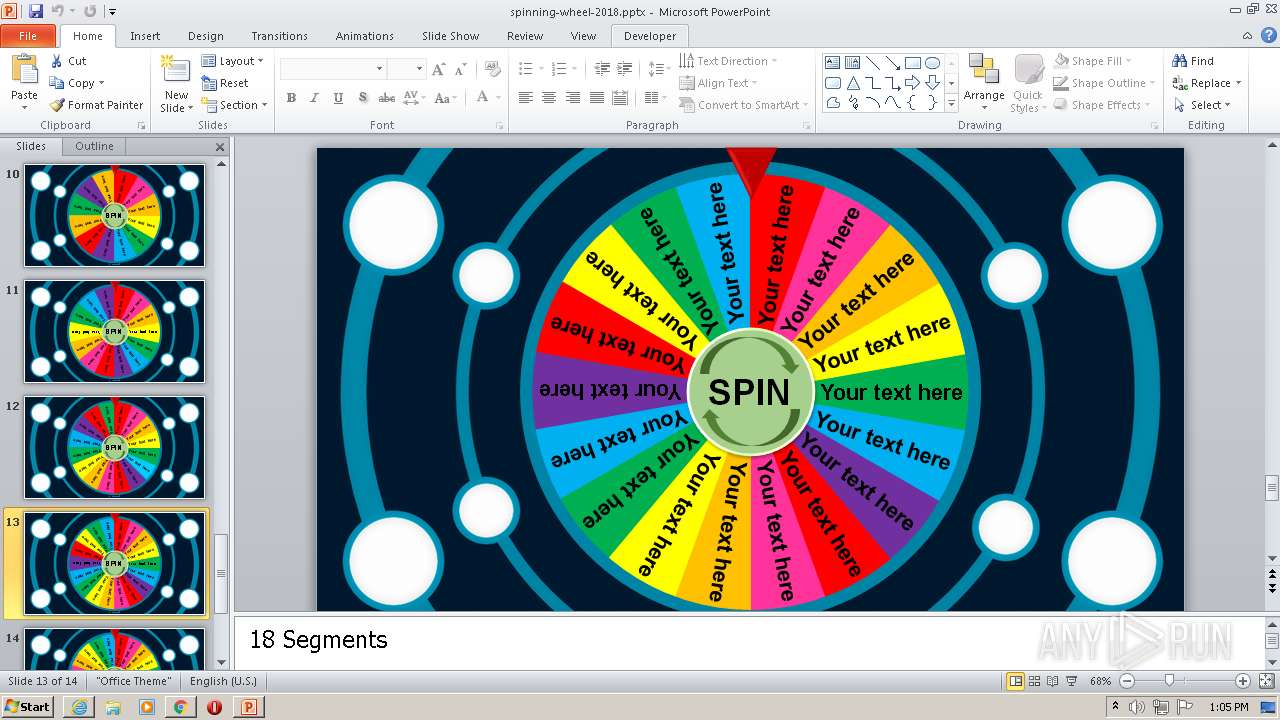
| URL: | https://tekhnologic.wordpress.com/2018/04/30/the-spinning-wheel-2018/ |
| Full analysis: | https://app.any.run/tasks/a017eef8-5aa5-4d67-9541-49c58d6e60f9 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 12:02:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 132203B7938349DDBC9E32FF0D29E5BD |
| SHA1: | E0D7E280032E0AB4DE221102F3B99779566B07E4 |
| SHA256: | 542823650C94C14C0B5A8B02D44DCCD35F0C69E83322BCCDDD496DDF2F275BD5 |
| SSDEEP: | 3:N8IZKCH9R1K2AIS16ApSKn:2I7RA36ESK |
MALICIOUS
Drops executable file immediately after starts
- chrome.exe (PID: 3724)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2816)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2912)
Starts Microsoft Office Application
- chrome.exe (PID: 2912)
- POWERPNT.EXE (PID: 2948)
Application launched itself
- POWERPNT.EXE (PID: 2948)
Executable content was dropped or overwritten
- chrome.exe (PID: 3724)
Drops a file with a compile date too recent
- chrome.exe (PID: 3724)
INFO
Checks supported languages
- iexplore.exe (PID: 2860)
- iexplore.exe (PID: 2816)
- chrome.exe (PID: 2912)
- chrome.exe (PID: 3132)
- chrome.exe (PID: 668)
- chrome.exe (PID: 1860)
- chrome.exe (PID: 2196)
- chrome.exe (PID: 2572)
- chrome.exe (PID: 604)
- chrome.exe (PID: 3932)
- chrome.exe (PID: 4072)
- chrome.exe (PID: 3868)
- chrome.exe (PID: 3268)
- chrome.exe (PID: 2040)
- chrome.exe (PID: 3264)
- chrome.exe (PID: 3492)
- chrome.exe (PID: 3580)
- chrome.exe (PID: 2824)
- chrome.exe (PID: 1020)
- chrome.exe (PID: 2184)
- chrome.exe (PID: 2660)
- chrome.exe (PID: 2784)
- chrome.exe (PID: 3968)
- chrome.exe (PID: 1492)
- chrome.exe (PID: 1728)
- chrome.exe (PID: 3364)
- chrome.exe (PID: 3336)
- chrome.exe (PID: 3908)
- chrome.exe (PID: 3376)
- chrome.exe (PID: 2104)
- chrome.exe (PID: 3672)
- chrome.exe (PID: 3236)
- chrome.exe (PID: 1884)
- chrome.exe (PID: 2036)
- chrome.exe (PID: 2180)
- POWERPNT.EXE (PID: 2948)
- POWERPNT.EXE (PID: 3516)
- chrome.exe (PID: 2384)
- chrome.exe (PID: 1332)
- chrome.exe (PID: 3376)
- chrome.exe (PID: 2608)
- chrome.exe (PID: 3724)
- chrome.exe (PID: 3748)
- chrome.exe (PID: 3100)
- chrome.exe (PID: 4016)
- chrome.exe (PID: 2032)
- chrome.exe (PID: 3680)
Reads the computer name
- iexplore.exe (PID: 2860)
- iexplore.exe (PID: 2816)
- chrome.exe (PID: 2912)
- chrome.exe (PID: 1860)
- chrome.exe (PID: 668)
- chrome.exe (PID: 604)
- chrome.exe (PID: 2824)
- chrome.exe (PID: 1728)
- chrome.exe (PID: 3672)
- chrome.exe (PID: 2784)
- POWERPNT.EXE (PID: 2948)
- POWERPNT.EXE (PID: 3516)
- chrome.exe (PID: 2036)
- chrome.exe (PID: 2180)
Changes internet zones settings
- iexplore.exe (PID: 2860)
Application launched itself
- iexplore.exe (PID: 2860)
- chrome.exe (PID: 2912)
Reads settings of System Certificates
- iexplore.exe (PID: 2816)
- iexplore.exe (PID: 2860)
- chrome.exe (PID: 1860)
Manual execution by user
- chrome.exe (PID: 2912)
Checks Windows Trust Settings
- iexplore.exe (PID: 2860)
- iexplore.exe (PID: 2816)
- chrome.exe (PID: 2912)
Reads the hosts file
- chrome.exe (PID: 1860)
- chrome.exe (PID: 2912)
Reads internet explorer settings
- iexplore.exe (PID: 2816)
Creates files in the user directory
- iexplore.exe (PID: 2816)
- iexplore.exe (PID: 2860)
- POWERPNT.EXE (PID: 2948)
Changes settings of System certificates
- iexplore.exe (PID: 2860)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2860)
Reads the date of Windows installation
- chrome.exe (PID: 1728)
Reads Microsoft Office registry keys
- chrome.exe (PID: 2912)
- POWERPNT.EXE (PID: 3516)
- POWERPNT.EXE (PID: 2948)
Searches for installed software
- POWERPNT.EXE (PID: 2948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
87
Monitored processes
47
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 604 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1068,10456120545819468382,16501905273009688446,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2832 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1068,10456120545819468382,16501905273009688446,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1056 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1068,10456120545819468382,16501905273009688446,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3748 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1068,10456120545819468382,16501905273009688446,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1720 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1492 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1068,10456120545819468382,16501905273009688446,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3980 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1728 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1068,10456120545819468382,16501905273009688446,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3608 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1860 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1068,10456120545819468382,16501905273009688446,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1340 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1884 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1068,10456120545819468382,16501905273009688446,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2108 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1068,10456120545819468382,16501905273009688446,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3404 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2036 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1068,10456120545819468382,16501905273009688446,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2740 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
27 522
Read events
27 101
Write events
389
Delete events
32
Modification events
| (PID) Process: | (2860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30968349 | |||
| (PID) Process: | (2860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30968349 | |||
| (PID) Process: | (2860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
245
Text files
321
Unknown types
54
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2912 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-62B99C7C-B60.pma | — | |
MD5:— | SHA256:— | |||
| 2860 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2860 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 2860 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 1860 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\index | binary | |
MD5:— | SHA256:— | |||
| 2860 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 2912 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:7721CDA9F5B73CE8A135471EB53B4E0E | SHA256:DD730C576766A46FFC84E682123248ECE1FF1887EC0ACAB22A5CE93A450F4500 | |||
| 2912 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:00046F773EFDD3C8F8F6D0F87A2B93DC | SHA256:593EDE11D17AF7F016828068BCA2E93CF240417563FB06DC8A579110AEF81731 | |||
| 3132 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
| 1860 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\data_1 | vxd | |
MD5:259E7ED5FB3C6C90533B963DA5B2FC1B | SHA256:35BB2F189C643DCF52ECF037603D104035ECDC490BF059B7736E58EF7D821A09 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
77
TCP/UDP connections
218
DNS requests
94
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2816 | iexplore.exe | GET | — | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEESz3%2FmlG2yGCtBzjzp1dVc%3D | US | — | — | whitelisted |
— | — | HEAD | 302 | 142.250.185.78:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | — | — | whitelisted |
1860 | chrome.exe | GET | 302 | 157.240.9.18:80 | http://graph.facebook.com/v2.2/10204852683303450/picture?type=large&_md5=355ed29caaae8f68b91f5542d2e01cc4 | US | — | — | whitelisted |
2816 | iexplore.exe | GET | — | 142.250.186.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | — | — | whitelisted |
— | — | HEAD | 200 | 173.194.150.220:80 | http://r6---sn-5goeen7r.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3?cms_redirect=yes&mh=VX&mip=196.196.52.6&mm=28&mn=sn-5goeen7r&ms=nvh&mt=1656330983&mv=m&mvi=6&pl=24&rmhost=r3---sn-5goeen7r.gvt1.com&shardbypass=sd&smhost=r1---sn-5goeenez.gvt1.com | US | — | — | whitelisted |
2860 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2816 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
2860 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
1860 | chrome.exe | GET | 302 | 142.250.185.78:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 591 b | whitelisted |
2816 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2816 | iexplore.exe | 192.0.78.12:443 | tekhnologic.wordpress.com | Automattic, Inc | US | malicious |
1860 | chrome.exe | 142.250.185.196:443 | www.google.com | Google Inc. | US | whitelisted |
2860 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1860 | chrome.exe | 142.250.185.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 192.0.78.13:443 | tekhnologic.wordpress.com | Automattic, Inc | US | malicious |
1860 | chrome.exe | 192.0.77.32:443 | s0.wp.com | Automattic, Inc | US | suspicious |
2816 | iexplore.exe | 192.0.77.32:443 | s0.wp.com | Automattic, Inc | US | suspicious |
1860 | chrome.exe | 142.250.186.35:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2816 | iexplore.exe | 172.217.23.110:443 | translate.google.com | Google Inc. | US | whitelisted |
2816 | iexplore.exe | 142.250.179.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
tekhnologic.wordpress.com |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.google.com |
| whitelisted |
www.google.com |
| malicious |