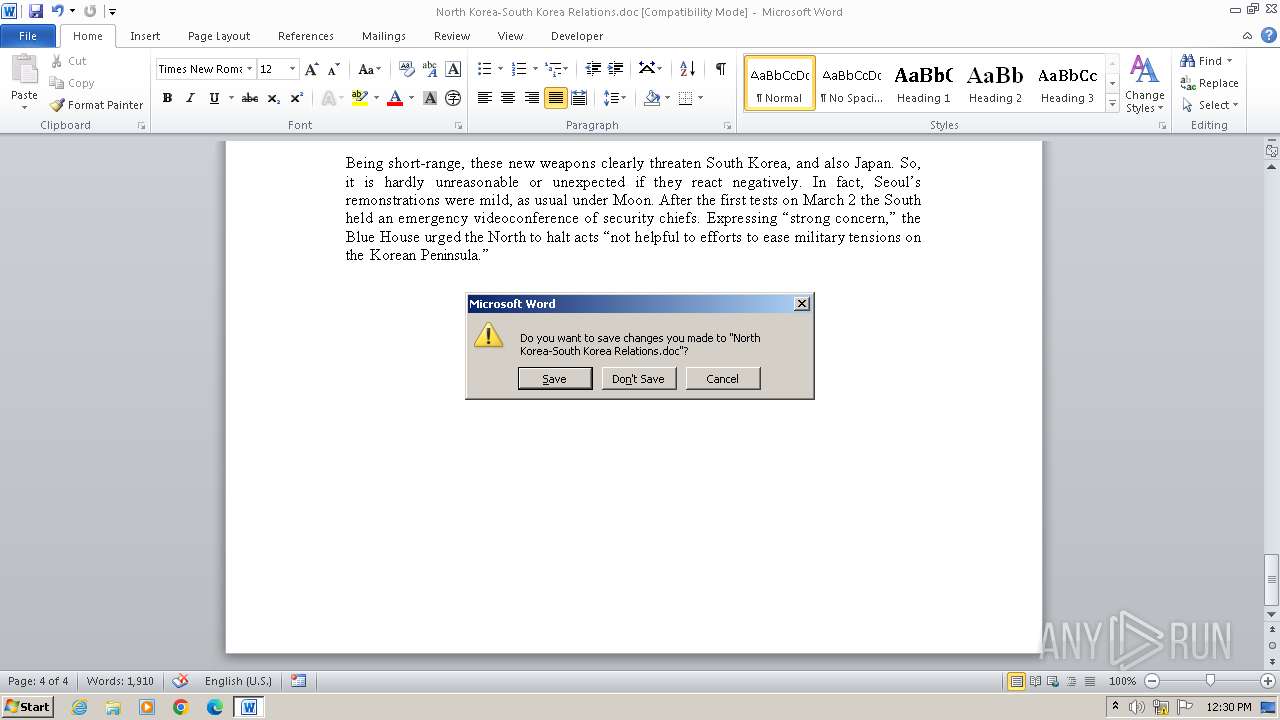
| File name: | North Korea-South Korea Relations.doc |
| Full analysis: | https://app.any.run/tasks/cba79e79-e883-4914-9f06-dbeb04edfa0a |
| Verdict: | Malicious activity |
| Analysis date: | November 28, 2023, 12:30:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 949, Author: Windows User, Template: Normal.dotm, Last Saved By: PILOT, Revision Number: 7, Name of Creating Application: Microsoft Office Word, Total Editing Time: 01:00, Create Time/Date: Mon May 18 03:04:00 2020, Last Saved Time/Date: Tue May 19 02:19:00 2020, Number of Pages: 4, Number of Words: 1857, Number of Characters: 10585, Security: 0 |
| MD5: | 6973FA7AED812980F0539302D64E618F |
| SHA1: | F3D6E76751AC192AE8D95C7B415C944D7752DA66 |
| SHA256: | 53DCFCC9537EC2DF87924938151B39556677D73D48AC59FBD536D7119C2EBDA8 |
| SSDEEP: | 768:TjhgEqRTjUgGeTh+F80/qL1scTipwPGM4GeGraTJ2w0p54OAKhgHGcO:TQTogGsClqZLiWuM4GeGracwKAm3 |
MALICIOUS
Unusual execution from MS Office
- WINWORD.EXE (PID: 2876)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2876)
Microsoft Office executes commands via PowerShell or Cmd
- WINWORD.EXE (PID: 2876)
SUSPICIOUS
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 2876)
INFO
Checks supported languages
- zx.exe (PID: 3320)
The executable file from the user directory is run by the CMD process
- zx.exe (PID: 3320)
Drops the executable file immediately after the start
- WINWORD.EXE (PID: 2876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | Windows User |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | PILOT |
| Software: | Microsoft Office Word |
| CreateDate: | 2020:05:18 02:04:00 |
| ModifyDate: | 2020:05:19 01:19:00 |
| Security: | None |
| Company: | - |
| CharCountWithSpaces: | 12418 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CodePage: | Windows Korean (Unified Hangul Code) |
| Hyperlinks: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 7 |
| TotalEditTime: | 1 minute |
| Words: | 1857 |
| Characters: | 10585 |
| Pages: | 4 |
| Paragraphs: | 24 |
| Lines: | 88 |
Total processes
40
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2496 | cmd /c C:\Users\admin\zx.exe r2P82eU2522n2h62zLP-2Z62oLP82Zu2pUPJ2ZL25L2S2eV252Pj2eu2v2PN2Z62ogP82Zg2yUPF2Zf2pg2S2Zt2yUP822YY | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2876 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\North Korea-South Korea Relations.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3320 | C:\Users\admin\zx.exe r2P82eU2522n2h62zLP-2Z62oLP82Zu2pUPJ2ZL25L2S2eV252Pj2eu2v2PN2Z62ogP82Zg2yUPF2Zf2pg2S2Zt2yUP822YY | C:\Users\admin\zx.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 201
Read events
2 747
Write events
321
Delete events
133
Modification events
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2876) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
1
Suspicious files
5
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRE655.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{62BAEEB8-38AE-47AC-AF36-4570AD8A8E4B}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFA3EAABF03550EE4B.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryEN0409.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$rth Korea-South Korea Relations.doc | binary | |
MD5:2BEC5A22A72520572056A7137C75B650 | SHA256:5C662695CCE8771CD167AA685BFE859609E3ADD0F3A457D8E66609A8FDC9EFD7 | |||
| 2876 | WINWORD.EXE | C:\Users\admin\zx.exe | executable | |
MD5:73A2BDB0188707F2677B820590D0ADD9 | SHA256:69EA215785F8895E1932D5208CDF61CB096572A43B2BB19CA31192847431B016 | |||
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:0505E2722A298142460286B8A1E399E6 | SHA256:56C5CE25540E7A1D2E8D73650F4BFB27E62A94F3F9C51B37EC30A34CA90BCA61 | |||
| 2876 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{EFDDB5AC-63C3-4277-AD1B-FB7AAD555D85}.tmp | binary | |
MD5:E5A96469982203CAA38B4A2C3397CD95 | SHA256:C234CC6FBBC4EBDB913FF57421B54A42F388C0D67AB4C8DAF2AED6B2264B5161 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |