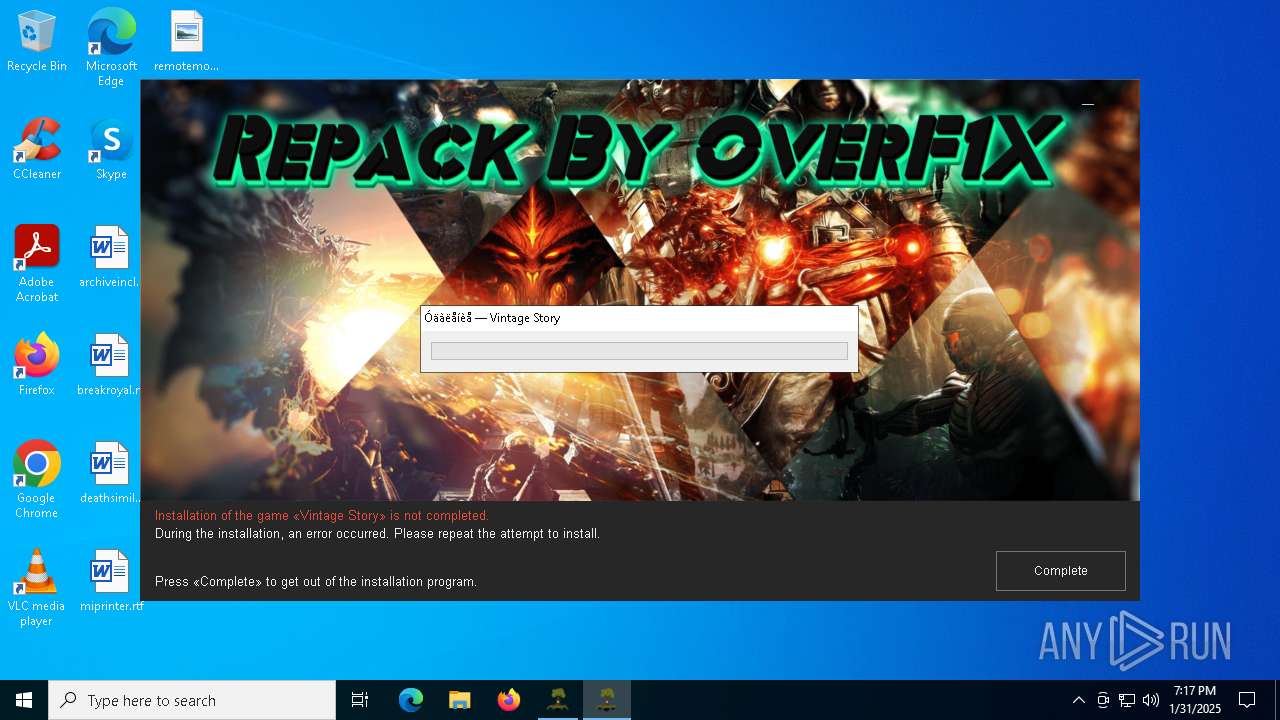
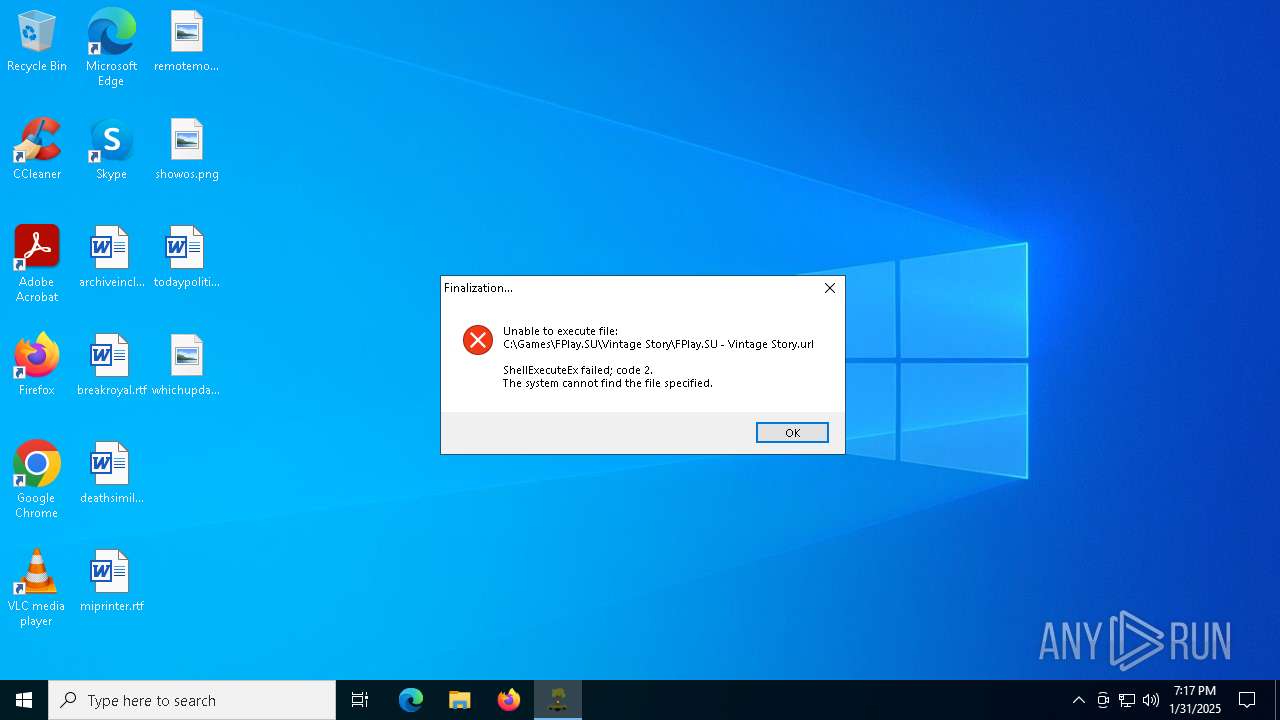
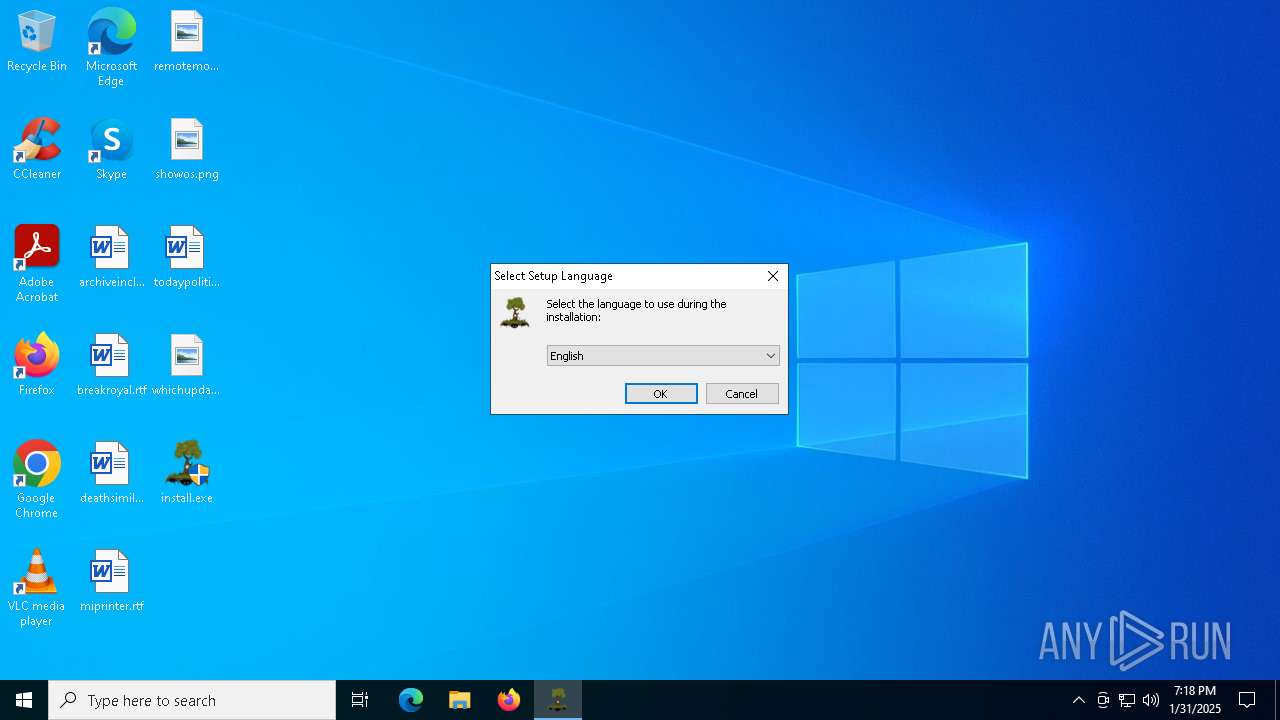
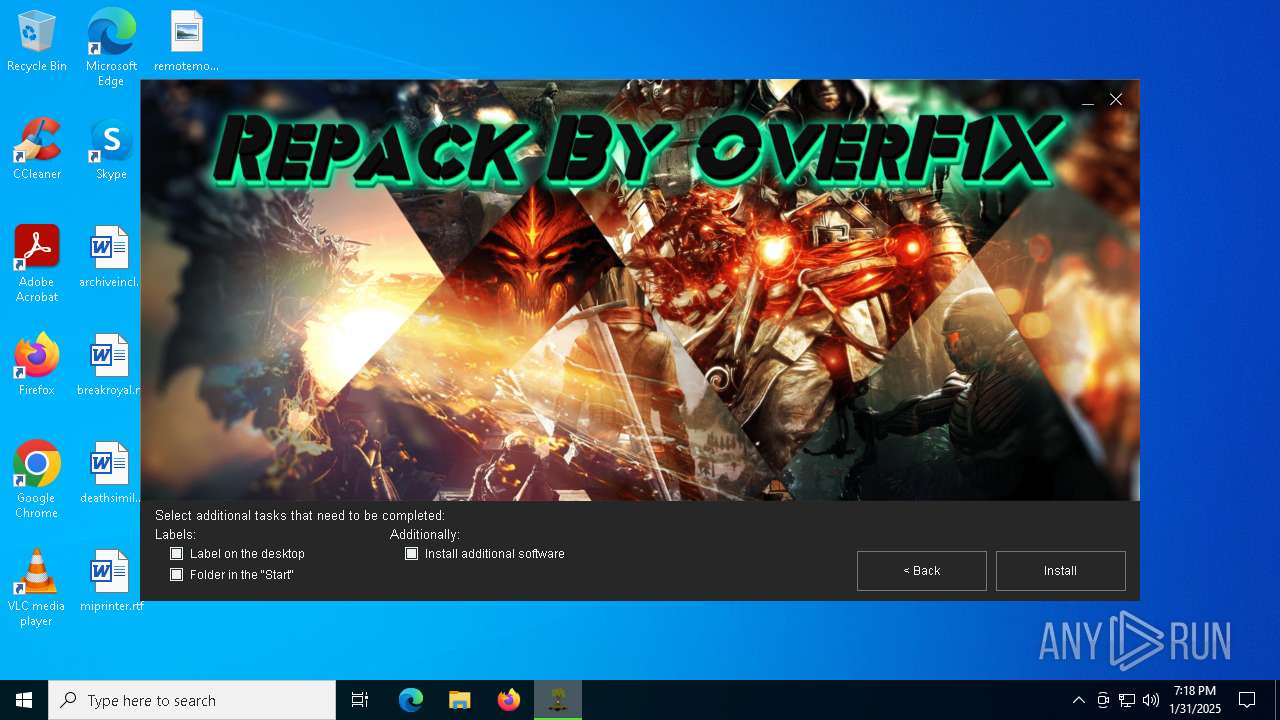
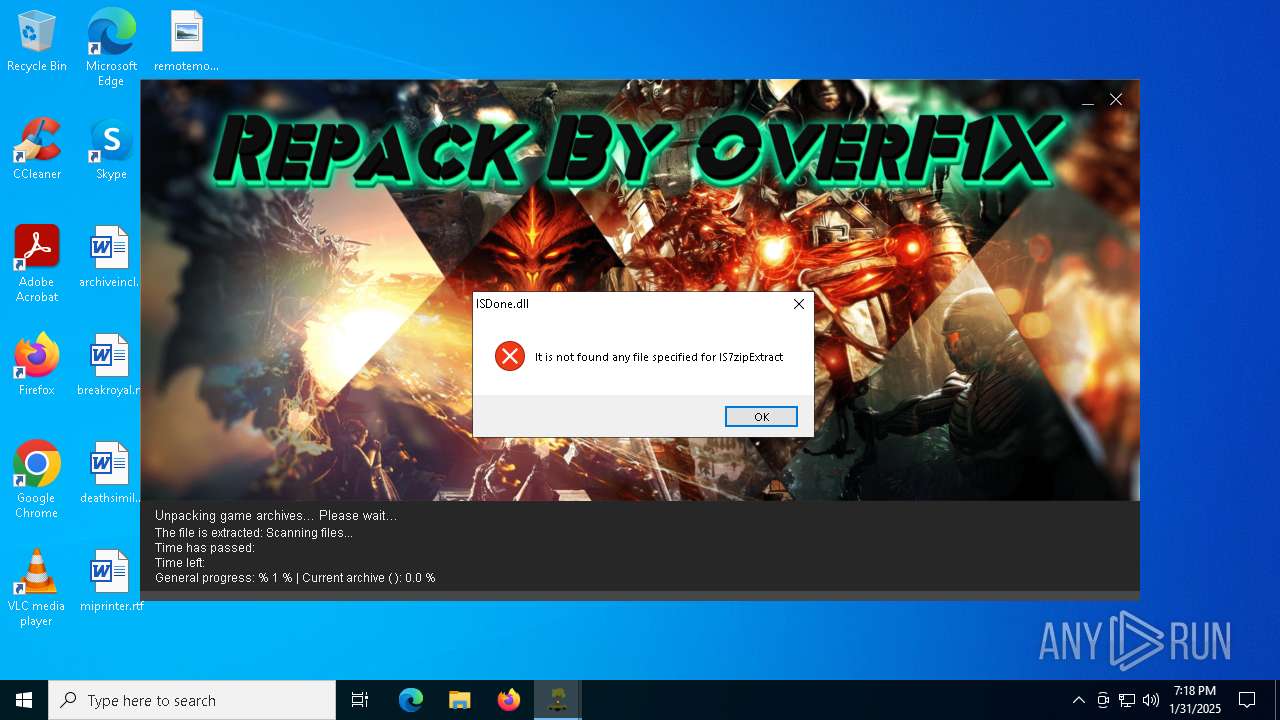
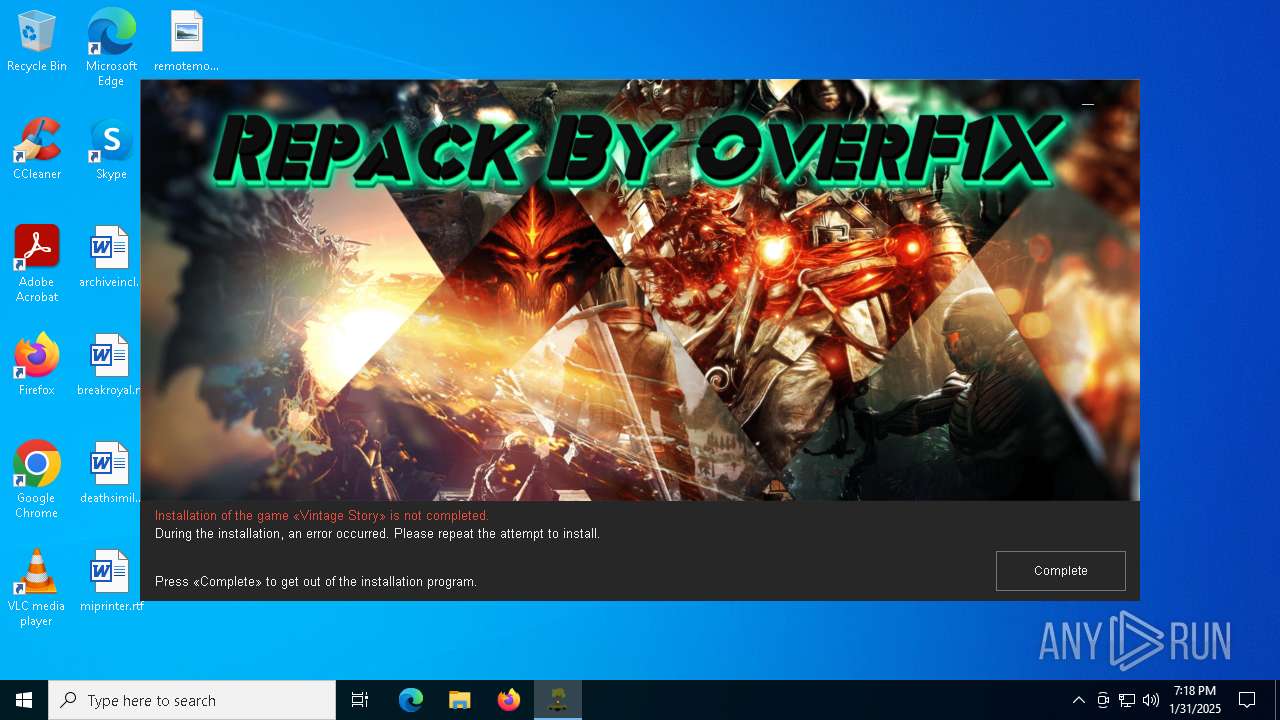
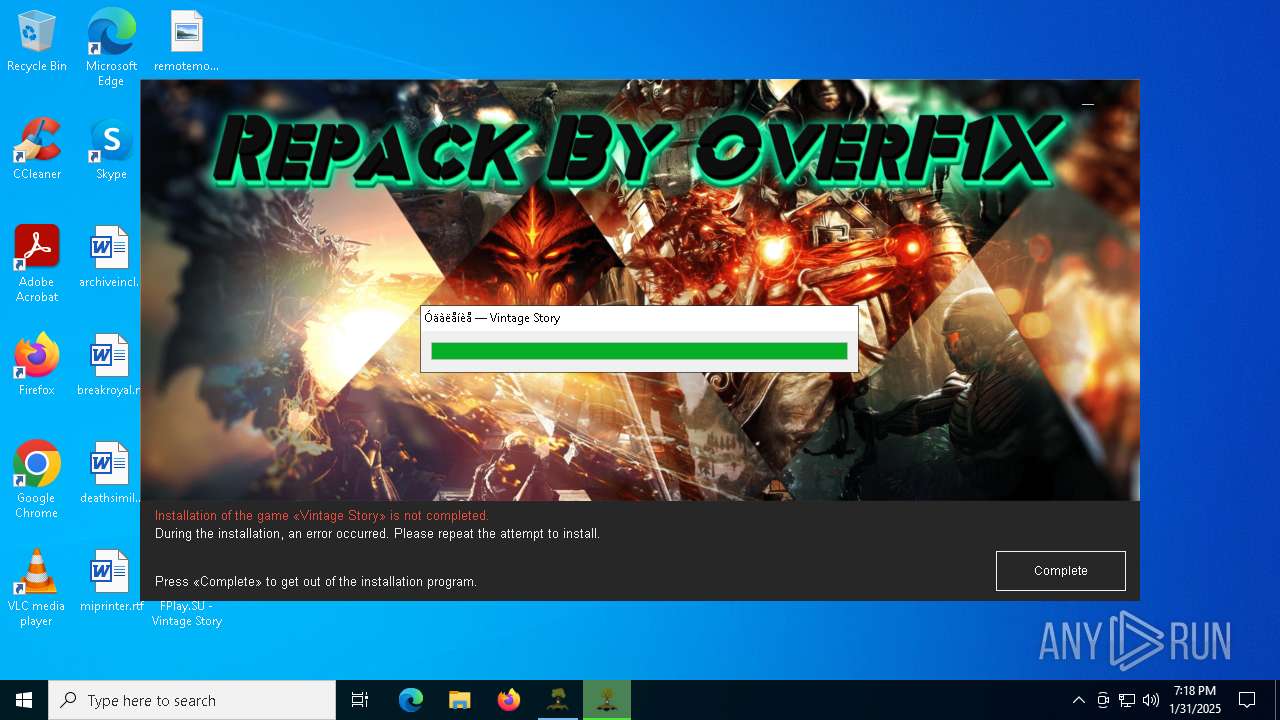
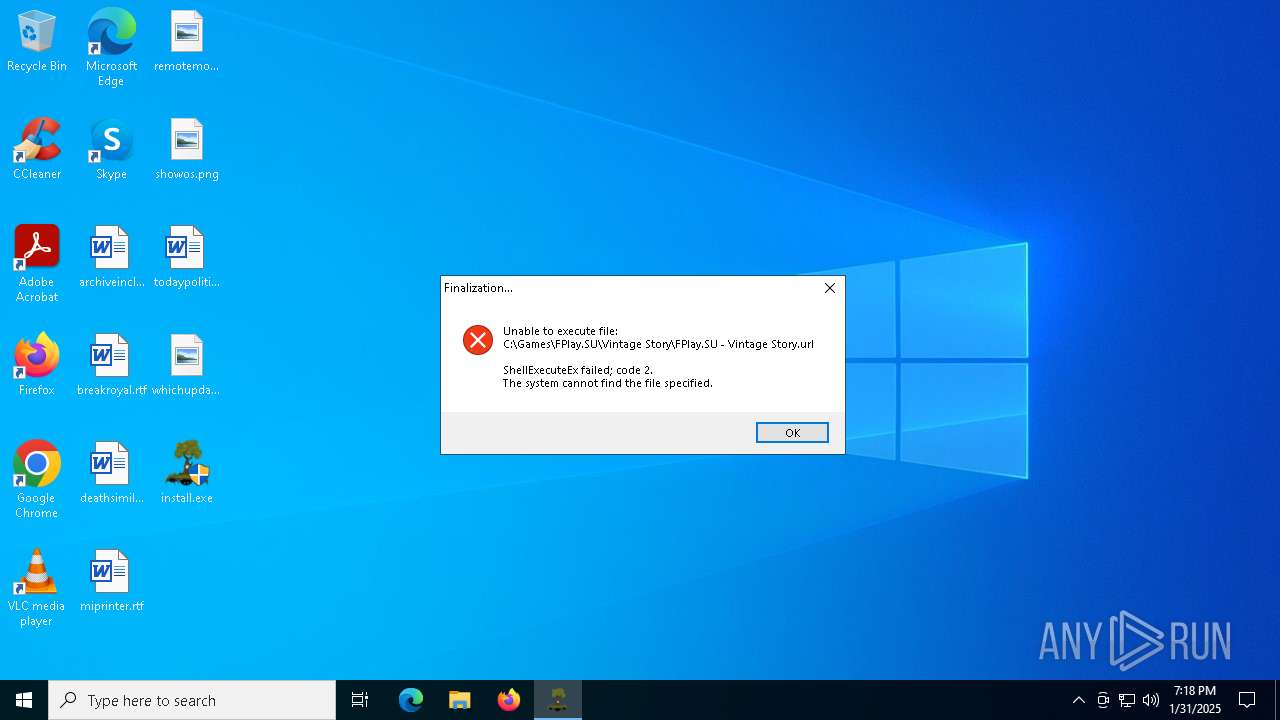
| File name: | install.exe |
| Full analysis: | https://app.any.run/tasks/42b629d3-06a8-4a1a-aa15-20cbce3bb272 |
| Verdict: | Malicious activity |
| Analysis date: | January 31, 2025, 19:17:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 76F6C92091D6D72237FD134CF38DD543 |
| SHA1: | 257BA330360D07E33097CD647B3E364E321CB601 |
| SHA256: | 53C8B7E0CDBDFC82C08EAE2FF1590C85FD53B8BDE152222DF510AE9DDBF46695 |
| SSDEEP: | 98304:nanvyA75oENidwkz09gDYvgdZym4y1PfIxQGAd1eIGSLK2/PvZnx4L4y1qDrqozj:b7tHNHgH07S/c |
MALICIOUS
No malicious indicators.SUSPICIOUS
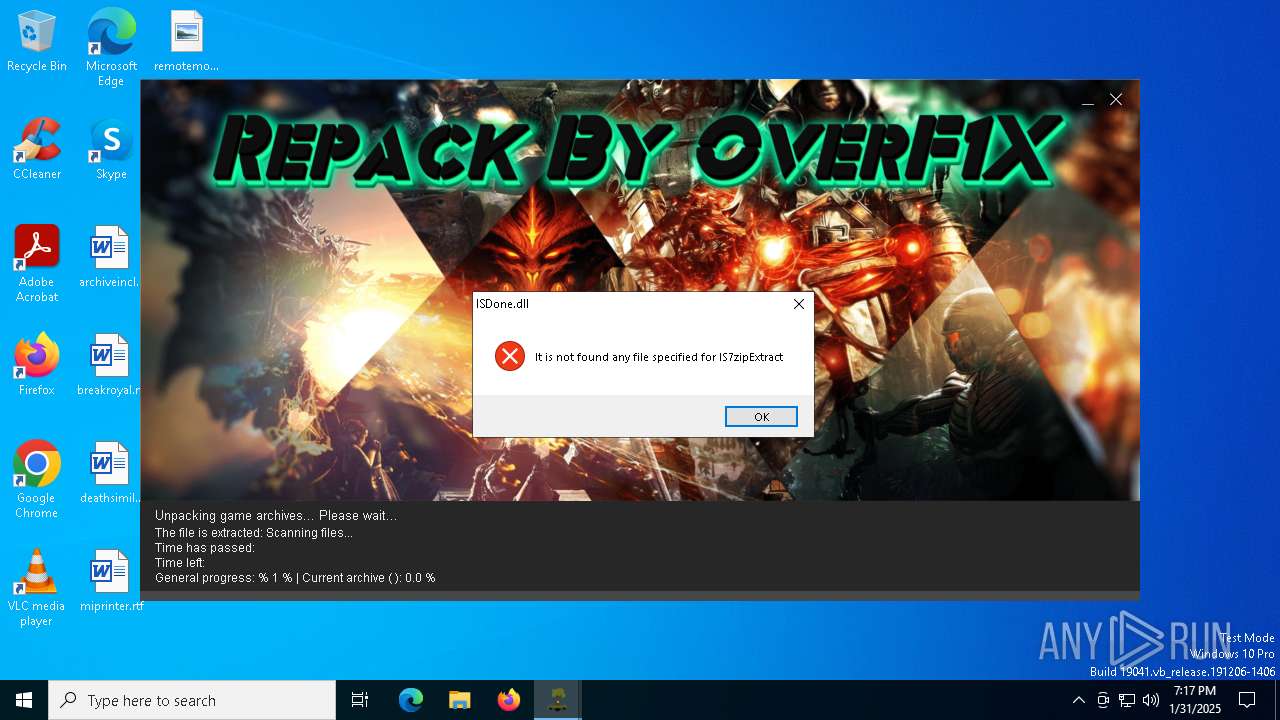
Executable content was dropped or overwritten
- install.exe (PID: 6340)
- install.tmp (PID: 6412)
- unins000.exe (PID: 7088)
- _iu14D2N.tmp (PID: 7108)
- install.exe (PID: 6508)
- install.tmp (PID: 5036)
- _iu14D2N.tmp (PID: 6592)
Reads the Windows owner or organization settings
- install.tmp (PID: 6412)
- install.tmp (PID: 5036)
- _iu14D2N.tmp (PID: 7108)
- _iu14D2N.tmp (PID: 6592)
Process drops legitimate windows executable
- install.tmp (PID: 6412)
- _iu14D2N.tmp (PID: 7108)
- install.tmp (PID: 5036)
- _iu14D2N.tmp (PID: 6592)
Starts itself from another location
- unins000.exe (PID: 7088)
- unins000.exe (PID: 6636)
Starts application with an unusual extension
- unins000.exe (PID: 7088)
- unins000.exe (PID: 6636)
INFO
Create files in a temporary directory
- install.exe (PID: 6340)
- install.tmp (PID: 6412)
- unins000.exe (PID: 7088)
- install.exe (PID: 6508)
- install.tmp (PID: 5036)
- _iu14D2N.tmp (PID: 7108)
- _iu14D2N.tmp (PID: 6592)
- unins000.exe (PID: 6636)
Checks supported languages
- install.exe (PID: 6340)
- install.tmp (PID: 6412)
- unins000.exe (PID: 7088)
- _iu14D2N.tmp (PID: 7108)
- install.tmp (PID: 5036)
- _iu14D2N.tmp (PID: 6592)
- unins000.exe (PID: 6636)
Reads the computer name
- install.tmp (PID: 6412)
- unins000.exe (PID: 7088)
- _iu14D2N.tmp (PID: 7108)
- install.tmp (PID: 5036)
- _iu14D2N.tmp (PID: 6592)
The sample compiled with russian language support
- install.tmp (PID: 6412)
- install.tmp (PID: 5036)
The sample compiled with english language support
- install.tmp (PID: 6412)
- _iu14D2N.tmp (PID: 7108)
- install.tmp (PID: 5036)
- _iu14D2N.tmp (PID: 6592)
Creates a software uninstall entry
- install.tmp (PID: 6412)
- install.tmp (PID: 5036)
Process checks computer location settings
- _iu14D2N.tmp (PID: 7108)
- _iu14D2N.tmp (PID: 6592)
Manual execution by a user
- install.exe (PID: 3840)
- install.exe (PID: 6508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (81.5) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10.5) |
| .exe | | | Win32 Executable (generic) (3.3) |
| .exe | | | Win16/32 Executable Delphi generic (1.5) |
| .exe | | | Generic Win/DOS Executable (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:07:26 13:09:48+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 86016 |
| InitializedDataSize: | 138240 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16478 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.20.3.0 |
| ProductVersionNumber: | 1.20.3.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
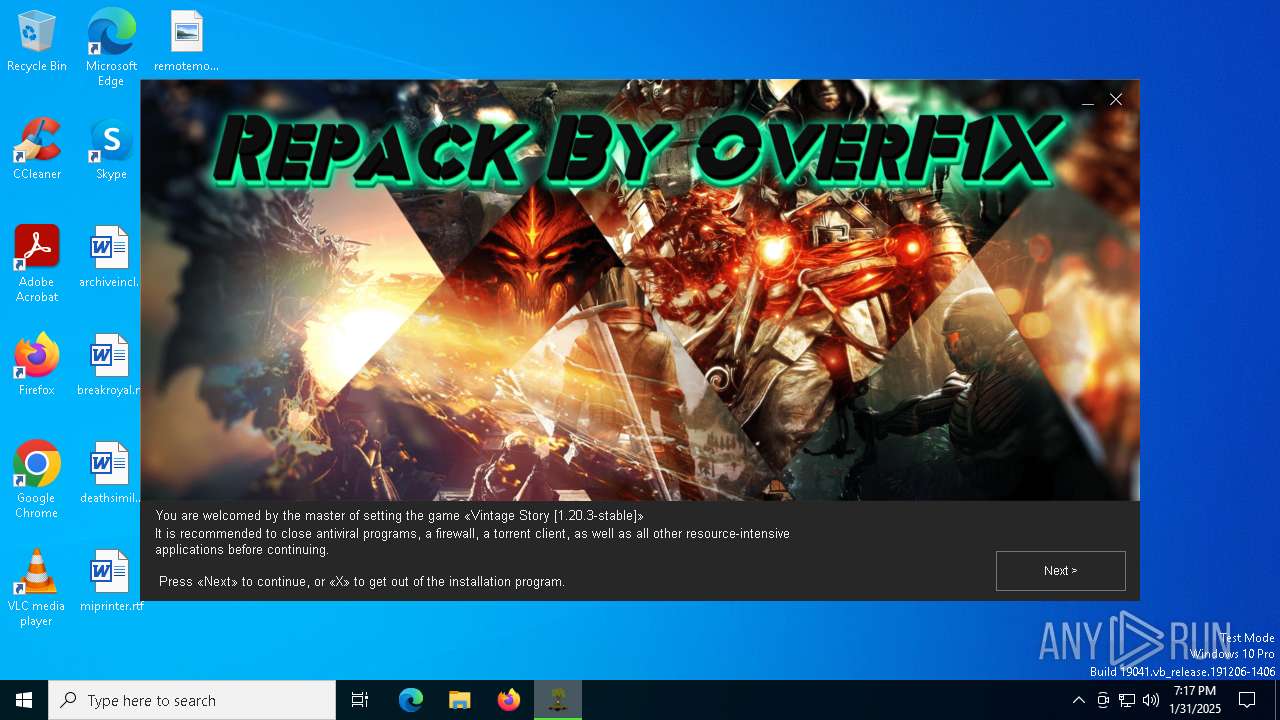
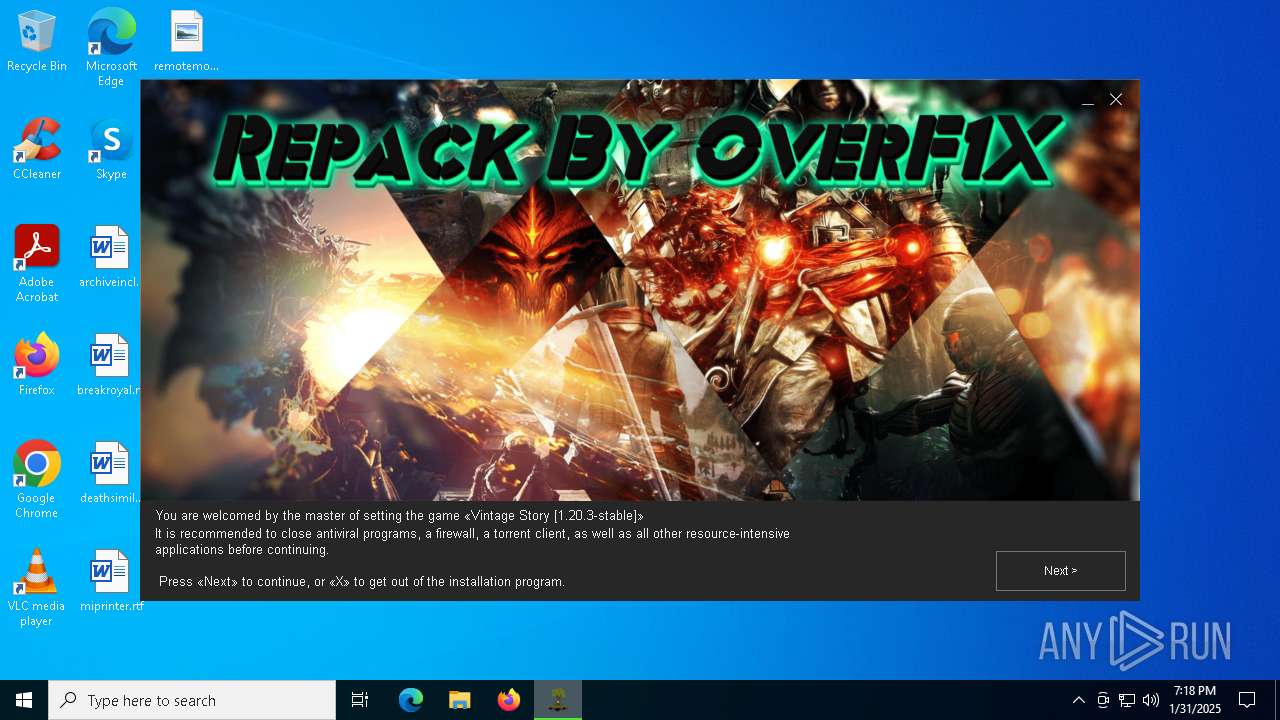
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | OverF1X |
| FileDescription: | Vintage Story 1.20.3.0 by OverF1X |
| FileVersion: | 1.20.3.0 |
| LegalCopyright: | © OverF1X |
| ProductName: | Vintage Story |
| ProductVersion: | 1.20.3.0 |
Total processes
142
Monitored processes
11
Malicious processes
2
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3664 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3732 | "C:\Users\admin\AppData\Local\Temp\install.exe" | C:\Users\admin\AppData\Local\Temp\install.exe | — | explorer.exe | |||||||||||
User: admin Company: OverF1X Integrity Level: MEDIUM Description: Vintage Story 1.20.3.0 by OverF1X Exit code: 3221226540 Version: 1.20.3.0 Modules
| |||||||||||||||
| 3840 | "C:\Users\admin\Desktop\install.exe" | C:\Users\admin\Desktop\install.exe | — | explorer.exe | |||||||||||
User: admin Company: OverF1X Integrity Level: MEDIUM Description: Vintage Story 1.20.3.0 by OverF1X Exit code: 3221226540 Version: 1.20.3.0 Modules
| |||||||||||||||
| 5036 | "C:\Users\admin\AppData\Local\Temp\is-A6FUF.tmp\install.tmp" /SL5="$80358,3600598,225280,C:\Users\admin\Desktop\install.exe" | C:\Users\admin\AppData\Local\Temp\is-A6FUF.tmp\install.tmp | install.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6340 | "C:\Users\admin\AppData\Local\Temp\install.exe" | C:\Users\admin\AppData\Local\Temp\install.exe | explorer.exe | ||||||||||||
User: admin Company: OverF1X Integrity Level: HIGH Description: Vintage Story 1.20.3.0 by OverF1X Exit code: 0 Version: 1.20.3.0 Modules
| |||||||||||||||
| 6412 | "C:\Users\admin\AppData\Local\Temp\is-CC62C.tmp\install.tmp" /SL5="$502F2,3600598,225280,C:\Users\admin\AppData\Local\Temp\install.exe" | C:\Users\admin\AppData\Local\Temp\is-CC62C.tmp\install.tmp | install.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6508 | "C:\Users\admin\Desktop\install.exe" | C:\Users\admin\Desktop\install.exe | explorer.exe | ||||||||||||
User: admin Company: OverF1X Integrity Level: HIGH Description: Vintage Story 1.20.3.0 by OverF1X Exit code: 0 Version: 1.20.3.0 Modules
| |||||||||||||||
| 6592 | "C:\Users\admin\AppData\Local\Temp\_iu14D2N.tmp" /SECONDPHASE="C:\Games\FPlay.SU\Vintage Story\Uninstall\unins000.exe" /FIRSTPHASEWND=$602D2 /SILENT | C:\Users\admin\AppData\Local\Temp\_iu14D2N.tmp | unins000.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6636 | "C:\Games\FPlay.SU\Vintage Story\Uninstall\unins000.exe" /SILENT | C:\Games\FPlay.SU\Vintage Story\Uninstall\unins000.exe | — | install.tmp | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 7088 | "C:\Games\FPlay.SU\Vintage Story\Uninstall\unins000.exe" /SILENT | C:\Games\FPlay.SU\Vintage Story\Uninstall\unins000.exe | install.tmp | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
990
Read events
944
Write events
36
Delete events
10
Modification events
| (PID) Process: | (7108) _iu14D2N.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{VINTAGES-TORY-0L6C-Z4W0-RPCBYOVERF1X}_is1 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7108) _iu14D2N.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\OverF1XRepack\Vintage Story |
| Operation: | delete value | Name: | Product GUID |
Value: {VINTAGES-TORY-0L6C-Z4W0-RPCBYOVERF1X} | |||
| (PID) Process: | (7108) _iu14D2N.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\OverF1XRepack\Vintage Story |
| Operation: | delete value | Name: | Install Dir |
Value: C:\Games\FPlay.SU\Vintage Story | |||
| (PID) Process: | (7108) _iu14D2N.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\OverF1XRepack\Vintage Story |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7108) _iu14D2N.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\OverF1XRepack |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7108) _iu14D2N.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Explorer\StartPage |
| Operation: | write | Name: | FavoritesRemovedChanges |
Value: 1 | |||
| (PID) Process: | (6412) install.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\OverF1XRepack\Vintage Story |
| Operation: | write | Name: | Install Dir |
Value: C:\Games\FPlay.SU\Vintage Story | |||
| (PID) Process: | (6412) install.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\OverF1XRepack\Vintage Story |
| Operation: | write | Name: | Product GUID |
Value: {VINTAGES-TORY-0L6C-Z4W0-RPCBYOVERF1X} | |||
| (PID) Process: | (6412) install.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{VINTAGES-TORY-0L6C-Z4W0-RPCBYOVERF1X}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.5.1.ee1 (u) | |||
| (PID) Process: | (6412) install.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{VINTAGES-TORY-0L6C-Z4W0-RPCBYOVERF1X}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Games\FPlay.SU\Vintage Story | |||
Executable files
41
Suspicious files
7
Text files
22
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6412 | install.tmp | C:\Users\admin\AppData\Local\Temp\is-OL485.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 6340 | install.exe | C:\Users\admin\AppData\Local\Temp\is-CC62C.tmp\install.tmp | executable | |
MD5:BA317844C8E8D573730038ED55A9AF23 | SHA256:751467D1CCDA971BDDC049D925EBFC94E18829C785C7142DDC049E2417852D7D | |||
| 6412 | install.tmp | C:\Users\admin\AppData\Local\Temp\is-OL485.tmp\_isetup\_setup64.tmp | executable | |
MD5:4FF75F505FDDCC6A9AE62216446205D9 | SHA256:A4C86FC4836AC728D7BD96E7915090FD59521A9E74F1D06EF8E5A47C8695FD81 | |||
| 6412 | install.tmp | C:\Users\admin\AppData\Local\Temp\is-OL485.tmp\Botva2.dll | executable | |
MD5:67965A5957A61867D661F05AE1F4773E | SHA256:450B9B0BA25BF068AFBC2B23D252585A19E282939BF38326384EA9112DFD0105 | |||
| 6412 | install.tmp | C:\Users\admin\AppData\Local\Temp\is-OL485.tmp\facompress.dll | executable | |
MD5:D43845F28651A42BA2105FCFCCA5253F | SHA256:17A9FFDF381F7A9F6CDFC85B157FC6CF80CD4B45ED8AD43EDAC73008923501A0 | |||
| 6412 | install.tmp | C:\Users\admin\AppData\Local\Temp\is-OL485.tmp\ISGSG.dll | executable | |
MD5:09974EAFF6DEFADDE38B1328754DBE09 | SHA256:9EEEF28D82FC4DB7D1269DFBC0EA282768CE5E2E4E4BDC867D80D6847468DCA7 | |||
| 6412 | install.tmp | C:\Users\admin\AppData\Local\Temp\is-OL485.tmp\Splash-1.png | image | |
MD5:66D1AC6C9609918A1215CB39E0EC99D2 | SHA256:351D32DDABAFBF86B12534D96162654B60447B5DA332046A2A46C37847297573 | |||
| 6412 | install.tmp | C:\Users\admin\AppData\Local\Temp\is-OL485.tmp\B2P.dll | executable | |
MD5:9B836FC10A6106483F246B2EC16A1ED4 | SHA256:FBA4940069190967698745562F3B0D5D5F9CE17109EE314336BA8C4F2151E3E3 | |||
| 6412 | install.tmp | C:\Users\admin\AppData\Local\Temp\is-OL485.tmp\unarc.dll | executable | |
MD5:890274AC337E16B51B0CD25A2FB37586 | SHA256:A363A14CF3D1416661BDEC2E084B3DE31DB1497E4A97E2DC91C0DEC193E42A3F | |||
| 6412 | install.tmp | C:\Users\admin\AppData\Local\Temp\is-OL485.tmp\cls-srep.dll | executable | |
MD5:9E1E200472D66356A4AE5D597B01DABC | SHA256:87DF573AC240E09EA4941E169FB2D15D5316A1B0E053446B8144E04B1154F061 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
28
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6096 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5464 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5464 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.21.65.132:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
5064 | SearchApp.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6096 | backgroundTaskHost.exe | 20.223.36.55:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |