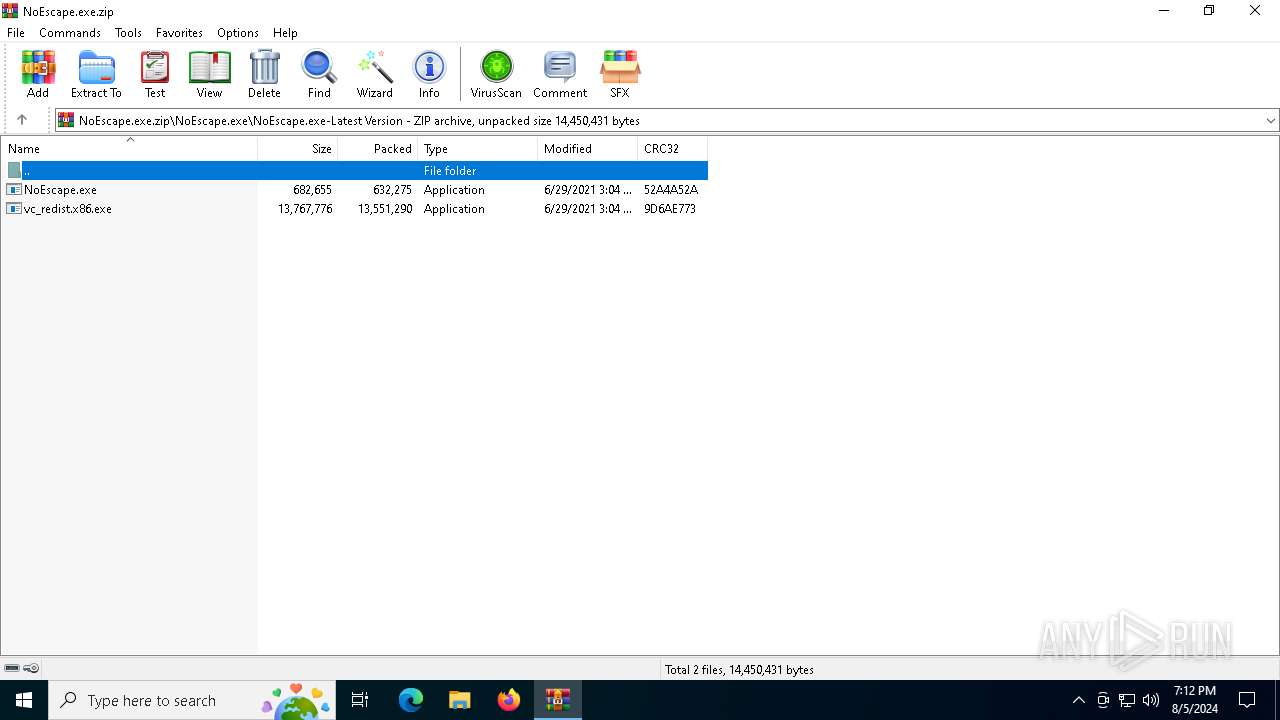
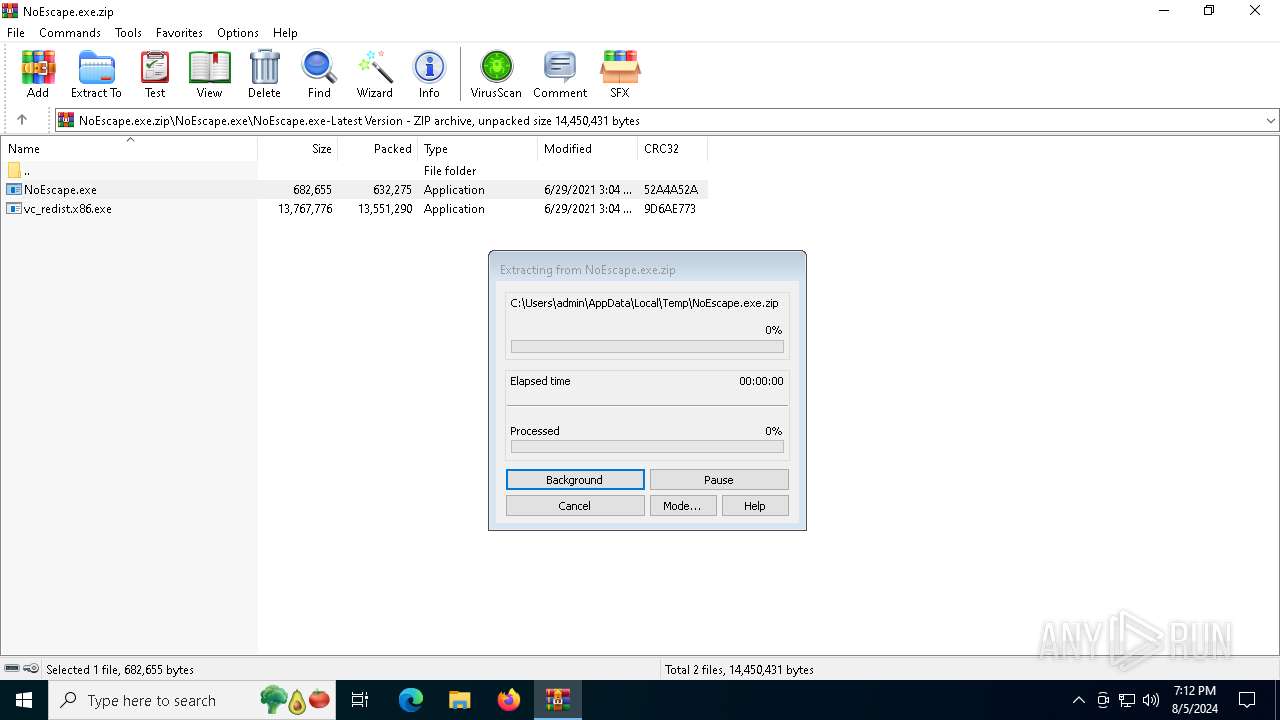
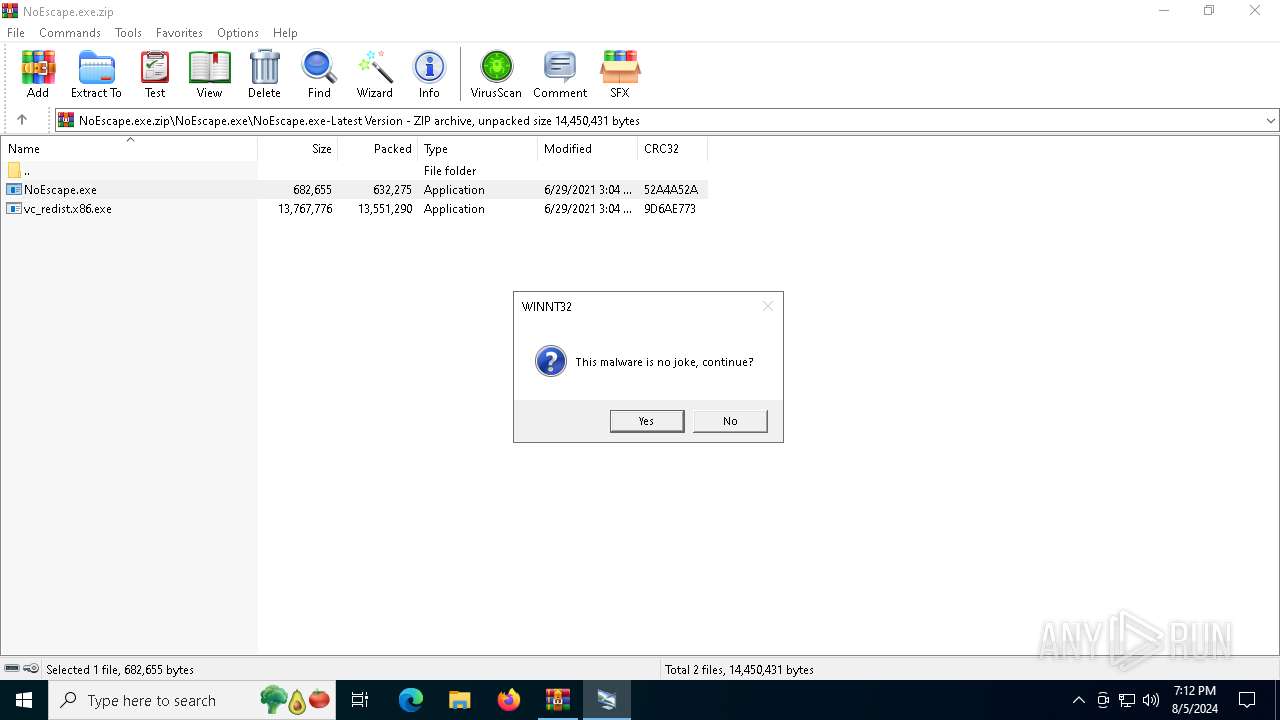
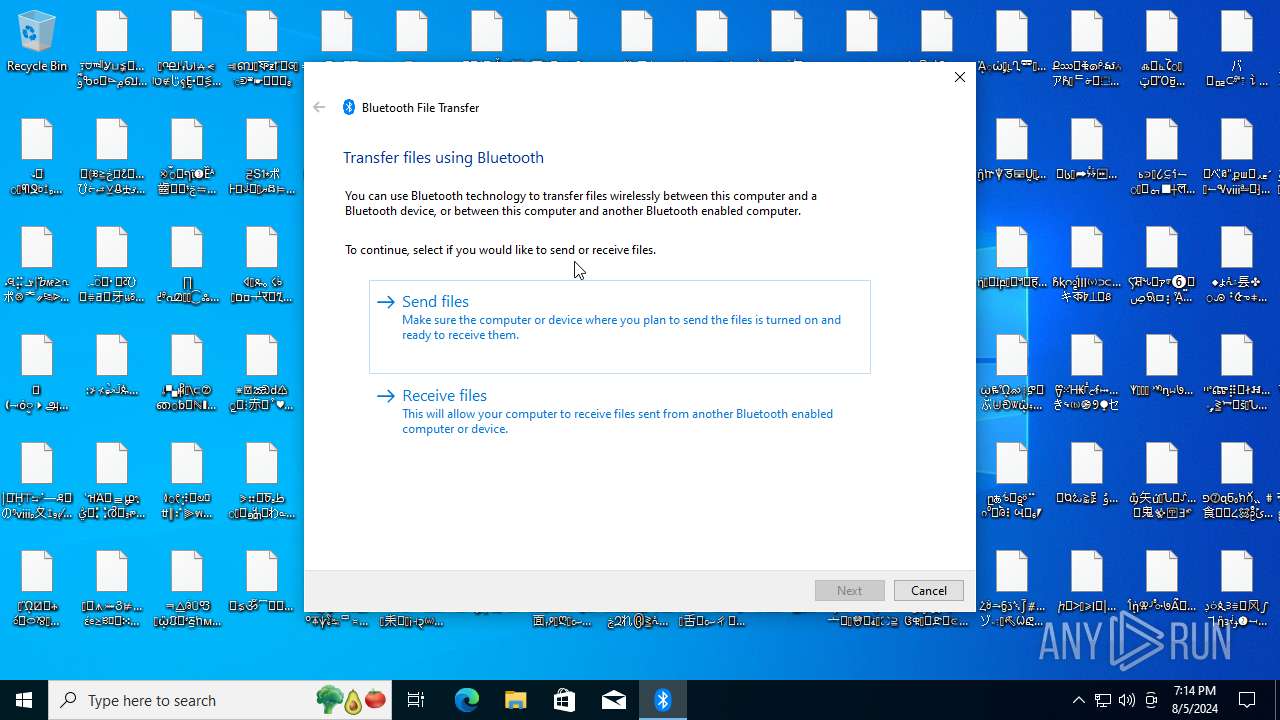
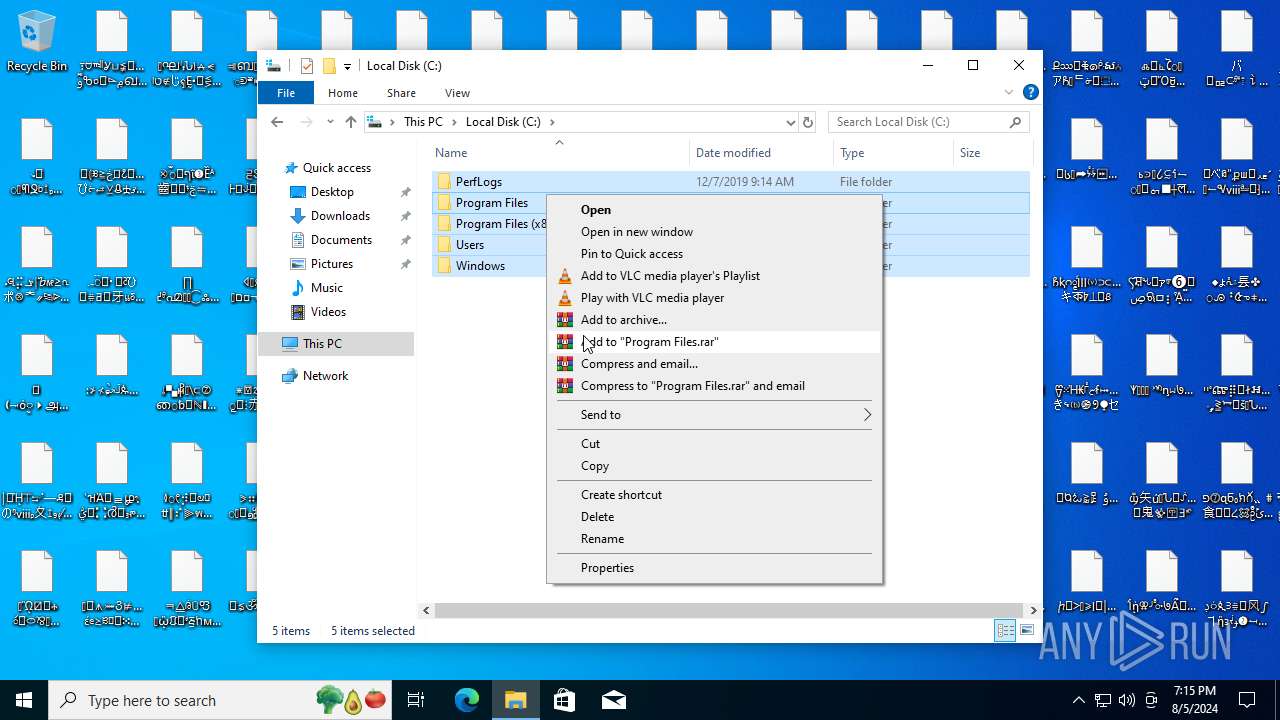
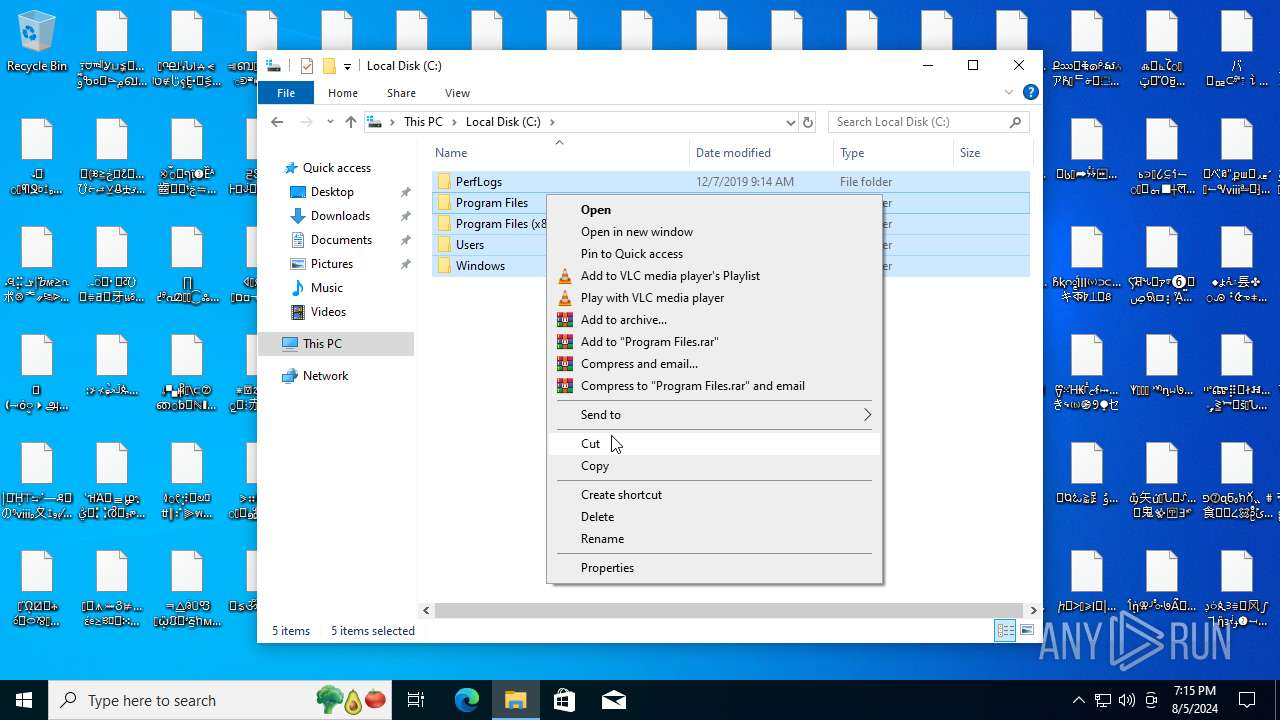
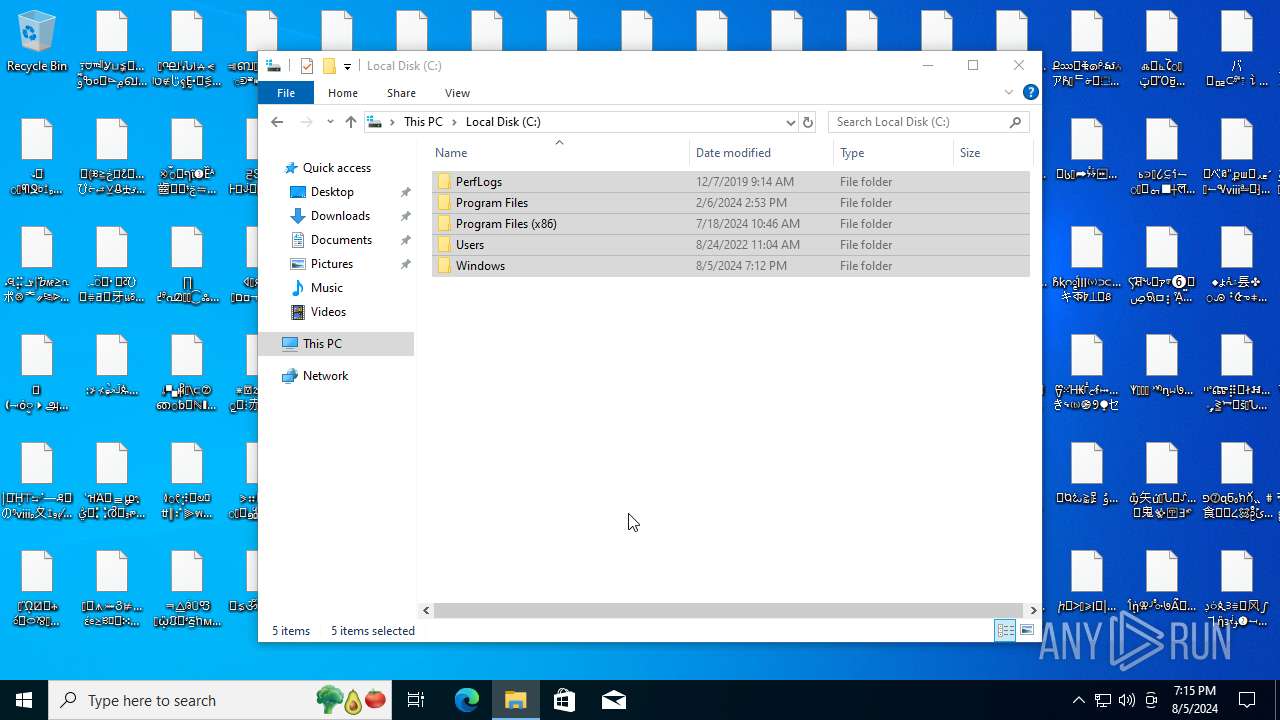
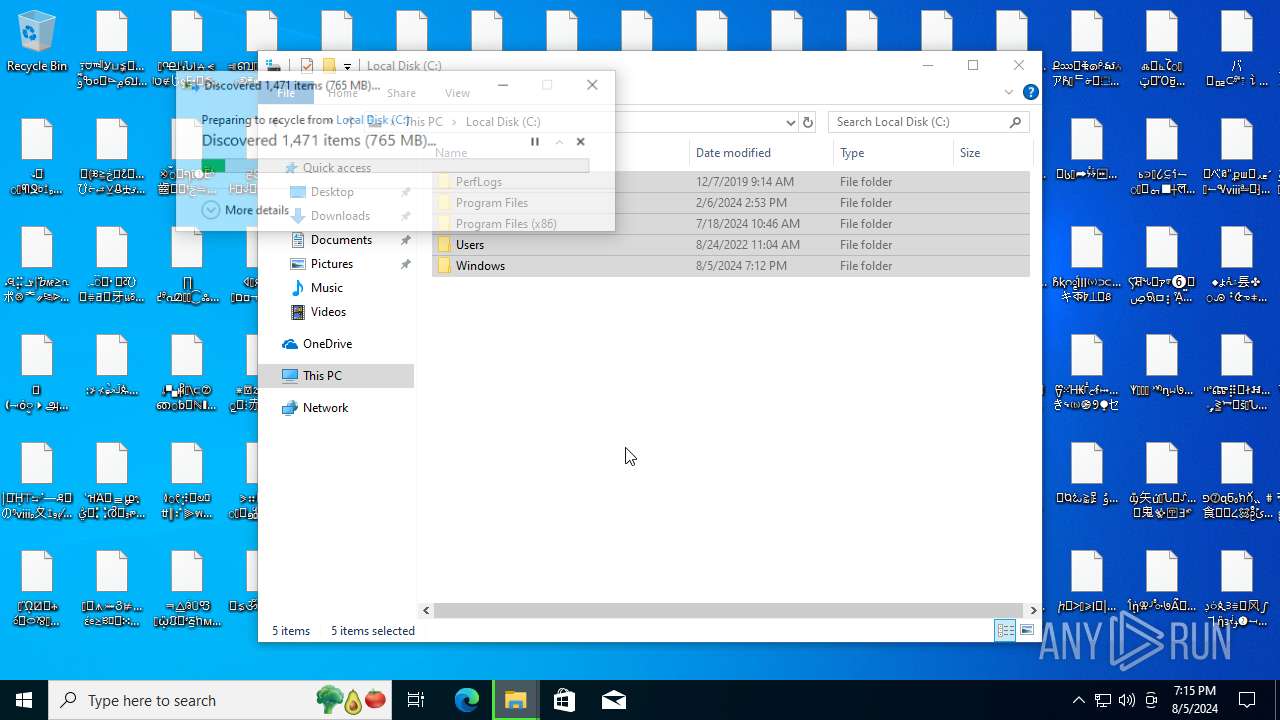
| File name: | NoEscape.exe.zip |
| Full analysis: | https://app.any.run/tasks/96f715de-849f-4ccf-a7c1-8b728f09e9c0 |
| Verdict: | Malicious activity |
| Analysis date: | August 05, 2024, 19:12:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 660708319A500F1865FA9D2FADFA712D |
| SHA1: | B2AE3AEF17095AB26410E0F1792A379A4A2966F8 |
| SHA256: | 542C2E1064BE8CD8393602F63B793E9D34EB81B1090A3C80623777F17FA25C6C |
| SSDEEP: | 393216:BATeK1bYlJbM9tAlAkRCnG7H+KlzMNCPm5lvvayDPk15DBJ:BoX16blXonYeKdKCPGayDPiJ |
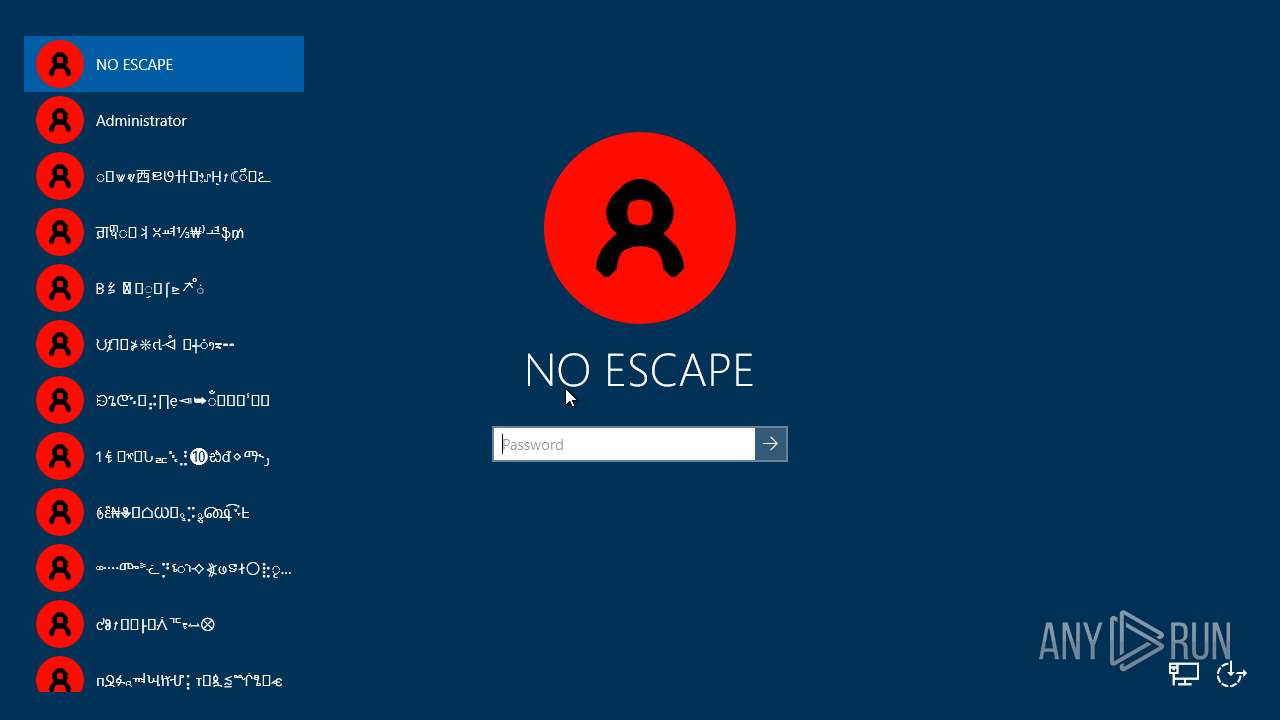
MALICIOUS
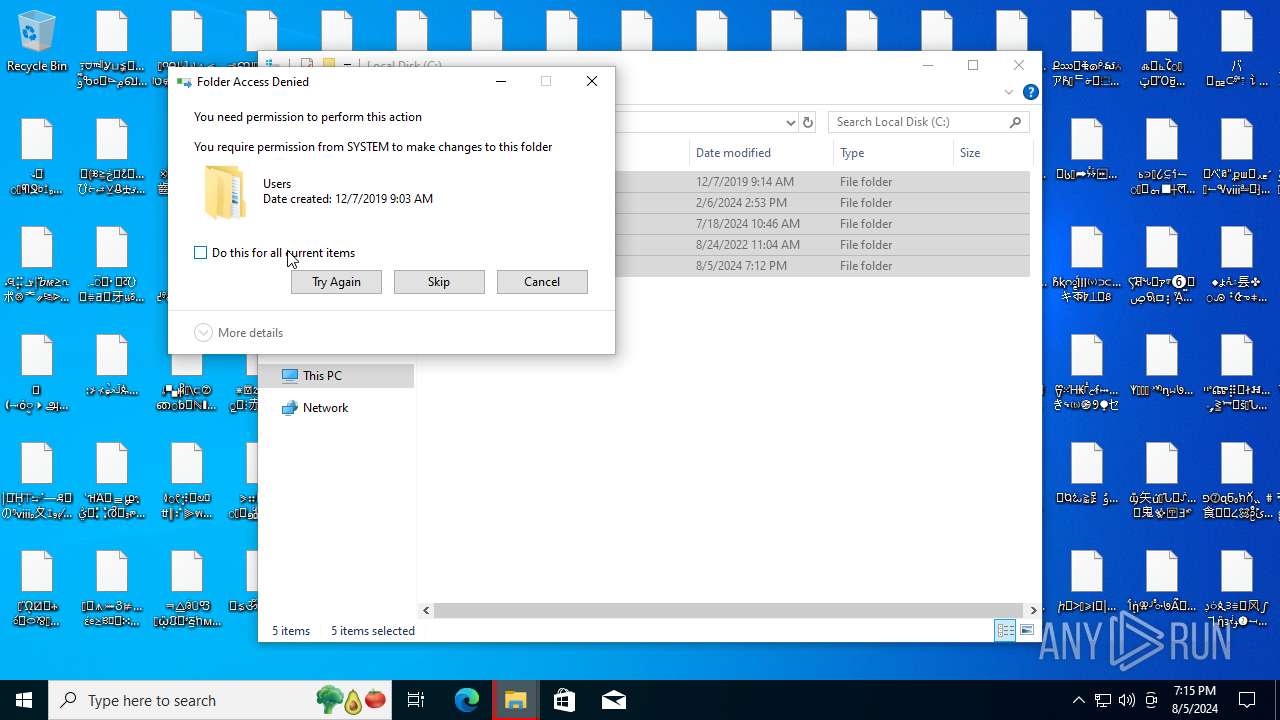
Drops the executable file immediately after the start
- vc_redist.x86.exe (PID: 6672)
- WinRAR.exe (PID: 6400)
- NoEscape.exe (PID: 6240)
Disables the Shutdown in the Start menu
- NoEscape.exe (PID: 6240)
UAC/LUA settings modification
- NoEscape.exe (PID: 6240)
Changes the login/logoff helper path in the registry
- NoEscape.exe (PID: 6240)
SUSPICIOUS
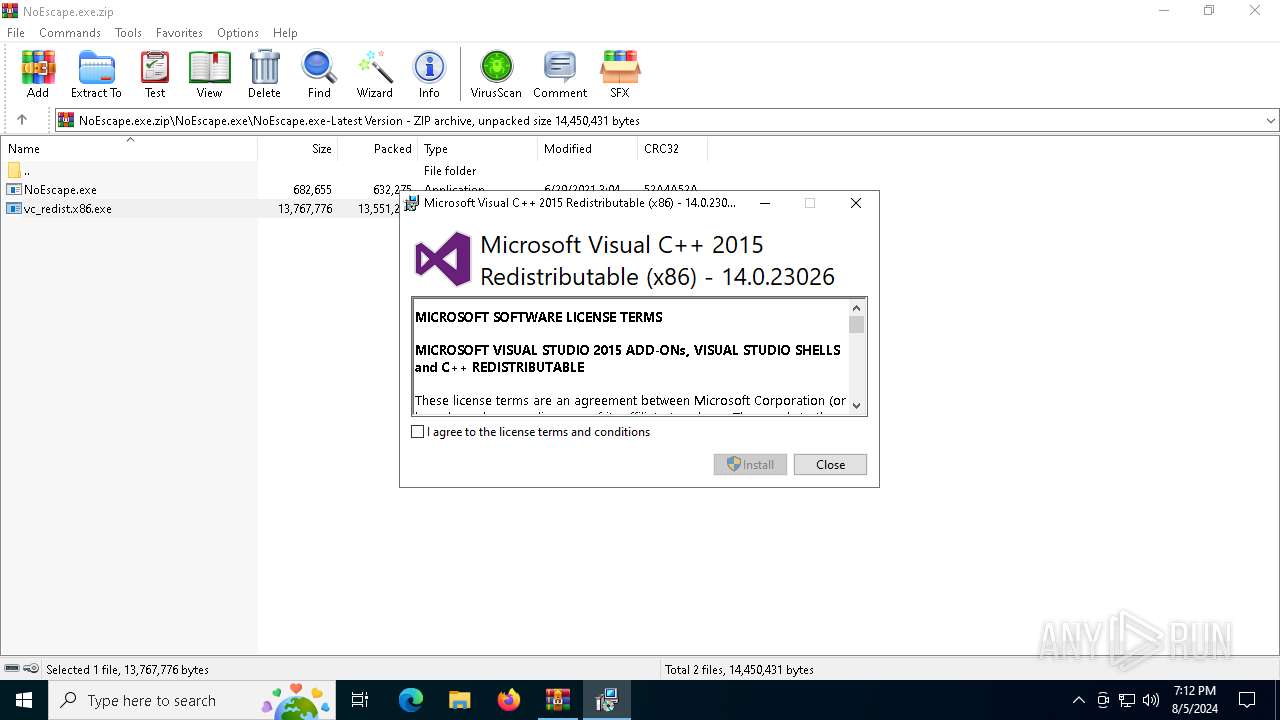
Starts a Microsoft application from unusual location
- vc_redist.x86.exe (PID: 6672)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6400)
- vc_redist.x86.exe (PID: 6672)
Searches for installed software
- vc_redist.x86.exe (PID: 6672)
Executable content was dropped or overwritten
- vc_redist.x86.exe (PID: 6672)
- NoEscape.exe (PID: 6240)
Application launched itself
- NoEscape.exe (PID: 6636)
Reads security settings of Internet Explorer
- NoEscape.exe (PID: 6636)
- WinRAR.exe (PID: 6400)
- ShellExperienceHost.exe (PID: 6188)
Reads the date of Windows installation
- NoEscape.exe (PID: 6636)
INFO
Checks supported languages
- vc_redist.x86.exe (PID: 6672)
- NoEscape.exe (PID: 6240)
- NoEscape.exe (PID: 6636)
- ShellExperienceHost.exe (PID: 6188)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6400)
Reads the computer name
- vc_redist.x86.exe (PID: 6672)
- NoEscape.exe (PID: 6636)
- NoEscape.exe (PID: 6240)
- ShellExperienceHost.exe (PID: 6188)
Create files in a temporary directory
- vc_redist.x86.exe (PID: 6672)
Process checks computer location settings
- NoEscape.exe (PID: 6636)
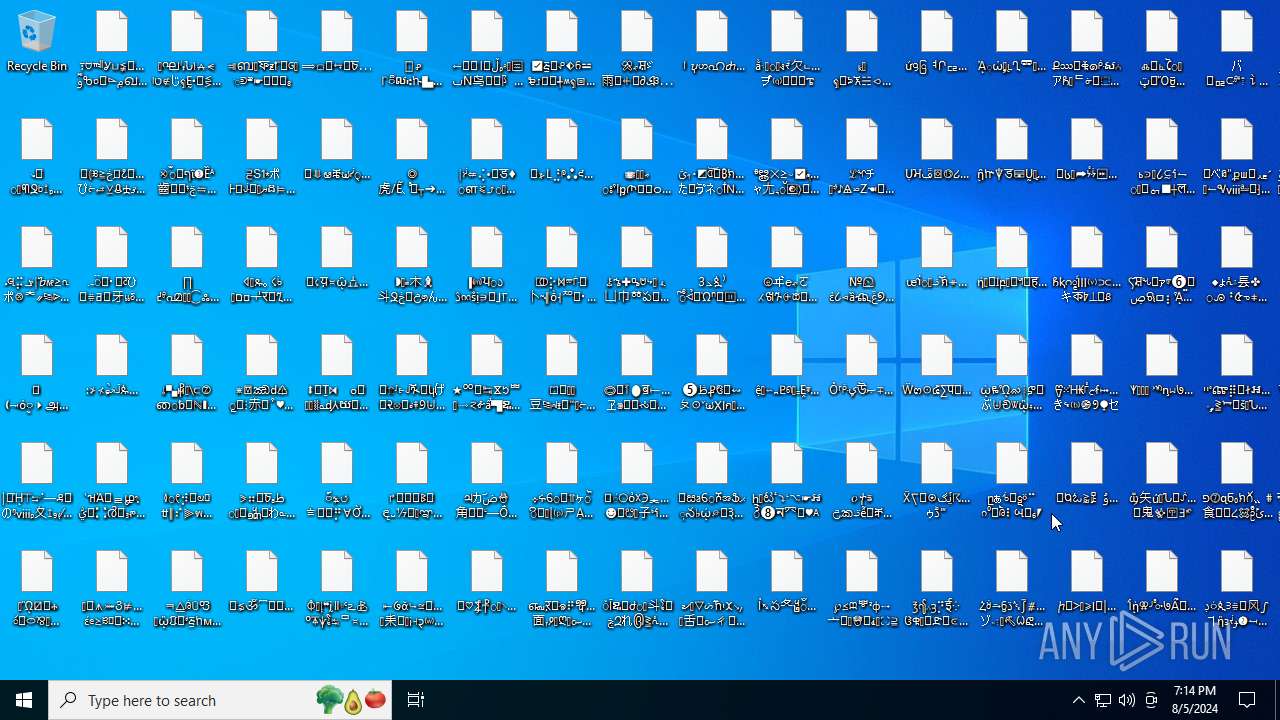
Creates files in the program directory
- NoEscape.exe (PID: 6240)
Creates files or folders in the user directory
- NoEscape.exe (PID: 6240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2021:06:29 17:08:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | NoEscape.exe/ |
Total processes
135
Monitored processes
5
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6188 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
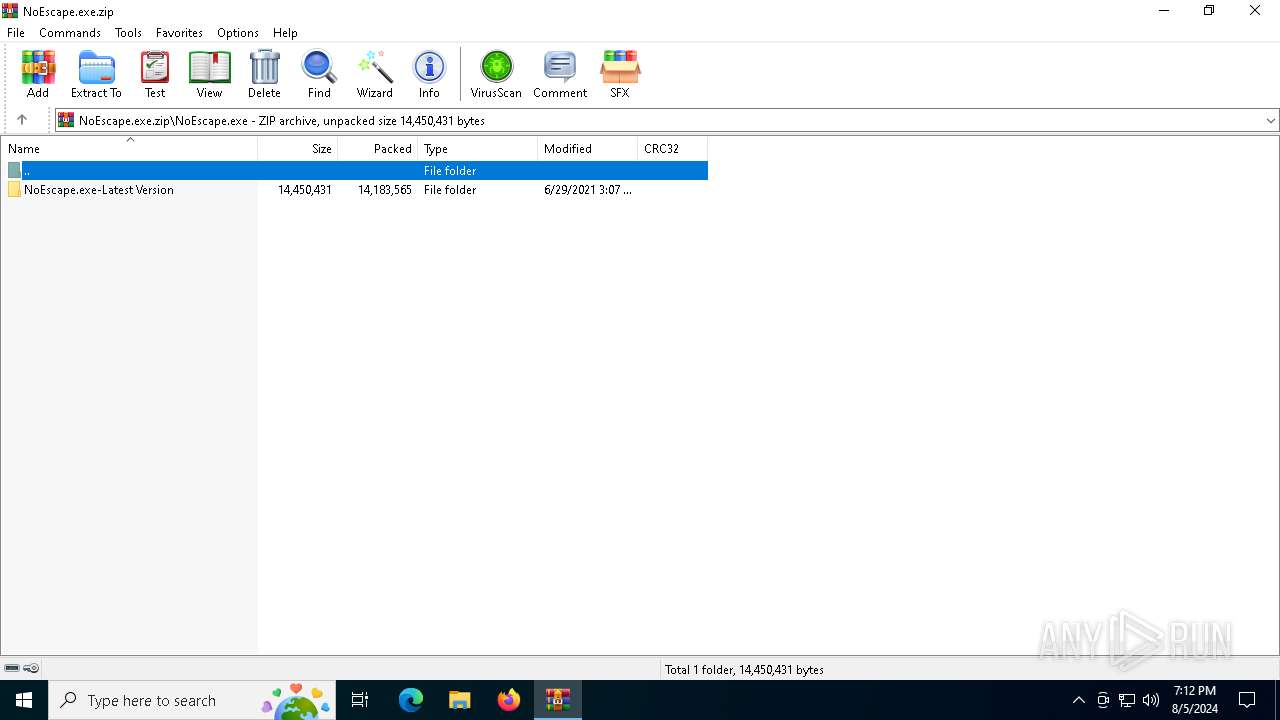
| 6240 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6400.46633\NoEscape.exe\NoEscape.exe-Latest Version\NoEscape.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6400.46633\NoEscape.exe\NoEscape.exe-Latest Version\NoEscape.exe | NoEscape.exe | ||||||||||||
User: admin Company: Endermanch Integrity Level: HIGH Description: Windows Customization Tool Exit code: 0 Version: 6.6.6.6 Modules
| |||||||||||||||
| 6400 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\NoEscape.exe.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1073807364 Version: 5.91.0 Modules
| |||||||||||||||
| 6636 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6400.46633\NoEscape.exe\NoEscape.exe-Latest Version\NoEscape.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6400.46633\NoEscape.exe\NoEscape.exe-Latest Version\NoEscape.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Endermanch Integrity Level: MEDIUM Description: Windows Customization Tool Exit code: 0 Version: 6.6.6.6 Modules
| |||||||||||||||
| 6672 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6400.45384\NoEscape.exe\NoEscape.exe-Latest Version\vc_redist.x86.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6400.45384\NoEscape.exe\NoEscape.exe-Latest Version\vc_redist.x86.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Visual C++ 2015 Redistributable (x86) - 14.0.23026 Exit code: 1638 Version: 14.0.23026.0 Modules
| |||||||||||||||
Total events
11 587
Read events
11 549
Write events
38
Delete events
0
Modification events
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\NoEscape.exe.zip | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
6
Suspicious files
166
Text files
39
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6672 | vc_redist.x86.exe | C:\Users\admin\AppData\Local\Temp\{74d0e5db-b326-4dae-a6b2-445b9de1836e}\.ba1\1036\license.rtf | text | |
MD5:6F70759DF32F212DBB65464258ECEEAF | SHA256:C7F03DA5D9A7F689B8DCBD507FF0B3FA98DABA55616F902E5E47E9839B753E1F | |||
| 6400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6400.45384\NoEscape.exe\NoEscape.exe-Latest Version\NoEscape.exe | executable | |
MD5:989AE3D195203B323AA2B3ADF04E9833 | SHA256:D30D7676A3B4C91B77D403F81748EBF6B8824749DB5F860E114A8A204BCA5B8F | |||
| 6672 | vc_redist.x86.exe | C:\Users\admin\AppData\Local\Temp\{74d0e5db-b326-4dae-a6b2-445b9de1836e}\.ba1\1042\license.rtf | text | |
MD5:F6E7A2A05EFB4413295C156A179578A3 | SHA256:DCEFD9B37D78F37ED8AAEF70AC2BFCDE441DCFB97469A6AA6AF89C1FFADBF814 | |||
| 6400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6400.45384\NoEscape.exe\NoEscape.exe-Latest Version\vc_redist.x86.exe | executable | |
MD5:1A15E6606BAC9647E7AD3CAA543377CF | SHA256:FDD1E1F0DCAE2D0AA0720895EFF33B927D13076E64464BB7C7E5843B7667CD14 | |||
| 6672 | vc_redist.x86.exe | C:\Users\admin\AppData\Local\Temp\{74d0e5db-b326-4dae-a6b2-445b9de1836e}\.ba1\1040\license.rtf | text | |
MD5:1D07E27F97CE22A58780A04227BE6465 | SHA256:F1214784C57AA3323426AF64D132045970717994EBA500B25283684DC1ADEBAA | |||
| 6672 | vc_redist.x86.exe | C:\Users\admin\AppData\Local\Temp\{74d0e5db-b326-4dae-a6b2-445b9de1836e}\.ba1\1028\license.rtf | text | |
MD5:EFA0E0316DBE1D01B04DB8AE55216E89 | SHA256:D5147EE2BA7826D5B68E0DC10FC2AC95079F89C38264C5648D924DEC9290D085 | |||
| 6672 | vc_redist.x86.exe | C:\Users\admin\AppData\Local\Temp\{74d0e5db-b326-4dae-a6b2-445b9de1836e}\.ba1\1049\license.rtf | text | |
MD5:EFF73C35DB2D6AC9F29D1B633C984A95 | SHA256:F00A2A67106CA3BADB4C233951A262EC0A9BBA3151E1D8DA0362DCADA7928DCD | |||
| 6672 | vc_redist.x86.exe | C:\Users\admin\AppData\Local\Temp\{74d0e5db-b326-4dae-a6b2-445b9de1836e}\.ba1\1041\license.rtf | text | |
MD5:0D9DD57746D5609494B35314FA88FD93 | SHA256:AC0D8E0EAAB1875909A6A6F106A37CD7468F87F71887A44263F5F0178F99C40B | |||
| 6672 | vc_redist.x86.exe | C:\Users\admin\AppData\Local\Temp\{74d0e5db-b326-4dae-a6b2-445b9de1836e}\.ba1\1045\license.rtf | text | |
MD5:A0D88589A339E57E412AB01E763D6A27 | SHA256:898D5CA01A3271D97350D06A6CCDB8803A176BB42BAF7E2C8F76C9037235CA8E | |||
| 6672 | vc_redist.x86.exe | C:\Users\admin\AppData\Local\Temp\{74d0e5db-b326-4dae-a6b2-445b9de1836e}\.ba1\1031\license.rtf | text | |
MD5:B4A1F60A329E18DD44C19F91E19E9A0D | SHA256:C017EDFE3B0D308E20FBF3DE8795FD4451A530475A2D0EE0824E166045EADFB7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
148
DNS requests
91
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5140 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6800 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5140 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6764 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2340 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4560 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5140 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5140 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |