772DE775E8AE65F1 |
| SSDEEP: | 98304:lOumKqav3ebKd9BBmhoZzmhamIOyDBh7RHsZ2UvhndEbmMggt2HYbPDArxGSmtef:b7+WCpe5a |
MALICIOUS
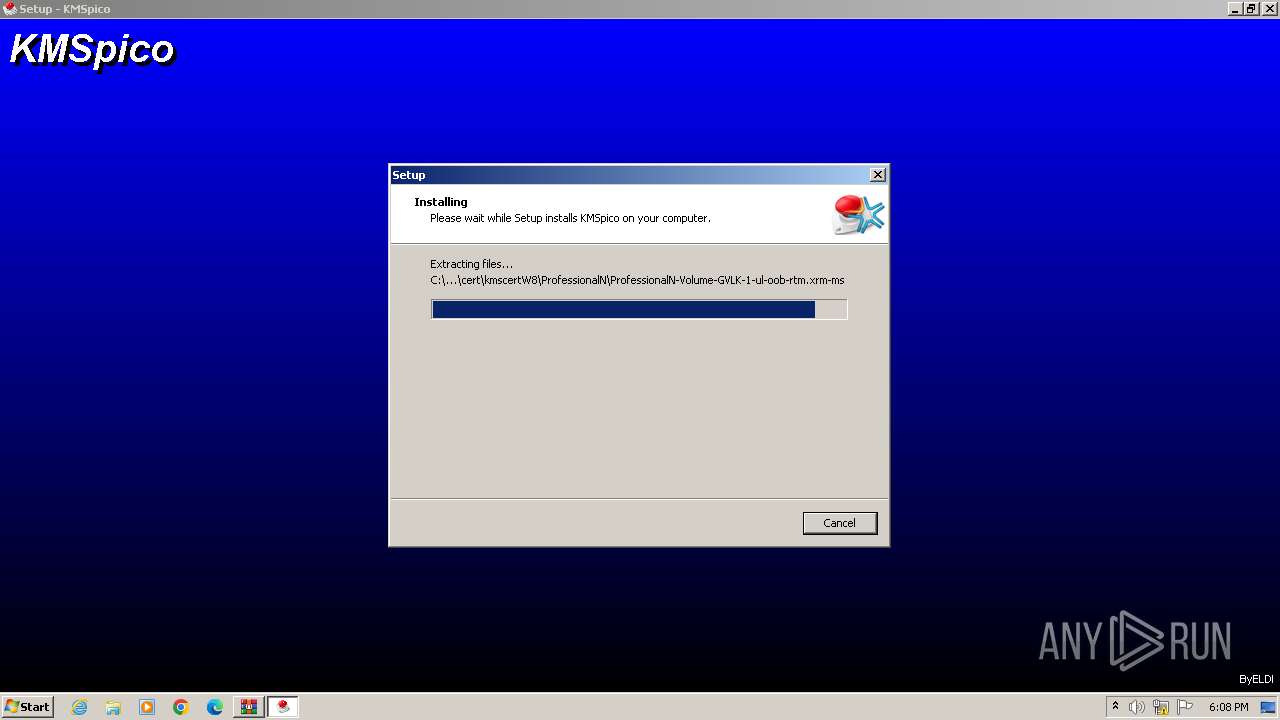
Drops the executable file immediately after the start
- Activador.exe (PID: 1088)
- Activador.exe (PID: 2300)
- Activador.tmp (PID: 600)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3144)
Creates a writable file in the system directory
- Activador.tmp (PID: 600)
SUSPICIOUS
Reads the Windows owner or organization settings
- Activador.tmp (PID: 600)
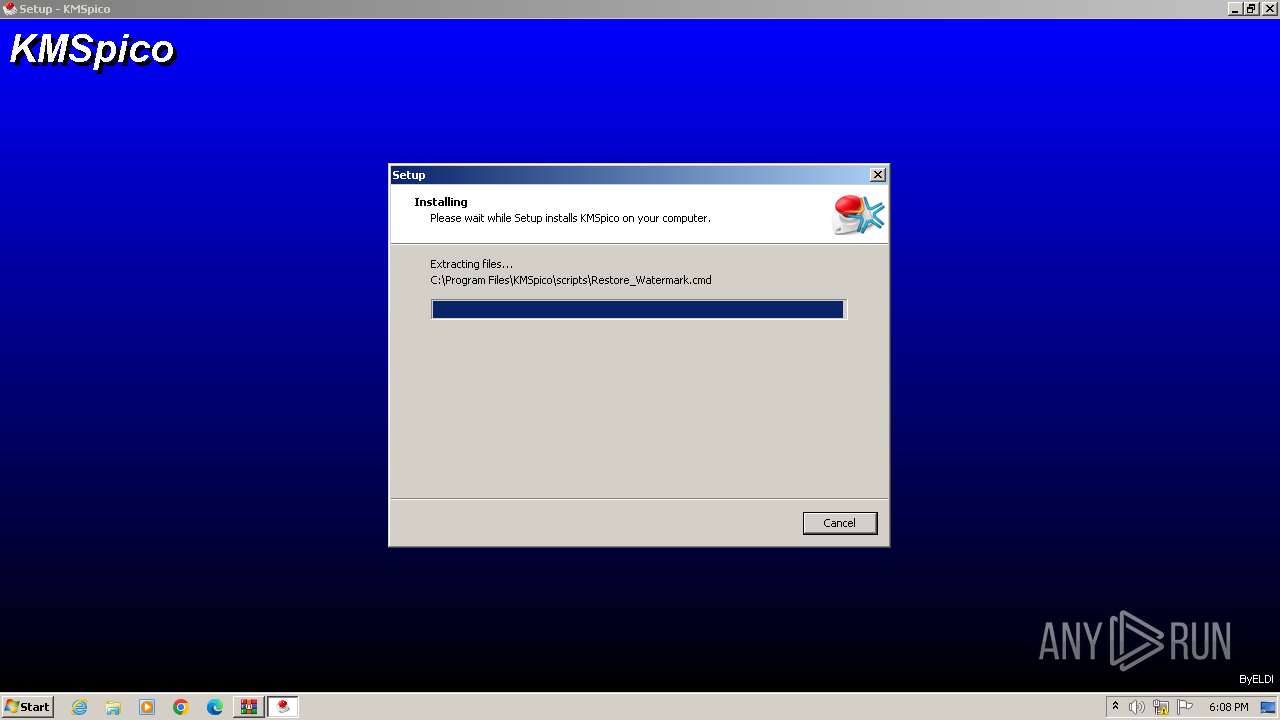
Executing commands from ".cmd" file
- Activador.tmp (PID: 600)
Starts SC.EXE for service management
- cmd.exe (PID: 1860)
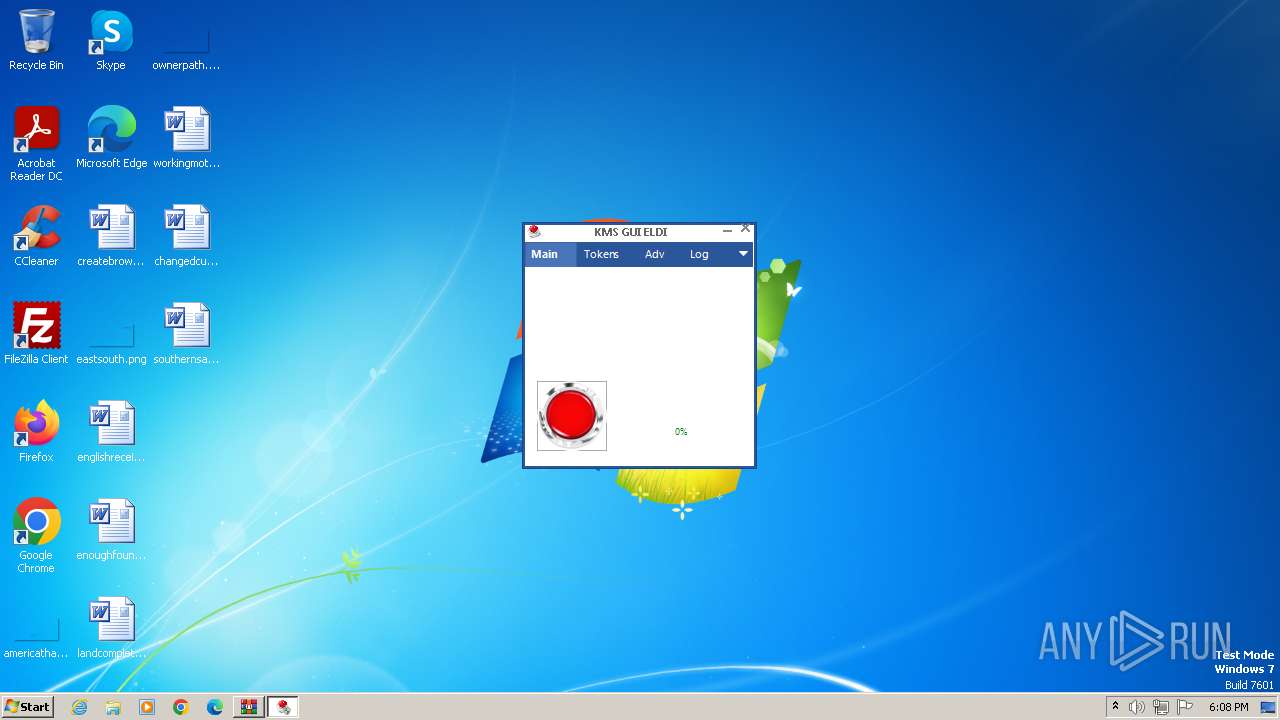
Creates or modifies Windows services
- KMSELDI.exe (PID: 240)
Starts CMD.EXE for commands execution
- Activador.tmp (PID: 600)
Process drops legitimate windows executable
- Activador.tmp (PID: 600)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3048)
Checks supported languages
- Activador.exe (PID: 1088)
- Activador.exe (PID: 2300)
- Activador.tmp (PID: 600)
- Activador.tmp (PID: 2620)
- UninsHs.exe (PID: 1608)
- KMSELDI.exe (PID: 240)
- wmpnscfg.exe (PID: 2128)
- AutoPico.exe (PID: 3396)
- KMSELDI.exe (PID: 2380)
Create files in a temporary directory
- Activador.exe (PID: 1088)
- Activador.exe (PID: 2300)
- Activador.tmp (PID: 600)
Reads the computer name
- Activador.tmp (PID: 2620)
- KMSELDI.exe (PID: 240)
- AutoPico.exe (PID: 3396)
- KMSELDI.exe (PID: 2380)
- wmpnscfg.exe (PID: 2128)
- Activador.tmp (PID: 600)
Reads the machine GUID from the registry
- KMSELDI.exe (PID: 240)
- AutoPico.exe (PID: 3396)
- KMSELDI.exe (PID: 2380)
Reads Environment values
- KMSELDI.exe (PID: 240)
- AutoPico.exe (PID: 3396)
- KMSELDI.exe (PID: 2380)
Reads product name
- KMSELDI.exe (PID: 240)
- AutoPico.exe (PID: 3396)
- KMSELDI.exe (PID: 2380)
Creates files in the program directory
- AutoPico.exe (PID: 3396)
- KMSELDI.exe (PID: 240)
- KMSELDI.exe (PID: 2380)
- Activador.tmp (PID: 600)
Reads Microsoft Office registry keys
- AutoPico.exe (PID: 3396)
- KMSELDI.exe (PID: 240)
- KMSELDI.exe (PID: 2380)
Manual execution by a user
- KMSELDI.exe (PID: 2380)
- wmpnscfg.exe (PID: 2128)
- KMSELDI.exe (PID: 2488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2015:12:01 21:51:40 |
| ZipCRC: | 0x50991a2b |
| ZipCompressedSize: | 3188037 |
| ZipUncompressedSize: | 3222904 |
| ZipFileName: | Activador.exe |
Total processes
62
Monitored processes
15
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Program Files\KMSpico\KMSELDI.exe" /silent /backup | C:\Program Files\KMSpico\KMSELDI.exe | Activador.tmp | ||||||||||||
User: admin Company: @ByELDI Integrity Level: HIGH Description: KMS GUI ELDI Exit code: 4294967295 Version: 37.0.0.0 Modules
| |||||||||||||||
| 600 | "C:\Users\admin\AppData\Local\Temp\is-KV1PH.tmp\Activador.tmp" /SL5="$13016C,2946007,69120,C:\Users\admin\AppData\Local\Temp\Rar$EXa3048.26323\Activador.exe" /SPAWNWND=$E012E /NOTIFYWND=$1001F6 | C:\Users\admin\AppData\Local\Temp\is-KV1PH.tmp\Activador.tmp | — | Activador.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1088 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3048.26323\Activador.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3048.26323\Activador.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: KMSpico Setup Exit code: 0 Version: 10.1.9 Modules
| |||||||||||||||
| 1608 | "C:\Program Files\KMSpico\UninsHs.exe" /r0=KMSpico,default,C:\Users\admin\AppData\Local\Temp\Rar$EXa3048.26323\Activador.exe | C:\Program Files\KMSpico\UninsHs.exe | — | Activador.tmp | |||||||||||
User: admin Company: Han-soft Integrity Level: HIGH Description: Uninstall for InnoSetup by Han-soft Exit code: 0 Version: 2.1.0.283 Modules
| |||||||||||||||
| 1860 | "C:\Windows\system32\cmd.exe" /C ""C:\Program Files\KMSpico\scripts\Install_Service.cmd"" | C:\Windows\System32\cmd.exe | — | Activador.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2128 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2300 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3048.26323\Activador.exe" /SPAWNWND=$E012E /NOTIFYWND=$1001F6 | C:\Users\admin\AppData\Local\Temp\Rar$EXa3048.26323\Activador.exe | Activador.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: KMSpico Setup Exit code: 0 Version: 10.1.9 Modules
| |||||||||||||||
| 2380 | "C:\Program Files\KMSpico\KMSELDI.exe" | C:\Program Files\KMSpico\KMSELDI.exe | explorer.exe | ||||||||||||
User: admin Company: @ByELDI Integrity Level: HIGH Description: KMS GUI ELDI Exit code: 0 Version: 37.0.0.0 Modules
| |||||||||||||||
| 2488 | "C:\Program Files\KMSpico\KMSELDI.exe" | C:\Program Files\KMSpico\KMSELDI.exe | — | explorer.exe | |||||||||||
User: admin Company: @ByELDI Integrity Level: MEDIUM Description: KMS GUI ELDI Exit code: 3221226540 Version: 37.0.0.0 Modules
| |||||||||||||||
| 2620 | "C:\Users\admin\AppData\Local\Temp\is-E2OVN.tmp\Activador.tmp" /SL5="$1001F6,2946007,69120,C:\Users\admin\AppData\Local\Temp\Rar$EXa3048.26323\Activador.exe" | C:\Users\admin\AppData\Local\Temp\is-E2OVN.tmp\Activador.tmp | — | Activador.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
Total events
4 749
Read events
4 694
Write events
49
Delete events
6
Modification events
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3048) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
22
Suspicious files
35
Text files
718
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1088 | Activador.exe | C:\Users\admin\AppData\Local\Temp\is-E2OVN.tmp\Activador.tmp | executable | |
MD5:1778C1F66FF205875A6435A33229AB3C | SHA256:95C06ACAC4FE4598840E5556F9613D43AA1039C52DAC64536F59E45A70F79DA6 | |||
| 600 | Activador.tmp | C:\Program Files\KMSpico\is-ANMCN.tmp | executable | |
MD5:30C7E8E918403B9247315249A8842CE5 | SHA256:6D4FA6727CA952B7B44FA9F3538D84B64E06C76908C76FADE7846532A7115A49 | |||
| 3048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3048.26323\Activador.exe | executable | |
MD5:1A5FC26D8596C2573C7A5E480FB94724 | SHA256:3F1EA290FBA74C05430E50488A3CE7C146F7328FCE21F6F41A098FD68FA09DA6 | |||
| 600 | Activador.tmp | C:\Program Files\KMSpico\is-19Q6R.tmp | executable | |
MD5:CC4D231DF34E57F59EB970353C7D9DE2 | SHA256:AFC8A00883A4EA07DF2DC1D4ED02F8A23B35C9456413B438A2D9CE3AE5076638 | |||
| 600 | Activador.tmp | C:\Program Files\KMSpico\unins000.exe | executable | |
MD5:30C7E8E918403B9247315249A8842CE5 | SHA256:6D4FA6727CA952B7B44FA9F3538D84B64E06C76908C76FADE7846532A7115A49 | |||
| 600 | Activador.tmp | C:\Windows\System32\Vestris.ResourceLib.dll | executable | |
MD5:3D733144477CADCF77009EF614413630 | SHA256:392D73617FD0A55218261572ECE2F50301E0CFA29B5ED24C3F692130AA406AF3 | |||
| 600 | Activador.tmp | C:\Program Files\KMSpico\is-712EN.tmp | executable | |
MD5:ABEB893CE2EB23F410057294A59A81C0 | SHA256:01976B54C70D0E7EBD2E185E415F1F92689CE02805A0E6EF99C796DED3BB261B | |||
| 600 | Activador.tmp | C:\Program Files\KMSpico\is-OHT2O.tmp | executable | |
MD5:F15C15D2D2A29BC84C6DA752A1D403A9 | SHA256:D934F4619C39F88D9630AAD2136AF719E6C20976B5FBFA77BBA3D97D3728D5E4 | |||
| 600 | Activador.tmp | C:\Program Files\KMSpico\is-KHSP8.tmp | executable | |
MD5:437B423586BC2DB5957EDB2B672CB7F1 | SHA256:A0CA411AAEBD5D38D0536738FDEB72589A33FA7CA5CC0E9E7C98033D32611111 | |||
| 600 | Activador.tmp | C:\Windows\system32\is-UN5RA.tmp | executable | |
MD5:3D733144477CADCF77009EF614413630 | SHA256:392D73617FD0A55218261572ECE2F50301E0CFA29B5ED24C3F692130AA406AF3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
240 | KMSELDI.exe | 75.119.140.230:123 | 1.pool.ntp.org | — | — | unknown |
3396 | AutoPico.exe | 176.9.157.155:123 | 1.pool.ntp.org | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
1.pool.ntp.org |
| whitelisted |
2.pool.ntp.org |
| whitelisted |
www.google.com |
| whitelisted |