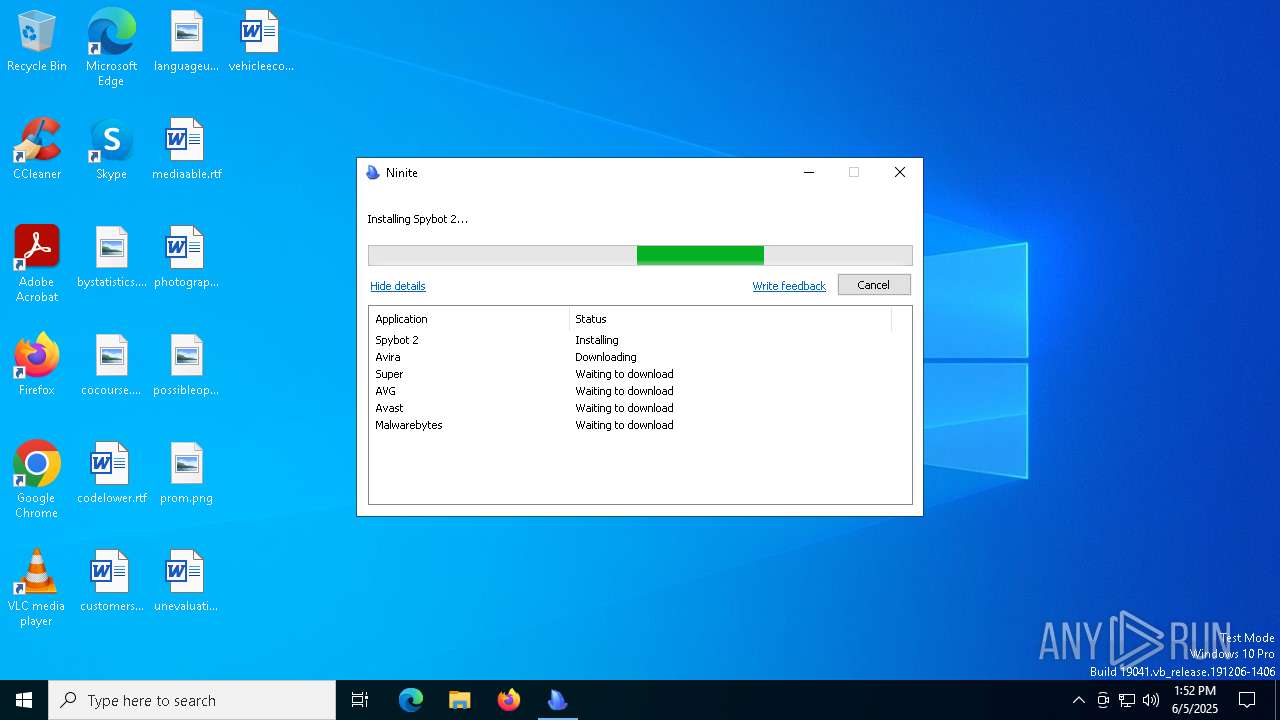
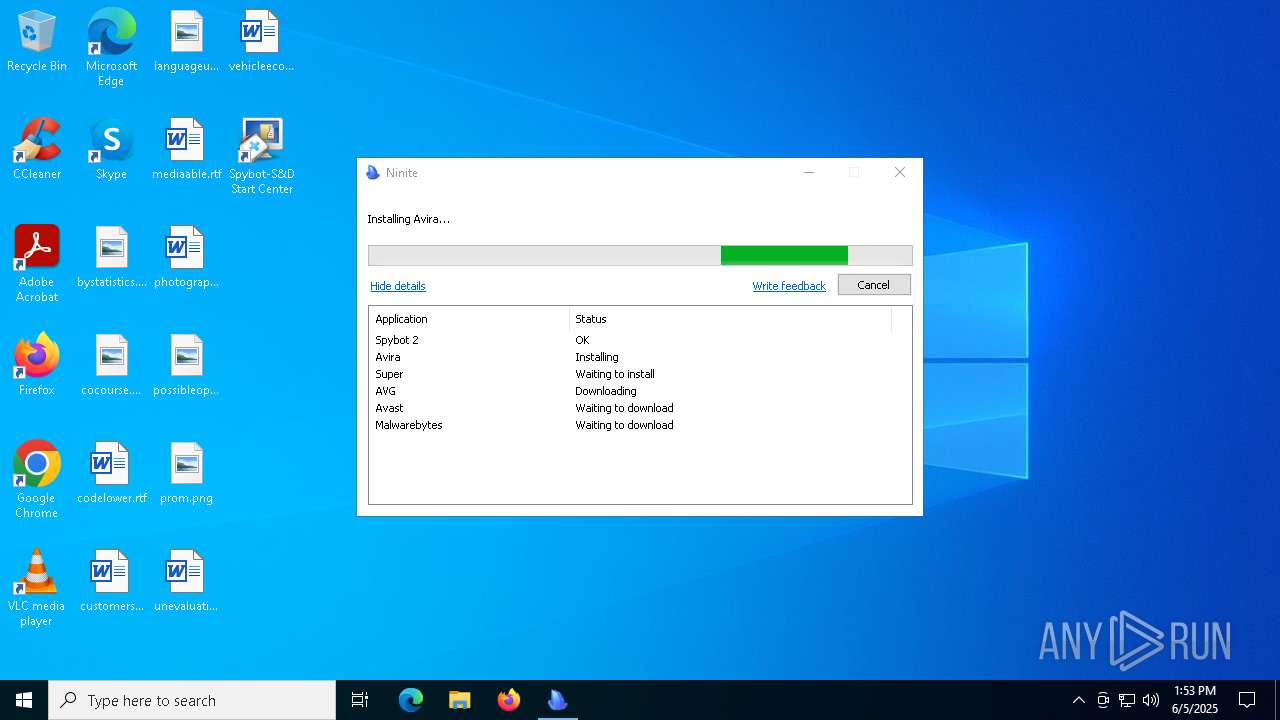
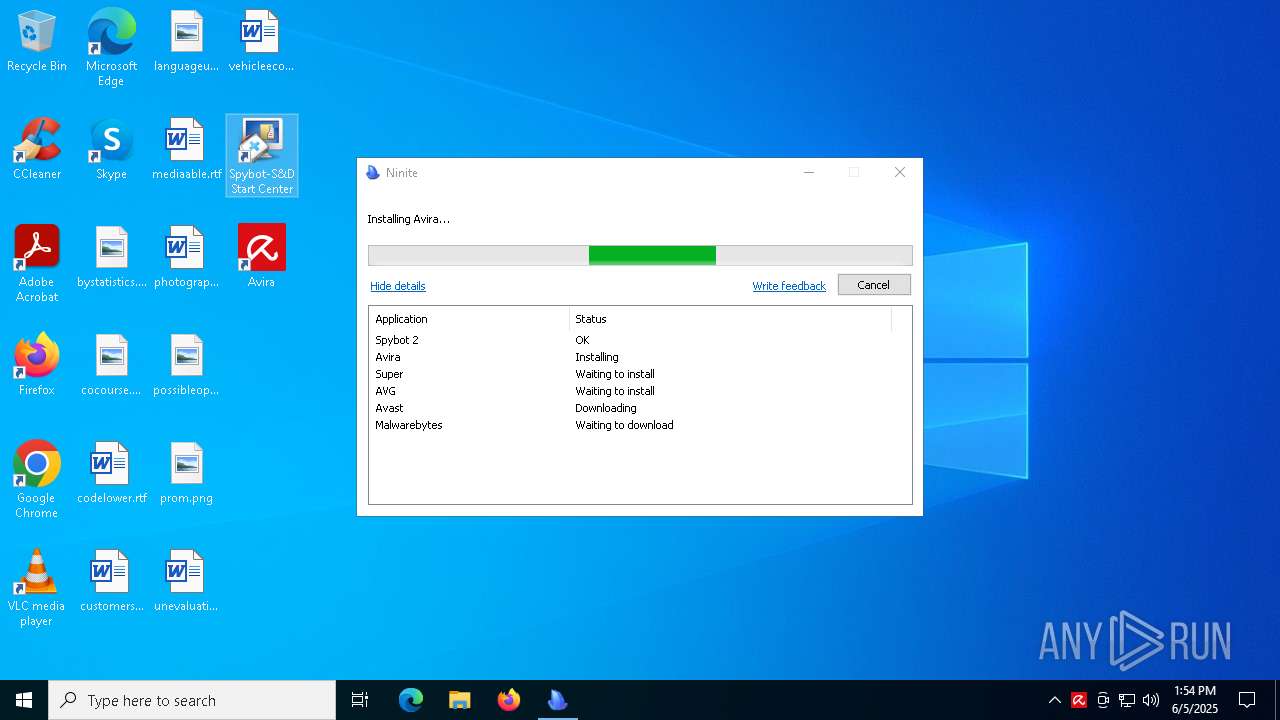
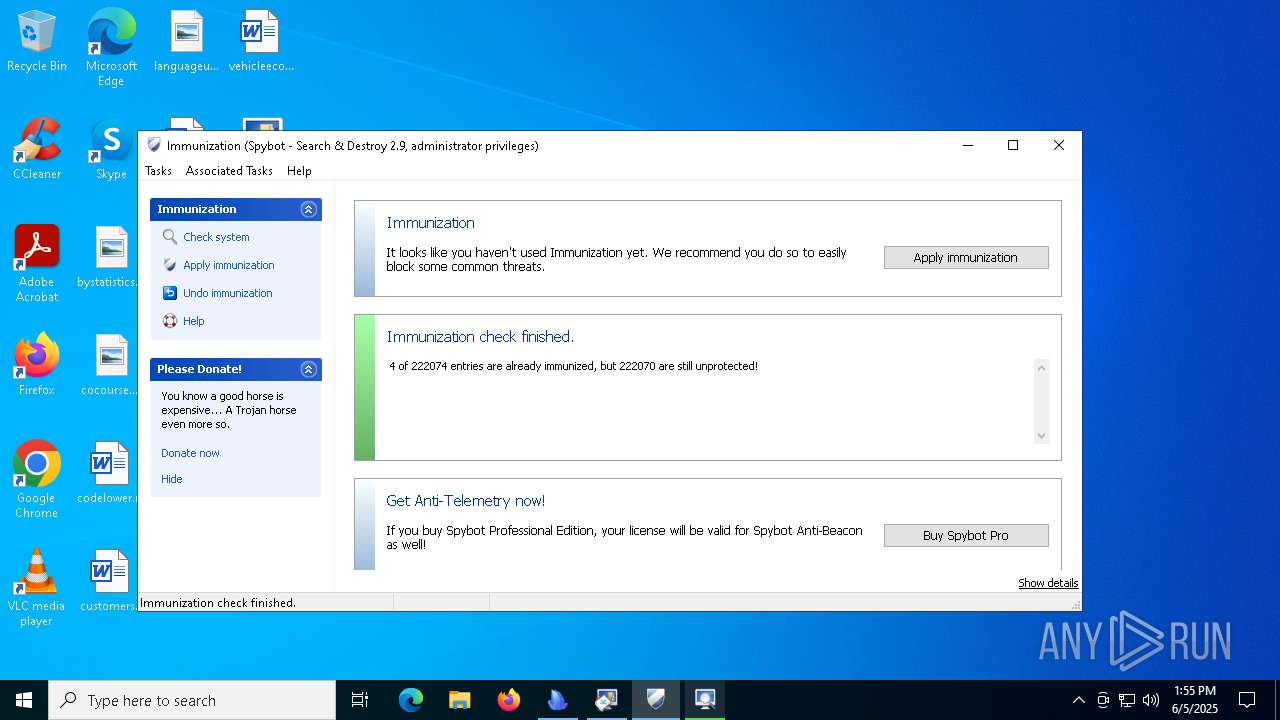
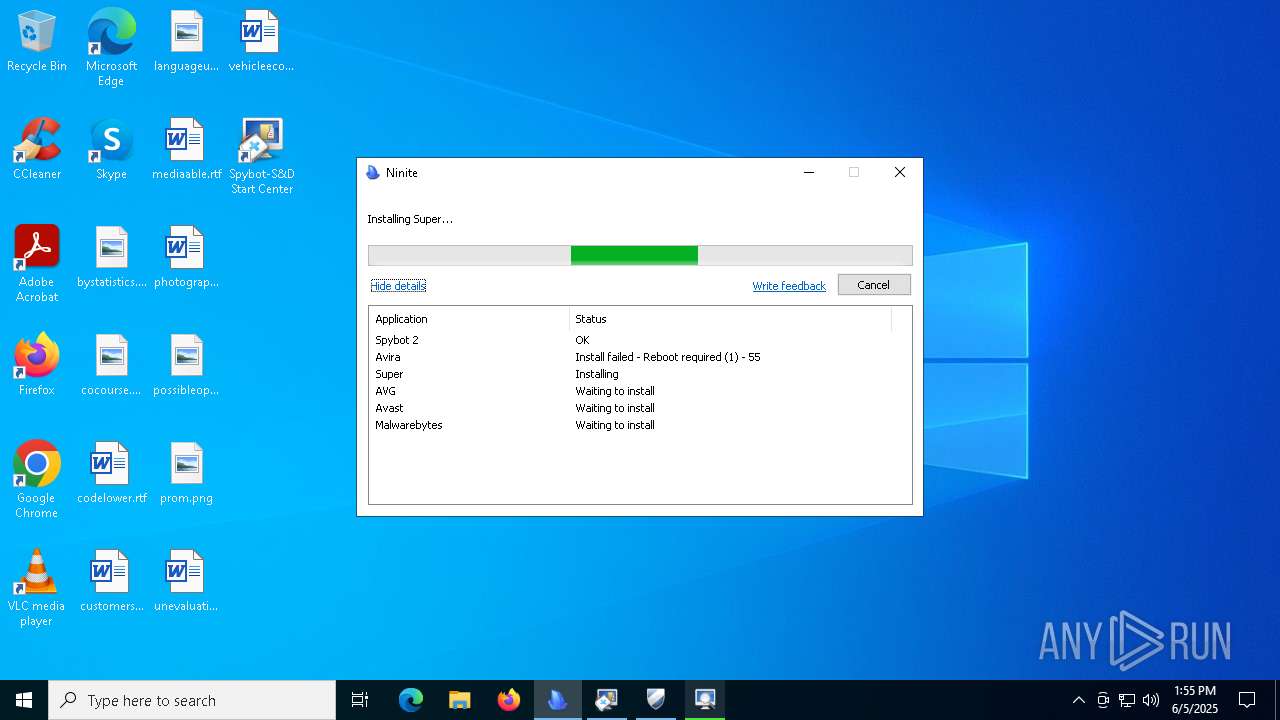
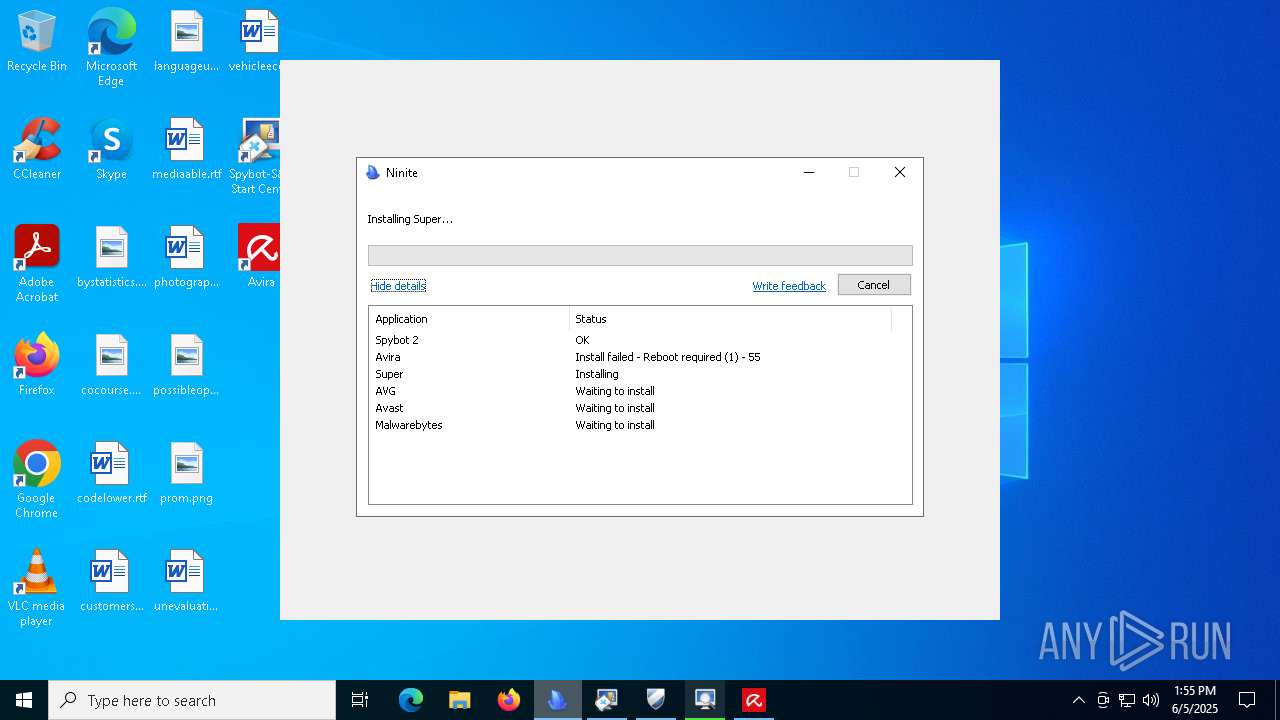
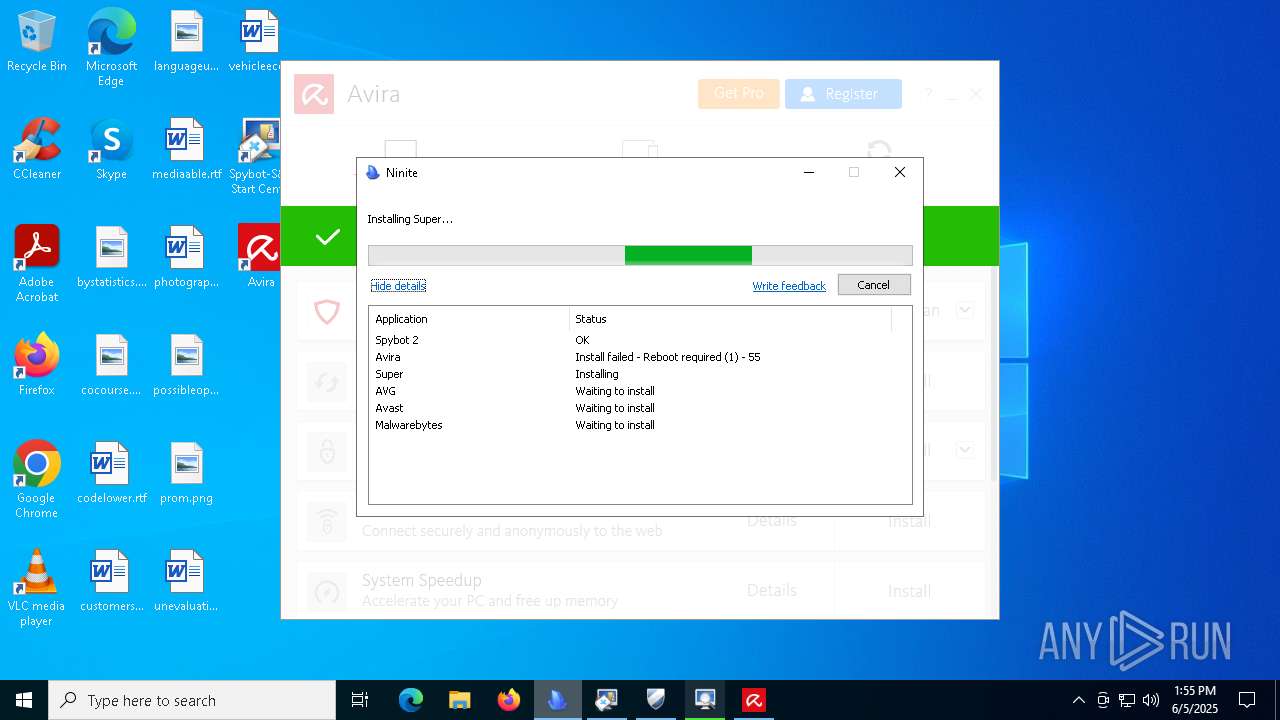
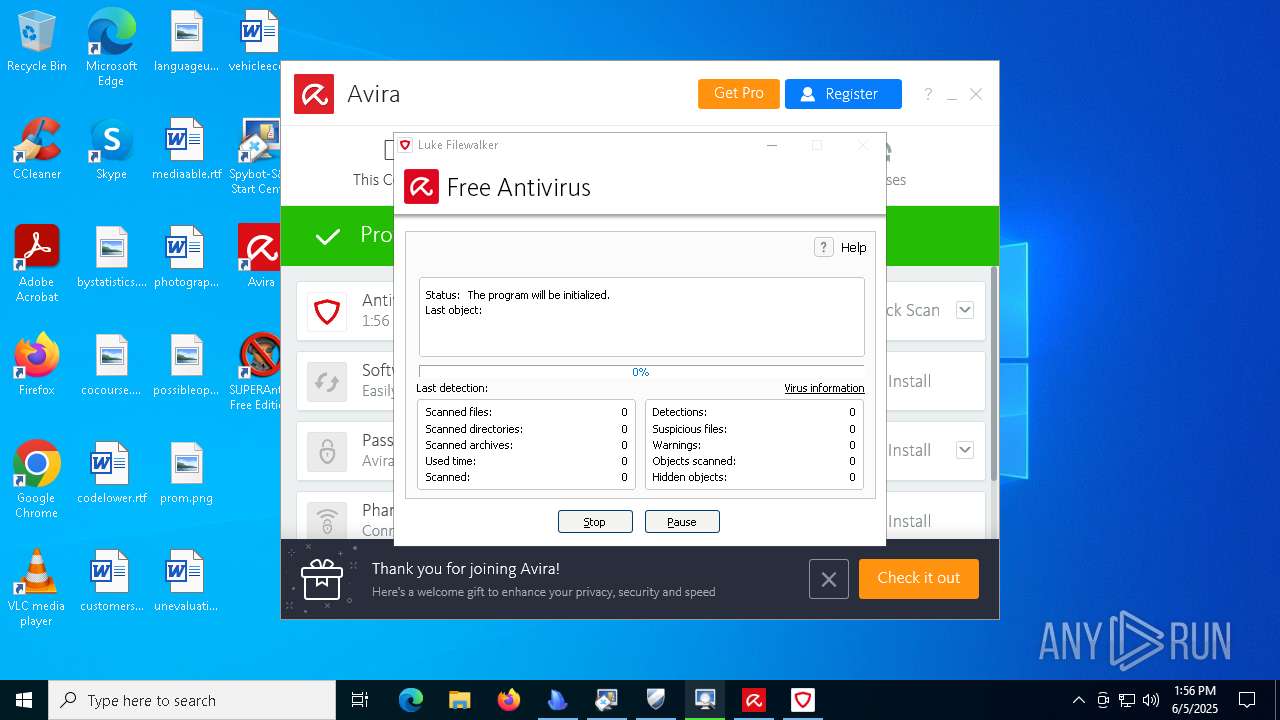
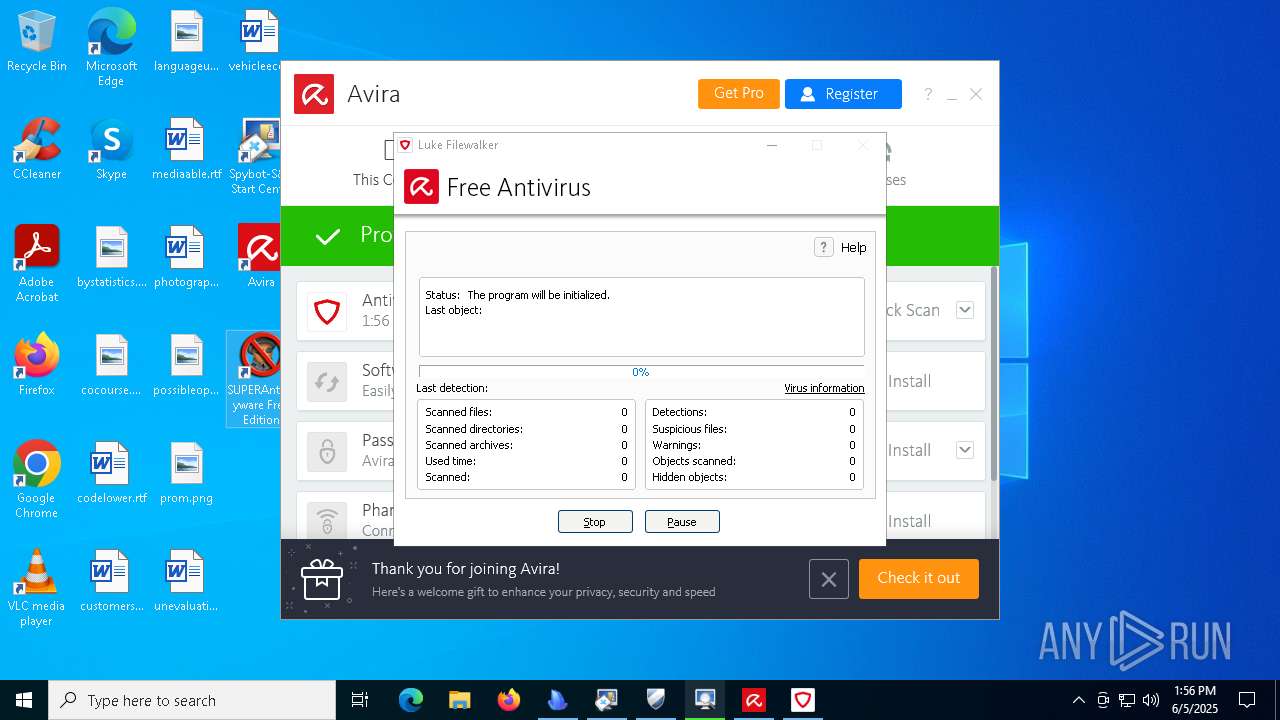
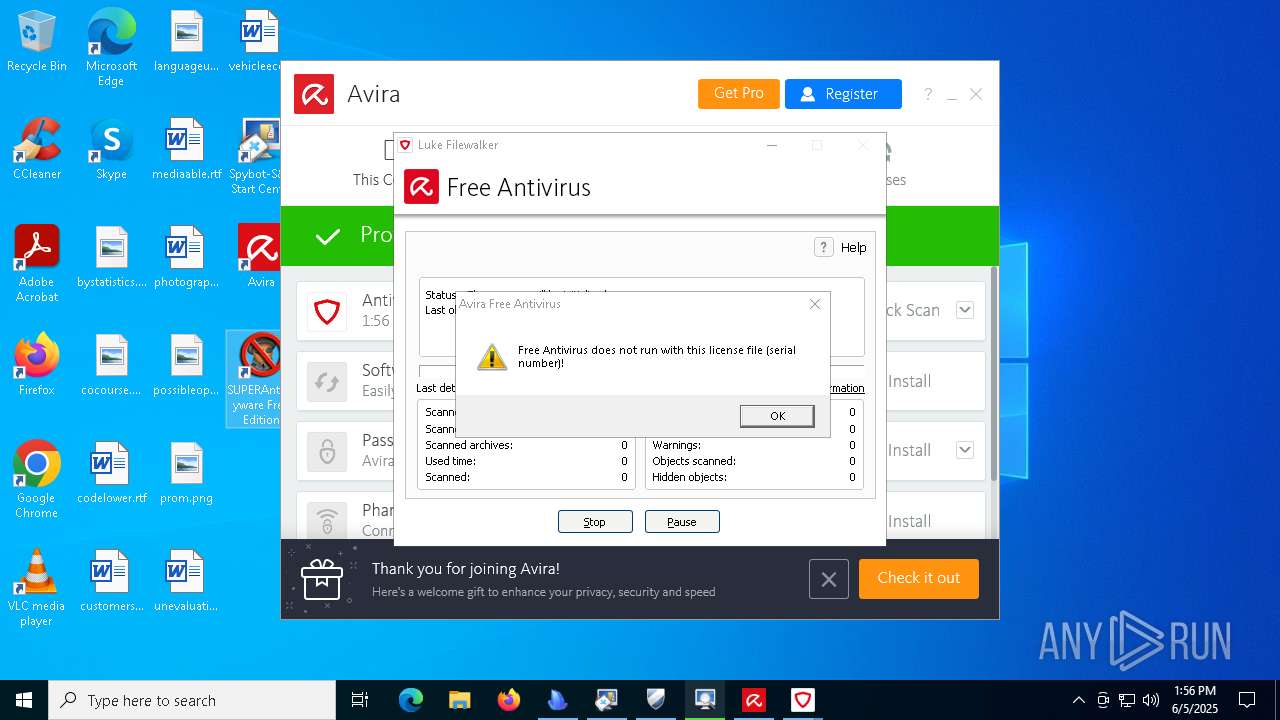
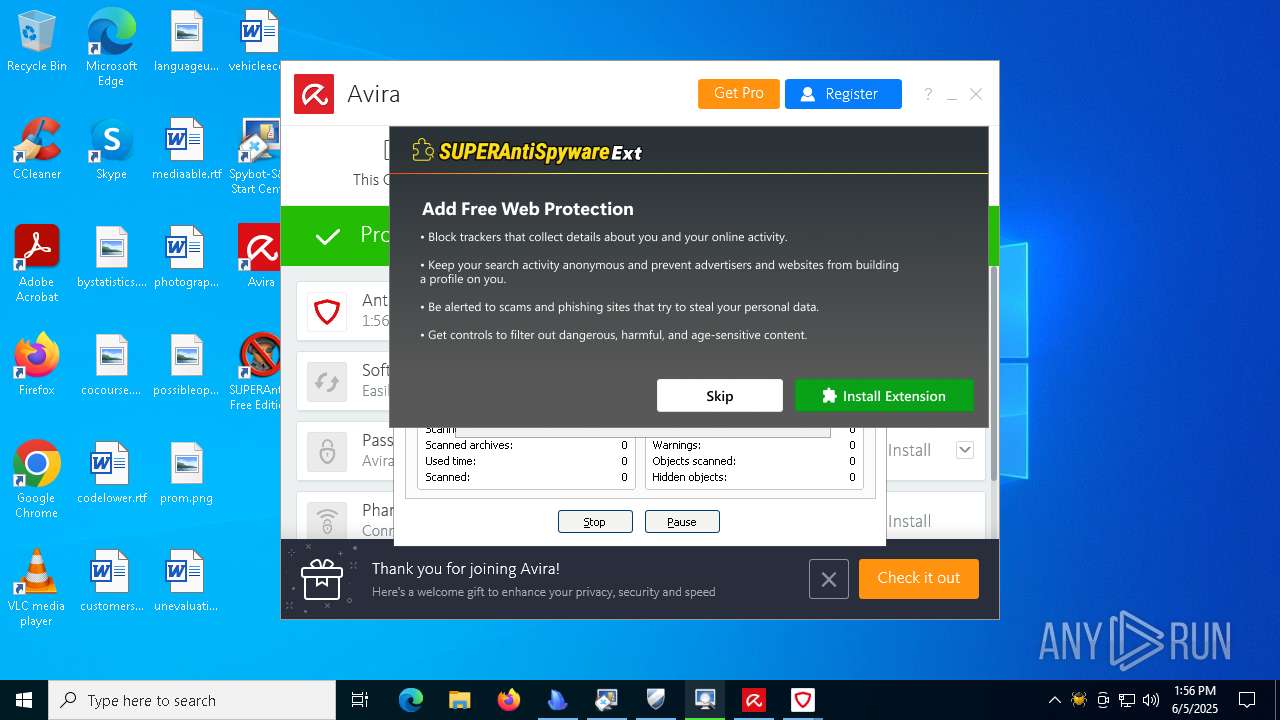
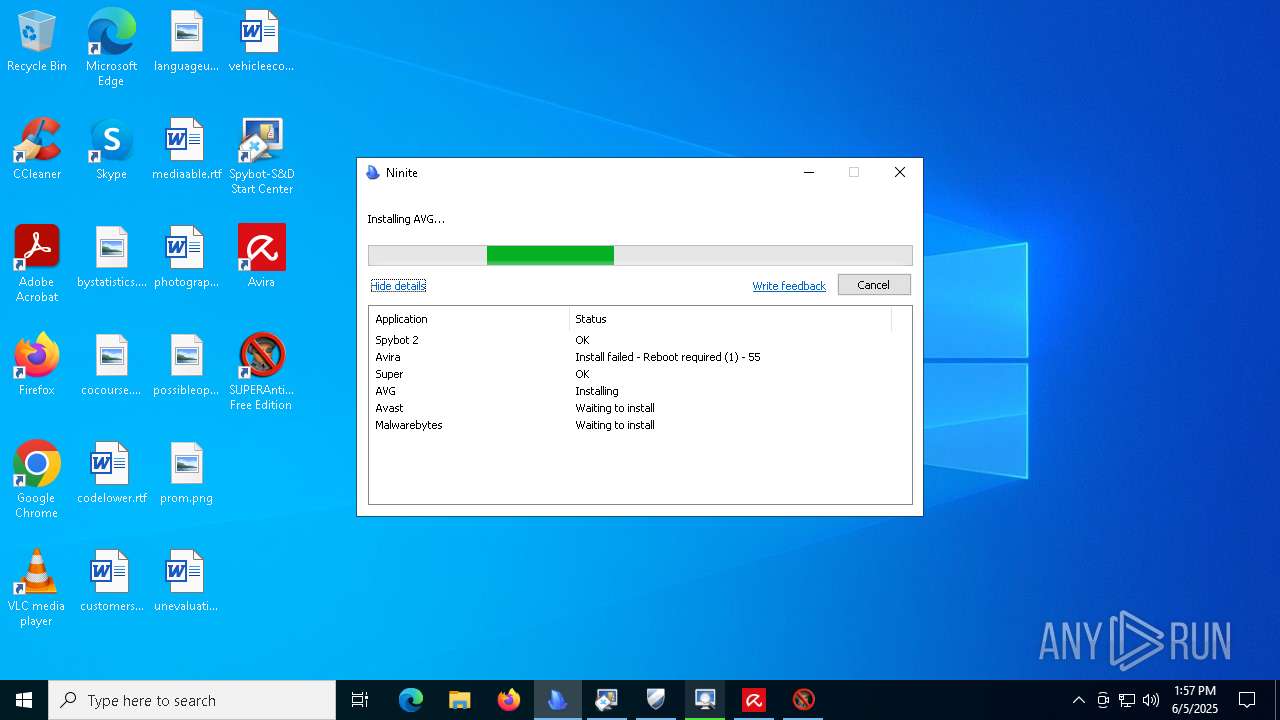
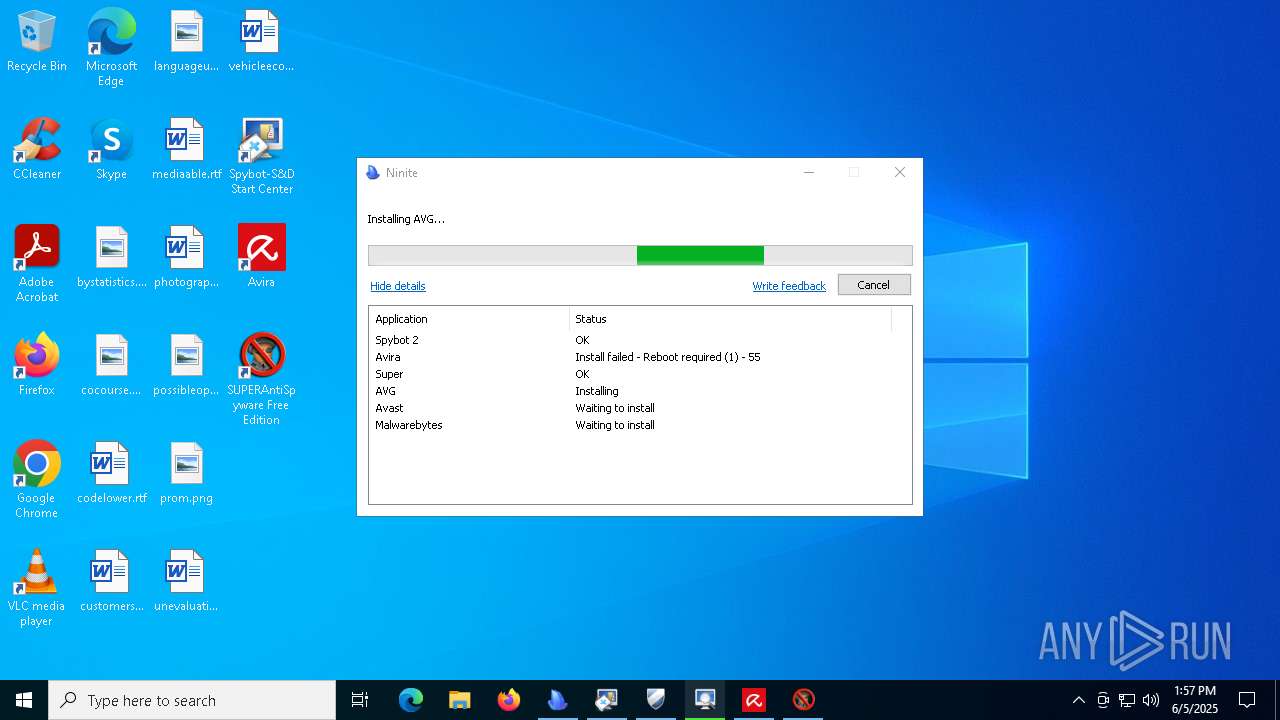
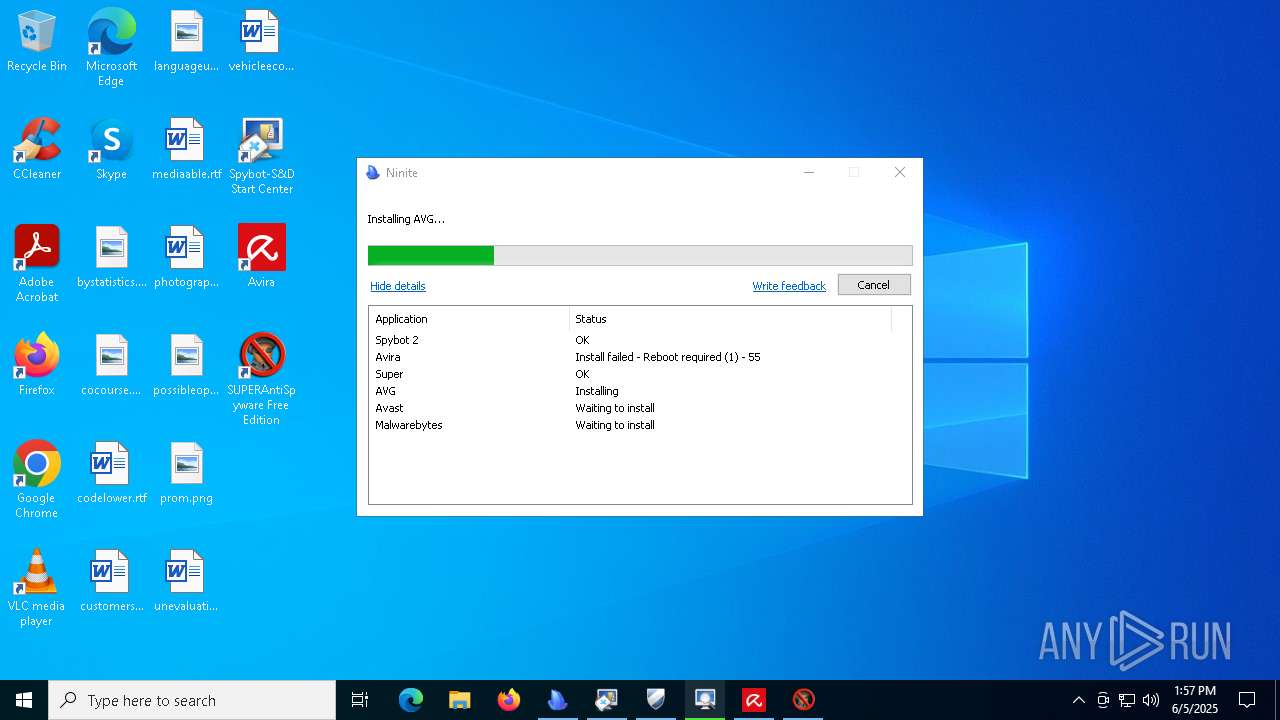
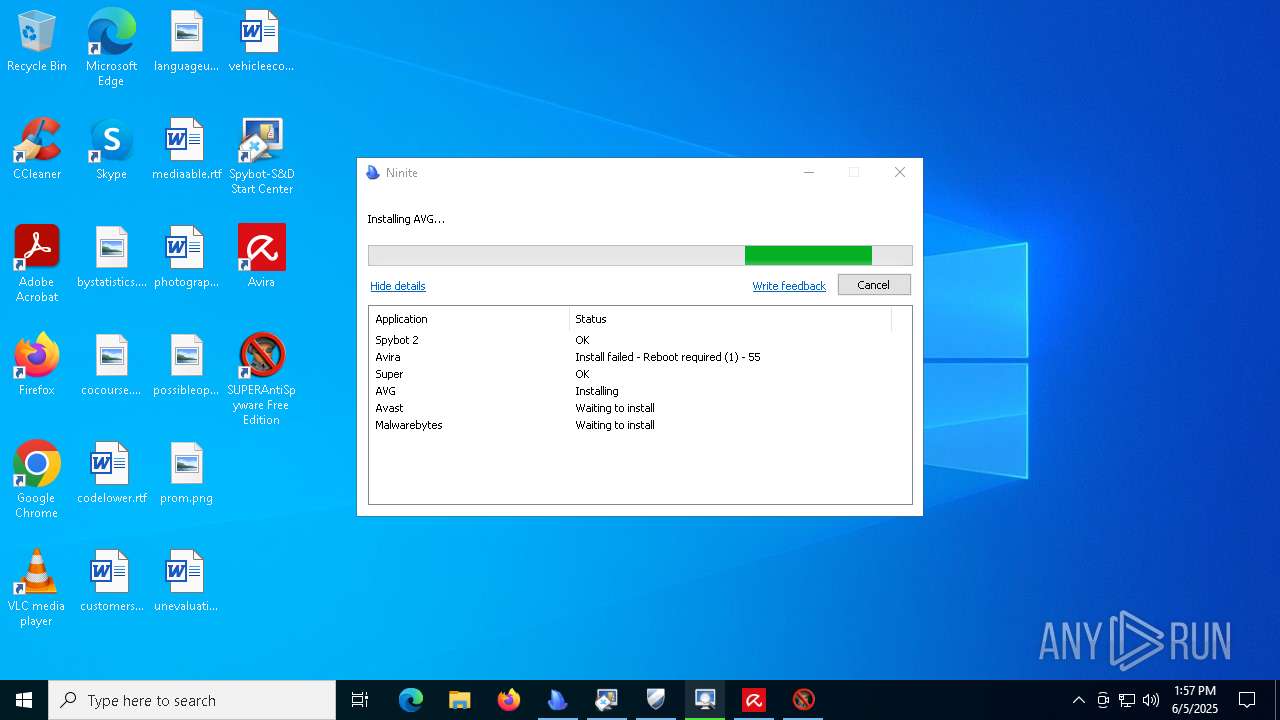
| download: | /avast-avg-avira-malwarebytes-spybot2-super/ninite.exe |
| Full analysis: | https://app.any.run/tasks/d767e7ae-7f53-4344-89c0-ae5315877516 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | June 05, 2025, 13:52:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 4B72F8BB4B22354564CD5E78D04FC298 |
| SHA1: | 3B3812A5CD41B7B33AED37A10388C0B83111F024 |
| SHA256: | 53DA14851405A462B690C0A4E0E75BA399F3FCC6FC92BCB6C4561001F884AFC3 |
| SSDEEP: | 12288:hLVP603RQX2pyf+cnci2N9pKKfyeo+pW1KKRyzE7:lVP60BM2pMUN9keo+c+zE7 |
MALICIOUS
Changes the autorun value in the registry
- target.tmp (PID: 1244)
Registers / Runs the DLL via REGSVR32.EXE
- setup.exe (PID: 7232)
- target.exe (PID: 8188)
Uses Task Scheduler to run other applications
- setup.exe (PID: 7232)
SUSPICIOUS
Reads security settings of Internet Explorer
- ninite.exe (PID: 4724)
- Ninite.exe (PID: 2236)
- Ninite.exe (PID: 7020)
- SDTray.exe (PID: 1512)
- SDFSSvc.exe (PID: 6708)
- SDUpdSvc.exe (PID: 4200)
- SDUpdate.exe (PID: 6940)
Application launched itself
- Ninite.exe (PID: 2236)
- Ninite.exe (PID: 7020)
- Avira.OE.Setup.Bundle.exe (PID: 2416)
- Avira.OE.Setup.Bundle.exe (PID: 8008)
- update.exe (PID: 2980)
- avscan.exe (PID: 5064)
Searches for installed software
- Ninite.exe (PID: 7020)
The process verifies whether the antivirus software is installed
- Ninite.exe (PID: 7020)
- target.tmp (PID: 1244)
- SDTray.exe (PID: 1512)
- SDFSSvc.exe (PID: 6708)
- SDUpdSvc.exe (PID: 4200)
- SDUpdate.exe (PID: 6940)
- SDSpybotLab.exe (PID: 3096)
Reads the Windows owner or organization settings
- target.tmp (PID: 1244)
Executable content was dropped or overwritten
- target.tmp (PID: 1244)
- target.exe (PID: 6048)
- ninite.exe (PID: 4724)
- Ninite.exe (PID: 7020)
- 7zG.exe (PID: 3032)
- spybotsd2-install-bdcore-update-2023a.exe (PID: 5124)
- avira_en____fm.exe (PID: 4748)
- spybotsd2-install-bdcore-update-2023a.tmp (PID: 5020)
- SDUpdSvc.exe (PID: 4200)
- rundll32.exe (PID: 5236)
- avira_en____fm.exe (PID: 3096)
- Avira.OE.Setup.Bundle.exe (PID: 5528)
- rundll32.exe (PID: 5232)
- rundll32.exe (PID: 1600)
- rundll32.exe (PID: 2136)
- rundll32.exe (PID: 2092)
- rundll32.exe (PID: 5344)
- rundll32.exe (PID: 2152)
- rundll32.exe (PID: 3868)
- rundll32.exe (PID: 3332)
- rundll32.exe (PID: 2660)
- rundll32.exe (PID: 4728)
- rundll32.exe (PID: 512)
- rundll32.exe (PID: 6388)
- rundll32.exe (PID: 1128)
- setup.exe (PID: 7232)
- rundll32.exe (PID: 6464)
- rundll32.exe (PID: 6072)
- Avira.ServiceHost.exe (PID: 5124)
- avira.exe (PID: 7520)
- avira.exe (PID: 7544)
- Avira.OE.Setup.Bundle.exe (PID: 7648)
- rundll32.exe (PID: 7852)
- rundll32.exe (PID: 7908)
- rundll32.exe (PID: 8096)
- rundll32.exe (PID: 7976)
- rundll32.exe (PID: 6676)
- rundll32.exe (PID: 1696)
- rundll32.exe (PID: 4180)
- rundll32.exe (PID: 6576)
- rundll32.exe (PID: 632)
- rundll32.exe (PID: 3132)
- rundll32.exe (PID: 5576)
- rundll32.exe (PID: 3008)
- rundll32.exe (PID: 7188)
- rundll32.exe (PID: 7756)
- rundll32.exe (PID: 1300)
- rundll32.exe (PID: 8012)
- rundll32.exe (PID: 7428)
- rundll32.exe (PID: 7564)
- drvinstall64.exe (PID: 7924)
- rundll32.exe (PID: 668)
- rundll32.exe (PID: 5124)
- rundll32.exe (PID: 4728)
- rundll32.exe (PID: 7424)
- rundll32.exe (PID: 5048)
- rundll32.exe (PID: 2136)
- rundll32.exe (PID: 7320)
- rundll32.exe (PID: 5164)
- rundll32.exe (PID: 4276)
- rundll32.exe (PID: 5400)
- rundll32.exe (PID: 2092)
- rundll32.exe (PID: 1228)
- rundll32.exe (PID: 8020)
- rundll32.exe (PID: 7540)
- rundll32.exe (PID: 2772)
- update.exe (PID: 2980)
- rundll32.exe (PID: 6660)
- rundll32.exe (PID: 6908)
- rundll32.exe (PID: 2644)
- rundll32.exe (PID: 512)
- rundll32.exe (PID: 672)
- rundll32.exe (PID: 5064)
- rundll32.exe (PID: 1600)
- rundll32.exe (PID: 3804)
- rundll32.exe (PID: 1512)
- Avira.OE.Setup.Bundle.exe (PID: 8008)
- Avira.OE.Setup.Bundle.exe (PID: 2392)
- target.exe (PID: 8188)
- avg_antivirus_free_setup_offline.exe (PID: 1512)
- Instup.exe (PID: 5216)
- SUPERAntiSpyware.exe (PID: 7248)
Process drops SQLite DLL files
- target.tmp (PID: 1244)
The process creates files with name similar to system file names
- target.tmp (PID: 1244)
Detected use of alternative data streams (AltDS)
- target.tmp (PID: 1244)
Drops a system driver (possible attempt to evade defenses)
- target.tmp (PID: 1244)
- 7zG.exe (PID: 3032)
- setup.exe (PID: 7232)
- drvinstall64.exe (PID: 7924)
- target.exe (PID: 8188)
Creates or modifies Windows services
- target.tmp (PID: 1244)
- SDFSSvc.exe (PID: 6708)
- SDUpdSvc.exe (PID: 4200)
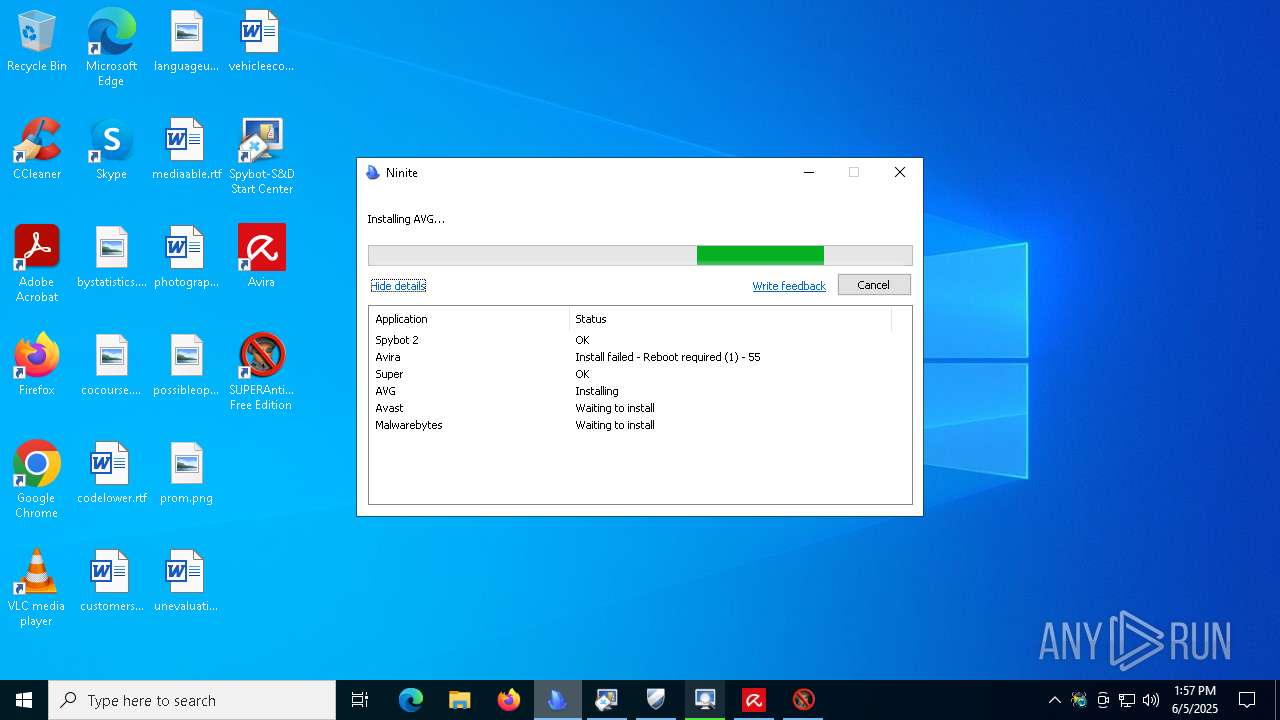
Drops 7-zip archiver for unpacking
- Ninite.exe (PID: 7020)
Process requests binary or script from the Internet
- Ninite.exe (PID: 7020)
- SDUpdSvc.exe (PID: 4200)
- update.exe (PID: 2980)
Creates/Modifies COM task schedule object
- target.tmp (PID: 1244)
Executes as Windows Service
- SDFSSvc.exe (PID: 6708)
- SDUpdSvc.exe (PID: 4200)
- Avira.ServiceHost.exe (PID: 5124)
- avguard.exe (PID: 7468)
- protectedservice.exe (PID: 7392)
- avmailc7.exe (PID: 7516)
- sched.exe (PID: 2656)
- Avira.ServiceHost.exe (PID: 4180)
- SASCore64.exe (PID: 7244)
Adds/modifies Windows certificates
- SDFSSvc.exe (PID: 6708)
The process executes via Task Scheduler
- SDUpdate.exe (PID: 6940)
Found regular expressions for crypto-addresses (YARA)
- SDFSSvc.exe (PID: 6708)
- SDUpdSvc.exe (PID: 4200)
Process drops legitimate windows executable
- 7zG.exe (PID: 3032)
- msiexec.exe (PID: 5404)
- setup.exe (PID: 7232)
- target.exe (PID: 8188)
- Instup.exe (PID: 5216)
There is functionality for taking screenshot (YARA)
- SDFSSvc.exe (PID: 6708)
- SDUpdSvc.exe (PID: 4200)
- avira_en____fm.exe (PID: 3096)
- setup.exe (PID: 7232)
- avira.exe (PID: 7520)
- avira.exe (PID: 7544)
- Avira.OE.Setup.Bundle.exe (PID: 7648)
Starts itself from another location
- avira_en____fm.exe (PID: 4748)
- avira.exe (PID: 7544)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 1540)
- schtasks.exe (PID: 3180)
- schtasks.exe (PID: 3132)
The process drops C-runtime libraries
- msiexec.exe (PID: 5404)
- target.exe (PID: 8188)
- Instup.exe (PID: 5216)
Potential Corporate Privacy Violation
- Ninite.exe (PID: 7020)
Creates a new Windows service
- sc.exe (PID: 8132)
Starts SC.EXE for service management
- setup.exe (PID: 7232)
INFO
The sample compiled with english language support
- ninite.exe (PID: 4724)
- target.tmp (PID: 1244)
- Ninite.exe (PID: 7020)
- 7zG.exe (PID: 3032)
- spybotsd2-install-bdcore-update-2023a.tmp (PID: 5020)
- avira_en____fm.exe (PID: 3096)
- avira_en____fm.exe (PID: 4748)
- msiexec.exe (PID: 5404)
- setup.exe (PID: 7232)
- Avira.ServiceHost.exe (PID: 5124)
- avira.exe (PID: 7520)
- Avira.OE.Setup.Bundle.exe (PID: 7648)
- avira.exe (PID: 7544)
- Avira.OE.Setup.Bundle.exe (PID: 5528)
- drvinstall64.exe (PID: 7924)
- update.exe (PID: 2980)
- Avira.OE.Setup.Bundle.exe (PID: 8008)
- Avira.OE.Setup.Bundle.exe (PID: 2392)
- target.exe (PID: 8188)
- Instup.exe (PID: 5216)
- avg_antivirus_free_setup_offline.exe (PID: 1512)
Reads the computer name
- ninite.exe (PID: 4724)
- Ninite.exe (PID: 7020)
- target.tmp (PID: 1244)
- Ninite.exe (PID: 2236)
- SDTray.exe (PID: 1512)
- SDFSSvc.exe (PID: 6708)
- SDUpdSvc.exe (PID: 4200)
- SDUpdate.exe (PID: 6940)
- SDSpybotLab.exe (PID: 3096)
Reads the machine GUID from the registry
- ninite.exe (PID: 4724)
- Ninite.exe (PID: 7020)
- SDTray.exe (PID: 1512)
- SDFSSvc.exe (PID: 6708)
- SDUpdate.exe (PID: 6940)
- SDUpdSvc.exe (PID: 4200)
- SDSpybotLab.exe (PID: 3096)
Checks proxy server information
- ninite.exe (PID: 4724)
- Ninite.exe (PID: 7020)
- SDTray.exe (PID: 1512)
Create files in a temporary directory
- ninite.exe (PID: 4724)
- target.exe (PID: 6048)
- Ninite.exe (PID: 7020)
- target.tmp (PID: 1244)
Reads the software policy settings
- ninite.exe (PID: 4724)
- Ninite.exe (PID: 7020)
- SDFSSvc.exe (PID: 6708)
- SDUpdate.exe (PID: 6940)
- SDUpdSvc.exe (PID: 4200)
Creates files or folders in the user directory
- ninite.exe (PID: 4724)
- Ninite.exe (PID: 7020)
Process checks computer location settings
- Ninite.exe (PID: 2236)
Checks supported languages
- Ninite.exe (PID: 2236)
- Ninite.exe (PID: 7020)
- target.tmp (PID: 1244)
- ninite.exe (PID: 4724)
- _setup64.tmp (PID: 536)
- SDTray.exe (PID: 1512)
- SDFSSvc.exe (PID: 6708)
- target.exe (PID: 6048)
- SDUpdSvc.exe (PID: 4200)
- SDUpdate.exe (PID: 6940)
- SDSpybotLab.exe (PID: 3096)
Creates files in the program directory
- target.tmp (PID: 1244)
- SDFSSvc.exe (PID: 6708)
- SDUpdSvc.exe (PID: 4200)
The sample compiled with german language support
- target.tmp (PID: 1244)
- 7zG.exe (PID: 3032)
- setup.exe (PID: 7232)
Launching a file from a Registry key
- target.tmp (PID: 1244)
Creates a software uninstall entry
- target.tmp (PID: 1244)
PECompact has been detected (YARA)
- SDFSSvc.exe (PID: 6708)
- SDUpdSvc.exe (PID: 4200)
Compiled with Borland Delphi (YARA)
- SDFSSvc.exe (PID: 6708)
- SDUpdSvc.exe (PID: 4200)
- setup.exe (PID: 7232)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5404)
SQLite executable
- msiexec.exe (PID: 5404)
Manual execution by a user
- SDWelcome.exe (PID: 7984)
- avgnt.exe (PID: 6576)
- Avira.Systray.exe (PID: 3872)
- SUPERAntiSpyware.exe (PID: 7248)
- SUPERAntiSpyware.exe (PID: 8756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:04:12 00:19:47+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 233472 |
| InitializedDataSize: | 182272 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1a53a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.1.1.1183 |
| ProductVersionNumber: | 0.1.1.1183 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Secure By Design Inc. |
| FileDescription: | Ninite |
| FileVersion: | 0,1,1,1183 |
| InternalName: | Ninite |
| LegalCopyright: | Copyright (C) 2009 Secure By Design Inc |
| OriginalFileName: | - |
| ProductName: | Ninite |
| ProductVersion: | 0,1,1,1183 |
Total processes
304
Monitored processes
166
Malicious processes
18
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | "C:\ProgramData\Package Cache\3774517F79CA2EBA0E576EF7652F5CB941BE12AA\Avira.OE.Setup.Prerequisites.exe" /enableMsiService | C:\ProgramData\Package Cache\3774517F79CA2EBA0E576EF7652F5CB941BE12AA\Avira.OE.Setup.Prerequisites.exe | — | Avira.OE.Setup.Bundle.exe | |||||||||||
User: SYSTEM Company: Avira Operations GmbH & Co. KG Integrity Level: SYSTEM Description: Avira.OE.Setup.Prerequisites Exit code: 0 Version: 1.2.158.786 Modules
| |||||||||||||||
| 512 | rundll32.exe "C:\WINDOWS\Installer\MSID529.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1168687 216 Avira.OE.Setup.CustomActions!Avira.OE.Setup.CustomActions.Configuration.ConfigureGlobalUninstaller | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 512 | rundll32.exe "C:\WINDOWS\Installer\MSI948B.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1283234 715 Avira.OE.Setup.CustomActions!Avira.OE.Setup.CustomActions.DesktopShortcut.UpdateStartMenuShortcut | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | helper 105 0x460 | C:\Users\admin\AppData\Local\Temp\is-6TQ6I.tmp\_isetup\_setup64.tmp | — | target.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 536 | C:\Windows\syswow64\MsiExec.exe -Embedding 9D0D3A6C9E76127DC35FFC4819AEF3C1 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | rundll32.exe "C:\WINDOWS\Installer\MSI84B3.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1213625 318 Avira.OE.Setup.CustomActions!Avira.OE.Setup.CustomActions.Configuration.SetSmartCacheVersion | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | rundll32.exe "C:\WINDOWS\Installer\MSI950C.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1217765 455 Avira.OE.Setup.CustomActions!Avira.OE.Setup.CustomActions.SystrayCustomActions.StopSystray | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | "C:\Program Files (x86)\Spybot - Search & Destroy 2\SDScan.exe" /scan | C:\Program Files (x86)\Spybot - Search & Destroy 2\SDScan.exe | SDWelcome.exe | ||||||||||||
User: admin Company: Safer-Networking Ltd. Integrity Level: HIGH Description: Malware Scanner Version: 2.9.85.200 Modules
| |||||||||||||||
| 672 | rundll32.exe "C:\WINDOWS\Installer\MSI82B3.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1278687 678 Avira.OE.Setup.CustomActions!Avira.OE.Setup.CustomActions.Configuration.ConfigureGlobalUninstaller | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
150 342
Read events
147 170
Write events
2 700
Delete events
472
Modification events
| (PID) Process: | (1244) target.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client |
| Operation: | write | Name: | Enabled |
Value: | |||
| (PID) Process: | (1244) target.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client |
| Operation: | write | Name: | DisabledByDefault |
Value: 0 | |||
| (PID) Process: | (1244) target.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client |
| Operation: | write | Name: | Server |
Value: | |||
| (PID) Process: | (1244) target.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp |
| Operation: | write | Name: | DefaultSecureProtocols |
Value: 2048 | |||
| (PID) Process: | (1244) target.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\SDUpdateService |
| Operation: | write | Name: | DependOnService |
Value: Tcpip | |||
| (PID) Process: | (1244) target.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List |
| Operation: | write | Name: | C:\Program Files (x86)\Spybot - Search & Destroy 2\SDUpdate.exe |
Value: C:\Program Files (x86)\Spybot - Search & Destroy 2\SDUpdate.exe:*:Enabled:Spybot-S&D 2 Updater | |||
| (PID) Process: | (1244) target.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List |
| Operation: | write | Name: | C:\Program Files (x86)\Spybot - Search & Destroy 2\SDUpdSvc.exe |
Value: C:\Program Files (x86)\Spybot - Search & Destroy 2\SDUpdSvc.exe:*:Enabled:Spybot-S&D 2 Background update service | |||
| (PID) Process: | (1244) target.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\SDUpdateService |
| Operation: | write | Name: | Description |
Value: Downloads updates and installs them. | |||
| (PID) Process: | (1244) target.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List |
| Operation: | write | Name: | C:\Program Files (x86)\Spybot - Search & Destroy 2\SDTray.exe |
Value: C:\Program Files (x86)\Spybot - Search & Destroy 2\SDTray.exe:*:Enabled:Spybot-S&D 2 Tray Icon | |||
| (PID) Process: | (1244) target.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List |
| Operation: | write | Name: | C:\Program Files (x86)\Spybot - Search & Destroy 2\SDTray.exe |
Value: C:\Program Files (x86)\Spybot - Search & Destroy 2\SDTray.exe:*:Enabled:Spybot - Search & Destroy tray access | |||
Executable files
1 757
Suspicious files
901
Text files
1 100
Unknown types
1 649
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7020 | Ninite.exe | C:\Users\admin\AppData\Local\Temp\4d653789-4214-11f0-b4ed-18f7786f96ee\target.exe_4d65378b-4214-11f0-b4ed-18f7786f96ee | — | |
MD5:— | SHA256:— | |||
| 7020 | Ninite.exe | C:\Users\admin\AppData\Local\Temp\4d653789-4214-11f0-b4ed-18f7786f96ee\target.exe | — | |
MD5:— | SHA256:— | |||
| 4724 | ninite.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | binary | |
MD5:3494671DA6AD486E07F7A10E7083E271 | SHA256:1676F0A213B7A2046C406FCFED3955BA7C777869793ABF74A857538E799365CE | |||
| 4724 | ninite.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B039FEA45CB4CC4BBACFC013C7C55604_50385F8EB1F713E33924A830D7A2A41C | binary | |
MD5:3151F0352A29742AABF2867C1F4E4494 | SHA256:933B2F62CE8397D1C9A7E8858E894B4705E2A0896F772D334F1F4226C32C3B59 | |||
| 7020 | Ninite.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_9487BC0D4381A7CDEB9A8CC43F66D27C | der | |
MD5:A4C2D80A3EBBEDF08CD3E6E28F0AFB76 | SHA256:B1977992DEC93264BB2376575081CBE50E8E29F9498348C99C6160A96BDD62C8 | |||
| 1244 | target.tmp | C:\Users\admin\AppData\Local\Temp\is-6TQ6I.tmp\inno-imgconvert.dll | executable | |
MD5:C6D7B183C8737095B6EF0961878B7DA5 | SHA256:CCCD543F453AC1459E7824A15B0F711A16846459D0325CFF3AB3B298830BFF42 | |||
| 4724 | ninite.exe | C:\Users\admin\AppData\Local\Temp\4c2cdaec-4214-11f0-b4ed-18f7786f96ee\Ninite.exe | executable | |
MD5:8C2C71081C6AFB8884501914E81FA20D | SHA256:AE60E4F6ED4EC4AA15E5A957A3A659AD06BB051A1C5BAF536B2D452CCF3D5494 | |||
| 4724 | ninite.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A1D627669EFC8CD4F21BCF387D97F9B5_BCCFCBC66B448214318C9391CA0E275F | der | |
MD5:CEAFC16CC6EC1CA0479808571EC5B22F | SHA256:66095CCA2E2B57E85D7973B7340C0173372709BE7B6EC55C13E768DAE2CC51FE | |||
| 4724 | ninite.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A1D627669EFC8CD4F21BCF387D97F9B5_BCCFCBC66B448214318C9391CA0E275F | binary | |
MD5:30EFEFE48E6123BE52E03CB3CB5AC4E5 | SHA256:8684141BC25EDBF65AF13A16E74DC9241147EDDCEA0A01A83D3842FDE114D172 | |||
| 1244 | target.tmp | C:\Users\admin\AppData\Local\Temp\is-6TQ6I.tmp\PrivacyPolicy.rtf | text | |
MD5:66BA720645C0DE1109D101E908624E07 | SHA256:1C649F1239410A2DB86E8AA203A428820C266CF96BF3FA423EF4F06CA9DC4E14 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
229
TCP/UDP connections
281
DNS requests
101
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4724 | ninite.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/gsgccr45codesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLuA3ygnKW%2F7xuSx%2F09F%2BhHVuEUQQU2rONwCSQo2t30wygWd0hZ2R2C3gCDGPUxoqhhiZifL455A%3D%3D | unknown | — | — | whitelisted |
7020 | Ninite.exe | GET | 200 | 2.16.252.233:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
7020 | Ninite.exe | GET | 200 | 18.245.65.219:80 | http://ocsp.r2m01.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBShdVEFnSEQ0gG5CBtzM48cPMe9XwQUgbgOY4qJEhjl%2Bjs7UJWf5uWQE4UCEA1Li7YBN7RrmcmQi5xUsGk%3D | unknown | — | — | whitelisted |
7020 | Ninite.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAVG%2Fhgj9%2BGUHaOfzhTEYXM%3D | unknown | — | — | whitelisted |
7020 | Ninite.exe | GET | 200 | 18.245.38.41:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4724 | ninite.exe | GET | 200 | 18.245.38.41:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | whitelisted |
6708 | SDFSSvc.exe | GET | 200 | 131.253.33.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTOQYLFSE5GO%2FpaRVfYu7d9gZEbQAQU2UEpsA8PY2zvadf1zSmepEhqMOYCEzMAAAAEllBL0tvuy4gAAAAAAAQ%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5796 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4268 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4724 | ninite.exe | 65.9.66.14:443 | ninite.com | AMAZON-02 | US | whitelisted |
4724 | ninite.exe | 18.245.38.41:80 | ocsp.rootca1.amazontrust.com | — | US | whitelisted |
4724 | ninite.exe | 151.101.130.133:80 | ocsp.globalsign.com | FASTLY | US | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ninite.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
updates3.safer-networking.org |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
client.wns.windows.com |
| whitelisted |
install.avira-update.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7020 | Ninite.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7020 | Ninite.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7020 | Ninite.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7020 | Ninite.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7020 | Ninite.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7020 | Ninite.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7020 | Ninite.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7020 | Ninite.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7020 | Ninite.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7020 | Ninite.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
Process | Message |
|---|---|
SDFSSvc.exe | Connection Manager |
SDFSSvc.exe | IE40 |
SDFSSvc.exe | \SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ |
SDFSSvc.exe | OneNoteFreeRetail - en-us |
SDFSSvc.exe | Professional2019Retail - tr-tr |
SDFSSvc.exe | WIC |
SDFSSvc.exe | {90160000-008C-040C-1000-0000000FF1CE} |
SDFSSvc.exe | \SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ |
SDFSSvc.exe | IE4Data |
SDFSSvc.exe | IEData |