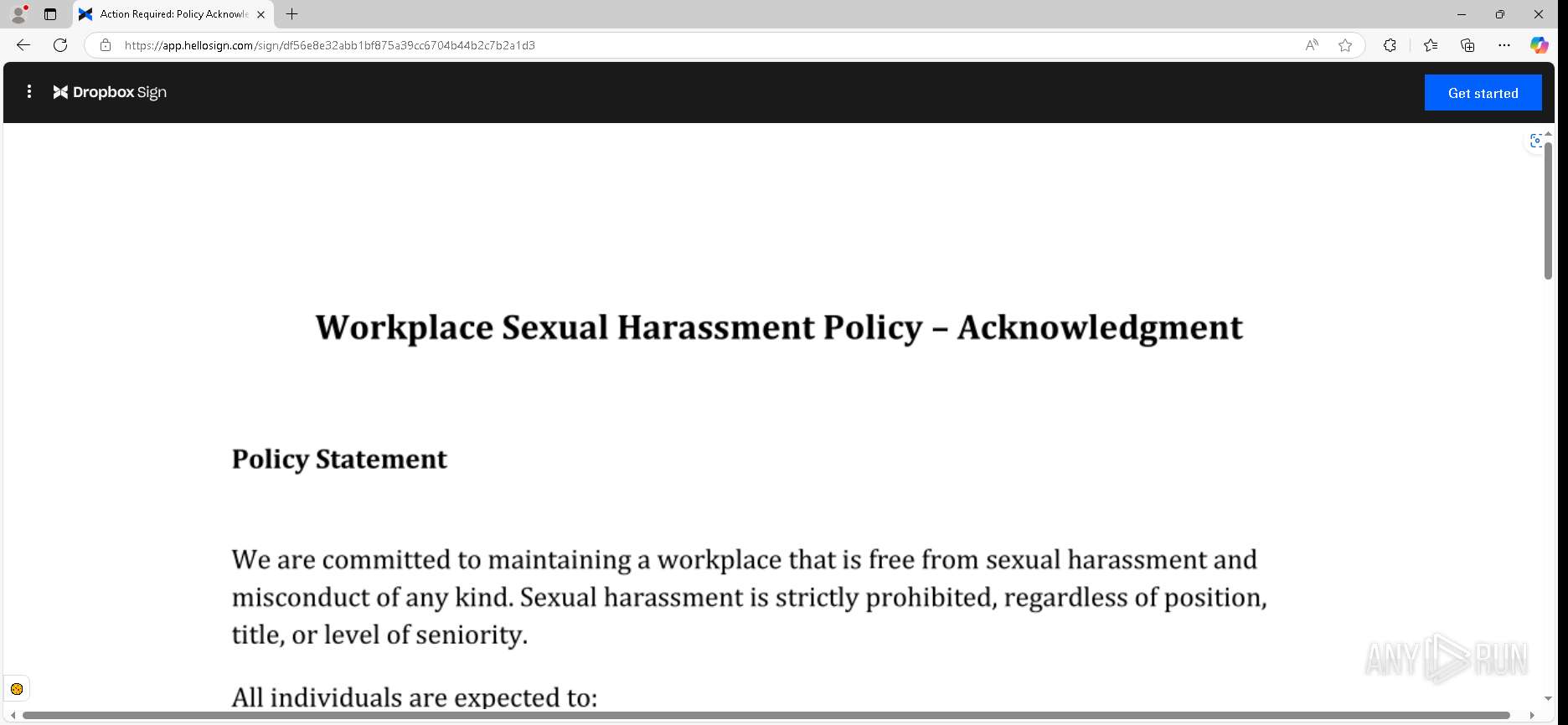
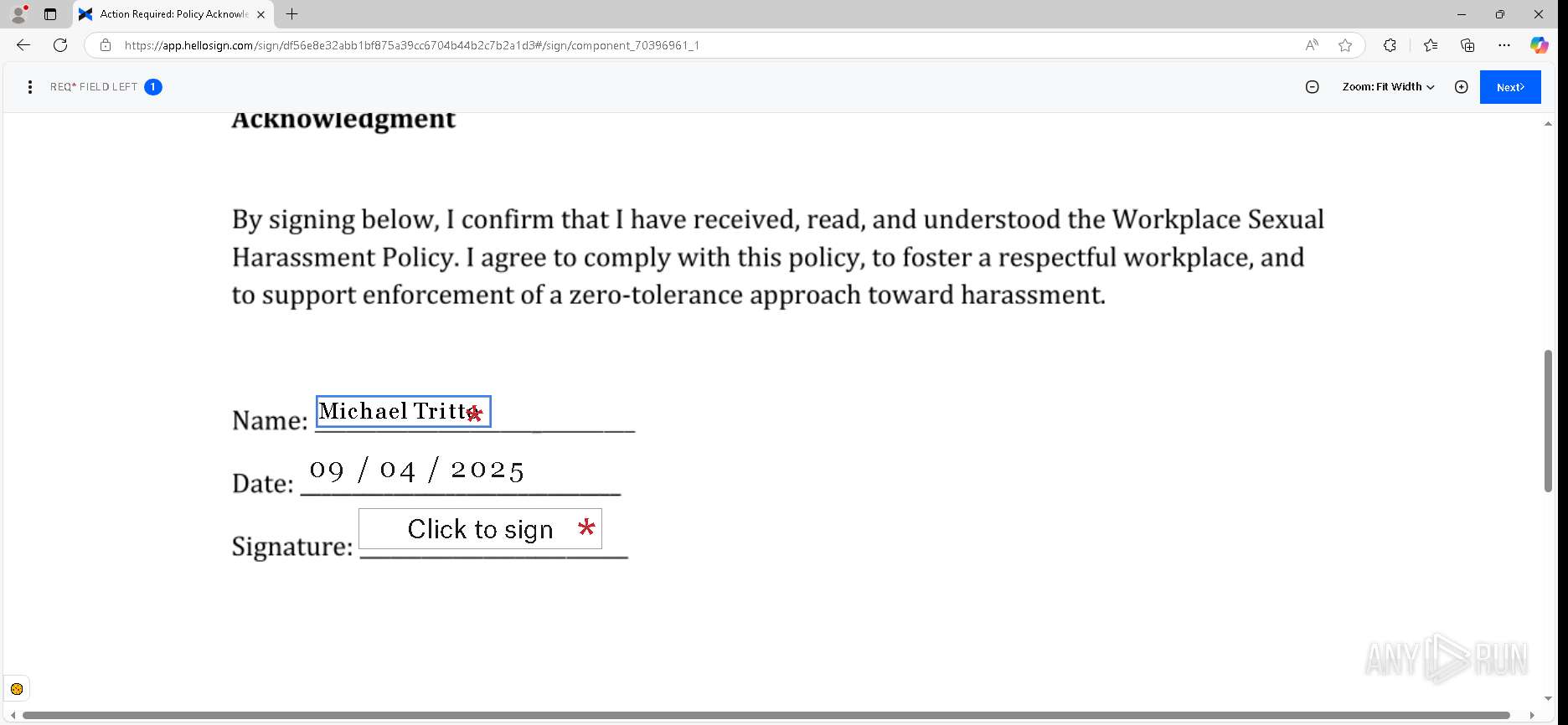
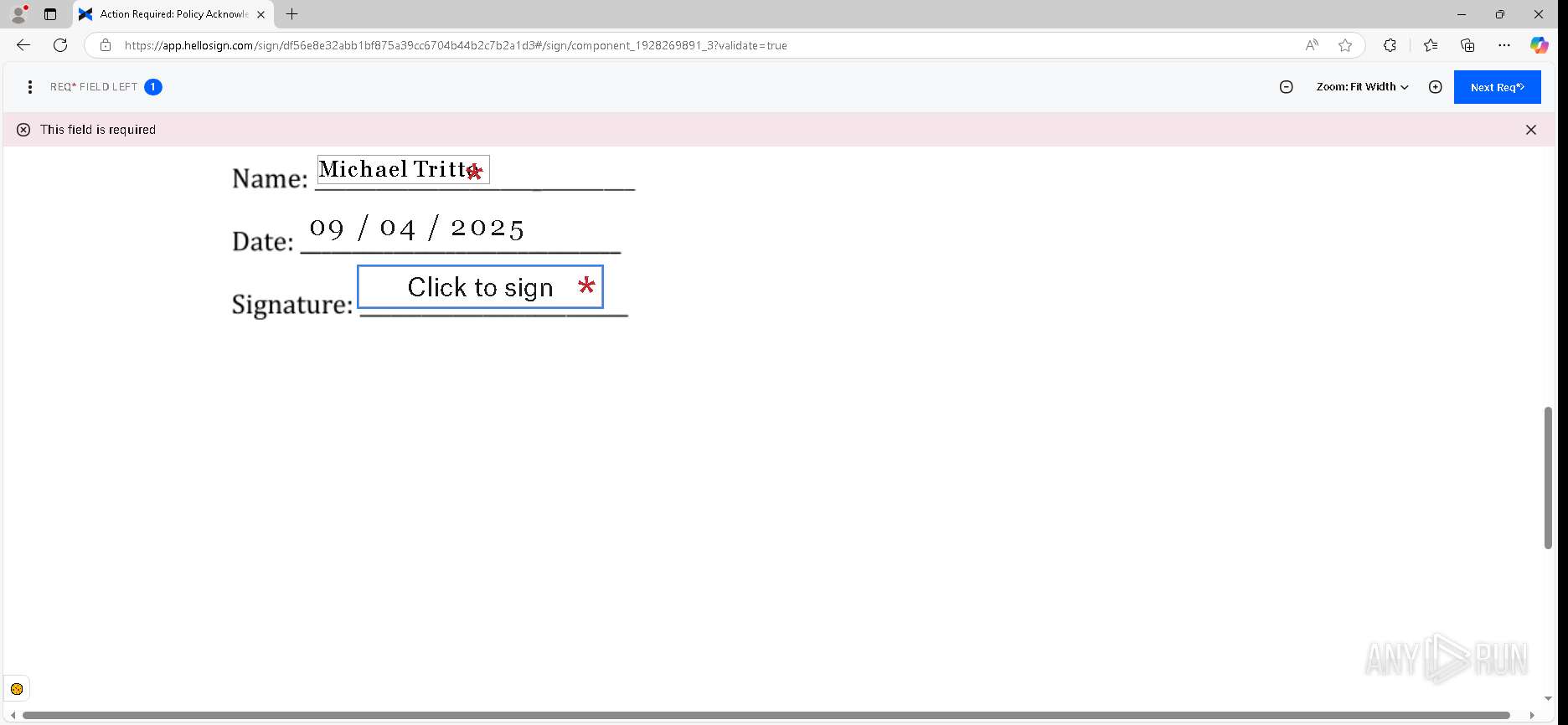
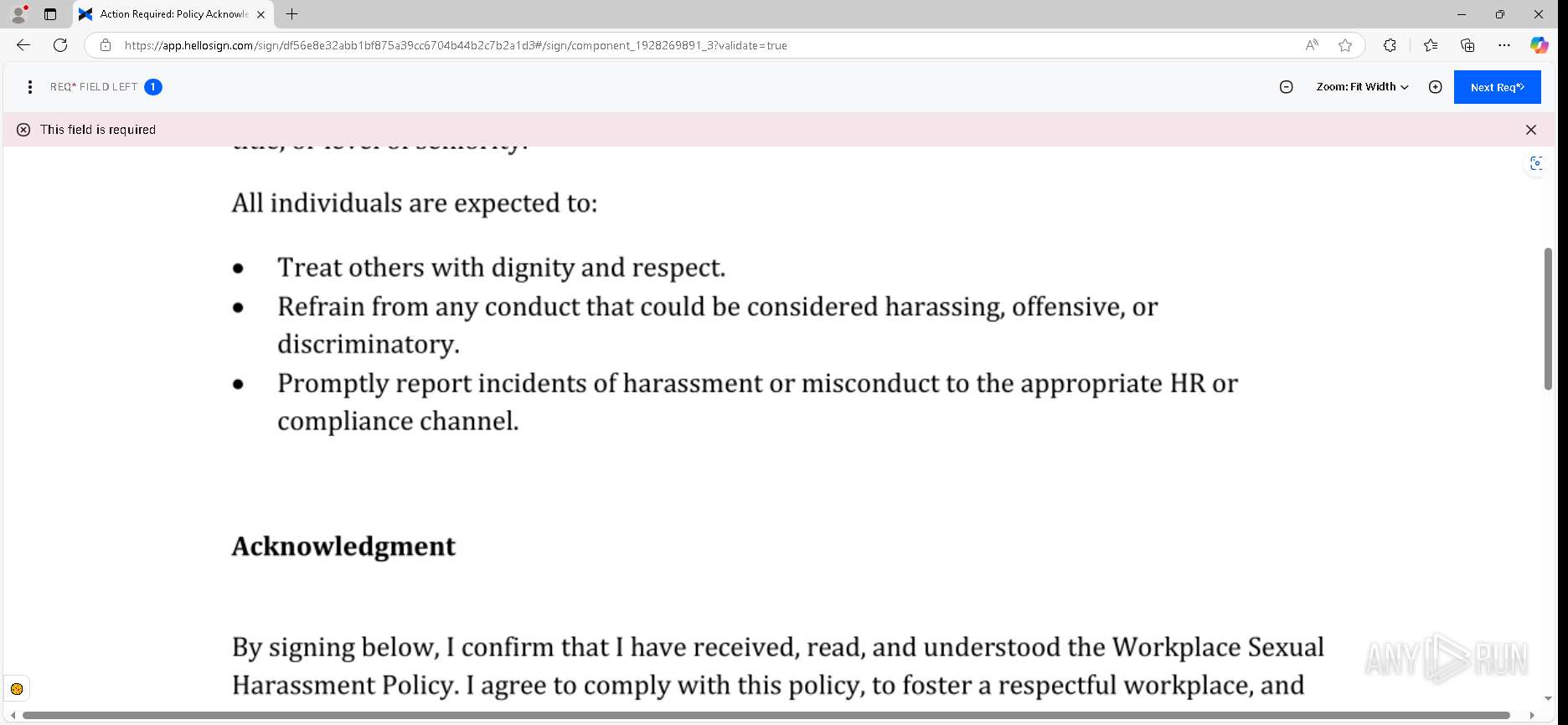
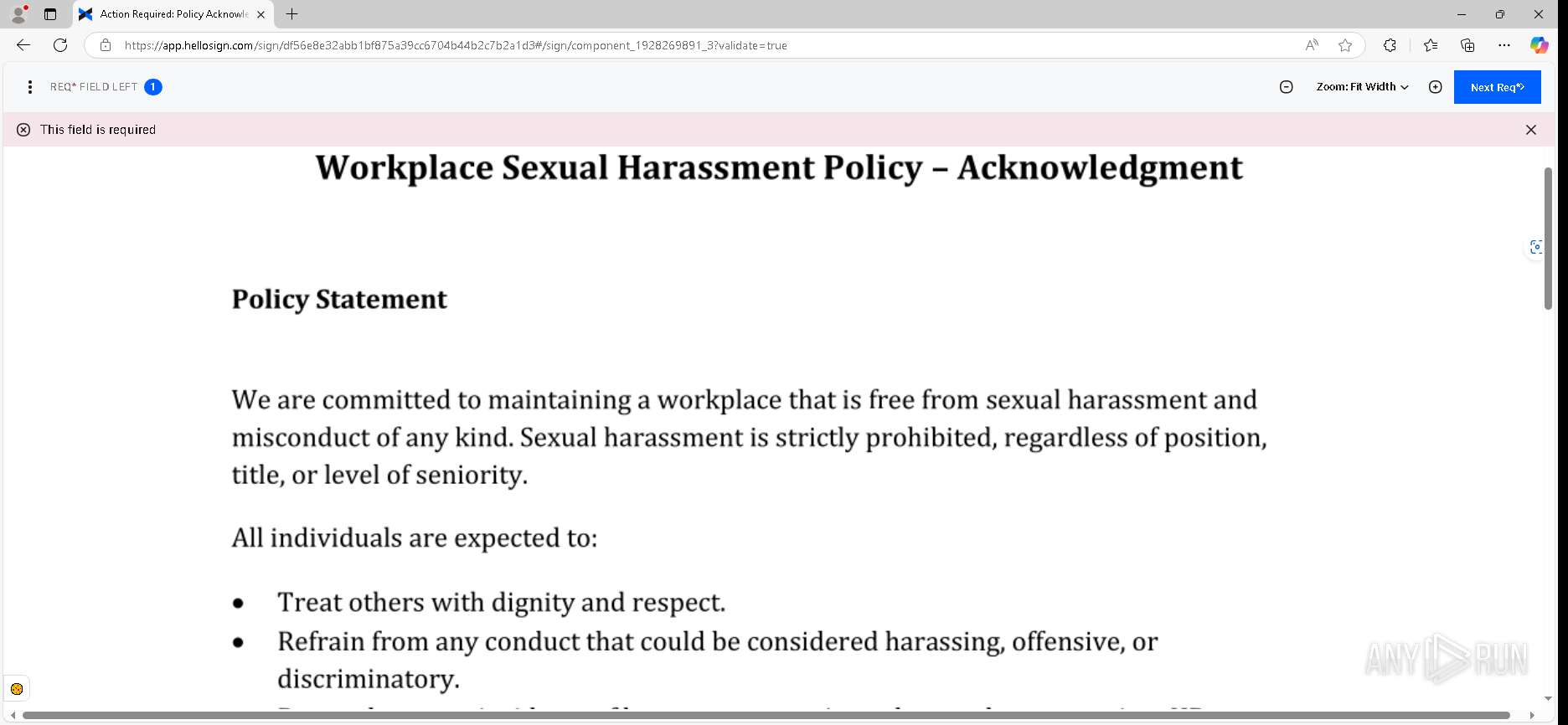
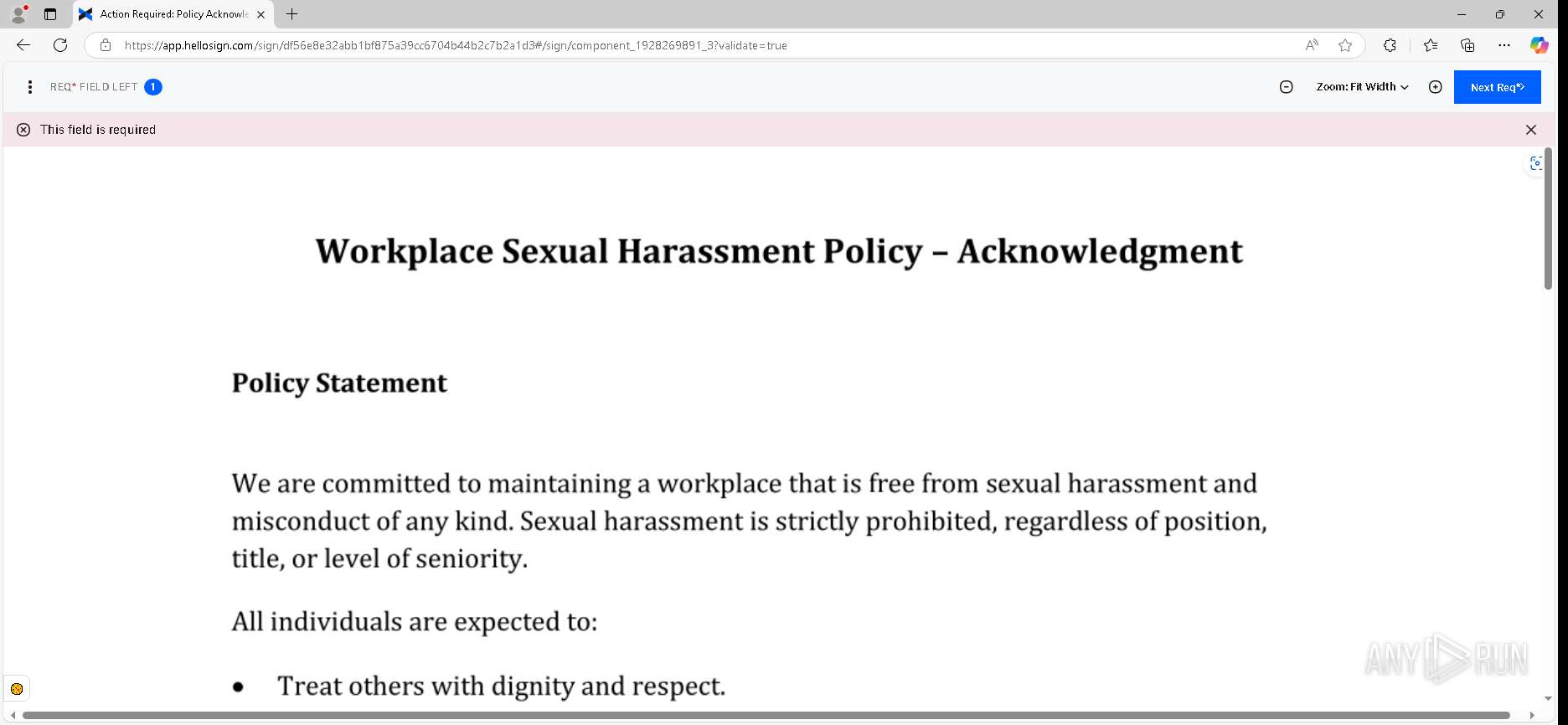
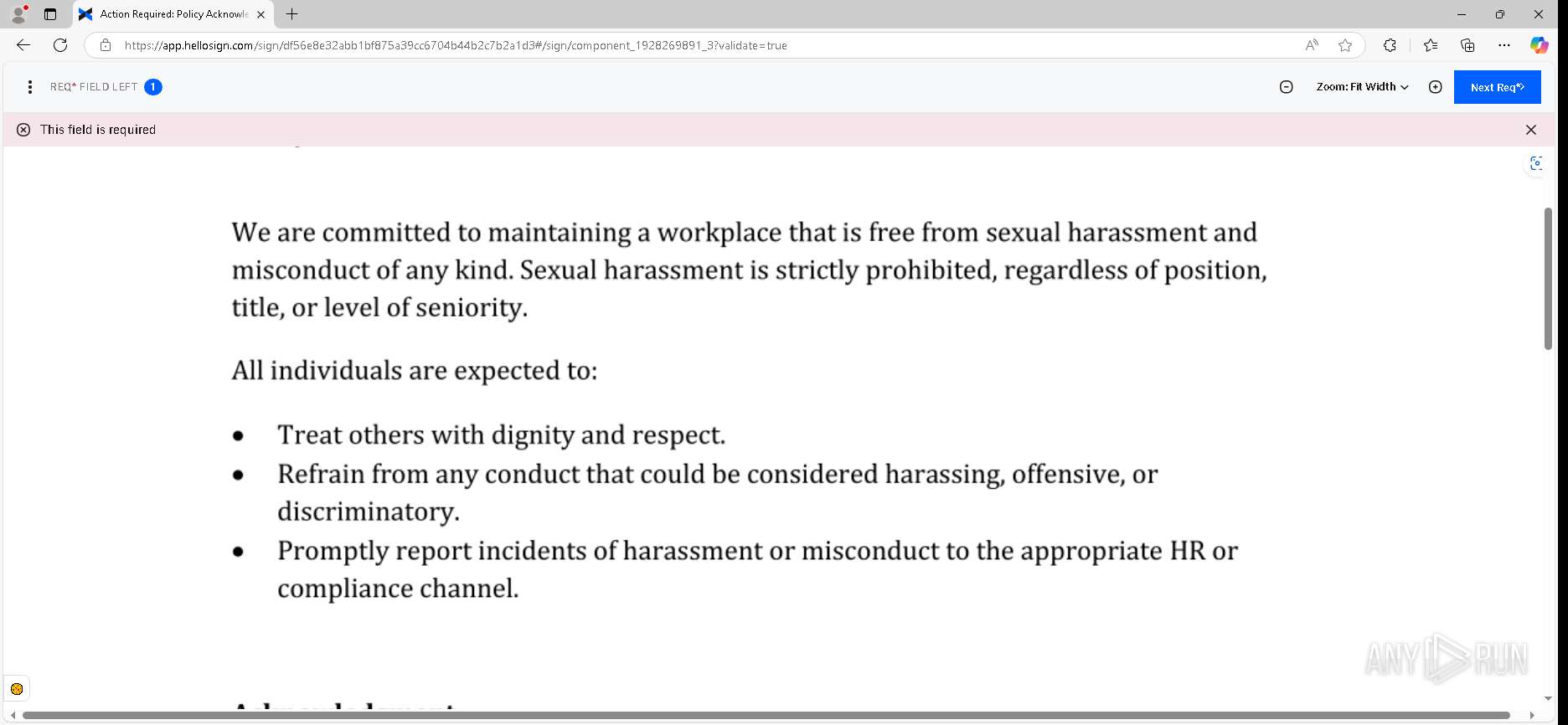
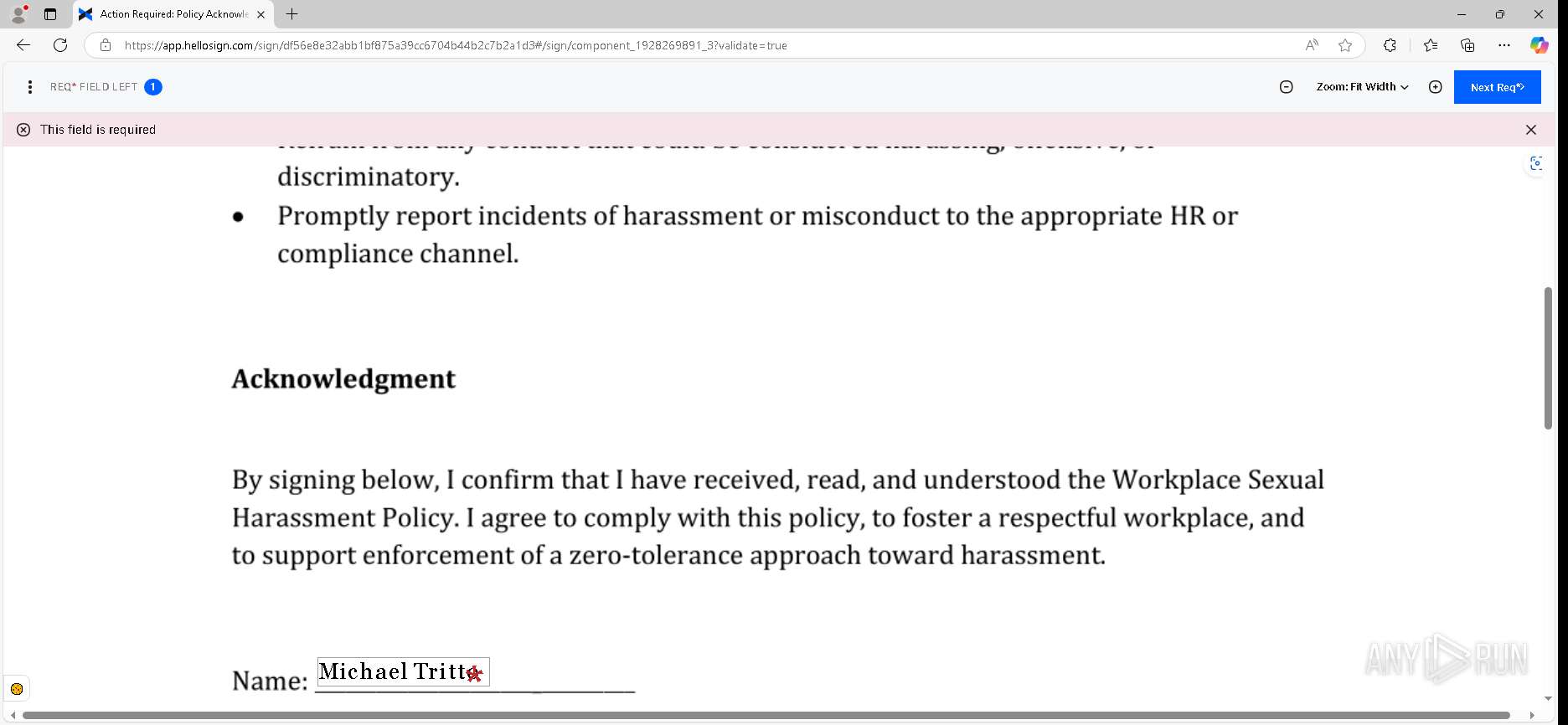
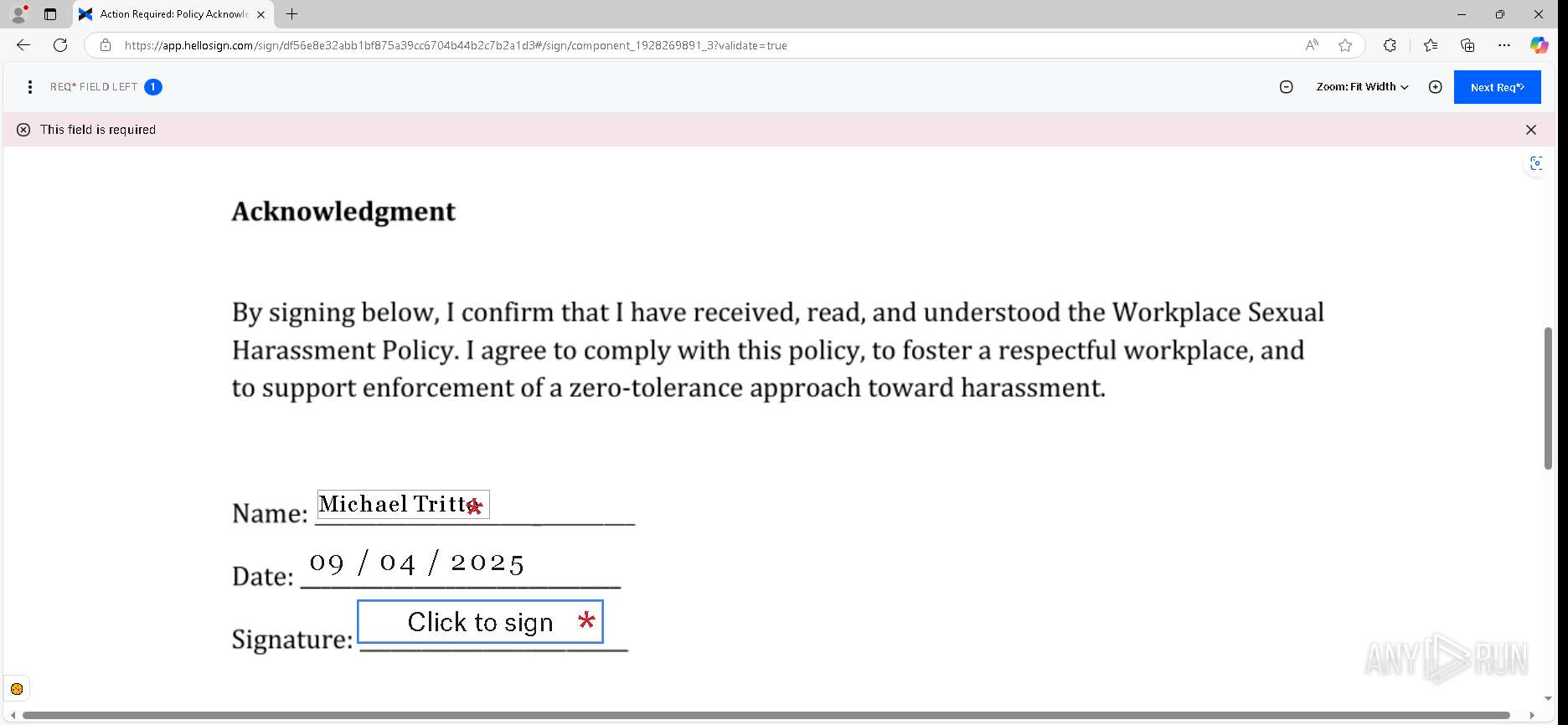
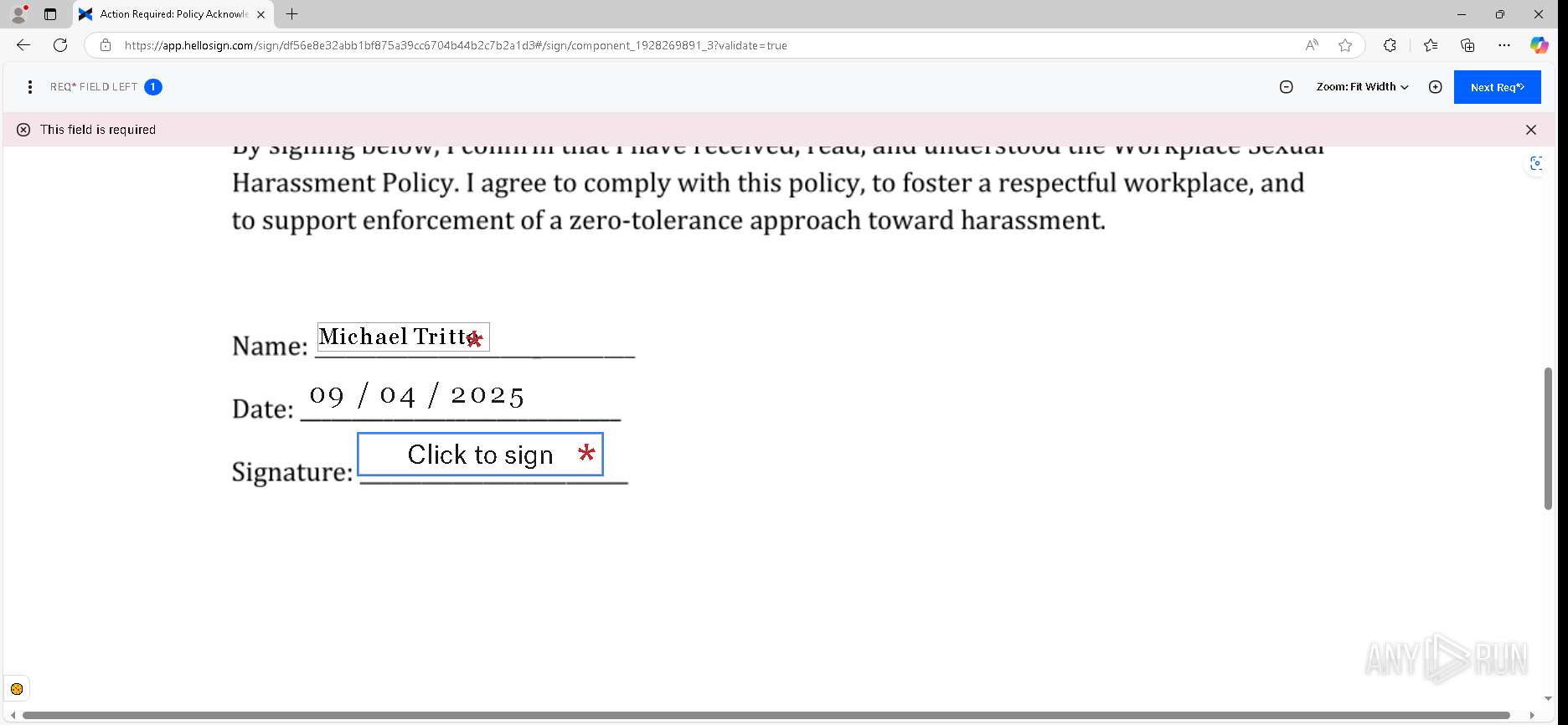
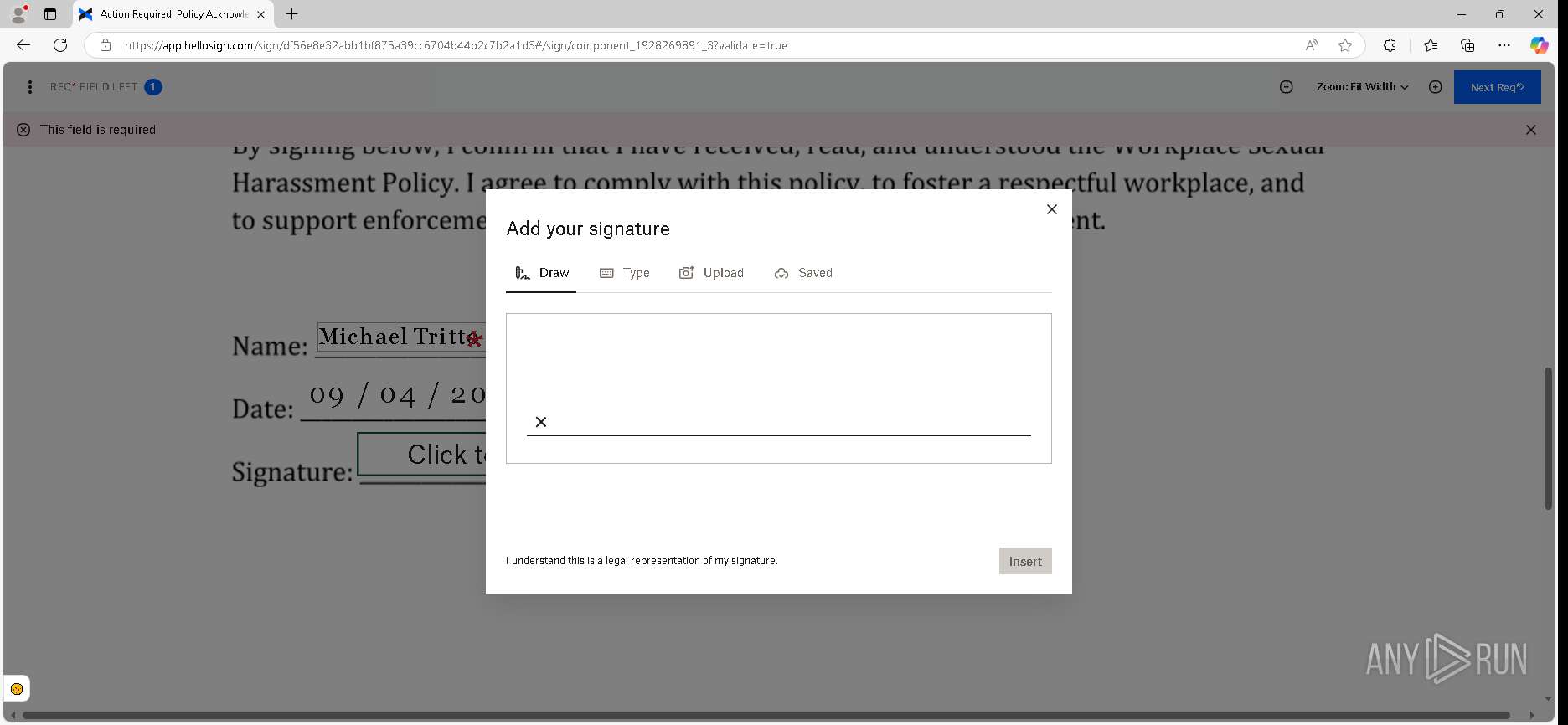
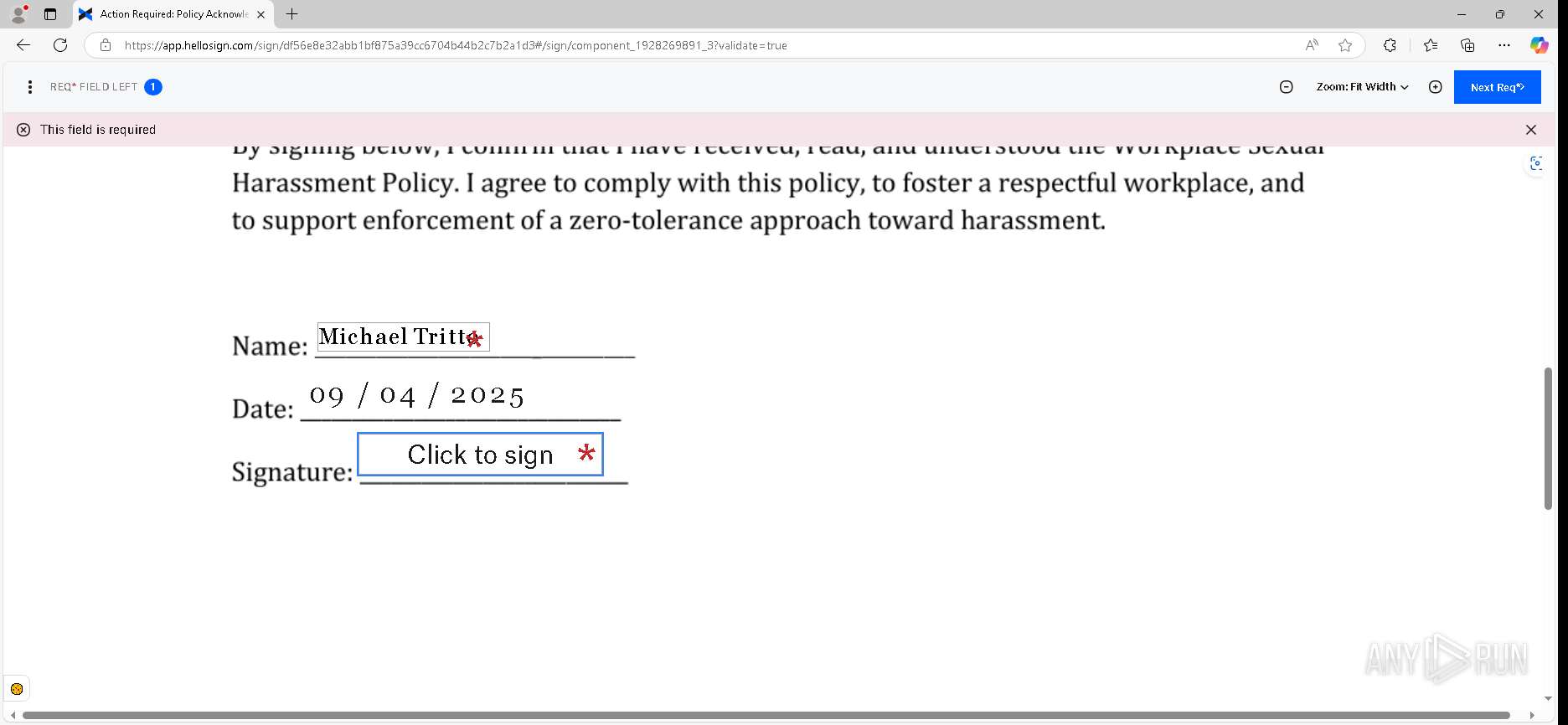
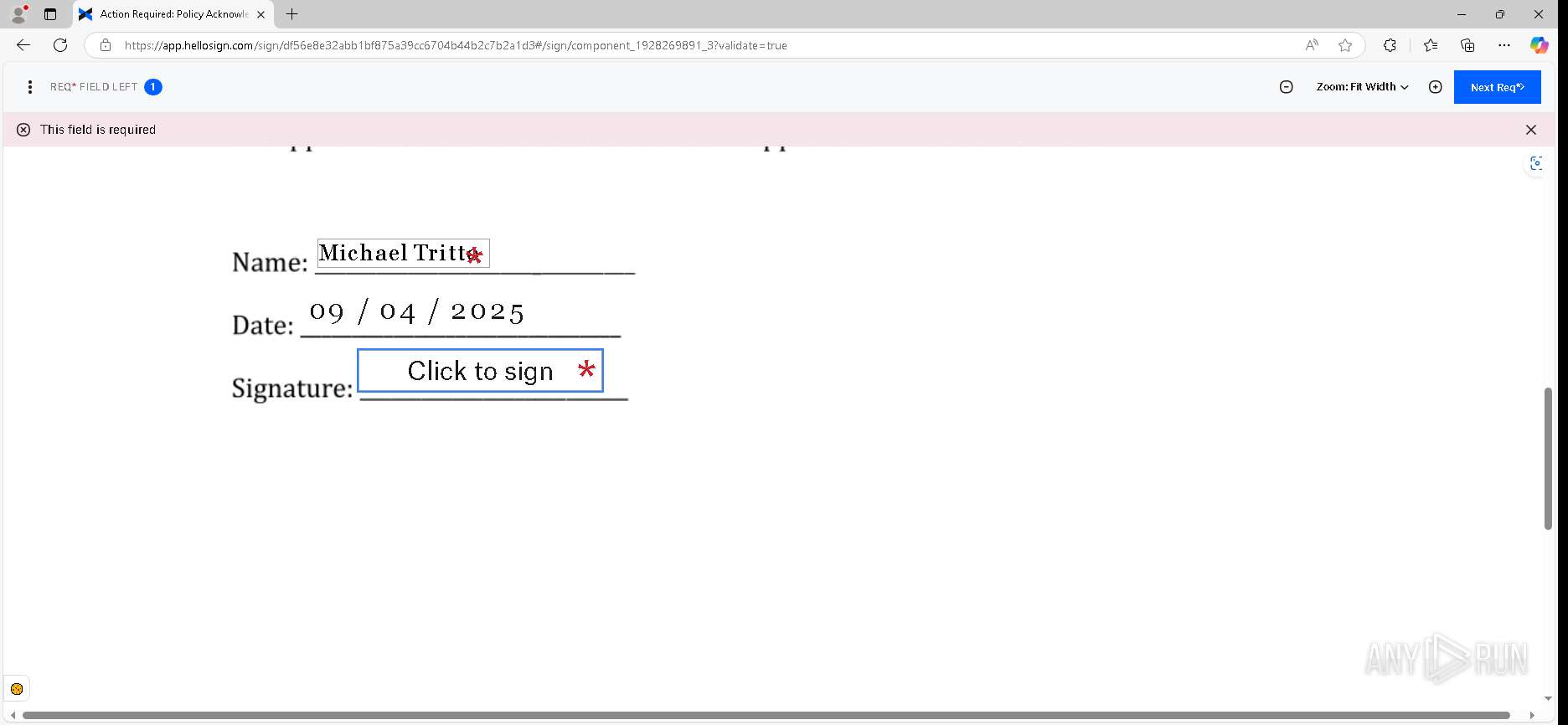
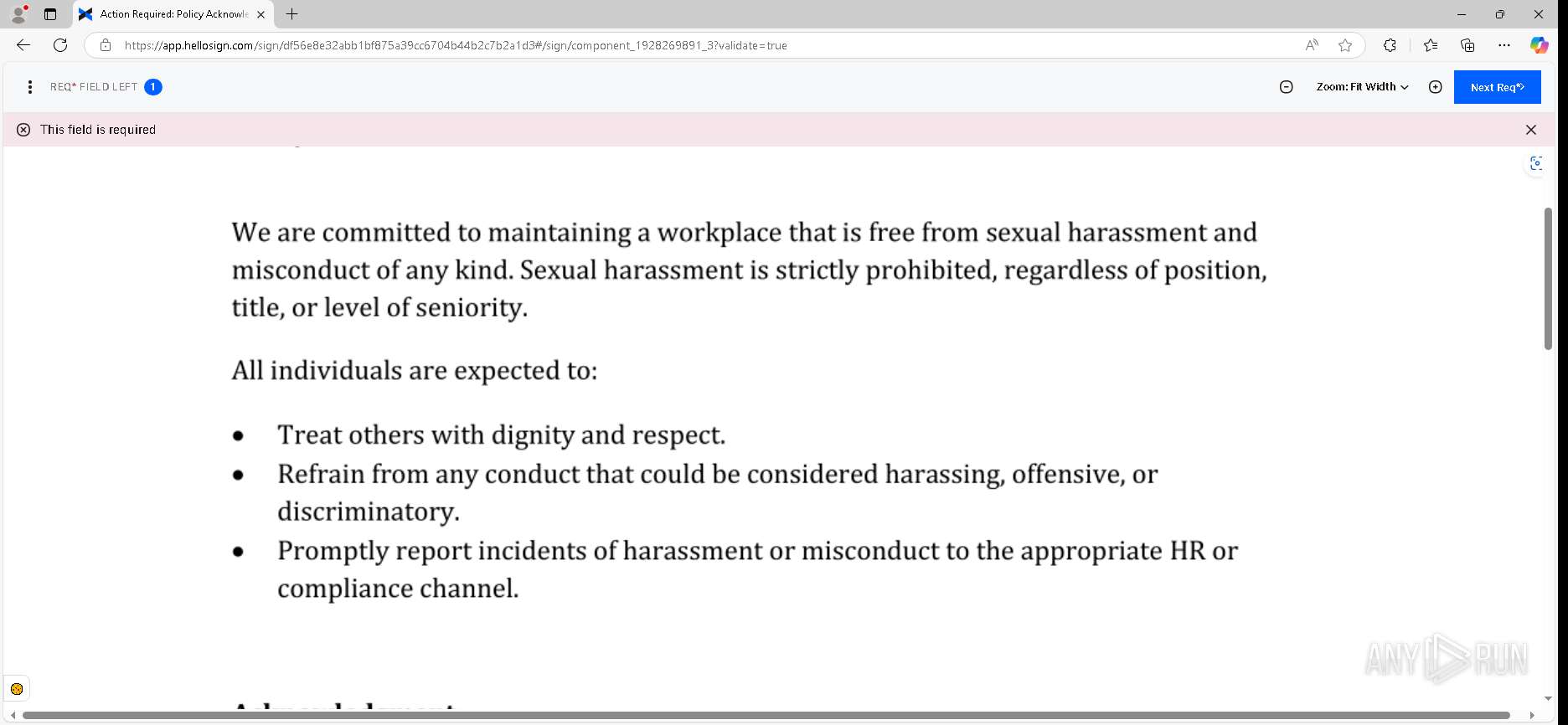
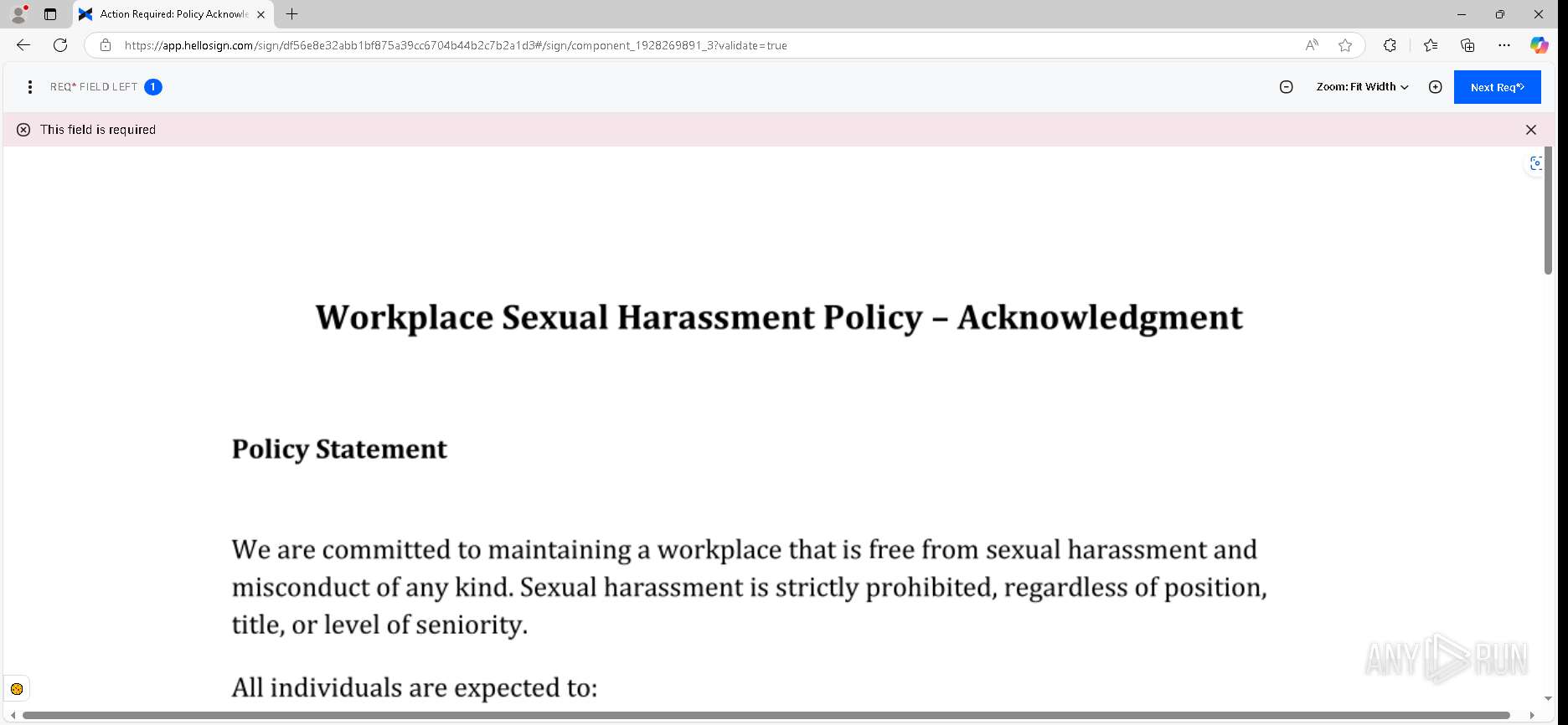
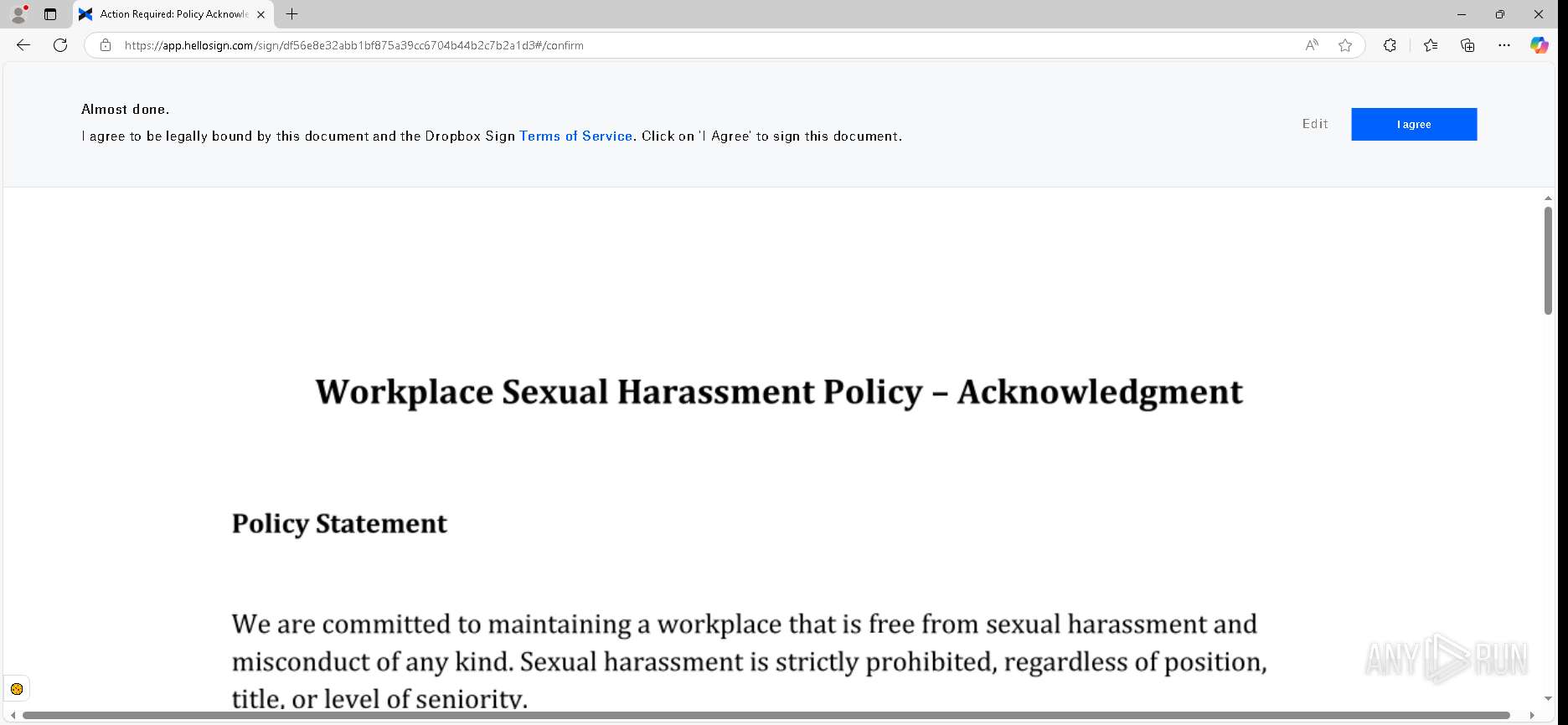
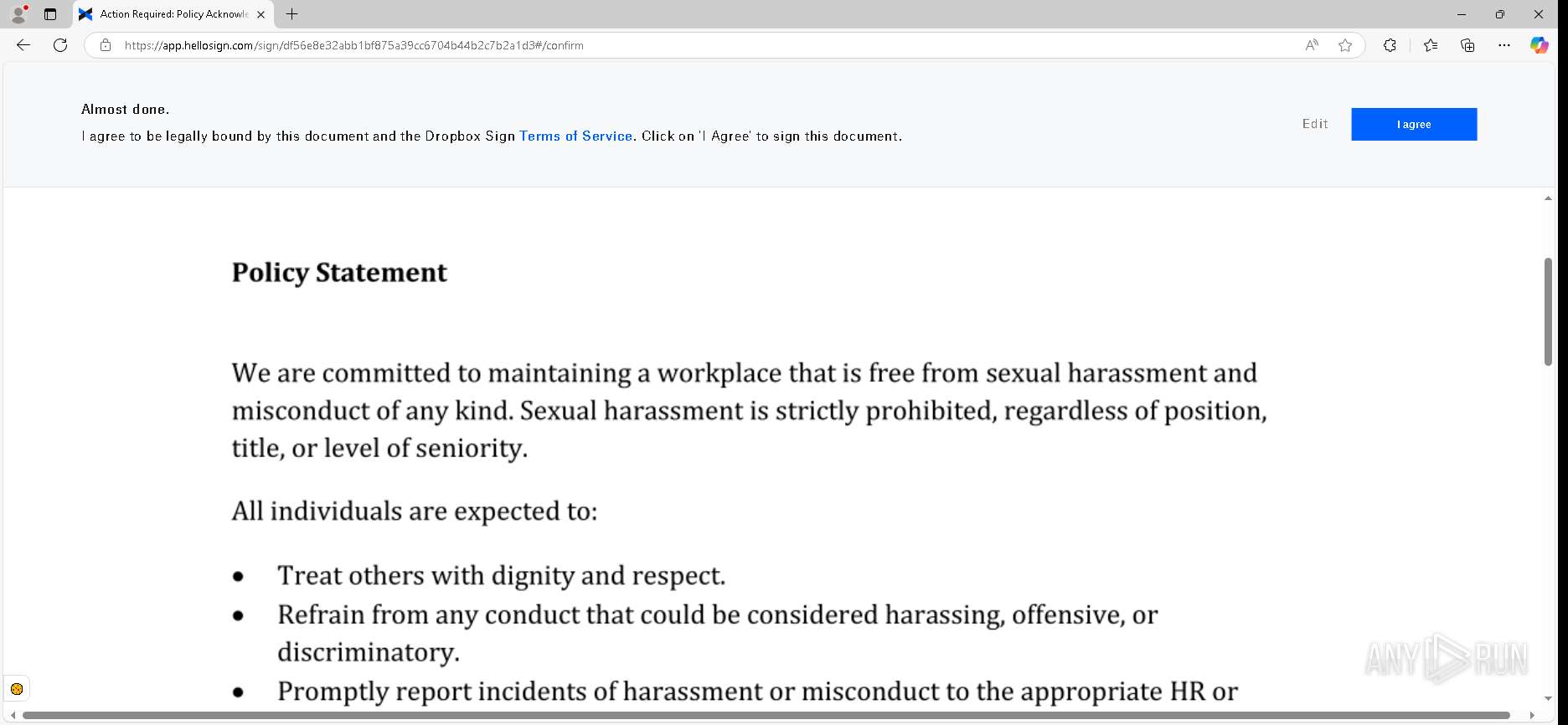
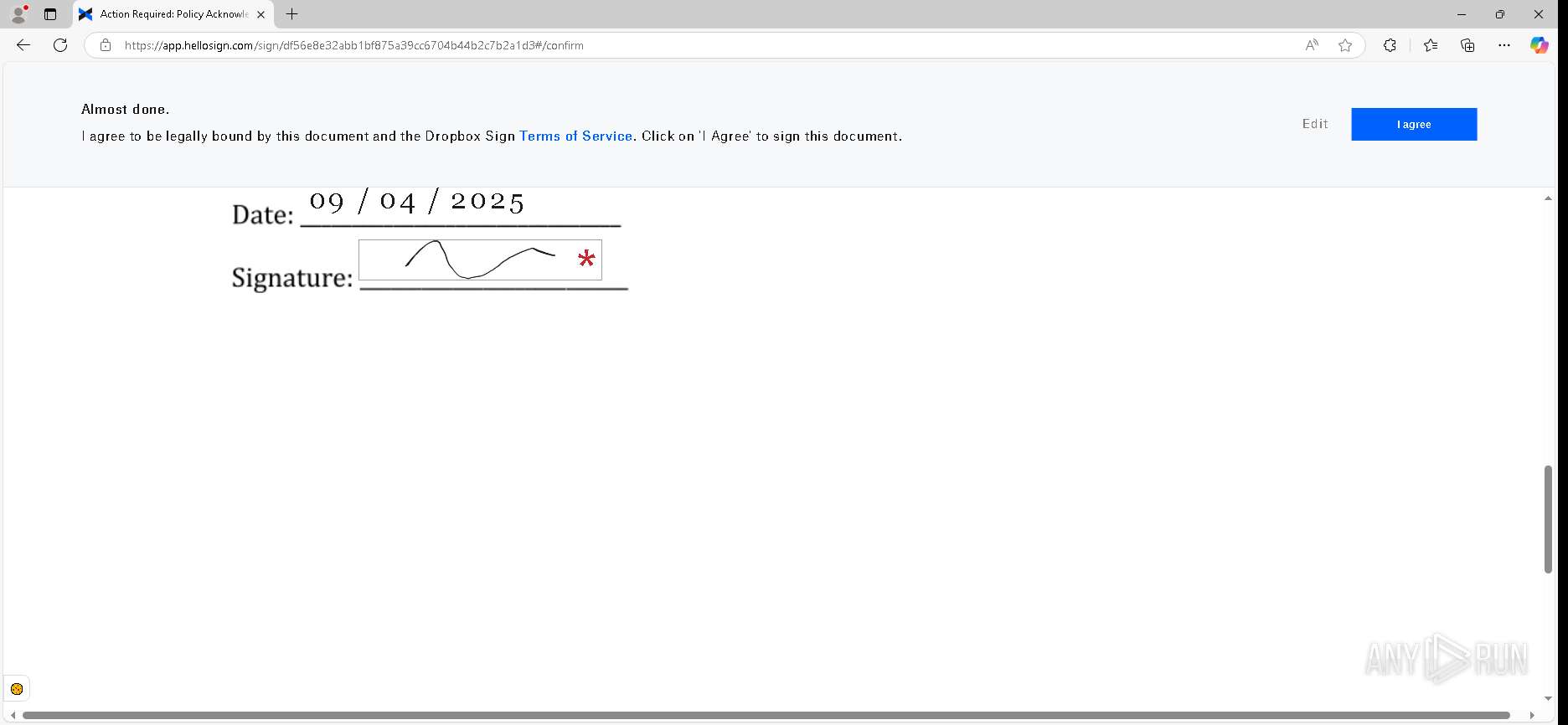
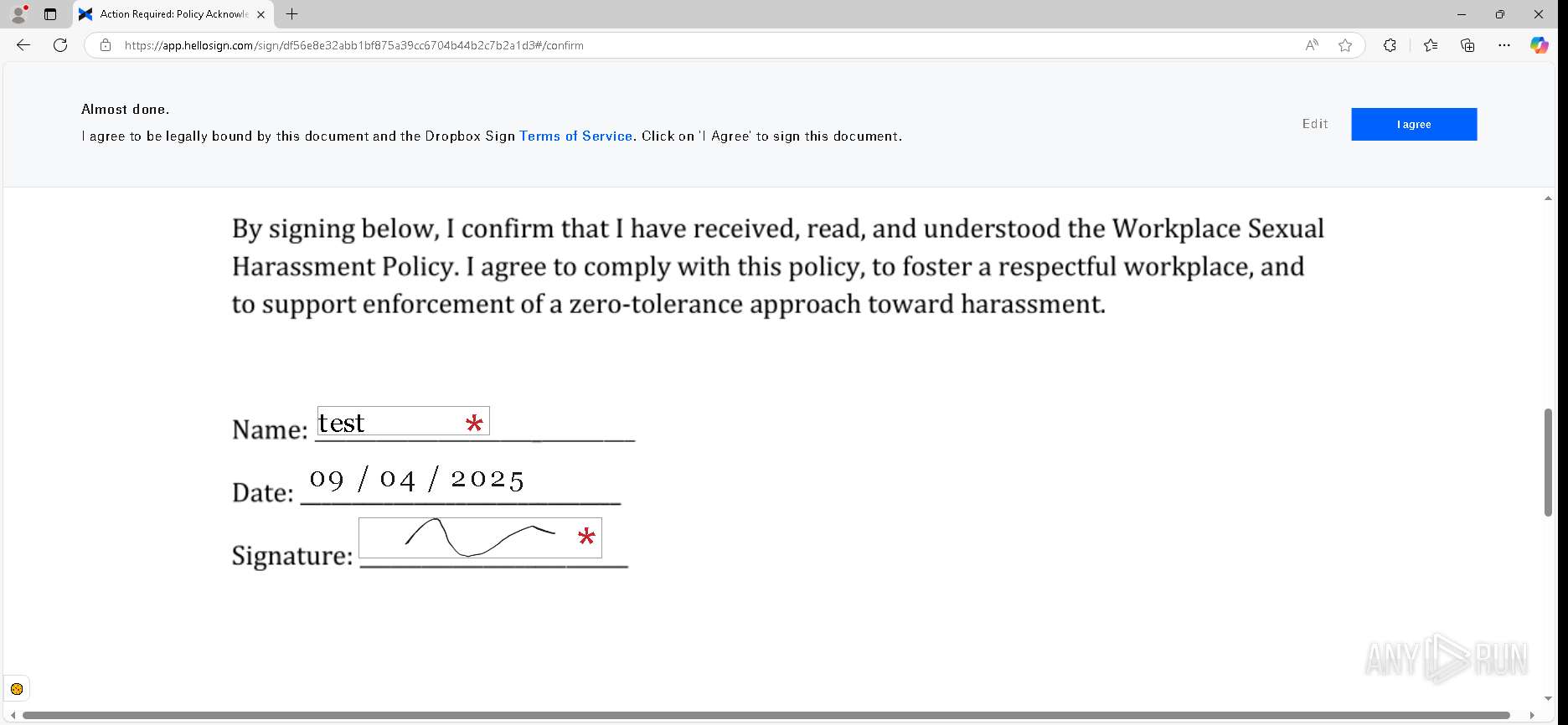
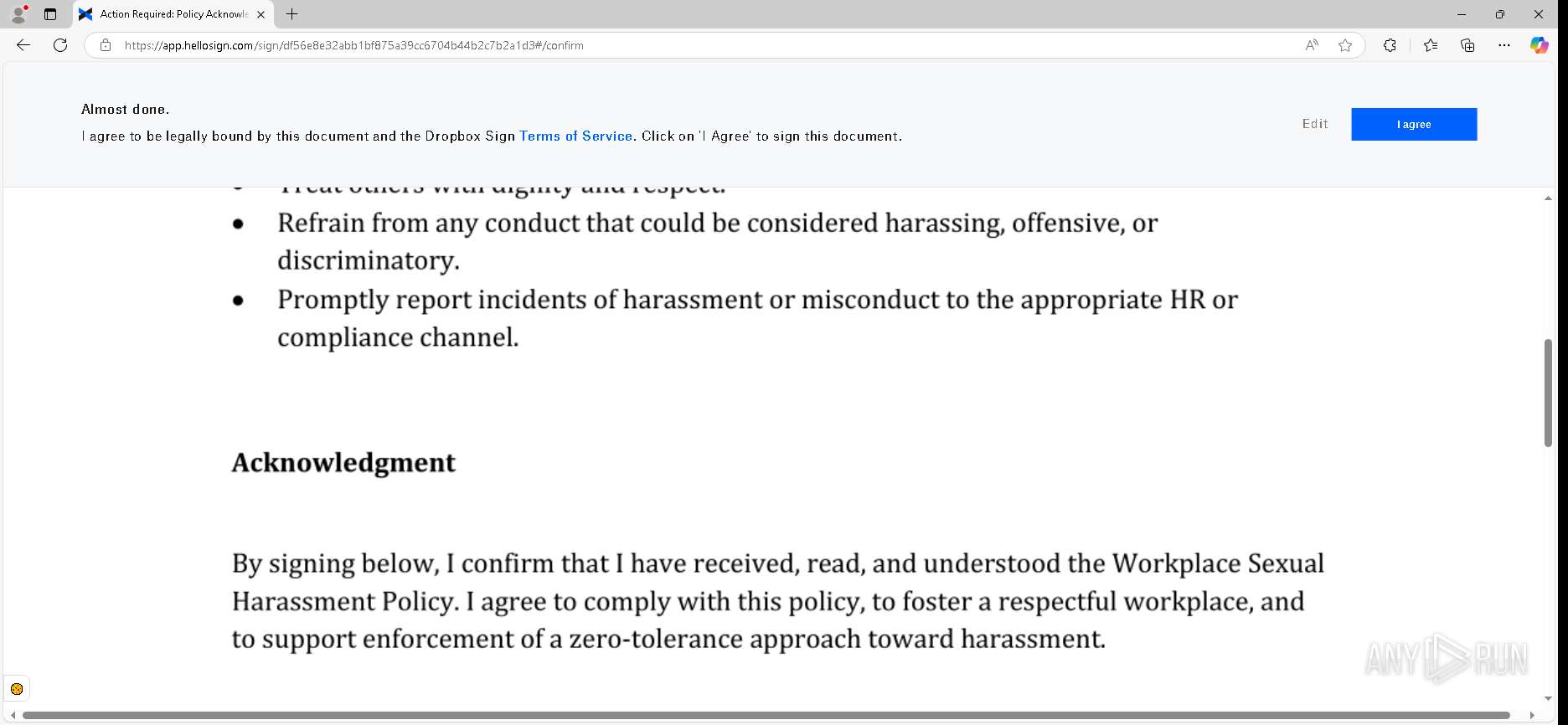
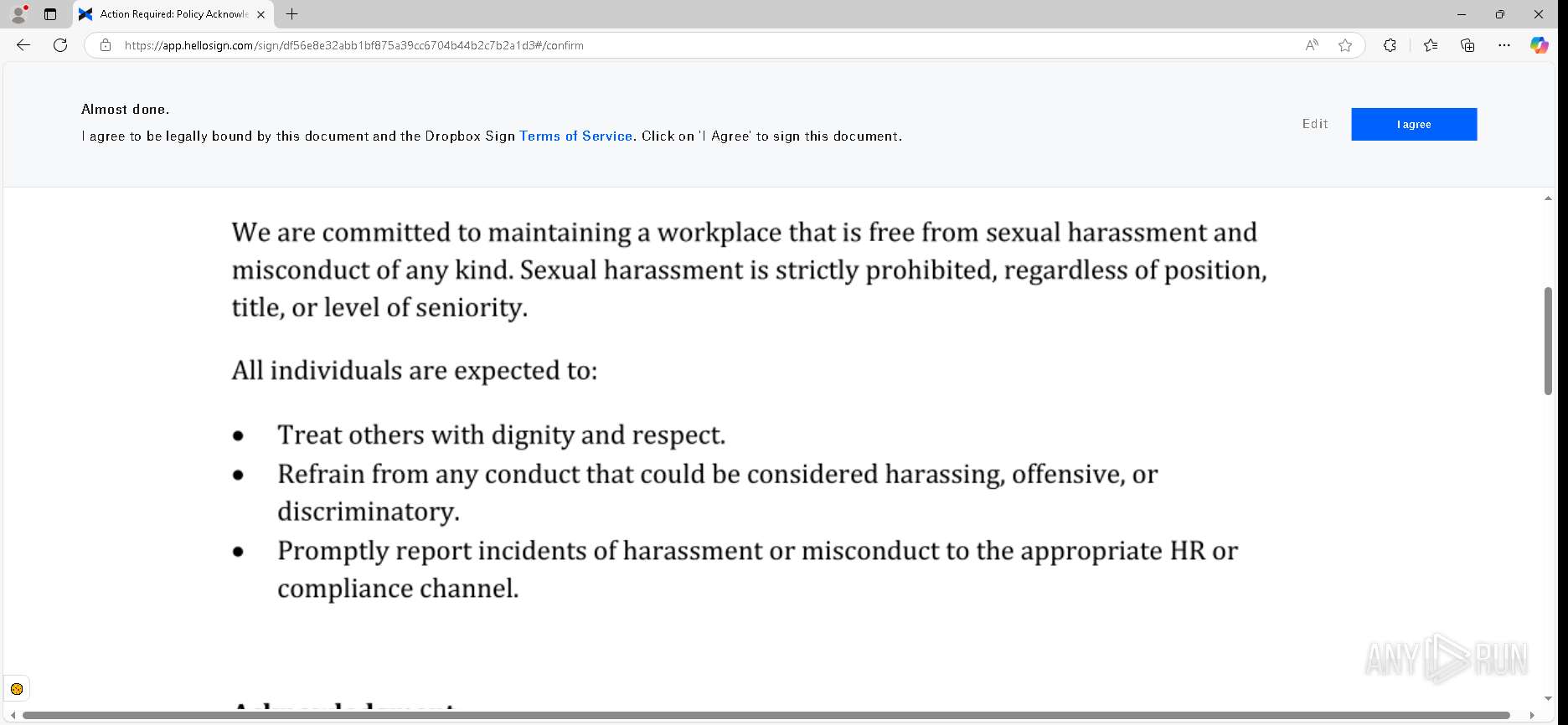
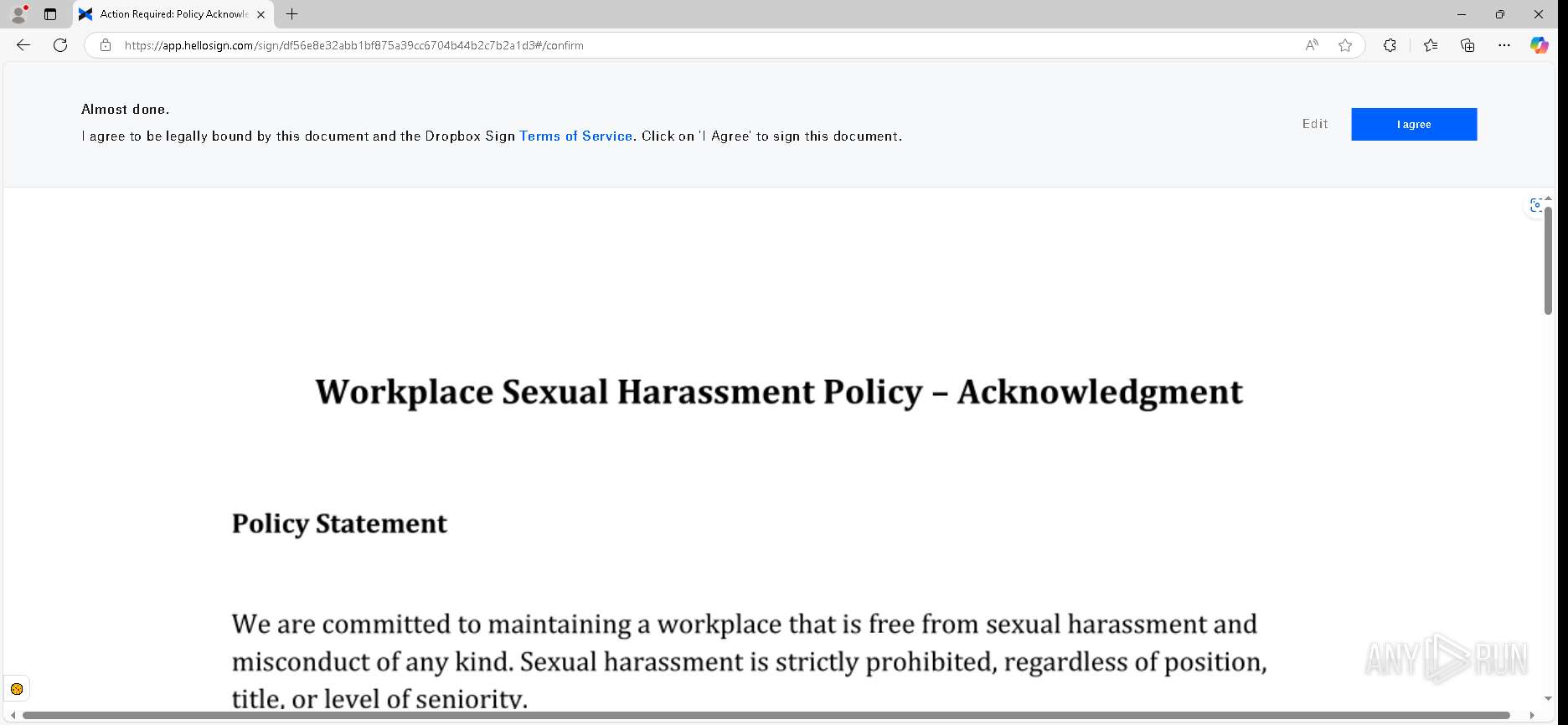
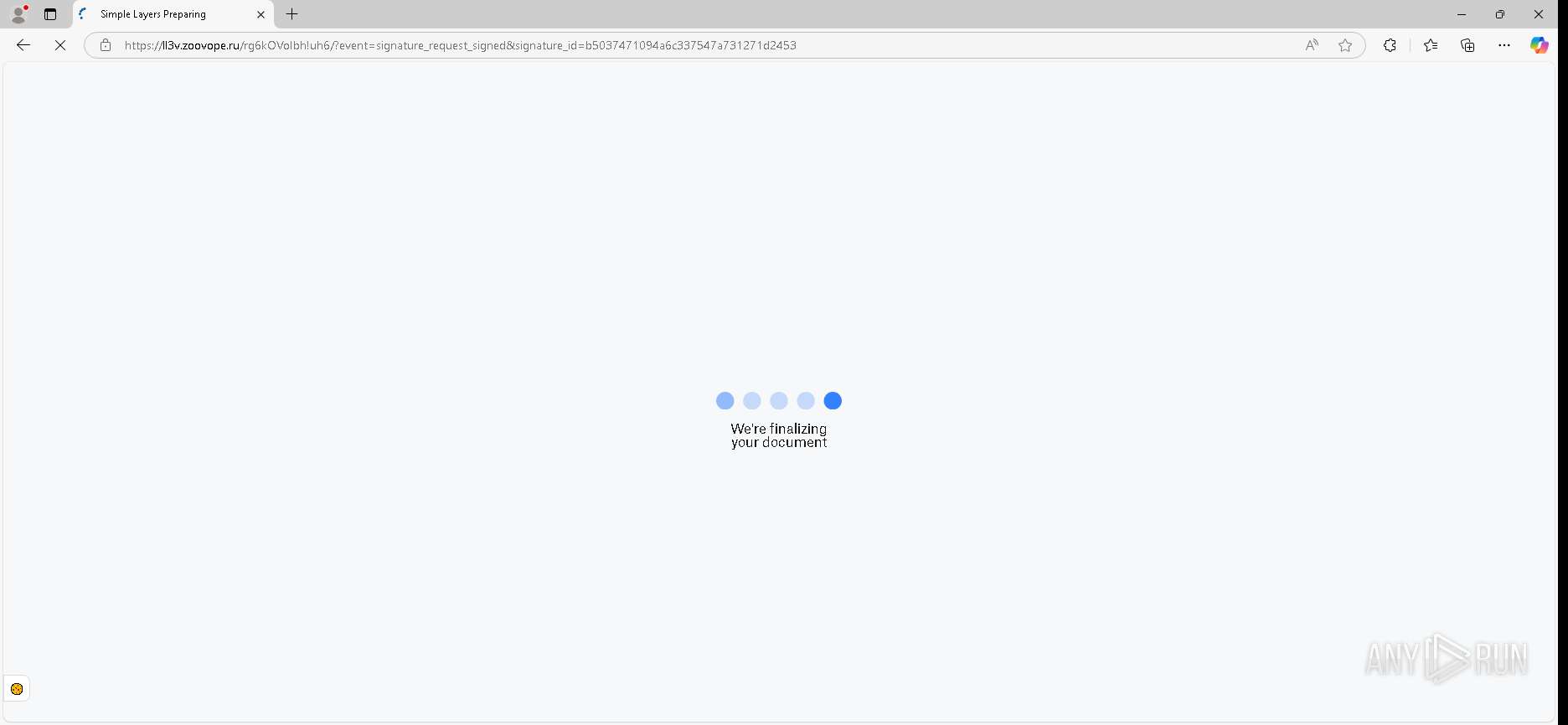
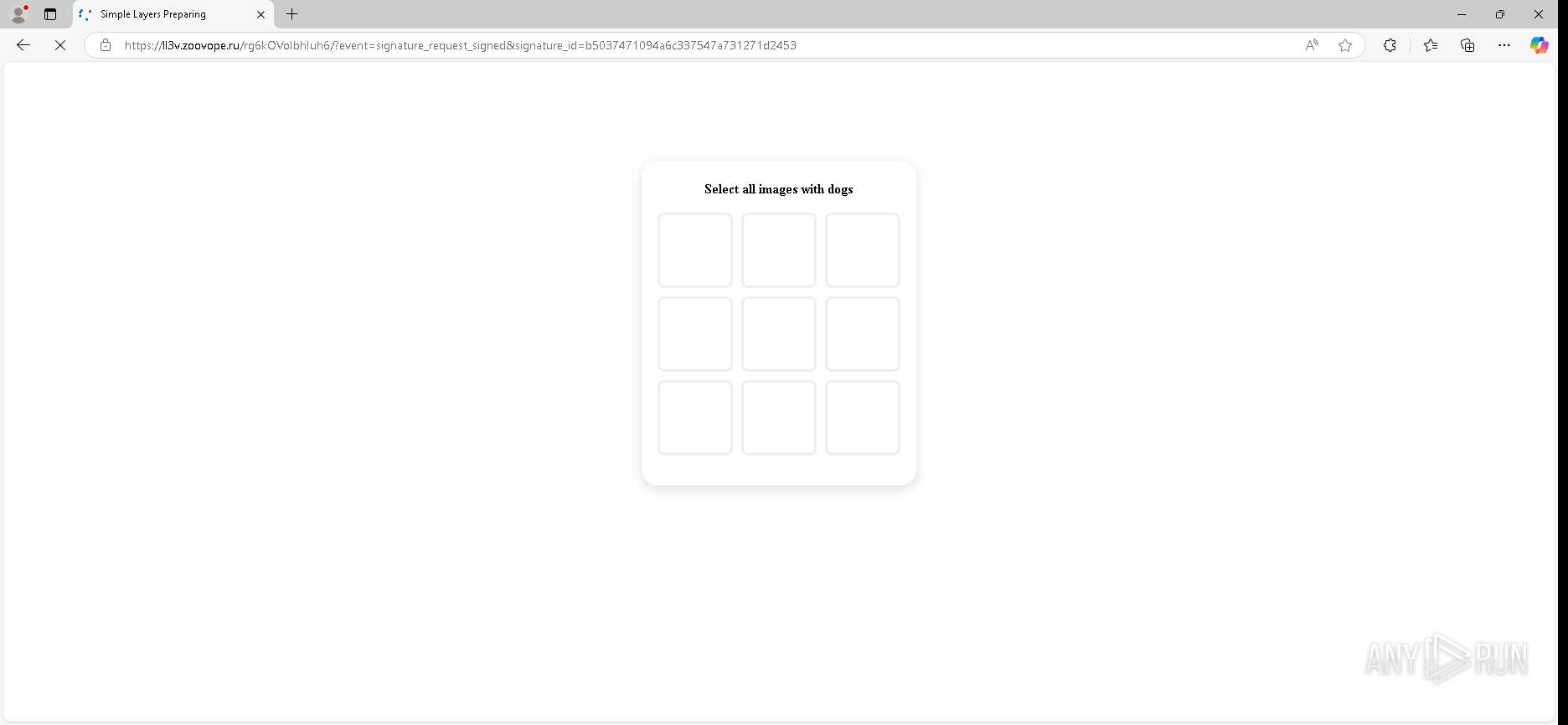
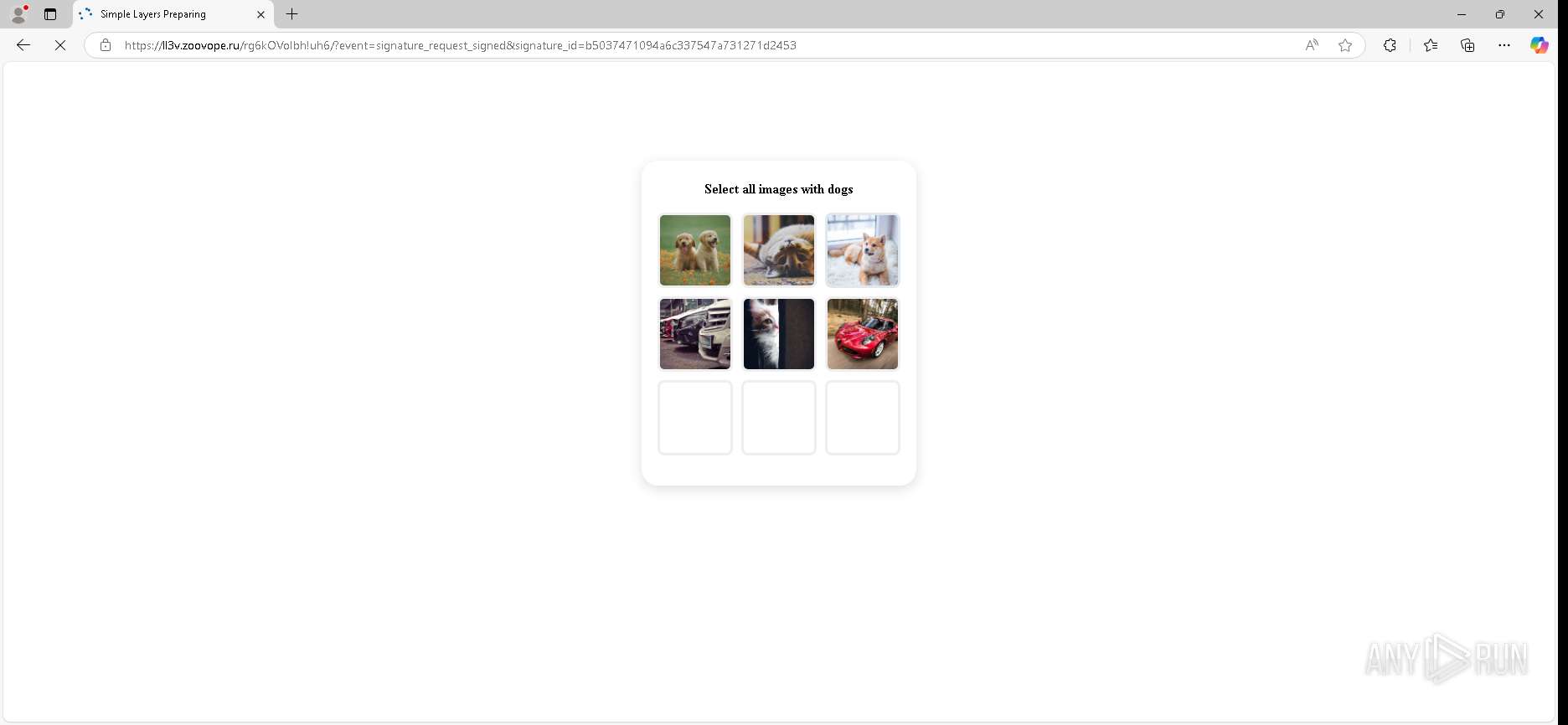
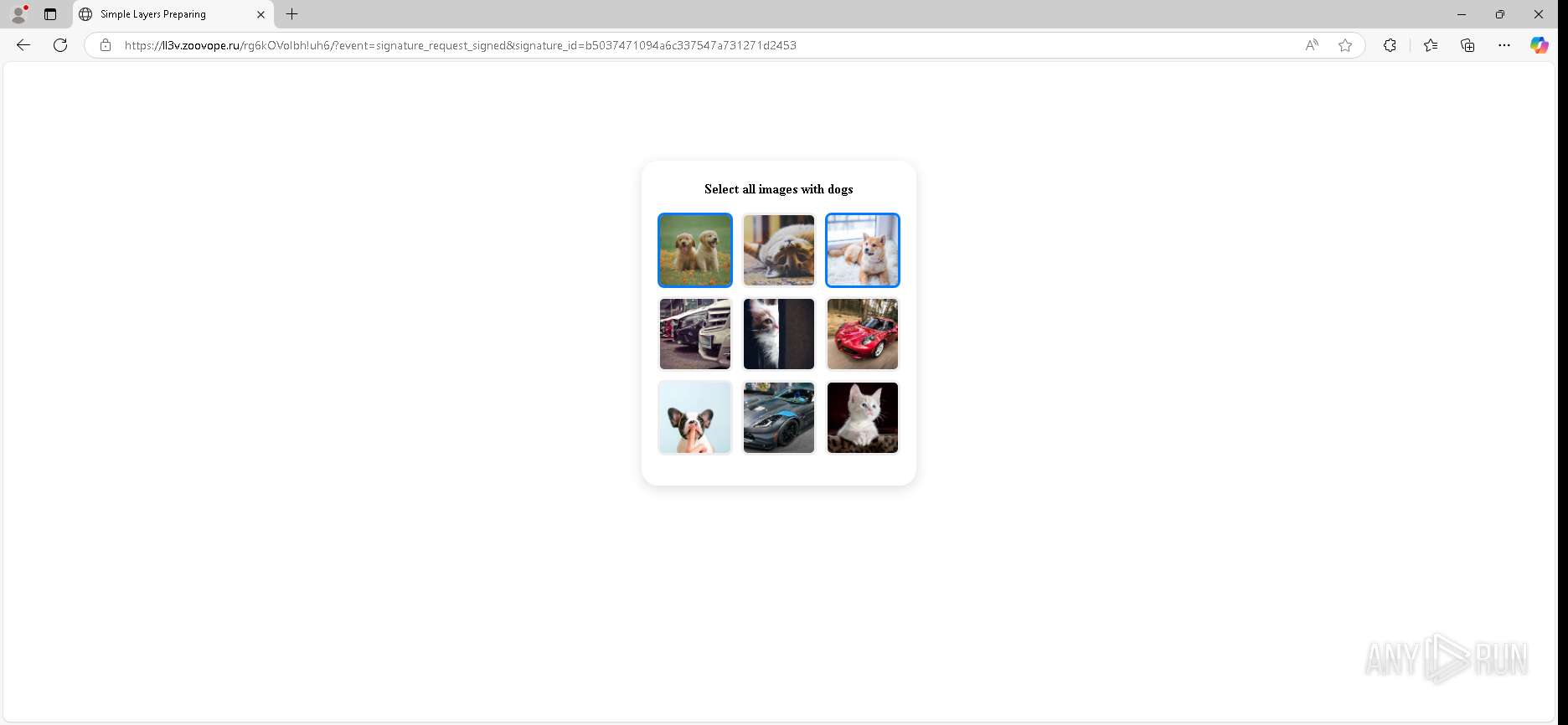
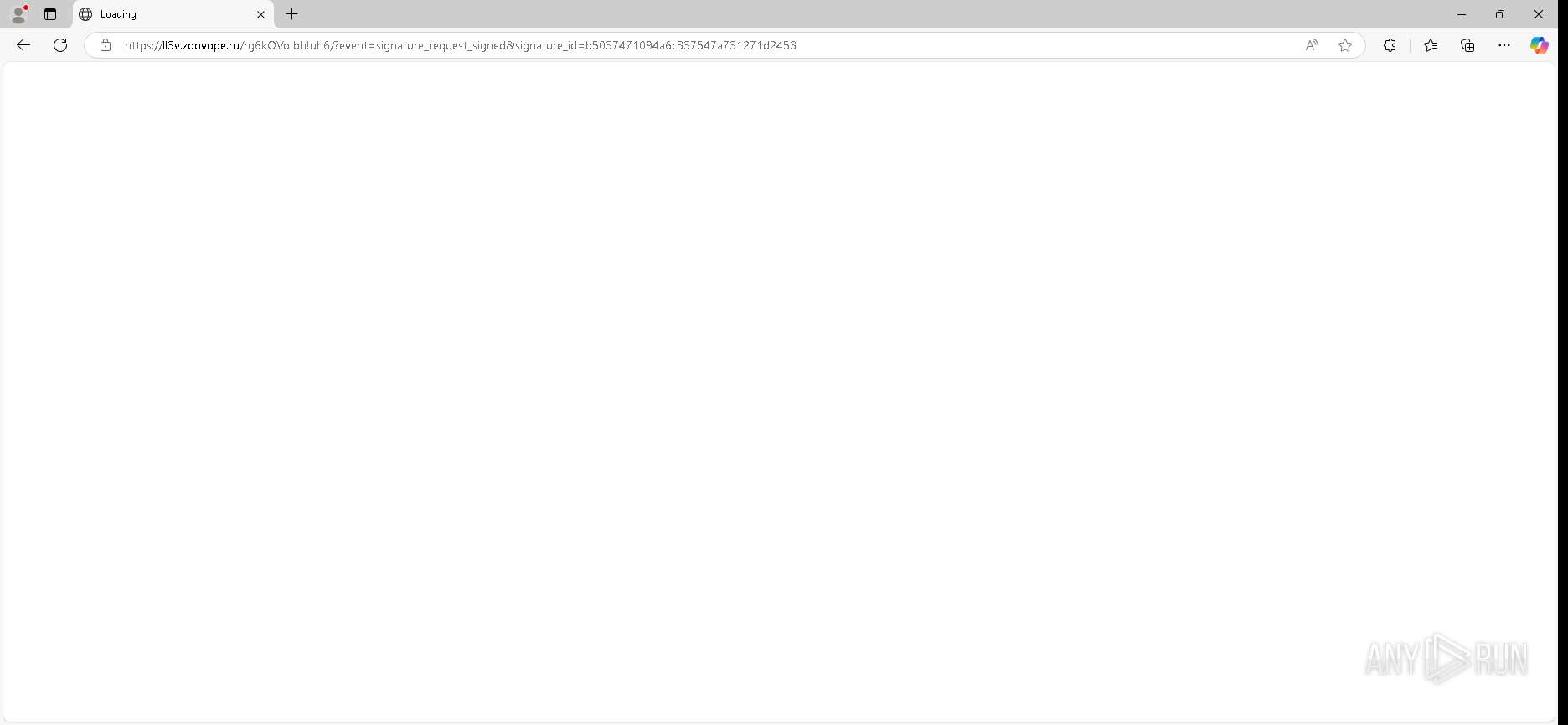
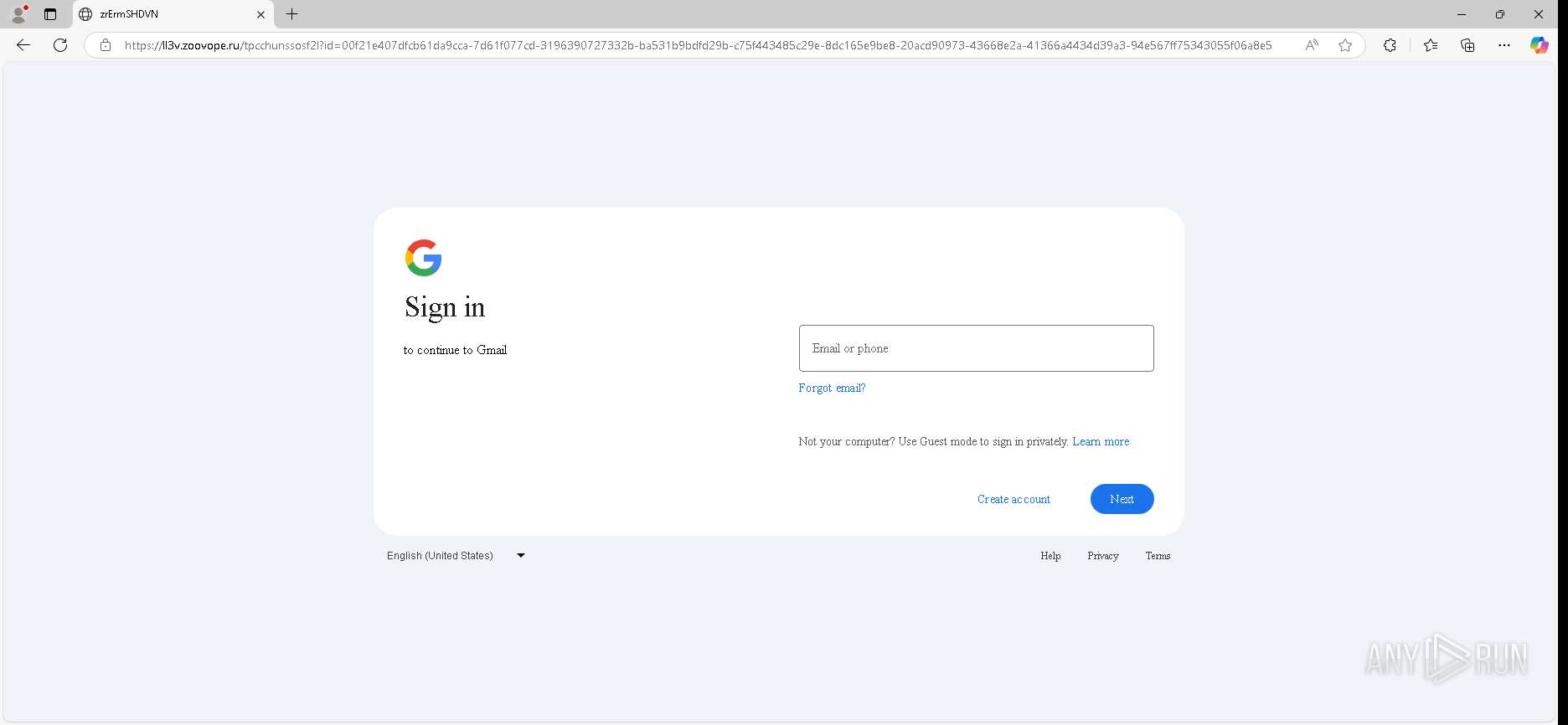
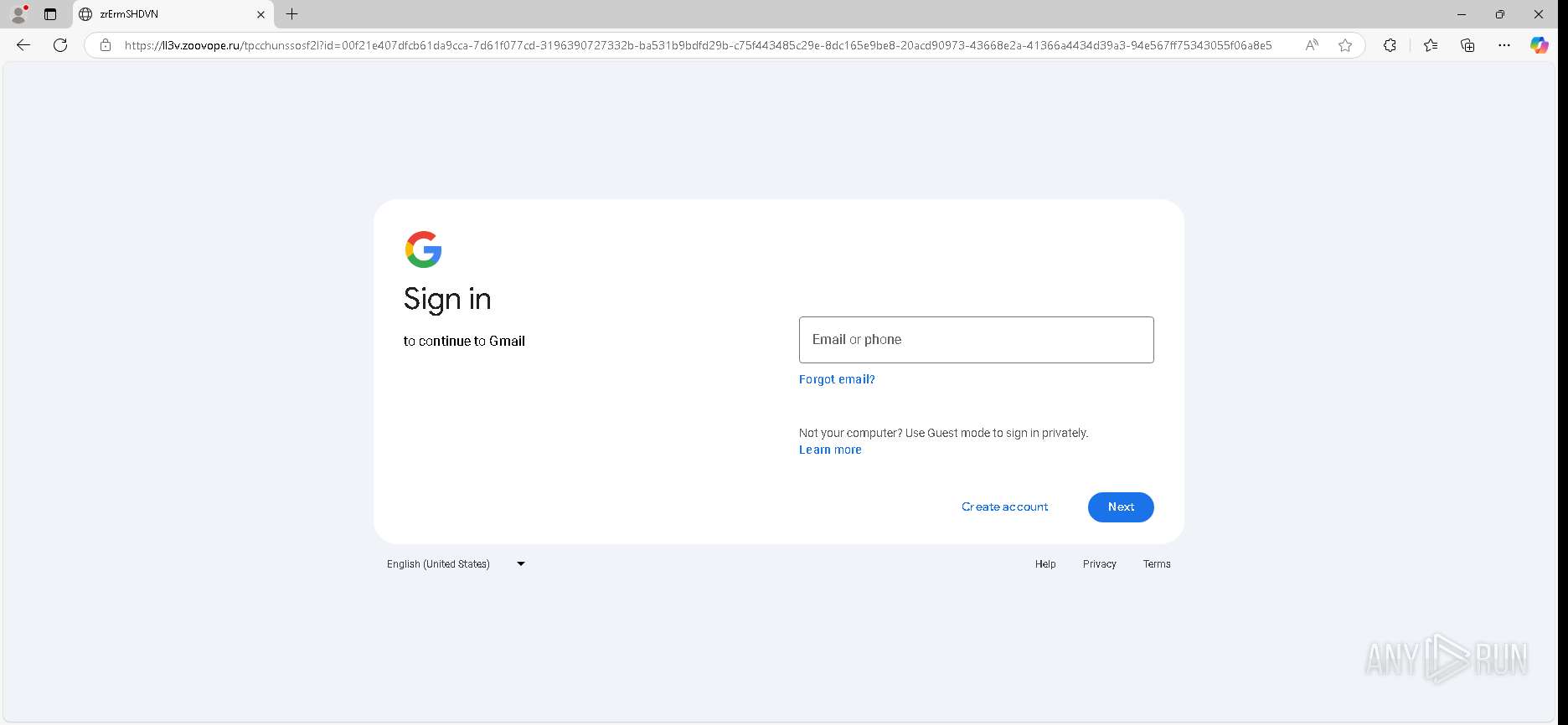
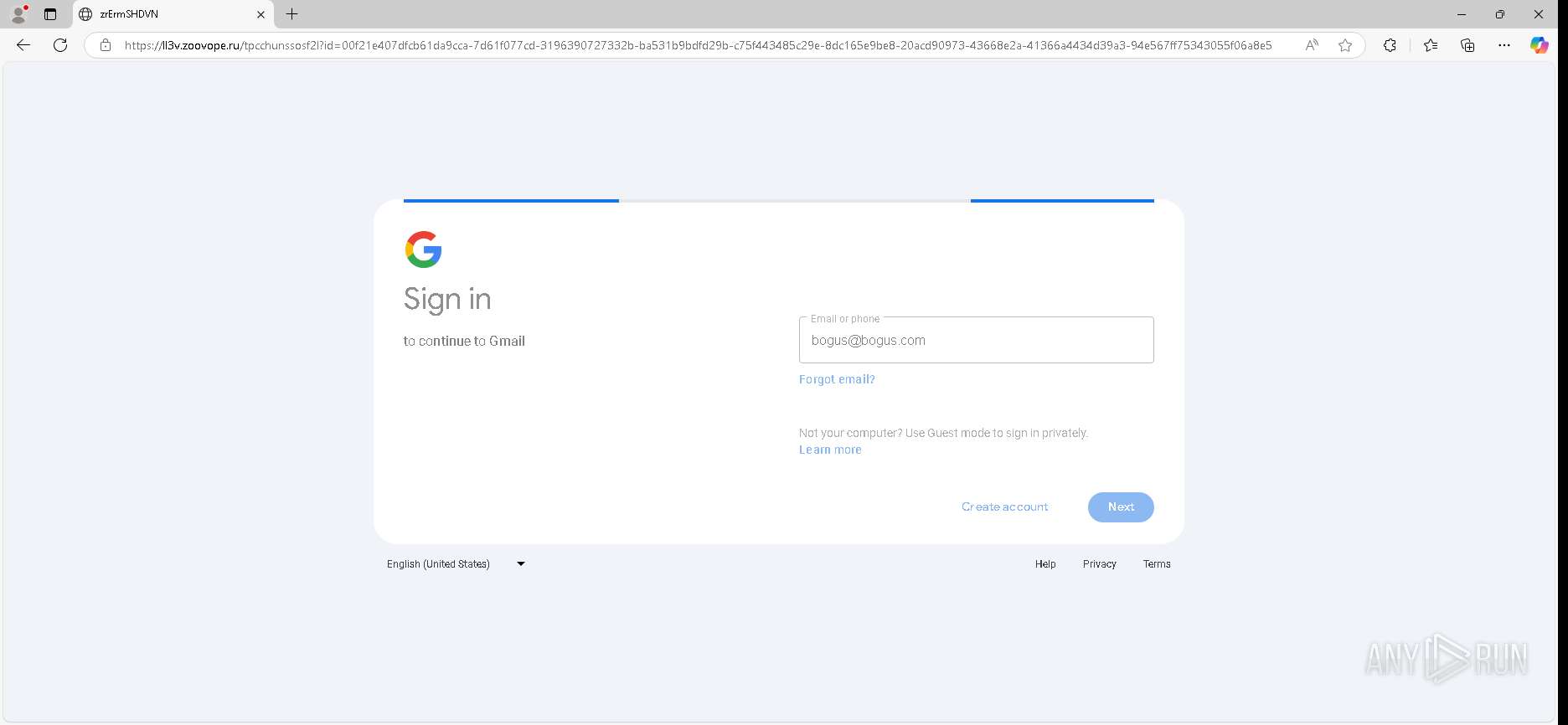
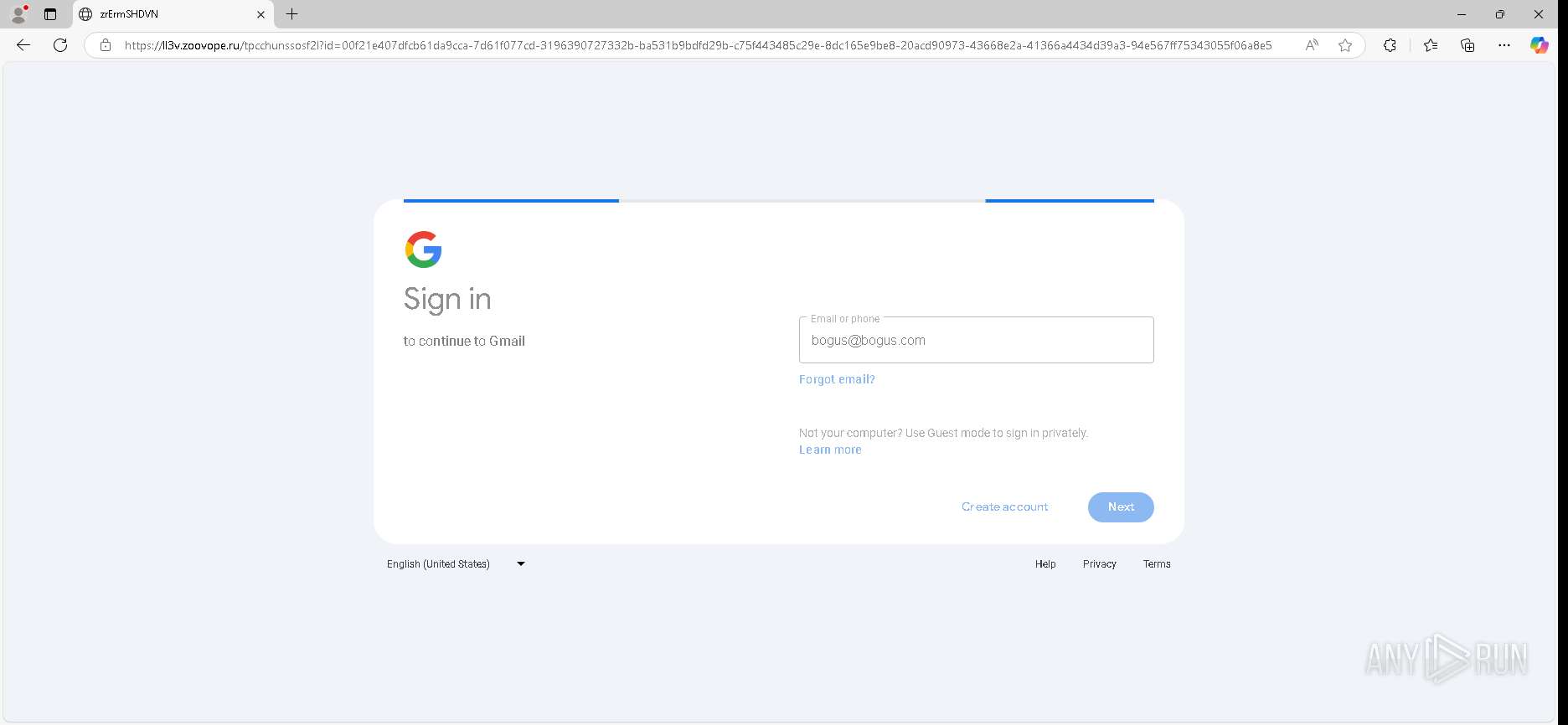
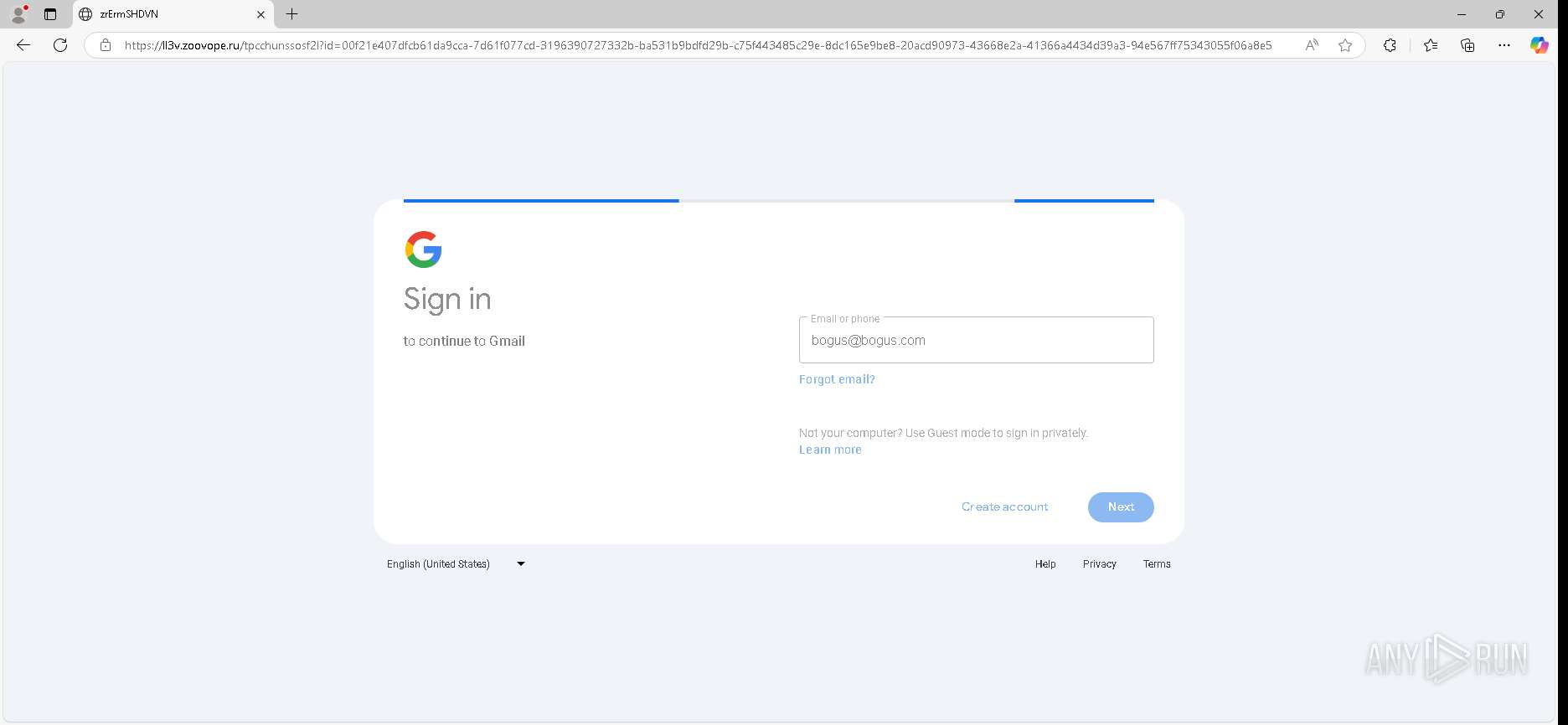
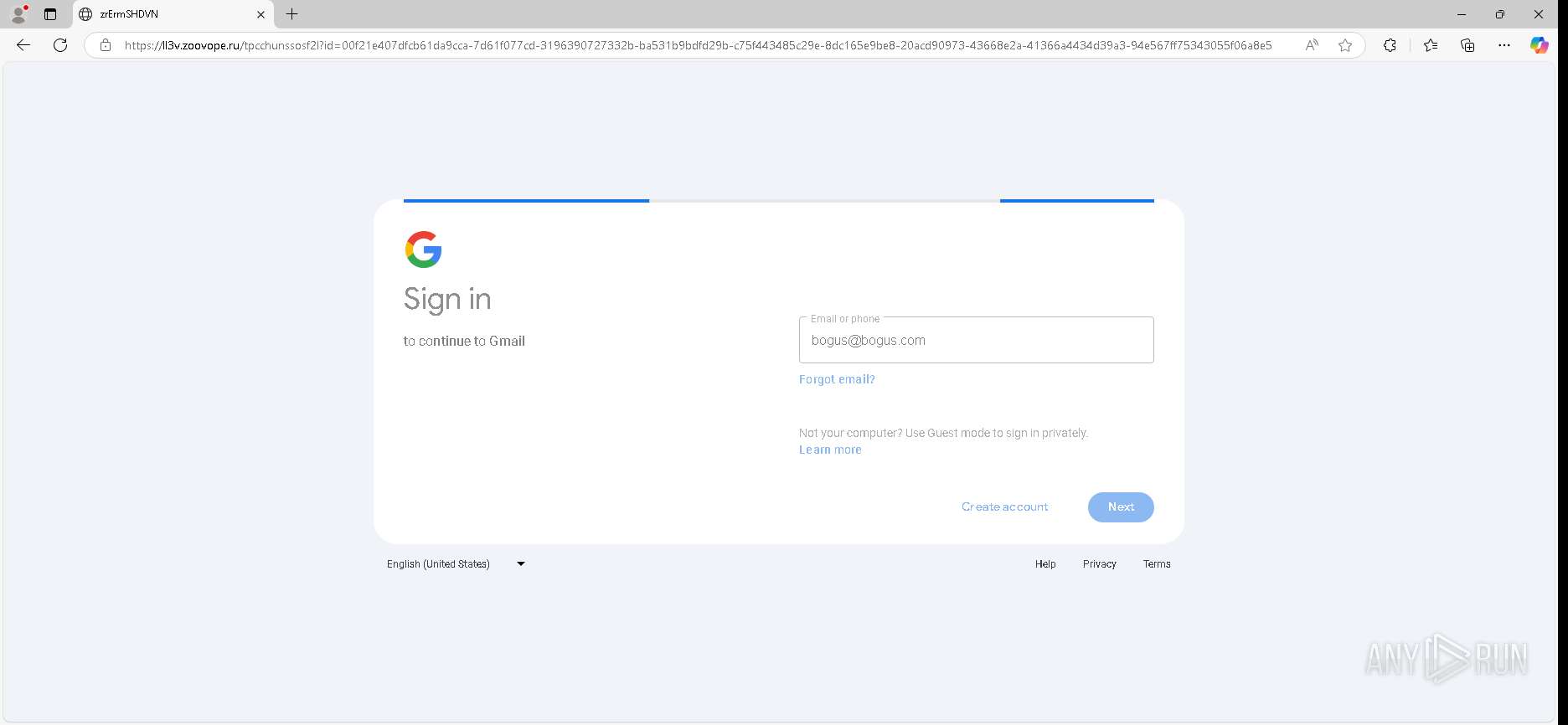
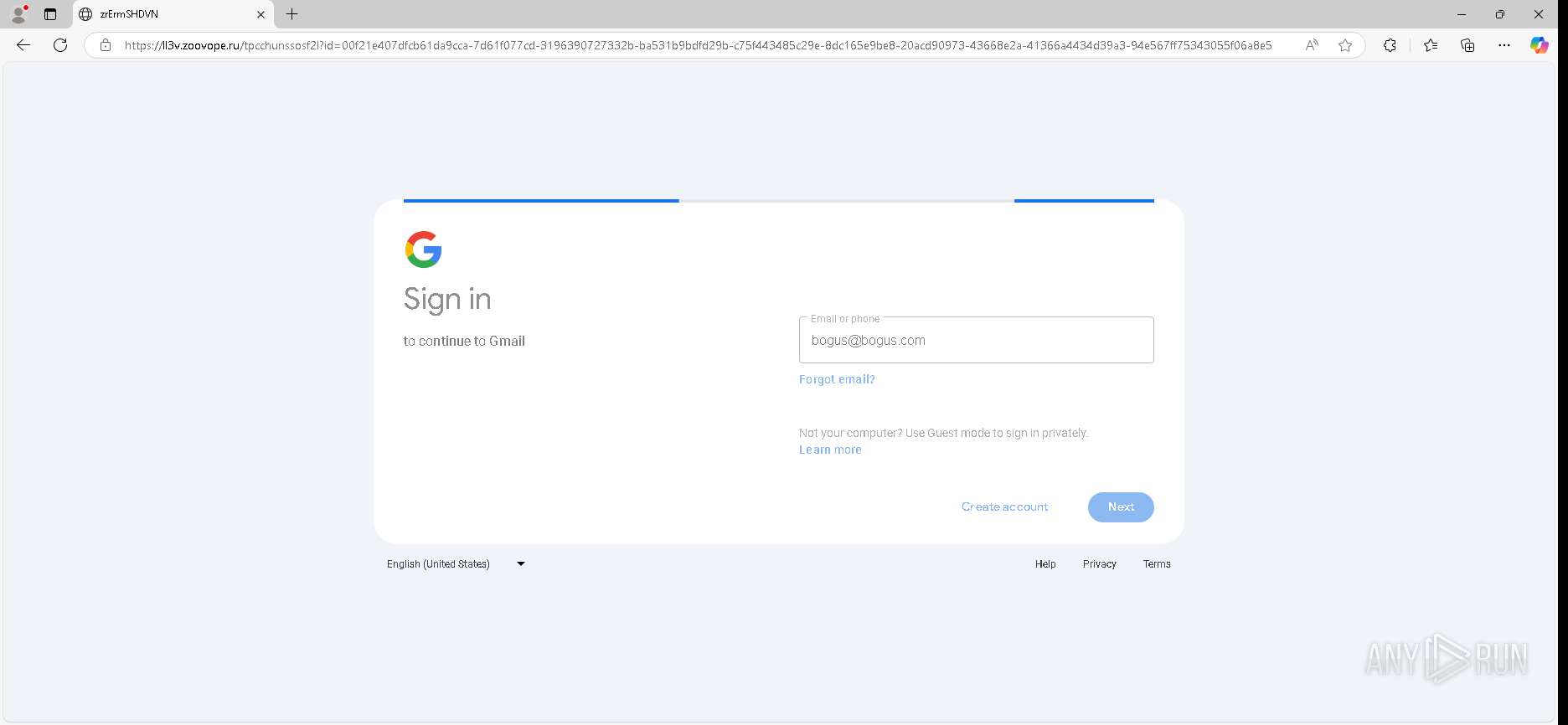
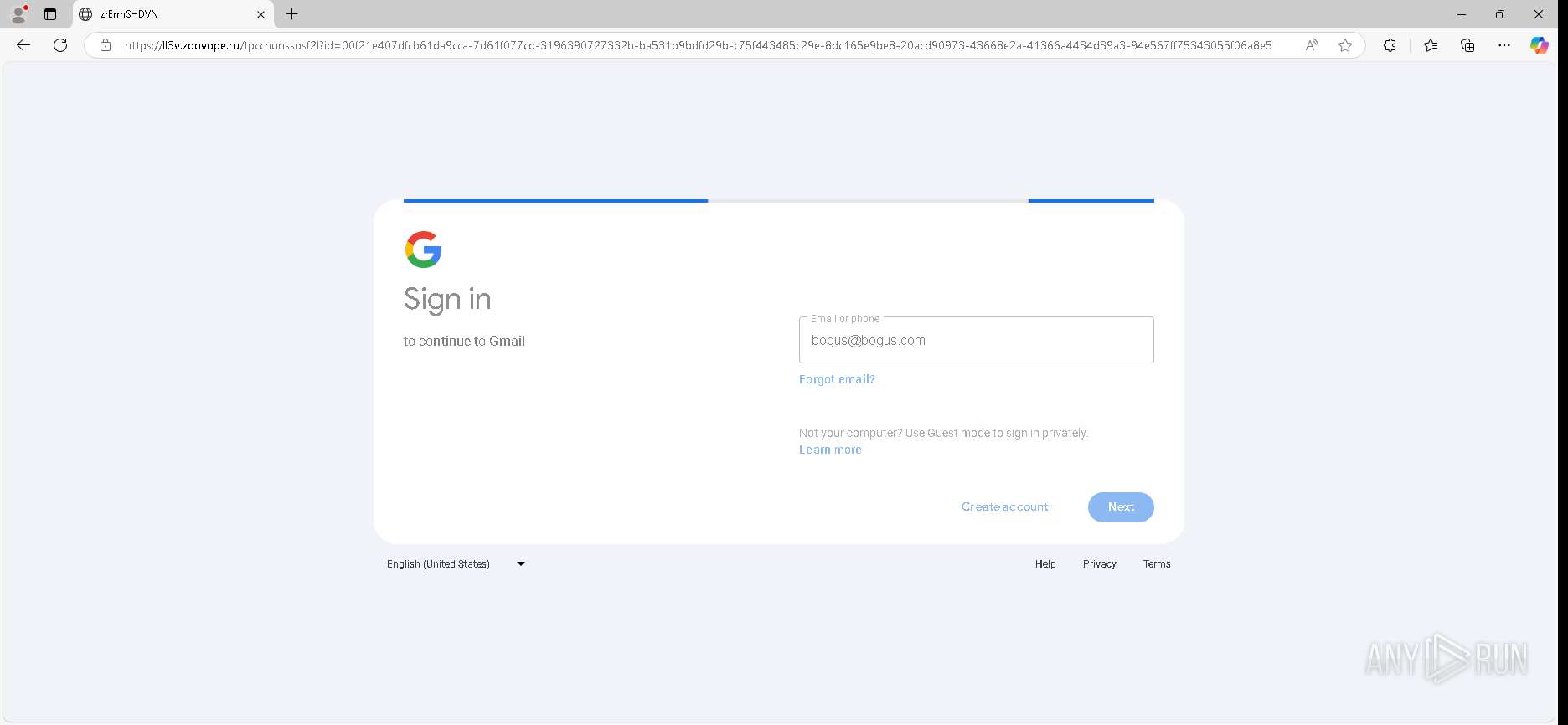
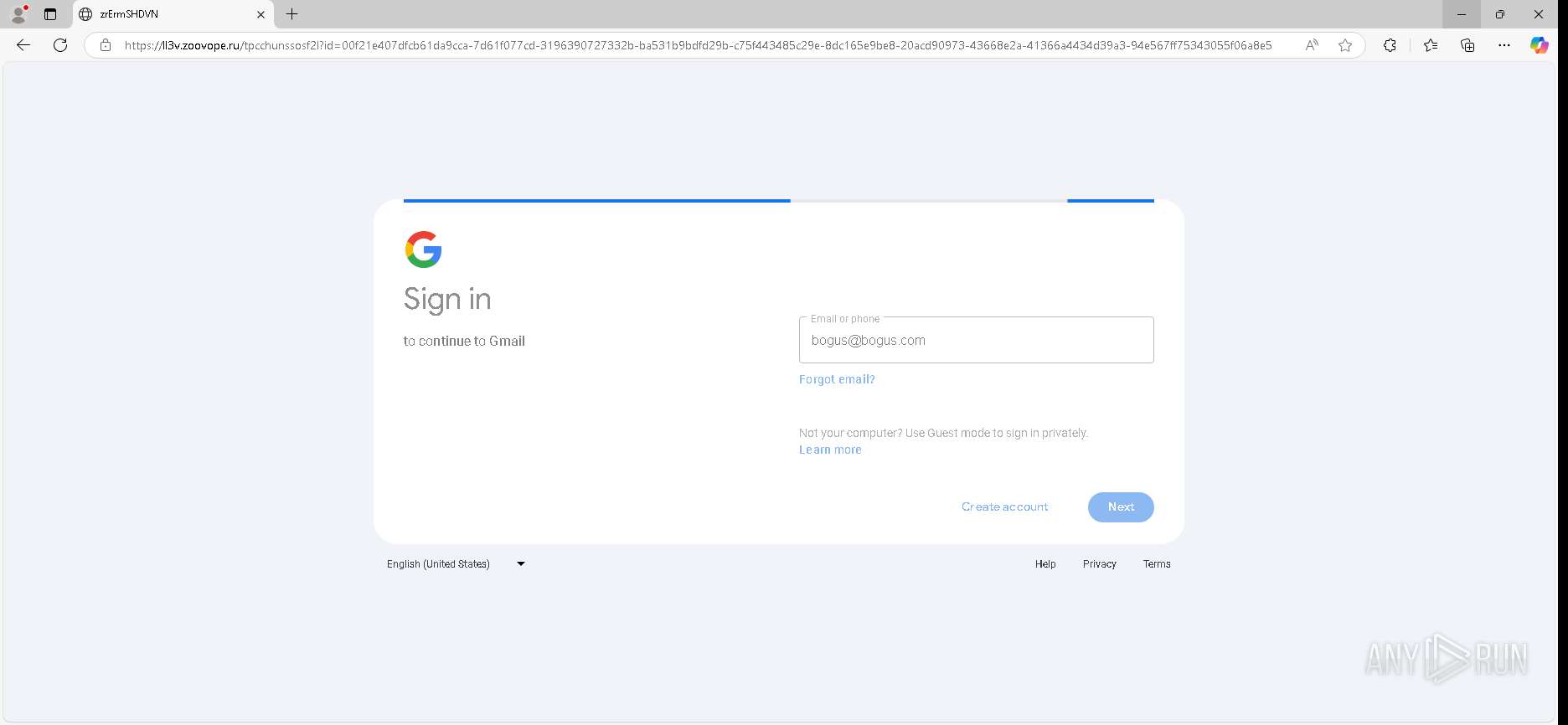
| URL: | https://urldefense.proofpoint.com/v2/url?u=https-3A__app.hellosign.com_t_d85563eadafed9e1700ce6a7c7e673f4e846321d-3Futm-5Fcampaign-3Dmultisigner-5Fcomplete-26utm-5Fsource-3Ddefault-26utm-5Fchannel-3Dproduct-5Fpromo-26utm-5Fmedium-3Demail-26utm-5Fcontent-3Doriginal&d=DwMFaQ&c=euGZstcaTDllvimEN8b7jXrwqOf-v5A_CdpgnVfiiMM&r=lUNQsQ_6pCP4_AUkkqN38UsZ6dqOUhr03-jSyBzQjRQ&m=B5dgC5IxaVFkpEdw5f0HJP23W5UnB7MOF9uw8_tYFxpzD9TNSgRPvSFdOs7s_sdu&s=Y59tFOY0EtnyknJ0WzlhAnC9ROu-cC6o-MwAG1_VAqw&e= |
| Full analysis: | https://app.any.run/tasks/56dd6707-5417-4d99-baf1-a0a81f579537 |
| Verdict: | Malicious activity |
| Analysis date: | September 04, 2025, 18:42:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| MD5: | 0101EEF3539A5544B70D20FE1028385C |
| SHA1: | 8FF6223D64EAED871D0D9BEDA2E3A6E04EE933F2 |
| SHA256: | 53BDCB303A8AB3C6C4B913A2FFAB8C7EE30C40F9BC13985D54CF8C59D79E36C8 |
| SSDEEP: | 12:2UHP1fgOAhtjkuVN/kXHc5XPXHJVT59oWvGpCilyNb:2ctYrjjFmgXXT5t+zlyNb |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
149
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 6888 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --webtransport-developer-mode --string-annotations --always-read-main-dll --field-trial-handle=2268,i,5563634417838714164,2438233923621497815,262144 --variations-seed-version --mojo-platform-channel-handle=2560 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
55
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6888 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000b7 | compressed | |
MD5:C84F3984FBC8C1601DA87228253E599A | SHA256:804ABD8A4E66D1E4B798EE23F83729422DE85410C7ED8DF65E6746C745D544C6 | |||
| 6888 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000b6 | compressed | |
MD5:D8ADB3CF712A7325800FA896A8528CF7 | SHA256:1603C3C81507857D594E631F0B2B718CDCA006D54B23128AD3B94F45809F321A | |||
| 6888 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000be | binary | |
MD5:0B7E652FBFB2C3F38B464CB6188CD1E5 | SHA256:28820F44116180CA368DE2AD123E9FF2052EFB3837B5D6F4FC9B9722A779F725 | |||
| 6888 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000b5 | binary | |
MD5:618F61A2E76A121BE2F67E474FE14A14 | SHA256:8A407BC163073CF5FA832318A4012C6FD8CB2743C399E841BC4D4DBB608E8F4D | |||
| 6888 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000bb | compressed | |
MD5:93D934AA2913A753B99AA2A8F56C4D89 | SHA256:9995FC9907D3DCBAB47F4E4023CDF0660618B0B71C22BE8FD079C25F3B5BD3BB | |||
| 6888 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000bd | compressed | |
MD5:CDE39CA9023080815D754093CD702C72 | SHA256:AFF49DDE4B83EDDC51E69824AD246ADDBEA852DED8CF8A3B0201DCA2E8E6C3FF | |||
| 6888 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000bc | binary | |
MD5:B9BC429CEA66A3F790D1ECB228C8EA16 | SHA256:B3DC3B55D94549513E695B882143FFA76242CCA02005C9E5F505912A901D83A0 | |||
| 6888 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000b8 | binary | |
MD5:93B6F18EC99BCB7C3FA7EA570A75E240 | SHA256:43693F7BDD6146E783FAB3F75BA0A51AA3CF9530ADBF790DBD686FC8A17AA3DB | |||
| 6888 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c4 | compressed | |
MD5:D86892E4E2F046618CF36F5B291084B3 | SHA256:D32678E9B2FD1568D564D0408F6924F9373E276202DF6DAB6BEFFAFEC7FA153B | |||
| 6888 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c2 | compressed | |
MD5:B6107BB53D7B5C520B3E847FA9F71CC9 | SHA256:8ADDF5D7D84C74DE44282F0D415486C1101CC8345A8D2E2930247329EAD4F9FF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
302
TCP/UDP connections
183
DNS requests
145
Threats
40
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3892 | svchost.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 150.171.28.11:443 | https://edge.microsoft.com/componentupdater/api/v1/update | unknown | text | 1.46 Kb | — |
— | — | GET | 200 | 92.123.104.67:443 | https://www.bing.com/bloomfilterfiles/ExpandedDomainsFilterGlobal.json | unknown | binary | 656 Kb | — |
5336 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6888 | msedge.exe | GET | 403 | 2.19.126.157:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1753186353&P2=404&P3=2&P4=JctxgV%2fBzu58lG09sot5gGnCe%2fY1hwdAjsjhuzjzxTQ2YzQOHr%2fJXcKzV3SdbfHgQEdRSVQGHksTHkDx0nQLkQ%3d%3d | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 23.197.142.186:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | — |
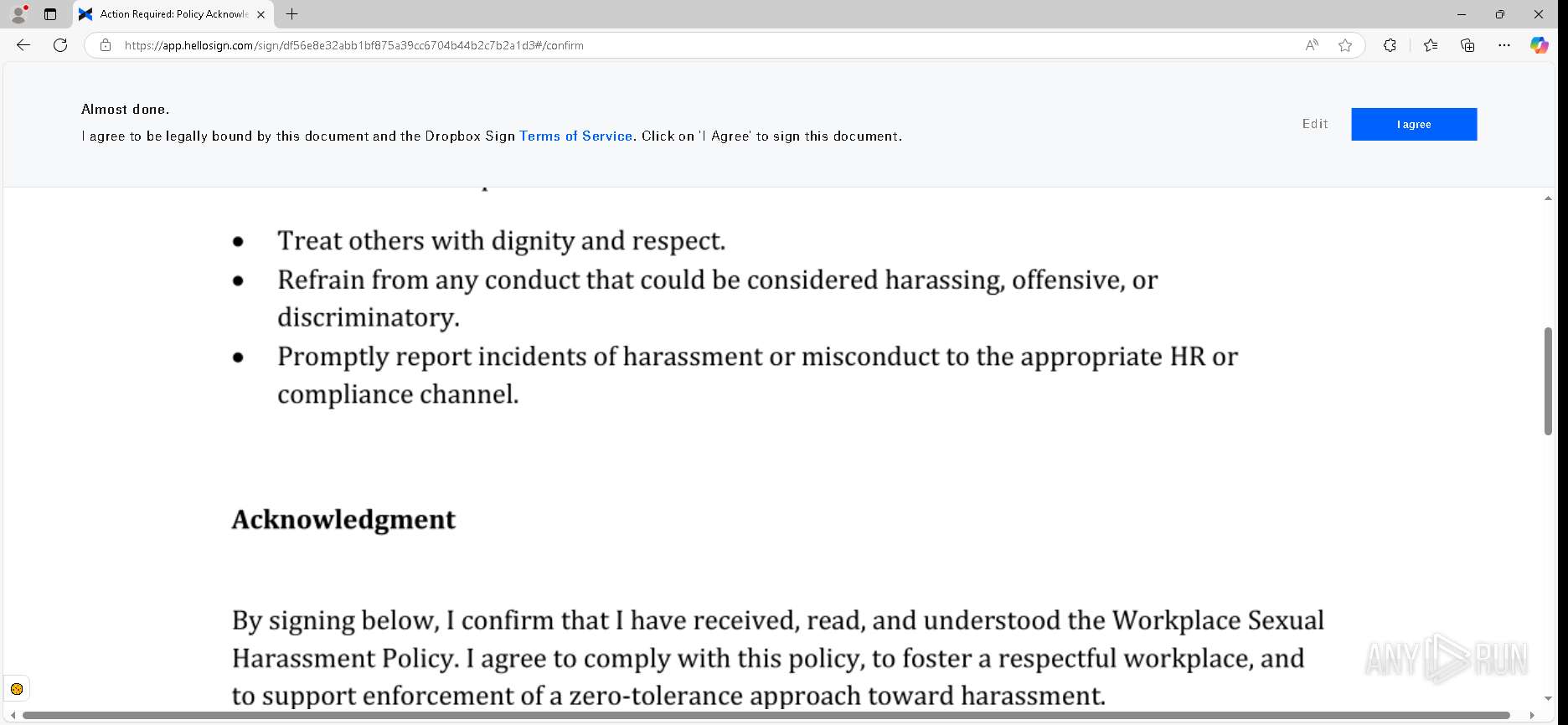
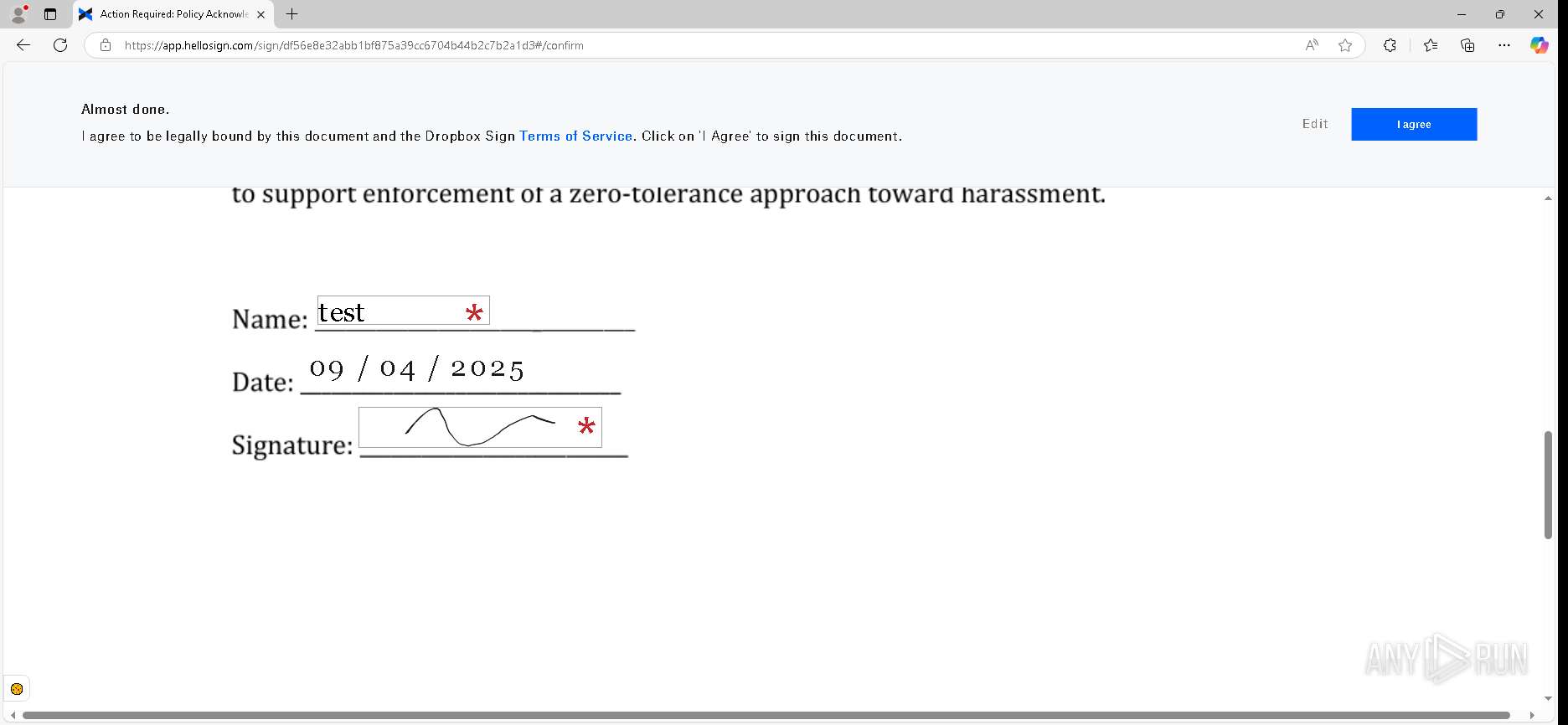
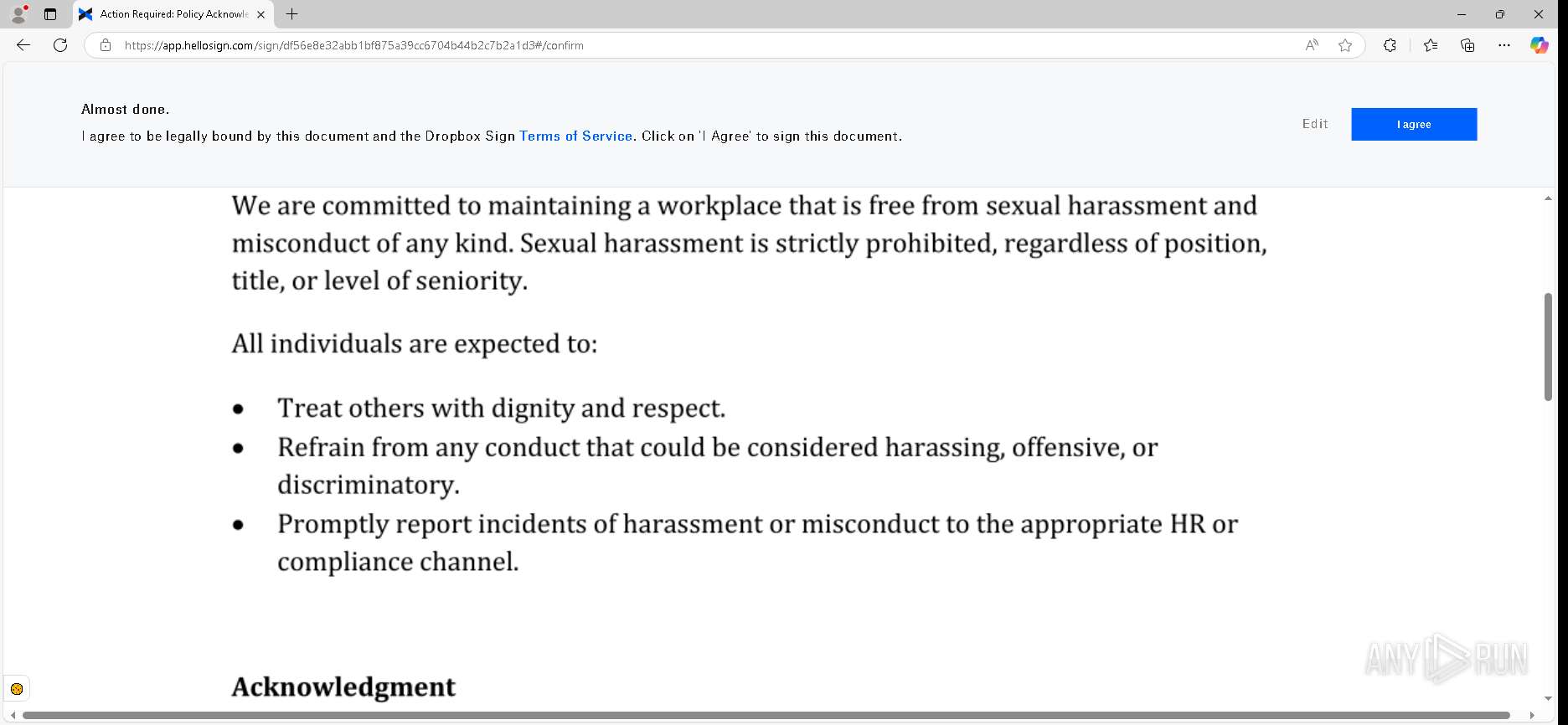
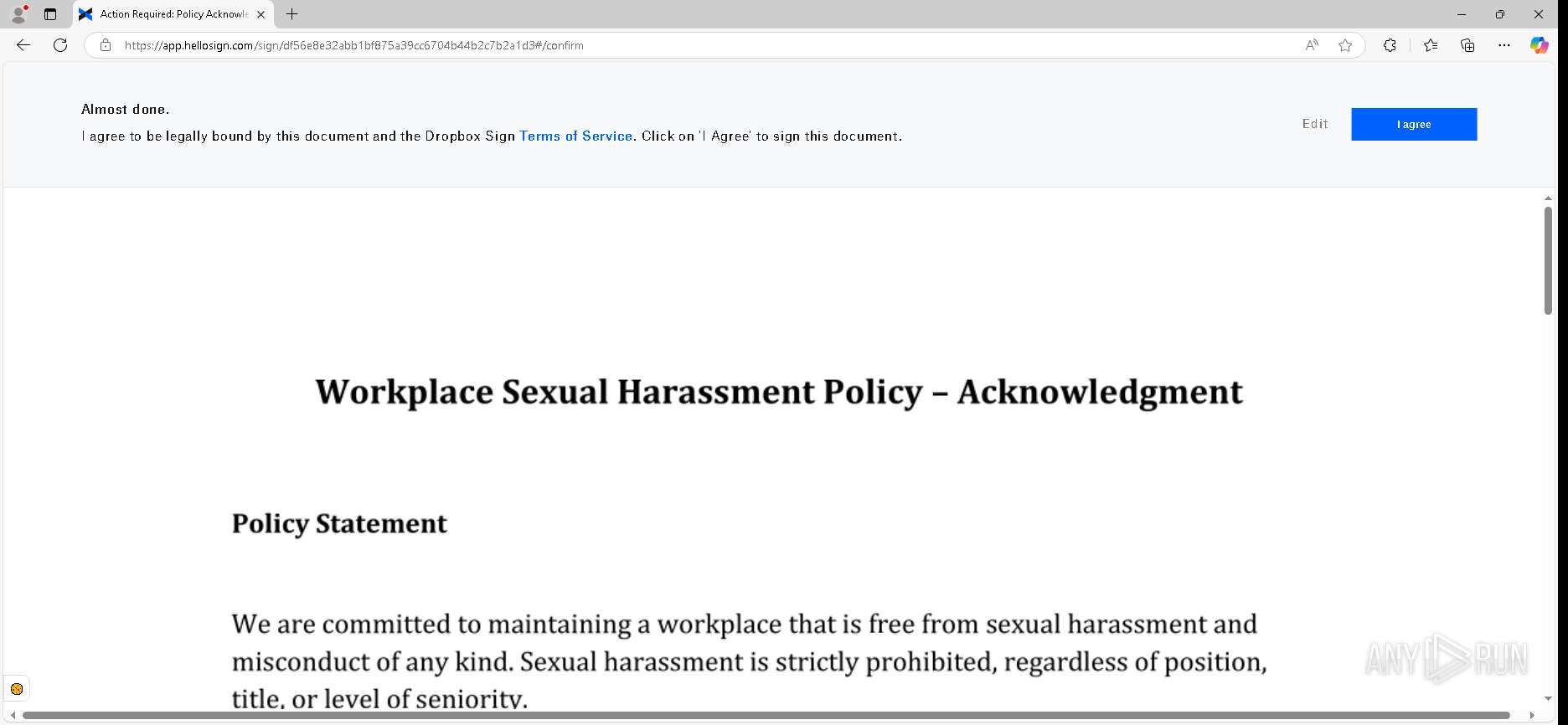
— | — | GET | 302 | 52.71.28.102:443 | https://urldefense.proofpoint.com/v2/url?u=https-3A__app.hellosign.com_t_d85563eadafed9e1700ce6a7c7e673f4e846321d-3Futm-5Fcampaign-3Dmultisigner-5Fcomplete-26utm-5Fsource-3Ddefault-26utm-5Fchannel-3Dproduct-5Fpromo-26utm-5Fmedium-3Demail-26utm-5Fcontent-3Doriginal&d=DwMFaQ&c=euGZstcaTDllvimEN8b7jXrwqOf-v5A_CdpgnVfiiMM&r=lUNQsQ_6pCP4_AUkkqN38UsZ6dqOUhr03-jSyBzQjRQ&m=B5dgC5IxaVFkpEdw5f0HJP23W5UnB7MOF9uw8_tYFxpzD9TNSgRPvSFdOs7s_sdu&s=Y59tFOY0EtnyknJ0WzlhAnC9ROu-cC6o-MwAG1_VAqw&e= | unknown | — | — | — |
— | — | POST | 403 | 69.192.161.161:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | html | 384 b | — |
3892 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5336 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3892 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2460 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6888 | msedge.exe | 2.19.126.157:80 | msedge.b.tlu.dl.delivery.mp.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
304 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
5008 | svchost.exe | 23.197.142.186:443 | fs.microsoft.com | Akamai International B.V. | US | whitelisted |
6888 | msedge.exe | 52.71.28.102:443 | urldefense.proofpoint.com | AMAZON-AES | US | whitelisted |
6888 | msedge.exe | 162.125.66.25:443 | app.hellosign.com | DROPBOX | DE | unknown |
3892 | svchost.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
msedge.b.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
urldefense.proofpoint.com |
| whitelisted |
app.hellosign.com |
| unknown |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Generic Phishing domain observed in HTTP Host (DadSec / Storm-1575) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Generic Phishing domain observed in HTTP Host (DadSec / Storm-1575) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Generic Phishing domain observed in HTTP Host (DadSec / Storm-1575) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |