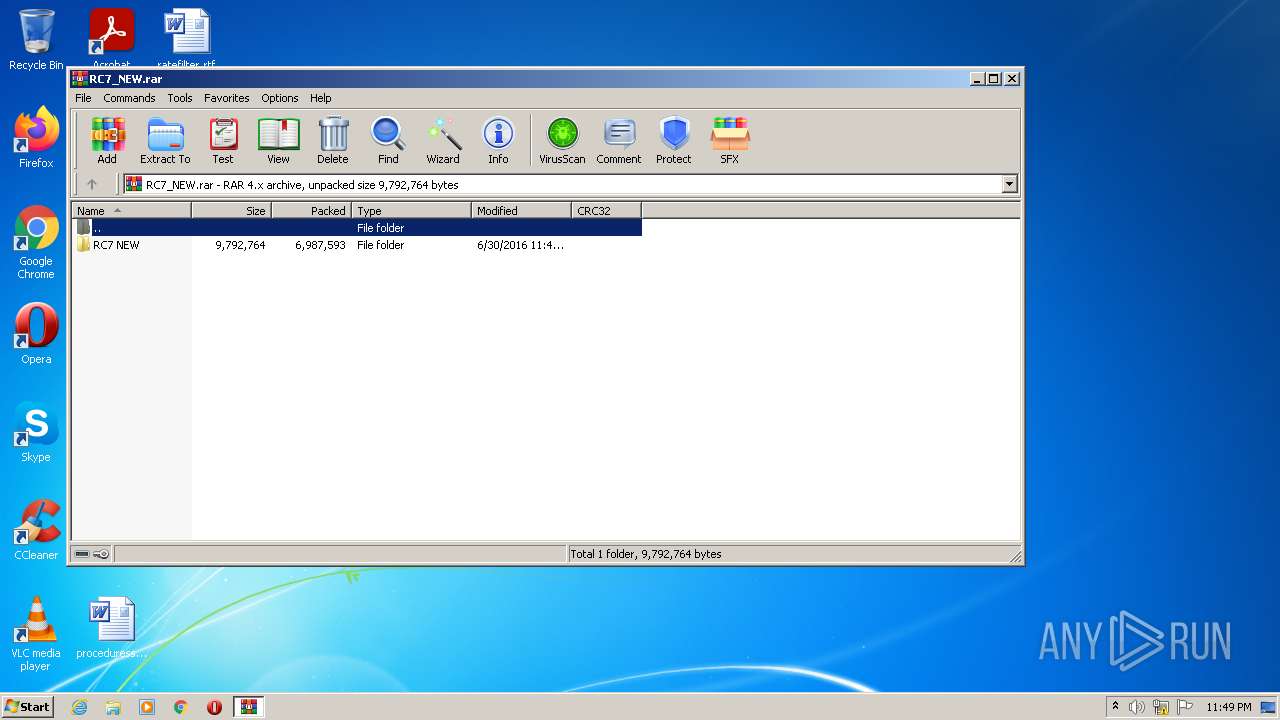
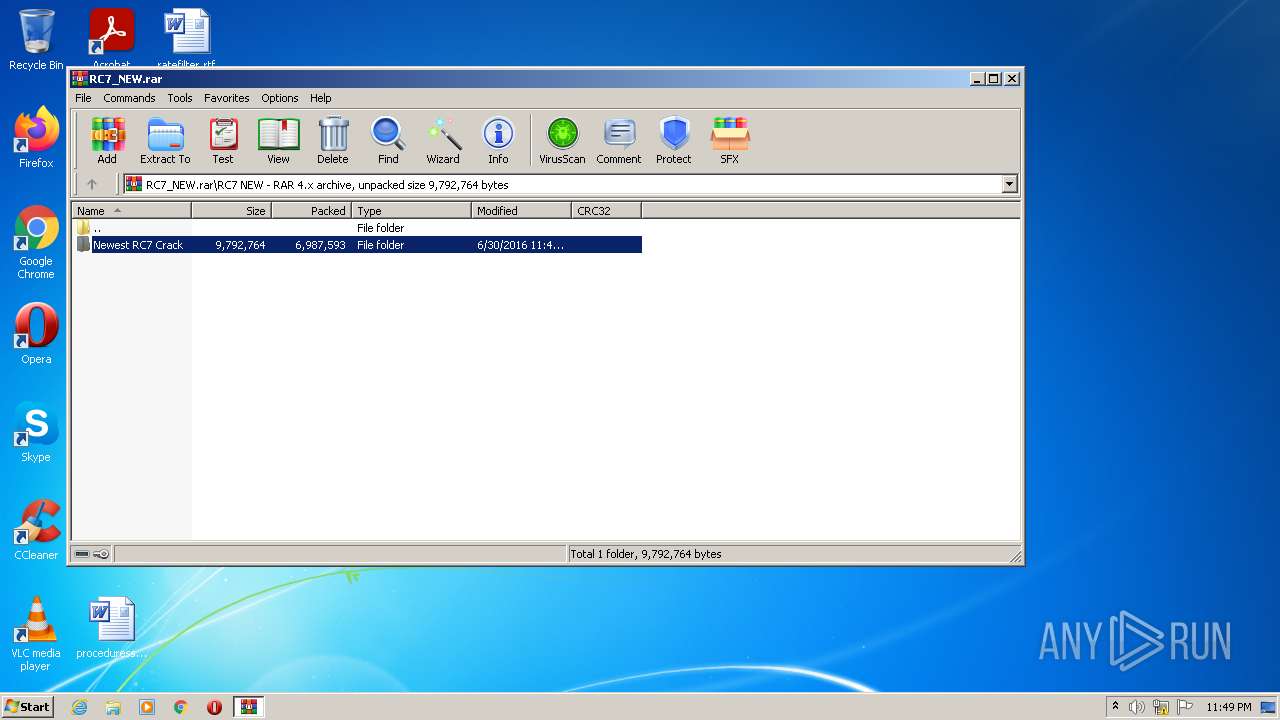
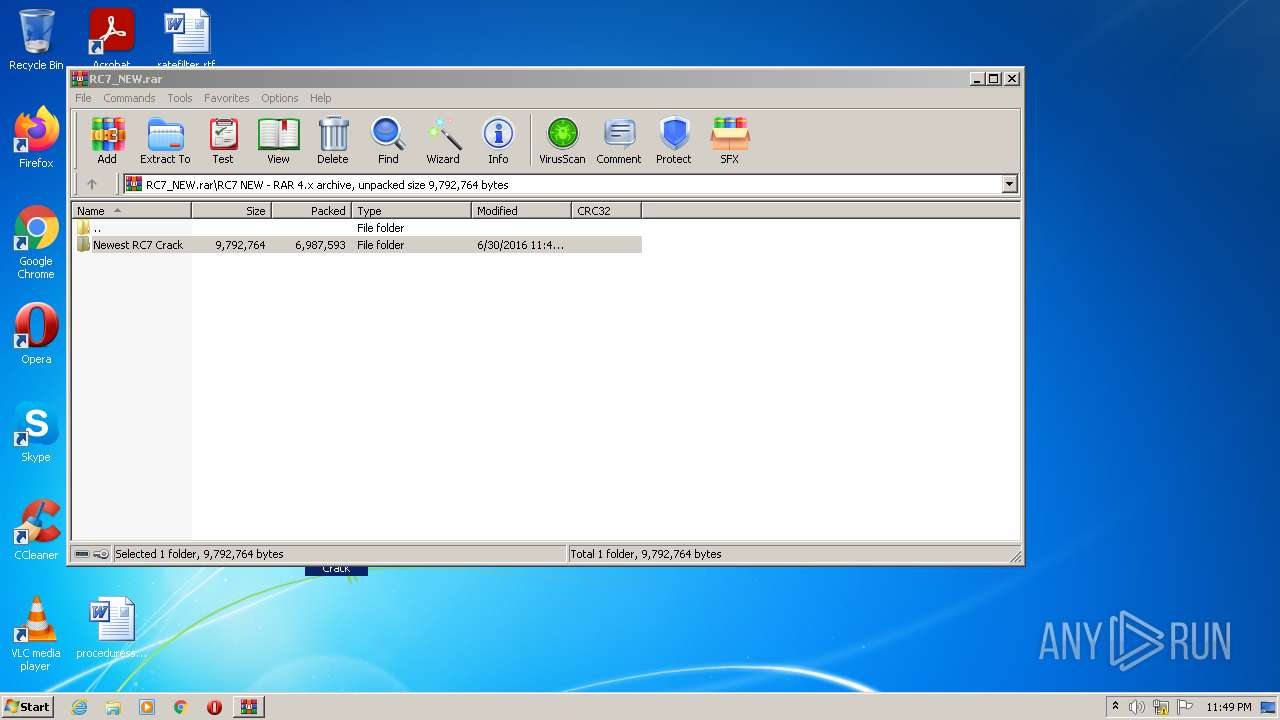
| download: | RC7_NEW.rar |
| Full analysis: | https://app.any.run/tasks/8dbcfb4c-3ed7-4bdf-9763-1390b1c16640 |
| Verdict: | Malicious activity |
| Analysis date: | February 08, 2022, 23:49:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | E16DE9C8AC4CBF04F5B08BC227CB7CD0 |
| SHA1: | 8A9CF923164D66827770521302BA66B304ADF5DA |
| SHA256: | 53B36D8CAF813D789826F0D16DD68CF39583D4BFF9B803142D9289520B8FDA8D |
| SSDEEP: | 196608:Hsw/vj7hCXREtv0QQzfd1FD4cNeiGiRo1pwru:9Xj0XssQ4F1J51VRkpwy |
MALICIOUS
Application was dropped or rewritten from another process
- Memcheck.exe (PID: 3852)
- Memcheck.exe (PID: 1300)
- Memcheck.exe (PID: 1276)
- RC7 CRACKED.exe (PID: 2844)
- Memcheck.exe (PID: 3936)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3832)
- Memcheck.exe (PID: 1276)
- RC7 CRACKED.exe (PID: 2844)
Drops executable file immediately after starts
- Memcheck.exe (PID: 3852)
- Memcheck.exe (PID: 3936)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3792)
- Memcheck.exe (PID: 3936)
- Memcheck.exe (PID: 3852)
- RC7 CRACKED.exe (PID: 2844)
- Memcheck.exe (PID: 1276)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3792)
- Memcheck.exe (PID: 3936)
Drops a file with too old compile date
- WinRAR.exe (PID: 3792)
- Memcheck.exe (PID: 3936)
- Memcheck.exe (PID: 3852)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3792)
- Memcheck.exe (PID: 3852)
- Memcheck.exe (PID: 3936)
Reads the computer name
- Memcheck.exe (PID: 3852)
- RC7 CRACKED.exe (PID: 2844)
- Memcheck.exe (PID: 1276)
- WinRAR.exe (PID: 3792)
Starts Internet Explorer
- RC7 CRACKED.exe (PID: 2844)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3824)
INFO
Manual execution by user
- Memcheck.exe (PID: 1300)
- Memcheck.exe (PID: 3852)
- RC7 CRACKED.exe (PID: 2844)
Checks supported languages
- iexplore.exe (PID: 2096)
- iexplore.exe (PID: 3824)
Reads the computer name
- iexplore.exe (PID: 2096)
- iexplore.exe (PID: 3824)
Application launched itself
- iexplore.exe (PID: 2096)
Changes internet zones settings
- iexplore.exe (PID: 2096)
Checks Windows Trust Settings
- iexplore.exe (PID: 3824)
- iexplore.exe (PID: 2096)
Creates files in the user directory
- iexplore.exe (PID: 3824)
Reads settings of System Certificates
- iexplore.exe (PID: 3824)
- iexplore.exe (PID: 2096)
Reads internet explorer settings
- iexplore.exe (PID: 3824)
Reads the date of Windows installation
- iexplore.exe (PID: 2096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| ArchivedFileName: | RC7 NEW\Newest RC7 Crack\0xAzul (2).dll |
|---|---|
| PackingMethod: | Normal |
| ModifyDate: | 2016:07:01 06:15:00 |
| OperatingSystem: | Win32 |
| UncompressedSize: | 212992 |
| CompressedSize: | 44623 |
Total processes
46
Monitored processes
9
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1276 | C:\Users\admin\AppData\Local\Temp\cetrainers\CETF823.tmp\extracted\Memcheck.exe "C:\Users\admin\AppData\Local\Temp\cetrainers\CETF823.tmp\extracted\CET_TRAINER.CETRAINER" "-ORIGIN:C:\Users\admin\Desktop\Newest RC7 Crack\" | C:\Users\admin\AppData\Local\Temp\cetrainers\CETF823.tmp\extracted\Memcheck.exe | Memcheck.exe | ||||||||||||
User: admin Company: Cheat Engine Integrity Level: HIGH Description: Cheat Engine Exit code: 0 Version: 6.5.0.4590 Modules
| |||||||||||||||
| 1300 | "C:\Users\admin\Desktop\Newest RC7 Crack\Memcheck.exe" | C:\Users\admin\Desktop\Newest RC7 Crack\Memcheck.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
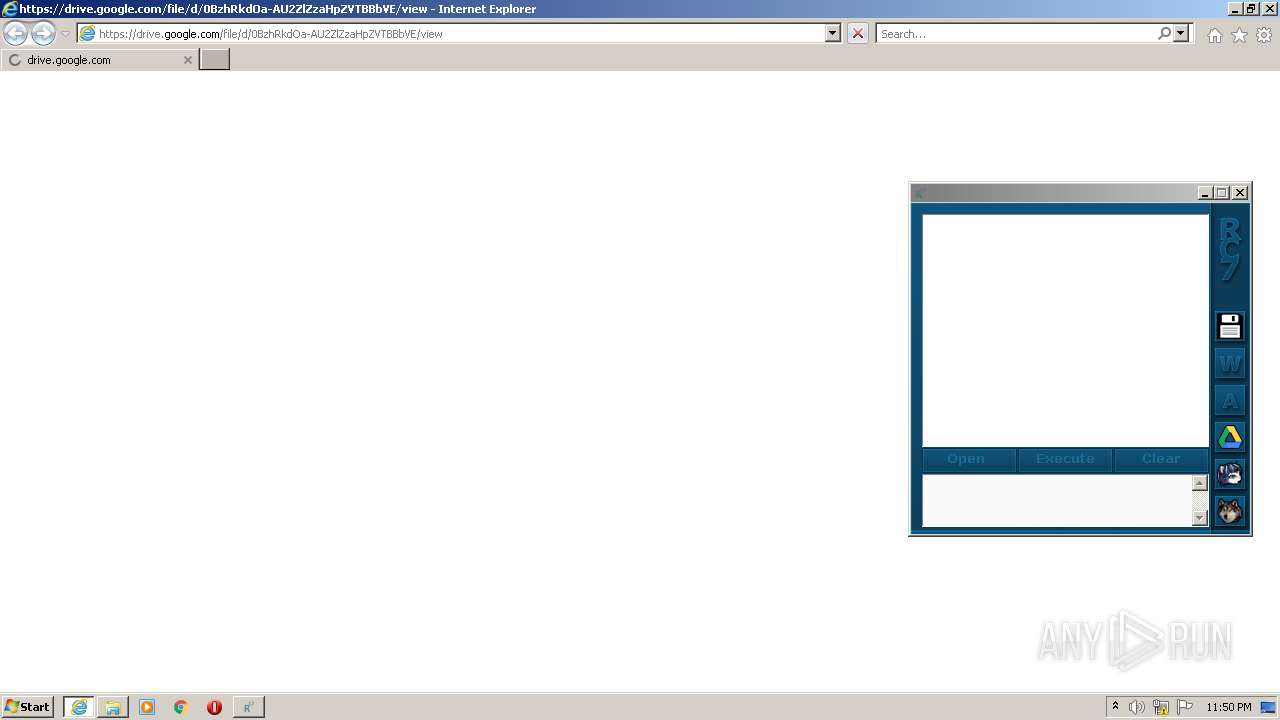
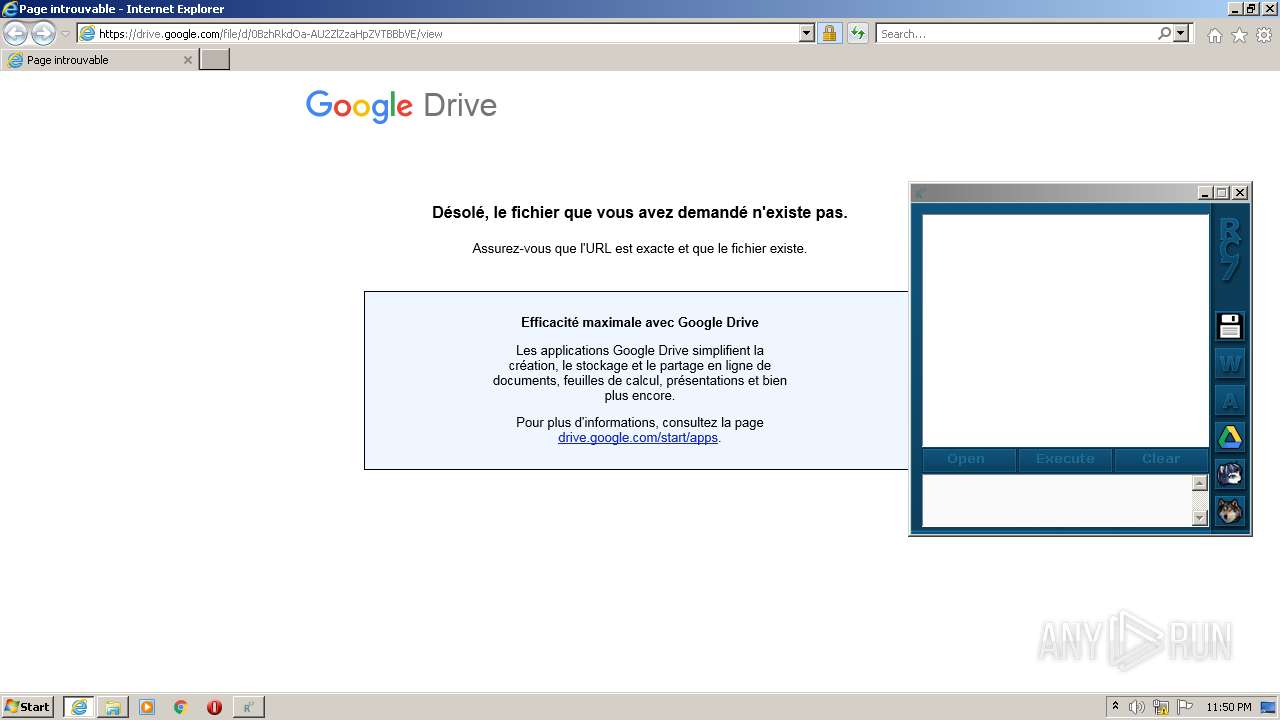
| 2096 | "C:\Program Files\Internet Explorer\iexplore.exe" https://drive.google.com/file/d/0BzhRkdOa-AU2ZlZzaHpZVTBBbVE/view | C:\Program Files\Internet Explorer\iexplore.exe | RC7 CRACKED.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2844 | "C:\Users\admin\Desktop\Newest RC7 Crack\RC7 CRACKED.exe" | C:\Users\admin\Desktop\Newest RC7 Crack\RC7 CRACKED.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3792 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\RC7_NEW.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3824 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2096 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3832 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 3852 | "C:\Users\admin\Desktop\Newest RC7 Crack\Memcheck.exe" | C:\Users\admin\Desktop\Newest RC7 Crack\Memcheck.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3936 | "C:\Users\admin\AppData\Local\Temp\cetrainers\CETF823.tmp\Memcheck.exe" -ORIGIN:"C:\Users\admin\Desktop\Newest RC7 Crack\" | C:\Users\admin\AppData\Local\Temp\cetrainers\CETF823.tmp\Memcheck.exe | Memcheck.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
15 463
Read events
15 322
Write events
140
Delete events
1
Modification events
| (PID) Process: | (3792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3792) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RC7_NEW.rar | |||
| (PID) Process: | (3792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3792) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
9
Suspicious files
12
Text files
6
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3792 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3792.33520\RC7 NEW\Newest RC7 Crack\memcheck(1).dll | executable | |
MD5:D0AED298460A16C1B587875D411B0B4A | SHA256:E4E19790BE03A782497D9CA11F74010B6A016127DE984C7CB67A9AC2D04BDFB6 | |||
| 3852 | Memcheck.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETF823.tmp\CET_Archive.dat | pgc | |
MD5:FCFCC486E4C100F20D99DF8F71F63D2E | SHA256:E8608C6BD3E575965E1A4CCEBA36FC6BE4E9BE86D479FC8CE4AA2A3F97611ACC | |||
| 3852 | Memcheck.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETF823.tmp\Memcheck.exe | executable | |
MD5:6852660B8CBB67EE3F1E31BF2F1E0AFD | SHA256:CD86234CF14DFC0E66AE9E575326FD0CF74723A5A60337F7079C0540B6DA5C8B | |||
| 3936 | Memcheck.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETF823.tmp\extracted\defines.lua | text | |
MD5:1DC41A0A351E745085FCC98A3933D91F | SHA256:A2E02DD32F0245FF31190288B368B3EFBBE7C48A95DD22C321231C2F46597D9B | |||
| 3824 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F2DDCD2B5F37625B82E81F4976CEE400_2C7C232DD1DEC4CAEEDF282CDEC7D367 | binary | |
MD5:— | SHA256:— | |||
| 3824 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:— | SHA256:— | |||
| 3824 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
| 3792 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3792.33520\RC7 NEW\Newest RC7 Crack\Memcheck.exe | executable | |
MD5:EA3726DEC12657F20AD2C861464DD434 | SHA256:1F44175232113CF3F570E863F8E9E0DB15B1D30364498C93CDECCF0D768F3CFE | |||
| 3792 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3792.33520\RC7 NEW\Newest RC7 Crack\0xAzul (2).dll | executable | |
MD5:FB437FA76DF479D1C7F32326494D3922 | SHA256:DF655E9B4AAD5C8C90828755126D8211D6DDD18AA9A38590FFBDA6F6969DF590 | |||
| 3824 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
19
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3824 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
3824 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDIRy5Lqyj5dAoAAAABLgV%2F | US | der | 472 b | whitelisted |
3824 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
2096 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3824 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDKa002niAMOQoAAAABLgV0 | US | der | 472 b | whitelisted |
3824 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDfzJPL1j6yvwoAAAABLgJc | US | der | 472 b | whitelisted |
2096 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3824 | iexplore.exe | GET | 200 | 2.16.106.233:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5fc378161150ad86 | unknown | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3824 | iexplore.exe | 216.58.212.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3824 | iexplore.exe | 2.16.106.233:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | whitelisted |
3824 | iexplore.exe | 142.250.186.174:443 | drive.google.com | Google Inc. | US | whitelisted |
3824 | iexplore.exe | 142.250.186.131:443 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3824 | iexplore.exe | 142.250.186.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2096 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2096 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3824 | iexplore.exe | 142.250.185.67:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2096 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
drive.google.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Memcheck.exe | Offset of LBR_Count=760 |
Memcheck.exe | sizeof fxstate = 512 |
Memcheck.exe | TSymhandler.create |
Memcheck.exe | TSymhandler.create 1 |
Memcheck.exe | TSymhandler.create 2 |
Memcheck.exe | TSymhandler.create 3 |
Memcheck.exe | TSymbolListHandler.create 1 |
Memcheck.exe | TSymbolListHandler.create 2 |
Memcheck.exe | TSymbolListHandler.create exit |
Memcheck.exe | TSymhandler.create exit |