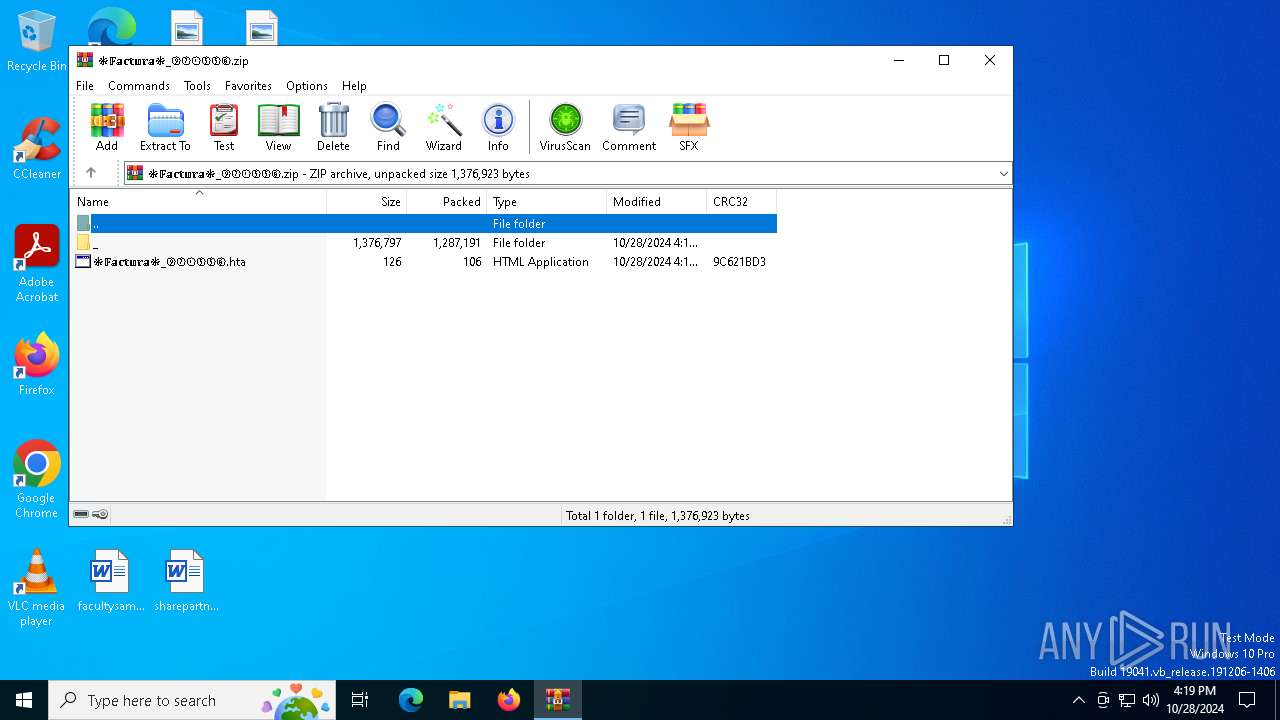
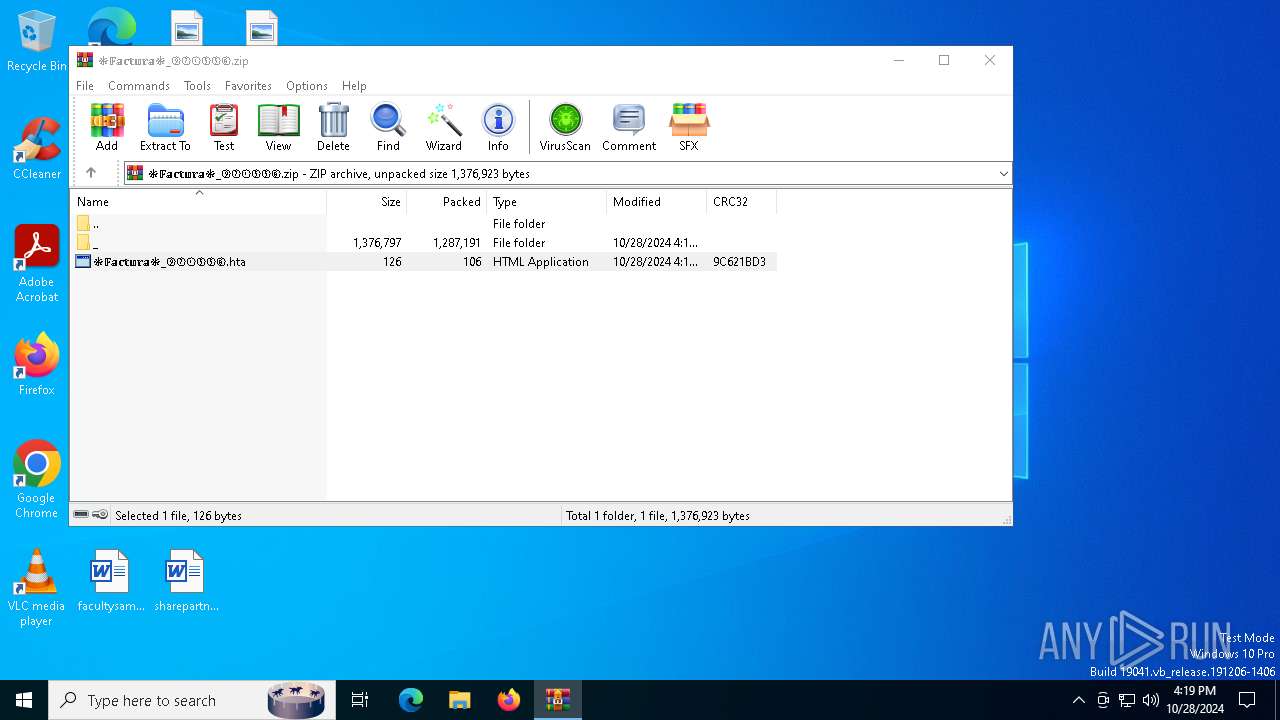
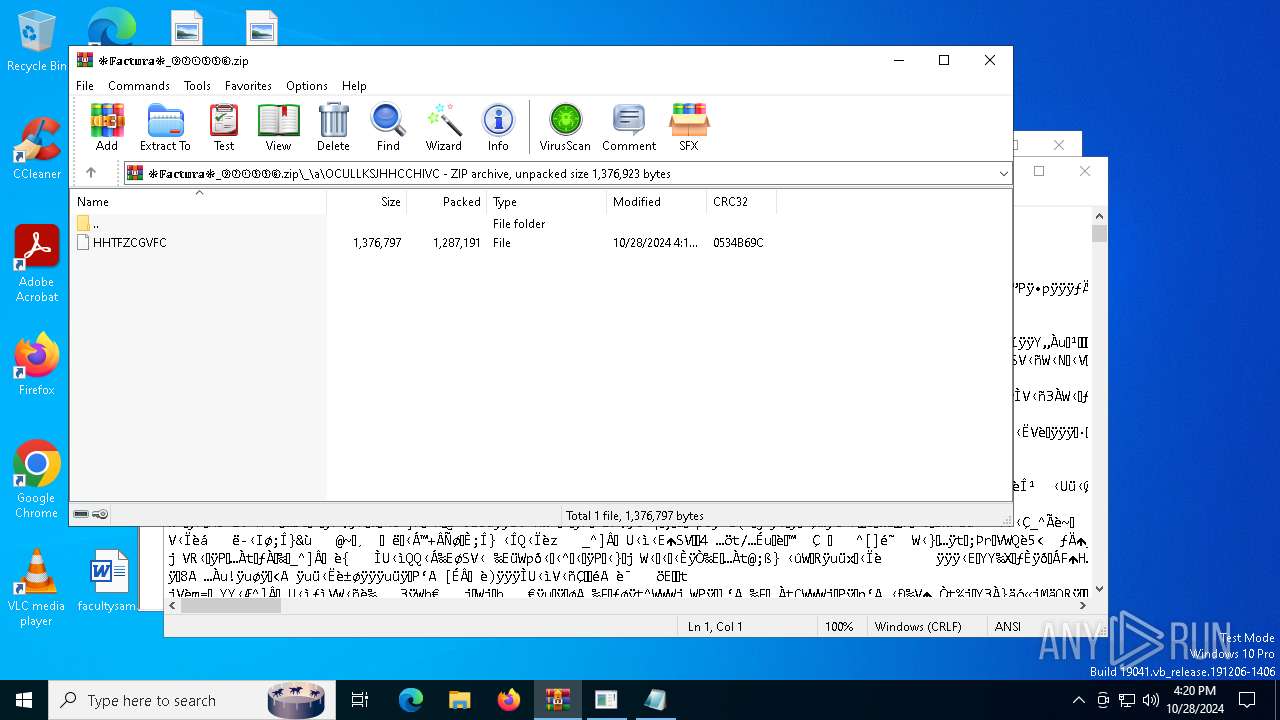
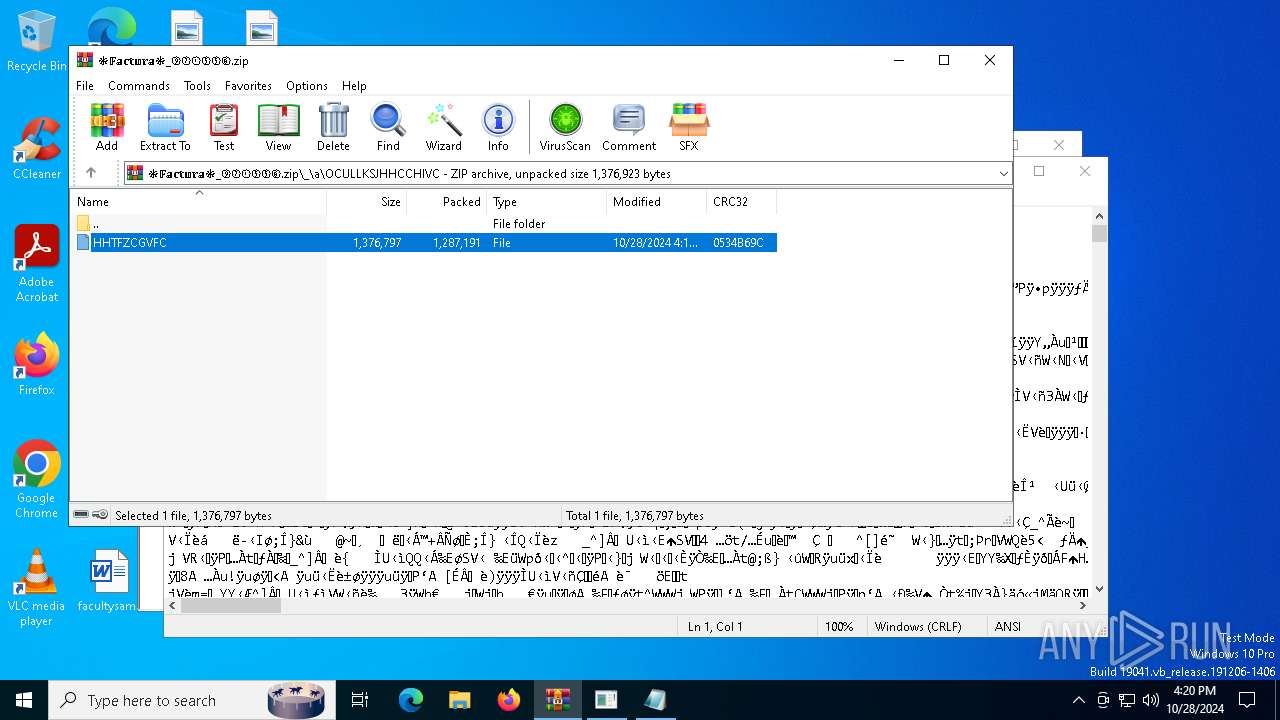
| File name: | ❉𝔽𝕒𝕔𝕥𝕦𝕣𝕒❉_⑨②①⑤⑤⑥.zip |
| Full analysis: | https://app.any.run/tasks/9f8f6d1f-47cb-44f3-834c-e65a9edfa291 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | October 28, 2024, 16:19:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 4E1735D95218BA548C943025981D7FE6 |
| SHA1: | 95DFF0E211BF33002A44D5C7999C88BA1C35D0DB |
| SHA256: | 53CADE7C6F20A6797E0099DB98087B84B80895071DB68B5CB0B168D905066945 |
| SSDEEP: | 49152:a8wVGErdTSk9tvdO7pxew9Pv2Bv6idRlF/XfTajbDAQ8AXFPafLwVpnk7pMNnOZj:aHcEMknvdOjeon2564Rz32fAEhrnbG6S |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5100)
Bypass execution policy to execute commands
- powershell.exe (PID: 6956)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 3832)
CASBANEIRO has been detected (SURICATA)
- powershell.exe (PID: 6956)
Connects to the CnC server
- powershell.exe (PID: 6956)
SUSPICIOUS
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 3832)
- cmd.exe (PID: 6164)
- cmd.exe (PID: 6432)
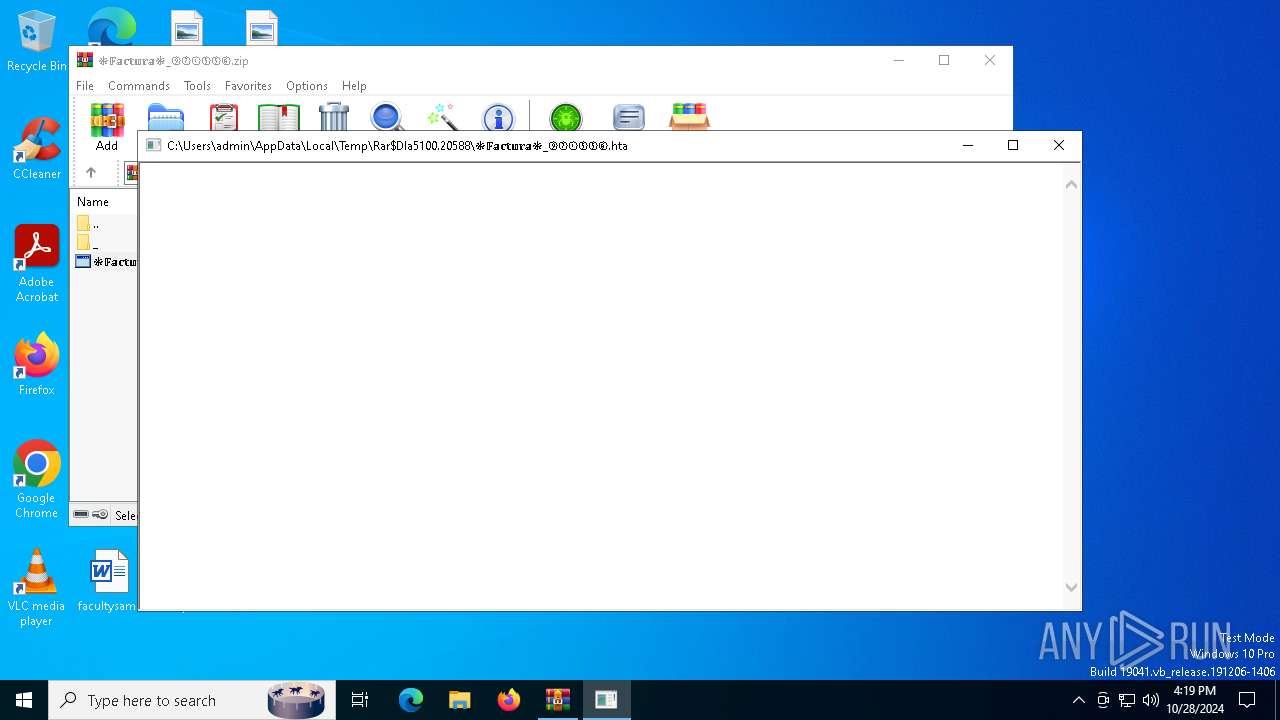
Executing commands from ".cmd" file
- mshta.exe (PID: 5984)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 5984)
- cmd.exe (PID: 6164)
- cmd.exe (PID: 6432)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 3832)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3832)
- cmd.exe (PID: 6164)
- cmd.exe (PID: 6432)
Probably download files using WebClient
- cmd.exe (PID: 3832)
Connects to the server without a host name
- powershell.exe (PID: 6956)
Contacting a server suspected of hosting an CnC
- powershell.exe (PID: 6956)
The process drops C-runtime libraries
- powershell.exe (PID: 6956)
Executable content was dropped or overwritten
- powershell.exe (PID: 6956)
- _ftypvh5_R.exe (PID: 6372)
Process drops legitimate windows executable
- powershell.exe (PID: 6956)
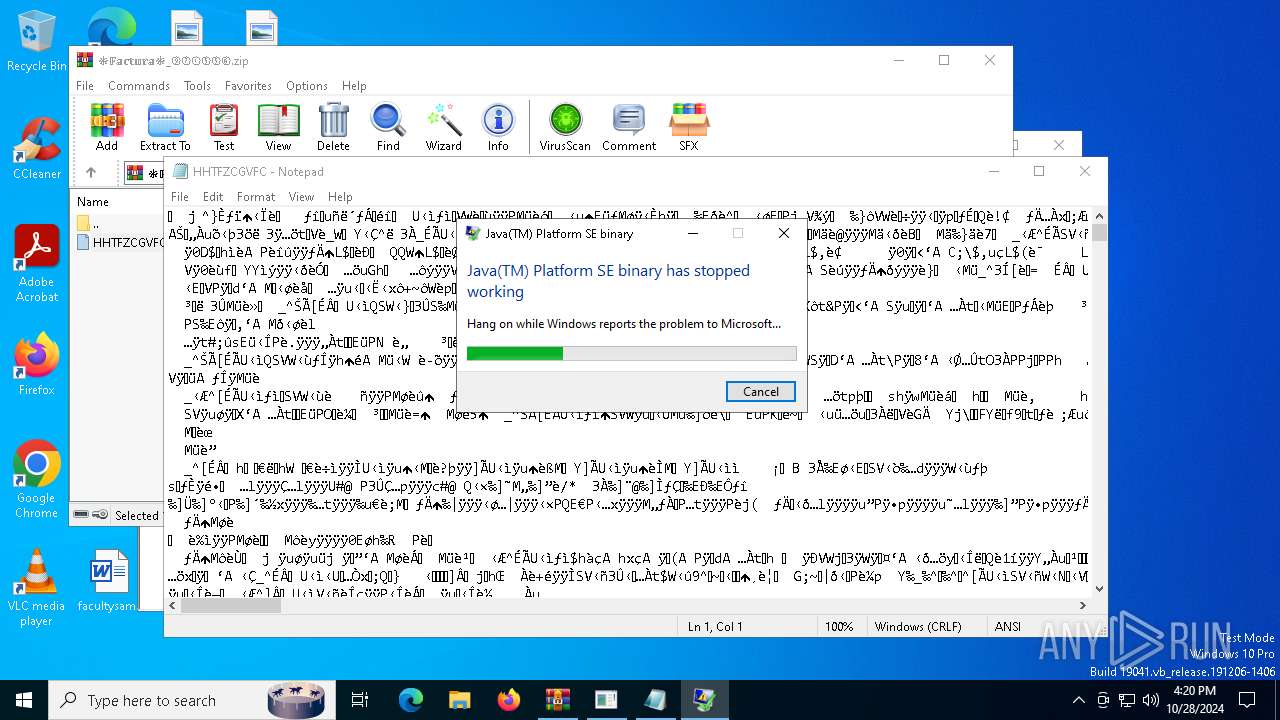
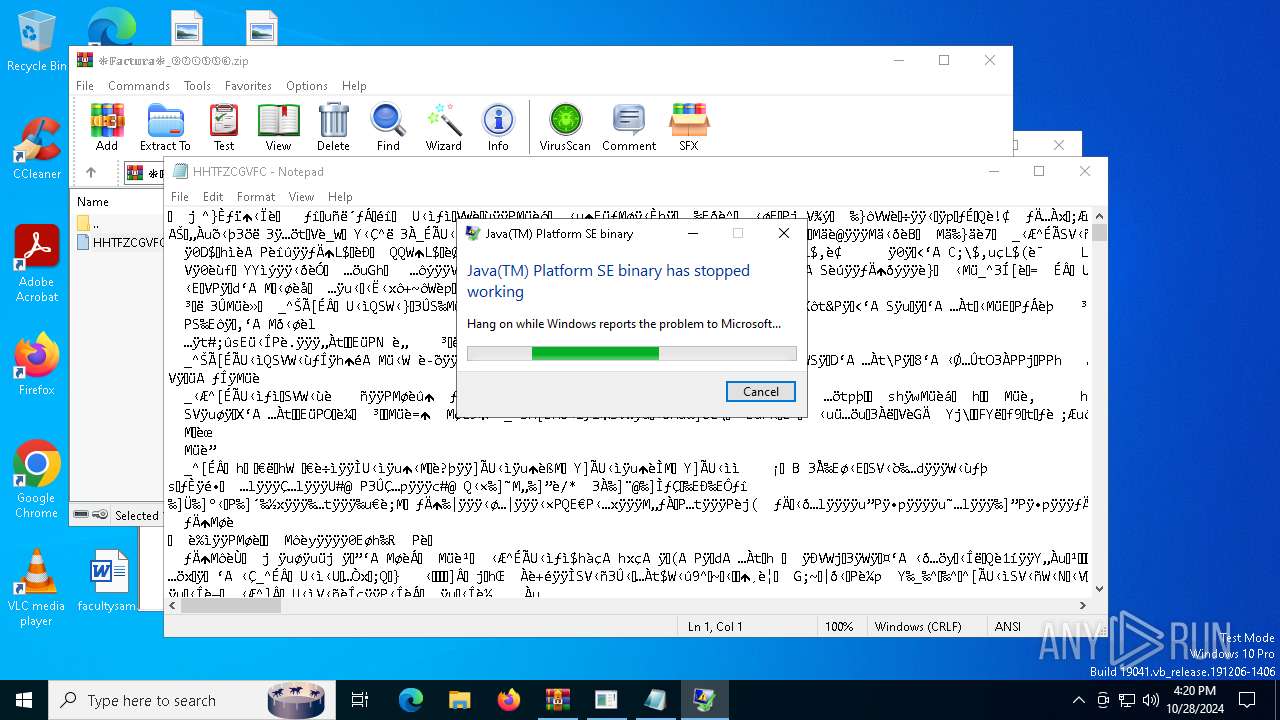
Executes application which crashes
- _ftypvh5_Ri7.exe (PID: 1768)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 804)
Application launched itself
- cmd.exe (PID: 6432)
- cmd.exe (PID: 6164)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6164)
- cmd.exe (PID: 6432)
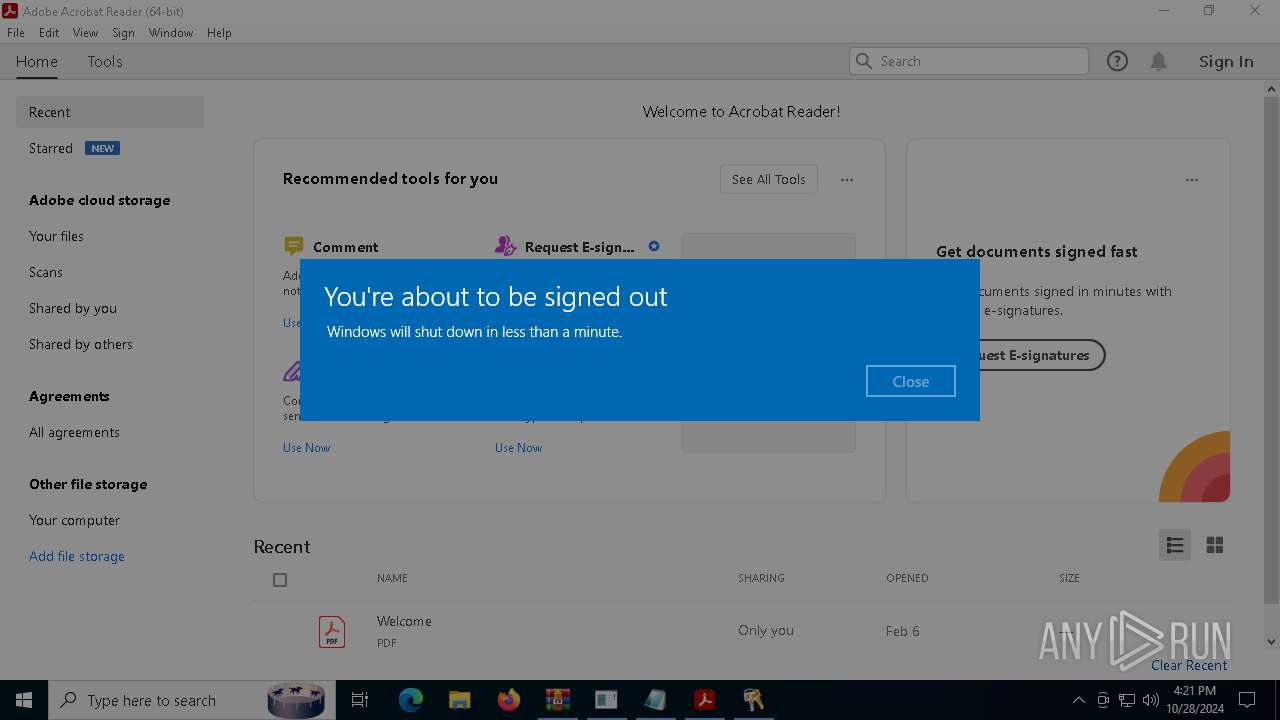
The system shut down or reboot
- powershell.exe (PID: 6956)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5100)
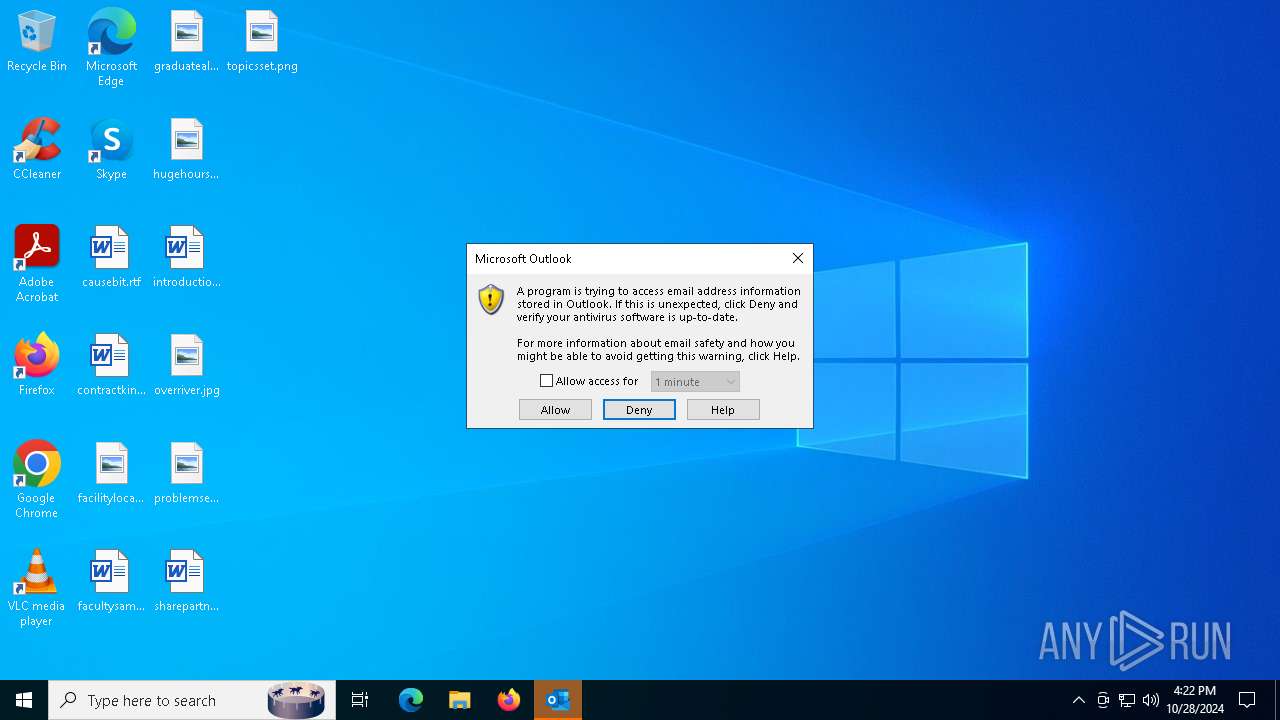
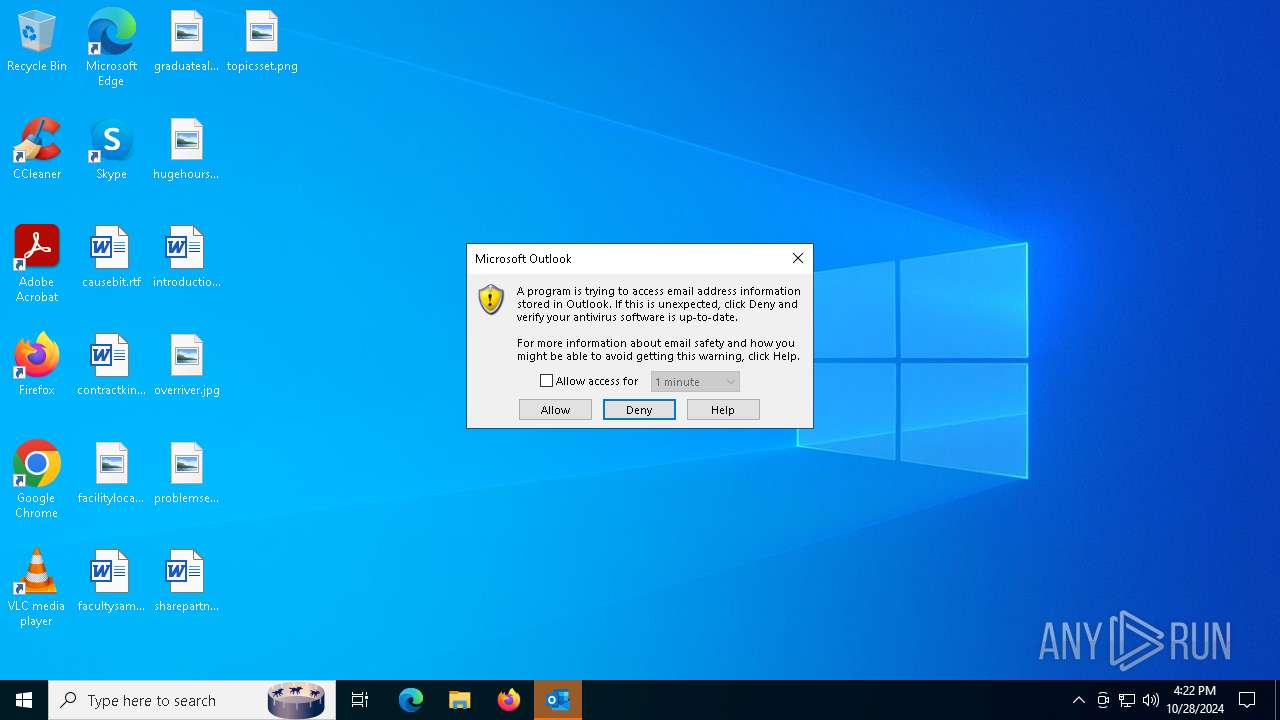
Application launched itself
- Acrobat.exe (PID: 4584)
- AcroCEF.exe (PID: 2084)
Manual execution by a user
- cmd.exe (PID: 6164)
- _ftypvh5_R.exe (PID: 6372)
- _ftypvh5_R.exe (PID: 6396)
- cmd.exe (PID: 6432)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0802 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:10:28 16:15:34 |
| ZipCRC: | 0x9c621bd3 |
| ZipCompressedSize: | 106 |
| ZipUncompressedSize: | 126 |
| ZipFileName: | ❉𝔽𝕒𝕔𝕥𝕦𝕣𝕒❉_⑨②①⑤⑤⑥.hta |
Total processes
288
Monitored processes
35
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 804 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) | |||||||||||||||
| 1008 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2700 --field-trial-handle=1620,i,11717359639943853445,18180418353830522091,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 1073807364 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1248 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1524 --field-trial-handle=1620,i,11717359639943853445,18180418353830522091,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1428 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1768 | "C:\_ftypvh5_R\_ftypvh5_Ri7.exe" | C:\_ftypvh5_R\_ftypvh5_Ri7.exe | powershell.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 3221225477 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2084 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 1073807364 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2416 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 1768 -s 712 | C:\Windows\SysWOW64\WerFault.exe | _ftypvh5_Ri7.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=utility --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2120 --field-trial-handle=1620,i,11717359639943853445,18180418353830522091,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 1073807364 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
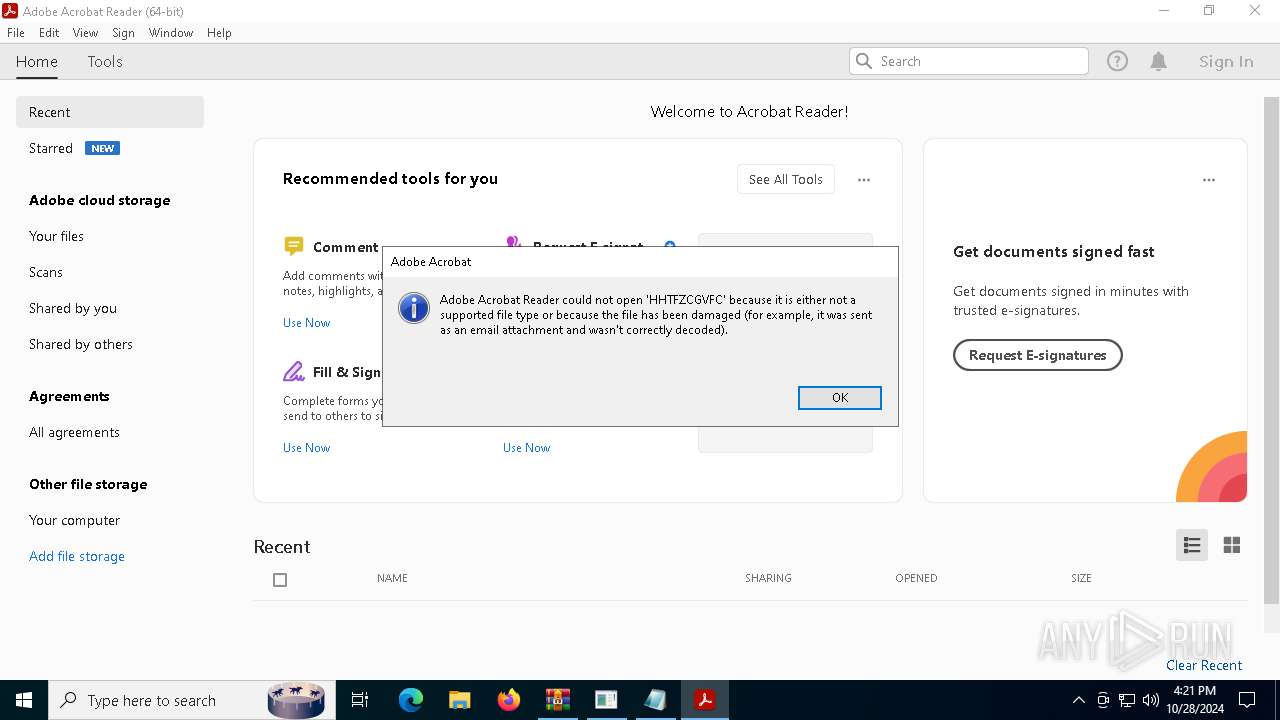
| 2816 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa5100.23672\HHTFZCGVFC | C:\Windows\System32\notepad.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 1073807364 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
26 233
Read events
26 190
Write events
41
Delete events
2
Modification events
| (PID) Process: | (5100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\❉𝔽𝕒𝕔𝕥𝕦𝕣𝕒❉_⑨②①⑤⑤⑥.zip | |||
| (PID) Process: | (5100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.hta\OpenWithProgids |
| Operation: | write | Name: | htafile |
Value: | |||
| (PID) Process: | (5984) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5984) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5984) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
11
Suspicious files
153
Text files
32
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5984 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:4AEAC92A1C1100FF979EB2F93CE27C1A | SHA256:17974FFCC86245F2C49E2C950DD44EA15FDC39CB29D1BB85826BD41D49C6305A | |||
| 5984 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:3DFCA46E00FFA4795C72A41375F159D3 | SHA256:DCBA1A505396539BAC40A7253C9F5DCCF06CBB79957E21D56305E1FC3AF5F40E | |||
| 6956 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_loq4cvpn.vtf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5984 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:BA93AAFD095FDEA458EFB1D25430F0EE | SHA256:6CF8B9F73ABE495654109EB6FD3148C78F5D6979490485BB118DE08015AAF526 | |||
| 6956 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\_ftypvh5_RAT.lnk | binary | |
MD5:702108BF96EA547314BC74A93ADE9E6B | SHA256:7E14F3052D0534136636F5A174F07EFEFF4B897FF18EA9E16CE7A2A39EE19459 | |||
| 6956 | powershell.exe | C:\_ftypvh5_R\_ftypvh5_R._ftypvh5_R | — | |
MD5:— | SHA256:— | |||
| 6956 | powershell.exe | C:\_ftypvh5_R\_ftypvh5_R.zip | — | |
MD5:— | SHA256:— | |||
| 5984 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\MZGTILOGSRVKBY[1] | text | |
MD5:FCAA0849953BA8EE0796C979D9B8D0D9 | SHA256:F4423661973855C95B3FC523CD3F53615F5287DE619075A5A12D01EC61E12E90 | |||
| 5984 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:EA8EE5E1B2E2A614B7D85CA14BCCDB0A | SHA256:57077F035344D4EFDA288010177E174A9D083583C209AD50A9BDED104FB07A1C | |||
| 6956 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wxfmmlms.dor.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
72
DNS requests
45
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1552 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5984 | mshta.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
5984 | mshta.exe | GET | 200 | 172.217.23.99:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
5984 | mshta.exe | GET | 200 | 142.250.186.67:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQC7uIYpw4nJmAnwguIyZivr | unknown | — | — | whitelisted |
6956 | powershell.exe | POST | 200 | 62.72.3.210:80 | http://62.72.3.210/ldht/index.php | unknown | — | — | malicious |
6696 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6936 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5640 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 92.123.104.36:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
filesatgrupo.shop |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5984 | mshta.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to connect to TLS FireBase Storage |
6956 | powershell.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to connect to TLS FireBase Storage |
6956 | powershell.exe | Misc activity | SUSPICIOUS [ANY.RUN] Sent Host Name in HTTP POST Body |
— | — | Misc activity | SUSPICIOUS [ANY.RUN] Sent Host Name in HTTP POST Body |
— | — | A Network Trojan was detected | BANKER [ANY.RUN] Metamorfo Check-In |
2 ETPRO signatures available at the full report