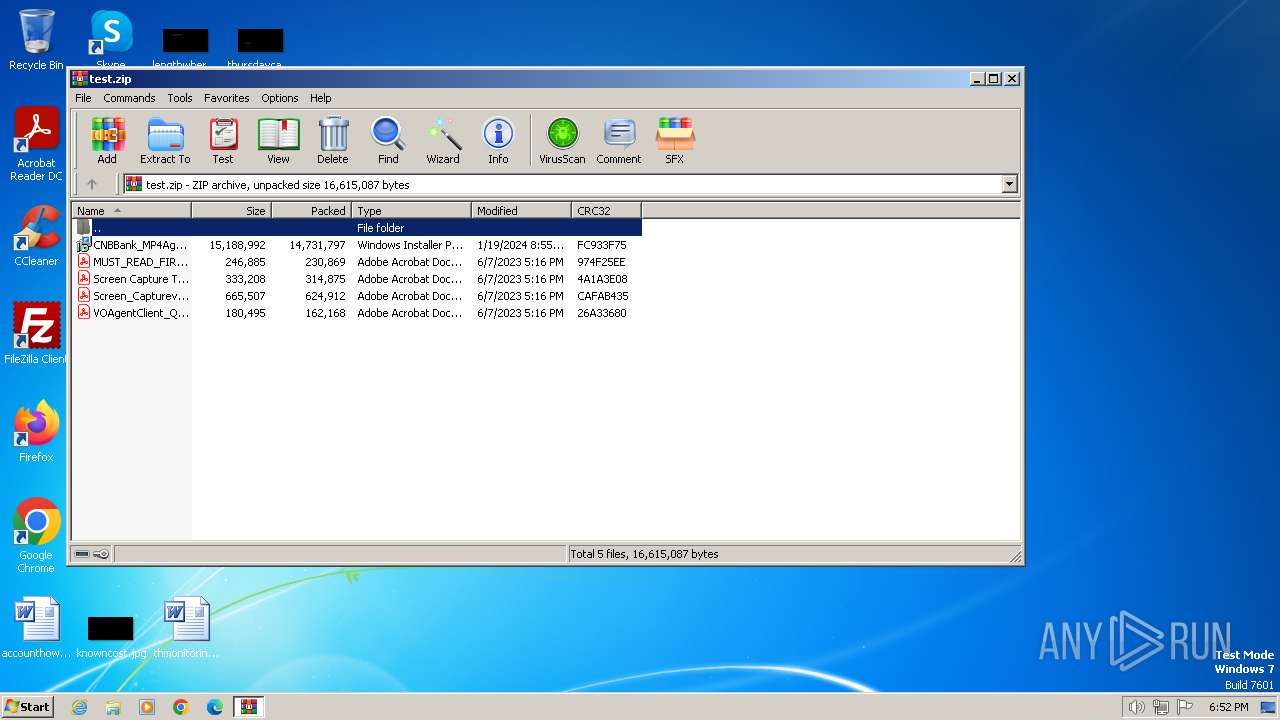
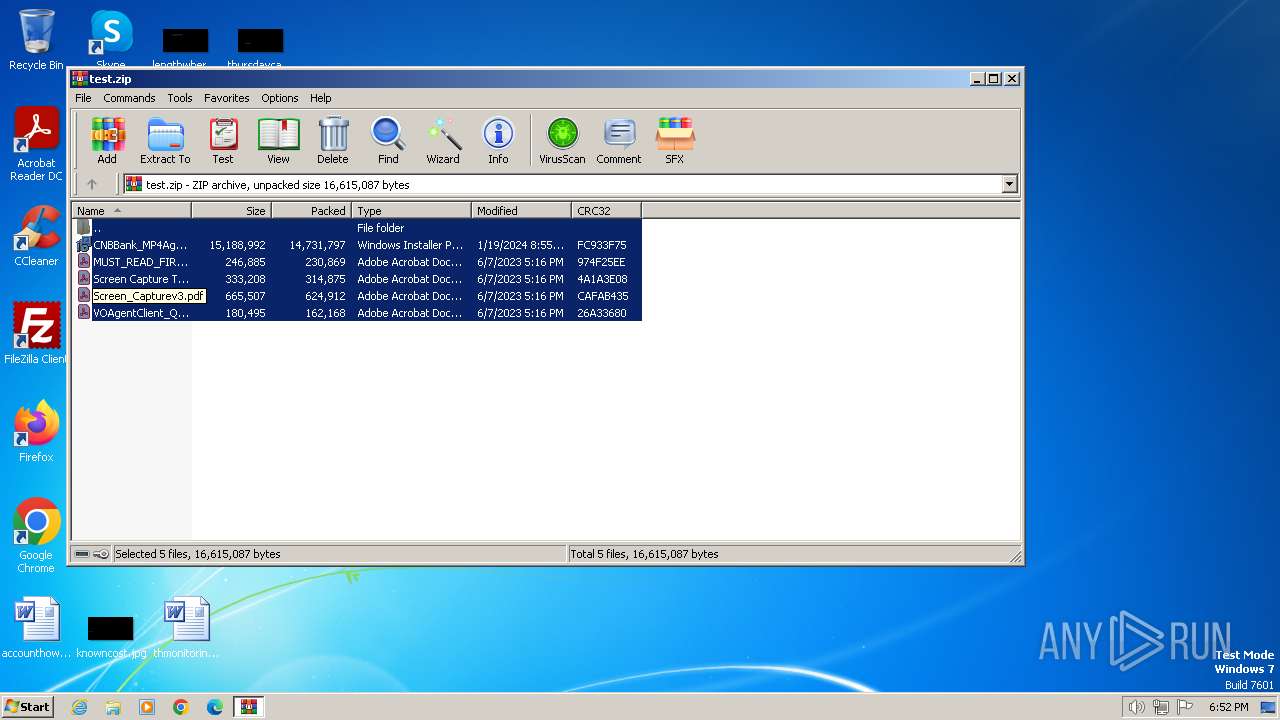
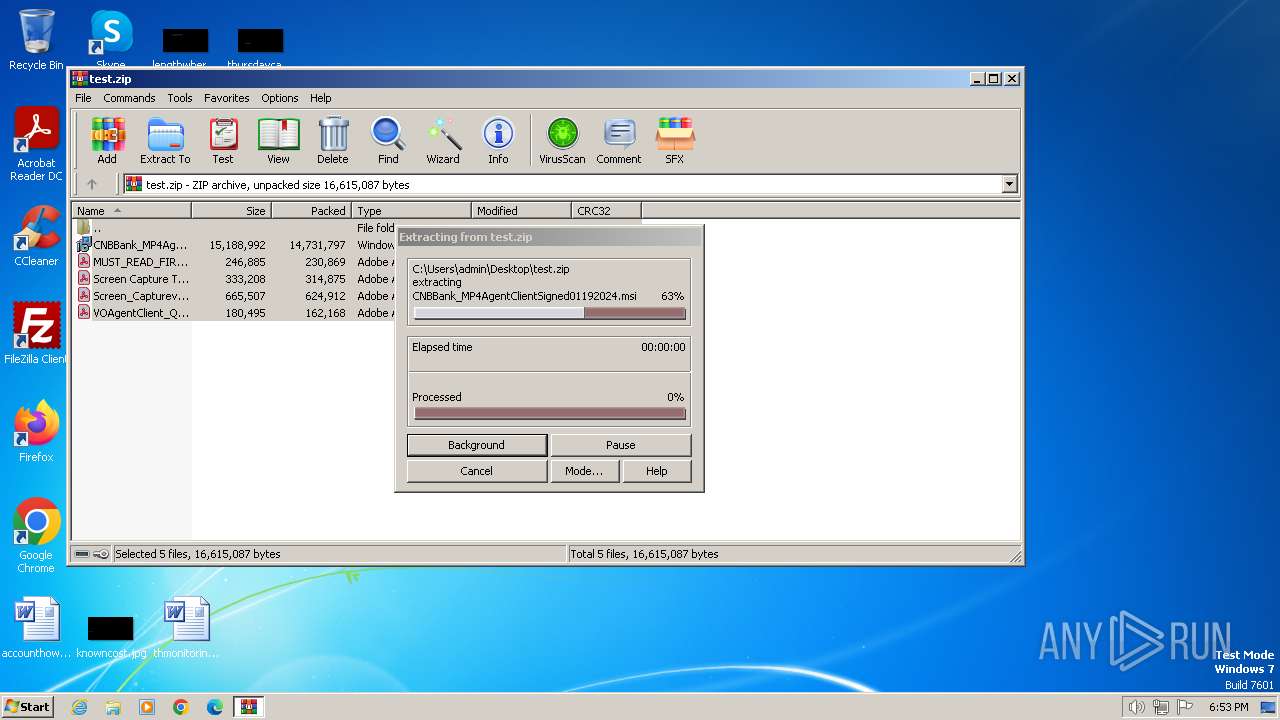
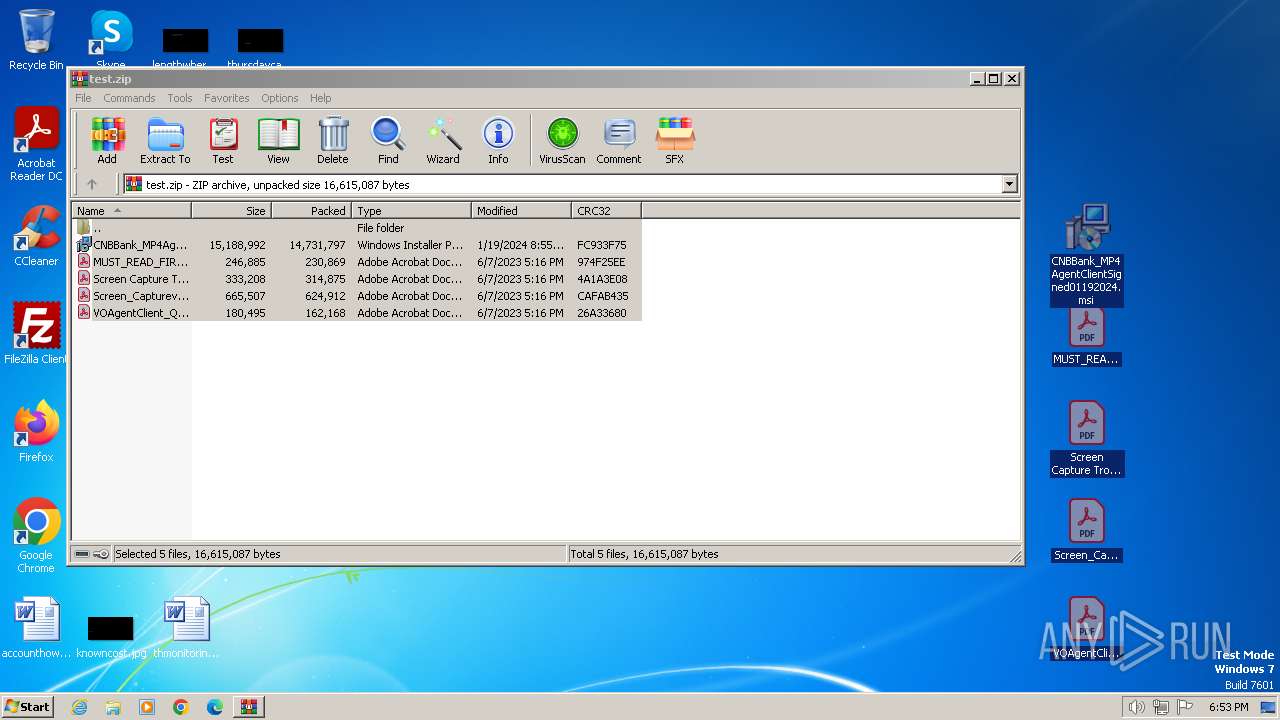
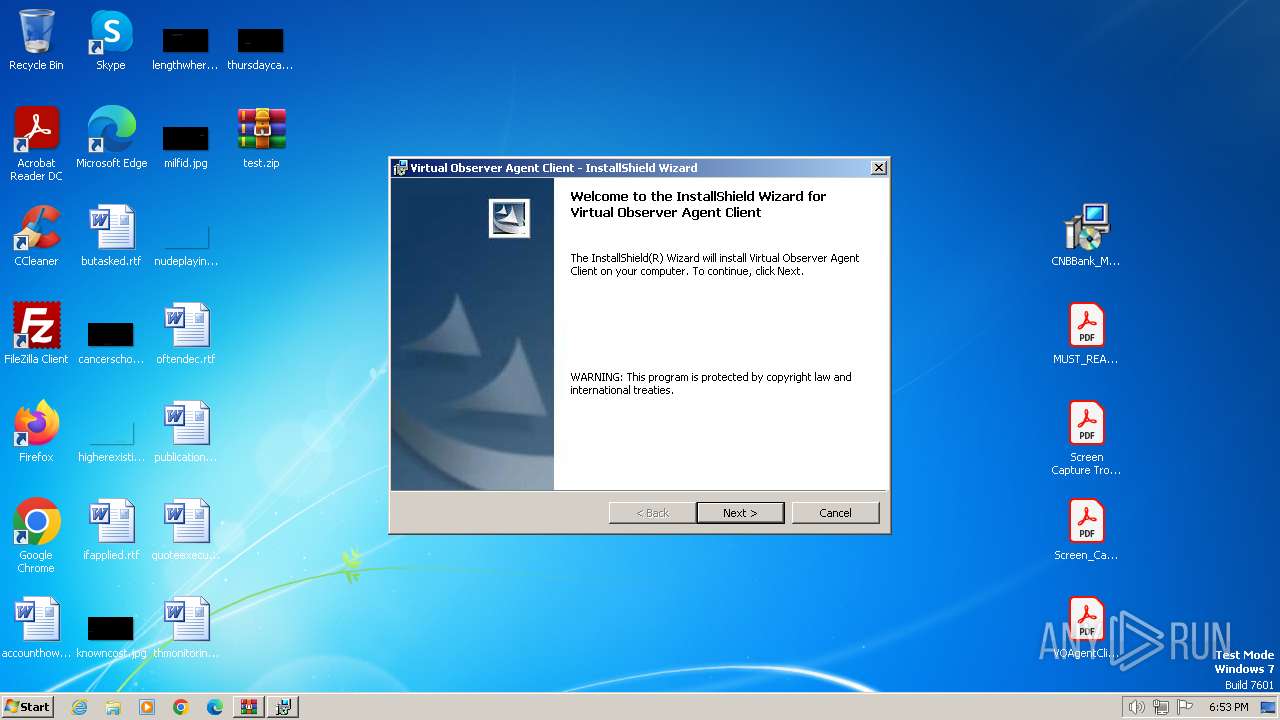
| File name: | test.zip |
| Full analysis: | https://app.any.run/tasks/b37364eb-5803-4e33-8407-b1b5e0ae6536 |
| Verdict: | Malicious activity |
| Analysis date: | February 05, 2024, 18:52:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 72BB414FFC3F6FF971317AE0CC76AAFC |
| SHA1: | B8EE030A047D6AF957531EF88D817BC9661CFB25 |
| SHA256: | 5408E55AB1981D7D8858DDC2D665DC9E3ACEDE96FD3A00BA3839F81A836C4AD2 |
| SSDEEP: | 196608:Im3F+erMRN/9hv2wRGlW/U3ebXuuPNSjvYN2KZ:BF+sI/W+UWEebXuMpN/Z |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1392)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 3608)
- cmd.exe (PID: 3520)
SUSPICIOUS
Starts SC.EXE for service management
- cmd.exe (PID: 3608)
- cmd.exe (PID: 3520)
Executes as Windows Service
- voacli.exe (PID: 2980)
- voacmt.exe (PID: 1220)
- voacmt.exe (PID: 2396)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 2848)
- regsvr32.exe (PID: 3944)
- regsvr32.exe (PID: 1876)
INFO
Manual execution by a user
- msiexec.exe (PID: 324)
- explorer.exe (PID: 2964)
- taskmgr.exe (PID: 3404)
- wmpnscfg.exe (PID: 2620)
- RegisterFiles.exe (PID: 1636)
- voaclm.exe (PID: 3456)
- voaclm.exe (PID: 2616)
- voacmt.exe (PID: 2228)
- ummi.exe (PID: 3828)
- ummi.exe (PID: 2924)
- voaccf.exe (PID: 3320)
- voaccf.exe (PID: 1880)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 324)
Reads the computer name
- voacld.exe (PID: 3756)
- wmpnscfg.exe (PID: 2620)
- voaclm.exe (PID: 3456)
- voaclm.exe (PID: 2616)
- ummi.exe (PID: 2924)
- voaccf.exe (PID: 3320)
- voacmt.exe (PID: 2228)
- voaccf.exe (PID: 1880)
- voacld.exe (PID: 2436)
- voacmt.exe (PID: 2396)
- voacli.exe (PID: 2980)
- voacmt.exe (PID: 1220)
Checks supported languages
- voacld.exe (PID: 3756)
- voacli.exe (PID: 2980)
- wmpnscfg.exe (PID: 2620)
- RegisterFiles.exe (PID: 1636)
- voaclm.exe (PID: 3456)
- voaclm.exe (PID: 2616)
- voacmt.exe (PID: 2228)
- ummi.exe (PID: 2924)
- voaccf.exe (PID: 3320)
- voacld.exe (PID: 2436)
- voacmt.exe (PID: 2396)
- voaccf.exe (PID: 1880)
- voacmt.exe (PID: 1220)
Creates files in the program directory
- cmd.exe (PID: 3608)
- voacli.exe (PID: 2980)
- cmd.exe (PID: 3520)
- voacmt.exe (PID: 1220)
Reads the machine GUID from the registry
- voacld.exe (PID: 3756)
- RegisterFiles.exe (PID: 1636)
- voaclm.exe (PID: 2616)
- voaclm.exe (PID: 3456)
- ummi.exe (PID: 2924)
- voacmt.exe (PID: 2228)
- voacld.exe (PID: 2436)
- voacmt.exe (PID: 2396)
- voaccf.exe (PID: 3320)
- voaccf.exe (PID: 1880)
- voacli.exe (PID: 2980)
- voacmt.exe (PID: 1220)
Create files in a temporary directory
- voacld.exe (PID: 3756)
- RegisterFiles.exe (PID: 1636)
- voaclm.exe (PID: 3456)
- voaclm.exe (PID: 2616)
- ummi.exe (PID: 2924)
- voacmt.exe (PID: 2228)
- voaccf.exe (PID: 3320)
- voacld.exe (PID: 2436)
- voaccf.exe (PID: 1880)
Creates files or folders in the user directory
- voaclm.exe (PID: 3456)
Reads mouse settings
- ummi.exe (PID: 2924)
- voacmt.exe (PID: 2228)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:01:19 08:55:44 |
| ZipCRC: | 0xfc933f75 |
| ZipCompressedSize: | 14731797 |
| ZipUncompressedSize: | 15188992 |
| ZipFileName: | CNBBank_MP4AgentClientSigned01192024.msi |
Total processes
99
Monitored processes
42
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Desktop\CNBBank_MP4AgentClientSigned01192024.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1000 | sc description VOACLI "Virtual Observer Agent Client Login Service" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1220 | "C:\Program Files\CSI\Virtual Observer\VOACMT.EXE" | C:\Program Files\CSI\Virtual Observer\voacmt.exe | — | services.exe | |||||||||||
User: SYSTEM Company: CSI.Net, Inc. Integrity Level: SYSTEM Description: Virtual Observer Agent Client Media Transfer Service Exit code: 0 Version: 3.00.0469 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\test.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1584 | sc create VOACLI binpath= "\"C:\Program Files\CSI\Virtual Observer\VOACLI.EXE\"" displayname= "VO - Agent Client Login Service" start= "auto" type= "own" depend= "lanmanworkstation" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 1073 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1636 | "C:\Program Files\CSI\Virtual Observer\RegisterFiles.exe" | C:\Program Files\CSI\Virtual Observer\RegisterFiles.exe | — | explorer.exe | |||||||||||
User: admin Company: CSI Integrity Level: MEDIUM Description: Register Files Exit code: 0 Version: 4.00.0003 Modules
| |||||||||||||||
| 1812 | sc start VOACMT | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1876 | regsvr32 "C:\Program Files\CSI\Virtual Observer\RichTX32.OCX" /s | C:\Windows\System32\regsvr32.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1880 | "C:\Program Files\CSI\Virtual Observer\voaccf.exe" | C:\Program Files\CSI\Virtual Observer\voaccf.exe | — | explorer.exe | |||||||||||
User: admin Company: CSI.Net, Inc. Integrity Level: MEDIUM Description: Virtual Observer Agent Client Configuration Exit code: 0 Version: 3.00.0106 Modules
| |||||||||||||||
| 2044 | sc description VOACMT "Virtual Observer Agent Client Media Transfer Service" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 013
Read events
5 952
Write events
48
Delete events
13
Modification events
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (324) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
1
Suspicious files
9
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1392.16463\CNBBank_MP4AgentClientSigned01192024.msi | — | |
MD5:— | SHA256:— | |||
| 3456 | voaclm.exe | — | ||
MD5:— | SHA256:— | |||
| 3456 | voaclm.exe | C:\Program Files\CSI\Virtual Observer\192-168-100-217-TraceFile.TXT | text | |
MD5:2D7CF756A0586101ACB2C496B89FF0A0 | SHA256:FC1B7DFC1AB9E101CA2091A470ADEA7CF33C18E97003DE2D64FD008D053A0094 | |||
| 1636 | RegisterFiles.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\CSI\Virtual Observer\RegFilesLOG.TXT | text | |
MD5:11B1EE18FD369689973E4205364344BC | SHA256:EBA92C6258ACFB0D0638D2C523AA091782210B94F0CA4F102B454EA70F2AA077 | |||
| 3456 | voaclm.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\CSI\Virtual Observer\192-168-100-217-Error.LOG | text | |
MD5:AB041A394B04C8A68DF64ACF510D47D0 | SHA256:03577E017137C6A02D25BE772F18B808322E317D493DAC467D79A6841BA13AE6 | |||
| 3456 | voaclm.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\CSI\Virtual Observer\192-168-100-217-VOACLM-TraceFile.TXT | text | |
MD5:A6FDB032DE553BBCA2FF067898C9230A | SHA256:321B04156EB7731341F239BE0D480E3B7F66665F7A2C66D66859E5C0DBFD0A97 | |||
| 2616 | voaclm.exe | C:\Users\admin\AppData\Local\Temp\~DFE24D570469DD7AE7.TMP | binary | |
MD5:CB6A295AC19AF1EBE2F863B76C0624D5 | SHA256:18B23D1B8185D41AFC29209F8DC69AD5B3954EA03A58D3C2767E1B5B7B48D1BF | |||
| 3456 | voaclm.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\CSI\Virtual Observer\RC\VOACLM.TMP | text | |
MD5:21D6FB666429079CF2835A13E10CA767 | SHA256:F51A62A800488C1A2E5956576E9192ED573D9033F2A324118D654BCFF15C094B | |||
| 2228 | voacmt.exe | C:\Users\admin\AppData\Local\Temp\~DFFC1ACE76EBF9A194.TMP | binary | |
MD5:62910CC3F914351E05AC0B4E8F5FB358 | SHA256:B5E0909F56392CAA31F262308D656B43F5BA95DC921434C044A511BB91979CDA | |||
| 2924 | ummi.exe | C:\Users\admin\AppData\Local\Temp\~DFAAFD0110FCB73C4E.TMP | binary | |
MD5:002B547718C6DCD0FAF27D86B2C5586D | SHA256:7DF3F36BF530DDFE4B3275BACD2AABAFB43C56836815EF0F6C4C5B09BA65AADA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |