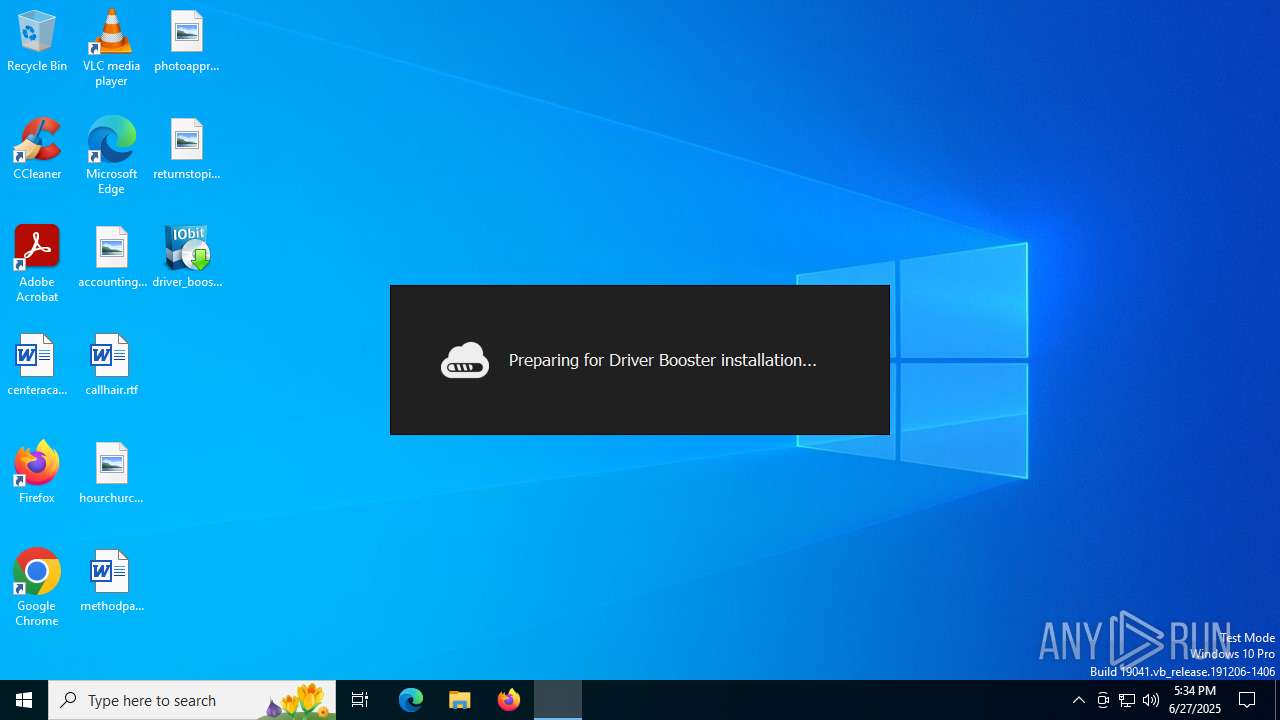
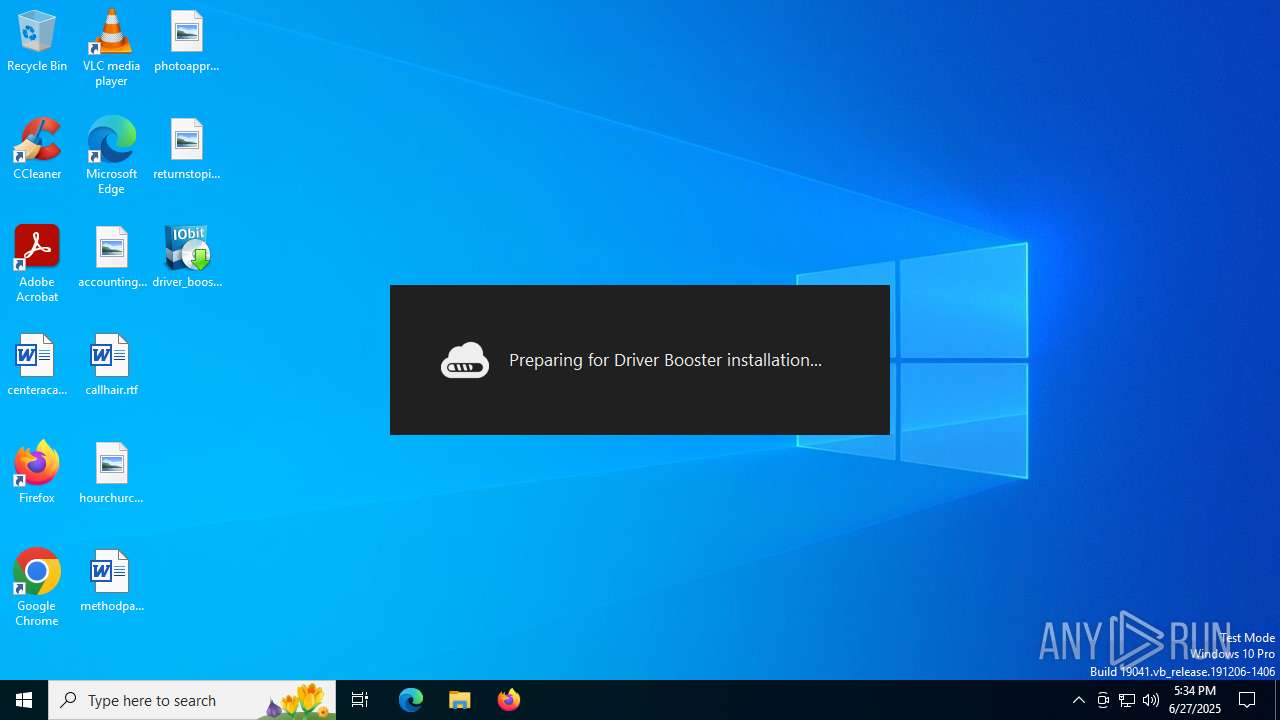
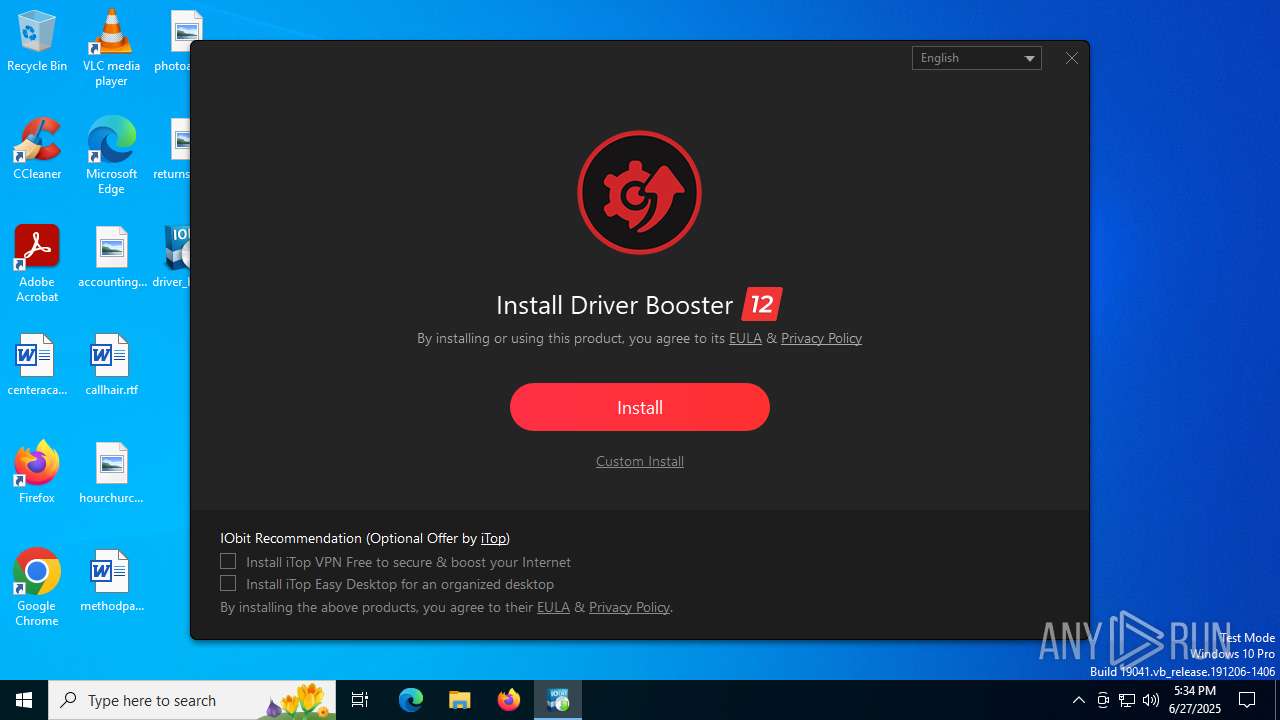
| File name: | driver_booster_setup.exe |
| Full analysis: | https://app.any.run/tasks/d60aecf7-8533-4a7e-b5d8-8b11265e3df7 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2025, 17:34:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | E55F001517B5CF9C5C3E7A458268B55B |
| SHA1: | BFA6E085083690A829CCE920C63906AEE2D82295 |
| SHA256: | 542F0227D98B75FDB8BB9665500C3A998004BB92F1CDDDD32F65119237FF1C99 |
| SSDEEP: | 196608:RdBuez5N2TwNjMpVP4MhzyviZDDP+f41VPlMtVYwsD7SC5Cho4rNlOQ:TBuWawgQlgm4HPatVYwsD7Sw14riQ |
MALICIOUS
Application was injected by another process
- explorer.exe (PID: 4772)
Runs injected code in another process
- ICONPIN64.exe (PID: 3756)
SUSPICIOUS
Executable content was dropped or overwritten
- driver_booster_setup.exe (PID: 7116)
- driver_booster_setup.exe (PID: 1324)
- driver_booster_setup.tmp (PID: 6788)
- driver_booster_setup.exe (PID: 4520)
- driver_booster_setup.tmp (PID: 6512)
- HWiNFO.exe (PID: 3740)
Reads security settings of Internet Explorer
- driver_booster_setup.tmp (PID: 5172)
- driver_booster_setup.tmp (PID: 6788)
- driver_booster_setup.tmp (PID: 6512)
- AutoUpdate.exe (PID: 2040)
Reads the Windows owner or organization settings
- driver_booster_setup.tmp (PID: 6788)
- driver_booster_setup.tmp (PID: 6512)
Searches for installed software
- setup.exe (PID: 6180)
- InstStat.exe (PID: 7000)
Process drops SQLite DLL files
- driver_booster_setup.tmp (PID: 6512)
Drops 7-zip archiver for unpacking
- driver_booster_setup.tmp (PID: 6512)
Process drops legitimate windows executable
- driver_booster_setup.tmp (PID: 6512)
Drops a system driver (possible attempt to evade defenses)
- HWiNFO.exe (PID: 3740)
INFO
Reads the computer name
- driver_booster_setup.tmp (PID: 5172)
- driver_booster_setup.tmp (PID: 6788)
- setup.exe (PID: 6180)
- driver_booster_setup.tmp (PID: 6512)
- HWiNFO.exe (PID: 3740)
- SetupHlp.exe (PID: 5628)
- AutoUpdate.exe (PID: 2040)
- InstStat.exe (PID: 7000)
Checks supported languages
- driver_booster_setup.exe (PID: 1324)
- driver_booster_setup.exe (PID: 7116)
- driver_booster_setup.tmp (PID: 5172)
- driver_booster_setup.tmp (PID: 6788)
- setup.exe (PID: 6180)
- driver_booster_setup.tmp (PID: 6512)
- driver_booster_setup.exe (PID: 4520)
- SetupHlp.exe (PID: 5628)
- HWiNFO.exe (PID: 3740)
- RttHlp.exe (PID: 3720)
- AutoUpdate.exe (PID: 2040)
- rma.exe (PID: 4984)
- ICONPIN64.exe (PID: 3756)
- InstStat.exe (PID: 7000)
Process checks computer location settings
- driver_booster_setup.tmp (PID: 5172)
- driver_booster_setup.tmp (PID: 6788)
- driver_booster_setup.tmp (PID: 6512)
- AutoUpdate.exe (PID: 2040)
Create files in a temporary directory
- driver_booster_setup.exe (PID: 7116)
- driver_booster_setup.exe (PID: 1324)
- driver_booster_setup.tmp (PID: 6788)
- driver_booster_setup.exe (PID: 4520)
- setup.exe (PID: 6180)
- driver_booster_setup.tmp (PID: 6512)
- HWiNFO.exe (PID: 3740)
- ICONPIN64.exe (PID: 3756)
- explorer.exe (PID: 4772)
The sample compiled with english language support
- driver_booster_setup.tmp (PID: 6788)
- driver_booster_setup.tmp (PID: 6512)
- HWiNFO.exe (PID: 3740)
Creates files in the program directory
- setup.exe (PID: 6180)
- driver_booster_setup.tmp (PID: 6512)
- SetupHlp.exe (PID: 5628)
- RttHlp.exe (PID: 3720)
- AutoUpdate.exe (PID: 2040)
- InstStat.exe (PID: 7000)
Reads the machine GUID from the registry
- setup.exe (PID: 6180)
- AutoUpdate.exe (PID: 2040)
- ICONPIN64.exe (PID: 3756)
- InstStat.exe (PID: 7000)
Compiled with Borland Delphi (YARA)
- setup.exe (PID: 6180)
- driver_booster_setup.exe (PID: 4520)
- driver_booster_setup.tmp (PID: 6512)
- slui.exe (PID: 1828)
- notepad.exe (PID: 4512)
Creates files or folders in the user directory
- setup.exe (PID: 6180)
- AutoUpdate.exe (PID: 2040)
- explorer.exe (PID: 4772)
- InstStat.exe (PID: 7000)
Detects InnoSetup installer (YARA)
- driver_booster_setup.exe (PID: 4520)
- driver_booster_setup.tmp (PID: 6512)
Creates a software uninstall entry
- driver_booster_setup.tmp (PID: 6512)
The sample compiled with arabic language support
- driver_booster_setup.tmp (PID: 6512)
Manual execution by a user
- notepad.exe (PID: 4512)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4772)
- notepad.exe (PID: 4512)
Checks proxy server information
- slui.exe (PID: 1828)
Reads the software policy settings
- slui.exe (PID: 1828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (42.6) |
|---|---|---|
| .exe | | | Win16/32 Executable Delphi generic (19.5) |
| .exe | | | Generic Win/DOS Executable (18.9) |
| .exe | | | DOS Executable Generic (18.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:06:14 13:27:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 66560 |
| InitializedDataSize: | 71680 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1181c |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 12.5.0.597 |
| ProductVersionNumber: | 12.5.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | IObit |
| FileDescription: | Driver Booster 12 Setup |
| FileVersion: | 12.5.0.597 |
| LegalCopyright: | © IObit. All rights reserved. |
| ProductName: | Driver Booster 12 |
| ProductVersion: | 12.5 |
Total processes
138
Monitored processes
17
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1324 | "C:\Users\admin\Desktop\driver_booster_setup.exe" /SPAWNWND=$50306 /NOTIFYWND=$702F8 | C:\Users\admin\Desktop\driver_booster_setup.exe | driver_booster_setup.tmp | ||||||||||||
User: admin Company: IObit Integrity Level: HIGH Description: Driver Booster 12 Setup Exit code: 1 Version: 12.5.0.597 Modules
| |||||||||||||||
| 1828 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | "C:\Program Files (x86)\IObit\Driver Booster\12.5.0\AutoUpdate.exe" /install | C:\Program Files (x86)\IObit\Driver Booster\12.5.0\AutoUpdate.exe | driver_booster_setup.tmp | ||||||||||||
User: admin Company: IObit Integrity Level: HIGH Description: Driver Booster Updater Exit code: 0 Version: 12.0.0.458 Modules
| |||||||||||||||
| 3720 | "C:\Program Files (x86)\IObit\Driver Booster\12.5.0\RttHlp.exe" /winstdate | C:\Program Files (x86)\IObit\Driver Booster\12.5.0\RttHlp.exe | — | SetupHlp.exe | |||||||||||
User: admin Company: IObit Integrity Level: HIGH Description: IObit RttHlp Exit code: 0 Version: 12.0.0.3 Modules
| |||||||||||||||
| 3740 | "C:\Program Files (x86)\IObit\Driver Booster\12.5.0\HWiNFO\HWiNFO.exe" /brandname | C:\Program Files (x86)\IObit\Driver Booster\12.5.0\HWiNFO\HWiNFO.exe | driver_booster_setup.tmp | ||||||||||||
User: admin Company: IObit Integrity Level: HIGH Description: Hardware Information Exit code: 0 Version: 12.0.0.21 Modules
| |||||||||||||||
| 3756 | "C:\Program Files (x86)\IObit\Driver Booster\12.5.0\TaskbarPin\ICONPIN64.exe" pin "C:\Program Files (x86)\IObit\Driver Booster\12.5.0\DriverBooster.exe" | C:\Program Files (x86)\IObit\Driver Booster\12.5.0\TaskbarPin\ICONPIN64.exe | driver_booster_setup.tmp | ||||||||||||
User: admin Company: IObit Integrity Level: HIGH Description: Icon Pin Exit code: 0 Version: 1.0.0.22 Modules
| |||||||||||||||
| 4512 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\7ztest.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4520 | "C:\Users\admin\Desktop\driver_booster_setup.exe" /sp- /verysilent /Installer /norestart /DIR="C:\Program Files (x86)\IObit\Driver Booster" /Installer-DeskIcon /Installer-TaskIcon /runupt | C:\Users\admin\Desktop\driver_booster_setup.exe | setup.exe | ||||||||||||
User: admin Company: IObit Integrity Level: HIGH Description: Driver Booster 12 Setup Exit code: 0 Version: 12.5.0.597 Modules
| |||||||||||||||
| 4772 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4984 | "C:\Program Files (x86)\IObit\Driver Booster\12.5.0\rma.exe" /run /auto | C:\Program Files (x86)\IObit\Driver Booster\12.5.0\rma.exe | — | AutoUpdate.exe | |||||||||||
User: admin Company: IObit Integrity Level: HIGH Description: Driver Booster rma Exit code: 0 Version: 12.0.0.12 Modules
| |||||||||||||||
Total events
8 994
Read events
8 925
Write events
61
Delete events
8
Modification events
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:000000000005033E |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000001C0022 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000040346 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000040346 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:000000000005033E |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000001C0022 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000060340 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000702FC |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000702FC |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010010000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000001600000000000000630065006E00740065007200610063006100640065006D00690063002E007200740066003E002000200000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000001C000000000000006100630063006F0075006E00740069006E0067006100730073006500730073006D0065006E0074002E0070006E0067003E002000200000001000000000000000630061006C006C0068006100690072002E007200740066003E00200020000000120000000000000068006F00750072006300680075007200630068002E0070006E0067003E0020002000000018000000000000006D006500740068006F00640070006100720074006900630075006C00610072002E007200740066003E002000200000001500000000000000700068006F0074006F0061007000700072006F006100630068002E006A00700067003E002000200000001400000000000000720065007400750072006E00730074006F007000690063002E006A00700067003E002000200000001C000000000000006400720069007600650072005F0062006F006F0073007400650072005F00730065007400750070002E006500780065003E002000200000001900000000000000440072006900760065007200200042006F006F0073007400650072002000310032002E006C006E006B003E0020007C0000000100000000000000020001000000000000000000010000000000000002000100000000000000000011000000060000000100000010000000000000000000000000000000000000000040000040400F000000803F0000004008000000803F000040400900000000000000404003000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D00000000000000803F01000000000000000040020000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000000040000000400E00 | |||
Executable files
171
Suspicious files
35
Text files
287
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7116 | driver_booster_setup.exe | C:\Users\admin\AppData\Local\Temp\is-2MA2J.tmp\driver_booster_setup.tmp | executable | |
MD5:048F89F1BE0CE17F10350B121C08B6BD | SHA256:8DFC033FF5A1EBAC9282F15F14AB048B73FB058FEC927A1F5D188A359315C6EB | |||
| 6788 | driver_booster_setup.tmp | C:\Users\admin\AppData\Local\Temp\is-APN3N.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 4772 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 6788 | driver_booster_setup.tmp | C:\Users\admin\AppData\Local\Temp\is-APN3N.tmp-dbinst\EULA.rtf | text | |
MD5:B0381F0BA7EAD83EA3BD882C1DE4CD48 | SHA256:44BC9472169403484A0D384F1CA81989EF7E4B07441758E8A0110078933CBCB5 | |||
| 6788 | driver_booster_setup.tmp | C:\Users\admin\AppData\Local\Temp\is-APN3N.tmp\EULA.rtf | text | |
MD5:B0381F0BA7EAD83EA3BD882C1DE4CD48 | SHA256:44BC9472169403484A0D384F1CA81989EF7E4B07441758E8A0110078933CBCB5 | |||
| 6788 | driver_booster_setup.tmp | C:\Users\admin\AppData\Local\Temp\is-APN3N.tmp\RdZone.dll | executable | |
MD5:F8A1EF0E765FDD04668C96AEB9E27EF3 | SHA256:EAC93CA567A74199DACB8063907360FEAD16440278F224B5A42645DBF7D3369E | |||
| 6788 | driver_booster_setup.tmp | C:\Users\admin\AppData\Local\Temp\is-APN3N.tmp\Inno_English.lng | text | |
MD5:4014E584F7EB5936A6D2B8B75ADE700F | SHA256:5ACF921D2B7D33D5FC9AB02569BE5F46B5F3CF8656BF1C245F2F61F55529BB3B | |||
| 1324 | driver_booster_setup.exe | C:\Users\admin\AppData\Local\Temp\is-UMJCN.tmp\driver_booster_setup.tmp | executable | |
MD5:048F89F1BE0CE17F10350B121C08B6BD | SHA256:8DFC033FF5A1EBAC9282F15F14AB048B73FB058FEC927A1F5D188A359315C6EB | |||
| 6788 | driver_booster_setup.tmp | C:\Users\admin\AppData\Local\Temp\is-APN3N.tmp\DriverBooster.exe | executable | |
MD5:400459D59532AC18DAFB1B97B188C07A | SHA256:F2C8E4C4DA8B7ECFE12EF1480A64A059EA1373C62CB2F5E3A1D3C6B8178F5184 | |||
| 6788 | driver_booster_setup.tmp | C:\Users\admin\AppData\Local\Temp\is-APN3N.tmp\libcrypto-1_1.dll | executable | |
MD5:902385503375A1C52787E2C88895E030 | SHA256:078D662AF771A3B93C44415447294DB364E22710CEDC274B685EC639783AC928 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
53
DNS requests
10
Threats
34
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.57:443 | https://update.iobit.com/dl/img/inst/img_screenshot_s_isr.png | unknown | image | 24.5 Kb | whitelisted |
— | — | GET | 200 | 23.48.23.46:443 | https://update.iobit.com/dl/img/inst/logo_s_isr.png | unknown | image | 1.19 Kb | whitelisted |
— | — | GET | 200 | 23.48.23.49:443 | https://update.iobit.com/dl/img/inst/logo_isr.png | unknown | image | 2.56 Kb | whitelisted |
1268 | svchost.exe | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 206 | 23.48.23.49:443 | https://update.iobit.com/infofiles/db/rmd/install_cfg_n.zlb | unknown | binary | 148 Kb | whitelisted |
— | — | GET | 200 | 23.48.23.51:443 | https://update.iobit.com/infofiles/db/rmd/install_cfg_n.zlb | unknown | binary | 595 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.32.238.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.32.238.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.32.238.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
update.iobit.com |
| whitelisted |
stats.iobit.com |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
— | — | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
Process | Message |
|---|---|
setup.exe | time1 |
setup.exe | time3 |
setup.exe | doFinshedEvent_Freeware 0 |
setup.exe | chk_os_ver 110;100;63;62;61 |
setup.exe | CheckSameVerList |
setup.exe | chk_arch |
setup.exe | Chk_ver_min |
setup.exe | chk_lcid |
setup.exe | Chk_ver_max |
setup.exe | CheckLicense |